Security
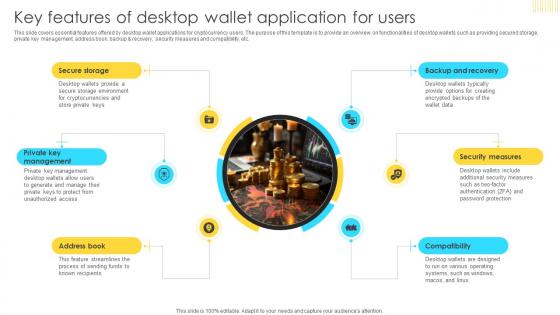
Mastering Blockchain Wallets Key Features Of Desktop Wallet Application BCT SS V
This slide covers essential features offered by desktop wallet applications for cryptocurrency users. The purpose of this template is to provide an overview on functionalities of desktop wallets such as providing secured storage, private key management, address book, backup and recovery, security measures and compatibility, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Mastering Blockchain Wallets Key Features Of Desktop Wallet Application BCT SS V a try. Our experts have put a lot of knowledge and effort into creating this impeccable Mastering Blockchain Wallets Key Features Of Desktop Wallet Application BCT SS V. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide covers essential features offered by desktop wallet applications for cryptocurrency users. The purpose of this template is to provide an overview on functionalities of desktop wallets such as providing secured storage, private key management, address book, backup and recovery, security measures and compatibility, etc.

Timeline To Implement Devsecops Process In Organization Role Of Devsecops Ppt Example
This slide shows the timeline for implementing the DevSecOps process. The key steps include defining the project objective, identifying key stakeholders, sharing basic guidelines on secure coding, basic compliance checks, regularly reviewing and updating security tools, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Timeline To Implement Devsecops Process In Organization Role Of Devsecops Ppt Example With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Timeline To Implement Devsecops Process In Organization Role Of Devsecops Ppt Example today and make your presentation stand out from the rest This slide shows the timeline for implementing the DevSecOps process. The key steps include defining the project objective, identifying key stakeholders, sharing basic guidelines on secure coding, basic compliance checks, regularly reviewing and updating security tools, etc.
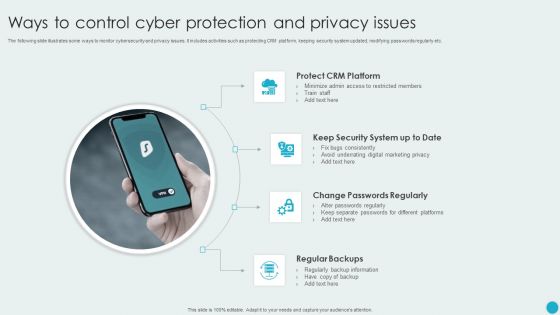
Ways To Control Cyber Protection And Privacy Issues Diagrams PDF
The following slide illustrates some ways to monitor cybersecurity and privacy issues. It includes activities such as protecting CRM platform, keeping security system updated, modifying passwords regularly etc. Persuade your audience using this Ways To Control Cyber Protection And Privacy Issues Diagrams PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Change Passwords Regularly, Regular Backups, Protect CRM Platform. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Information Technology Protection And Privacy Roadmap Sample PDF
The following slide showcases IT security and privacy roadmap to protect digital information from severe threats. It includes elements such as assess, build, select, deploy, train and test. Persuade your audience using this Information Technology Protection And Privacy Roadmap Sample PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Deploy, Build, Select, Train. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
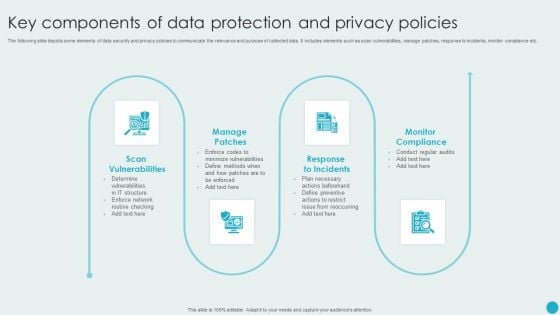
Key Components Of Data Protection And Privacy Policies Graphics PDF
The following slide depicts some elements of data security and privacy policies to communicate the relevance and purpose of collected data. It includes elements such as scan vulnerabilities, manage patches, response to incidents, monitor compliance etc. Presenting Key Components Of Data Protection And Privacy Policies Graphics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Manage Patches, Response To Incidents, Monitor Compliance. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Technologies To Ensure Data Protection And Privacy Background PDF
The following slide showcases some technologies to administer organizational data privacy and security concerns. It includes elements such as data encryption, change management and auditing, user and behavior analytics UEBA, backup and recovery etc. Presenting Technologies To Ensure Data Protection And Privacy Background PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Data Encryption, Change Management And Auditing, Backup And Recovery. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Protection And Privacy Response Action Plan Graphics PDF
