Security

Lifeshield Security Projects Johannesburg In Powerpoint And Google Slides Cpb
Introducing our well-designed Lifeshield Security Projects Johannesburg In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Lifeshield Security Projects Johannesburg. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Lifeshield Security Projects Johannesburg In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
System Security Diagram In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled System Security Diagram In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits System Security Diagram that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our System Security Diagram In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Computer Security Incident Handling Optimizing Cybersecurity Framework Roadmap Designs PDF
Presenting this set of slides with name computer security incident handling optimizing cybersecurity framework roadmap designs pdf. The topics discussed in these slides are implement enterprise security program, implement control environment, implement security processes. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Measures And Ways To Mitigate Security Management Challenges Formats PDF
Deliver an awe inspiring pitch with this creative measures and ways to mitigate security management challenges formats pdf bundle. Topics like potential insider threats, external security breaches, security management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Essential Elements Of Security Monitoring Plan Background PDF
Deliver an awe inspiring pitch with this creative essential elements of security monitoring plan background pdf bundle. Topics like critical infrastructure, application security, cloud security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
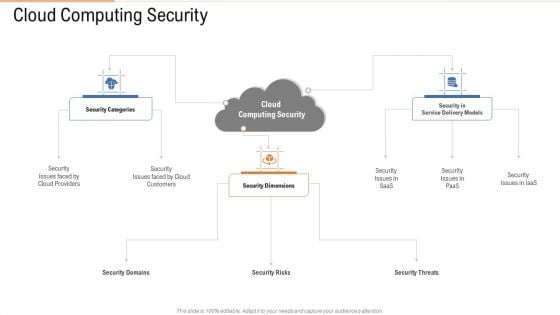
Cloud Computing Security Ppt Portfolio Background Images PDF
Presenting cloud computing security ppt portfolio background images pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like security dimensions, customers, security categories. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
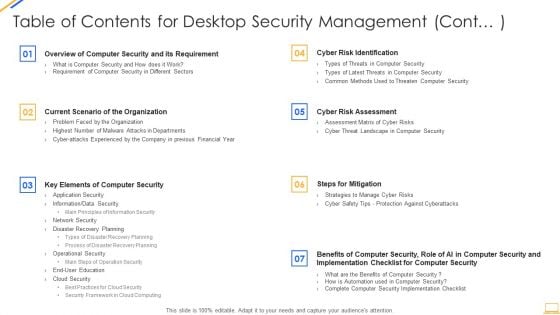
Table Of Contents For Desktop Security Management Cont Ideas PDF
Deliver an awe inspiring pitch with this creative table of contents for desktop security management cont ideas pdf bundle. Topics like security implementation, security budget, dashboards, communication can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
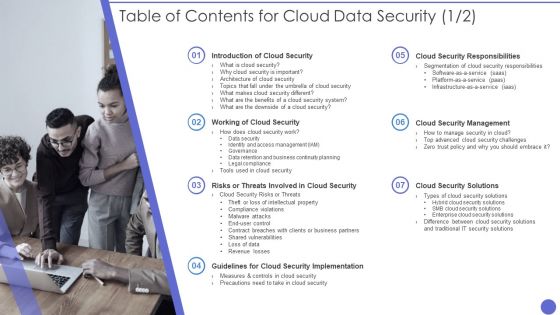
Table Of Contents For Cloud Data Security Formats PDF
Presenting Table Of Contents For Cloud Data Security Formats PDF to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like Cloud Security, Security System, Benefits. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
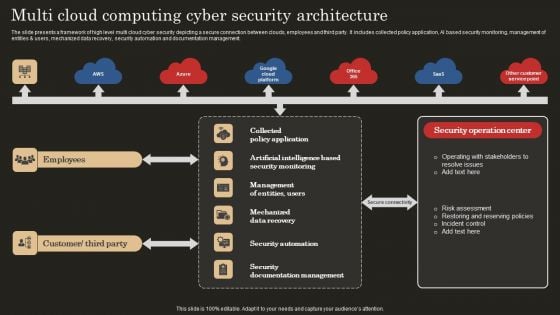
Multi Cloud Computing Cyber Security Architecture Microsoft PDF
The slide presents a framework of high level multi cloud cyber security depicting a secure connection between clouds, employees and third party. It includes collected policy application, AI based security monitoring, management of entities and users, mechanized data recovery, security automation and documentation management. Showcasing this set of slides titled Multi Cloud Computing Cyber Security Architecture Microsoft PDF. The topics addressed in these templates are Mechanized Data Recovery, Security Automation, Employees. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Agenda For Data Security In Cloud Computing Ppt Powerpoint
Present like a pro with Agenda For Data Security In Cloud Computing Ppt Powerpoint. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. Our Agenda For Data Security In Cloud Computing Ppt Powerpoint are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
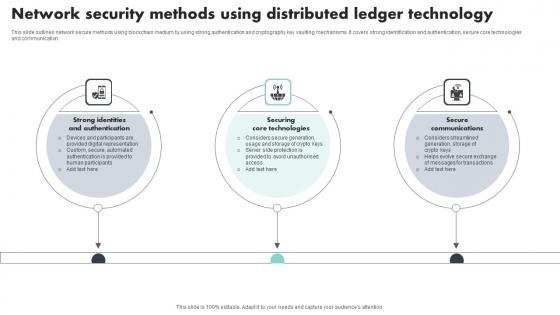
Network Security Methods Using Distributed Ledger Technology Introduction Pdf
This slide outlines network secure methods using blockchain medium by using strong authentication and cryptography key vaulting mechanisms. It covers strong identification and authentication, secure core technologies and communication Pitch your topic with ease and precision using this Network Security Methods Using Distributed Ledger Technology Introduction Pdf This layout presents information on Strong Identities And Authentication, Securing Core Technologies It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide outlines network secure methods using blockchain medium by using strong authentication and cryptography key vaulting mechanisms. It covers strong identification and authentication, secure core technologies and communication
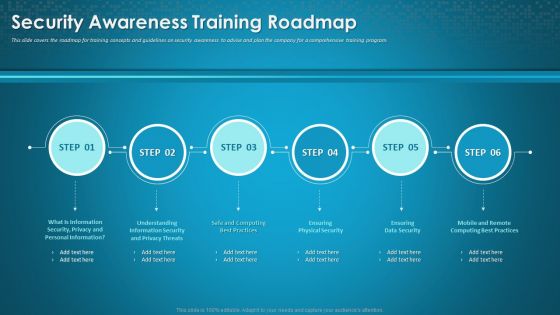
Organizational Network Staff Learning Security Awareness Training Roadmap Sample PDF
This slide covers the roadmap for training concepts and guidelines on security awareness to advise and plan the company for a comprehensive training program. Presenting organizational network staff learning security awareness training roadmap sample pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like ensuring data security, information security and privacy threats, ensuring physical security. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.

