Security Services
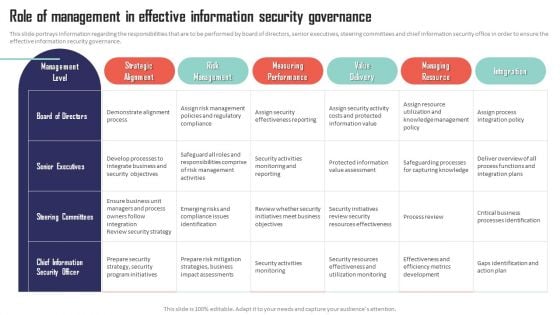
Mobile Device Management Role Of Management In Effective Information Security Microsoft PDF
This slide portrays information regarding the responsibilities that are to be performed by board of directors, senior executives, steering committees and chief information security office in order to ensure the effective information security governance. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Mobile Device Management Role Of Management In Effective Information Security Microsoft PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates
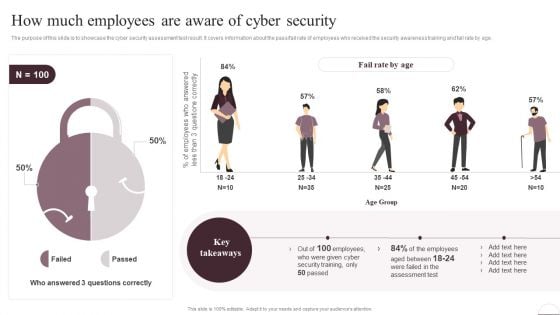
Prevention Of Information How Much Employees Are Aware Of Cyber Security Slides PDF
The purpose of this slide is to showcase the cyber security assessment test result. It covers information about the pass or fail rate of employees who received the security awareness training and fail rate by age. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Prevention Of Information How Much Employees Are Aware Of Cyber Security Slides PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates

Comparative Analysis Of Cloud And Traditional Computing It Security Diagrams PDF
This slide provide the difference between the cloud computer security and standard computer security that enable manager to choose the best strategy. It shows the variation of data centers, initial cost investment, price, time to market etc.Persuade your audience using this Comparative Analysis Of Cloud And Traditional Computing It Security Diagrams PDF. This PPT design covers one stage, thus making it a great tool to use. It also caters to a variety of topics including Provided Parties, Initial Cost Investment, Comparatively Longer. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
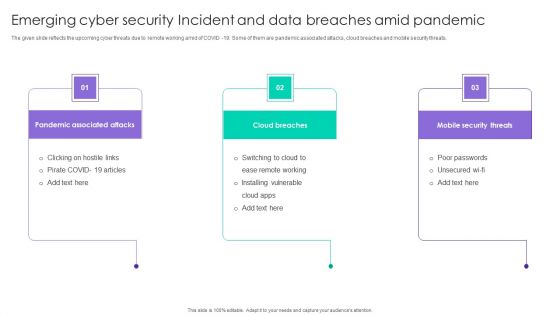
Emerging Cyber Security Incident And Data Breaches Amid Pandemic Ppt Ideas Skills PDF
The given slide reflects the upcoming cyber threats due to remote working amid of COVID -19. Some of them are pandemic associated attacks, cloud breaches and mobile security threats. Persuade your audience using this Emerging Cyber Security Incident And Data Breaches Amid Pandemic Ppt Ideas Skills PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Pandemic Associated Attacks, Cloud Breaches, Mobile Security Threats. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
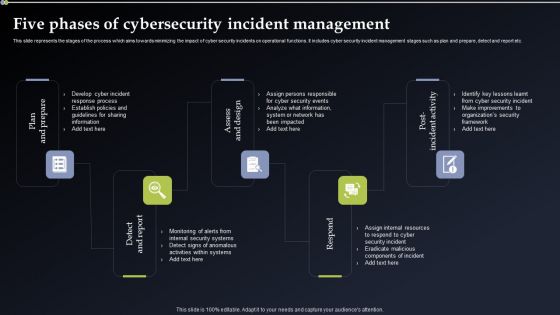
Deploying Cyber Security Incident Response Administration Five Phases Of Cybersecurity Incident Management Diagrams PDF
This slide represents the stages of the process which aims towards minimizing the impact of cyber security incidents on operational functions. It includes cyber security incident management stages such as plan and prepare, detect and report etc. There are so many reasons you need a Deploying Cyber Security Incident Response Administration Five Phases Of Cybersecurity Incident Management Diagrams PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