The following slide illustrates the series of steps to respond security incidents. It includes elements such as report, identify, declare, respond, remediate and close. Persuade your audience using this Protection And Privacy Response Action Plan Graphics PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Declare, Respond, Remediate, Identify. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
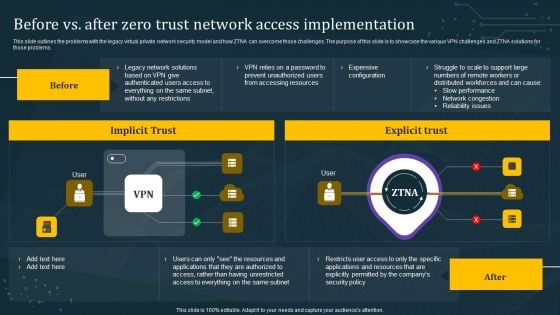
Before Vs After Zero Trust Network Access Implementation Background PDF
This slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Before Vs After Zero Trust Network Access Implementation Background PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Cyber Protection Incident And Privacy Analysis With KPI Dashboard Ideas PDF
The following slide highlights some kpas of cyber security incidents to evaluate and monitor threats. It includes elements such as open incidents, warnings by severity, average response time, warnings pending for inspection etc. Showcasing this set of slides titled Cyber Protection Incident And Privacy Analysis With KPI Dashboard Ideas PDF. The topics addressed in these templates are Cyber Protection Incident, Privacy Analysis, KPI Dashboard. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Major Reasons To Manage Online Protection And Privacy Issues Template PDF
The following slide highlights the major causes to administer digital security and privacy concerns. It includes activities such as setting credibility with users, optimizing social media presence, improving marketing efforts etc. Persuade your audience using this Major Reasons To Manage Online Protection And Privacy Issues Template PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Set Credibility With Users, Optimize Social Media Presence, To Reduce Damage Expenses. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Major Steps To Develop Protection And Precaution Strategy Themes PDF
This slide shows multi steps process to build safety and security strategy. These strategies are assess vulnerabilities, adopt safety measures, control access, alert authorities and audit procedures. Persuade your audience using this Major Steps To Develop Protection And Precaution Strategy Themes PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Assess Vulnerabilities, Adopt Safety Measures, Control Access. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
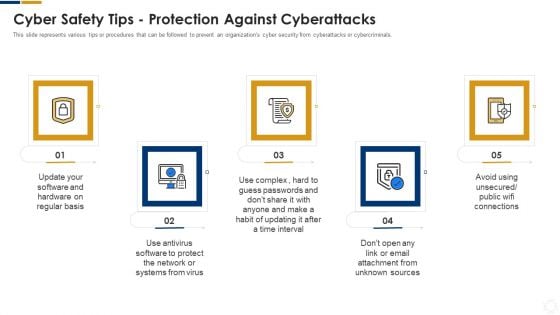
Cybersecurity Cyber Safety Tips Protection Against Cyberattacks Ppt Styles Gallery PDF
This slide represents various tips or procedures that can be followed to prevent an organizations cyber security from cyberattacks or cybercriminals. This is a cybersecurity cyber safety tips protection against cyberattacks ppt styles gallery pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like systems, network. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
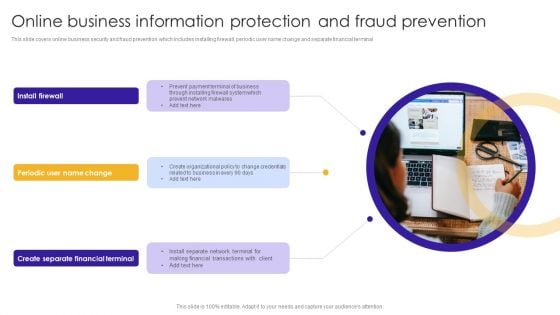
Online Business Information Protection And Fraud Prevention Topics PDF
This slide covers online business security and fraud prevention which includes installing firewall, periodic user name change and separate financial terminal. Persuade your audience using this Online Business Information Protection And Fraud Prevention Topics PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Create Separate, Financial Terminal, Prevent Network. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
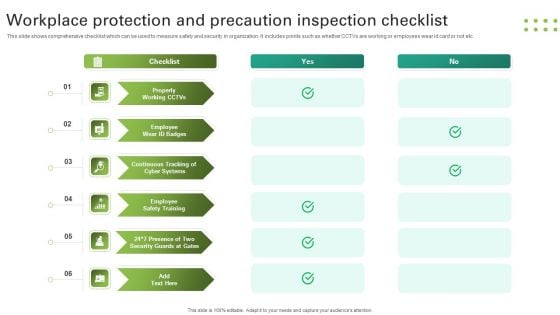
Workplace Protection And Precaution Inspection Checklist Clipart PDF
This slide shows comprehensive checklist which can be used to measure safety and security in organization. It includes points such as whether CCTVs are working or employees wear id card or not etc. Presenting Workplace Protection And Precaution Inspection Checklist Clipart PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Checklist, Properly Working Cctvs, Employee Wear Id Badges. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
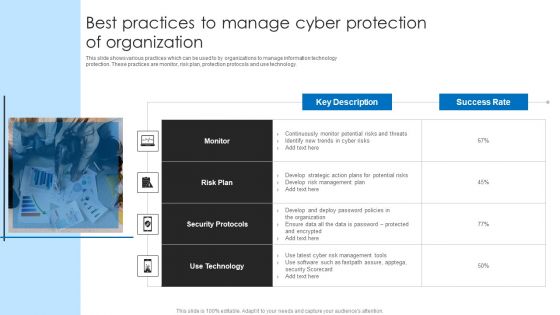
Best Practices To Manage Cyber Protection Of Organization Microsoft PDF
This slide shows various practices which can be used to by organizations to manage information technology protection. These practices are monitor, risk plan, protection protocols and use technology. Persuade your audience using this Best Practices To Manage Cyber Protection Of Organization Microsoft PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Risk Plan, Security Protocols, Technology. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