Organizational Network Staff Learning Security Awareness Program Checklist Background PDF
This slide covers the Checklist that will help organizations prepare and implement their safety awareness training. The details listed below can be used to promote preparation and education planning in the area of security awareness. Presenting organizational network staff learning security awareness program checklist background pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like security awareness program, implementing security awareness, sustaining security awareness. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.
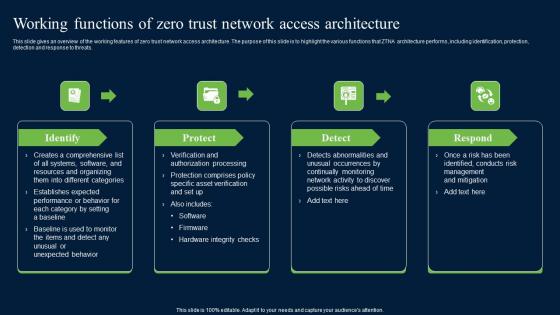
Working Functions Of Zero Trust Network Access Security Infographics Pdf
This slide gives an overview of the working features of zero trust network access architecture. The purpose of this slide is to highlight the various functions that ZTNA architecture performs, including identification, protection, detection and response to threats. Create an editable Working Functions Of Zero Trust Network Access Security Infographics Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Working Functions Of Zero Trust Network Access Security Infographics Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide gives an overview of the working features of zero trust network access architecture. The purpose of this slide is to highlight the various functions that ZTNA architecture performs, including identification, protection, detection and response to threats.
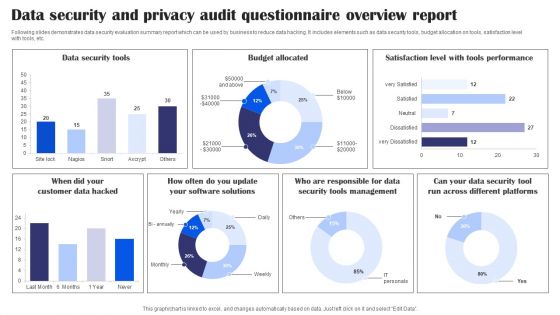
Data Security And Privacy Audit Questionnaire Overview Report Survey SS
Following slides demonstrates data security evaluation summary report which can be used by business to reduce data hacking. It includes elements such as data security tools, budget allocation on tools, satisfaction level with tools, etc. Pitch your topic with ease and precision using this Data Security And Privacy Audit Questionnaire Overview Report Survey SS. This layout presents information on Data Security Tools, Budget Allocated, Tools Performance, Data Security Tools Management. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
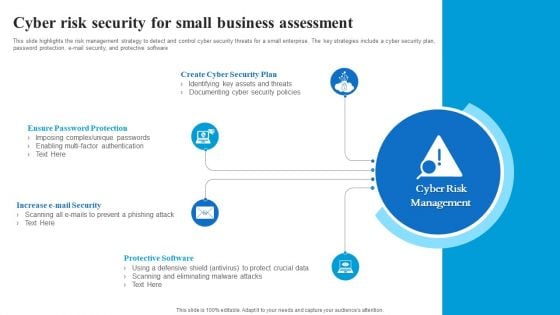
Cyber Risk Security For Small Business Assessment Brochure PDF
This slide highlights the risk management strategy to detect and control cyber security threats for a small enterprise. The key strategies include a cyber security plan, password protection, e-mail security, and protective software. Presenting Cyber Risk Security For Small Business Assessment Brochure PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Create Cyber Security Plan, Ensure Password Protection, Protective Software. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
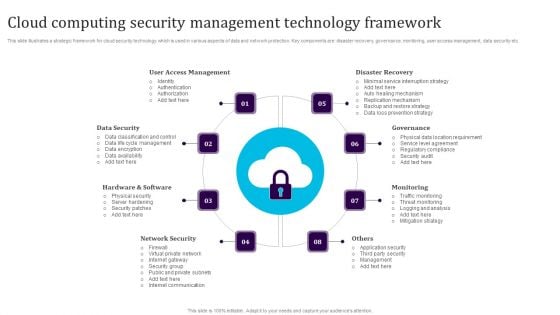
Cloud Computing Security Management Technology Framework Elements PDF
This slide illustrates a strategic framework for cloud security technology which is used in various aspects of data and network protection. Key components are disaster recovery, governance, monitoring, user access management, data security etc. Persuade your audience using this Cloud Computing Security Management Technology Framework Elements PDF. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including User Access Management, Data Security, Hardware And Software, Network Security, Monitoring, Governance. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Web Development What Is The Cyber Security Designs PDF
This slide represents how data security keeps in mind while developing websites, and security measures are already added to designed websites to protect them from malicious attacks.Presenting Web Development What Is The Cyber Security Designs PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Categories Of Cyber, Operational Security, Includes Network Security In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
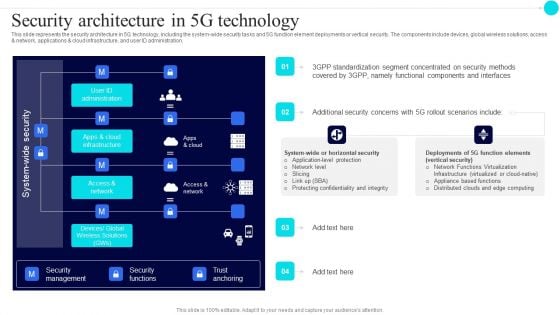
Security Architecture In 5G Technology 5G Functional Architecture Topics PDF
This slide represents the security architecture in 5G technology, including the system-wide security tasks and 5G function element deployments or vertical security. The components include devices, global wireless solutions, access and network, applications and cloud infrastructure, and user ID administration.Deliver an awe inspiring pitch with this creative Security Architecture In 5G Technology 5G Functional Architecture Topics PDF bundle. Topics like Standardization Segment, Concentrated Security, Components Interfaces can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Companys Data Safety Recognition Security Awareness Program Checklist Portrait PDF