IT OT Convergence Security Objectives Challenges Catalysts And Benefits Designs PDF
This slide covers objectives challenges catalysts and benefits of the Security in IT OT convergence and Reduce systems cyberattack surface. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward IT OT Convergence Security Objectives Challenges Catalysts And Benefits Designs PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal IT OT Convergence Security Objectives Challenges Catalysts And Benefits Designs PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.
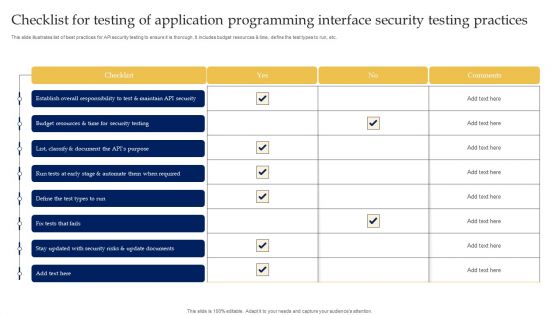
Checklist For Testing Of Application Programming Interface Security Testing Practices Microsoft PDF
This slide illustrates list of best practices for API security testing to ensure it is thorough. It includes budget resources and time, define the test types to run, etc. Showcasing this set of slides titled Checklist For Testing Of Application Programming Interface Security Testing Practices Microsoft PDF. The topics addressed in these templates are Application Programming, Interface Security, Testing Practices. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
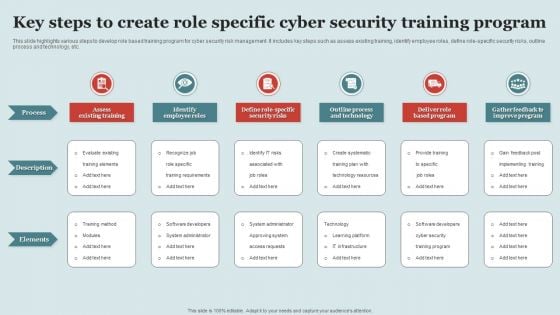
Key Steps To Create Role Specific Cyber Security Training Program Structure PDF
This slide highlights various steps to develop role based training program for cyber security risk management. It includes key steps such as assess existing training, identify employee roles, define role-specific security risks, outline process and technology, etc. Persuade your audience using this Key Steps To Create Role Specific Cyber Security Training Program Structure PDF This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Process, Description, Elements. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Proposal For Enterprise Security System Case Study One Pager Sample Example Document
The following slide displays the case study for security system proposal, as it highlights the project description, project results, project budget and project timeline. Presenting you an exemplary Proposal For Enterprise Security System Case Study One Pager Sample Example Document. Our one pager comprises all the must have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Proposal For Enterprise Security System Case Study One Pager Sample Example Document brilliant piece now.

Proposal For Enterprise Security System Cover Letter One Pager Sample Example Document
The following slide displays the cover slide for the security system proposal, as it highlights the key details of the client requirement. Presenting you an exemplary Proposal For Enterprise Security System Cover Letter One Pager Sample Example Document. Our one pager comprises all the must have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Proposal For Enterprise Security System Cover Letter One Pager Sample Example Document brilliant piece now.

Proposal For Enterprise Security System Next Step One Pager Sample Example Document
The following slide displays the next step that the organization has to take once the security proposal has been signed, these steps can be tem meeting ,on-site visit etc. Presenting you an exemplary Proposal For Enterprise Security System Next Step One Pager Sample Example Document. Our one pager comprises all the must have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Proposal For Enterprise Security System Next Step One Pager Sample Example Document brilliant piece now.
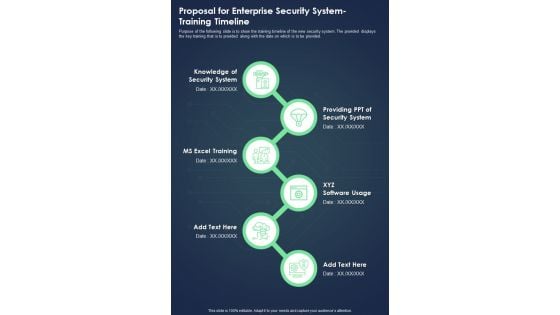
Proposal For Enterprise Security System Training Timeline One Pager Sample Example Document
Purpose of the following slide is to show the training timeline of the new security system. The provided displays the key training that is to provided along with the date on which is to be provided. Presenting you an exemplary Proposal For Enterprise Security System Training Timeline One Pager Sample Example Document. Our one pager comprises all the must have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Proposal For Enterprise Security System Training Timeline One Pager Sample Example Document brilliant piece now.

Proposal For Enterprise Security System Your Investment One Pager Sample Example Document
The following slide displays the investment required by the origination to implement the new security system Presenting you an exemplary Proposal For Enterprise Security System Your Investment One Pager Sample Example Document. Our one pager comprises all the must have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Proposal For Enterprise Security System Your Investment One Pager Sample Example Document brilliant piece now.
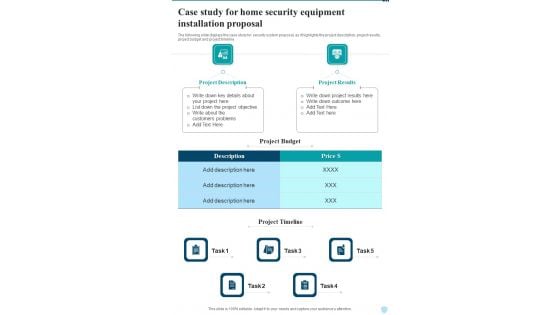
Case Study For Home Security Equipment Installation Proposal One Pager Sample Example Document
The following slide displays the case study for security system proposal, as it highlights the project description, project results, project budget and project timeline Presenting you an exemplary Case Study For Home Security Equipment Installation Proposal One Pager Sample Example Document. Our one pager comprises all the must have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Case Study For Home Security Equipment Installation Proposal One Pager Sample Example Document brilliant piece now.
Cover Letter For Home Security Equipment Installation Proposal One Pager Sample Example Document
The following slide displays the cover slide for the security system proposal, as it highlights the key details of the client requirement. Presenting you an exemplary Cover Letter For Home Security Equipment Installation Proposal One Pager Sample Example Document. Our one pager comprises all the must have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Cover Letter For Home Security Equipment Installation Proposal One Pager Sample Example Document brilliant piece now.

