Security Strategy
Information Security Risk Evaluation Probability Assessment Matrix For Risk Management Demonstration PDF
This slide showcase matrix that can help organization to identify the probability of different information security attacks and formulate mitigation strategy in advance. It can help organization to manage the major risks and safeguard the information.Deliver and pitch your topic in the best possible manner with this Information Security Risk Evaluation Probability Assessment Matrix For Risk Management Demonstration PDF. Use them to share invaluable insights on Accidental Intentional, Unauthorized, Critical Information and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Table Of Contents Critical Measures For Ensuring Business Security Formats PDF
Make sure to capture your audiences attention in your business displays with our gratis customizable Table Of Contents Critical Measures For Ensuring Business Security Formats PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Plan Steps In Professional PDF
This slide provides information about the first and the foremost step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Establishing a Security Monitoring Strategy and Supporting Policies. Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring plan steps in professional pdf bundle. Topics like cybersecurity monitoring plan steps in detail establish a security monitoring strategy and supporting policies can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Addressing Challenges In IoT Based Satellite Security IoT In Orbit Unleashing The Power IoT SS V
This slide highlights mitigation strategies to address satellite network security challenges to ensure data integrity and safeguarding communication. It includes challenges such as satellite network jamming, device damage, and unauthorized access. Find a pre-designed and impeccable Addressing Challenges In IoT Based Satellite Security IoT In Orbit Unleashing The Power IoT SS V. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide highlights mitigation strategies to address satellite network security challenges to ensure data integrity and safeguarding communication. It includes challenges such as satellite network jamming, device damage, and unauthorized access.

Introduction Of Utility Token In Data Security Securing Your Data Ppt Presentation
This slide showcases the overview of utility tokens in data security. The purpose of this slide is to discuss the introduction of utility tokens required for data security and preventing thefts. Explore a selection of the finest Introduction Of Utility Token In Data Security Securing Your Data Ppt Presentation here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Introduction Of Utility Token In Data Security Securing Your Data Ppt Presentation to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide showcases the overview of utility tokens in data security. The purpose of this slide is to discuss the introduction of utility tokens required for data security and preventing thefts.
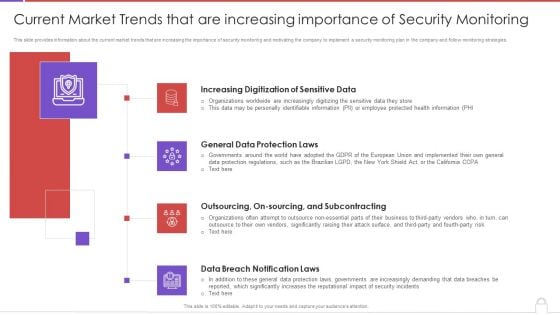
Methods To Develop Current Market Trends That Are Increasing Importance Of Security Portrait PDF
This slide provides information about the current market trends that are increasing the importance of security monitoring and motivating the company to implement a security monitoring plan in the company and follow monitoring strategies. This is a methods to develop current market trends that are increasing importance of security portrait pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like increasing digitization sensitive data, general data protection laws, outsourcing, on sourcing, and subcontracting, data breach notification laws. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Comparison Between Secure Web Gateway And Cloud Security Gateways Web Threat Protection System
This slide demonstrates the concept of cloud security gateways and Secure Web Gateways. The purpose of this slide is to compare cloud security gateways and SWGs on the basis of various factors such as scope, deployment, architecture, features and cost. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Comparison Between Secure Web Gateway And Cloud Security Gateways Web Threat Protection System will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide demonstrates the concept of cloud security gateways and Secure Web Gateways. The purpose of this slide is to compare cloud security gateways and SWGs on the basis of various factors such as scope, deployment, architecture, features and cost.

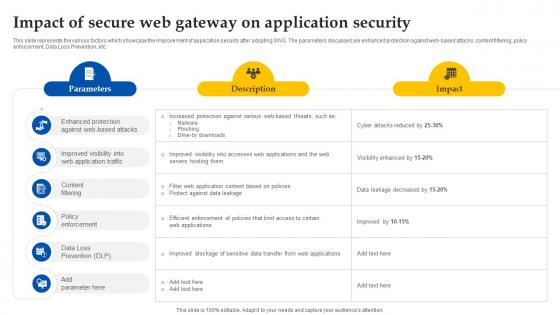
Impact Of Secure Web Gateway On Application Security Web Threat Protection System
This slide represents the various factors which showcase the improvement of application security after adopting SWG. The parameters discussed are enhanced protection against web-based attacks, content filtering, policy enforcement, Data Loss Prevention, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Impact Of Secure Web Gateway On Application Security Web Threat Protection System template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Impact Of Secure Web Gateway On Application Security Web Threat Protection System that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide represents the various factors which showcase the improvement of application security after adopting SWG. The parameters discussed are enhanced protection against web-based attacks, content filtering, policy enforcement, Data Loss Prevention, etc.
