Security

Methods Of Software Risk Assessment Ppt Powerpoint Guide
This is a methods of software risk assessment ppt powerpoint guide. This is a seven stage process. The stages in this process are risk management, risk assessment, risk identification, risk periodization, security requirements, external review, penetration testing.
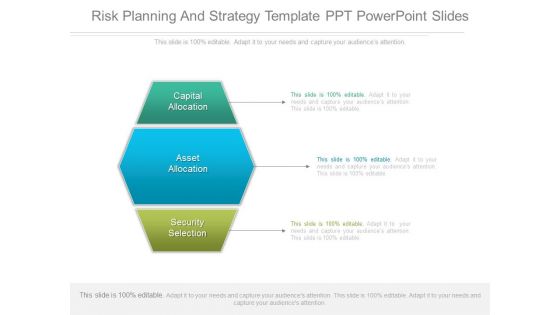
Risk Planning And Strategy Template Ppt Powerpoint Slides
This is a risk planning and strategy template ppt powerpoint slides. This is a three stage process. The stages in this process are capital allocation, asset allocation, security selection.
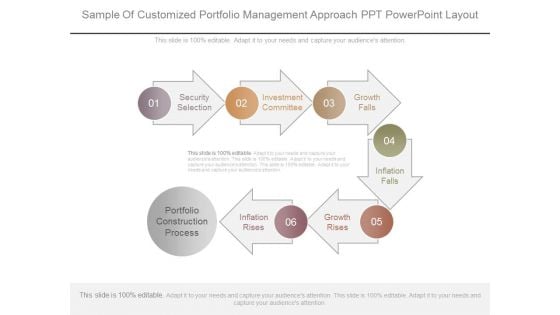
Sample Of Customized Portfolio Management Approach Ppt Powerpoint Layout
This is a sample of customized portfolio management approach ppt powerpoint layout. This is a six stage process. The stages in this process are security selection, investment committee, growth falls, portfolio construction process, inflation rises, growth rises, inflation falls.
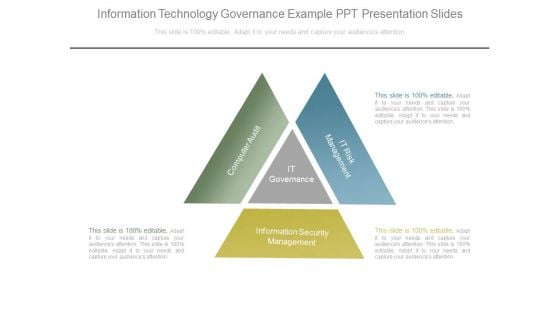
Information Technology Governance Example Ppt Presentation Slides
This is a information technology governance example ppt presentation slides. This is a three stage process. The stages in this process are computer audit, it governance, it risk management, information security management.