Next Step For Home Security Equipment Installation Proposal One Pager Sample Example Document
The following slide displays the next step that the organization has to take once the security proposal has been signed, these steps can be tem meeting ,on site visit etc. Presenting you an exemplary Next Step For Home Security Equipment Installation Proposal One Pager Sample Example Document. Our one pager comprises all the must have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Next Step For Home Security Equipment Installation Proposal One Pager Sample Example Document brilliant piece now.
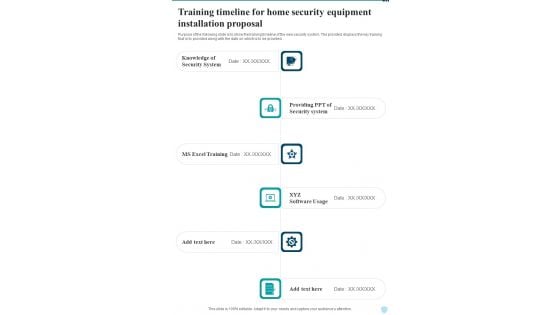
Training Timeline For Home Security Equipment Installation Proposal One Pager Sample Example Document
Purpose of the following slide is to show the training timeline of the new security system. The provided displays the key training that is to provided along with the date on which is to be provided. Presenting you an exemplary Training Timeline For Home Security Equipment Installation Proposal One Pager Sample Example Document. Our one pager comprises all the must have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Training Timeline For Home Security Equipment Installation Proposal One Pager Sample Example Document brilliant piece now.
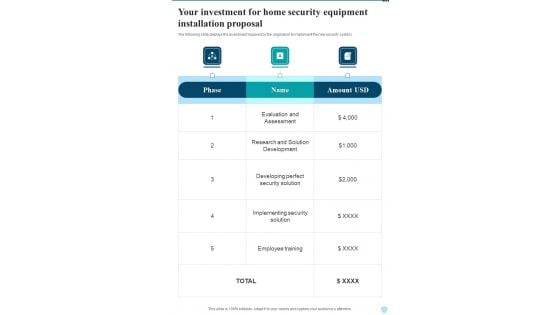
Your Investment For Home Security Equipment Installation Proposal One Pager Sample Example Document
The following slide displays the investment required by the origination to implement the new security system. Presenting you an exemplary Your Investment For Home Security Equipment Installation Proposal One Pager Sample Example Document. Our one pager comprises all the must have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Your Investment For Home Security Equipment Installation Proposal One Pager Sample Example Document brilliant piece now.
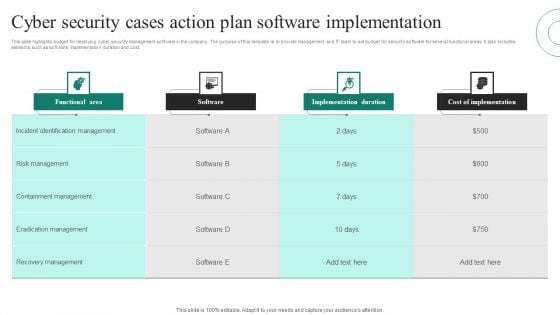
Cyber Security Cases Action Plan Software Implementation Ppt PowerPoint Presentation File Grid PDF
This slide highlights budget for deploying cyber security management software in the company. The purpose of this template is to provide management and IT team to set budget for security software for several functional areas. It also includes elements such as software, implementation duration and cost. Pitch your topic with ease and precision using this Cyber Security Cases Action Plan Software Implementation Ppt PowerPoint Presentation File Grid PDF. This layout presents information on Functional Area, Software, Implementation Duration, Cost Implementation. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
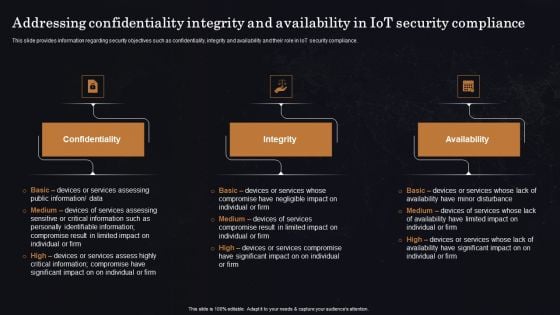
Addressing Confidentiality Integrity And Availability In Iot Security Compliance Ppt Portfolio Deck PDF
This slide provides information regarding security objectives such as confidentiality, integrity and availability and their role in IoT security compliance. Boost your pitch with our creative Addressing Confidentiality Integrity And Availability In Iot Security Compliance Ppt Portfolio Deck PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
Cloud Security Standards And Control Frameworks Ppt PowerPoint Presentation File Icon PDF
This slide provides an overview of the cloud security protocols and control frameworks. The purpose of this slide is to showcase the various information security standards and control frameworks, including ISO-27001, ISO-27017, ISO-27018, GDPR, SOC reporting, PCI DSS, and HIPAA. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Cloud Security Standards And Control Frameworks Ppt PowerPoint Presentation File Icon PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.