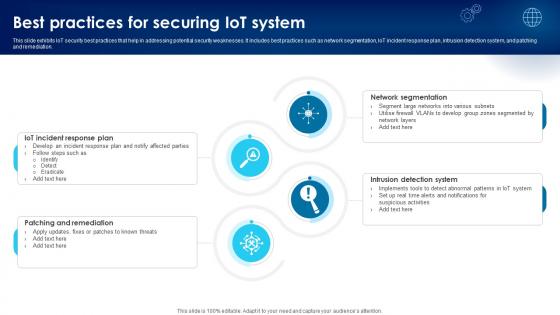
Building Trust With IoT Security Best Practices For Securing IoT System IoT SS V
This slide exhibits IoT security best practices that help in addressing potential security weaknesses. It includes best practices such as network segmentation, IoT incident response plan, intrusion detection system, and patching and remediation. Want to ace your presentation in front of a live audience Our Building Trust With IoT Security Best Practices For Securing IoT System IoT SS V can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide exhibits IoT security best practices that help in addressing potential security weaknesses. It includes best practices such as network segmentation, IoT incident response plan, intrusion detection system, and patching and remediation.

Best Practices For Tokenization In Data Security Securing Your Data Ppt Example
The purpose of this slide is to highlight the best approaches for tokenization. The practices include broadening data tokenization scope, regularly revise policies, effective cyber security, etc. There are so many reasons you need a Best Practices For Tokenization In Data Security Securing Your Data Ppt Example The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. The purpose of this slide is to highlight the best approaches for tokenization. The practices include broadening data tokenization scope, regularly revise policies, effective cyber security, etc.
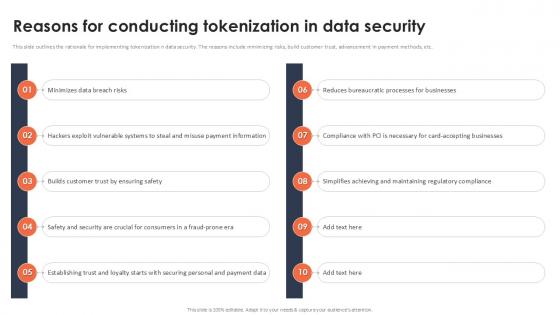
Reasons For Conducting Tokenization In Data Security Securing Your Data Ppt Presentation
This slide outlines the rationale for implementing tokenization n data security. The reasons include minimizing risks, build customer trust, advancement in payment methods, etc. Do you know about Slidesgeeks Reasons For Conducting Tokenization In Data Security Securing Your Data Ppt Presentation These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide outlines the rationale for implementing tokenization n data security. The reasons include minimizing risks, build customer trust, advancement in payment methods, etc.
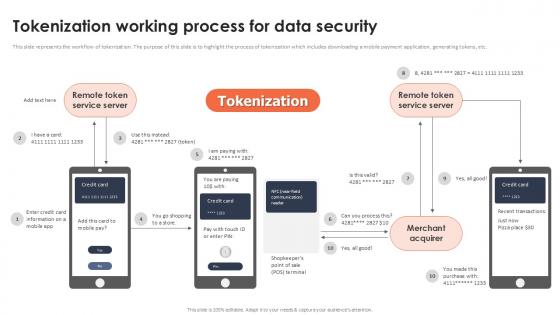
Tokenization Working Process For Data Security Securing Your Data Ppt Presentation
This slide represents the workflow of tokenization. The purpose of this slide is to highlight the process of tokenization which includes downloading a mobile payment application, generating tokens, etc. Find highly impressive Tokenization Working Process For Data Security Securing Your Data Ppt Presentation on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Tokenization Working Process For Data Security Securing Your Data Ppt Presentation for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide represents the workflow of tokenization. The purpose of this slide is to highlight the process of tokenization which includes downloading a mobile payment application, generating tokens, etc.