Market Opportunity Forecasts Example Presentation Visual Aids
This is a market opportunity forecasts example presentation visual aids. This is a eight stage process. The stages in this process are security audit, system integration, consoling training, solution architecture, analysis, account based intelligence, tools, models and forecasting.
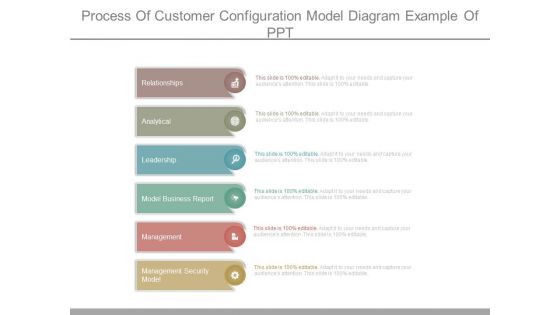
Process Of Customer Configuration Model Diagram Example Of Ppt
This is a process of customer configuration model diagram example of ppt. This is a six stage process. The stages in this process are relationships, analytical, leadership, model business report, management, management security model.
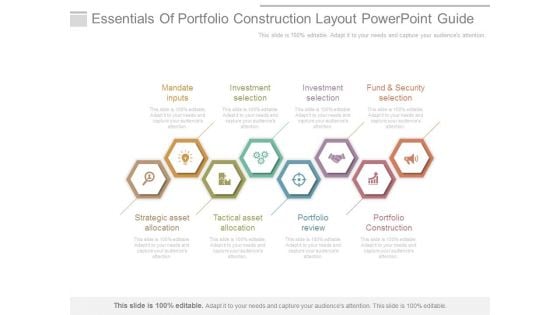
Essentials Of Portfolio Construction Layout Powerpoint Guide
This is a essentials of portfolio construction layout powerpoint guide. This is a eight stage process. The stages in this process are mandate inputs, investment selection, fund and security selection, strategic asset allocation, tactical asset allocation, portfolio review, portfolio construction.
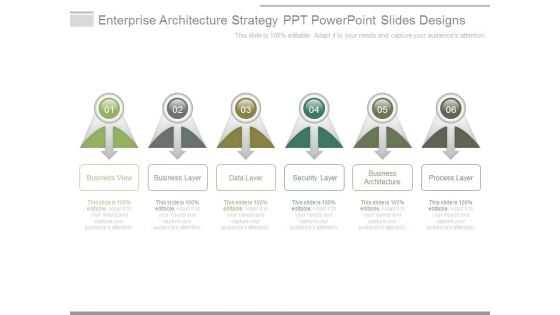
Enterprise Architecture Strategy Ppt Powerpoint Slides Designs
This is a enterprise architecture strategy ppt powerpoint slides designs. This is a six stage process. The stages in this process are business view, business layer, data layer, security layer, business architecture, process layer.
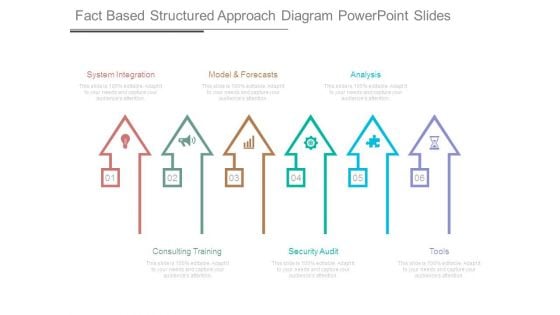
Fact Based Structured Approach Diagram Powerpoint Slides
This is a fact based structured approach diagram powerpoint slides. This is a six stage process. The stages in this process are system integration, model and forecasts, analysis, consulting training, security audit, tools.
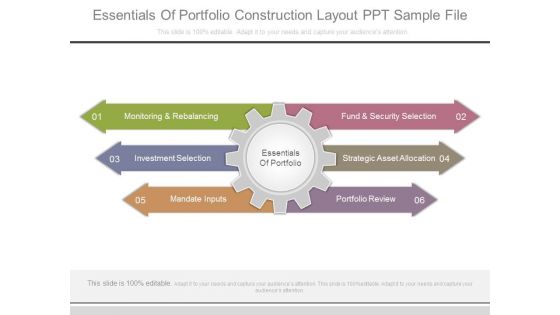
Essentials Of Portfolio Construction Layout Ppt Sample File
This is a essentials of portfolio construction layout ppt sample file. This is a six stage process. The stages in this process are monitoring and rebalancing, investment selection, mandate inputs, fund and security selection, strategic asset allocation, portfolio review.

Cyber Management Template Presentation Background Images
This is a cyber management template presentation background images. This is a six stage process. The stages in this process are risk review, policy, audit, cyber security life cycle, implementation, administration.
Portfolio Administration Plan Layout Powerpoint Slide Background Designs
This is a portfolio administration plan layout powerpoint slide background designs. This is a six stage process. The stages in this process are customer value, competitor analysis, strategy action, market analysis, asset management, security selection.
Connecting Link Process For Start Up Ppt PowerPoint Presentation Summary
This is a connecting link process for start up ppt powerpoint presentation summary. This is a five stage process. The stages in this process are computer configuration, windows settings, security settings, local policies, audit policy.
Audit System Measures Ppt PowerPoint Presentation Example 2015
This is a audit system measures ppt powerpoint presentation example 2015. This is a five stage process. The stages in this process are computer configuration, windows settings, security settings, local policies, audit policy.
Five Stage Audit System Events Ppt PowerPoint Presentation Good
This is a five stage audit system events ppt powerpoint presentation good. This is a five stage process. The stages in this process are computer configuration, windows settings, security settings, local policies, audit policy.
Steps To Track Audit System Events Ppt PowerPoint Presentation Summary
This is a steps to track audit system events ppt powerpoint presentation summary. This is a five stage process. The stages in this process are computer configuration, windows settings, security settings, local policies, audit policy.

Key Measures For Audit System Events Ppt PowerPoint Presentation Example
This is a key measures for audit system events ppt powerpoint presentation example. This is a five stage process. The stages in this process are windows settings, local policies, audit, policy, security settings, computer configuration.
Audit System Events Ppt PowerPoint Presentation Model
This is a audit system events ppt powerpoint presentation model. This is a five stage process. The stages in this process are computer configuration, windows settings , security settings , local policies, audit policy.
Audit System Events Ppt PowerPoint Presentation Tips
This is a audit system events ppt powerpoint presentation tips. This is a five stage process. The stages in this process are windows settings, local policies, computer configuration, security settings, audit policy.
Audit System Events Ppt PowerPoint Presentation Ideas
This is a audit system events ppt powerpoint presentation ideas. This is a five stage process. The stages in this process are computer configuration, windows settings, security settings, local policies, audit policy.
Audit System Events Ppt PowerPoint Presentation Visual Aids Infographics
This is a audit system events ppt powerpoint presentation visual aids infographics. This is a five stage process. The stages in this process are windows settings, security settings, local policies.
Audit System Events Ppt PowerPoint Presentation Professional Display
This is a audit system events ppt powerpoint presentation professional display. This is a five stage process. The stages in this process are computer configuration, windows settings, security settings, local policies, audit policy.