This slide covers the Checklist that will help organizations prepare and implement their safety awareness training. The details listed below can be used to promote preparation and education planning in the area of security awareness. This is a companys data safety recognition security awareness program checklist portrait pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like implementing security awareness, security awareness program, sustaining security awareness. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
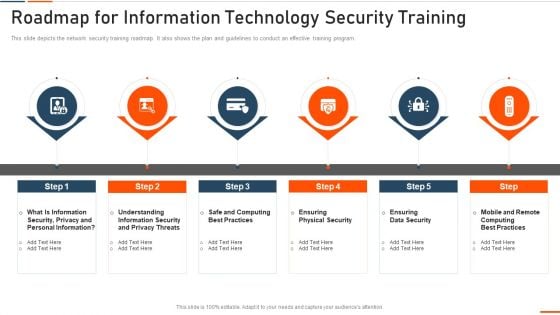
Roadmap For Information Technology Security Training Ppt Ideas Influencers PDF
This slide depicts the network security training roadmap. It also shows the plan and guidelines to conduct an effective training program. This is a roadmap for roadmap for information technology security training ppt ideas influencers pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like rmation security, computing best practices, physical security, data security . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Essential Measures For Business Cyber Security Assessment Plan Rules PDF
This slide demonstrates the safety measures in a business security plan that helps in decreasing the frequency of security threats data hacks, information breaches etc. The measures include handy backups, multi layer security, protective software, and employee training. Presenting Essential Measures For Business Cyber Security Assessment Plan Rules PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Manage Handy Backups, Incorporate Multi Layer Security, Train Employees, Invest In Protective Software. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
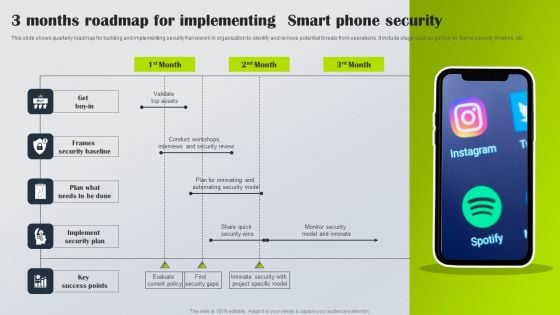
3 Months Roadmap For Implementing Smart Phone Security Information PDF
This slide shows quarterly roadmap for building and implementing security framework in organization to identify and remove potential threats from operations. It include stage such as get buy-in, frame security timeline, etc. Presenting 3 Months Roadmap For Implementing Smart Phone Security Information PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Get Buy In, Frames Security Baseline, Implement Security Plan. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
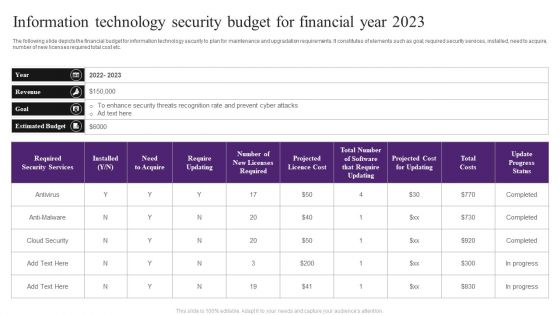
Information Technology Security Budget For Financial Year 2023 Slides PDF
The following slide depicts the financial budget for information technology security to plan for maintenance and upgradation requirements. It constitutes of elements such as goal, required security services, installed, need to acquire, number of new licenses required total cost etc. Showcasing this set of slides titled Information Technology Security Budget For Financial Year 2023 Slides PDF. The topics addressed in these templates are Enhance Security, Estimated Budget, Cloud Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
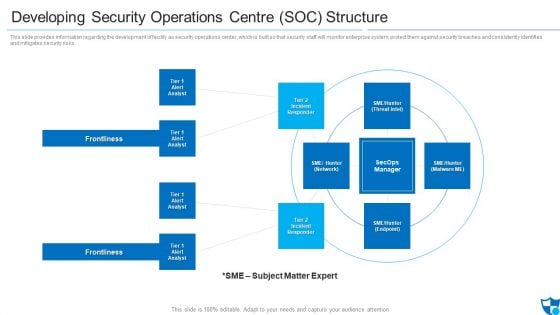
Developing Security Operations Centre SOC Structure Microsoft PDF
This slide provides information regarding the development of facility as security operations center, which is built so that security staff will monitor enterprise system, protect them against security breaches and consistently identifies and mitigates security risks. Presenting developing security operations centre soc structure microsoft pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like incident responder, tier 2 incident responder, frontlines. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
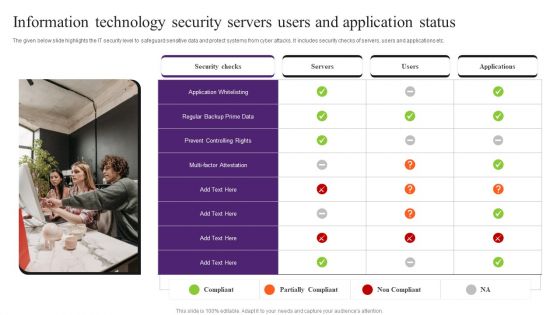
Information Technology Security Servers Users And Application Status Pictures PDF
The given below slide highlights the IT security level to safeguard sensitive data and protect systems from cyber attacks. It includes security checks of servers, users and applications etc. Presenting Information Technology Security Servers Users And Application Status Pictures PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Application Whitelisting, Security Checks, Information Technology Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
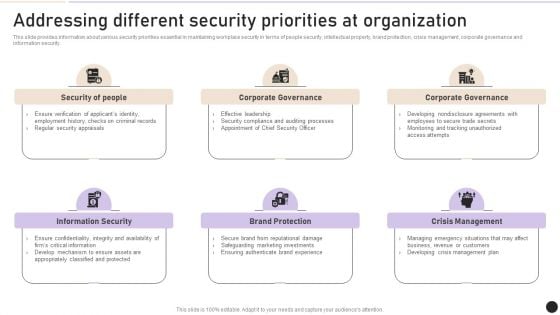
Addressing Different Security Priorities At Organization Clipart PDF
This slide provides information about various security priorities essential in maintaining workplace security in terms of people security, intellectual property, brand protection, crisis management, corporate governance and information security. Find a pre designed and impeccable Addressing Different Security Priorities At Organization Clipart PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Data Breach Prevention Recognition Security Awareness Program Checklist Template PDF