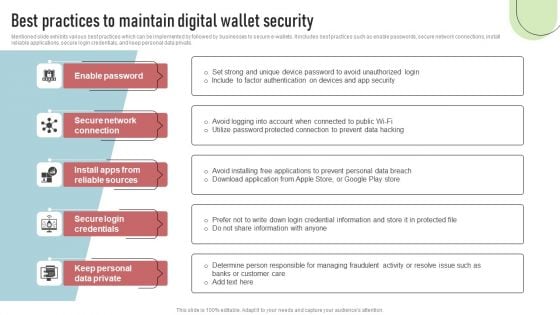
Cashless Payment Strategies To Enhance Business Performance Best Practices To Maintain Digital Wallet Security Brochure PDF
Mentioned slide exhibits various best practices which can be implemented by followed by businesses to secure e-wallets. It includes best practices such as enable passwords, secure network connections, install reliable applications, secure login credentials, and keep personal data private. Retrieve professionally designed Cashless Payment Strategies To Enhance Business Performance Best Practices To Maintain Digital Wallet Security Brochure PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
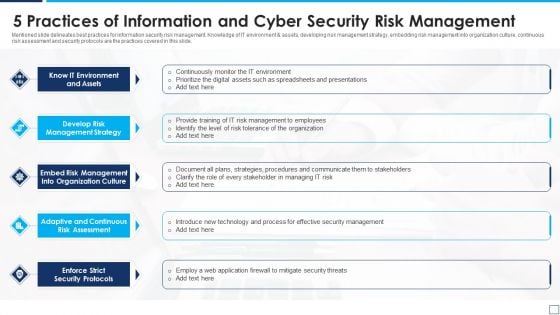
5 Practices Of Information And Cyber Security Risk Management Graphics PDF
Mentioned slide delineates best practices for information security risk management. Knowledge of IT environment and assets, developing risk management strategy, embedding risk management into organization culture, continuous risk assessment and security protocols are the practices covered in this slide. Presenting 5 practices of information and cyber security risk management graphics pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including know it environment and assets, develop risk management strategy, enforce strict security protocols. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
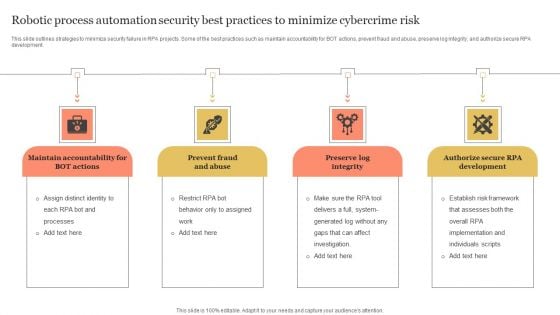
Robotic Process Automation Security Best Practices To Minimize Cybercrime Risk Themes PDF
This slide outlines strategies to minimize security failure in RPA projects. Some of the best practices such as maintain accountability for BOT actions, prevent fraud and abuse, preserve log integrity, and authorize secure RPA development. Presenting Robotic Process Automation Security Best Practices To Minimize Cybercrime Risk Themes PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Maintain Accountability, Prevent Fraud And Abuse, Preserve Log Integrity. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Tokenization In Payment Card Industry For Data Security Securing Your Data Ppt Example
This slide outlines the introduction of tokenization in payment card industry. The purpose of this slide is to showcase the process of tokenization in payment card industry to secure non sharable details of client. Slidegeeks is here to make your presentations a breeze with Tokenization In Payment Card Industry For Data Security Securing Your Data Ppt Example With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide outlines the introduction of tokenization in payment card industry. The purpose of this slide is to showcase the process of tokenization in payment card industry to secure non sharable details of client.

CASB 2 0 IT Cloud Access Security Broker And Secure Web Gateway
This slide represents how CASB 2.0 not just discovers the shadow IT but helps to control it too. The purpose of this slide is to showcase how CASB 2.0 improves the SWG model by empowering it with rich cloud app data, getting dynamic control of shadow IT and simplifying deployment. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our CASB 2 0 IT Cloud Access Security Broker And Secure Web Gateway was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into CASB 2 0 IT Cloud Access Security Broker And Secure Web Gateway. This slide represents how CASB 2.0 not just discovers the shadow IT but helps to control it too. The purpose of this slide is to showcase how CASB 2.0 improves the SWG model by empowering it with rich cloud app data, getting dynamic control of shadow IT and simplifying deployment.
Web Access Control Solution Impact Of Secure Web Gateway On Application Security
This slide represents the various factors which showcase the improvement of application security after adopting SWG. The parameters discussed are enhanced protection against web-based attacks, content filtering, policy enforcement, Data Loss Prevention, etc. Welcome to our selection of the Web Access Control Solution Impact Of Secure Web Gateway On Application Security. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide represents the various factors which showcase the improvement of application security after adopting SWG. The parameters discussed are enhanced protection against web-based attacks, content filtering, policy enforcement, Data Loss Prevention, etc.

Data Security Benefits Of Adopting Tokenization Securing Your Data Ppt Presentation
This slide discusses the cons of tokenization. The purpose of this slide is to showcase the advantages of tokenization such as utilizing less resources, decreases risk, stimulates innovation, etc. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Data Security Benefits Of Adopting Tokenization Securing Your Data Ppt Presentation and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide discusses the cons of tokenization. The purpose of this slide is to showcase the advantages of tokenization such as utilizing less resources, decreases risk, stimulates innovation, etc.
Icons Slide For Secure Access Service Edge Cloud Security Model Ppt Gallery Layout PDF
Help your business to create an attention-grabbing presentation using our Icons Slide For Secure Access Service Edge Cloud Security Model Ppt Gallery Layout PDF set of slides. The slide contains innovative icons that can be flexibly edited. Choose this Icons Slide For Secure Access Service Edge Cloud Security Model Ppt Gallery Layout PDF template to create a satisfactory experience for your customers. Go ahead and click the download button.
