Security Strategy
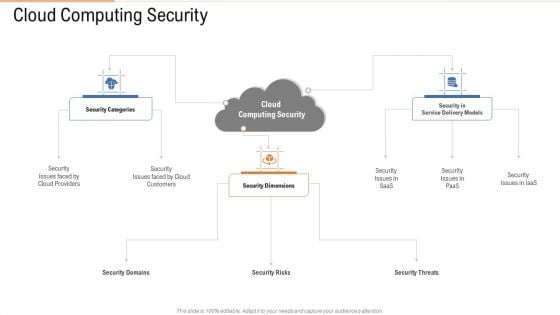
Cloud Computing Security Ppt Portfolio Background Images PDF
Presenting cloud computing security ppt portfolio background images pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like security dimensions, customers, security categories. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
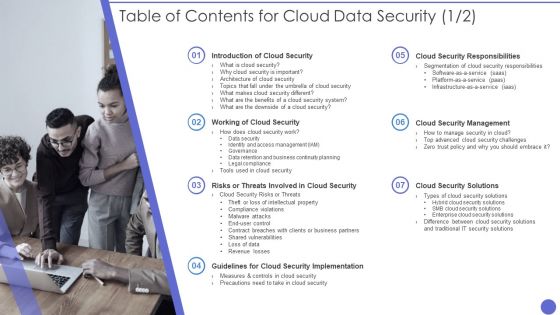
Table Of Contents For Cloud Data Security Formats PDF
Presenting Table Of Contents For Cloud Data Security Formats PDF to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like Cloud Security, Security System, Benefits. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Icon Showcasing Effective Online Security Policy Topics PDF
Persuade your audience using this Icon Showcasing Effective Online Security Policy Topics PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Icon Showcasing Effective, Online Security Policy. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Evaluation Of HR Security Policy And Procedure Diagrams PDF
Persuade your audience using this Evaluation Of HR Security Policy And Procedure Diagrams PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Evaluation HR Security, Policy Procedure. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Exploring Investment Opportunities With Security Token Offerings Complete Deck
This seventy nine slide Exploring Investment Opportunities With Security Token Offerings Complete Deck is your content ready tool to impress the stakeholders with your business planning and its manner of execution. Showcase your ideas and how you plan to make them real in detail with this PPT Template Bundle. The slides have the conceptual bandwidth to present the crucial aspects of your plan, such as funding, marketing, resource allocation, timeline, roadmap, and more. When you present your plans with this PPT Layout, the stakeholders are sure to come on board because you will be able to present a succinct, thought-out, winning project. Download this Complete Deck now to take control into your hands. The 100 percent customizable offer is just too good to be resisted. Our Exploring Investment Opportunities With Security Token Offerings Complete Deck are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Addressing The Various Security Incidents And Attacks Icons PDF
Purpose of this slide is to educate team members about different security incidents and attacks. It includes information about traditional security incidents, cyber security attacks and common techniques.Create an editable Addressing The Various Security Incidents And Attacks Icons PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Addressing The Various Security Incidents And Attacks Icons PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Organizational Network Staff Learning Security Awareness Program Timeline Portrait PDF
This slide covers the security awareness implementation timeline for the organization cyber security training plan with conducting a simulated phishing exercise and system vendor risk assessment. Deliver an awe-inspiring pitch with this creative organizational network staff learning security awareness program timeline portrait pdf bundle. Topics like security awareness program timeline can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
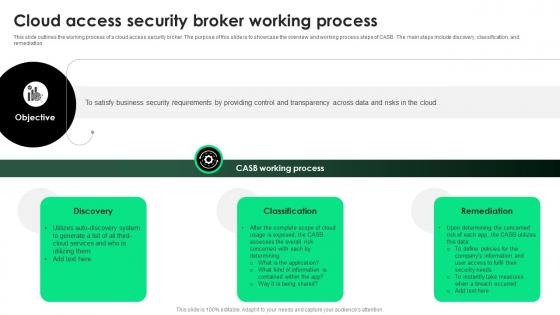
CASB 2 0 IT Cloud Access Security Broker Working Process
This slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, and remediation. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download CASB 2 0 IT Cloud Access Security Broker Working Process to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the CASB 2 0 IT Cloud Access Security Broker Working Process. This slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, and remediation.

