Security
Computer Security Vector Icon Ppt PowerPoint Presentation File Outline PDF
Presenting this set of slides with name computer security vector icon ppt powerpoint presentation file outline pdf. This is a three stage process. The stages in this process are computer security vector icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security System Image Ppt PowerPoint Presentation Styles Microsoft PDF
Presenting this set of slides with name cyber security system image ppt powerpoint presentation styles microsoft pdf. This is a three stage process. The stages in this process are cyber security system image. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
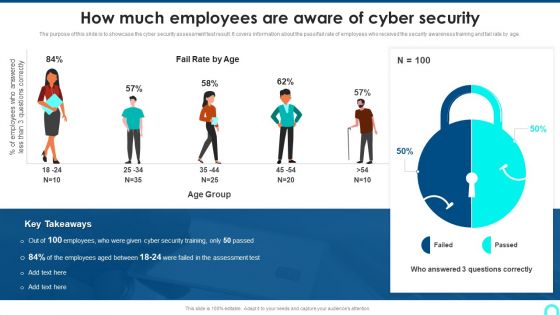
How Much Employees Are Aware Of Cyber Security Introduction PDF
The purpose of this slide is to showcase the cyber security assessment test result. It covers information about the pass fail rate of employees who received the security awareness training and fail rate by age.This is a How Much Employees Are Aware Of Cyber Security Introduction PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Questions Correctly, Employees Answered, Employees Between. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Stock Photo Atm Card With Lock For Security PowerPoint Slide
This image slide contains graphics of ATM card with lock. You may use this image to depict safe, secure and easy way to manage your money. Accelerate the impact of your ideas with this image slide.
Corporate Data Management And Privacy Security Mechanism Icon Slides PDF
Persuade your audience using this Corporate Data Management And Privacy Security Mechanism Icon Slides PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Corporate Data, Management Privacy, Security Mechanism Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Stock Photo 3d Globe Inside The Chain Security PowerPoint Slide
3d globe is covered with chain in this business image. This image is specially designed for displaying global security issues. Use this image for business and defense related presentations and create a good impact on viewers.

Business Help Security PowerPoint Templates Ppt Backgrounds For Slides 0113
We present our Business Help Security PowerPoint Templates PPT Backgrounds For Slides 0113.Use our Security PowerPoint Templates because It can Bubble and burst with your ideas. Use our Business PowerPoint Templates because Our PowerPoint Templates and Slides help you meet the demand of the Market. Just browse and pick the slides that appeal to your intuitive senses. Present our Puzzles or Jigsaws PowerPoint Templates because It can Bubble and burst with your ideas. Use our Future PowerPoint Templates because Our PowerPoint Templates and Slides will let you Hit the target. Go the full distance with ease and elan. Present our Success PowerPoint Templates because Our PowerPoint Templates and Slides will let Your superior ideas hit the target always and everytime.Use these PowerPoint slides for presentations relating to Business rescue, security, puzzles or jigsaws, future, business, success. The prominent colors used in the PowerPoint template are Red, Blue, White. Customers tell us our Business Help Security PowerPoint Templates PPT Backgrounds For Slides 0113 are designed by a team of presentation professionals. PowerPoint presentation experts tell us our success PowerPoint templates and PPT Slides are designed by a team of presentation professionals. You can be sure our Business Help Security PowerPoint Templates PPT Backgrounds For Slides 0113 are incredible easy to use. Customers tell us our success PowerPoint templates and PPT Slides will make the presenter look like a pro even if they are not computer savvy. Professionals tell us our Business Help Security PowerPoint Templates PPT Backgrounds For Slides 0113 will make the presenter successul in his career/life. You can be sure our jigsaws PowerPoint templates and PPT Slides are the best it can get when it comes to presenting. Establish benchmarks with our Business Help Security PowerPoint Templates Ppt Backgrounds For Slides 0113. Your thoughts will be an example to live upto.

Traditional Perimeter Based Network Security Overview And Limitations Inspiration PDF
This slide represents the overview of traditional perimeter-based network security. The purpose of this slide is to showcase the various challenges of conventional perimeter-based security and how ZTNA can overcomethose challenges. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Traditional Perimeter Based Network Security Overview And Limitations Inspiration PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
Cyber Security Vector Icon Ppt PowerPoint Presentation Inspiration
Presenting this set of slides with name cyber security vector icon ppt powerpoint presentation inspiration. This is a one stage process. The stages in this process are technology, social network, social engineering. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Emergency Procedures Security Ppt PowerPoint Presentation Icon Styles
Presenting this set of slides with name emergency procedures security ppt powerpoint presentation icon styles. This is a three stage process. The stages in this process are technology, marketing, planning, business, management. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Solution Key Security PowerPoint Templates Ppt Backgrounds For Slides 0113
We present our Solution Key Security PowerPoint Templates PPT Backgrounds For Slides 0113.Download our Real estate PowerPoint Templates because They will Put your wonderful verbal artistry on display. Our PowerPoint Templates and Slides will provide you the necessary glam and glitter. Present our Sales PowerPoint Templates because You can Bask in the warmth of our PowerPoint Templates and Slides. Enjoy the heartfelt glowing response of your listeners. Use our Marketing PowerPoint Templates because You can Be the star of the show with our PowerPoint Templates and Slides. Rock the stage with your ideas. Download and present our Signs PowerPoint Templates because You have the co-ordinates for your destination of success. Let our PowerPoint Templates and Slides map out your journey. Download and present our Security PowerPoint Templates because our PowerPoint Templates and Slides are the string of your bow. Fire of your ideas and conquer the podium.Use these PowerPoint slides for presentations relating to Red house-shape key, real estate, sales, marketing, signs, security. The prominent colors used in the PowerPoint template are Red, Yellow, Gray. We assure you our Solution Key Security PowerPoint Templates PPT Backgrounds For Slides 0113 will save the presenter time. PowerPoint presentation experts tell us our real PowerPoint templates and PPT Slides provide great value for your money. Be assured of finding the best projection to highlight your words. Presenters tell us our Solution Key Security PowerPoint Templates PPT Backgrounds For Slides 0113 provide you with a vast range of viable options. Select the appropriate ones and just fill in your text. Professionals tell us our real PowerPoint templates and PPT Slides will generate and maintain the level of interest you desire. They will create the impression you want to imprint on your audience. The feedback we get is that our Solution Key Security PowerPoint Templates PPT Backgrounds For Slides 0113 are aesthetically designed to attract attention. We guarantee that they will grab all the eyeballs you need. PowerPoint presentation experts tell us our signs PowerPoint templates and PPT Slides are incredible easy to use. Charge to success with our Solution Key Security PowerPoint Templates Ppt Backgrounds For Slides 0113. You will come out on top.