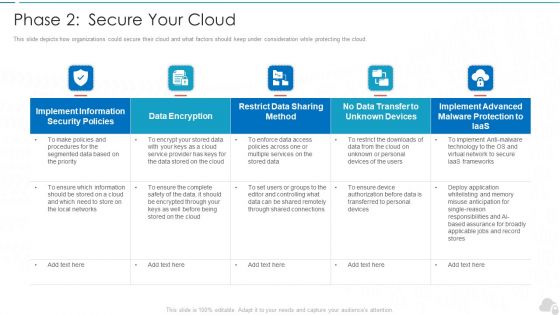
Phase 2 Secure Your Cloud Cloud Computing Security IT Ppt Slides Skills PDF
This slide depicts how organizations could secure their cloud and what factors should keep under consideration while protecting the cloud. Deliver an awe inspiring pitch with this creative phase 2 secure your cloud cloud computing security it ppt slides skills pdf bundle. Topics like implement, security policies, data encryption, services, frameworks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
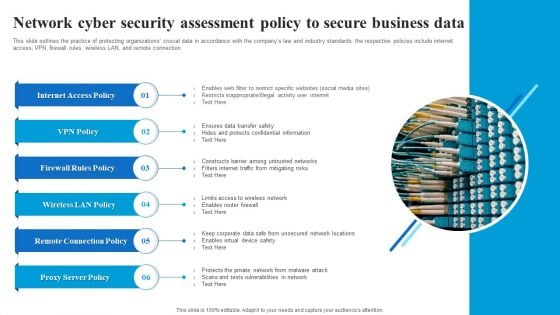
Network Cyber Security Assessment Policy To Secure Business Data Microsoft PDF
This slide outlines the practice of protecting organizations crucial data in accordance with the companys law and industry standards. the respective policies include internet access, VPN, firewall rules, wireless LAN, and remote connection. Showcasing this set of slides titled Network Cyber Security Assessment Policy To Secure Business Data Microsoft PDF. The topics addressed in these templates are Internet Access Policy, Firewall Rules Policy, Wireless LAN Policy, Remote Connection Policy. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Table Of Contents For Secure Access Service Edge Cloud Security Model Ppt Professional Backgrounds PDF
Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Table Of Contents For Secure Access Service Edge Cloud Security Model Ppt Professional Backgrounds PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Table Of Contents For Secure Access Service Edge Cloud Security Model Ppt Professional Backgrounds PDF today and make your presentation stand out from the rest.
Secure Access Service Edge Cloud Security Model Table Of Contents Ppt Layouts Format Ideas PDF
Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Secure Access Service Edge Cloud Security Model Table Of Contents Ppt Layouts Format Ideas PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Secure Access Service Edge Cloud Security Model Table Of Contents Ppt Layouts Format Ideas PDF.
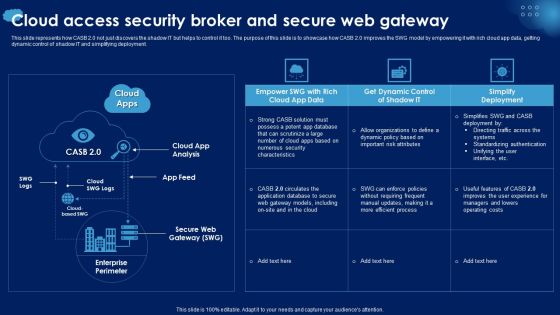
Cloud Access Security Broker And Secure Web Gateway Ppt PowerPoint Presentation Diagram Images PDF
This slide represents how CASB 2.0 not just discovers the shadow IT but helps to control it too. The purpose of this slide is to showcase how CASB 2.0 improves the SWG model by empowering it with rich cloud app data, getting dynamic control of shadow IT and simplifying deployment. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Cloud Access Security Broker And Secure Web Gateway Ppt PowerPoint Presentation Diagram Images PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Cloud Access Security Broker And Secure Web Gateway Ppt PowerPoint Presentation Diagram Images PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.
