Security Strategy
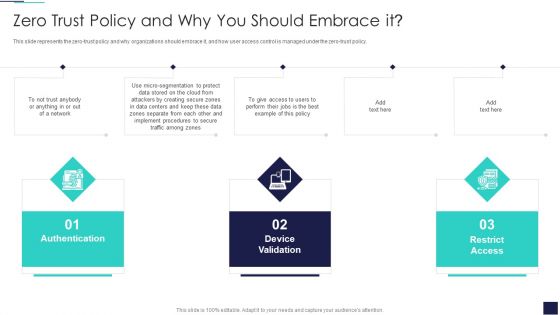
Cloud Information Security Zero Trust Policy And Why You Should Embrace IT Ppt File Outfit PDF
This slide represents the zero-trust policy and why organizations should embrace it, and how user access control is managed under the zero-trust policy. This is a Cloud Information Security Zero Trust Policy And Why You Should Embrace IT Ppt File Outfit PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Authentication Device, Validation Network, Restrict Access. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
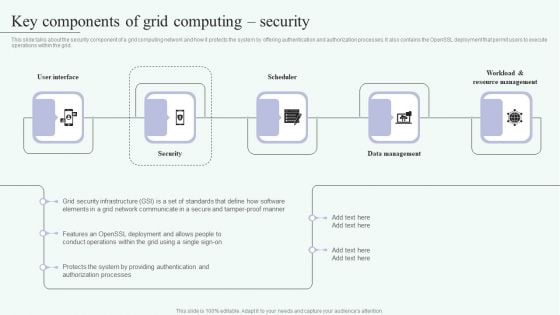
Grid Computing For High Performance Solutions Key Components Of Grid Computing Security Clipart PDF
This slide talks about the security component of a grid computing network and how it protects the system by offering authentication and authorization processes. It also contains the OpenSSL deployment that permit users to execute operations within the grid. Welcome to our selection of the Grid Computing For High Performance Solutions Key Components Of Grid Computing Security Clipart PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.
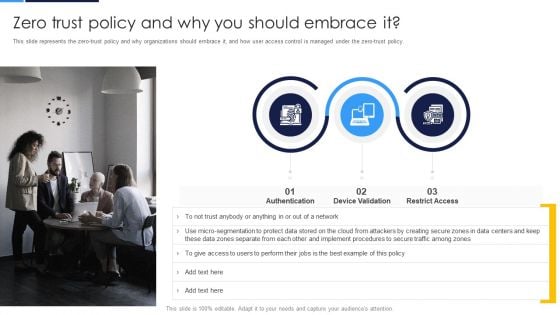
Cloud Security Assessment Zero Trust Policy And Why You Should Embrace It Designs PDF
This slide represents the zero trust policy and why organizations should embrace it, and how user access control is managed under the zero-trust policy.This is a Cloud Security Assessment Zero Trust Policy And Why You Should Embrace It Designs PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Best Example, Authentication, Implement Procedures. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Approaches To Improve Infra Cyber Security In AI Infrastructure Diagrams PDF
The following slide showcases various approaches to AI infrastructure which bodes well for future of organizations association. It presents information related to regulatory framework, expert consultations, etc. Presenting Approaches To Improve Infra Cyber Security In AI Infrastructure Diagrams PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Regulatory Framework, Protect AI Related Data, Involve Cybersecurity Experts. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
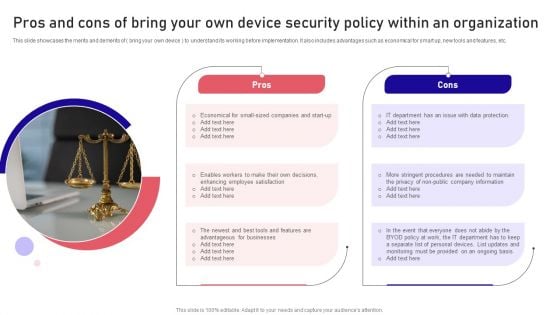
Pros And Cons Of Bring Your Own Device Security Policy Within An Organization Sample PDF
This slide showcases the merits and demerits of bring your own device to understand its working before implementation. It also includes advantages such as economical for smart up, new tools and features, etc. Presenting Pros And Cons Of Bring Your Own Device Security Policy Within An Organization Sample PDF to dispense important information. This template comprises two stages. It also presents valuable insights into the topics including Data Protection, Organization, Company Information. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Comparative Analysis Between Bring Your Own Device Security Policy And CYOD Mobile Device Programs Clipart PDF