Business Context Diagram 3d Man With Chain Security PowerPoint Slides
We present our business context diagram 3d man with chain security PowerPoint Slides.Download our Security PowerPoint Templates because You canTake a leap off the starting blocks with our PowerPoint Templates and Slides. They will put you ahead of the competition in quick time. Present our Chains PowerPoint Templates because Our PowerPoint Templates and Slides will effectively help you save your valuable time. They are readymade to fit into any presentation structure. Present our Business PowerPoint Templates because Our PowerPoint Templates and Slides are aesthetically designed to attract attention. We gaurantee that they will grab all the eyeballs you need. Use our Process and Flows PowerPoint Templates because Timeline crunches are a fact of life. Meet all deadlines using our PowerPoint Templates and Slides. Download and present our Shapes PowerPoint Templates because Our PowerPoint Templates and Slides will give good value for money. They also have respect for the value of your time.Use these PowerPoint slides for presentations relating to 3d, Business, Chain, Connect, Connection, Heavy, Industrial, Industry, Isolated, Link, Linked, Man, Metal, Power, Powerful, Protection, Secure, Steel, Strength, Support, Symbol, Teamwork, Weak, White. The prominent colors used in the PowerPoint template are Blue, Gray, Black. Professionals tell us our business context diagram 3d man with chain security PowerPoint Slides are effectively colour coded to prioritise your plans They automatically highlight the sequence of events you desire. The feedback we get is that our Industry PowerPoint templates and PPT Slides are designed to make your presentations professional. Professionals tell us our business context diagram 3d man with chain security PowerPoint Slides are effectively colour coded to prioritise your plans They automatically highlight the sequence of events you desire. People tell us our Connection PowerPoint templates and PPT Slides are designed by professionals PowerPoint presentation experts tell us our business context diagram 3d man with chain security PowerPoint Slides look good visually. You can be sure our Industry PowerPoint templates and PPT Slides will make you look like a winner. You've found a treasure for presentations. Get goingwith our Business Context Diagram 3d Man With Chain Security PowerPoint Slides. You'll deliver your best presentation yet.

Overview Of Cyber Security Awareness Course Ppt Ideas Styles PDF
The purpose of this slide is to provide a glimpse of the selected cyber security awareness course. It covers information about the instructor details, course content, attendees and learning outcome. Slidegeeks is here to make your presentations a breeze with Overview Of Cyber Security Awareness Course Ppt Ideas Styles PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Framework Administration Interdependence Resiliency And Security Ppt Ideas PDF
Presenting framework administration interdependence resiliency and security ppt ideas pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like lifecycle adaptive components of resilience framework, infrastructure resilience wheel. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.

Locked The Target Security PowerPoint Templates And PowerPoint Backgrounds 0211
Microsoft PowerPoint Template and Background with a pair of silver handcuffs attached to target Let your ideas acquire a flourish. Our PT&s will ensure they blossom.

Importance Of 5G Network Security Policies Portrait Pdf
This slide highlights importance for 5G network security policies for Network stabilization. It further includes security EU, access network security , core network security etc. Showcasing this set of slides titled Importance Of 5G Network Security Policies Portrait Pdf. The topics addressed in these templates are Access Network Security, Core Network Security, Security Enablers. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide highlights importance for 5G network security policies for Network stabilization. It further includes security EU, access network security , core network security etc.

Effective Security Strategic Agenda For Hotels Introduction Pdf
This slide represents effective security action plan for hotels and motels. It further includes major security features such as area security, surveillance, contaminant protection and security personnel. Showcasing this set of slides titled Effective Security Strategic Agenda For Hotels Introduction Pdf. The topics addressed in these templates are Security, Action Taken, Responsible Authority. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide represents effective security action plan for hotels and motels. It further includes major security features such as area security, surveillance, contaminant protection and security personnel.
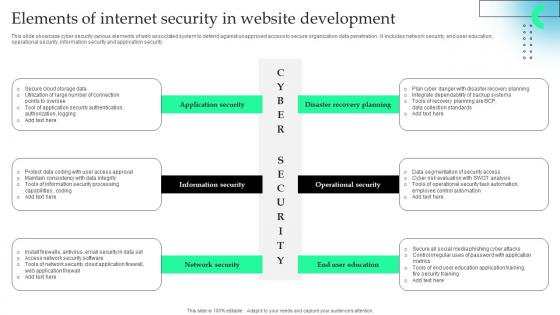
Elements Of Internet Security In Website Development Formats Pdf
This slide showcase cyber security various elements of web associated system to defend against unapproved access to secure organization data penetration . It includes network security, end user education, operational security, information security and application security.Pitch your topic with ease and precision using this Elements Of Internet Security In Website Development Formats Pdf This layout presents information on Information Security, Network Security, Operational Security It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide showcase cyber security various elements of web associated system to defend against unapproved access to secure organization data penetration . It includes network security, end user education, operational security, information security and application security.

4 Steps For Building Internet Security Strategy Clipart Pdf
This slide showcase developing and implementation of cyber security strategy for streamline the data security and organization vision and mission. It includes cyber threat landscape, assess cybersecurity maturity, determine security program and document cybersecurity strategy.Showcasing this set of slides titled 4 Steps For Building Internet Security Strategy Clipart Pdf The topics addressed in these templates are Cyber Security Maturity, Cyber Security Program, Document Cybersecurity Strategy All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcase developing and implementation of cyber security strategy for streamline the data security and organization vision and mission. It includes cyber threat landscape, assess cybersecurity maturity, determine security program and document cybersecurity strategy.
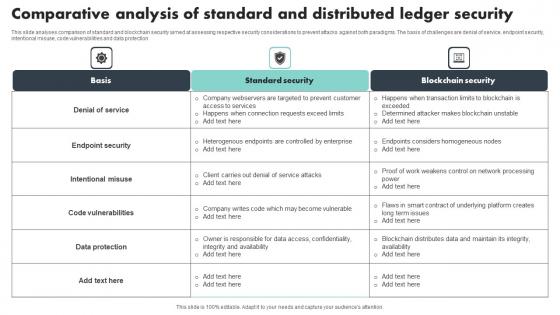
Comparative Analysis Of Standard And Distributed Ledger Security Mockup Pdf
This slide analyses comparison of standard and blockchain security aimed at assessing respective security considerations to prevent attacks against both paradigms. The basis of challenges are denial of service, endpoint security, intentional misuse, code vulnerabilities and data protection Pitch your topic with ease and precision using this Comparative Analysis Of Standard And Distributed Ledger Security Mockup Pdf This layout presents information on Denial Of Service, Endpoint Security, Code Vulnerabilities It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide analyses comparison of standard and blockchain security aimed at assessing respective security considerations to prevent attacks against both paradigms. The basis of challenges are denial of service, endpoint security, intentional misuse, code vulnerabilities and data protection