Requirements For Appropriate Cloud Security Model Ppt PowerPoint Presentation File Gallery PDF
This slide outlines the different prerequisites organizations should consider when choosing a cloud security model and provider. The purpose of this slide is to showcase the various requirements a cloud security provider should possess, including visibility and threat detection, continuous compliance, data encryption and so on. There are so many reasons you need a Requirements For Appropriate Cloud Security Model Ppt PowerPoint Presentation File Gallery PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
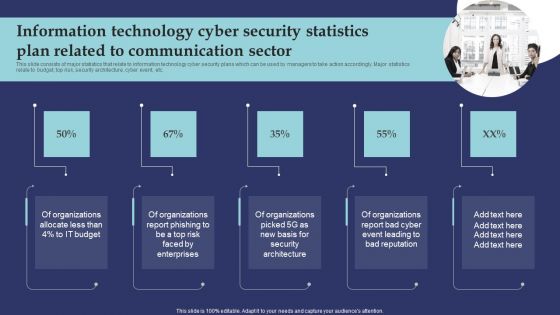
Information Technology Cyber Security Statistics Plan Related To Communication Sector Microsoft PDF
This slide consists of major statistics that relate to information technology cyber security plans which can be used by managers to take action accordingly. Major statistics relate to budget, top risk, security architecture, cyber event, etc. Presenting Information Technology Cyber Security Statistics Plan Related To Communication Sector Microsoft PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Organizations Allocate, Organizations Report Phishing, Organizations Report Bad Cyber. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Impact Of Cyber Security Policies And Practices Ppt PowerPoint Presentation Diagram Graph Charts PDF
The following slide focuses on drafting cyber security policies to manage data control and breach. It mainly includes elements such as impact of existing cyber safety policies, mitigation actions, Presenting this PowerPoint presentation, titled Impact Of Cyber Security Policies And Practices Ppt PowerPoint Presentation Diagram Graph Charts PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Impact Of Cyber Security Policies And Practices Ppt PowerPoint Presentation Diagram Graph Charts PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Impact Of Cyber Security Policies And Practices Ppt PowerPoint Presentation Diagram Graph Charts PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.
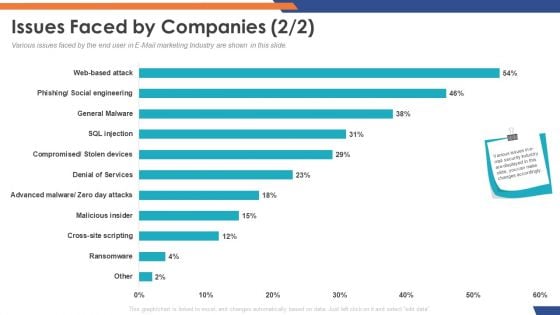
Email Security Market Research Report Issues Faced By Companies Cross Site Download PDF
Presenting this set of slides with name email security market research report issues faced by companies cross site download pdf. The topics discussed in these slides are general malware, social engineering, cross site scripting, denial of service, web based attack. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
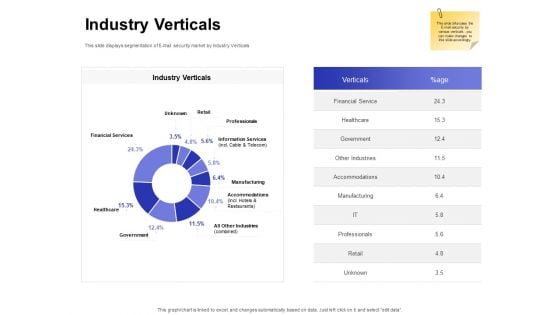
Global Cloud Based Email Security Market Industry Verticals Retail Demonstration PDF
Presenting this set of slides with name global cloud based email security market industry verticals retail demonstration pdf. The topics discussed in these slides are financial service, healthcare, government, accommodations, professionals, manufacturing, retail. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Global Cloud Based Email Security Market Issues Faced By Companies Download PDF
Presenting this set of slides with name global cloud based email security market issues faced by companies download pdf. The topics discussed in these slides are general malware, social engineering, cross site scripting, denial of service, web based attack. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Password Protection Information Security Icon Ppt Powerpoint Presentation Visual Aids Portfolio
This is a password protection information security icon ppt powerpoint presentation visual aids portfolio. This is a three stage process. The stages in this process are password, access approval, authentication icon.

Challenges For New Entrants In Global Security Industry PPT Example IR SS V
The slide showcases the barriers to entry in Defense industry. The main purpose of this slide is to recognize the variables that may impede or make it difficult for new entrants to enter the market successfully. By identifying these impediments, aspiring Defense companies can make educated judgements and establish appropriate strategies to overcome or manage them efficiently. Want to ace your presentation in front of a live audience Our Challenges For New Entrants In Global Security Industry PPT Example IR SS V can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. The slide showcases the barriers to entry in Defense industry. The main purpose of this slide is to recognize the variables that may impede or make it difficult for new entrants to enter the market successfully. By identifying these impediments, aspiring Defense companies can make educated judgements and establish appropriate strategies to overcome or manage them efficiently.