Comprehensive Guide To Blockchain Digital Security Risk Management Complete Deck
This Comprehensive Guide To Blockchain Digital Security Risk Management Complete Deck will give you an idea about business planning and how it helps in achievement of objectives and goals. With seventy seven slides,this complete deck aims to ensure that business planning is internalized in the audience. The 100 percent customisable template is also colour coded in a way that visually the message has a very clear impact. The presenter might not be a business expert,but the high quality PPT forces him her to rise to the ocassion. Download now to wow a roomful of people. Our Comprehensive Guide To Blockchain Digital Security Risk Management Complete Deck are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Application Security Testing Ppt Powerpoint Presentation Complete Deck With Slides

Global Security Industry Report Ppt Presentation IR CD V
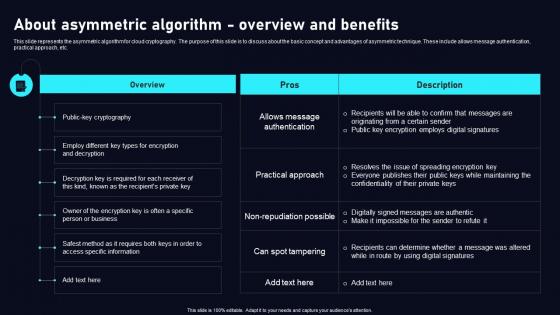
About Asymmetric Algorithm Cloud Data Security Using Cryptography Brochure Pdf
This slide represents the asymmetric algorithm for cloud cryptography. The purpose of this slide is to discuss about the basic concept and advantages of asymmetric technique. These include allows message authentication, practical approach, etc. Get a simple yet stunning designed About Asymmetric Algorithm Cloud Data Security Using Cryptography Brochure Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit About Asymmetric Algorithm Cloud Data Security Using Cryptography Brochure Pdf can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide represents the asymmetric algorithm for cloud cryptography. The purpose of this slide is to discuss about the basic concept and advantages of asymmetric technique. These include allows message authentication, practical approach, etc.
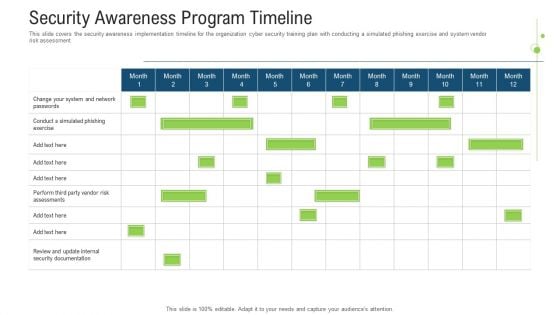
Security Awareness Program Timeline Ppt Outline Introduction PDF
This slide covers the security awareness implementation timeline for the organization cyber security training plan with conducting a simulated phishing exercise and system vendor risk assessment. Deliver an awe inspiring pitch with this creative Security Awareness Program Timeline Ppt Outline Introduction Pdf bundle. Topics like security awareness program timeline can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
6 Step Process To Implement Information Availability Security Icons PDF
This slide represents 6 step process to implement data availability security illustrating simplified recording, on site maintenance and online security, training, record disposal and plan. Presenting 6 step process to implement information availability security icons pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including required, develop, security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Companys Data Safety Recognition Security Awareness Program Checklist Portrait PDF
This slide covers the Checklist that will help organizations prepare and implement their safety awareness training. The details listed below can be used to promote preparation and education planning in the area of security awareness. This is a companys data safety recognition security awareness program checklist portrait pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like implementing security awareness, security awareness program, sustaining security awareness. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Data Breach Prevention Recognition Security Awareness Program Checklist Template PDF
This slide covers the Checklist that will help organizations prepare and implement their safety awareness training. The details listed below can be used to promote preparation and education planning in the area of security awareness. This is a data breach prevention recognition security awareness program checklist template pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like implementing security awareness, sustaining security awareness, document security awareness program. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
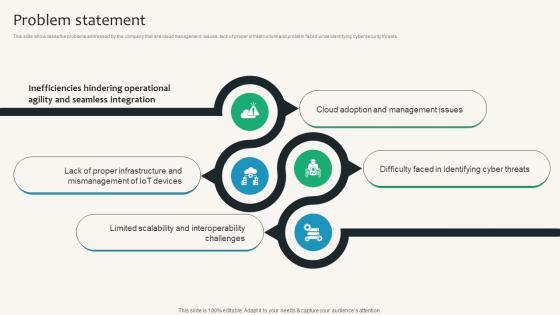
Problem Statement Security Service Provider Business Model BMC SS V
This slide showcases the problems addressed by the company that are cloud management issues, lack of proper infrastructure and problem faced while identifying cybersecurity threats. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Problem Statement Security Service Provider Business Model BMC SS V can be your best option for delivering a presentation. Represent everything in detail using Problem Statement Security Service Provider Business Model BMC SS V and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide showcases the problems addressed by the company that are cloud management issues, lack of proper infrastructure and problem faced while identifying cybersecurity threats.