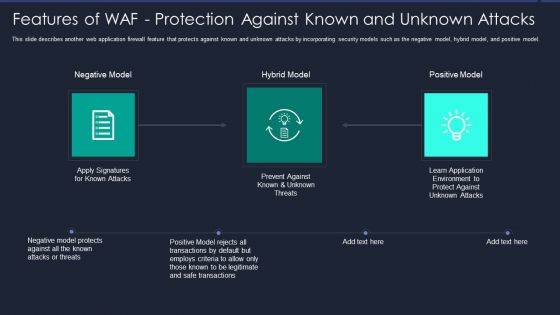
Web App Firewall Services IT Features Of WAF Protection Against Known Clipart PDF
This slide describes another web application firewall feature that protects against known and unknown attacks by incorporating security models such as the negative model, hybrid model, and positive model. Presenting web app firewall services it features of waf protection against known clipart pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like negative model, hybrid model, positive model. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
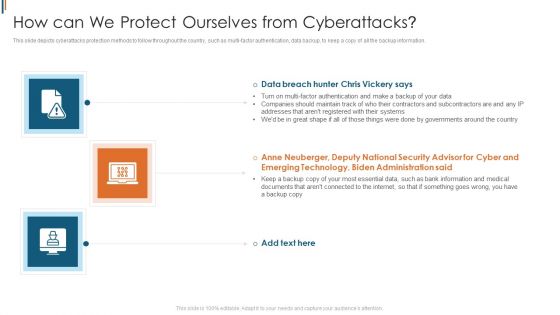
Ukraine Cyberwarfare How Can We Protect Ourselves From Cyberattacks Designs Pdf
This slide depicts cyberattacks protection methods to follow throughout the country, such as multi-factor authentication, data backup, to keep a copy of all the backup information. Presenting ukraine cyberwarfare how can we protect ourselves from cyberattacks designs pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like anne neuberger, deputy national security advisor for cyber and emerging technology, biden administration said. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Checklist To Ensure Asset Protection From Improving Cybersecurity With Incident Download PDF
Following slide displays checklist having security control measures that can be used by members to ensure the safety of companys assets from any insider threat.Present like a pro with Checklist To Ensure Asset Protection From Improving Cybersecurity With Incident Download PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Cyber Risks And Incident Response Playbook Checklist To Ensure Asset Protection From Internal Threats Structure PDF
Following slide displays checklist having security control measures that can be used by members to ensure the safety of companys assets from any insider threat. Present like a pro with Cyber Risks And Incident Response Playbook Checklist To Ensure Asset Protection From Internal Threats Structure PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether youre in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Cybersecurity Guidelines IT Internet Usage Policy Password Guidelines Download PDF
This slide talks about the password guidelines under the internet usage policy. It is further divided into three categories such as selection of a strong password, keeping the password safe, and other security measures. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Cybersecurity Guidelines IT Internet Usage Policy Password Guidelines Download PDF from Slidegeeks and deliver a wonderful presentation.

Features Of WAF Protection Against Known And Unknown Attacks WAF Platform Inspiration PDF
This slide describes another web application firewall feature that protects against known and unknown attacks by incorporating security models such as the negative model, hybrid model, and positive model. Presenting Features Of WAF Protection Against Known And Unknown Attacks WAF Platform Inspiration PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Hybrid Model, Negative Model, Positive Model. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Enhanced Protection Corporate Event Administration Budget For Effective Secops System Management Sample PDF
Firm has prepared the budget for managing security operational system management. It also provides information about the software used and the duration required for implementation. Deliver and pitch your topic in the best possible manner with this enhanced protection corporate event administration budget for effective secops system management sample pdf. Use them to share invaluable insights on functional area, software, implement duration, cost of implementation and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
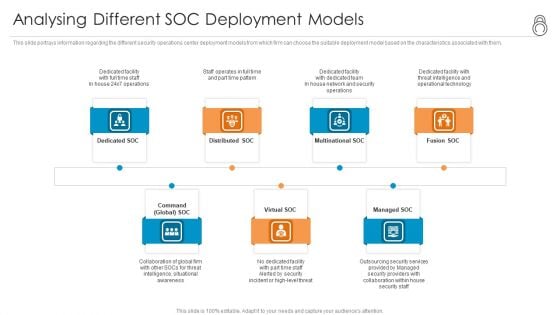
Enhanced Protection Corporate Event Administration Analysing Different SOC Deployment Models Information PDF
This slide portrays information regarding the different security operations center deployment models from which firm can choose the suitable deployment model based on the characteristics associated to the. This is a enhanced protection corporate event administration analysing different soc deployment models information pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like multinational soc, distributed soc, dedicated soc, command global soc, virtual soc. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