Implementing Safety Administration Initiative For Risk Mitigation Way To Overcome Security Demonstration PDF
This slide provides information about the way that the company and IT security manager must choose in order to solve the challenge or problem related to Potential Insider Threats. the solution is to set up an advanced security management plan in place with the help of a set series of steps mentioned in the slide. This is a implementing safety administration initiative for risk mitigation way to overcome security demonstration pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like goals, information, risk, analysis, management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Various CSR Initiatives Taken Global Security Industry PPT Presentation IR SS V
The slide highlights csr initiatives taken in Defense sector. It is to ensure market stability, consumer protection and foster innovation while mitigating risks. It includes financial education and literacy, supporting vulnerable communities, disaster relief and preparedness. This Various CSR Initiatives Taken Global Security Industry PPT Presentation IR SS V from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. The slide highlights csr initiatives taken in Defense sector. It is to ensure market stability, consumer protection and foster innovation while mitigating risks. It includes financial education and literacy, supporting vulnerable communities, disaster relief and preparedness.
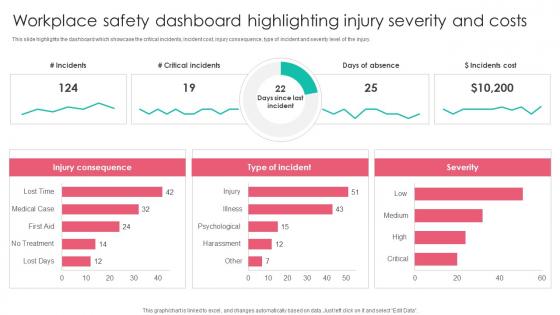
Workplace Safety Dashboard Highlighting Workplace Safety Protocol And Security Practices Elements Pdf
This slide highlights the dashboard which showcase the critical incidents, incident cost, injury consequence, type of incident and severity level of the injury. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Workplace Safety Dashboard Highlighting Workplace Safety Protocol And Security Practices Elements Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide highlights the dashboard which showcase the critical incidents, incident cost, injury consequence, type of incident and severity level of the injury.
Virtual Private Network With Internet Security Firewall Protection Ppt PowerPoint Presentation File Master Slide PDF
Persuade your audience using this virtual private network with internet security firewall protection ppt powerpoint presentation file master slide pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including virtual private network with internet security firewall protection. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
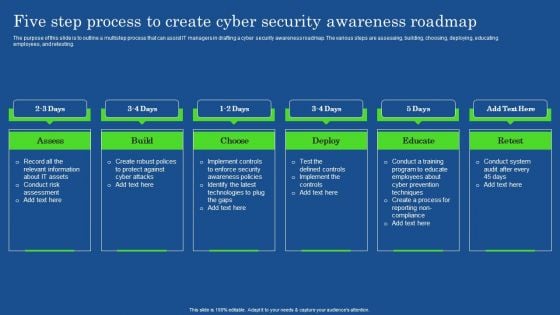
Five Step Process To Create Cyber Security Awareness Roadmap Microsoft PDF
The purpose of this slide is to outline a multistep process that can assist IT managers in drafting a cyber security awareness roadmap. The various steps are assessing, building, choosing, deploying, educating employees, and retesting. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Five Step Process To Create Cyber Security Awareness Roadmap Microsoft PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Five Step Process To Create Cyber Security Awareness Roadmap Microsoft PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers

Global Data Security Industry Report Growth And Future Prospects In The Cybersecurity Industry IR SS V
The slide highlights the future outlook and potential for the cybersecurity industry. The purpose of the slide is to inform stakeholders regarding growth opportunities, creating a compelling case for investment and collaboration. It covers drivers, trends, and the revolutionary impact of the industry. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Global Data Security Industry Report Growth And Future Prospects In The Cybersecurity Industry IR SS V and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. The slide highlights the future outlook and potential for the cybersecurity industry. The purpose of the slide is to inform stakeholders regarding growth opportunities, creating a compelling case for investment and collaboration. It covers drivers, trends, and the revolutionary impact of the industry.
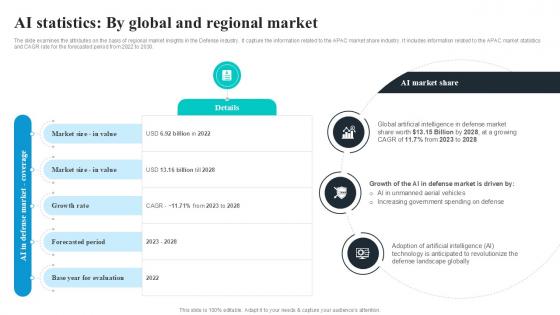
AI Statistics By Global And Regional Global Security Industry PPT Template IR SS V
The slide examines the attributes on the basis of regional market insights in the Defense industry. It capture the information related to the APAC market share industry. It includes information related to the APAC market statistics and CAGR rate for the forecasted period from 2022 to 2030. Boost your pitch with our creative AI Statistics By Global And Regional Global Security Industry PPT Template IR SS V. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. The slide examines the attributes on the basis of regional market insights in the Defense industry. It capture the information related to the APAC market share industry. It includes information related to the APAC market statistics and CAGR rate for the forecasted period from 2022 to 2030.

