Security Strategy
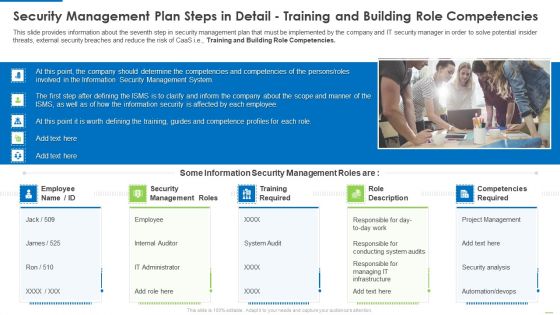
Security Management Plan Steps In Detail Training And Building Role Competencies Topics PDF
This slide provides information about the seventh step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Training and Building Role Competencies. Presenting security management plan steps in detail training and building role competencies topics pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like security management roles, training required, role description. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security Management Plan Steps In Detail Training And Building Role Competencies Portrait PDF
This slide provides information about the seventh step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Training and Building Role Competencies. This is a security management plan steps in detail training and building role competencies portrait pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like management system, information security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
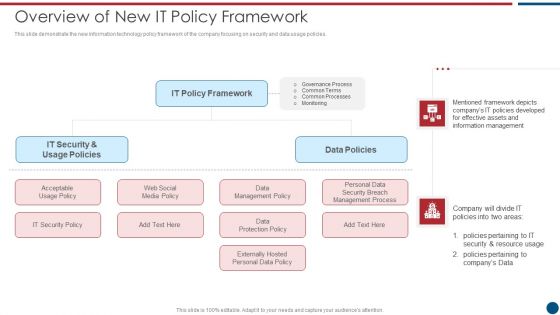
Risk Based Procedures To IT Security Overview Of New IT Policy Framework Guidelines PDF
This slide demonstrate the new information technology policy framework of the company focusing on security and data usage policies. Presenting Risk Based Procedures To IT Security Overview Of New IT Policy Framework Guidelines PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like IT Policy, Data Policies, IT Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
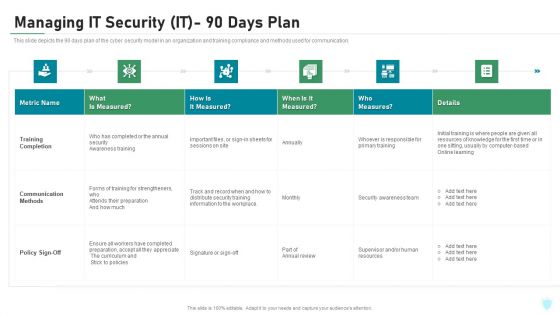
Managing IT Security IT 90 Days Plan Ppt Layouts Picture PDF
This slide depicts the 90 days plan of the cyber security model in an organization and training compliance and methods used for communication. Deliver and pitch your topic in the best possible manner with this managing it security it 90 days plan ppt layouts picture pdf. Use them to share invaluable insights on training completion, communication methods, policy sign off and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
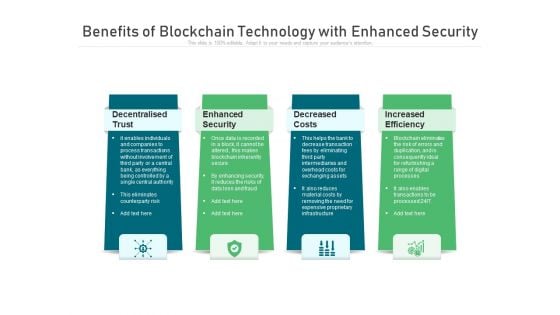
Benefits Of Blockchain Technology With Enhanced Security Ppt PowerPoint Presentation Gallery Infographics PDF
Presenting benefits of blockchain technology with enhanced security ppt powerpoint presentation gallery infographics pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including decentralised trust, enhanced security, decreased costs. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
5 Benchmarks Visual For Mobile Security Ppt PowerPoint Presentation Gallery Tips PDF
Presenting 5 benchmarks visual for mobile security ppt powerpoint presentation gallery tips pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including 5 benchmarks visual for mobile security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Security Computer System Interface Browser With Gear Icon Ppt Inspiration Objects PDF
Presenting Security Computer System Interface Browser With Gear Icon Ppt Inspiration Objects PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Security Computer System, Interface Browser, Gear Icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Elliptic Curve Cryptography ECC Data Security In Cloud Computing Ppt Template
This slide talks about the Elliptic Curve Cryptography algorithm. The purpose of this slide is to elaborate the different applications of ECC algorithm. The uses of this algorithm are key agreement, mobile devices, cryptocurrency, etc. Welcome to our selection of the Elliptic Curve Cryptography ECC Data Security In Cloud Computing Ppt Template. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide talks about the Elliptic Curve Cryptography algorithm. The purpose of this slide is to elaborate the different applications of ECC algorithm. The uses of this algorithm are key agreement, mobile devices, cryptocurrency, etc.