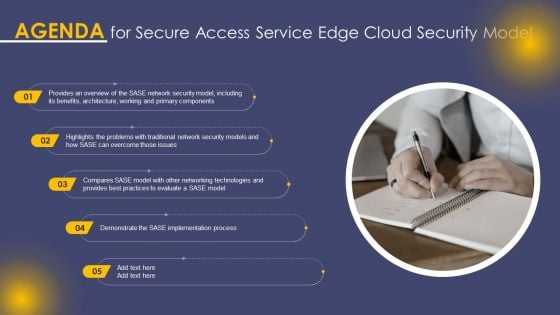
Agenda For Secure Access Service Edge Cloud Security Model Ppt Outline Maker PDF
Find a pre designed and impeccable Agenda For Secure Access Service Edge Cloud Security Model Ppt Outline Maker PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
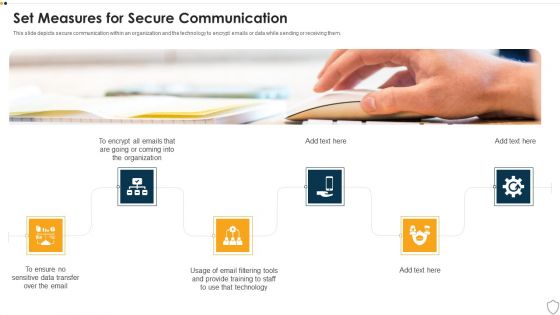
IT Security Set Measures For Secure Communication Ppt Infographic Template Background Designs PDF
This slide depicts secure communication within an organization and the technology to encrypt emails or data while sending or receiving them. This is a it security set measures for secure communication ppt infographic template background designs pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like technology, training, organization, data transfer. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
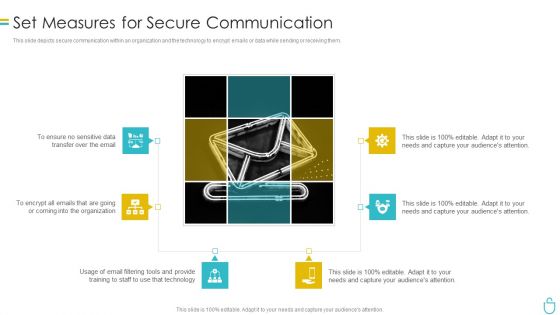
Information Security Set Measures For Secure Communication Ppt Outline Slide Download PDF
This slide depicts secure communication within an organization and the technology to encrypt emails or data while sending or receiving them. This is a information security set measures for secure communication ppt outline slide download pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like organization, technology. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Secure Access Service Edge Cloud Security Model ZTNA 10 Vs ZTNA 20 Ppt Gallery Designs PDF
This slide represents the comparison between zero trust network access versions 1.0 and 2.0. The purpose of this slide is to demonstrate the overview of both versions, including differences. It also includes the architecture of both versions of zero-trust network access. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Secure Access Service Edge Cloud Security Model ZTNA 10 Vs ZTNA 20 Ppt Gallery Designs PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
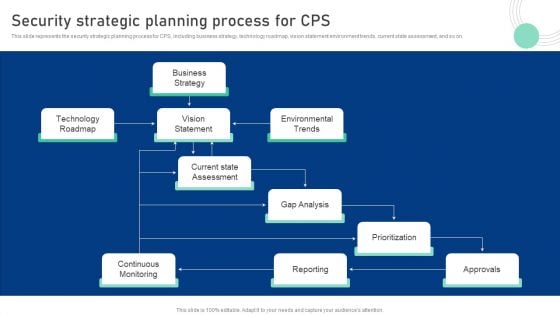
Cyber Physical System To Enhance Security Strategic Planning Process For Cps Demonstration PDF
This slide represents the security strategic planning process for CPS, including business strategy, technology roadmap, vision statement environment trends, current state assessment, and so on. Slidegeeks is here to make your presentations a breeze with Cyber Physical System To Enhance Security Strategic Planning Process For Cps Demonstration PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, youre sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether youre giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
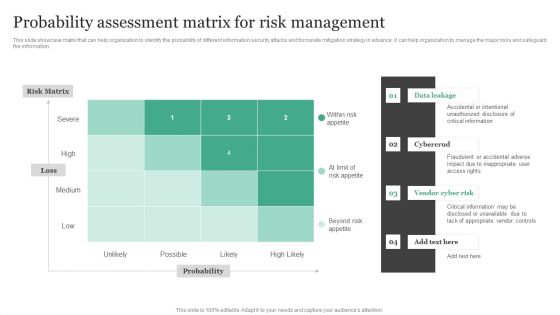
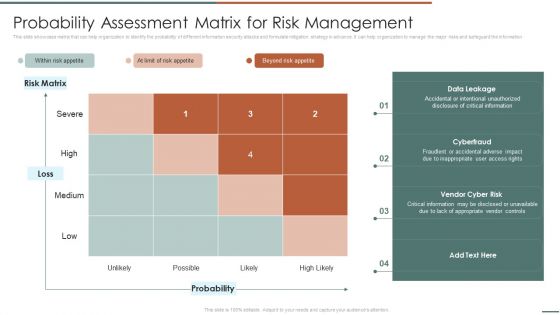
Probability Assessment Matrix For Risk Management Information Security Risk Administration Pictures PDF
This slide showcase matrix that can help organization to identify the probability of different information security attacks and formulate mitigation strategy in advance. It can help organization to manage the major risks and safeguard the information.This Probability Assessment Matrix For Risk Management Information Security Risk Administration Pictures PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
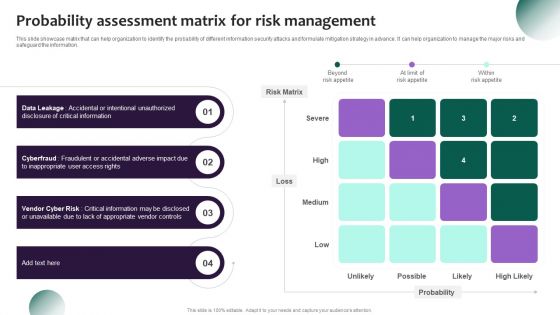
Information Systems Security And Risk Management Plan Probability Assessment Matrix For Risk Management Portrait PDF
This slide showcase matrix that can help organization to identify the probability of different information security attacks and formulate mitigation strategy in advance. It can help organization to manage the major risks and safeguard the information. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Information Systems Security And Risk Management Plan Probability Assessment Matrix For Risk Management Portrait PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
Integrating Data Privacy System Data Privacy Vs Data Security Ppt Icon Guidelines PDF
This slide compares data privacy with data security, indicating that security is concerned with safeguarding data, and privacy is about responsible data usage. Make sure to capture your audiences attention in your business displays with our gratis customizable Integrating Data Privacy System Data Privacy Vs Data Security Ppt Icon Guidelines PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
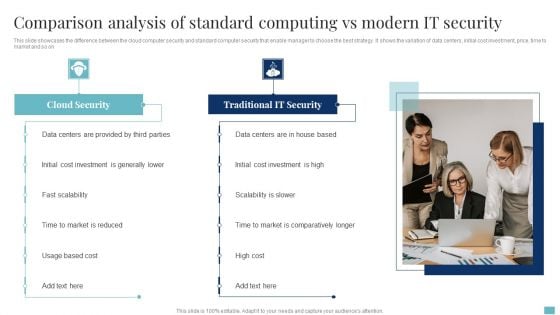
Comparison Analysis Of Standard Computing Vs Modern It Security Clipart PDF