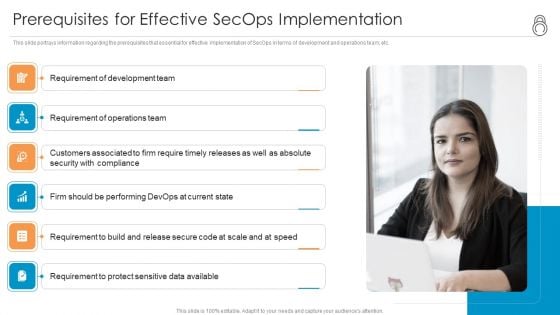
Enhanced Protection Corporate Event Administration Prerequisites For Effective Secops Implementation Inspiration PDF
This slide portrays information regarding the prerequisites that essential for effective implementation of SecOps in terms of development and operations team, etc. This is a enhanced protection corporate event administration prerequisites for effective secops implementation inspiration pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like development, data available, security with compliance, operations team. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cybersecurity Online Risk Assessment Process To Enhance Data Protection Introduction PDF
The purpose of this slide is to represent a process for cybersecurity digital risk assessment to analyze business threats. It includes various stages such as classifying information assets, evaluating risks, examining risk, observing and reviewing effectiveness and implementing security controls. Presenting Cybersecurity Online Risk Assessment Process To Enhance Data Protection Introduction PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Classify Information Assets, Evaluate Risk, Examine Risk. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Various Strategies To Ensure Food Safety Increased Superiority For Food Products Icons PDF
This slide provides information regarding various strategies used by firm in ensuring food safety in terms of streamlining global safety requirements, digitalization of food, food safety network. This is a various strategies to ensure food safety increased superiority for food products icons pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like streamlining global safety requirements, digitalization of food security or safety data, building food safety network. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Zero Trust Network Access Performance Tracking Dashboard Template PDF
This slide represents the performance tracking dashboard for zero trust network access. The purpose of this slide is to showcase the level of request modes, connected users, daily usage of the network, security rating, device risk and threat flow. Find a pre-designed and impeccable Zero Trust Network Access Performance Tracking Dashboard Template PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
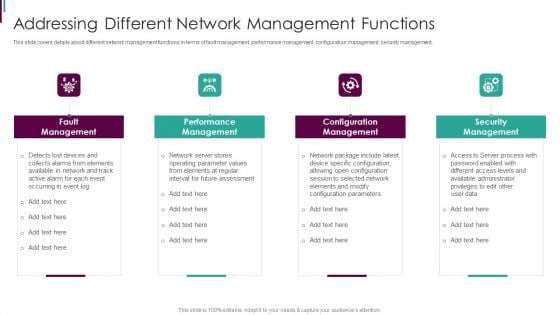
Developing Business Analytics Framework Addressing Different Network Information PDF
This slide covers details about different network management functions in terms of fault management, performance management, configuration management, security management. This is a Developing Business Analytics Framework Addressing Different Network Information PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Fault Management , Performance Management, Configuration Management You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
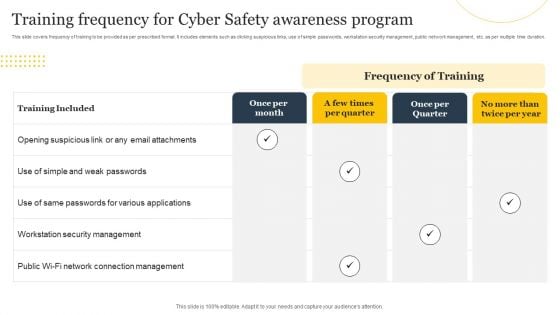
Training Frequency For Cyber Safety Awareness Program Ppt Pictures Graphics PDF
This slide covers frequency of training to be provided as per prescribed format. It includes elements such as clicking suspicious links, use of simple passwords, workstation security management, public network management, etc. as per multiple time duration. Showcasing this set of slides titled Training Frequency For Cyber Safety Awareness Program Ppt Pictures Graphics PDF. The topics addressed in these templates are Training Included, Once Per Month, Frequency Training. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
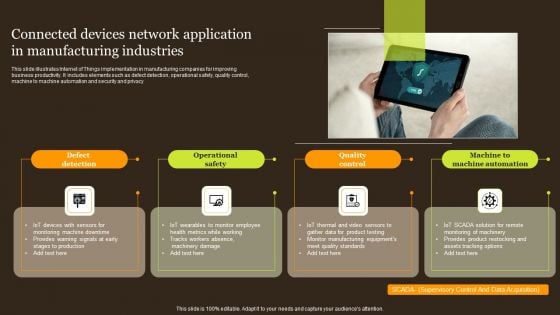
Connected Devices Network Application In Manufacturing Industries Portrait PDF
This slide illustrates Internet of Things implementation in manufacturing companies for improving business productivity. It includes elements such as defect detection, operational safety, quality control, machine to machine automation and security and privacy. Presenting Connected Devices Network Application In Manufacturing Industries Portrait PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Defect Detection, Operational Safety, Quality Control . This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