This slide showcases distinguish between bring your own device and choose your own device policies and programs for mobile devices. It also includes differentiation on basis such as benefits , challenges, etc. Pitch your topic with ease and precision using this Comparative Analysis Between Bring Your Own Device Security Policy And CYOD Mobile Device Programs Clipart PDF. This layout presents information on Basis, Benefits, Best Practices. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
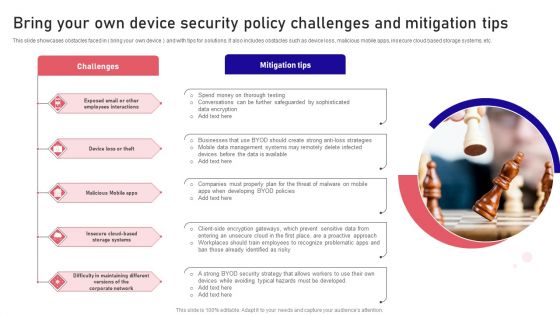
Bring Your Own Device Security Policy Challenges And Mitigation Tips Designs PDF
This slide showcases obstacles faced in bring your own device and with tips for solutions. It also includes obstacles such as device loss, malicious mobile apps, insecure cloud based storage systems, etc. Presenting Bring Your Own Device Security Policy Challenges And Mitigation Tips Designs PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Challenges, Mitigation Tips, Malicious Mobile. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
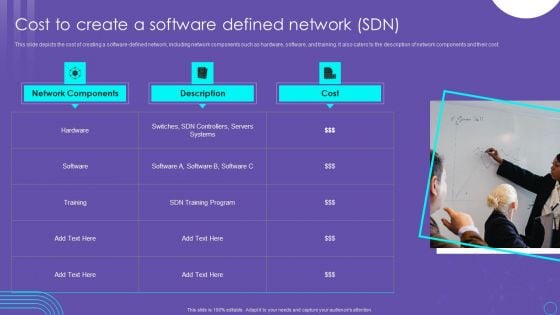
SDN Security Architecture Cost To Create A Software Defined Network SDN Slides PDF
This slide depicts the cost of creating a software defined network, including network components such as hardware, software, and training. It also caters to the description of network components and their cost. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our SDN Security Architecture Cost To Create A Software Defined Network SDN Slides PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into SDN Security Architecture Cost To Create A Software Defined Network SDN Slides PDF
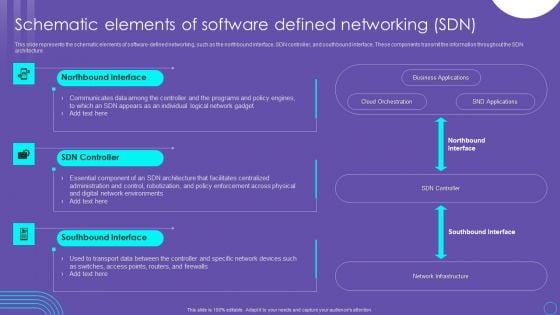
SDN Security Architecture Schematic Elements Of Software Defined Networking SDN Pictures PDF
This slide represents the schematic elements of software defined networking, such as the northbound interface, SDN controller, and southbound interface. These components transmit the information throughout the SDN architecture. Create an editable SDN Security Architecture Schematic Elements Of Software Defined Networking SDN Pictures PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. SDN Security Architecture Schematic Elements Of Software Defined Networking SDN Pictures PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
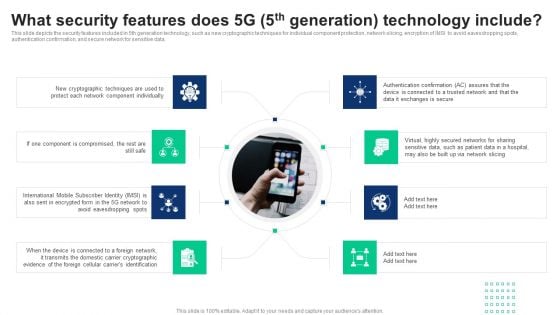
1G To 5G Cellular What Security Features Does 5G 5Th Generation Technology Include Information PDF
This slide depicts the security features included in 5th generation technology, such as new cryptographic techniques for individual component protection, network slicing, encryption of IMSI to avoid eavesdropping spots, authentication confirmation, and secure network for sensitive data. Welcome to our selection of the 1G To 5G Cellular What Security Features Does 5G 5Th Generation Technology Include Information PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.