General Corporate Matters Ppt PowerPoint Presentation Infographics Slideshow
This is a general corporate matters ppt powerpoint presentation infographics slideshow. This is a four stage process. The stages in this process are point, lists of all security holders, list of current officers and directors.
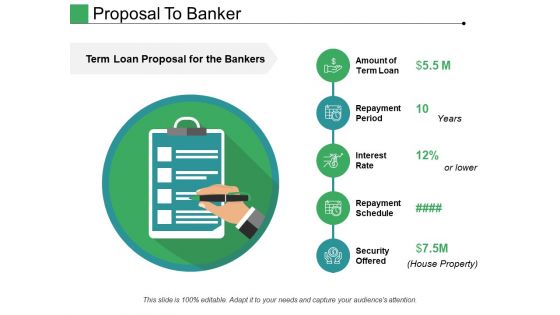
Proposal To Banker Ppt PowerPoint Presentation Layouts Display
This is a proposal to banker ppt powerpoint presentation layouts display. This is a five stage process. The stages in this process are repayment period, interest rate, repayment schedule, security offered.
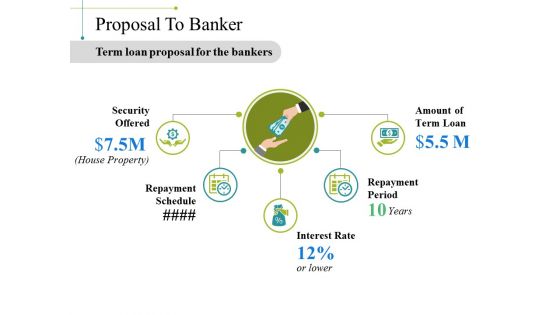
Proposal To Banker Ppt PowerPoint Presentation Outline Grid
This is a proposal to banker ppt powerpoint presentation outline grid. This is a five stage process. The stages in this process are security offered, repayment schedule, interest rate, repayment period, amount of term loan.

Proposal To Banker Ppt PowerPoint Presentation Sample
This is a proposal to banker ppt powerpoint presentation sample. This is a five stage process. The stages in this process are amount of term loan, repayment period, interest rate, security offered, repayment, schedule.
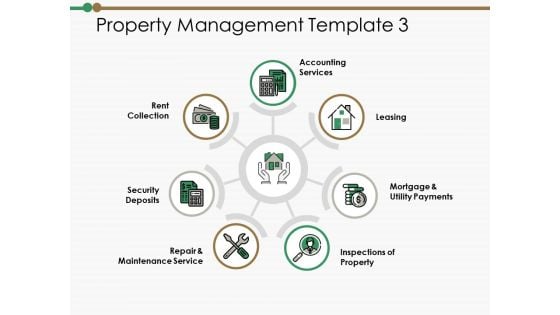
Property Management Template Ppt PowerPoint Presentation Styles Designs
This is a property management template ppt powerpoint presentation styles designs. This is a seven stage process. The stages in this process are rent collection, security deposits, inspections of property.