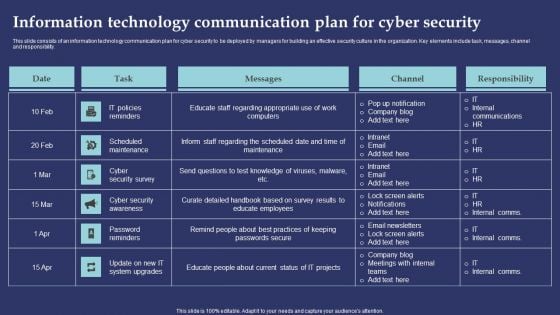
Information Technology Communication Plan For Cyber Security Information PDF
This slide consists of an information technology communication plan for cyber security to be deployed by managers for building an effective security culture in the organization. Key elements include task, messages, channel and responsibility. Showcasing this set of slides titled Information Technology Communication Plan For Cyber Security Information PDF. The topics addressed in these templates are IT Policies Reminders, Scheduled Maintenance, Cyber Security Survey. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
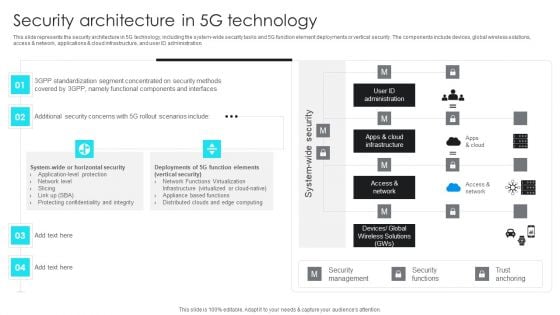
5G Network Operations Security Architecture In 5G Technology Inspiration PDF
This slide represents the security architecture in 5G technology, including the system-wide security tasks and 5G function element deployments or vertical security. The components include devices, global wireless solutions, access and network, applications cloud infrastructure, and user ID administration. Presenting this PowerPoint presentation, titled 5G Network Operations Security Architecture In 5G Technology Inspiration PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this 5G Network Operations Security Architecture In 5G Technology Inspiration PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable 5G Network Operations Security Architecture In 5G Technology Inspiration PDFthat is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.
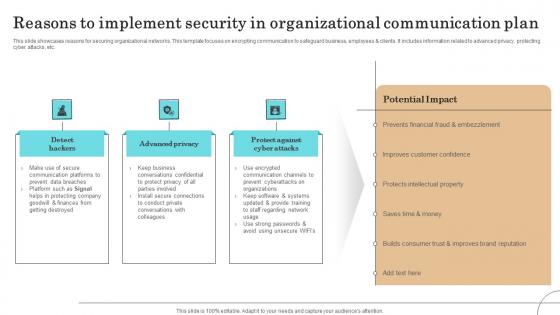
Reasons To Implement Security In Organizational Communication Plan Sample Pdf
This slide showcases reasons for securing organizational networks. This template focuses on encrypting communication to safeguard business, employees clients. It includes information related to advanced privacy, protecting cyber attacks, etc.Showcasing this set of slides titled Reasons To Implement Security In Organizational Communication Plan Sample Pdf The topics addressed in these templates are Communication Platforms, Protecting Company, Improves Customer Confidence All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcases reasons for securing organizational networks. This template focuses on encrypting communication to safeguard business, employees clients. It includes information related to advanced privacy, protecting cyber attacks, etc.
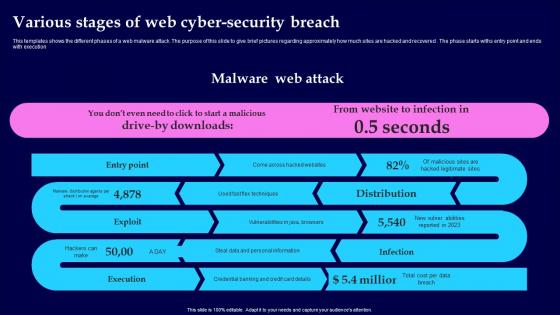
Various Stages Of Web Cyber Security Breach Introduction Pdf
This templates shows the different phases of a web malware attack. The purpose of this slide to give brief pictures regarding approximately how much sites are hacked and recovered. The phase starts withs entry point and ends with execution Pitch your topic with ease and precision using this Various Stages Of Web Cyber Security Breach Introduction Pdf This layout presents information on Malware Web Attack, Various Stages, Cyber Security Breach It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This templates shows the different phases of a web malware attack. The purpose of this slide to give brief pictures regarding approximately how much sites are hacked and recovered. The phase starts withs entry point and ends with execution
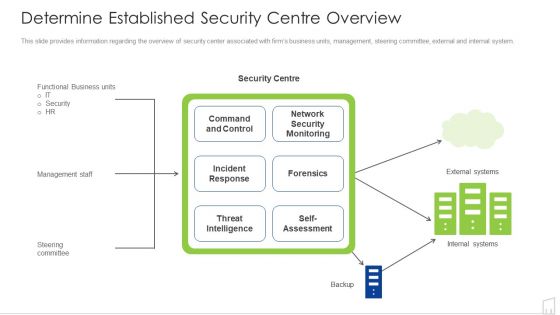
Determine Established Security Centre Overview Ppt Show Visual Aids PDF
This slide provides information regarding the overview of security center associated with firms business units, management, steering committee, external and internal system. Deliver an awe inspiring pitch with this creative determine established security centre overview ppt show visual aids pdf bundle. Topics like security, network, systems, management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
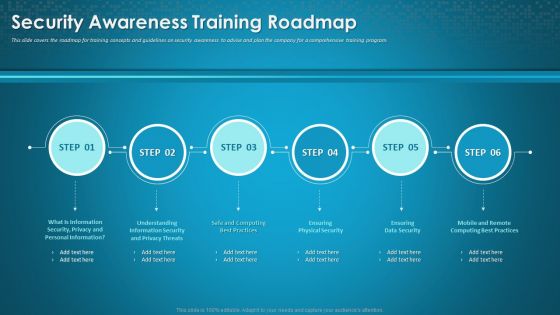
Organizational Network Staff Learning Security Awareness Training Roadmap Sample PDF
This slide covers the roadmap for training concepts and guidelines on security awareness to advise and plan the company for a comprehensive training program. Presenting organizational network staff learning security awareness training roadmap sample pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like ensuring data security, information security and privacy threats, ensuring physical security. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.