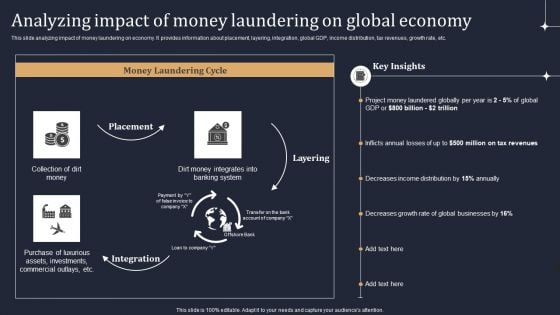
KYC Transaction Monitoring System Business Security Analyzing Impact Of Money Laundering Guidelines PDF
This slide analyzing impact of money laundering on economy. It provides information about placement, layering, integration, global GDP, income distribution, tax revenues, growth rate, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable KYC Transaction Monitoring System Business Security Analyzing Impact Of Money Laundering Guidelines PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
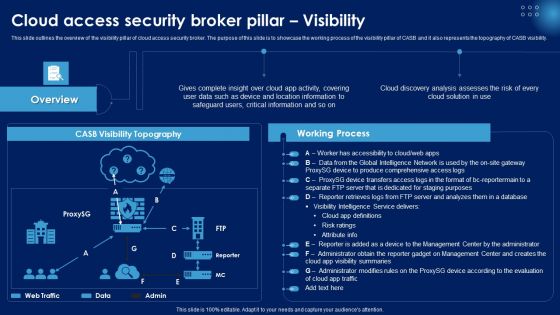
Cloud Access Security Broker Pillar Visibility Ppt PowerPoint Presentation File Infographics PDF
This slide outlines the overview of the visibility pillar of cloud access security broker. The purpose of this slide is to showcase the working process of the visibility pillar of CASB and it also represents the topography of CASB visibility. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Cloud Access Security Broker Pillar Visibility Ppt PowerPoint Presentation File Infographics PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
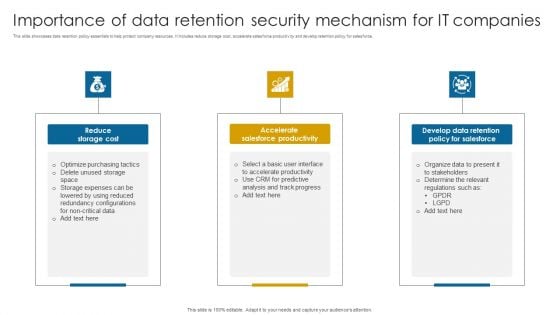
Importance Of Data Retention Security Mechanism For It Companies Professional PDF
This slide showcases data retention policy essentials to help protect company resources. It includes reduce storage cost, accelerate salesforce productivity and develop retention policy for salesforce.Presenting Importance Of Data Retention Security Mechanism For It Companies Professional PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Salesforce Productivity, Develop Data Retention, Determine Relevant. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
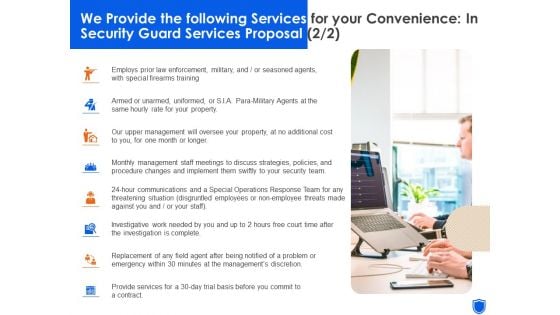
We Provide The Following Services For Your Convenience In Security Guard Services Proposal Professional PDF
This is a we provide the following services for your convenience in security guard services proposal professional pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like employs prior law enforcement, military or seasoned agents, with special firearms training. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
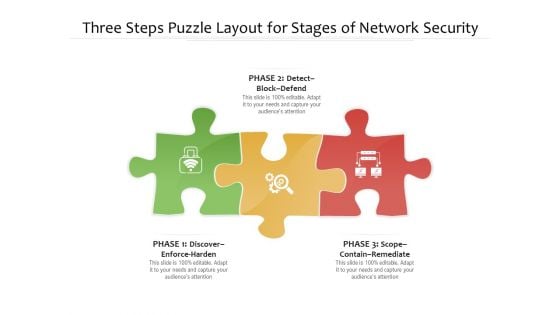
Three Steps Puzzle Layout For Stages Of Network Security Ppt PowerPoint Presentation File Vector PDF
Persuade your audience using this three steps puzzle layout for stages of network security ppt powerpoint presentation file vector pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including detect block defend, discover enforce harden, scope contain remediate. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
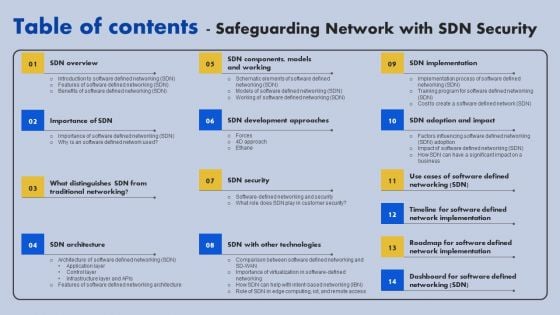
Table Of Contents Safeguarding Network With SDN Security Ppt Ideas Design Ideas PDF
If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Table Of Contents Safeguarding Network With SDN Security Ppt Ideas Design Ideas PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.