Market Restraints Impacting The Global Security Industry PPT Template IR SS V
The slide provides an insight on the market restraints existing in the Defense market. The purpose of this slide is to aware about the different areas of Defense which are impacted. It capture the information related to short comings faced in the industry. This modern and well-arranged Market Restraints Impacting The Global Security Industry PPT Template IR SS V provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. The slide provides an insight on the market restraints existing in the Defense market. The purpose of this slide is to aware about the different areas of Defense which are impacted. It capture the information related to short comings faced in the industry.

Working Of Common Data Encryption Data Security In Cloud Computing Ppt Example
This slide represents the working flow of Common Data Encryption DES algorithm. The purpose of this slide is to outline the algorithm steps. This slide also explains the DES modes of operation, which include Digital Codebook, Cipher Block Chaining, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Working Of Common Data Encryption Data Security In Cloud Computing Ppt Example and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide represents the working flow of Common Data Encryption DES algorithm. The purpose of this slide is to outline the algorithm steps. This slide also explains the DES modes of operation, which include Digital Codebook, Cipher Block Chaining, etc.
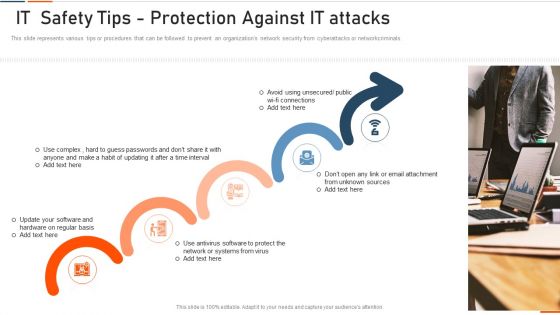
Information Technology Security IT Safety Tips Protection Against IT Attacks Ppt Layouts Outfit PDF
This slide represents various tips or procedures that can be followed to prevent an organizations network security from cyberattacks or networkcriminals. This is a information technology security it safety tips protection against it attacks ppt layouts outfit pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like network, antivirus, systems, sources, unsecured. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Execution Of ICT Strategic Plan Network Security Model To Effective Communication Demonstration PDF
This slide represents the network security model for effective communication in the organization. It covers information regarding security threats, firewalls, virtual private networks, etc. Get a simple yet stunning designed Execution Of ICT Strategic Plan Network Security Model To Effective Communication Demonstration PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Execution Of ICT Strategic Plan Network Security Model To Effective Communication Demonstration PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
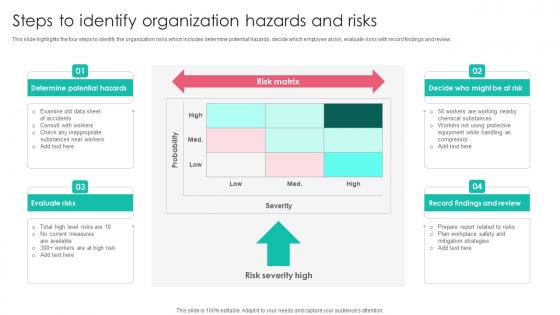
Steps To Identify Organization Hazards Workplace Safety Protocol And Security Practices Template Pdf
This slide highlights the four steps to identify the organization risks which includes determine potential hazards, decide which employee at risk, evaluate risks with record findings and review. Want to ace your presentation in front of a live audience Our Steps To Identify Organization Hazards Workplace Safety Protocol And Security Practices Template Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use. This slide highlights the four steps to identify the organization risks which includes determine potential hazards, decide which employee at risk, evaluate risks with record findings and review.
Data Protection Security Controls Ppt PowerPoint Presentation File Designs Cpb Pdf
Presenting this set of slides with name data protection security controls ppt powerpoint presentation file designs cpb pdf. This is an editable Powerpoint five stages graphic that deals with topics like data protection security controls to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
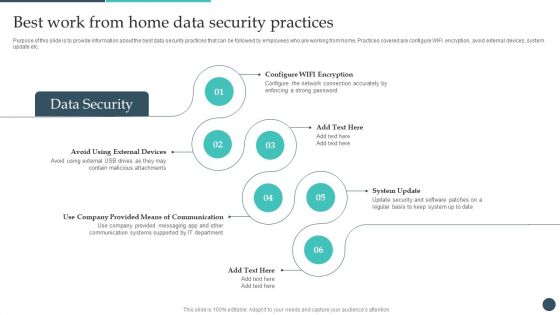
Safety Breach Response Playbook Best Work From Home Data Security Practices Topics PDF
Purpose of this slide is to provide information about the best data security practices that can be followed by employees who are working from home. Practices covered are configure WIFI encryption, avoid external devices, system update etc. Explore a selection of the finest Safety Breach Response Playbook Best Work From Home Data Security Practices Topics PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Safety Breach Response Playbook Best Work From Home Data Security Practices Topics PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