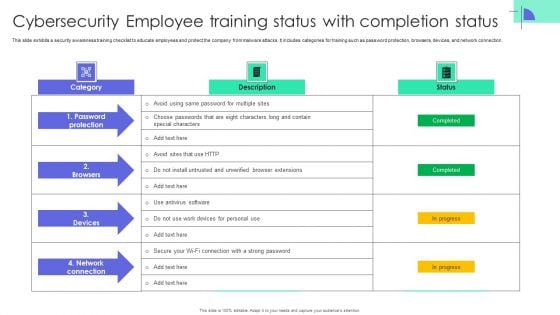
Cybersecurity Employee Training Status With Completion Status Structure PDF
This slide exhibits a security awareness training checklist to educate employees and protect the company from malware attacks. It includes categories for training such as password protection, browsers, devices, and network connection. Pitch your topic with ease and precision using this Cybersecurity Employee Training Status With Completion Status Structure PDF. This layout presents information on Training Status Completion Status, Cybersecurity Employee. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Cybersecurity Monitoring Plan Steps In Detail Monitoring Network Traffic Summary PDF
This slide provides information about the third step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e., Monitoring Network Traffic. Presenting cybersecurity monitoring plan steps in detail monitoring network traffic summary pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like inbound and outbound traffic, could indicate attacks, unusual network traffic. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
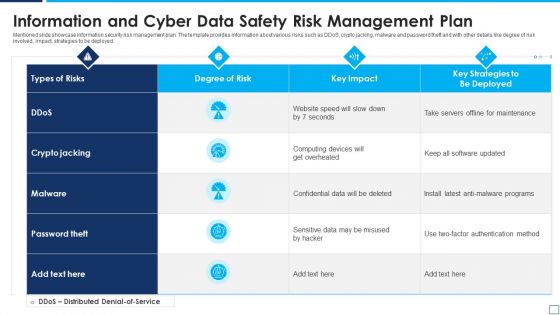
Information And Cyber Data Safety Risk Management Plan Summary PDF
Mentioned slide showcase information security risk management plan. The template provides information about various risks such as DDoS, crypto jacking, malware and password theft and with other details like degree of risk involved, impact, strategies to be deployed. Showcasing this set of slides titled information and cyber data safety risk management plan summary pdf. The topics addressed in these templates are information and cyber data safety risk management plan. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Various Strategies To Ensure Food Safety Application Of Quality Management For Food Processing Companies Icons PDF
This slide provides information regarding various strategies used by firm in ensuring food safety in terms of streamlining global safety requirements, digitalization of food, food safety network. This is a various strategies to ensure food safety application of quality management for food processing companies icons pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like streamlining global safety requirements, digitalization of food security or safety data, building food safety network. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
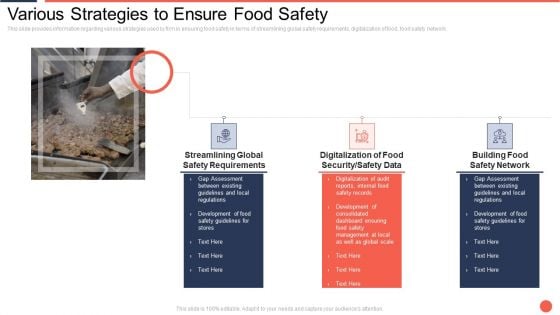
Various Strategies To Ensure Food Safety Assuring Food Quality And Hygiene Brochure PDF
This slide provides information regarding various strategies used by firm in ensuring food safety in terms of streamlining global safety requirements, digitalization of food, food safety network. This is a various strategies to ensure food safety assuring food quality and hygiene brochure pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like streamlining global safety requirements, digitalization of food security or safety data, building food safety network. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
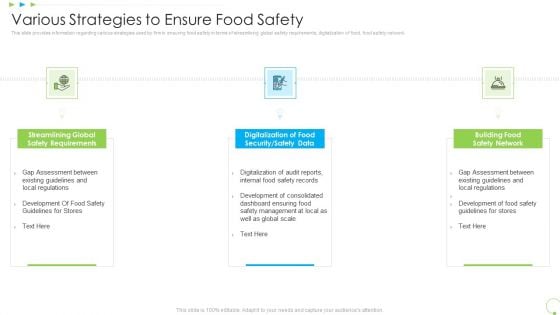
Various Strategies To Ensure Food Safety Uplift Food Production Company Quality Standards Structure PDF
This slide provides information regarding various strategies used by firm in ensuring food safety in terms of streamlining global safety requirements, digitalization of food, food safety network. This is a various strategies to ensure food safety uplift food production company quality standards structure pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like streamlining global safety requirements, digitalization of food security or safety data, building food safety network. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
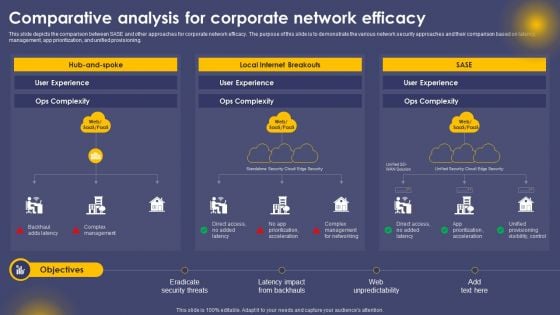
Comparative Analysis For Corporate Network Efficacy Ppt Model Master Slide PDF
This slide depicts the comparison between SASE and other approaches for corporate network efficacy. The purpose of this slide is to demonstrate the various network security approaches and their comparison based on latency, management, app prioritization, and unified provisioning. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Comparative Analysis For Corporate Network Efficacy Ppt Model Master Slide PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.