Vendor Data Security Checklist For Market Research Company Sample Pdf
The purpose of this slide is to showcase checklist for supplier information security for market research company. It includes various process to be completed such as vendor possess a security rating that meets with expectations, supplier has invested in data protection and information security controls etc. Pitch your topic with ease and precision using this Vendor Data Security Checklist For Market Research Company Sample Pdf. This layout presents information on Vendor Data Security, Market Research. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. The purpose of this slide is to showcase checklist for supplier information security for market research company. It includes various process to be completed such as vendor possess a security rating that meets with expectations, supplier has invested in data protection and information security controls etc.
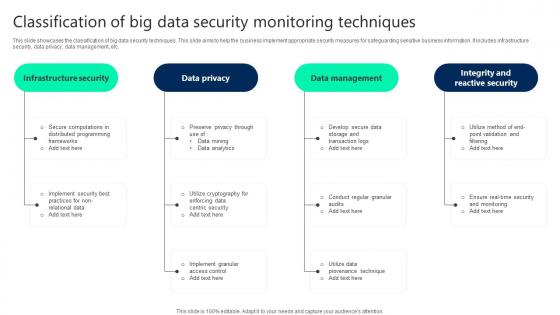
Classification Of Big Data Security Monitoring Techniques Professional pdf
This slide showcases the classification of big data security techniques. This slide aims to help the business implement appropriate security measures for safeguarding sensitive business information. It includes infrastructure security, data privacy, data management, etc. Pitch your topic with ease and precision using this Classification Of Big Data Security Monitoring Techniques Professional pdf. This layout presents information on Infrastructure Security, Data Privacy, Data Management. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide showcases the classification of big data security techniques. This slide aims to help the business implement appropriate security measures for safeguarding sensitive business information. It includes infrastructure security, data privacy, data management, etc.

Courses For Malware Cyber Security Breach Awareness Download Pdf
This slides shows various training programs of cyber security awareness to aware staff. The purpose of this slide is to reducing threat in future. The various course are Cofense online security, webroot security training, etc. Showcasing this set of slides titled Courses For Malware Cyber Security Breach Awareness Download Pdf The topics addressed in these templates are Awareness Training, Webroot Security, Cybsafe Borderless All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slides shows various training programs of cyber security awareness to aware staff. The purpose of this slide is to reducing threat in future. The various course are Cofense online security, webroot security training, etc.
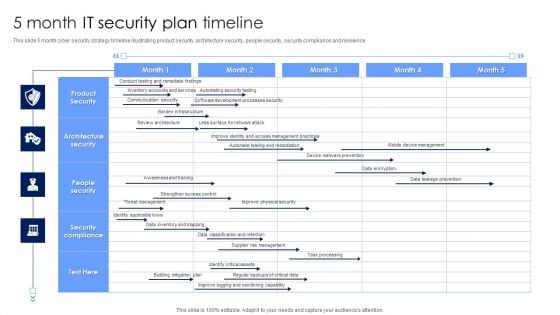
5 Month IT Security Plan Timeline Pictures PDF
This slide 5 month cyber security strategy timeline illustrating product security, architecture security, people security, security compliance and resilience. Showcasing this set of slides titled 5 Month IT Security Plan Timeline Pictures PDF. The topics addressed in these templates are Architecture Security, People Security, Security Compliance. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
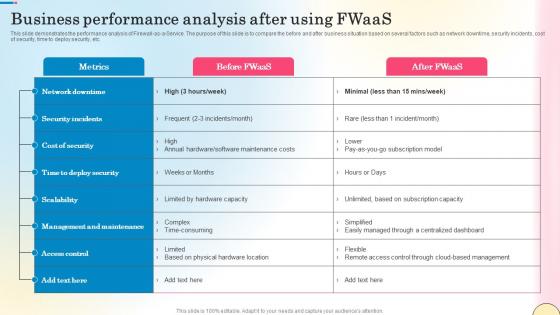
Business Performance Analysis After Using Fwaas Network Security Sample Pdf
This slide demonstrates the performance analysis of Firewall-as-a-Service. The purpose of this slide is to compare the before and after business situation based on several factors such as network downtime, security incidents, cost of security, time to deploy security, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Business Performance Analysis After Using Fwaas Network Security Sample Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide demonstrates the performance analysis of Firewall-as-a-Service. The purpose of this slide is to compare the before and after business situation based on several factors such as network downtime, security incidents, cost of security, time to deploy security, etc.