Security Software Company Investor Funding Pitch Deck Value Proposition USP Introduction PDF
This slide showcases unique selling propositions of solution offered by IT company differentiates product from others. Differentiators are quick time-to-value , high effectiveness for detection and response , platform-as-a-service technique and have patents for Ava, EntityiQ and adversarial modeling. Explore a selection of the finest Security Software Company Investor Funding Pitch Deck Value Proposition USP Introduction PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Security Software Company Investor Funding Pitch Deck Value Proposition USP Introduction PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Cloud Access Security Broker Pillar Compliance Ppt PowerPoint Presentation File Layouts PDF
This slide gives an overview of the compliance pillar of cloud access security broker. The purpose of this slide is to showcase how compliance is a vital factor for an organization migrating its data and systems to the cloud. Compliance can help industries such as healthcare, retail, and financial services. Present like a pro with Cloud Access Security Broker Pillar Compliance Ppt PowerPoint Presentation File Layouts PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Table Of Contents For Integrating Data Privacy System To Enhance Security Themes PDF
Want to ace your presentation in front of a live audience Our Table Of Contents For Integrating Data Privacy System To Enhance Security Themes PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.
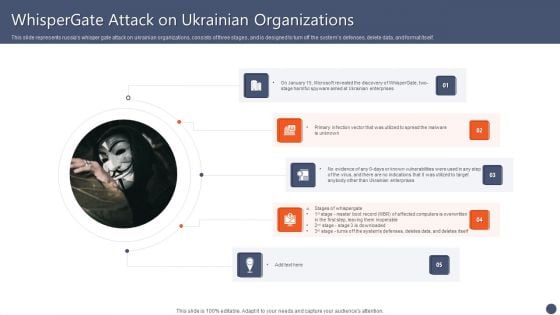
Series Of Cyber Security Attacks Against Ukraine 2022 Whispergate Attack On Ukrainian Organizations Information PDF
This slide represents russias whisper gate attack on ukrainian organizations, consists of three stages, and is designed to turn off the systems defenses, delete data, and format itself. Are you searching for a Series Of Cyber Security Attacks Against Ukraine 2022 Whispergate Attack On Ukrainian Organizations Information PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Series Of Cyber Security Attacks Against Ukraine 2022 Whispergate Attack On Ukrainian Organizations Information PDF from Slidegeeks today.

Matrix For Threat Solution And Risk Management Information Security Risk Administration Inspiration PDF
This slide showcases matrix that can help organization to formulate solutions for different types of information security attacks. It can help organization to mitigate the risks and safeguard information in case of any attack.Welcome to our selection of the Matrix For Threat Solution And Risk Management Information Security Risk Administration Inspiration PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 precent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.
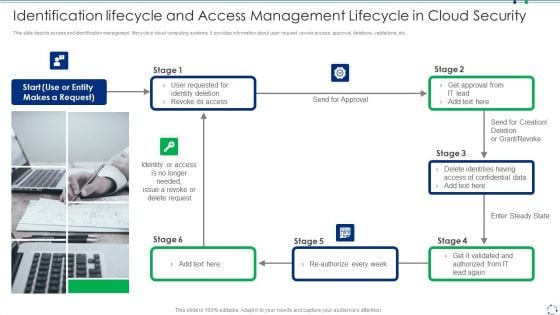
Identification Lifecycle And Access Management Lifecycle In Cloud Security Guidelines PDF
This slide depicts access and identification management lifecycle in cloud computing systems. It provides information about user request, revoke access, approval, deletions, validations, etc.Presenting identification lifecycle and access management lifecycle in cloud security guidelines pdf to dispense important information. This template comprises one stage. It also presents valuable insights into the topics including identity deletion, revoke its access, identity or access This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Table Of Contents KYC Transaction Monitoring System For Business Security Global Brochure PDF
Slidegeeks is here to make your presentations a breeze with Table Of Contents KYC Transaction Monitoring System For Business Security Global Brochure PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Certified Information Systems Security Professional CISSP Details IT Certifications To Enhance Rules PDF
This slide covers CISSP certification details such as what is the CISSP, how to become certified, how to prepare for CISSP and why to get CISSP certifications. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Certified Information Systems Security Professional CISSP Details IT Certifications To Enhance Rules PDF can be your best option for delivering a presentation. Represent everything in detail using Certified Information Systems Security Professional CISSP Details IT Certifications To Enhance Rules PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