Security Management Plan Steps In Detail Identifying Goals And Objectives Download PDF
This slide provides information about the first and the foremost step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Identifying Goals and Objectives. This is a security management plan steps in detail identifying goals and objectives download pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like implementation, security, management, organizational, information. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
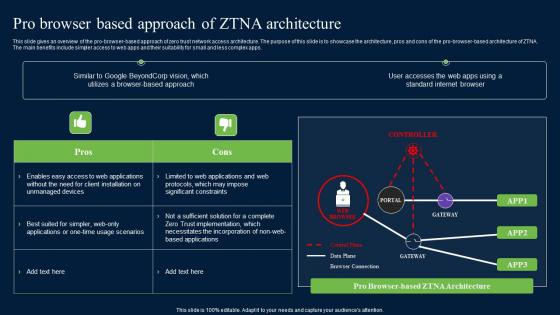
Pro Browser Based Approach Of ZTNA Architecture Zero Trust Network Security Formats Pdf
The main benefits include simpler access to web apps and their suitability for small and less complex apps. Presenting this PowerPoint presentation, titled Pro Browser Based Approach Of ZTNA Architecture Zero Trust Network Security Formats Pdf, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Pro Browser Based Approach Of ZTNA Architecture Zero Trust Network Security Formats Pdf. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Pro Browser Based Approach Of ZTNA Architecture Zero Trust Network Security Formats Pdf that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. The main benefits include simpler access to web apps and their suitability for small and less complex apps.
Equity Security Market In India Business Ppt PowerPoint Presentation Summary Layout
Presenting this set of slides with name equity security market in india business ppt powerpoint presentation summary layout. This is a three stage process. The stages in this process are marketing, business, management, planning, strategy. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Barriers And Solutions Icons Slide Security Technology Ppt PowerPoint Presentation Model Information
Presenting this set of slides with name barriers and solutions icons slide security technology ppt powerpoint presentation model information. The topics discussed in these slides are technology, communication, planning, strategy, marketing. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Tqm Model Security Process Ppt PowerPoint Presentation Infographic Template File Formats
Presenting this set of slides with name tqm model security process ppt powerpoint presentation infographic template file formats. This is a five stage process. The stages in this process are marketing, business, management, planning, strategy. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security Implementation Framework Ppt PowerPoint Presentation Complete Deck With Slides
Presenting this set of slides with name cyber security implementation framework ppt powerpoint presentation complete deck with slides. The topics discussed in these slides are business, management, marketing, planning, strategy. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
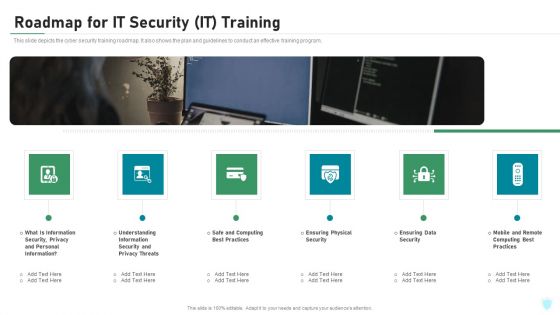
Roadmap For IT Security IT Training Ppt Slides Format Ideas PDF
This slide depicts the cyber security training roadmap. It also shows the plan and guidelines to conduct an effective training program. Presenting roadmap for it security it training ppt slides format ideas pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like security, privacy, safe and computing, ensuring physical security, mobile and remote. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Five Stages Circular Process Business Cyber Security Ppt PowerPoint Presentation Icon Tips
Presenting this set of slides with name five stages circular process business cyber security ppt powerpoint presentation icon tips. This is a five stage process. The stages in this process are technology, strategy, steps approach. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Prevention Of Information Comparison Of Various Security Awareness Training Software Template PDF
The purpose of this slide is to drawn comparison of multiple software which can be used to provide cyber security training to the key stakeholders. Information covered in this slide is related to phishing simulations, security reporting, individualized security training plan etc. There are so many reasons you need a Prevention Of Information Comparison Of Various Security Awareness Training Software Template PDF. The first reason is you cant spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Review Cyber Security Status With Due Diligence Checklist Ppt PowerPoint Presentation File Inspiration PDF
The following slide showcases checklist to monitor security progress status and ensure business credibility. It includes elements such as mobility and clean up policy,disaster recovery, password encryption, tasks, reviews etc. There are so many reasons you need a Review Cyber Security Status With Due Diligence Checklist Ppt PowerPoint Presentation File Inspiration PDF. The first reason is you cannot spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
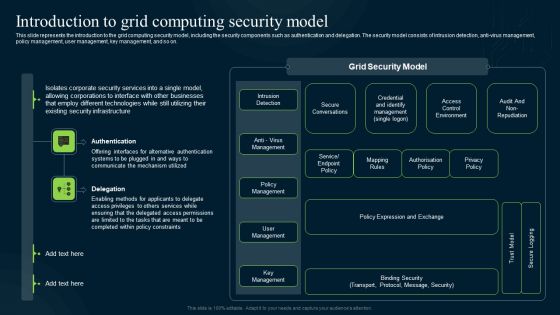
Grid Computing Infrastructure Introduction To Grid Computing Security Model Background PDF
This slide represents the introduction to the grid computing security model, including the security components such as authentication and delegation. The security model consists of intrusion detection, anti-virus management, policy management, user management, key management, and so on. This modern and well-arranged Grid Computing Infrastructure Introduction To Grid Computing Security Model Background PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
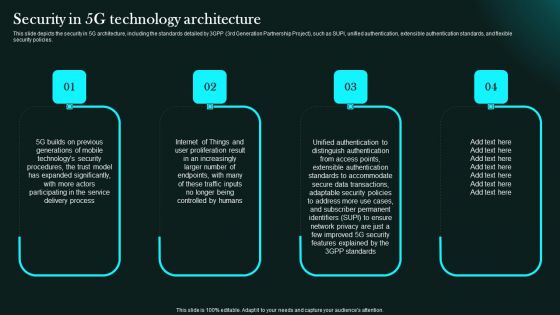
Security In 5G Technology Architecture 5G Network Functional Architecture Clipart PDF
This slide depicts the security in 5G architecture, including the standards detailed by 3GPP 3rd Generation Partnership Project, such as SUPI, unified authentication, extensible authentication standards, and flexible security policies.Slidegeeks has constructed Security In 5G Technology Architecture 5G Network Functional Architecture Clipart PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.
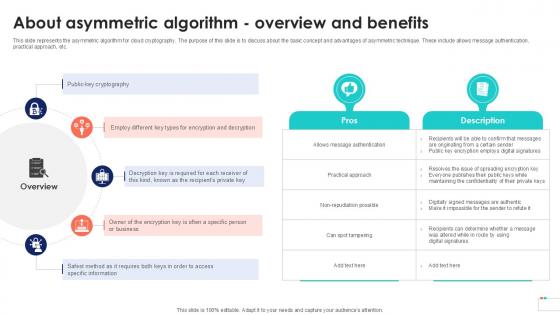
About Asymmetric Algorithm Overview Data Security In Cloud Computing Ppt Template
This slide represents the asymmetric algorithm for cloud cryptography. The purpose of this slide is to discuss about the basic concept and advantages of asymmetric technique. These include allows message authentication, practical approach, etc. Boost your pitch with our creative About Asymmetric Algorithm Overview Data Security In Cloud Computing Ppt Template. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide represents the asymmetric algorithm for cloud cryptography. The purpose of this slide is to discuss about the basic concept and advantages of asymmetric technique. These include allows message authentication, practical approach, etc.