Organizational Network Staff Learning Security Awareness Program Checklist Background PDF
This slide covers the Checklist that will help organizations prepare and implement their safety awareness training. The details listed below can be used to promote preparation and education planning in the area of security awareness. Presenting organizational network staff learning security awareness program checklist background pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like security awareness program, implementing security awareness, sustaining security awareness. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.
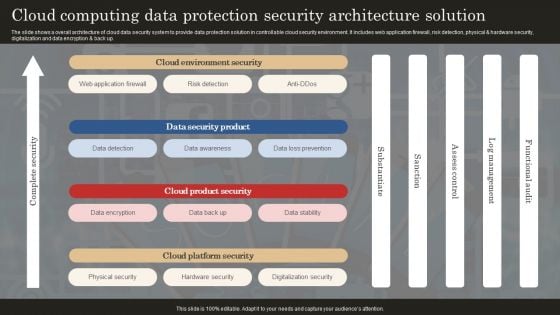
Cloud Computing Data Protection Security Architecture Solution Professional PDF
The slide shows a overall architecture of cloud data security system to provide data protection solution in controllable cloud security environment. It includes web application firewall, risk detection, physical and hardware security, digitalization and data encryption and back up. Showcasing this set of slides titled Cloud Computing Data Protection Security Architecture Solution Professional PDF. The topics addressed in these templates are Web Application Firewall, Data Detection, Data Awareness. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Data Breach Prevention Recognition Security Awareness Program Timeline Inspiration PDF
This slide covers the security awareness implementation timeline for the organization cyber security training plan with conducting a simulated phishing exercise and system vendor risk assessment. Deliver and pitch your topic in the best possible manner with this data breach prevention recognition security awareness program timeline inspiration pdf. Use them to share invaluable insights on security awareness, implementation timeline, organization, cyber security training plan, risk assessment and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
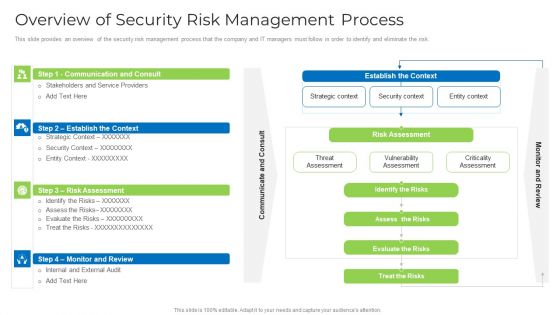
Overview Of Security Risk Management Process Formats PDF
This slide provides an overview of the security risk management process that the company and IT managers must follow in order to identify and eliminate the risk. Deliver an awe inspiring pitch with this creative overview of security risk management process formats pdf bundle. Topics like strategic context, vulnerability assessment, security context, risks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
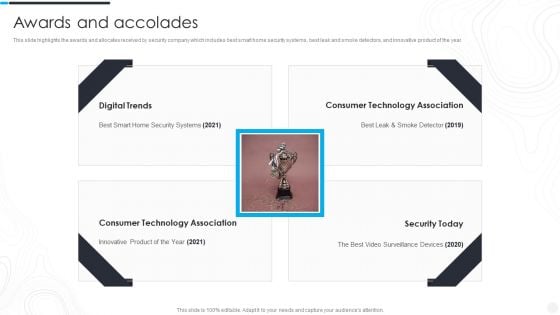
Security Camera System Company Profile Awards And Accolades Portrait PDF
This slide highlights the awards and allocates received by security company which includes best smart home security systems, best leak and smoke detectors, and innovative product of the year.Deliver an awe inspiring pitch with this creative Security Camera System Company Profile Awards And Accolades Portrait PDF bundle. Topics like Digital Trends, Consumer Technology, Technology Association can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
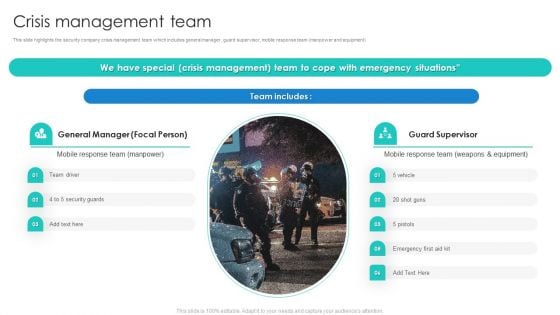
Manpower Corporate Security Business Profile Crisis Management Team Rules PDF