Prevention Of Information Overview Of Cyber Security Awareness Course Icons PDF
The purpose of this slide is to provide a glimpse of the selected cyber security awareness course. It covers information about the instructor details, course content, attendees and learning outcome. This Prevention Of Information Overview Of Cyber Security Awareness Course Icons PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

KYC Transaction Monitoring System Business Security Risks Identified During Transaction Monitoring Designs PDF
This slide showcases risks identified during transaction monitoring. It provides information about anti money laundering fines, staff productivity, motivation, organizational profitability, compliance, fees, false positive, workload, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give KYC Transaction Monitoring System Business Security Risks Identified During Transaction Monitoring Designs PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable KYC Transaction Monitoring System Business Security Risks Identified During Transaction Monitoring Designs PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Table Of Contents Developing Information Technology Security Awareness Training Program For Employees Graphics PDF
If you are looking for a format to display your unique thoughts, then the professionally designed Table Of Contents Developing Information Technology Security Awareness Training Program For Employees Graphics PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Table Of Contents Developing Information Technology Security Awareness Training Program For Employees Graphics PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Table Of Contents Increasing Information Security Awareness In Company Using Various Techniques Clipart PDF
If you are looking for a format to display your unique thoughts, then the professionally designed Table Of Contents Increasing Information Security Awareness In Company Using Various Techniques Clipart PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Table Of Contents Increasing Information Security Awareness In Company Using Various Techniques Clipart PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
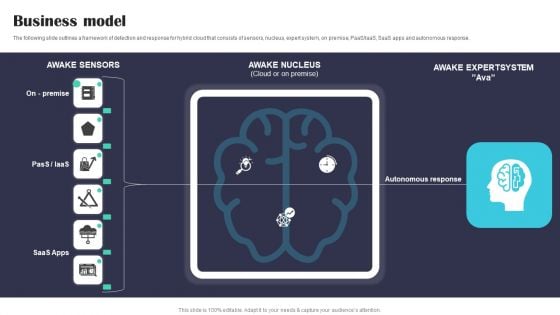
Security Software Company Investor Funding Pitch Deck Business Model Structure PDF
The following slide outlines a framework of detection and response for hybrid cloud that consists of sensors, nucleus, expert system, on premise, PaaS or IaaS, SaaS apps and autonomous response. Create an editable Security Software Company Investor Funding Pitch Deck Business Model Structure PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Security Software Company Investor Funding Pitch Deck Business Model Structure PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Security Software Company Investor Funding Pitch Deck Investment Ask Clipart PDF
This slide represents the information related to the investment requirements to the investors for seeking needed funds and the purpose of seeking finance. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Security Software Company Investor Funding Pitch Deck Investment Ask Clipart PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Security Software Company Investor Funding Pitch Deck Investment Ask Clipart PDF today and make your presentation stand out from the rest.

Table Of Contents For Comprehensive Guide For Ensuring IT Infrastructure Security Slides PDF
If you are looking for a format to display your unique thoughts, then the professionally designed Table Of Contents For Comprehensive Guide For Ensuring IT Infrastructure Security Slides PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Table Of Contents For Comprehensive Guide For Ensuring IT Infrastructure Security Slides PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Agenda For Building Security Awareness Among Workforce To Minimize Cybersecurity Threats Template PDF
Find a pre designed and impeccable Agenda For Building Security Awareness Among Workforce To Minimize Cybersecurity Threats Template PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