This slide covers the Checklist that will help organizations prepare and implement their safety awareness training. The details listed below can be used to promote preparation and education planning in the area of security awareness. This is a data breach prevention recognition security awareness program checklist template pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like implementing security awareness, sustaining security awareness, document security awareness program. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Data Breach Prevention Recognition Security Awareness Program Timeline Inspiration PDF
This slide covers the security awareness implementation timeline for the organization cyber security training plan with conducting a simulated phishing exercise and system vendor risk assessment. Deliver and pitch your topic in the best possible manner with this data breach prevention recognition security awareness program timeline inspiration pdf. Use them to share invaluable insights on security awareness, implementation timeline, organization, cyber security training plan, risk assessment and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Estimated Security Management Plan Critical Success Factors Microsoft PDF
This slide shows some of the estimated future IT Security Management Critical Success Factors of the company prior to the proactive measures taken by the company to mitigate security management problems and implementing an advanced Information Security Management System. Deliver and pitch your topic in the best possible manner with this estimated security management plan critical success factors microsoft pdf. Use them to share invaluable insights on estimated security management plan critical success factors and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Current Security Management Plan Critical Success Factors Formats PDF
This slide shows some of the current IT Security Management Critical Success Factors of the company prior to the proactive measures taken by the company to mitigate security management problems and implementing an advanced Information Security Management System. Deliver and pitch your topic in the best possible manner with this current security management plan critical success factors formats pdf. Use them to share invaluable insights on security, management, implementation and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Estimated Security Management Plan Critical Success Factors Designs PDF
This slide shows some of the estimated future IT Security Management Critical Success Factors of the company prior to the proactive measures taken by the company to mitigate security management problems and implementing an advanced Information Security Management System. Deliver and pitch your topic in the best possible manner with this estimated security management plan critical success factors designs pdf. Use them to share invaluable insights on security, management, implementation and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
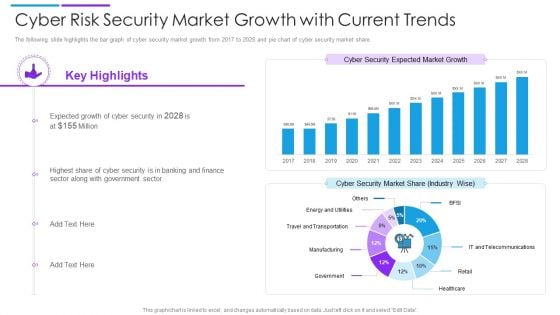
Cyber Risk Security Market Growth With Current Trends Summary PDF
The following slide highlights the bar graph of cyber security market growth from 2017 to 2028 and pie chart of cyber security market share. Showcasing this set of slides titled cyber risk security market growth with current trends summary pdf. The topics addressed in these templates are cyber security market share, cyber security expected market growth, banking and finance. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Comparison Of Various Security Awareness Training Software Elements PDF
The purpose of this slide is to drawn comparison of multiple software which can be used to provide cyber security training to the key stakeholders. Information covered in this slide is related to phishing simulations, security reporting, individualized security training plan etc. Deliver and pitch your topic in the best possible manner with this Comparison Of Various Security Awareness Training Software Elements PDF. Use them to share invaluable insights on Individualized Security, Industry Specific, Deployment and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
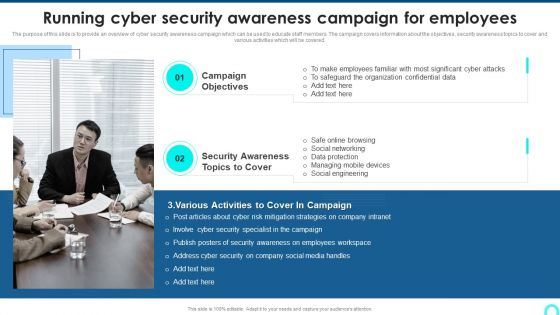
Running Cyber Security Awareness Campaign For Employees Clipart PDF
The purpose of this slide is to provide an overview of cyber security awareness campaign which can be used to educate staff members. The campaign covers information about the objectives, security awareness topics to cover and various activities which will be covered.Presenting Running Cyber Security Awareness Campaign For Employees Clipart PDF to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like Campaign Objectives, Security Awareness, Security Awareness. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