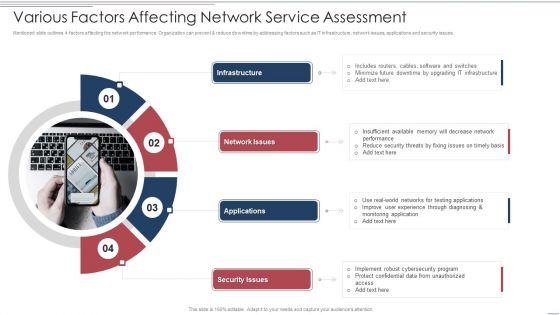
Various Factors Affecting Network Service Assessment Brochure PDF
Mentioned slide outlines 4 factors affecting the network performance. Organization can prevent and reduce downtime by addressing factors such as IT infrastructure, network issues, applications and security issues. Persuade your audience using this Various Factors Affecting Network Service Assessment Brochure PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Infrastructure, Network Issues, Applications. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
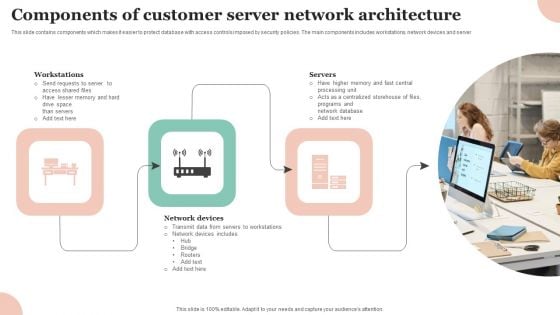
Components Of Customer Server Network Architecture Professional PDF
This slide contains components which makes it easier to protect database with access controls imposed by security policies. The main components includes workstations, network devices and server Persuade your audience using this Components Of Customer Server Network Architecture Professional PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Workstations, Network Devices, Servers . Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
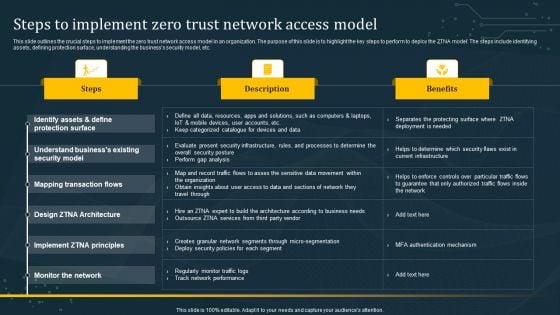
Steps To Implement Zero Trust Network Access Model Graphics PDF
This slide outlines the crucial steps to implement the zero trust network access model in an organization. The purpose of this slide is to highlight the key steps to perform to deploy the ZTNA model. The steps include identifying assets, defining protection surface, understanding the businesss security model, etc. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Steps To Implement Zero Trust Network Access Model Graphics PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates

New Product Launch Event Management Activities Existing Products And Service Offerings Of Firm Introduction PDF
This slide showcases products and services of information technology company. The offerings covered are file servers, virtual desktops, office phones, network equipment, help desk, data backup, web designing, network security and cloud services. Make sure to capture your audiences attention in your business displays with our gratis customizable New Product Launch Event Management Activities Existing Products And Service Offerings Of Firm Introduction PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Construction Project Instructions Playbook Essential Guidelines To Ensure Workers Safety Background PDF
This slide provides information regarding essential guidelines to ensure workers safety with details about workers clothing and PPE, site protection and security and tools and equipment. Create an editable Construction Project Instructions Playbook Essential Guidelines To Ensure Workers Safety Background PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre designed presentation templates help save time. Construction Project Instructions Playbook Essential Guidelines To Ensure Workers Safety Background PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
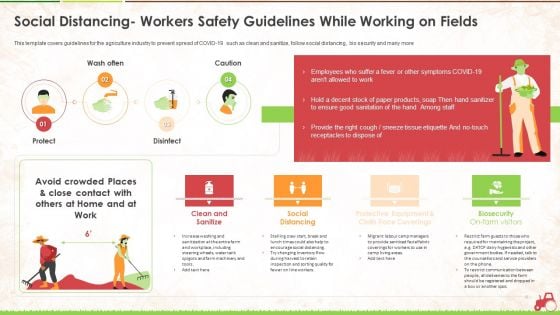
Social Distancing Workers Safety Guidelines While Working On Fields Ppt Ideas Infographic Template PDF
This template covers guidelines for the agriculture industry to prevent spread of COVID-19 such as clean and sanitize, follow social distancing, bio security and many more Deliver an awe-inspiring pitch with this creative social distancing workers safety guidelines while working on fields ppt ideas infographic template pdf. bundle. Topics like clean and sanitize, social distancing, protective equipment and cloth face coverings, biosecurity on farm visitors can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
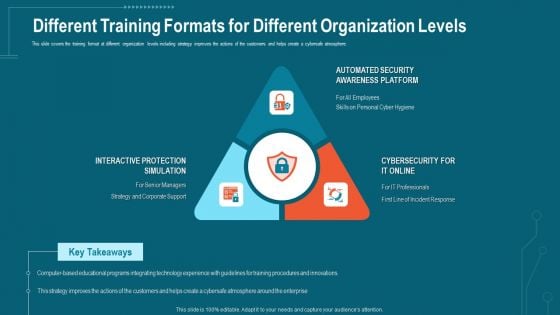
Companys Data Safety Recognition Different Training Formats For Different Organization Levels Structure PDF
This slide covers the training format at different organization levels including strategy improves the actions of the customers and helps create a cybersafe atmosphere. This is a companys data safety recognition different training formats for different organization levels structure pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like interactive protection simulation, automated security awareness platform, cybersecurity. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
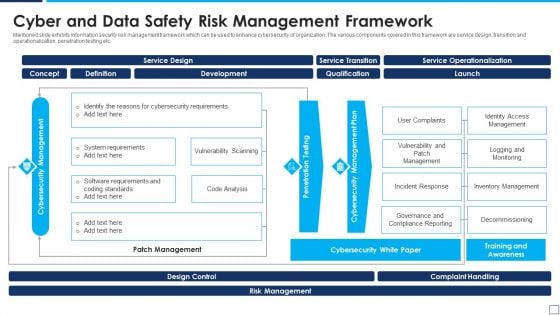
Cyber And Data Safety Risk Management Framework Designs PDF
Mentioned slide exhibits information security risk management framework which can be used to enhance cybersecurity of organization. The various components covered in this framework are service design, transition and operationalization, penetration testing etc. Showcasing this set of slides titled cyber and data safety risk management framework designs pdf. The topics addressed in these templates are service design, development, service operationalization. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
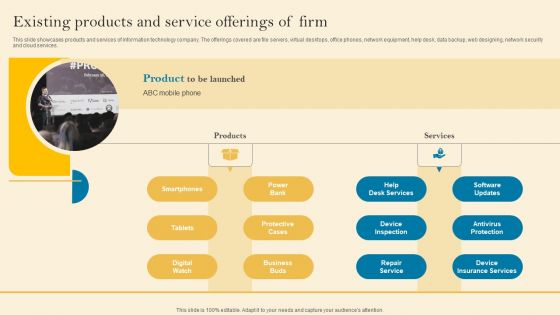
Product Inauguration Event Planning And Administration Existing Products And Service Guidelines PDF
This slide showcases products and services of information technology company. The offerings covered are file servers, virtual desktops, office phones, network equipment, help desk, data backup, web designing, network security and cloud services. Want to ace your presentation in front of a live audience Our Product Inauguration Event Planning And Administration Existing Products And Service Guidelines PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.