Distributed Ledger Technology Impact On Data Security Infographics Pdf
This slide highlights impact on blockchain on data security aimed at reducing costs, increasing transparency, enhancing security and efficiency. It covers encryption and validation, decentralized data security with difficulties in hacking Pitch your topic with ease and precision using this Distributed Ledger Technology Impact On Data Security Infographics Pdf This layout presents information on Encryption And Validation, Decentralized Data Security, Difficulties In Hacking It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide highlights impact on blockchain on data security aimed at reducing costs, increasing transparency, enhancing security and efficiency. It covers encryption and validation, decentralized data security with difficulties in hacking
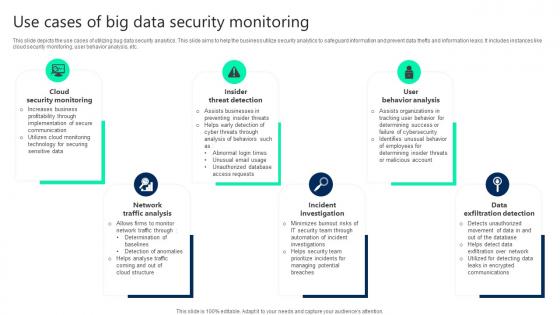
Use Cases Of Big Data Security Monitoring Clipart pdf
This slide depicts the use cases of utilizing bug data security analytics. This slide aims to help the business utilize security analytics to safeguard information and prevent data thefts and information leaks. It includes instances like cloud security monitoring, user behavior analysis, etc. Pitch your topic with ease and precision using this Use Cases Of Big Data Security Monitoring Clipart pdf. This layout presents information on Cloud Security Monitoring, Insider Threat Detection, User Behavior Analysis. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide depicts the use cases of utilizing bug data security analytics. This slide aims to help the business utilize security analytics to safeguard information and prevent data thefts and information leaks. It includes instances like cloud security monitoring, user behavior analysis, etc.
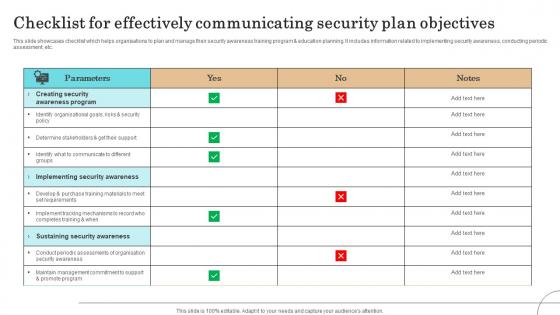
Checklist For Effectively Communicating Security Plan Objectives Introduction Pdf
This slide showcases checklist which helps organisations to plan and manage their security awareness training program education planning. It includes information related to implementing security awareness, conducting periodic assessment, etc.Showcasing this set of slides titled Checklist For Effectively Communicating Security Plan Objectives Introduction Pdf The topics addressed in these templates are Implementing Security Awareness, Sustaining Security Awareness, Awareness Program All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcases checklist which helps organisations to plan and manage their security awareness training program education planning. It includes information related to implementing security awareness, conducting periodic assessment, etc.
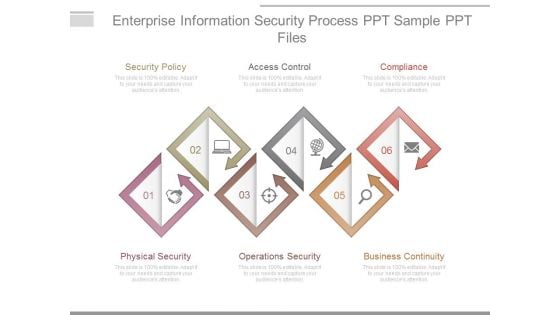
Enterprise Information Security Process Ppt Sample Ppt Files
This is a enterprise information security process ppt sample ppt files. This is a six stage process. The stages in this process are security policy, access control, compliance, physical security, operations security, business continuity.
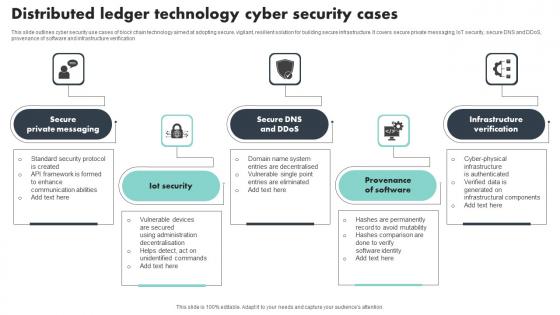
Distributed Ledger Technology Cyber Security Cases Brochure Pdf
This slide outlines cyber security use cases of block chain technology aimed at adopting secure, vigilant, resilient solution for building secure infrastructure. It covers secure private messaging, IoT security, secure DNS and DDoS, provenance of software and infrastructure verification Showcasing this set of slides titled Distributed Ledger Technology Cyber Security Cases Brochure Pdf The topics addressed in these templates are Private Messaging, Provenance Of Software, Infrastructure Verification All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide outlines cyber security use cases of block chain technology aimed at adopting secure, vigilant, resilient solution for building secure infrastructure. It covers secure private messaging, IoT security, secure DNS and DDoS, provenance of software and infrastructure verification
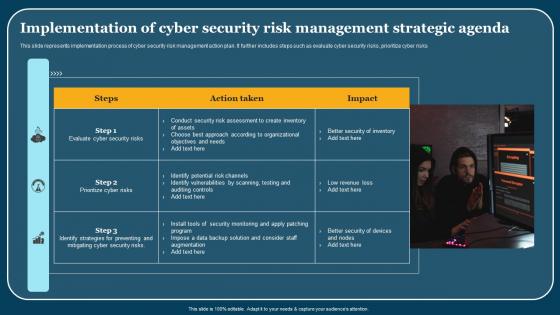
Implementation Of Cyber Security Risk Management Strategic Agenda Pictures Pdf
This slide represents implementation process of cyber security risk management action plan. It further includes steps such as evaluate cyber security risks, prioritize cyber risks. Pitch your topic with ease and precision using this Implementation Of Cyber Security Risk Management Strategic Agenda Pictures Pdf. This layout presents information on Steps, Action Taken, Impact. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide represents implementation process of cyber security risk management action plan. It further includes steps such as evaluate cyber security risks, prioritize cyber risks.
Key Benefits Of Implementing Application Security Testing Ppt Powerpoint Icons
This slide highlights the key advantages of application security which include minimum risk exposure, security, etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Key Benefits Of Implementing Application Security Testing Ppt Powerpoint Icons from Slidegeeks and deliver a wonderful presentation. This slide highlights the key advantages of application security which include minimum risk exposure, security, etc.