This slide showcases the difference between the cloud computer security and standard computer security that enable manager to choose the best strategy. It shows the variation of data centers, initial cost investment, price, time to market and so on. Persuade your audience using this Comparison Analysis Of Standard Computing Vs Modern It Security Clipart PDF. This PPT design covers two stages, thus making it a great tool to use. It also caters to a variety of topics including Data Centers, Cloud Security, Cost Investment. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Comparative Analysis Of Cloud And Traditional Computing It Security Diagrams PDF
This slide provide the difference between the cloud computer security and standard computer security that enable manager to choose the best strategy. It shows the variation of data centers, initial cost investment, price, time to market etc.Persuade your audience using this Comparative Analysis Of Cloud And Traditional Computing It Security Diagrams PDF. This PPT design covers one stage, thus making it a great tool to use. It also caters to a variety of topics including Provided Parties, Initial Cost Investment, Comparatively Longer. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
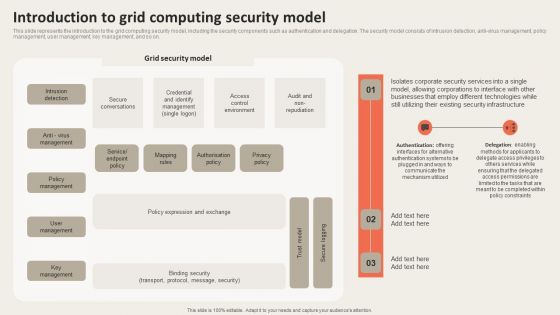
Grid Computing Applications Introduction To Grid Computing Security Model Rules PDF
This slide represents the introduction to the grid computing security model, including the security components such as authentication and delegation. The security model consists of intrusion detection, anti-virus management, policy management, user management, key management, and so on. Make sure to capture your audiences attention in your business displays with our gratis customizable Grid Computing Applications Introduction To Grid Computing Security Model Rules PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
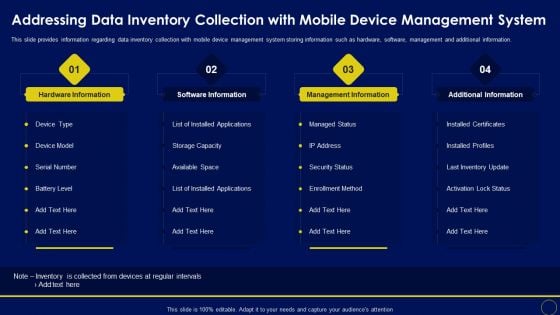
Addressing Data Inventory Collection With Mobile Business Mobile Device Security Management Structure PDF
This slide provides information regarding data inventory collection with mobile device management system storing information such as hardware, software, management and additional information. Make sure to capture your audiences attention in your business displays with our gratis customizable Addressing Data Inventory Collection With Mobile Business Mobile Device Security Management Structure PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
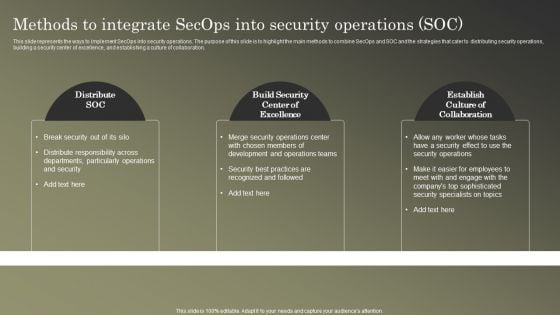
Cybersecurity Operations Cybersecops Methods To Integrate Secops Into Security Rules PDF
This slide represents the ways to implement SecOps into security operations. The purpose of this slide is to highlight the main methods to combine SecOps and SOC and the strategies that cater to distributing security operations, building a security center of excellence, and establishing a culture of collaboration. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Cybersecurity Operations Cybersecops Methods To Integrate Secops Into Security Rules PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Cybersecurity Operations Cybersecops Methods To Integrate Secops Into Security Rules PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
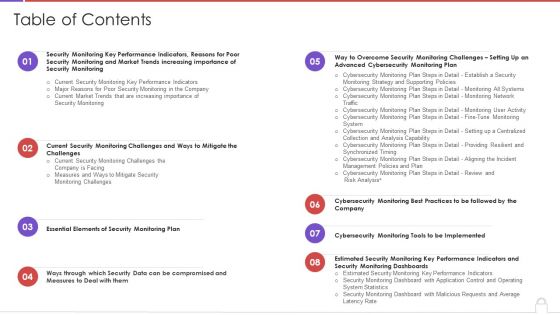
Table Of Contents Methods To Develop Advanced It Security Monitoring Plan Structure PDF
Deliver and pitch your topic in the best possible manner with this table of contents methods to develop advanced it security monitoring plan structure pdf. Use them to share invaluable insights on security monitoring, key performance indicators, security monitoring plan and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Security Management Plan Steps In Detail Evaluating Information Processing Assets Graphics PDF
This slide provides information about the second step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. Evaluating Information Processing Assets. Deliver and pitch your topic in the best possible manner with this security management plan steps in detail evaluating information processing assets graphics pdf. Use them to share invaluable insights on security management plan steps in detail evaluating information processing assets and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Security Management Plan Steps In Detail Remote Access Control Mockup PDF
This slide provides information about the sixth step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. Remote Access Control. Deliver an awe inspiring pitch with this creative security management plan steps in detail remote access control mockup pdf bundle. Topics like security management plan steps in detail remote access control can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Management Plan Steps In Detail Risk Assessment And Analysis Summary PDF