IT Policies And Procedures Information Security Policy For Employees Download PDF
Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our IT Policies And Procedures Information Security Policy For Employees Download PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into IT Policies And Procedures Information Security Policy For Employees Download PDF.

Methods To Identify Crypto Comprehensive Guide To Blockchain Digital Security Template Pdf
The following slide illustrates various methods to determine blockchain phishing attack and safeguard confidential information. It includes elements such as copycatting, spellings, ambiguous links, using public email ID, disordered content etc. This Methods To Identify Crypto Comprehensive Guide To Blockchain Digital Security Template Pdf is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Methods To Identify Crypto Comprehensive Guide To Blockchain Digital Security Template Pdf features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today The following slide illustrates various methods to determine blockchain phishing attack and safeguard confidential information. It includes elements such as copycatting, spellings, ambiguous links, using public email ID, disordered content etc.
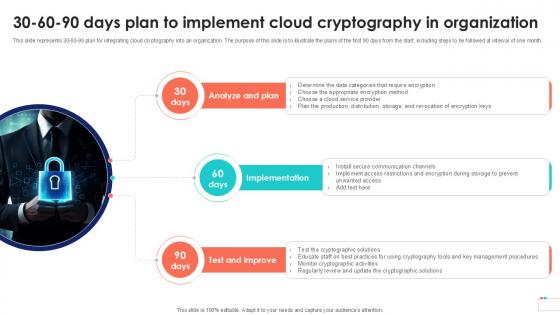
30 60 90 Days Plan To Implement Data Security In Cloud Computing Ppt Sample
This slide represents 30-60-90 plan for integrating cloud cryptography into an organization. The purpose of this slide is to illustrate the plans of the first 90 days from the start, including steps to be followed at interval of one month. Find a pre-designed and impeccable 30 60 90 Days Plan To Implement Data Security In Cloud Computing Ppt Sample. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide represents 30-60-90 plan for integrating cloud cryptography into an organization. The purpose of this slide is to illustrate the plans of the first 90 days from the start, including steps to be followed at interval of one month.
Information Security Management System Vector Icon Ppt PowerPoint Presentation Gallery Templates PDF
Presenting information security management system vector icon ppt powerpoint presentation gallery templates pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including information security management system vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Icon For Payment Security Technology In Market Investor Transactions Summary PDF
Presenting Icon For Payment Security Technology In Market Investor Transactions Summary PDF to dispense important information. This template comprises Four stages. It also presents valuable insights into the topics including Icon For Payment Security, Technology Market Investor, Transactions Summary. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
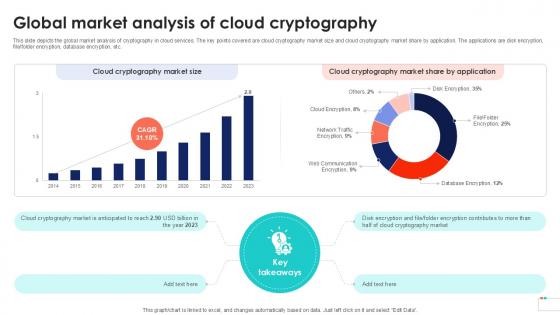
Global Market Analysis Of Cloud Data Security In Cloud Computing Ppt Powerpoint
This slide depicts the global market analysis of cryptography in cloud services. The key points covered are cloud cryptography market size and cloud cryptography market share by application. The applications are disk encryption, file, folder encryption, database encryption, etc. Are you searching for a Global Market Analysis Of Cloud Data Security In Cloud Computing Ppt Powerpoint that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Global Market Analysis Of Cloud Data Security In Cloud Computing Ppt Powerpoint from Slidegeeks today. This slide depicts the global market analysis of cryptography in cloud services. The key points covered are cloud cryptography market size and cloud cryptography market share by application. The applications are disk encryption, file, folder encryption, database encryption, etc.