Log Management Process In Application Security Testing Ppt Powerpoint Brochure
This slide showcases the introduction of log management in application security for decreasing the security threats. The Log Management Process In Application Security Testing Ppt Powerpoint Brochure is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide showcases the introduction of log management in application security for decreasing the security threats.
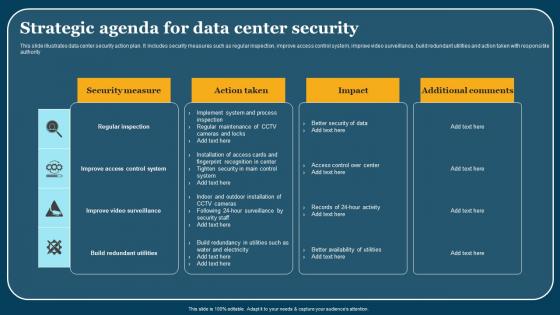
Strategic Agenda For Data Center Security Elements Pdf
This slide illustrates data center security action plan. It includes security measures such as regular inspection, improve access control system, improve video surveillance, build redundant utilities and action taken with responsible authority. Pitch your topic with ease and precision using this Strategic Agenda For Data Center Security Elements Pdf. This layout presents information on Security Areas, Description, Action Taken. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide illustrates data center security action plan. It includes security measures such as regular inspection, improve access control system, improve video surveillance, build redundant utilities and action taken with responsible authority.
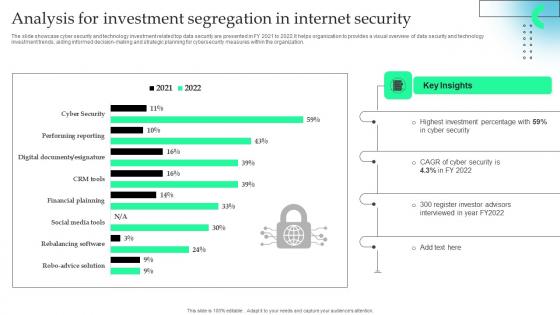
Analysis For Investment Segregation In Internet Security Formats Pdf
The slide showcase cyber security and technology investment related top data security are presented in FY 2021 to 2022.It helps organization to provides a visual overview of data security and technology investment trends, aiding informed decision making and strategic planning for cybersecurity measures within the organization.Pitch your topic with ease and precision using this Analysis For Investment Segregation In Internet Security Formats Pdf This layout presents information on Highest Investment, Register Investor Advisors, Key Insights It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. The slide showcase cyber security and technology investment related top data security are presented in FY 2021 to 2022.It helps organization to provides a visual overview of data security and technology investment trends, aiding informed decision making and strategic planning for cybersecurity measures within the organization.
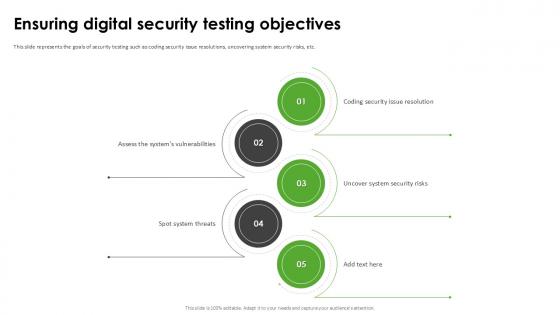
Ensuring Digital Security Harnessing The World Of Ethical Ppt Example
This slide represents the goals of security testing such as coding security issue resolutions, uncovering system security risks, etc. Slidegeeks is here to make your presentations a breeze with Ensuring Digital Security Harnessing The World Of Ethical Ppt Example With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide represents the goals of security testing such as coding security issue resolutions, uncovering system security risks, etc.

Key Parameters To Prepare Security Strategic Agenda Summary Pdf
This slide represents action plan for physical security to provide protection. It further includes security areas such as physical safeguards, administrative safeguards, technical safeguards, etc , their description, action taken, and date of completion. Pitch your topic with ease and precision using this Key Parameters To Prepare Security Strategic Agenda Summary Pdf. This layout presents information on Security Areas, Description, Action Taken. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide represents action plan for physical security to provide protection. It further includes security areas such as physical safeguards, administrative safeguards, technical safeguards, etc , their description, action taken, and date of completion.
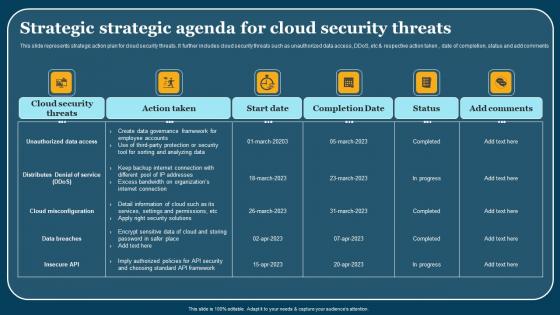
Strategic Strategic Agenda For Cloud Security Threats Ideas Pdf
This slide represents strategic action plan for cloud security threats. It further includes cloud security threats such as unauthorized data access, DDoS, etc and respective action taken , date of completion, status and add comments. Showcasing this set of slides titled Strategic Strategic Agenda For Cloud Security Threats Ideas Pdf. The topics addressed in these templates are Cloud Security Threats, Action Taken, Start Date. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide represents strategic action plan for cloud security threats. It further includes cloud security threats such as unauthorized data access, DDoS, etc and respective action taken , date of completion, status and add comments.