Building Security Awareness Among Workforce To Minimize Cybersecurity Threats Table Of Contents Download PDF
Boost your pitch with our creative Building Security Awareness Among Workforce To Minimize Cybersecurity Threats Table Of Contents Download PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
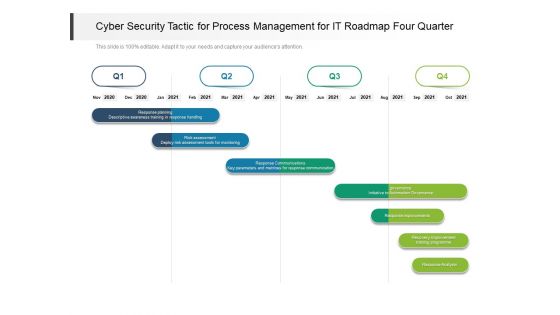
Cyber Security Tactic For Process Management For IT Roadmap Four Quarter Pictures
Presenting our innovatively structured cyber security tactic for process management for it roadmap four quarter pictures Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
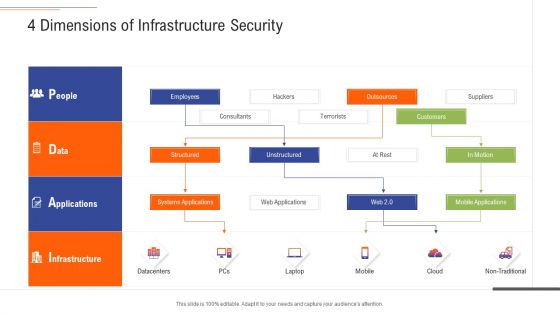
Support Services Management 4 Dimensions Of Infrastructure Security Ppt Slides Ideas PDF
This is a support services management 4 dimensions of infrastructure security ppt slides ideas pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like people, data, applications, infrastructure. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
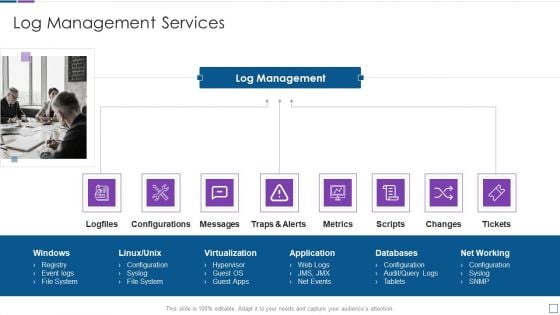
Real Time Assessment Of Security Threats Log Management Services Metrics Slides PDF
This is a real time assessment of security threats log management services metrics slides pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like configurations, log management, metrics, virtualization, databases. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
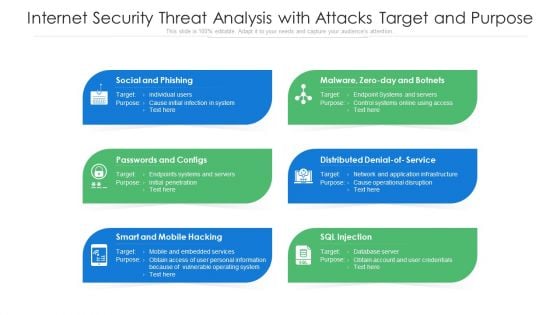
Internet Security Threat Analysis With Attacks Target And Purpose Ppt PowerPoint Presentation Pictures Structure PDF
Presenting internet security threat analysis with attacks target and purpose ppt powerpoint presentation pictures structure pdf to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including social and phishing, passwords and configs, smart and mobile hacking. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
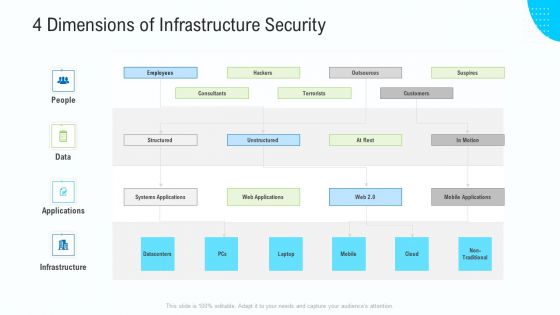
Business Activities Assessment Examples 4 Dimensions Of Infrastructure Security Professional PDF
Presenting business activities assessment examples 4 dimensions of infrastructure security professional pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like 30 60 90 days plan. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
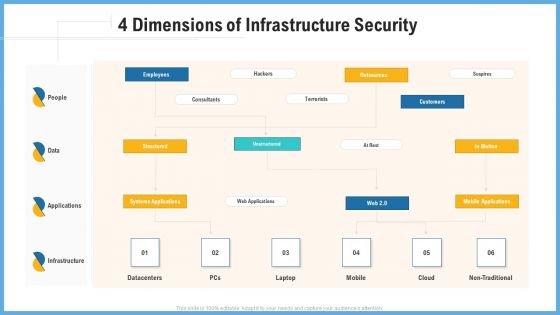
Improving Operational Activities Enterprise 4 Dimensions Of Infrastructure Security Slides PDF
This is a improving operational activities enterprise 4 dimensions of infrastructure security slides pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like 30 60 90 days plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
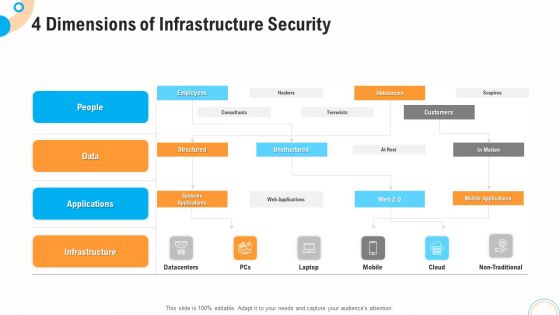
Fiscal And Operational Assessment 4 Dimensions Of Infrastructure Security Guidelines PDF
Presenting fiscal and operational assessment 4 dimensions of infrastructure security guidelines pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like 30 60 90 days plan. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
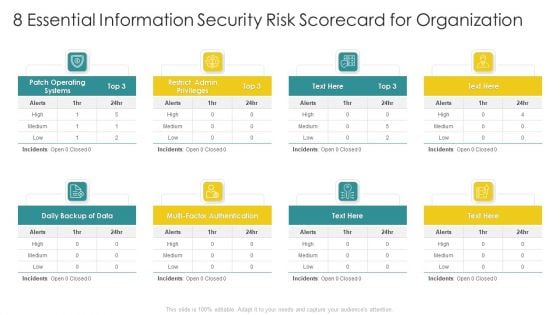
Cybersecurity Risk Scorecard 8 Essential Information Security Risk Scorecard For Organization Elements PDF
Presenting cybersecurity risk scorecard 8 essential information security risk scorecard for organization elements pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like 30 60 90 days plan. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
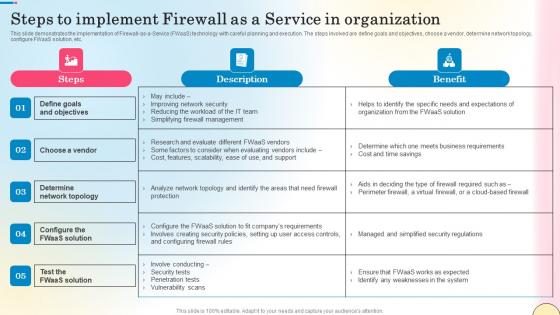
Steps To Implement Firewall As A Service In Organization Network Security Formats Pdf
This slide demonstrates the implementation of Firewall-as-a-Service FWaaS technology with careful planning and execution. The steps involved are define goals and objectives, choose a vendor, determine network topology, configure FWaaS solution, etc. Get a simple yet stunning designed Steps To Implement Firewall As A Service In Organization Network Security Formats Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Steps To Implement Firewall As A Service In Organization Network Security Formats Pdf can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide demonstrates the implementation of Firewall-as-a-Service FWaaS technology with careful planning and execution. The steps involved are define goals and objectives, choose a vendor, determine network topology, configure FWaaS solution, etc.