Develop Corporate Cyber Security Risk Mitigation Plan Cover Letter For Organization Cyber Protection Services Inspiration PDF
Presenting develop corporate cyber security risk mitigation plan cover letter for organization cyber protection services inspiration pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like systems and servers, achieve goals, secure organization information, network security monitoring. In addtion, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.

Business Model Canvas Security Service Provider Business Model BMC SS V
This slide provides the business model canvas of the company. It involves key partners, key activities, USP, customer relationships, customer segments, channels, revenue streams, channels, key resources, cost structure. Find a pre-designed and impeccable Business Model Canvas Security Service Provider Business Model BMC SS V. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide provides the business model canvas of the company. It involves key partners, key activities, USP, customer relationships, customer segments, channels, revenue streams, channels, key resources, cost structure.

Picture Editing Company Outline Canva Security Processes And Systems Elements PDF
This slide highlights the Canva security systems encryption, data security, attack, monitoring, staged releases, secure development, account safety and in- app permissions. Welcome to our selection of the Picture Editing Company Outline Canva Security Processes And Systems Elements PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.

Solutions To Overcome Various Security For Cloud Based Systems Challenges Mockup PDF
This slide shows solutions to various challenges faced by organizations to provide cloud security. These challenges are data breaches, lack of expertise, insider threats and unsecured APIs. Showcasing this set of slides titled Solutions To Overcome Various Security For Cloud Based Systems Challenges Mockup PDF. The topics addressed in these templates are Solutions To Overcome, Various Security For Cloud, Based Systems Challenges . All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
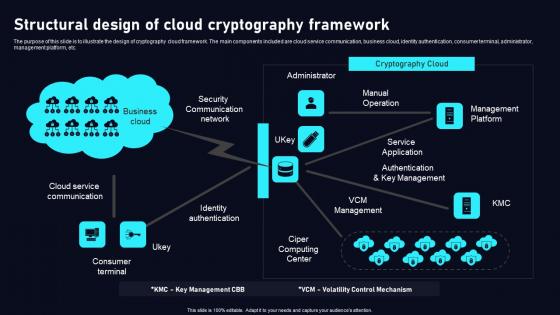
Structural Design Of Cloud Cryptography Cloud Data Security Using Cryptography Themes Pdf
The purpose of this slide is to illustrate the design of cryptography cloud framework. The main components included are cloud service communication, business cloud, identity authentication, consumer terminal, administrator, management platform, etc. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Structural Design Of Cloud Cryptography Cloud Data Security Using Cryptography Themes Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates The purpose of this slide is to illustrate the design of cryptography cloud framework. The main components included are cloud service communication, business cloud, identity authentication, consumer terminal, administrator, management platform, etc.
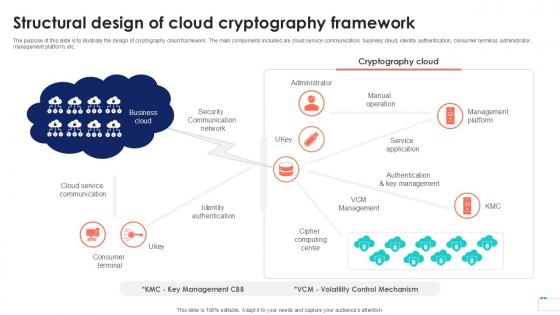
Structural Design Of Cloud Cryptography Data Security In Cloud Computing Ppt Sample
The purpose of this slide is to illustrate the design of cryptography cloud framework. The main components included are cloud service communication, business cloud, identity authentication, consumer terminal, administrator, management platform, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Structural Design Of Cloud Cryptography Data Security In Cloud Computing Ppt Sample will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. The purpose of this slide is to illustrate the design of cryptography cloud framework. The main components included are cloud service communication, business cloud, identity authentication, consumer terminal, administrator, management platform, etc.
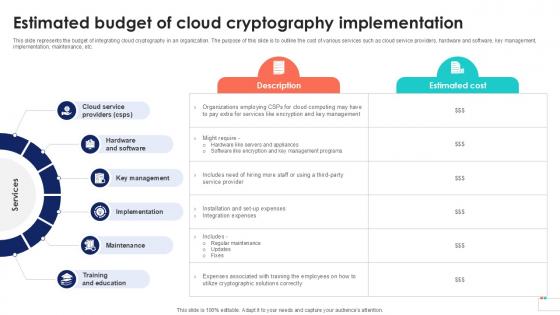
Estimated Budget Of Cloud Cryptography Data Security In Cloud Computing Ppt Slide
This slide represents the budget of integrating cloud cryptography in an organization. The purpose of this slide is to outline the cost of various services such as cloud service providers, hardware and software, key management, implementation, maintenance, etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Estimated Budget Of Cloud Cryptography Data Security In Cloud Computing Ppt Slide from Slidegeeks and deliver a wonderful presentation. This slide represents the budget of integrating cloud cryptography in an organization. The purpose of this slide is to outline the cost of various services such as cloud service providers, hardware and software, key management, implementation, maintenance, etc.