Portable Home Safety Systems Company Profile End To End Service Delivery Model Designs PDF
This slide highlights the home security company end to end service implementation and delivery model which includes four stages find, design, install and manage. Presenting Portable Home Safety Systems Company Profile End To End Service Delivery Model Designs PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Delivery And Installation, Retail Outlets, Sales Representative. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Communication Infrastructure Services Download PDF
The following slide demonstrates information and communication technology infrastructure services for optimizing output, mitigate internal and external security threat. It includes components such as operations and network management etc. Persuade your audience using this IT Communication Infrastructure Services Download PDF. This PPT design covers two stages, thus making it a great tool to use. It also caters to a variety of topics including Applications, Description, Operations Management . Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
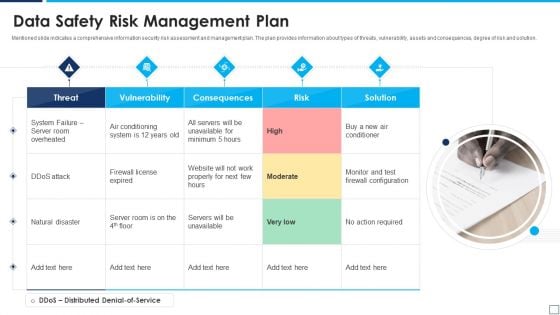
Data Safety Risk Management Plan Designs PDF
Mentioned slide indicates a comprehensive information security risk assessment and management plan. The plan provides information about types of threats, vulnerability, assets and consequences, degree of risk and solution. Persuade your audience using this data safety risk management plan designs pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including data safety risk management plan. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
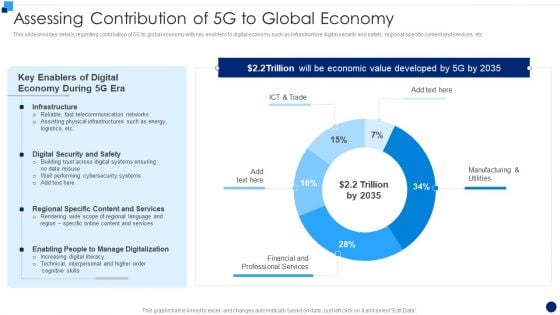
Developing 5G Wireless Cellular Network Assessing Contribution Of 5G To Global Economy Rules PDF
This slide provides details regarding contribution of 5G to global economy with key enablers to digital economy such as infrastructure digital security and safety, regional specific content and services, etc. Deliver and pitch your topic in the best possible manner with this Developing 5G Wireless Cellular Network Assessing Contribution Of 5G To Global Economy Rules PDF. Use them to share invaluable insights on Telecommunication Networks, Cybersecurity Systems, Content And Services and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
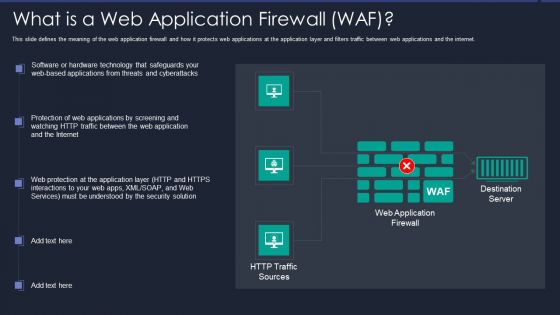
Web App Firewall Services IT What Is A Web Application Firewall WAF Graphics PDF
This slide defines the meaning of the web application firewall and how it protects web applications at the application layer and filters traffic between web applications and the internet. This slide defines the meaning of the web application firewall and how it protects web applications at the application layer and filters traffic between web applications and the internet. Deliver and pitch your topic in the best possible manner with this web app firewall services it what is a web application firewall waf graphics pdf. Use them to share invaluable insights on applications, technology, security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Data Safety Initiatives Embedding Risk Based Approach Into Product Development Process Topics PDF
Purpose of this slide is to highlight the risk-based approach and process efficiency along with the cost incur details. It also shows that company will develop agile security and privacy models. Deliver an awe inspiring pitch with this creative data safety initiatives embedding risk based approach into product development process topics pdf bundle. Topics like requirements, design and development, testing, deployment, throughout process can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
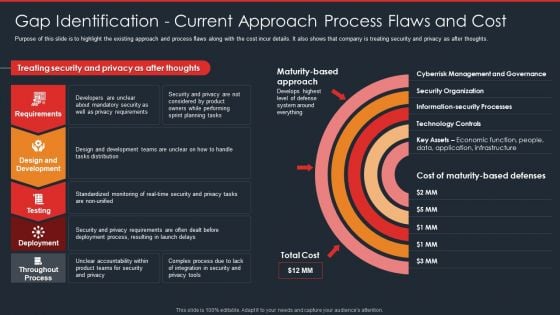
Data Safety Initiatives Gap Identification Current Approach Process Flaws And Cost Ideas PDF
Purpose of this slide is to highlight the existing approach and process flaws along with the cost incur details. It also shows that company is treating security and privacy as after thoughts. Deliver an awe inspiring pitch with this creative data safety initiatives gap identification current approach process flaws and cost ideas pdf bundle. Topics like requirements, design and development, testing, deployment, throughout process can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
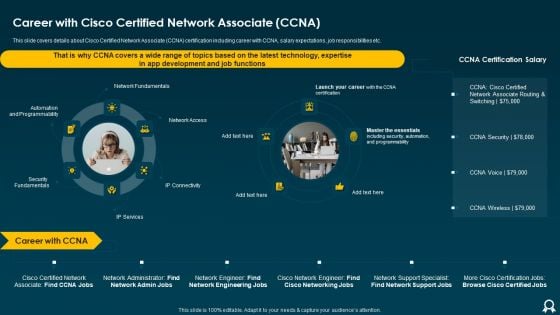