Key Aspects Of 5G Network Security Topics Pdf
This slide highlights 5G security policies for various domains. It further includes network, user equipment, management, access network and applications. Pitch your topic with ease and precision using this Key Aspects Of 5G Network Security Topics Pdf. This layout presents information on Security Domains, Description, Importance Level. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide highlights 5G security policies for various domains. It further includes network, user equipment, management, access network and applications.
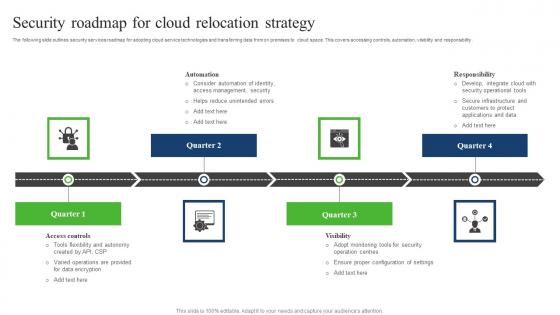
Security Roadmap For Cloud Relocation Strategy Sample Pdf
The following slide outlines security services roadmap for adopting cloud service technologies and transferring data from on premises to cloud space. This covers accessing controls, automation, visibility and responsibility. Showcasing this set of slides titled Security Roadmap For Cloud Relocation Strategy Sample Pdf. The topics addressed in these templates are Responsibility, Automation, Security Roadmap, Cloud Relocation Strategy. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. The following slide outlines security services roadmap for adopting cloud service technologies and transferring data from on premises to cloud space. This covers accessing controls, automation, visibility and responsibility.
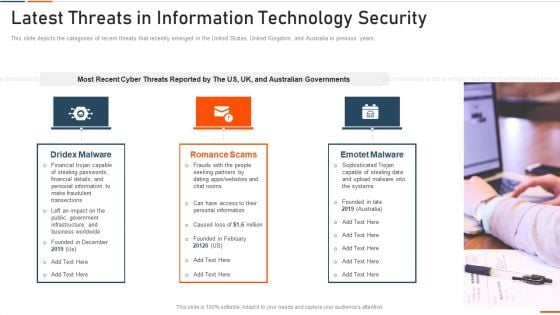
Latest Threats In Information Technology Security Ppt Pictures Designs PDF
This slide represents the different elements of Network security such as application security, network security, information security, etc. This is a latest threats in information technology security ppt pictures designs pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like network security, cloud security, application security, operational security, information security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
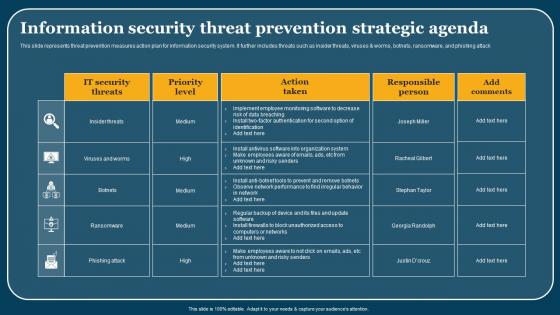
Information Security Threat Prevention Strategic Agenda Introduction Pdf
This slide represents threat prevention measures action plan for information security system. It further includes threats such as insider threats, viruses and worms, botnets, ransomware, and phishing attack. Pitch your topic with ease and precision using this Information Security Threat Prevention Strategic Agenda Introduction Pdf. This layout presents information on Security Threats, Priority Level, Action Taken. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide represents threat prevention measures action plan for information security system. It further includes threats such as insider threats, viruses and worms, botnets, ransomware, and phishing attack.
Cyber Security Checklist To Ensure Strong Authentication Icons Pdf
Following slide shows the checklist for cyber security safety to ensure robust authentication which will assist in regular checking from preventing threat. It includes various parameter for cross checking the cyber security. Showcasing this set of slides titled Cyber Security Checklist To Ensure Strong Authentication Icons Pdf. The topics addressed in these templates are Cyber Security Checklist, Status. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Following slide shows the checklist for cyber security safety to ensure robust authentication which will assist in regular checking from preventing threat. It includes various parameter for cross checking the cyber security.

Green Computing Improving Security By Green Computing Technology
This slide outlineshow green computing can improve security. The purpose of this slide is to showcase the pillars of data security, security concerns and solution, and different antivirus software that can help users to protect their computers and networks. The Green Computing Improving Security By Green Computing Technology is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide outlineshow green computing can improve security. The purpose of this slide is to showcase the pillars of data security, security concerns and solution, and different antivirus software that can help users to protect their computers and networks.
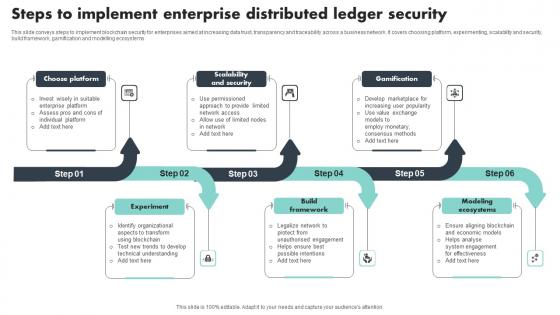
Steps To Implement Enterprise Distributed Ledger Security Download Pdf
This slide conveys steps to implement blockchain security for enterprises aimed at increasing data trust, transparency and traceability across a business network. It covers choosing platform, experimenting, scalability and security, build framework, gamification and modelling ecosystems Pitch your topic with ease and precision using this Steps To Implement Enterprise Distributed Ledger Security Download Pdf This layout presents information on Choose Platform, Scalability And Security, Gamification It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide conveys steps to implement blockchain security for enterprises aimed at increasing data trust, transparency and traceability across a business network. It covers choosing platform, experimenting, scalability and security, build framework, gamification and modelling ecosystems