Execution Of ICT Strategic Plan Network Security Model To Effective Communication Demonstration PDF
This slide represents the network security model for effective communication in the organization. It covers information regarding security threats, firewalls, virtual private networks, etc. Get a simple yet stunning designed Execution Of ICT Strategic Plan Network Security Model To Effective Communication Demonstration PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Execution Of ICT Strategic Plan Network Security Model To Effective Communication Demonstration PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
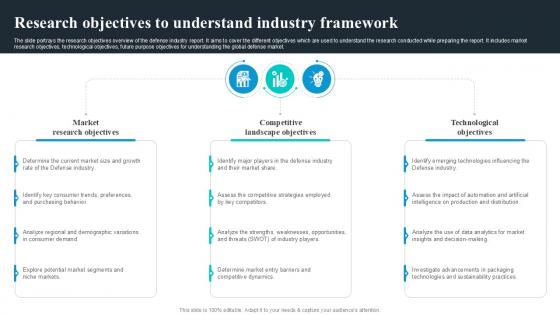
Research Objectives To Understand Global Security Industry PPT Template IR SS V
The slide highlights the SWOT analysis of Defense industry. The main purpose of this side is to understand and measure the comprehensive assessment of defense market. It further helps in mitigating the potential risks. Key components include strengths, weakness opportunities and threats. The slide portrays the research objectives overview of the defense industry report. It aims to cover the different objectives which are used to understand the research conducted while preparing the report. It includes market research objectives, technological objectives, future purpose objectives for understanding the global defense market. Are you searching for a Research Objectives To Understand Global Security Industry PPT Template IR SS V that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Research Objectives To Understand Global Security Industry PPT Template IR SS V from Slidegeeks today. The slide highlights the SWOT analysis of Defense industry. The main purpose of this side is to understand and measure the comprehensive assessment of defense market. It further helps in mitigating the potential risks. Key components include strengths, weakness opportunities and threats.

Building Trust With IoT Security Automated Patch Management To Increase Overall Productivity IoT SS V
This slide includes an automated patch management process that ensures patch availability on devices in accordance with deployment policies. It includes steps such as scan for missing patches, collect patches from vendors, deploy patches, and report results. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Building Trust With IoT Security Automated Patch Management To Increase Overall Productivity IoT SS V for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide includes an automated patch management process that ensures patch availability on devices in accordance with deployment policies. It includes steps such as scan for missing patches, collect patches from vendors, deploy patches, and report results.

Stages To Develop Security Analysis Approach Documentation Ppt PowerPoint Presentation File Graphics PDF
Showcasing this set of slides titled stages to develop security analysis approach documentation ppt powerpoint presentation file graphics pdf. The topics addressed in these templates are relevant frameworks, stages to develop security, analysis approach documentation. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
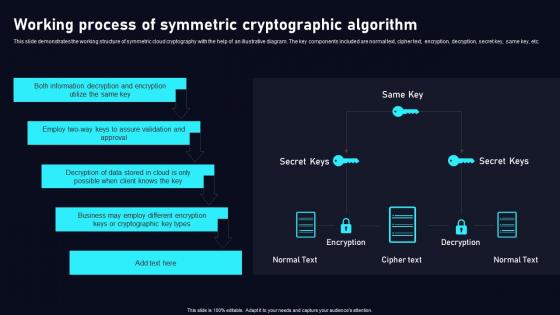
Working Process Of Symmetric Cloud Data Security Using Cryptography Download Pdf
This slide demonstrates the working structure of symmetric cloud cryptography with the help of an illustrative diagram. The key components included are normal text, cipher text, encryption, decryption, secret key, same key, etc. Want to ace your presentation in front of a live audience OurWorking Process Of Symmetric Cloud Data Security Using Cryptography Download Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use. This slide demonstrates the working structure of symmetric cloud cryptography with the help of an illustrative diagram. The key components included are normal text, cipher text, encryption, decryption, secret key, same key, etc.