This slide highlights the security company crisis management team which includes general manager, guard supervisor, mobile response team manpower and equipment Deliver an awe inspiring pitch with this creative Manpower Corporate Security Business Profile Crisis Management Team Rules PDF bundle. Topics like Team Driver, Security Guards, Equipment can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
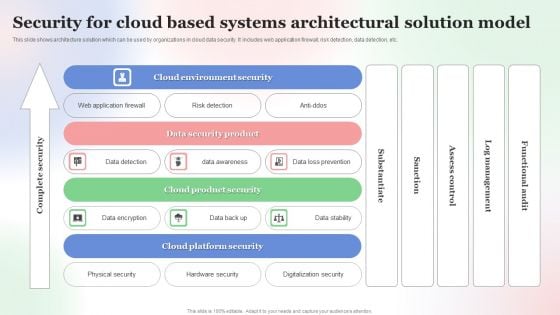
Security For Cloud Based Systems Architectural Solution Model Background PDF
This slide shows architecture solution which can be used by organizations in cloud data security. It includes web application firewall, risk detection, data detection, etc. Showcasing this set of slides titled Security For Cloud Based Systems Architectural Solution Model Background PDF. The topics addressed in these templates are Security For Cloud Based, Systems Architectural Solution Model. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cloud Computing Application Security Architecture Framework Elements PDF
The slide shows a framework describing security architecture to meet organizational unique requirements. It includes setting goals, determining process, constructing architecture and reviewing and revising security model. Showcasing this set of slides titled Cloud Computing Application Security Architecture Framework Elements PDF. The topics addressed in these templates are Set Goals, Determine Process, Construct Architecture. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
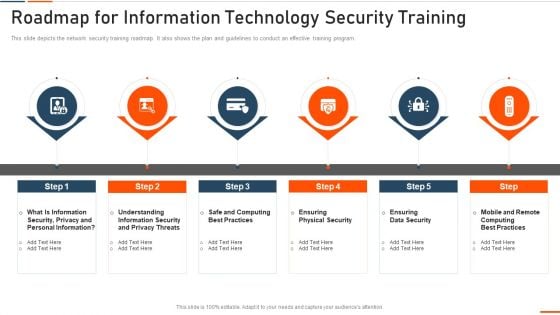
Roadmap For Information Technology Security Training Ppt Ideas Influencers PDF
This slide depicts the network security training roadmap. It also shows the plan and guidelines to conduct an effective training program. This is a roadmap for roadmap for information technology security training ppt ideas influencers pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like rmation security, computing best practices, physical security, data security . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
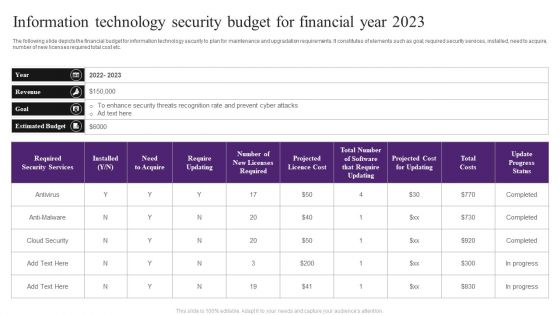
Information Technology Security Budget For Financial Year 2023 Slides PDF
The following slide depicts the financial budget for information technology security to plan for maintenance and upgradation requirements. It constitutes of elements such as goal, required security services, installed, need to acquire, number of new licenses required total cost etc. Showcasing this set of slides titled Information Technology Security Budget For Financial Year 2023 Slides PDF. The topics addressed in these templates are Enhance Security, Estimated Budget, Cloud Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

About Cryptography Overview Cloud Data Security Using Cryptography Designs Pdf
This slide talks about the concept of cryptography to secure the information sent to the recipient. The purpose of this slide is to represent the various principles of cryptography such as confidentiality, integrity, authentication, etc. Slidegeeks is here to make your presentations a breeze with About Cryptography Overview Cloud Data Security Using Cryptography Designs Pdf With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide talks about the concept of cryptography to secure the information sent to the recipient. The purpose of this slide is to represent the various principles of cryptography such as confidentiality, integrity, authentication, etc.