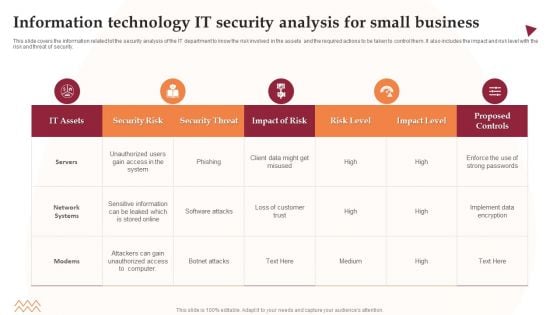
Information Technology IT Security Analysis For Small Business Information PDF
This slide covers the information related tot the security analysis of the IT department to know the risk involved in the assets and the required actions to be taken to control them. It also includes the impact and risk level with the risk and threat of security. Showcasing this set of slides titled Information Technology IT Security Analysis For Small Business Information PDF. The topics addressed in these templates are Security Risk, Security Threat, Impact Of Risk. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Security Threat Management Strategy With Strategies Ideas PDF
This slide focuses on the security risk mitigation plan which covers security components, vulnerabilities and mitigation strategies such as administrative, physical, technical and organizational safeguards with conducting workforce training, installing alarm systems, etc. Showcasing this set of slides titled Security Threat Management Strategy With Strategies Ideas PDF. The topics addressed in these templates are Security Component, Examples Of Vulnerabilities, Security Mitigation Strategies. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Addressing The Various Security Incidents And Attacks Icons PDF
Purpose of this slide is to educate team members about different security incidents and attacks. It includes information about traditional security incidents, cyber security attacks and common techniques.Create an editable Addressing The Various Security Incidents And Attacks Icons PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Addressing The Various Security Incidents And Attacks Icons PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
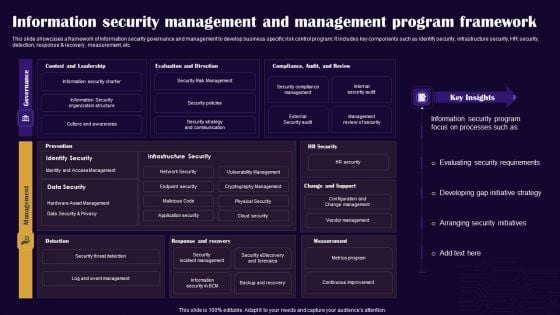
Information Security Management And Management Program Framework Inspiration PDF
This slide showcases a framework of information security governance and management to develop business specific risk control program. It includes key components such as identify security, infrastructure security, HR security, detection, response and recovery, measurement, etc. Showcasing this set of slides titled Information Security Management And Management Program Framework Inspiration PDF. The topics addressed in these templates are Governance, Management, Key Insights All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
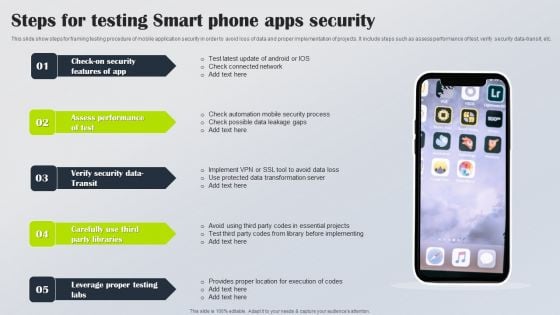
Steps For Testing Smart Phone Apps Security Inspiration PDF
This slide show steps for framing testing procedure of mobile application security in order to avoid loss of data and proper implementation of projects. It include steps such as assess performance of test, verify security data transit, etc. Presenting Steps For Testing Smart Phone Apps Security Inspiration PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Check Security Features App, Assess Performance Test, Verify Security Data Transit. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
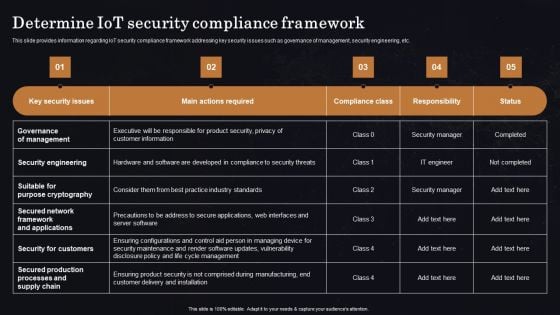
Determine Iot Security Compliance Framework Ppt Professional Vector PDF
This slide provides information regarding IoT security compliance framework addressing key security issues such as governance of management, security engineering, etc. Get a simple yet stunning designed Determine Iot Security Compliance Framework Ppt Professional Vector PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Determine Iot Security Compliance Framework Ppt Professional Vector PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Agenda For Workplace Safety Protocol And Security Practices Information Pdf
Slidegeeks is here to make your presentations a breeze with Agenda For Workplace Safety Protocol And Security Practices Information Pdf With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first Our Agenda For Workplace Safety Protocol And Security Practices Information Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
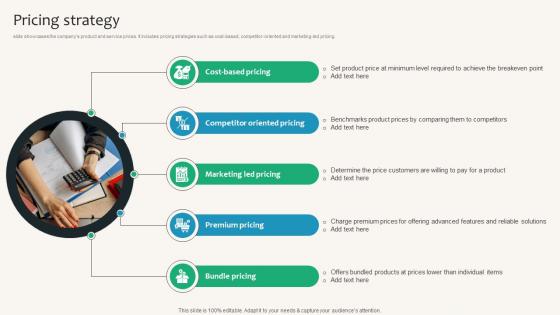
Pricing Strategy Security Service Provider Business Model BMC SS V
slide showcases the companys product and service prices. It includes pricing strategies such as cost-based, competitor-oriented and marketing-led pricing. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Pricing Strategy Security Service Provider Business Model BMC SS V. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Pricing Strategy Security Service Provider Business Model BMC SS V today and make your presentation stand out from the rest slide showcases the companys product and service prices. It includes pricing strategies such as cost-based, competitor-oriented and marketing-led pricing.