Global Data Security Industry Report Csr Initiatives Taken By Companies In Cybersecurity Industry IR SS V
The slide outlines CSR initiatives undertaken by the cybersecurity industry. The purpose of the slide is to encourage ethical practices, social responsibility, and sustainable development. The key components include cybersecurity education and training, community engagement. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Global Data Security Industry Report Csr Initiatives Taken By Companies In Cybersecurity Industry IR SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. The slide outlines CSR initiatives undertaken by the cybersecurity industry. The purpose of the slide is to encourage ethical practices, social responsibility, and sustainable development. The key components include cybersecurity education and training, community engagement.
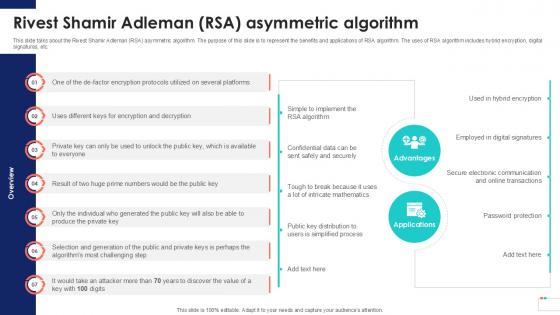
Rivest Shamir Adleman RSA Asymmetric Data Security In Cloud Computing Ppt Example
This slide talks about the Rivest Shamir Adleman RSA asymmetric algorithm. The purpose of this slide is to represent the benefits and applications of RSA algorithm. The uses of RSA algorithm includes hybrid encryption, digital signatures, etc. Want to ace your presentation in front of a live audience Our Rivest Shamir Adleman RSA Asymmetric Data Security In Cloud Computing Ppt Example can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide talks about the Rivest Shamir Adleman RSA asymmetric algorithm. The purpose of this slide is to represent the benefits and applications of RSA algorithm. The uses of RSA algorithm includes hybrid encryption, digital signatures, etc.
8 Cycle Representation Of Security Policy Ppt PowerPoint Presentation Gallery Grid PDF
Persuade your audience using this 8 cycle representation of security policy ppt powerpoint presentation gallery grid pdf. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including 8 cycle representation of security policy. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
5 Stage Framework Security Policy Management Slide Ppt PowerPoint Presentation Outline Examples PDF
Persuade your audience using this 5 stage framework security policy management slide ppt powerpoint presentation outline examples pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including 5 stage framework security policy management slide. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Comparing Two Choices Diagram For Security Policy Orchestration Ppt PowerPoint Presentation Gallery Design Templates PDF
Persuade your audience using this comparing two choices diagram for security policy orchestration ppt powerpoint presentation gallery design templates pdf. This PPT design covers two stages, thus making it a great tool to use. It also caters to a variety of topics including comparing two choices diagram for security policy orchestration. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
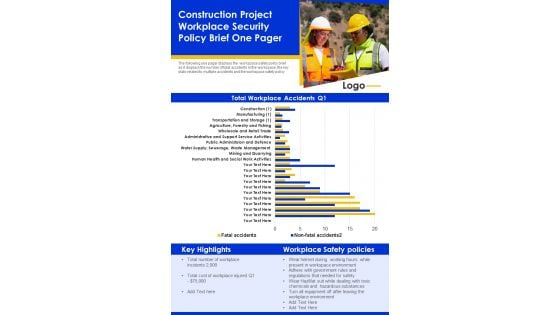
Construction Project Workplace Security Policy Brief One Pager PDF Document PPT Template
Heres a predesigned Construction Project Workplace Security Policy Brief One Pager PDF Document PPT Template for you. Built on extensive research and analysis, this one-pager template has all the centerpieces of your specific requirements. This temple exudes brilliance and professionalism. Being completely editable, you can make changes to suit your purpose. Get this Construction Project Workplace Security Policy Brief One Pager PDF Document PPT Template Download now.
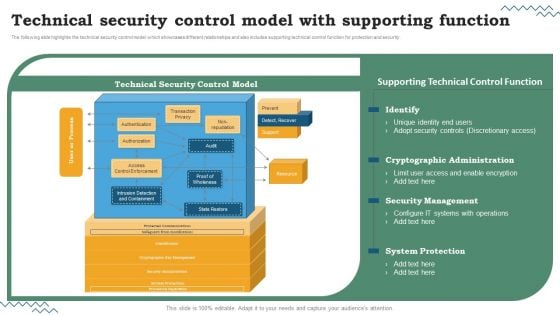
Software Development Life Cycle Planning Technical Security Control Model With Supporting Function Inspiration PDF
The following slide highlights the technical security control model which showcases different relationships and also includes supporting technical control function for protection and security. Are you searching for a Software Development Life Cycle Planning Technical Security Control Model With Supporting Function Inspiration PDF that is uncluttered, straightforward, and original. Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort youve put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Software Development Life Cycle Planning Technical Security Control Model With Supporting Function Inspiration PDF from Slidegeeks today.
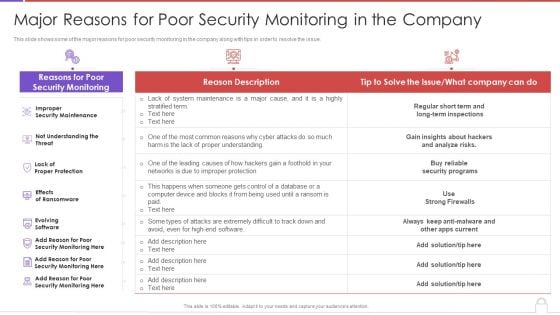
Methods To Develop Major Reasons For Poor Security Monitoring In The Company Information PDF
This slide shows some of the major reasons for poor security monitoring in the company along with tips in order to resolve the issue. Deliver and pitch your topic in the best possible manner with this methods to develop major reasons for poor security monitoring in the company information pdf. Use them to share invaluable insights on improper security maintenance, evolving software, high end software and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