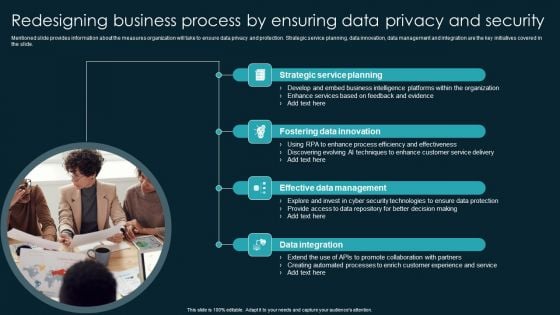
Redesigning Business Process By Ensuring Data Privacy And Security Infographics PDF
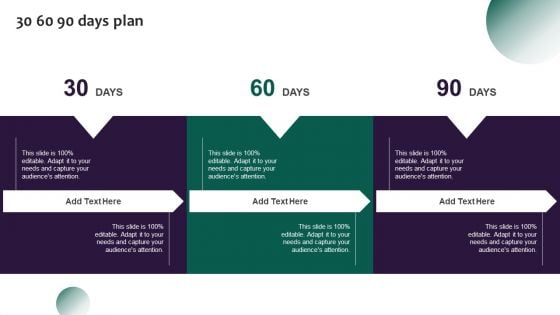
Information Systems Security And Risk Management Plan 30 60 90 Days Plan Information PDF
Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Information Systems Security And Risk Management Plan 30 60 90 Days Plan Information PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Facility Management 4 Dimensions Of Infrastructure Security Ppt File Layout PDF
This is a facility management 4 dimensions of infrastructure security ppt file layout pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like people, data, applications, infrastructure. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
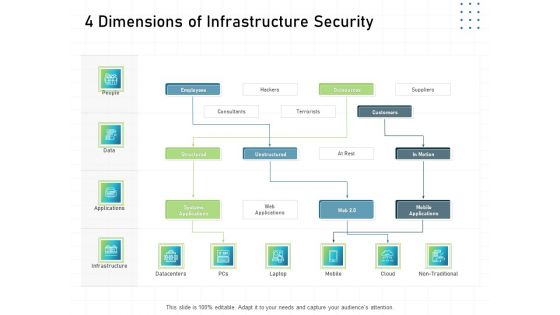
IT Infrastructure Administration 4 Dimensions Of Infrastructure Security Ppt Model Example Topics PDF
This is a it infrastructure administration 4 dimensions of infrastructure security ppt model example topics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like people, data, applications, infrastructure. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
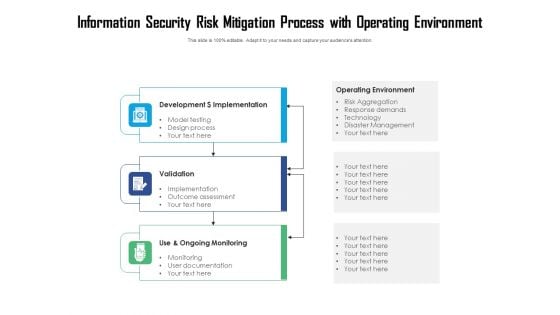
Information Security Risk Mitigation Process With Operating Environment Ppt PowerPoint Presentation File Templates PDF
Persuade your audience using this information security risk mitigation process with operating environment ppt powerpoint presentation file templates pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including development dollar implementation, validation, use and ongoing monitoring. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
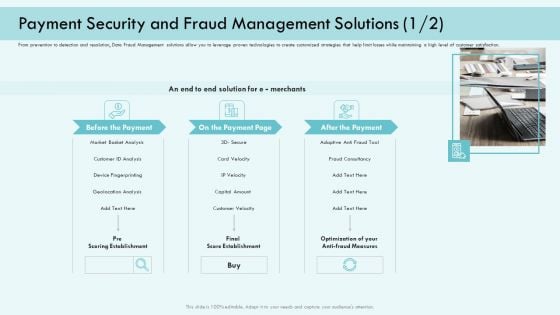
E Payment Transaction System Payment Security And Fraud Management Solutions Analysis Infographics PDF
Presenting E payment transaction system payment security and fraud management solutions analysis infographics pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like market basket analysis, device fingerprinting, customer velocity, optimization of your anti fraud measures. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

E Payment Transaction System Payment Security And Fraud Management Solutions Development Professional PDF
This is a E payment transaction system payment security and fraud management solutions development professional pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like recognizing users and streamlining the payments process with zero added friction, operational costs, software development. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
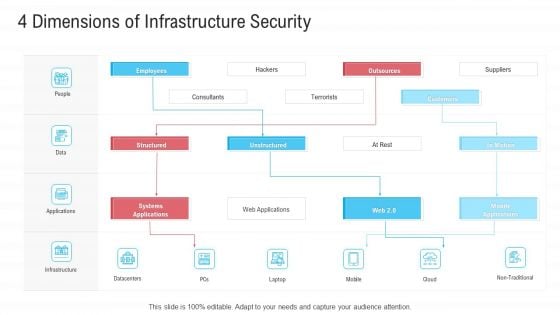
Infrastructure Designing And Administration 4 Dimensions Of Infrastructure Security Pictures PDF
This is a infrastructure designing and administration 4 dimensions of infrastructure security pictures pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like people, data, applications, infrastructure. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
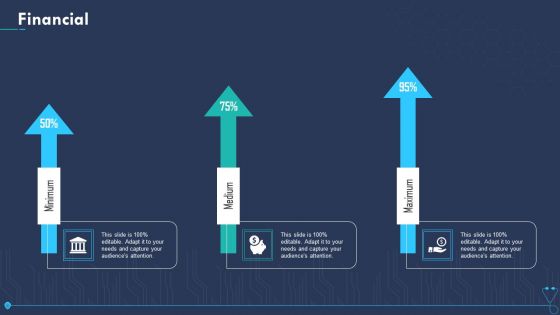
Case Competition Overpower The Obstacle Of Cyber Security In Medicare Financial Elements PDF