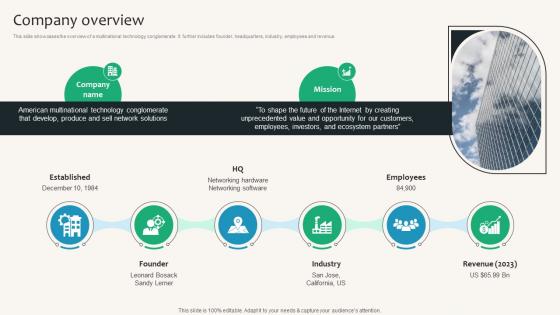
Company Overview Security Service Provider Business Model BMC SS V
This slide showcases the overview of a multinational technology conglomerate. It further includes founder, headquarters, industry, employees and revenue. Create an editable Company Overview Security Service Provider Business Model BMC SS V that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Company Overview Security Service Provider Business Model BMC SS V is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide showcases the overview of a multinational technology conglomerate. It further includes founder, headquarters, industry, employees and revenue.
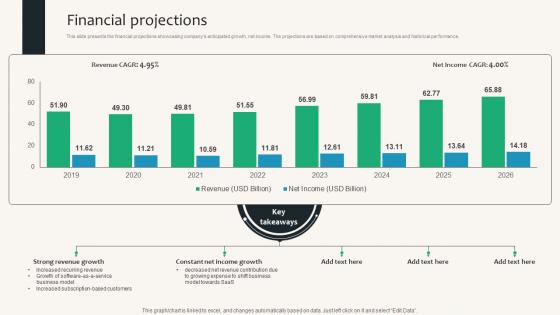
Financial Projections Security Service Provider Business Model BMC SS V
This slide presents the financial projections showcasing companys anticipated growth, net income. The projections are based on comprehensive market analysis and historical performance. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Financial Projections Security Service Provider Business Model BMC SS V a try. Our experts have put a lot of knowledge and effort into creating this impeccable Financial Projections Security Service Provider Business Model BMC SS V. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide presents the financial projections showcasing companys anticipated growth, net income. The projections are based on comprehensive market analysis and historical performance.
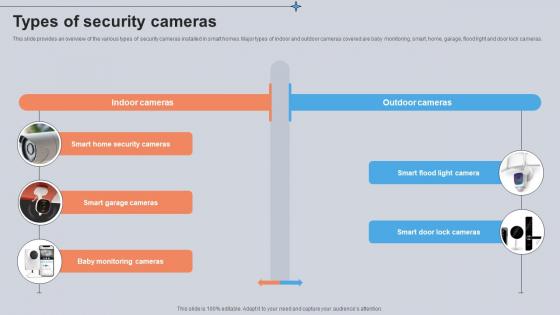
Types Of Security Cameras Utilizing Smart Appliances IoT SS V
This slide provides an overview of the various types of security cameras installed in smart homes. Major types of indoor and outdoor cameras covered are baby monitoring, smart, home, garage, flood light and door lock cameras. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Types Of Security Cameras Utilizing Smart Appliances IoT SS V. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Types Of Security Cameras Utilizing Smart Appliances IoT SS V today and make your presentation stand out from the rest This slide provides an overview of the various types of security cameras installed in smart homes. Major types of indoor and outdoor cameras covered are baby monitoring, smart, home, garage, flood light and door lock cameras.
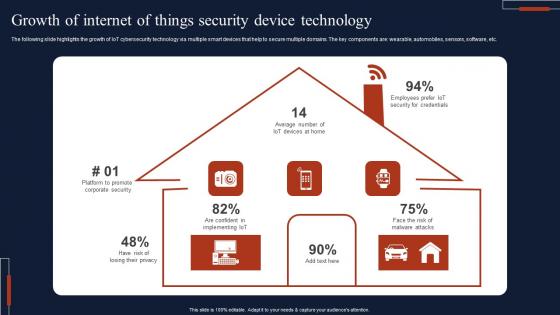
Growth Of Internet Of Things Security Device Technology Professional Pdf
The following slide highlights the growth of IoT cybersecurity technology via multiple smart devices that help to secure multiple domains. The key components are wearable, automobiles, sensors, software, etc. Pitch your topic with ease and precision using this Growth Of Internet Of Things Security Device Technology Professional Pdf This layout presents information on Growth Of Internet, Things Security, Device Technology It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. The following slide highlights the growth of IoT cybersecurity technology via multiple smart devices that help to secure multiple domains. The key components are wearable, automobiles, sensors, software, etc.
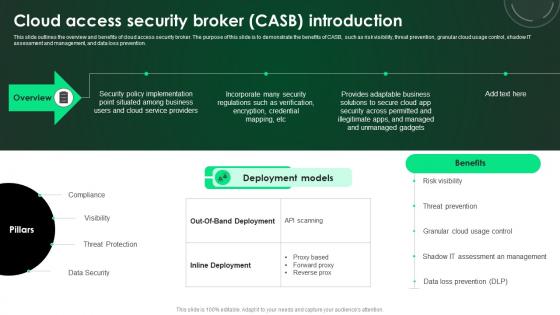
CASB 2 0 IT Cloud Access Security Broker CASB Introduction
This slide outlines the overview and benefits of cloud access security broker. The purpose of this slide is to demonstrate the benefits of CASB, such as risk visibility, threat prevention, granular cloud usage control, shadow IT assessment and management, and data loss prevention. This CASB 2 0 IT Cloud Access Security Broker CASB Introduction is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The CASB 2 0 IT Cloud Access Security Broker CASB Introduction features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide outlines the overview and benefits of cloud access security broker. The purpose of this slide is to demonstrate the benefits of CASB, such as risk visibility, threat prevention, granular cloud usage control, shadow IT assessment and management, and data loss prevention.