Page Experience Signals In Google Search Console Training Ppt
This slide covers search signals for page experience largely known as core web vitals. It also includes KPIs such as mobile-friendly experience, safe browsing experience, HTTPS security and no intrusive interstitials.
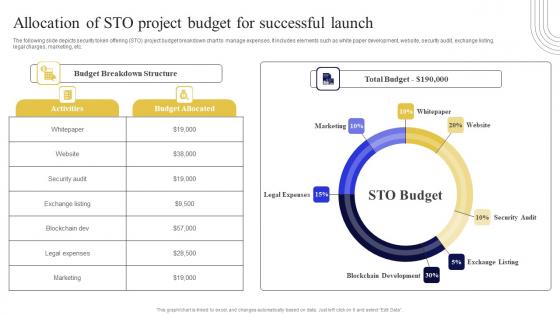
Allocation Of STO Project Budget For Exploring Investment Opportunities Demonstration Pdf
The following slide depicts security token offering STO project budget breakdown chart to manage expenses. It includes elements such as white paper development, website, security audit, exchange listing, legal charges, marketing, etc. Create an editable Allocation Of STO Project Budget For Exploring Investment Opportunities Demonstration Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Allocation Of STO Project Budget For Exploring Investment Opportunities Demonstration Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. The following slide depicts security token offering STO project budget breakdown chart to manage expenses. It includes elements such as white paper development, website, security audit, exchange listing, legal charges, marketing, etc.
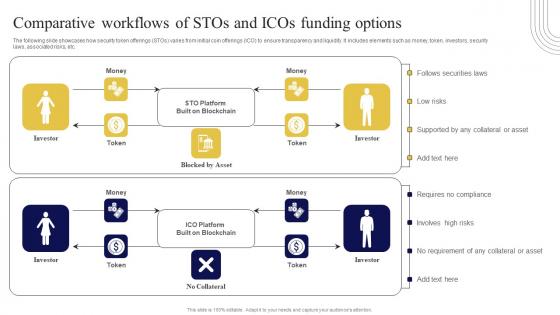
Comparative Workflows Of Stos And Icos Exploring Investment Opportunities Professional Pdf
The following slide showcases how security token offerings STOs varies from initial coin offerings ICO to ensure transparency and liquidity. It includes elements such as money, token, investors, security laws, associated risks, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Comparative Workflows Of Stos And Icos Exploring Investment Opportunities Professional Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Comparative Workflows Of Stos And Icos Exploring Investment Opportunities Professional Pdf today and make your presentation stand out from the rest The following slide showcases how security token offerings STOs varies from initial coin offerings ICO to ensure transparency and liquidity. It includes elements such as money, token, investors, security laws, associated risks, etc.
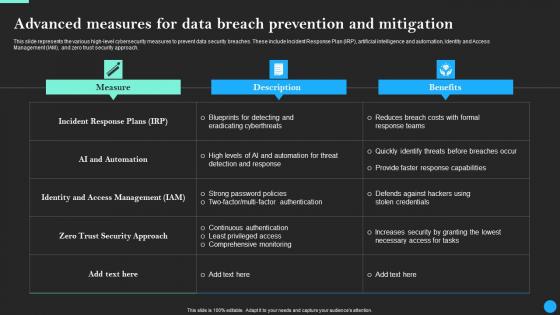
Advanced Measures For Data Breach Prevention Data Breach Prevention Inspiration Pdf
This slide represents the various high-level cybersecurity measures to prevent data security breaches. These include Incident Response Plan IRP, artificial intelligence and automation, Identity and Access Management IAM, and zero trust security approach. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Advanced Measures For Data Breach Prevention Data Breach Prevention Inspiration Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide represents the various high-level cybersecurity measures to prevent data security breaches. These include Incident Response Plan IRP, artificial intelligence and automation, Identity and Access Management IAM, and zero trust security approach.

Web Consulting Business Cybersecurity Issues Overview And Key Statistics
Mentioned slide provides introduction about cyber security issues. It includes key elements such as description, types of security issue, key facts, and negative impact on business. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Web Consulting Business Cybersecurity Issues Overview And Key Statistics to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. Mentioned slide provides introduction about cyber security issues. It includes key elements such as description, types of security issue, key facts, and negative impact on business.
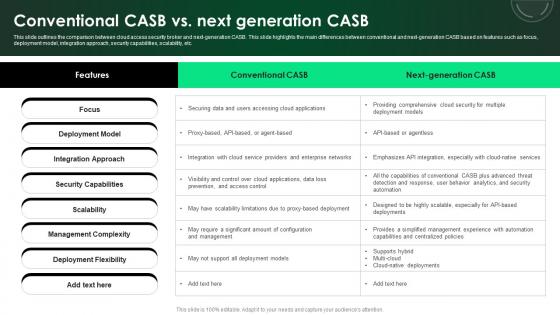
CASB 2 0 IT Conventional CASB Vs Next Generation CASB
This slide outlines the comparison between cloud access security broker and next-generation CASB. This slide highlights the main differences between conventional and next-generation CASB based on features such as focus, deployment model, integration approach, security capabilities, scalability, etc. Find a pre-designed and impeccable CASB 2 0 IT Conventional CASB Vs Next Generation CASB. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide outlines the comparison between cloud access security broker and next-generation CASB. This slide highlights the main differences between conventional and next-generation CASB based on features such as focus, deployment model, integration approach, security capabilities, scalability, etc.

Managing Technical And Non Cybersecurity Issues Overview And Key Statistics
Mentioned slide provides introduction about cyber security issues. It includes key elements such as description, types of security issue, key facts, and negative impact on business. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Managing Technical And Non Cybersecurity Issues Overview And Key Statistics was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Managing Technical And Non Cybersecurity Issues Overview And Key Statistics. Mentioned slide provides introduction about cyber security issues. It includes key elements such as description, types of security issue, key facts, and negative impact on business.