Presenting case competition overpower the obstacle of cyber security in medicare financial elements pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like minimum, medium, maximum. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Case Competition Overpower The Obstacle Of Cyber Security In Medicare Post It Sample PDF
Presenting case competition overpower the obstacle of cyber security in medicare post it sample pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like post it. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
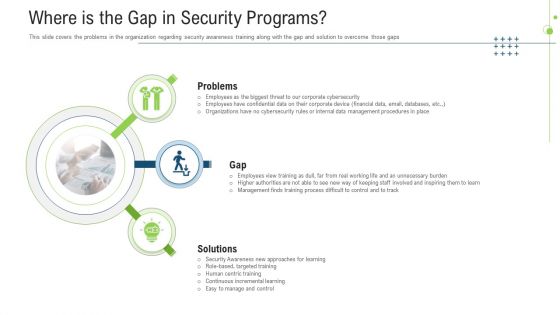
Where Is The Gap In Security Programs Ppt File Examples PDF
This is a where is the gap in security programs ppt file examples pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like problems, gap, solutions. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
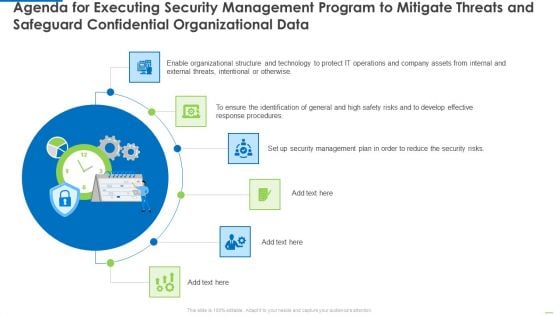
Agenda For Executing Security Management Program To Mitigate Threats And Safeguard Confidential Organizational Data Clipart PDF
Presenting Agenda for executing security management program to mitigate threats and safeguard confidential organizational data clipart pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like effective response procedures, intentional or otherwise, enable organizational. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Post It Notes Cloud Computing Security IT Ppt Portfolio Graphics Example PDF
This is a post it notes cloud computing security it ppt portfolio graphics example pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like post it notes. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
30 60 90 Days IT Security IT Ppt Show Portrait PDF
This is a 30 60 90 days it security it ppt show portrait pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like 30 60 90 days. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Post It Notes IT Security IT Ppt Icon Infographic Template PDF
This is a post it notes it security it ppt icon infographic template pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like post it notes. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Financing Catalogue For Security Underwriting Agreement Post It Notes Sample PDF
This is a financing catalogue for security underwriting agreement post it notes sample pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like post it notes. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Financing Catalogue For Security Underwriting Agreement Table Of Contents Mockup PDF
Presenting financing catalogue for security underwriting agreement table of contents mockup pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like company overview, market overview, deal overview. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Table Of Contents Cyber Security Administration In Organization Assets Background PDF
Presenting table of contents cyber security administration in organization assets background pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like handling, assets, digital, workplace, violence. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.


 Continue with Email
Continue with Email

 Home
Home


