Suggested Coverage For Security Management Plan Graphics PDF
This slide provides information about the areas that are covered under the security management plan. This is a suggested coverage for security management plan graphics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like management, risk, security, information, system. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Private Security Service Provider Company Summary Report Clipart PDF
This slide provide information of firm providing security services to safeguards life of human beings who are facing threats. It includes elements such as about, category, services, company stats, packages, our service benefits. Pitch your topic with ease and precision using this Private Security Service Provider Company Summary Report Clipart PDF. This layout presents information on Provide World, Security Guard, Security Team. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
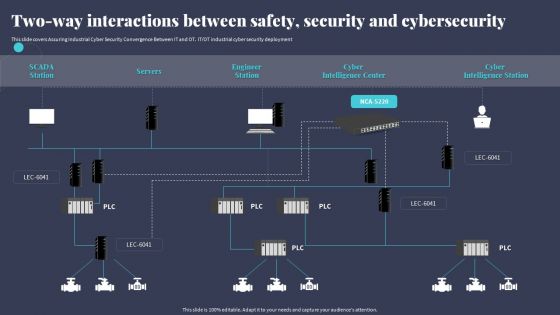
Two Way Interactions Between Safety Security And Cybersecurity Microsoft PDF
This slide covers Assuring Industrial Cyber Security Convergence Between IT and OT. ITOT industrial cyber security deployment. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Two Way Interactions Between Safety Security And Cybersecurity Microsoft PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Two Way Interactions Between Safety Security And Cybersecurity Microsoft PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.

Comparison Of Various Security Awareness Training Software Elements PDF
The purpose of this slide is to drawn comparison of multiple software which can be used to provide cyber security training to the key stakeholders. Information covered in this slide is related to phishing simulations, security reporting, individualized security training plan etc. Deliver and pitch your topic in the best possible manner with this Comparison Of Various Security Awareness Training Software Elements PDF. Use them to share invaluable insights on Individualized Security, Industry Specific, Deployment and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Estimated Security Management Plan Critical Success Factors Guidelines PDF
This is a estimated security management plan critical success factors guidelines pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security incidents level, intrusion attempts, security implementation. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
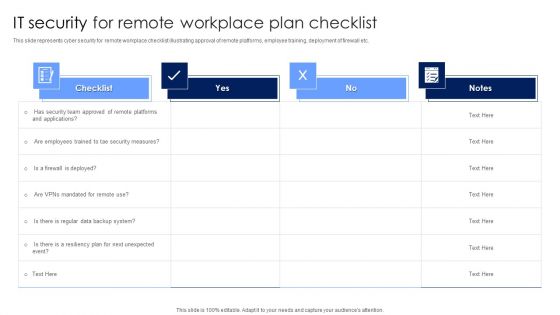
IT Security For Remote Workplace Plan Checklist Introduction PDF
This slide represents cyber security for remote workplace checklist illustrating approval of remote platforms, employee training, deployment of firewall etc. Pitch your topic with ease and precision using this IT Security For Remote Workplace Plan Checklist Introduction PDF. This layout presents information on Security Measures, Employees, Team. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Tokenization Working Process For Data Security PPT Powerpoint
This slide represents the workflow of tokenization. The purpose of this slide is to highlight the process of tokenization which includes downloading a mobile payment application, generating tokens, etc. Boost your pitch with our creative Tokenization Working Process For Data Security PPT Powerpoint. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide represents the workflow of tokenization. The purpose of this slide is to highlight the process of tokenization which includes downloading a mobile payment application, generating tokens, etc.
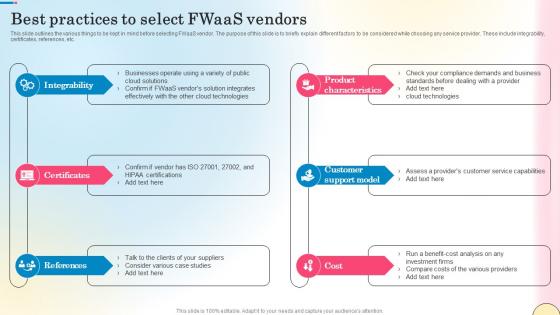
Best Practices To Select Fwaas Vendors Network Security Ideas Pdf
This slide outlines the various things to be kept in mind before selecting FWaaS vendor. The purpose of this slide is to briefly explain different factors to be considered while choosing any service provider. These include integrability, certificates, references, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Best Practices To Select Fwaas Vendors Network Security Ideas Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Best Practices To Select Fwaas Vendors Network Security Ideas Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide outlines the various things to be kept in mind before selecting FWaaS vendor. The purpose of this slide is to briefly explain different factors to be considered while choosing any service provider. These include integrability, certificates, references, etc.