This slide provides information about the third step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. Risk Assessment and Analysis. Deliver and pitch your topic in the best possible manner with this security management plan steps in detail risk assessment and analysis summary pdf. Use them to share invaluable insights on security management plan steps in detail risk assessment and analysis and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Information Technology Policy And Processes Information Security Policy For Employees Structure PDF
This slide depicts the information security policy that critical topics covered in this policy. It also covers the reasons for frequent changes in the policy. Make sure to capture your audiences attention in your business displays with our gratis customizable Information Technology Policy And Processes Information Security Policy For Employees Structure PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
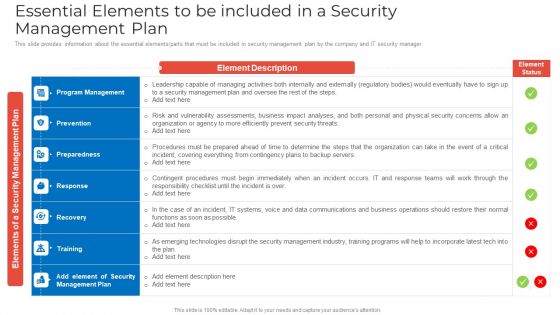
Essential Elements To Be Included In A Security Management Plan Rules PDF
This slide provides information about the essential elements parts that must be included in security management plan by the company and IT security manager. Deliver an awe inspiring pitch with this creative essential elements to be included in a security management plan rules pdf bundle. Topics like program management, prevention, preparedness can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Smart Home Security Solutions Company Profile Company Overview With Key Services Brochure PDF
This slide highlights security company background information which includes the company services offered, area served, total employees, headquarter, website and company value added services. Deliver an awe inspiring pitch with this creative Smart Home Security Solutions Company Profile Company Overview With Key Services Brochure PDF bundle. Topics like Affordable Home Security, Home Automation Alarm, Monitory Services Solutions can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
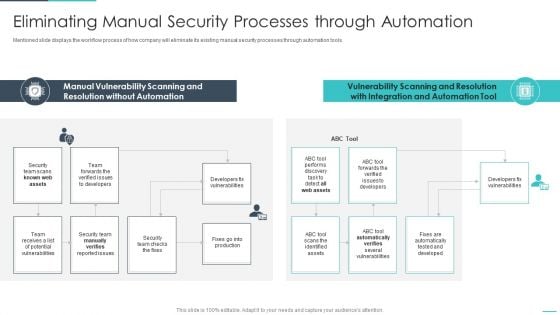
Handling Cyber Threats Digital Era Eliminating Manual Security Processes Ppt Show Influencers PDF
Mentioned slide displays the workflow process of how company will eliminate its existing manual security processes through automation tools. Deliver and pitch your topic in the best possible manner with this handling cyber threats digital era eliminating manual security processes ppt show influencers pdf. Use them to share invaluable insights on eliminating manual security processes through automation and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
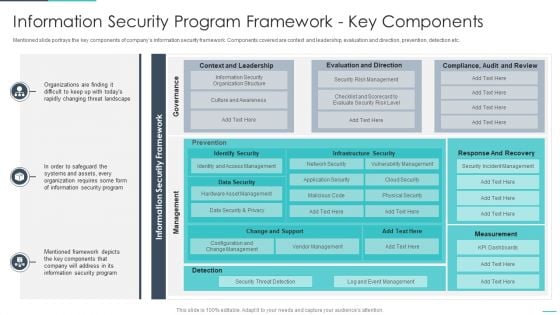
Handling Cyber Threats Digital Era Information Security Program Framework Ppt Model Summary PDF
Mentioned slide portrays the key components of companys information security framework. Components covered are context and leadership, evaluation and direction, prevention, detection etc. Deliver and pitch your topic in the best possible manner with this handling cyber threats digital era information security program framework ppt model summary pdf. Use them to share invaluable insights on information security program framework key components and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Security Management Plan Steps In Detail Adopting Access Controls Download PDF
This slide provides information about the fifth step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. Adopting Access Controls. Deliver an awe inspiring pitch with this creative security management plan steps in detail adopting access controls download pdf bundle. Topics like logical access controls, control implementation costs, physical access controls can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Data Safety Initiatives Key Security Controls To Be Addressed In The Program Summary PDF
Purpose of this slide is to provide information about key security controls that are to be addressed in companys information security program. Security controls covered are user application hardening, daily backups and patch applications. Deliver an awe inspiring pitch with this creative data safety initiatives key security controls to be addressed in the program summary pdf bundle. Topics like prevents attacks, limits extent of attacks, data recovery can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Internet Security Threat Analysis Plan With Key Trends Ppt PowerPoint Presentation Summary Mockup PDF