Comprehensive Guide For Website Cybersecurity Issues Overview And Key Statistics
Mentioned slide provides introduction about cyber security issues. It includes key elements such as description, types of security issue, key facts, and negative impact on business. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Comprehensive Guide For Website Cybersecurity Issues Overview And Key Statistics to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. Mentioned slide provides introduction about cyber security issues. It includes key elements such as description, types of security issue, key facts, and negative impact on business.
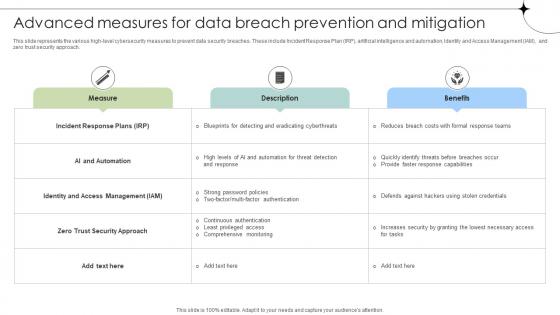
Advanced Measures For Data Breach Prevention And Mitigation Data Fortification Strengthening Defenses
This slide represents the various high-level cybersecurity measures to prevent data security breaches. These include Incident Response Plan IRP, artificial intelligence and automation, Identity and Access Management IAM, and zero trust security approach.Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Advanced Measures For Data Breach Prevention And Mitigation Data Fortification Strengthening Defenses for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide represents the various high-level cybersecurity measures to prevent data security breaches. These include Incident Response Plan IRP, artificial intelligence and automation, Identity and Access Management IAM, and zero trust security approach.