Security Guide To Designing A Staff Handbook Information Pdf

Checklist To Implement Cloud Security In Business Microsoft PDF
This slide shows the checklist to implement cloud security in business, including policies and procedures, access control, networking, backup data, security patches, etc. Presenting Checklist To Implement Cloud Security In Business Microsoft PDF to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like Access Control, Networking, Security Patches And Updates. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
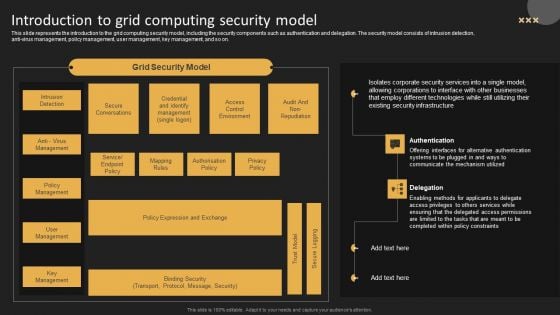
Introduction To Grid Computing Security Model Template PDF
This slide represents the introduction to the grid computing security model, including the security components such as authentication and delegation. The security model consists of intrusion detection, anti virus management, policy management, user management, key management, and so on. Get a simple yet stunning designed Introduction To Grid Computing Security Model Template PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Introduction To Grid Computing Security Model Template PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
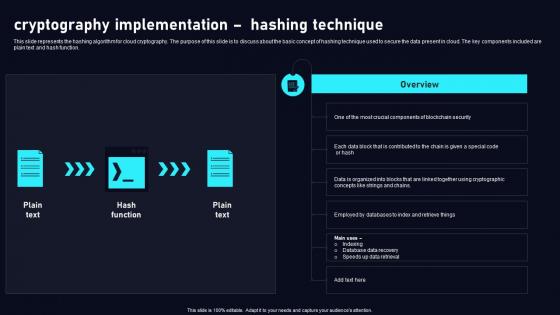
Cryptography Implementation Hashing Cloud Data Security Using Cryptography Pictures Pdf
This slide represents the hashing algorithm for cloud cryptography. The purpose of this slide is to discuss about the basic concept of hashing technique used to secure the data present in cloud. The key components included are plain text and hash function. Are you searching for a Cryptography Implementation Hashing Cloud Data Security Using Cryptography Pictures Pdf that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Cryptography Implementation Hashing Cloud Data Security Using Cryptography Pictures Pdf from Slidegeeks today. This slide represents the hashing algorithm for cloud cryptography. The purpose of this slide is to discuss about the basic concept of hashing technique used to secure the data present in cloud. The key components included are plain text and hash function.
IT Security Plan Icon Depicting Biometric Identification Topics PDF
Showcasing this set of slides titled IT Security Plan Icon Depicting Biometric Identification Topics PDF. The topics addressed in these templates are IT Security Plan Icon, Depicting Biometric Identification. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
IT Security Plan Icon Showcasing Electronic Alert Ideas PDF
Pitch your topic with ease and precision using this IT Security Plan Icon Showcasing Electronic Alert Ideas PDF. This layout presents information on IT Security Plan Icon, Showcasing Electronic Alert. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Cloud Cryptography Implementation Data Security In Cloud Computing Ppt Template
This slide represents the hashing algorithm for cloud cryptography. The purpose of this slide is to discuss about the basic concept of hashing technique used to secure the data present in cloud. The key components included are plain text and hash function. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Cloud Cryptography Implementation Data Security In Cloud Computing Ppt Template and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide represents the hashing algorithm for cloud cryptography. The purpose of this slide is to discuss about the basic concept of hashing technique used to secure the data present in cloud. The key components included are plain text and hash function.

Private Plans Security PowerPoint Templates And PowerPoint Backgrounds 0211
Microsoft PowerPoint Template and Background with gold key inserted into a set of unrolled blueprints Expound your logic on our Private Plans Security PowerPoint Templates And PowerPoint Backgrounds 0211. Let them in on your chain of thought.
Plant Safety Measures Icon With Security Sign Background PDF
Pitch your topic with ease and precision using this Plant Safety Measures Icon With Security Sign Background PDF. This layout presents information on Plant Safety Measures Icon, Security Sign. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
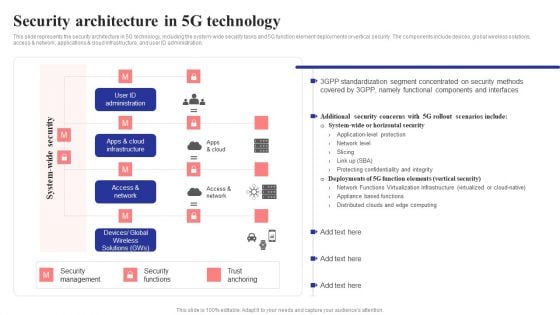
Security Architecture In 5G Technology 5G Network Structure Background PDF
This slide represents the security architecture in 5G technology, including the system-wide security tasks and 5G function element deployments or vertical security. The components include devices, global wireless solutions, access network, applications cloud infrastructure, and user ID administration.Are you searching for a Security Architecture In 5G Technology 5G Network Structure Background PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Security Architecture In 5G Technology 5G Network Structure Background PDF from Slidegeeks today.