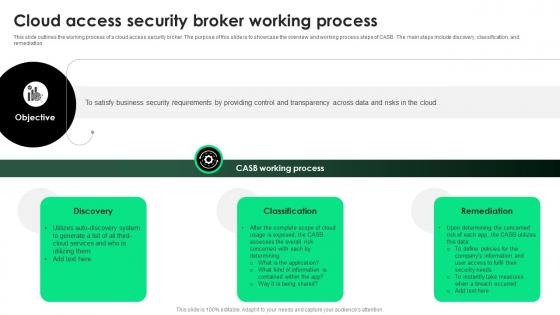
CASB 2 0 IT Cloud Access Security Broker Working Process
This slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, and remediation. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download CASB 2 0 IT Cloud Access Security Broker Working Process to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the CASB 2 0 IT Cloud Access Security Broker Working Process. This slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, and remediation.
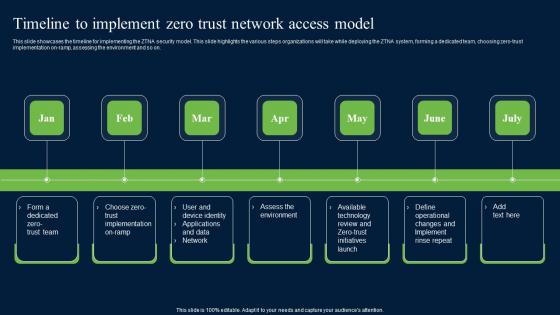
Timeline To Implement Zero Trust Network Security Themes Pdf
This slide showcases the timeline for implementing the ZTNA security model. This slide highlights the various steps organizations will take while deploying the ZTNA system, forming a dedicated team, choosing zero-trust implementation on-ramp, assessing the environment and so on. Slidegeeks is here to make your presentations a breeze with Timeline To Implement Zero Trust Network Security Themes Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide showcases the timeline for implementing the ZTNA security model. This slide highlights the various steps organizations will take while deploying the ZTNA system, forming a dedicated team, choosing zero-trust implementation on-ramp, assessing the environment and so on.
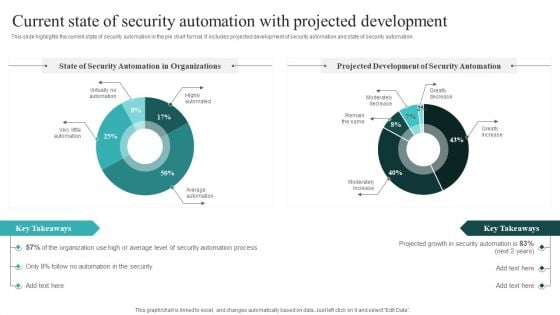
Current State Of Security Automation With Projected Development Slides PDF
This slide highlights the current state of security automation in the pie chart format. It includes projected development of security automation and state of security automation. If you are looking for a format to display your unique thoughts, then the professionally designed IT Security Automation Systems Guide Different Security Automation Tools With Pros And Cons Summary PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download IT Security Automation Systems Guide Different Security Automation Tools With Pros And Cons Summary PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
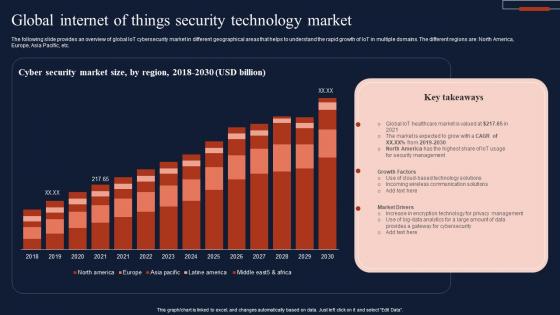
Global Internet Of Things Security Technology Market Infographics Pdf
The following slide provides an overview of global IoT cybersecurity market in different geographical areas that helps to understand the rapid growth of IoT in multiple domains. The different regions are North America, Europe, Asia Pacific, etc. Showcasing this set of slides titled Global Internet Of Things Security Technology Market Infographics Pdf The topics addressed in these templates are Cyber Security, Market Size, Technology Market All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. The following slide provides an overview of global IoT cybersecurity market in different geographical areas that helps to understand the rapid growth of IoT in multiple domains. The different regions are North America, Europe, Asia Pacific, etc.
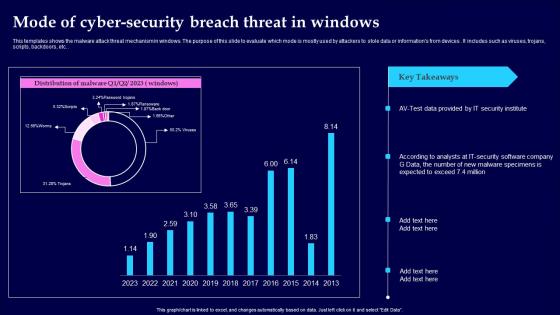
Mode Of Cyber Security Breach Threat In Windows Clipart Pdf
This templates shows the malware attack threat mechanism in windows. The purpose of this slide to evaluate which mode is mostly used by attackers to stole data or informations from devices. It includes such as viruses, trojans, scripts, backdoors, etc. Showcasing this set of slides titled Mode Of Cyber Security Breach Threat In Windows Clipart Pdf The topics addressed in these templates are Mode Of Cyber Security, Threat In Windows All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This templates shows the malware attack threat mechanism in windows. The purpose of this slide to evaluate which mode is mostly used by attackers to stole data or informations from devices. It includes such as viruses, trojans, scripts, backdoors, etc.