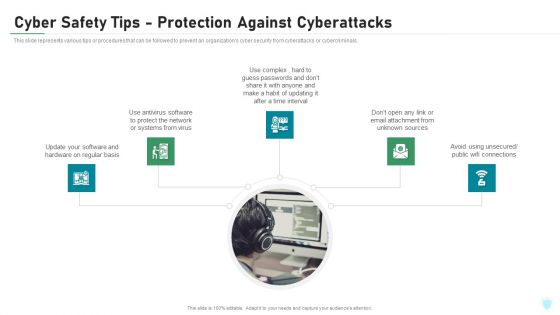
Info Security Cyber Safety Tips Protection Against Cyberattacks Ppt PowerPoint Presentation Gallery Designs Download PDF
This slide represents various tips or procedures that can be followed to prevent an organizations cyber security from cyberattacks or cybercriminals. This is a info security cyber safety tips protection against cyberattacks ppt powerpoint presentation gallery designs download pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like protect the network, email attachment, time interval. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Desktop Security Management Cyber Safety Tips Protection Against Cyberattacks Download PDF
This slide represents various tips or procedures that can be followed to prevent an organizations cyber security from cyberattacks or cybercriminals. Presenting desktop security management cyber safety tips protection against cyberattacks download pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like systems, network, sources. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
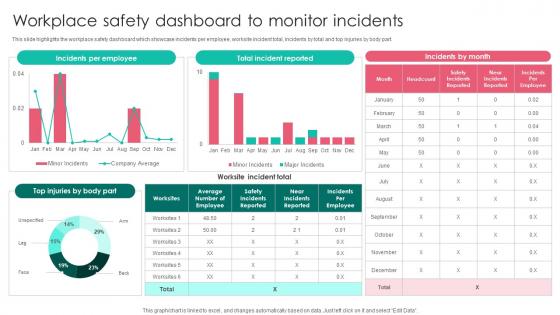
Workplace Safety Dashboard Monitor Workplace Safety Protocol And Security Practices Demonstration Pdf
This slide highlights the workplace safety dashboard which showcase incidents per employee, worksite incident total, incidents by total and top injuries by body part. Present like a pro with Workplace Safety Dashboard Monitor Workplace Safety Protocol And Security Practices Demonstration Pdf Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide highlights the workplace safety dashboard which showcase incidents per employee, worksite incident total, incidents by total and top injuries by body part.
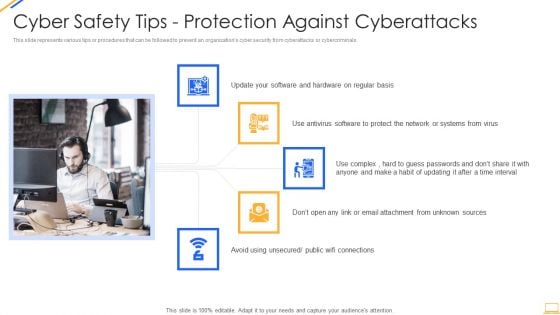
Cyber Safety Tips Protection Against Cyberattacks IT Security IT Ppt File Aids PDF
This slide represents various tips or procedures that can be followed to prevent an organizations cyber security from cyberattacks or cybercriminals. Presenting cyber safety tips protection against cyberattacks it security it ppt file aids pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like cyber safety tips protection against cyberattacks. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
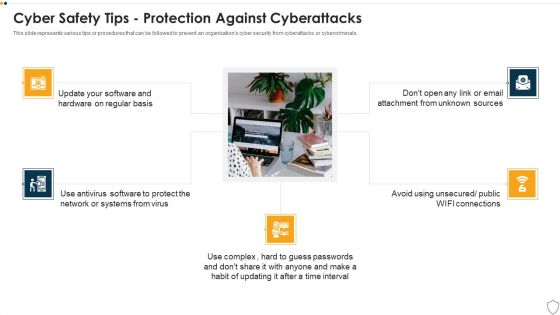
IT Security Cyber Safety Tips Protection Against Cyberattacks Ppt Portfolio Diagrams PDF
This slide represents various tips or procedures that can be followed to prevent an organizations cyber security from cyberattacks or cybercriminals. This is a it security cyber safety tips protection against cyberattacks ppt portfolio diagrams pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cyber safety tips protection against cyberattacks. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Process For Information Security Risk Assessment Cybersecurity Risk Assessment Portrait PDF
This slide showcases process that can help organization to perform information security risk assessment. It can help identify security threats and allocate vulnerability rating to information assets. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Process For Information Security Risk Assessment Cybersecurity Risk Assessment Portrait PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Process For Information Security Risk Assessment Cybersecurity Risk Assessment Portrait PDF today and make your presentation stand out from the rest.
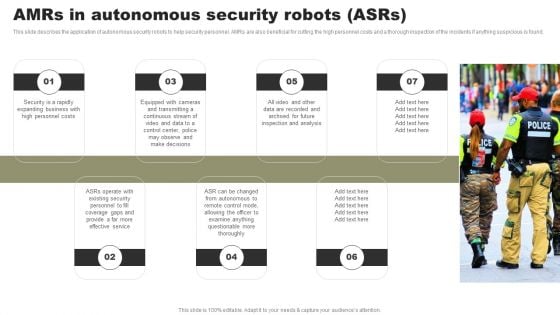
Types Of Independent Robotic System Amrs In Autonomous Security Robots Asrs Brochure PDF
This slide describes the application of autonomous security robots to help security personnel. AMRs are also beneficial for cutting the high personnel costs and a thorough inspection of the incidents if anything suspicious is found. Create an editable Types Of Independent Robotic System Amrs In Autonomous Security Robots Asrs Brochure PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre designed presentation templates help save time. Types Of Independent Robotic System Amrs In Autonomous Security Robots Asrs Brochure PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Key Security Considerations For 5G For Threat Handling 5G Network Architecture Instructions Diagrams PDF