Challenges With Devsecops Implementation And Solutions Role Of Devsecops Ppt Powerpoint
This slide explain the various limitations with DevSecOps and its solution. The purpose of this slide is to discuss the solutions provided to different challenges associated with DevSecOps. These include late sage security integration, tool integration and complexity, security awareness and training, etc. There are so many reasons you need a Challenges With Devsecops Implementation And Solutions Role Of Devsecops Ppt Powerpoint The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide explain the various limitations with DevSecOps and its solution. The purpose of this slide is to discuss the solutions provided to different challenges associated with DevSecOps. These include late sage security integration, tool integration and complexity, security awareness and training, etc.
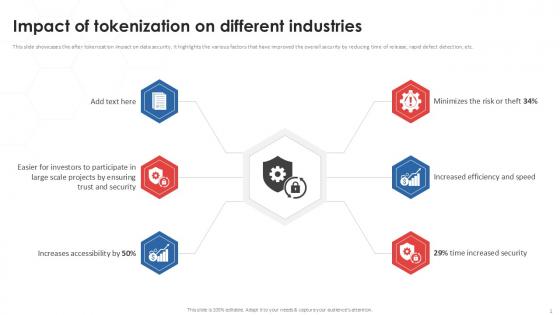
Impact Of Tokenization On Different Industries PPT Template
This slide showcases the after tokenization impact on data security. It highlights the various factors that have improved the overall security by reducing time of release, rapid defect detection, etc. Find a pre-designed and impeccable Impact Of Tokenization On Different Industries PPT Template. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide showcases the after tokenization impact on data security. It highlights the various factors that have improved the overall security by reducing time of release, rapid defect detection, etc.
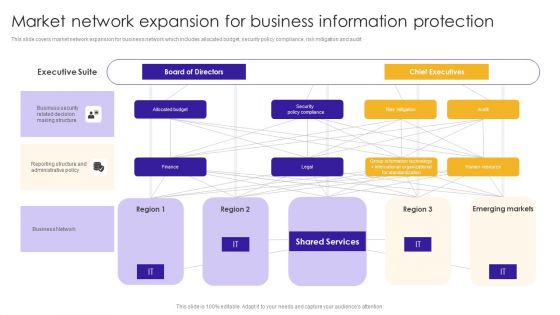
Market Network Expansion For Business Information Protection Sample PDF
This slide covers market network expansion for business network which includes allocated budget, security policy compliance, risk mitigation and audit. Showcasing this set of slides titled Market Network Expansion For Business Information Protection Sample PDF. The topics addressed in these templates are Business Security, Related Decision, Making Structure. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
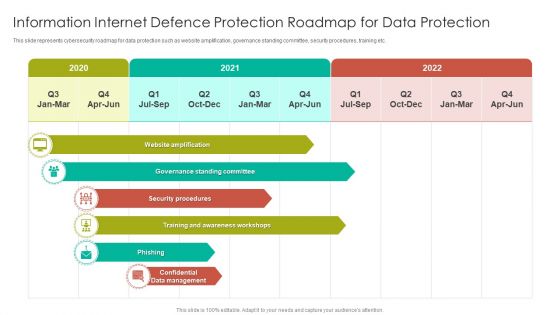
Information Internet Defence Protection Roadmap For Data Protection Topics PDF
This slide represents cybersecurity roadmap for data protection such as website amplification, governance standing committee, security procedures, training etc. Showcasing this set of slides titled Information Internet Defence Protection Roadmap For Data Protection Topics PDF. The topics addressed in these templates are Governance Standing, Security Procedures, Awareness Workshops. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting
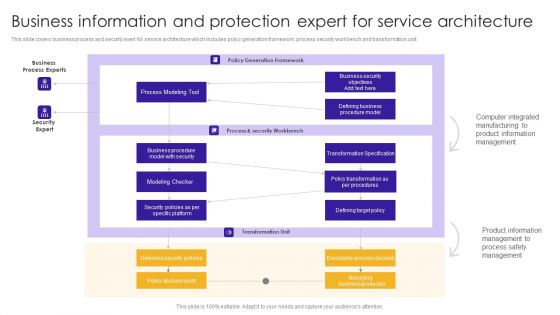
Business Information And Protection Expert For Service Architecture Demonstration PDF
This slide covers business process and security exert for service architecture which includes policy generation framework, process security workbench and transformation unit.Showcasing this set of slides titled Business Information And Protection Expert For Service Architecture Demonstration PDF. The topics addressed in these templates are Business Process, Computer Integrated, Product Information. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
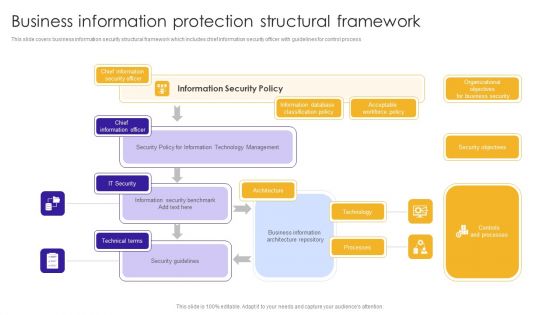
Business Information Protection Structural Framework Summary PDF
This slide covers business information security structural framework which includes chief information security officer with guidelines for control process.Showcasing this set of slides titled Business Information Protection Structural Framework Summary PDF. The topics addressed in these templates are Information Database, Classification Policy, Architecture Repository. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