IT Security Risk Management Approach Introduction Scorecard To Check Cybersecurity And Digital Graphics PDF
Following slide illustrates a scorecard that company will use to check its preparedness against various cyber security and digital risk events. Sections covered here are fraud prevention considerations, score and notes. This is a IT Security Risk Management Approach Introduction Scorecard To Check Cybersecurity And Digital Graphics PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Specific Measures, Security Control, Cybersecurity Risk. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
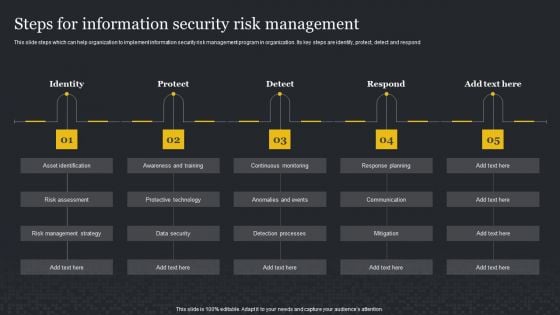
Steps For Information Security Risk Management Cybersecurity Risk Assessment Mockup PDF
This slide steps which can help organization to implement information security risk management program in organization. Its key steps are identify, protect, detect and respond. Create an editable Steps For Information Security Risk Management Cybersecurity Risk Assessment Mockup PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Steps For Information Security Risk Management Cybersecurity Risk Assessment Mockup PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
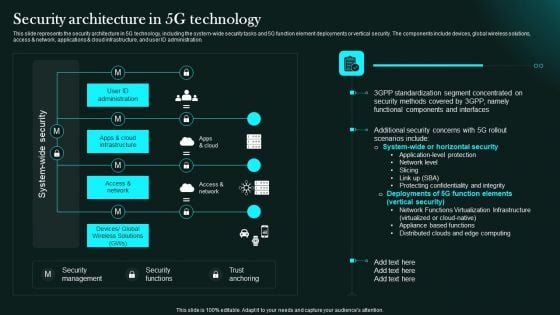
Security Architecture In 5G Technology 5G Network Functional Architecture Clipart PDF
This slide represents the security architecture in 5G technology, including the system-wide security tasks and 5G function element deployments or vertical security. The components include devices, global wireless solutions, access network, applications cloud infrastructure, and user ID administration.Retrieve professionally designed Security Architecture In 5G Technology 5G Network Functional Architecture Clipart PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You Do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Organization Impact Metrics Strategic Hacking Prevention Awareness Training For IT Security Graphics PDF
This slide the metrics That assess how your security awareness plan serves the overall security system of your company, and therefore the organizations mission. Presenting organization impact metrics strategic hacking prevention awareness training for it security graphics pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like organization, policy violations, data loss incidents, human resources. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
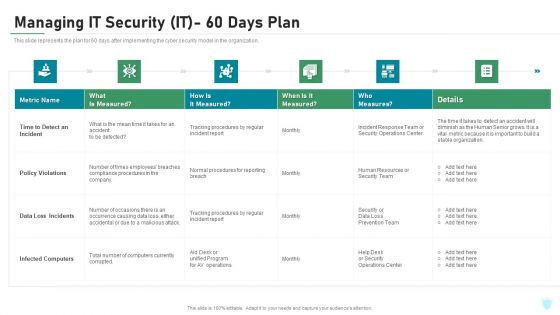
Managing IT Security IT 60 Days Plan Ppt Ideas Graphics PDF
This slide represents the plan for 60 days after implementing the cyber security model in the organization. Deliver an awe inspiring pitch with this creative managing it security it 60 days plan ppt ideas graphics pdf bundle. Topics like policy violations, infected computers, data loss incidents, time to detect an incident can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
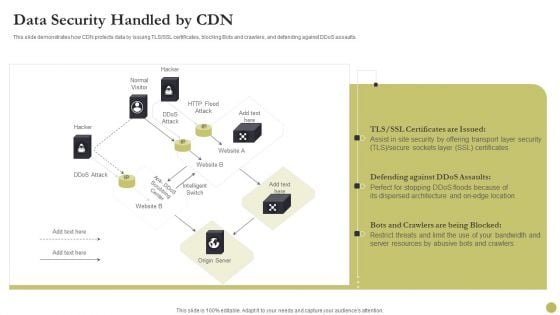
Content Delivery Network Edge Server Data Security Handled By CDN Diagrams PDF
This slide demonstrates how CDN protects data by issuing TLS or SSL certificates, blocking Bots and crawlers, and defending against DDoS assaults. Deliver and pitch your topic in the best possible manner with this Content Delivery Network Edge Server Data Security Handled By CDN Diagrams PDF. Use them to share invaluable insights on Security, Location, Server Resources and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Five Steps Of Productivity Improvement Innovation And Security Ppt PowerPoint Presentation Layouts Inspiration
This is a five steps of productivity improvement innovation and security ppt powerpoint presentation layouts inspiration. This is a five stage process. The stages in this process are risk management, risk factors, risk variable.