IT Data Services Certification Programs Career With Cisco Certified Network Associate CCNA Brochure PDF
This slide covers details about Cisco Certified Network Associate CCNA certification including career with CCNA, salary expectations, job responsibilities etc. This is a IT Data Services Certification Programs Career With Cisco Certified Network Associate CCNA Brochure PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Network Fundamentals, Automation And Programmability, Security Fundamentals. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
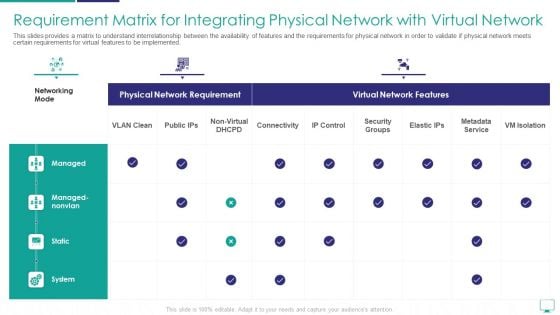
Requirement Matrix For Integrating Physical Network With Virtual Network Sample PDF
This slides provides a matrix to understand interrelationship between the availability of features and the requirements for physical network in order to validate if physical network meets certain requirements for virtual features to be implemented.Deliver an awe inspiring pitch with this creative requirement matrix for integrating physical network with virtual network sample pdf bundle. Topics like metadata service, security groups, managed nonvlan can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Assessing Contribution Of 5G To Global Economy 5G Network Architecture Instructions Microsoft PDF
This slide provides details regarding contribution of 5G to global economy with key enablers to digital economy such as infrastructure digital security and safety, regional specific content and services, etc. Deliver and pitch your topic in the best possible manner with this Assessing Contribution Of 5G To Global Economy 5G Network Architecture Instructions Microsoft PDF. Use them to share invaluable insights on Digital Economy, Fast Telecommunication, Physical Infrastructures and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
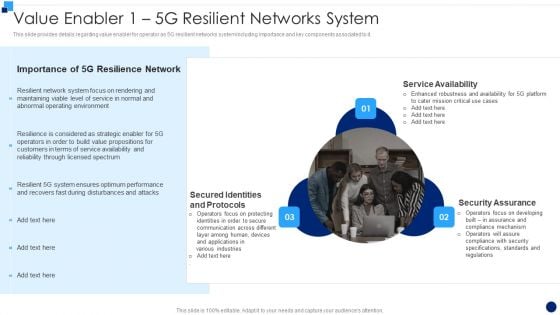
Developing 5G Wireless Cellular Network Value Enabler 1 5G Resilient Networks System Clipart PDF
This slide provides details regarding value enabler for operator as 5G resilient networks system including importance and key components associated to it. This is a Developing 5G Wireless Cellular Network Value Enabler 1 5G Resilient Networks System Clipart PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Assurance, Service Availability, Protocols. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Next Step For Post Building Management Services Proposal One Pager Sample Example Document
The following slide displays the next step that the organization has to take once the security proposal has been signed, these steps can be tem meeting ,on site visit etc. Presenting you an exemplary Next Step For Post Building Management Services Proposal One Pager Sample Example Document. Our one pager comprises all the must have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Next Step For Post Building Management Services Proposal One Pager Sample Example Document brilliant piece now.
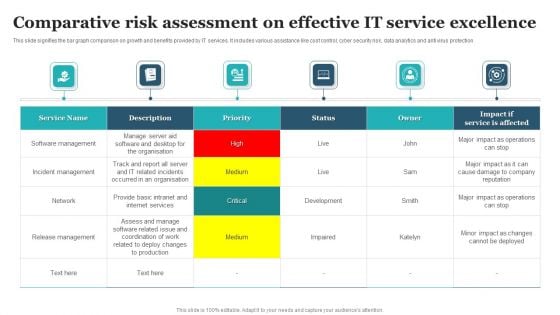
Comparative Risk Assessment On Effective IT Service Excellence Designs PDF
This slide signifies the bar graph comparison on growth and benefits provided by IT services. It includes various assistance like cost control, cyber security risk, data analytics and anti virus protection. Showcasing this set of slides titled Comparative Risk Assessment On Effective IT Service Excellence Designs PDF. The topics addressed in these templates are Software Management, Incident Management, Release Management. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

SIEM Competitive Advantage Enhancing Cyber Safety With Vulnerability Administration Introduction PDF
This slide covers the SIEM competitive landscape based on various categories such as digital experience management, health check, application performance monitoring, event management, etc. Deliver and pitch your topic in the best possible manner with this siem competitive advantage enhancing cyber safety with vulnerability administration introduction pdf. Use them to share invaluable insights on security information and event management, application performance monitoring, digital experience management, service health check and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.


 Continue with Email
Continue with Email

 Home
Home


