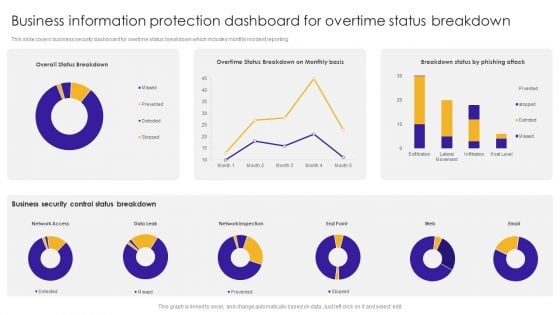
Business Information Protection Dashboard For Overtime Status Breakdown Introduction PDF
This slide covers business security dashboard for overtime status breakdown which includes monthly incident reporting.Pitch your topic with ease and precision using this Business Information Protection Dashboard For Overtime Status Breakdown Introduction PDF. This layout presents information on Business Security, Control Status Breakdown, Network Inspection. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
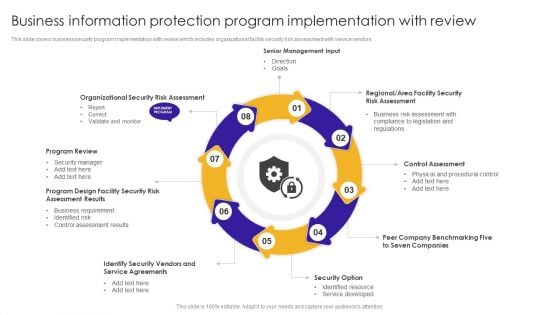
Business Information Protection Program Implementation With Review Information PDF
This slide covers business security program implementation with review which includes organizational facility security risk assessment with service vendors.Persuade your audience using this Business Information Protection Program Implementation With Review Information PDF. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including Program Review, Assessment Results, Business Requirement. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Cyber Protection And Precaution Tracking Dashboard Designs PDF
This slide shows the dashboard of cyber safety and security of an organization. It includes risk level, compliance status, tracking and security budget. Showcasing this set of slides titled Cyber Protection And Precaution Tracking Dashboard Designs PDF. The topics addressed in these templates are Risk, Compliance Status, Risk Level. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
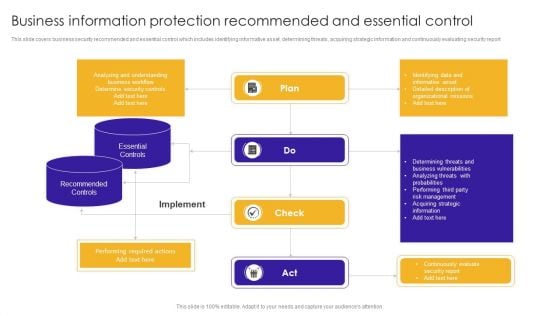
Business Information Protection Recommended And Essential Control Background PDF
This slide covers business security recommended and essential control which includes identifying informative asset, determining threats, acquiring strategic information and continuously evaluating security report. Showcasing this set of slides titled Business Information Protection Recommended And Essential Control Background PDF. The topics addressed in these templates are Determining Threats, Business Vulnerabilities, Risk Management. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
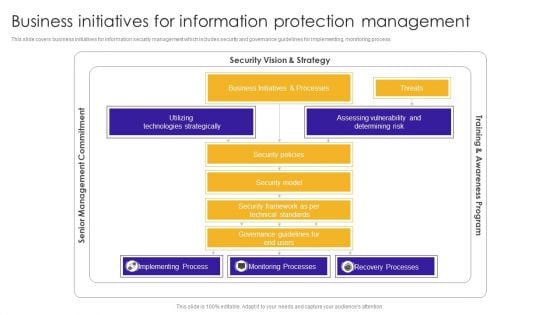
Business Initiatives For Information Protection Management Designs PDF
This slide covers business initiatives for information security management which includes security and governance guidelines for implementing, monitoring process. Pitch your topic with ease and precision using this Business Initiatives For Information Protection Management Designs PDF. This layout presents information on Technologies Strategically, Assessing Vulnerability, Implementing Process. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
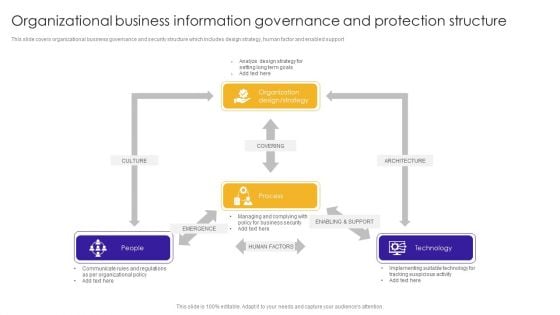
Organizational Business Information Governance And Protection Structure Guidelines PDF
This slide covers organizational business governance and security structure which includes design strategy, human factor and enabled support. Showcasing this set of slides titled Organizational Business Information Governance And Protection Structure Guidelines PDF. The topics addressed in these templates are Communicate Rules, Organizational Policy, Business Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Agenda Of Enhancing Cyber Safety With Vulnerability Administratio Professional PDF
This is a agenda of enhancing cyber safety with vulnerability administratio professional pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security intelligence, log management and compliance, provides security services. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