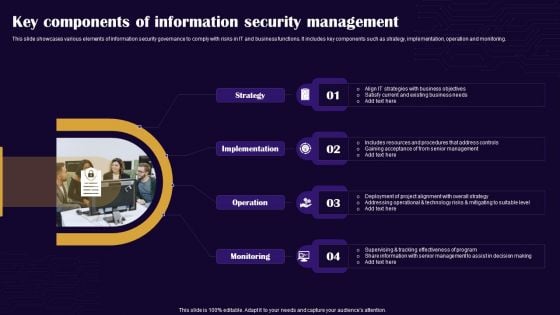
Key Components Of Information Security Management Graphics PDF
This slide showcases various elements of information security governance to comply with risks in IT and business functions. It includes key components such as strategy, implementation, operation and monitoring. Persuade your audience using this Key Components Of Information Security Management Graphics PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Strategy, Implementation, Operation. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
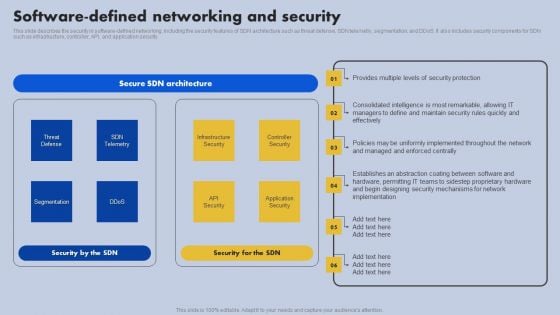
Software Defined Networking And Security Ppt Styles Slides PDF
This slide describes the security in software-defined networking, including the security features of SDN architecture such as threat defense, SDN telemetry, segmentation, and ddos. It also includes security components for SDN such as infrastructure, controller, API, and application security. Slidegeeks is here to make your presentations a breeze with Software Defined Networking And Security Ppt Styles Slides PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
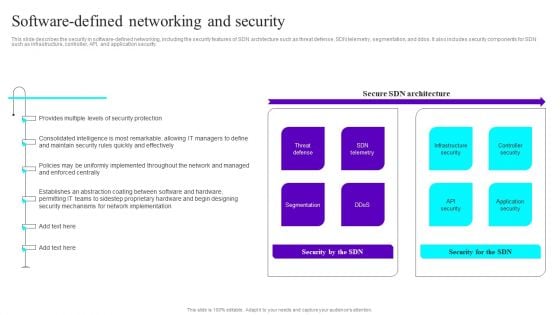
Software Defined Networking And Security Ppt Slides File Formats PDF
This slide describes the security in software-defined networking, including the security features of SDN architecture such as threat defense, SDN telemetry, segmentation, and ddos. It also includes security components for SDN such as infrastructure, controller, API, and application security. Slidegeeks is here to make your presentations a breeze with Software Defined Networking And Security Ppt Slides File Formats PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
Data Warehouse Security Mechanism And Procedure Icon Demonstration PDF
Showcasing this set of slides titled Data Warehouse Security Mechanism And Procedure Icon Demonstration PDF. The topics addressed in these templates are Data Warehouse, Security Mechanism, Procedure Icon. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Cyber Security Certification Career Roadmap Icon Pictures PDF
Showcasing this set of slides titled Cyber Security Certification Career Roadmap Icon Pictures PDF. The topics addressed in these templates are Career Roadmap Icon, Cyber Security Certification. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Risk Security Impact Mitigation Icon With Shield Themes PDF
Pitch your topic with ease and precision using this Risk Security Impact Mitigation Icon With Shield Themes PDF. This layout presents information on Icon With Shield, Risk Security Impact Mitigation. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Cyber Security Compliance Traceability Matrix Icon Formats PDF
Showcasing this set of slides titled Cyber Security Compliance Traceability Matrix Icon Formats PDF. The topics addressed in these templates are Cyber Security, Compliance, Traceability Matrix. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Big Data Security Analytics Icon With Shield Symbol Background PDF
Pitch your topic with ease and precision using this Big Data Security Analytics Icon With Shield Symbol Background PDF. This layout presents information on Big Data Security Analytics, Icon With Shield Symbol. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.


 Continue with Email
Continue with Email

 Home
Home


