Improving Security By Green Computing Technology Eco Friendly Computing IT
This slide outlines how green computing can improve security. The purpose of this slide is to showcase the pillars of data security, security concerns and solution, and different antivirus software that can help users to protect their computers and networks.Are you searching for a Improving Security By Green Computing Technology Eco Friendly Computing IT that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Improving Security By Green Computing Technology Eco Friendly Computing IT from Slidegeeks today. This slide outlines how green computing can improve security. The purpose of this slide is to showcase the pillars of data security, security concerns and solution, and different antivirus software that can help users to protect their computers and networks.
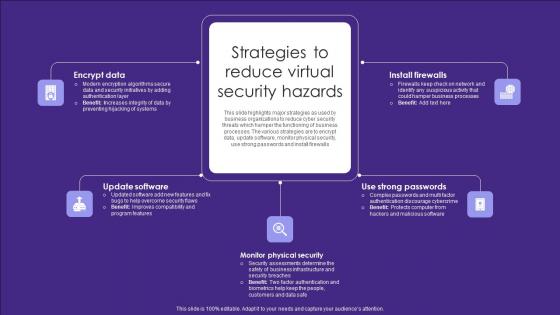
Strategies To Reduce Virtual Security Hazards Summary Pdf
This slide highlights major strategies as used by business organizations to reduce cyber security threats which hamper the functioning of business processes. The various strategies are to encrypt data, update software, monitor physical security, use strong passwords and install firewalls Showcasing this set of slides titled Strategies To Reduce Virtual Security Hazards Summary Pdf. The topics addressed in these templates are Install Firewalls, Strong Passwords, Physical Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide highlights major strategies as used by business organizations to reduce cyber security threats which hamper the functioning of business processes. The various strategies are to encrypt data, update software, monitor physical security, use strong passwords and install firewalls
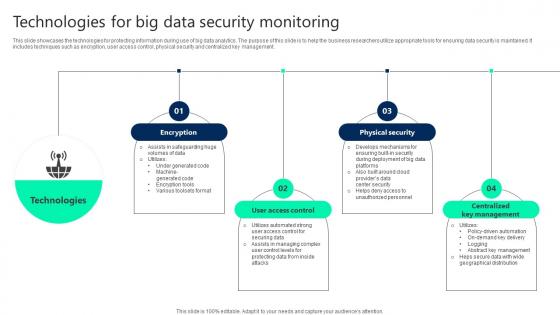
Technologies For Big Data Security Monitoring Summary pdf
This slide showcases the technologies for protecting information during use of big data analytics. The purpose of this slide is to help the business researchers utilize appropriate tools for ensuring data security is maintained. It includes techniques such as encryption, user access control, physical security and centralized key management. Showcasing this set of slides titled Technologies For Big Data Security Monitoring Summary pdf. The topics addressed in these templates are User Access Control, Physical Security, Centralized Key Management. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcases the technologies for protecting information during use of big data analytics. The purpose of this slide is to help the business researchers utilize appropriate tools for ensuring data security is maintained. It includes techniques such as encryption, user access control, physical security and centralized key management.
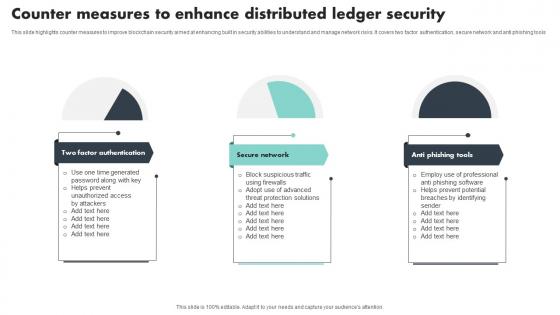
Counter Measures To Enhance Distributed Ledger Security Mockup Pdf
This slide highlights counter measures to improve blockchain security aimed at enhancing built in security abilities to understand and manage network risks. It covers two factor authentication, secure network and anti phishing tools Showcasing this set of slides titled Counter Measures To Enhance Distributed Ledger Security Mockup Pdf The topics addressed in these templates are Factor Authentication, Secure Network, Anti Phishing Tools All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide highlights counter measures to improve blockchain security aimed at enhancing built in security abilities to understand and manage network risks. It covers two factor authentication, secure network and anti phishing tools
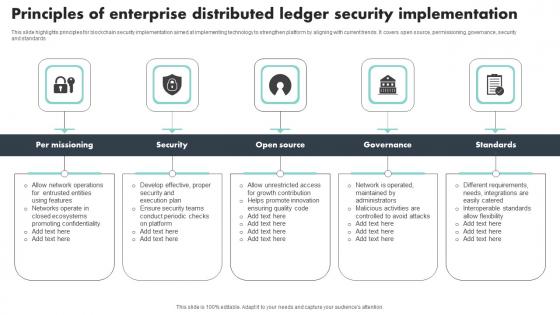
Principles Of Enterprise Distributed Ledger Security Implementation Brochure Pdf
This slide highlights principles for blockchain security implementation aimed at implementing technology to strengthen platform by aligning with current trends. It covers open source, permissioning, governance, security and standards Pitch your topic with ease and precision using this Principles Of Enterprise Distributed Ledger Security Implementation Brochure Pdf This layout presents information on Per Missioning, Security, Governance, Standards It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide highlights principles for blockchain security implementation aimed at implementing technology to strengthen platform by aligning with current trends. It covers open source, permissioning, governance, security and standards
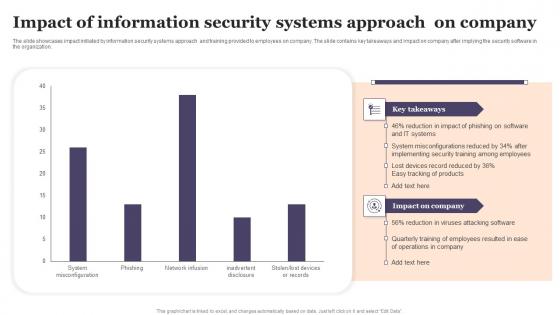
Impact Of Information Security Systems Approach On Company Designs Pdf
The slide showcases impact initiated by information security systems approach and training provided to employees on company. The slide contains key takeaways and impact on company after implying the security software in the organization. Showcasing this set of slides titled Impact Of Information Security Systems Approach On Company Designs Pdf The topics addressed in these templates are Impact Of Information, Security Systems, Approach On Company All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. The slide showcases impact initiated by information security systems approach and training provided to employees on company. The slide contains key takeaways and impact on company after implying the security software in the organization.
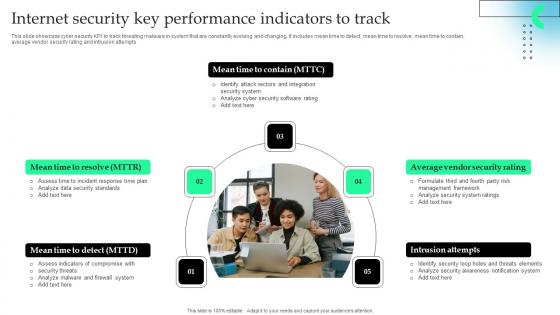
Internet Security Key Performance Indicators To Track Microsoft Pdf
This slide showcase cyber security KPI to track threating malware in system that are constantly evolving and changing. It includes mean time to detect, mean time to resolve, mean time to contain, average vendor security rating and intrusion attempts.Showcasing this set of slides titled Internet Security Key Performance Indicators To Track Microsoft Pdf The topics addressed in these templates are Firewall System, Security Standards, Identify Attack All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcase cyber security KPI to track threating malware in system that are constantly evolving and changing. It includes mean time to detect, mean time to resolve, mean time to contain, average vendor security rating and intrusion attempts.