1 Computers Behind A Firewall Connected To A Centralized Server Ppt Slides
This image slide displays computer behind a firewall connected to a centralized server. This image slide has been crafted with graphic of laptops, server and firewall icon connected. This image slide depicts security in networking. You may change size, color and orientation of any icon to your liking. Use this PowerPoint template, in your presentations to explain concepts technology, networking and security. This image slide will enhance the quality of your presentations.

Digitized Record Book Technology Pros And Cons Of Private Digital Ledger Download PDF
This slide represents the Pros and cons of the private blockchain framework based on factors such as speed, flexibility, trust-building, and security. Deliver an awe inspiring pitch with this creative digitized record book technology pros and cons of private digital ledger download pdf bundle. Topics like network, organization, data, lower security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
1 Icon Of A Firewall To Separate The Internal Network From The External World Ppt Slides
This image slide displays icon of firewall. This image slide has been crafted with graphic of firewall icon to separate internal network from the external world. This image slide depicts security on network. You may change size, color and orientation of any icon to your liking. Use this PowerPoint template, in your presentations to explain concepts like networking and security. This image slide will enhance the quality of your presentations.
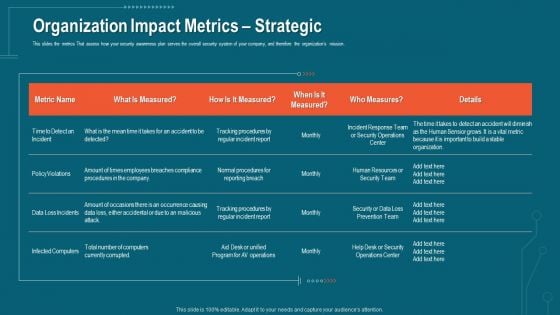
Companys Data Safety Recognition Organization Impact Metrics Strategic Topics PDF
This slides the metrics That assess how your security awareness plan serves the overall security system of your company, and therefore the organizations mission. Deliver an awe-inspiring pitch with this creative companys data safety recognition organization impact metrics strategic topics pdf bundle. Topics like organization impact metrics strategic can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
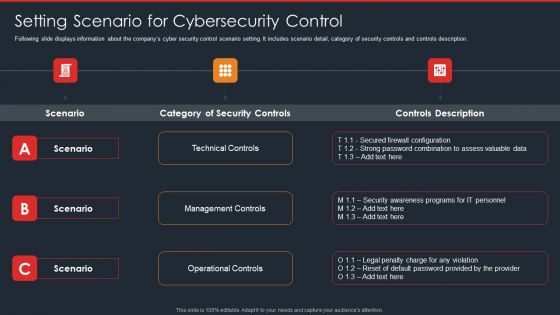
Data Safety Initiatives Setting Scenario For Cybersecurity Control Inspiration PDF
Following slide displays information about the companys cyber security control scenario setting. It includes scenario detail, category of security controls and controls description. Deliver an awe inspiring pitch with this creative data safety initiatives setting scenario for cybersecurity control inspiration pdf bundle. Topics like scenario, technical controls, management controls, operational controls can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
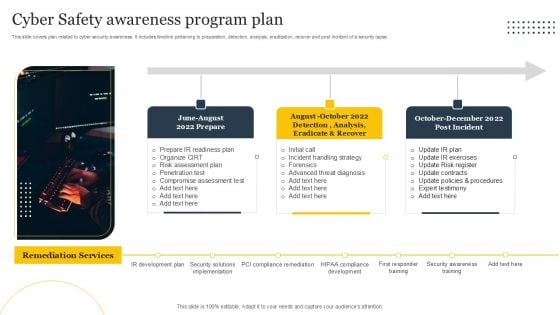
Cyber Safety Awareness Program Plan Ppt Icon Smartart PDF
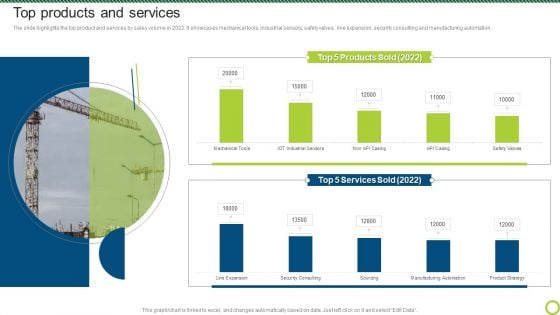
Engineering Solutions Company Detail Top Products And Services Portrait PDF
The slide highlights the top product and services by sales volume in 2022. It showcases mechanical tools, industrial sensors, safety valves, line expansion, security consulting and manufacturing automation.Deliver an awe inspiring pitch with this creative Engineering Solutions Company Detail Top Products And Services Portrait PDF bundle. Topics like Services Sold, Products Sold, Security Consulting can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
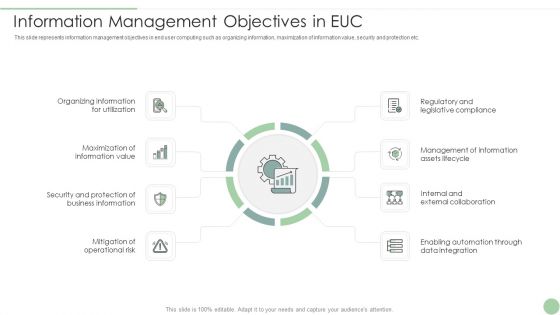
Information Management Objectives In EUC Ppt PowerPoint Presentation File Visuals PDF
This slide represents information management objectives in end user computing such as organizing information, maximization of information value, security and protection etc. Presenting Information Management Objectives In EUC Ppt PowerPoint Presentation File Visuals PDF to dispense important information. This template comprises eight stages. It also presents valuable insights into the topics including Organizing Information Utilization, Security And Protection, Business Information. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
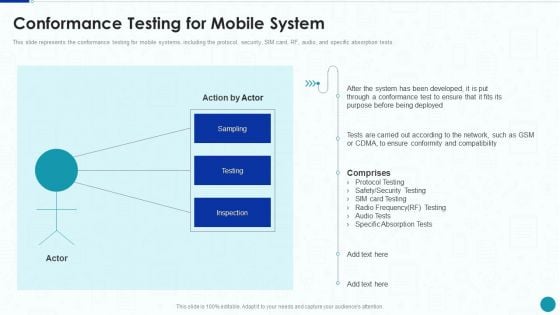
Compliance Testing IT Conformance Testing For Mobile System Microsoft PDF
This slide represents the conformance testing for mobile systems, including the protocol, security, SIM card, RF, audio, and specific absorption tests. Deliver an awe inspiring pitch with this creative Compliance Testing IT Conformance Testing For Mobile System Microsoft PDF bundle. Topics like Network, System, Security Testing can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Nuclear Power Plants Safety Regulations With Icon Ppt PowerPoint Presentation Gallery Infographic Template PDF
Persuade your audience using this nuclear power plants safety regulations with icon ppt powerpoint presentation gallery infographic template pdf. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including effective security, measuring, security plan. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
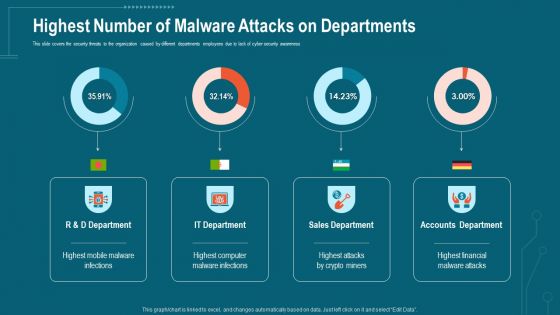
Companys Data Safety Recognition Highest Number Of Malware Attacks On Departments Sample PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Deliver an awe-inspiring pitch with this creative companys data safety recognition highest number of malware attacks on departments sample pdf bundle. Topics like sales department, accounts department, it department can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.


 Continue with Email
Continue with Email

 Home
Home


