This slide provides details regarding key security considerations associated to 5G in order to handle threats such as data breach, denial of service, unauthorized activities, etc. Deliver and pitch your topic in the best possible manner with this Key Security Considerations For 5G For Threat Handling 5G Network Architecture Instructions Diagrams PDF. Use them to share invaluable insights on Nodes Authentication, Rule Consistency, Policy Enforcement and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Data Privacy Data Security Ppt PowerPoint Presentation Ideas Sample Cpb Pdf
Presenting this set of slides with name data privacy data security ppt powerpoint presentation ideas sample cpb pdf. This is an editable Powerpoint four stages graphic that deals with topics like data privacy data security to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Data Security Privacy Ppt PowerPoint Presentation Summary Vector Cpb Pdf Pdf
Presenting this set of slides with name data security privacy ppt powerpoint presentation summary vector cpb pdf pdf. This is an editable Powerpoint four stages graphic that deals with topics like data security privacy to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Safety Guidelines To Control Fire At Workplace Safety Protocol And Security Practices Microsoft Pdf
This slide highlights the measures to control fire at workplace which includes steps such as raise the alarm, alert everyone, fight fire and evacuate from the worksite. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Safety Guidelines To Control Fire At Workplace Safety Protocol And Security Practices Microsoft Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide highlights the measures to control fire at workplace which includes steps such as raise the alarm, alert everyone, fight fire and evacuate from the worksite.
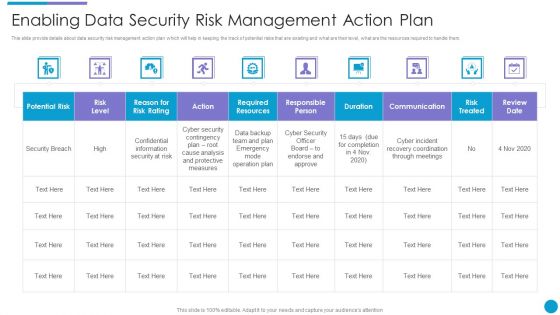
Major Techniques For Project Safety IT Enabling Data Security Risk Management Action Plan Template PDF
This slide provide details about data security risk management action plan which will help in keeping the track of potential risks that are existing and what are their level, what are the resources required to handle them. Deliver and pitch your topic in the best possible manner with this major techniques for project safety it enabling data security risk management action plan template pdf. Use them to share invaluable insights on communication, duration, risk treated, action, risk level and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
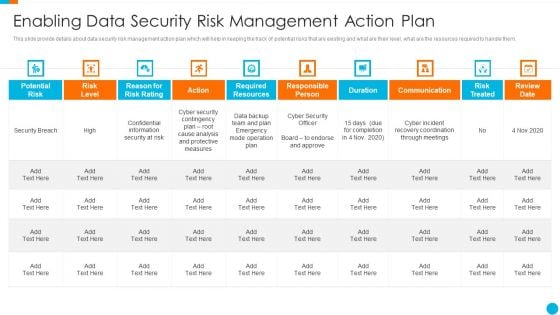
Upgrading Total Project Safety IT Enabling Data Security Risk Management Action Plan Template PDF
This slide provide details about data security risk management action plan which will help in keeping the track of potential risks that are existing and what are their level, what are the resources required to handle them. Deliver and pitch your topic in the best possible manner with this upgrading total project safety it enabling data security risk management action plan template pdf. Use them to share invaluable insights on potential risk, risk level, reason for risk rating, action, required resources, communication and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Network Security Devices Computer Network Ppt PowerPoint Presentation Visual Aids Background Images Cpb Pdf
Presenting this set of slides with name network security devices computer network ppt powerpoint presentation visual aids background images cpb pdf. This is an editable Powerpoint three stages graphic that deals with topics like network security devices computer network to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Business Diagram Correct Wrong And Security Icons For Antivirus Software Presentation Template
This business slide displays correct wrong and security icons. Download this slide to depict antivirus and software protection related concepts. It will make your presentation look professional and keep your audience mesmerized.
Mail With Key Email Security Vector Icon Ppt Powerpoint Presentation Icon Templates
This is a mail with key email security vector icon ppt powerpoint presentation icon templates. This is a three stage process. The stages in this process are password, access approval, authentication icon.
Network Monitoring Management Security Ppt PowerPoint Presentation Summary Clipart Images Cpb
Presenting this set of slides with name network monitoring management security ppt powerpoint presentation summary clipart images cpb. This is an editable Powerpoint five stages graphic that deals with topics like network monitoring management security to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.


 Continue with Email
Continue with Email

 Home
Home


