Virtual Security Hazards Detection And Response Topics Pdf
This slide illustrates ways to detect cyber security risks that emerge in business organizations and provides techniques to respond to such attacks. The response techniques are to reduce access time, optimize operations of security centre, adopt proactive cybersecurity and set intruder traps Showcasing this set of slides titled Virtual Security Hazards Detection And Response Topics Pdf. The topics addressed in these templates are Security Centre, Access Time, Cybersecurity. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide illustrates ways to detect cyber security risks that emerge in business organizations and provides techniques to respond to such attacks. The response techniques are to reduce access time, optimize operations of security centre, adopt proactive cybersecurity and set intruder traps

Data Encryption Features In Application Security Testing Ppt Powerpoint Portrait
This slide outlines the characteristics of encryption in application security such as security, easy-to-use, document support, etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Data Encryption Features In Application Security Testing Ppt Powerpoint Portrait was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Data Encryption Features In Application Security Testing Ppt Powerpoint Portrait This slide outlines the characteristics of encryption in application security such as security, easy-to-use, document support, etc.
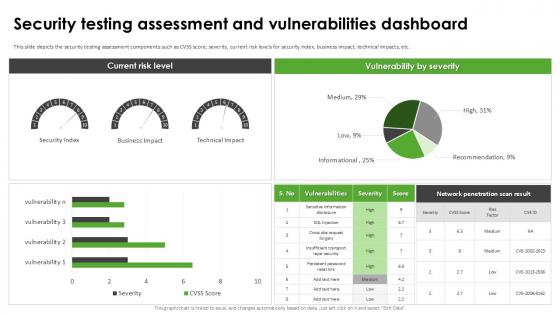
Security Testing Assessment Harnessing The World Of Ethical Ppt Example
This slide depicts the security testing assessment components such as CVSS score, severity, current risk levels for security index, business impact, technical impacts, etc. This Security Testing Assessment Harnessing The World Of Ethical Ppt Example is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Security Testing Assessment Harnessing The World Of Ethical Ppt Example features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide depicts the security testing assessment components such as CVSS score, severity, current risk levels for security index, business impact, technical impacts, etc.
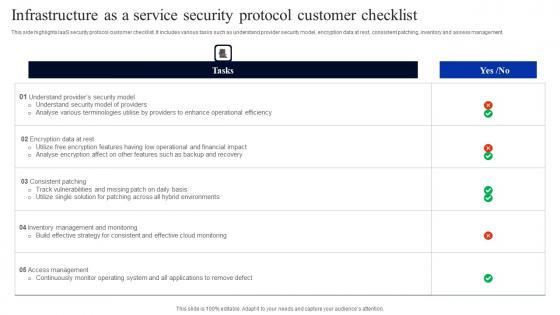
Infrastructure As A Service Security Protocol Customer Checklist Elements Pdf
This side highlights IaaS security protocol customer checklist. It includes various tasks such as understand provider security model, encryption data at rest, consistent patching, inventory and assess management. Showcasing this set of slides titled Infrastructure As A Service Security Protocol Customer Checklist Elements Pdf. The topics addressed in these templates are Encryption Data Rest, Consistent Patching, Inventory Assess Management. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This side highlights IaaS security protocol customer checklist. It includes various tasks such as understand provider security model, encryption data at rest, consistent patching, inventory and assess management.
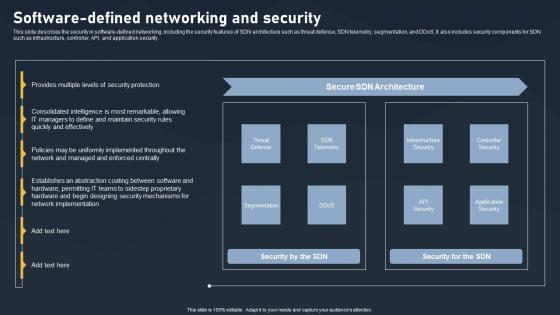
Software Defined Networking And Security SDN Building Blocks Portrait Pdf
This slide describes the security in software-defined networking, including the security features of SDN architecture such as threat defense, SDN telemetry, segmentation, and DDoS. It also includes security components for SDN such as infrastructure, controller, API, and application security.Whether you have daily or monthly meetings, a brilliant presentation is necessary. Software Defined Networking And Security SDN Building Blocks Portrait Pdf can be your best option for delivering a presentation. Represent everything in detail using Software Defined Networking And Security SDN Building Blocks Portrait Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide describes the security in software defined networking, including the security features of SDN architecture such as threat defense, SDN telemetry, segmentation, and DDoS. It also includes security components for SDN such as infrastructure, controller, API, and application security.
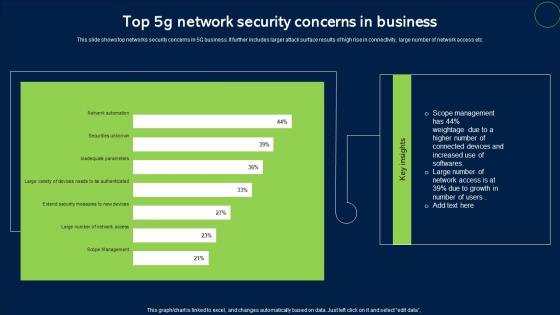
Top 5G Network Security Concerns In Business Sample Pdf
This slide shows top networks security concerns in 5G business. It further includes larger attack surface results of high rise in connectivity, large number of network access etc. Pitch your topic with ease and precision using this Top 5G Network Security Concerns In Business Sample Pdf. This layout presents information on Network Security, Concerns In Business. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide shows top networks security concerns in 5G business. It further includes larger attack surface results of high rise in connectivity, large number of network access etc.
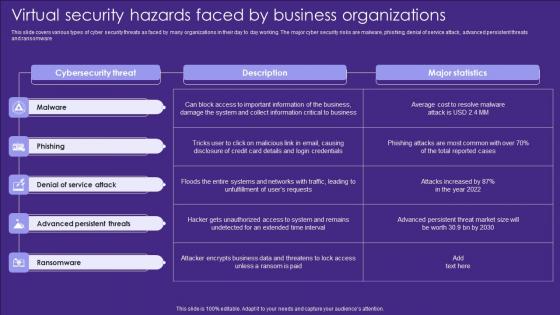
Virtual Security Hazards Faced By Business Organizations Sample Pdf
This slide covers various types of cyber security threats as faced by many organizations in their day to day working. The major cyber security risks are malware, phishing, denial of service attack, advanced persistent threats and ransomware Pitch your topic with ease and precision using this Virtual Security Hazards Faced By Business Organizations Sample Pdf. This layout presents information on Ransomware, Threats, Attack. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide covers various types of cyber security threats as faced by many organizations in their day to day working. The major cyber security risks are malware, phishing, denial of service attack, advanced persistent threats and ransomware
Data Security Strategic Agenda Checklist Icon Mockup Pdf
Pitch your topic with ease and precision using this Data Security Strategic Agenda Checklist Icon Mockup Pdf. This layout presents information on Data Security Strategic, Agenda Checklist. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our Data Security Strategic Agenda Checklist Icon Mockup Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.


 Continue with Email
Continue with Email

 Home
Home


