Showcasing this set of slides titled internet security threat analysis plan with key trends ppt powerpoint presentation summary mockup pdf. The topics addressed in these templates are internet security threat analysis plan with key trends. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Saas Cloud Security Action Plan Icon Ppt PowerPoint Presentation File Templates PDF
Showcasing this set of slides titled Saas Cloud Security Action Plan Icon Ppt PowerPoint Presentation File Templates PDF. The topics addressed in these templates are Saas Cloud Security, Action Plan, Icon. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Table Of Contents Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Information PDF
Deliver and pitch your topic in the best possible manner with this table of contents modern security observation plan to eradicate cybersecurity risk and data breach information pdf. Use them to share invaluable insights on essential elements of security, compromised and measures, performance indicators and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Cybersecurity Risk Scorecard Information Security Companies Risk Coverage Scorecard Icons PDF
Deliver an awe inspiring pitch with this creative cybersecurity risk scorecard information security companies risk coverage scorecard icons pdf bundle. Topics like hacker protection, network security, cubit score can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Icons Slide Safeguarding Network With SDN Security Ppt File Summary PDF
Help your business to create an attention-grabbing presentation using our Icons Slide Safeguarding Network With SDN Security Ppt File Summary PDF set of slides. The slide contains innovative icons that can be flexibly edited. Choose this Icons Slide Safeguarding Network With SDN Security Ppt File Summary PDF template to create a satisfactory experience for your customers. Go ahead and click the download button.
Security Of Business Website Vector Icon Ppt PowerPoint Presentation Pictures Infographics PDF
Showcasing this set of slides titled security of business website vector icon ppt powerpoint presentation pictures infographics pdf. The topics addressed in these templates are security of business website vector icon. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Security Measures To Prevent Accident At Workplace Ppt PowerPoint Presentation Pictures Display PDF
Showcasing this set of slides titled security measures to prevent accident at workplace ppt powerpoint presentation pictures display pdf. The topics addressed in these templates are security measures to prevent accident at workplace. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
App Design Model Icon For Security Optimization Ppt PowerPoint Presentation Inspiration PDF
Showcasing this set of slides titled app design model icon for security optimization ppt powerpoint presentation inspiration pdf. The topics addressed in these templates are app design model icon for security optimization. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Virus Cyber Security Attack Warning On Web Browser Icon Ppt Example 2015 PDF
Pitch your topic with ease and precision using this Virus Cyber Security Attack Warning On Web Browser Icon Ppt Example 2015 PDF. This layout presents information on Virus Cyber Security, Attack Warning, Web Browser Icon. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Security And Human Resource Services Business Profile Commercial And Residential Microsoft PDF
This slide highlights the commercial and residential building security offered by security company which includes visitor management, vehicle and parking management, CCTV operating and monitoring. Want to ace your presentation in front of a live audience Our Security And Human Resource Services Business Profile Commercial And Residential Microsoft PDF can help you do that by engaging all the users towards you.. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.

Risk Based Procedures To IT Security Gap Identification Current Approach Process Flaws And Cost Elements PDF
Purpose of this slide is to highlight the existing approach and process flaws along with the cost incur details. It also shows that company is treating security and privacy as after thoughts. Deliver an awe inspiring pitch with this creative Risk Based Procedures To IT Security Gap Identification Current Approach Process Flaws And Cost Elements PDF bundle. Topics like Cyberrisk Management, Security Organization, Technology Controls can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.


 Continue with Email
Continue with Email

 Home
Home


