Action Plan Timeline For Safety And Security System Services Proposal One Pager Sample Example Document
Purpose of the following slide is to show the action plan timeline for security guard service proposal as it displays steps of the process such as training and evaluating etc. Presenting you an exemplary Action Plan Timeline For Safety And Security System Services Proposal One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Action Plan Timeline For Safety And Security System Services Proposal One Pager Sample Example Document brilliant piece now.
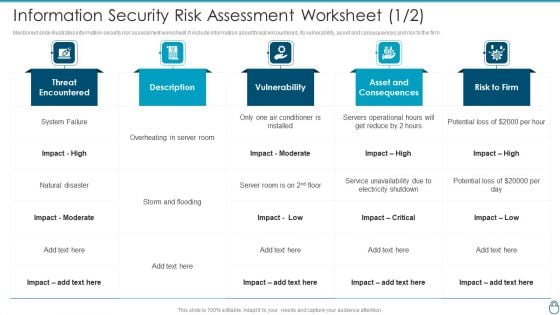
Cybersecurity Risk Administration Plan Information Security Risk Assessment Worksheet Asset Graphics PDF
Mentioned slide illustrates information security risk assessment worksheet. It include information about threat encountered, its vulnerability, asset and consequences and risk to the firm.Deliver an awe inspiring pitch with this creative Cybersecurity Risk Administration Plan Information Security Risk Assessment Worksheet Asset Graphics PDF bundle. Topics like Conditioner Is Installed, Asset And Consequences, Electricity Shutdown can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
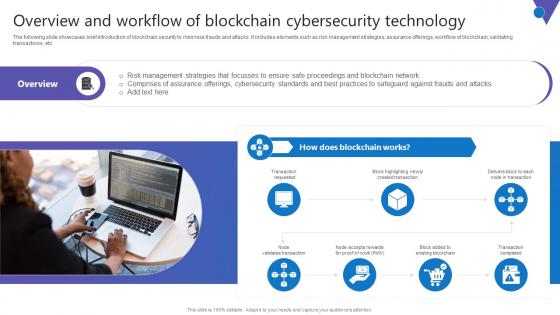
Overview And Workflow Comprehensive Guide To Blockchain Digital Security Summary Pdf
The following slide showcases brief introduction of blockchain security to minimize frauds and attacks. It includes elements such as risk management strategies, assurance offerings, workflow of blockchain, validating transactions, etc. Explore a selection of the finest Overview And Workflow Comprehensive Guide To Blockchain Digital Security Summary Pdf here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Overview And Workflow Comprehensive Guide To Blockchain Digital Security Summary Pdf to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. The following slide showcases brief introduction of blockchain security to minimize frauds and attacks. It includes elements such as risk management strategies, assurance offerings, workflow of blockchain, validating transactions, etc.

Cyber Security Implementation Framework Analyzing IT Department On NIST Cybersecurity Framework Topics PDF
Presenting this set of slides with name cyber security implementation framework analyzing it department on nist cybersecurity framework topics pdf. This is a one stage process. The stages in this process are asset management, governance, data security, threat intelligence, incident response planning, incident recovery. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
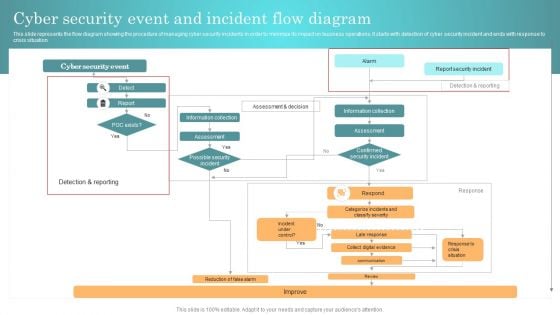
Incident Response Techniques Deployement Cyber Security Event And Incident Flow Diagram Structure PDF
This slide represents the flow diagram showing the procedure of managing cyber security incidents in order to minimize its impact on business operations. It starts with detection of cyber security incident and ends with response to crisis situation. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Incident Response Techniques Deployement Cyber Security Event And Incident Flow Diagram Structure PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Incident Response Techniques Deployement Cyber Security Event And Incident Flow Diagram Structure PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.
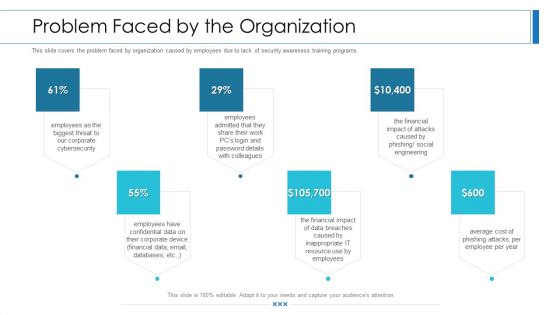
Workforce Security Realization Coaching Plan Problem Faced By The Organization Ppt Styles PDF
This slide covers the problem faced by organization caused by employees due to lack of security awareness training programs. This is a workforce security realization coaching plan problem faced by the organization ppt styles pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity, social engineering, financial impact, organization, security awareness. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.


 Continue with Email
Continue with Email

 Home
Home


