Top Countries Effect By Cyber Security Breach Background Pdf
This templates shows the top countries impacted by malware attacks. The purpose of this slide which country is most effected by malware attack what precaution they should take to reduce the numbers of attacks in futures. it includes various countries such as sweden, japan , china, etc. Pitch your topic with ease and precision using this Top Countries Effect By Cyber Security Breach Background Pdf This layout presents information on Malware Attack, Countries Effect, Cyber Security Breach It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This templates shows the top countries impacted by malware attacks. The purpose of this slide which country is most effected by malware attack what precaution they should take to reduce the numbers of attacks in futures. it includes various countries such as sweden, japan , china, etc.
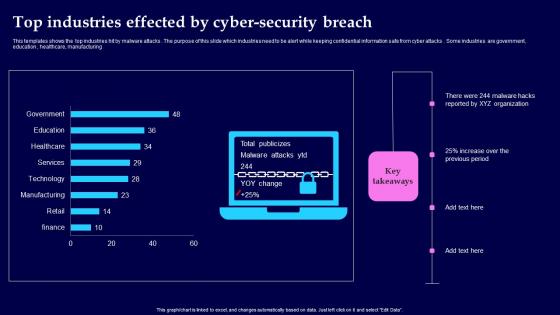
Top Industries Effected By Cyber Security Breach Background Pdf
This templates shows the top industries hit by malware attacks. The purpose of this slide which industries need to be alert while keeping confidential information safe from cyber attacks. Some industries are government, education, healthcare, manufacturing Showcasing this set of slides titled Top Industries Effected By Cyber Security Breach Background Pdf The topics addressed in these templates are Top Industries Effected, Cyber Security Breach All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This templates shows the top industries hit by malware attacks. The purpose of this slide which industries need to be alert while keeping confidential information safe from cyber attacks. Some industries are government, education, healthcare, manufacturing
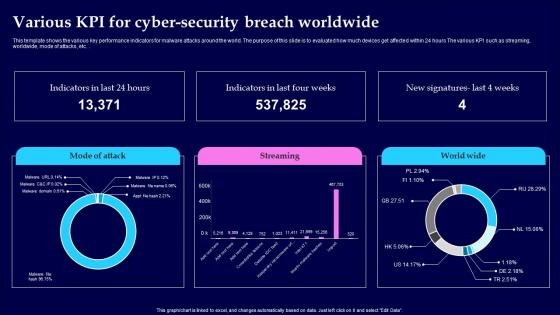
Various KPI For Cyber Security Breach Worldwide Pictures Pdf
This template shows the various key performance indicators for malware attacks around the world. The purpose of this slide is to evaluated how much devices get affected within 24 hours The various KPI such as streaming, worldwide, mode of attacks, etc. Showcasing this set of slides titled Various KPI For Cyber Security Breach Worldwide Pictures Pdf The topics addressed in these templates are Cyber Security Breach, Worldwide All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This template shows the various key performance indicators for malware attacks around the world. The purpose of this slide is to evaluated how much devices get affected within 24 hours The various KPI such as streaming, worldwide, mode of attacks, etc.
Security Breach Events Tracking Dashboard Data Fortification Strengthening Defenses
This slide represents the dashboard to track data breach attacks. The purpose of this slide is to provide a graphical representation of cyber attacks that occurred in a specific period. It also depicts the overview of different types of attacks.Create an editable Security Breach Events Tracking Dashboard Data Fortification Strengthening Defenses that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Security Breach Events Tracking Dashboard Data Fortification Strengthening Defenses is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide represents the dashboard to track data breach attacks. The purpose of this slide is to provide a graphical representation of cyber attacks that occurred in a specific period. It also depicts the overview of different types of attacks.
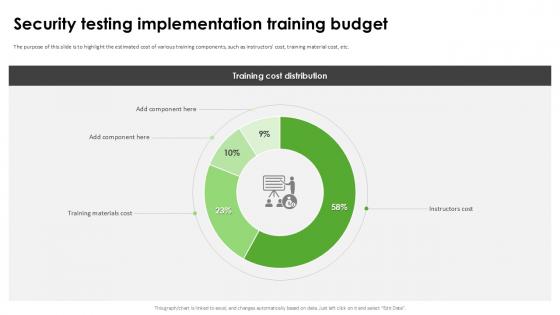
Security Testing Implementation Harnessing The World Of Ethical Ppt Presentation
The purpose of this slide is to highlight the estimated cost of various training components, such as instructors cost, training material cost, etc. Explore a selection of the finest Security Testing Implementation Harnessing The World Of Ethical Ppt Presentation here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Security Testing Implementation Harnessing The World Of Ethical Ppt Presentation to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. The purpose of this slide is to highlight the estimated cost of various training components, such as instructors cost, training material cost, etc.
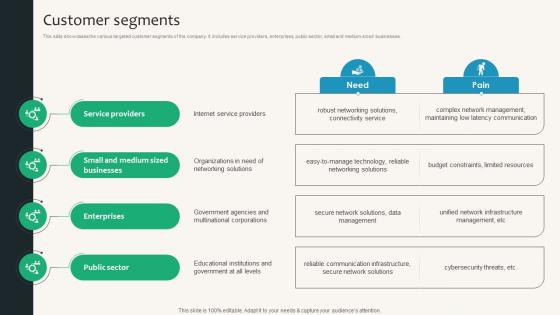
Customer Segments Security Service Provider Business Model BMC SS V
This slide showcases the various targeted customer segments of the company. It includes service providers, enterprises, public sector, small and medium-sized businesses. There are so many reasons you need a Customer Segments Security Service Provider Business Model BMC SS V. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide showcases the various targeted customer segments of the company. It includes service providers, enterprises, public sector, small and medium-sized businesses.
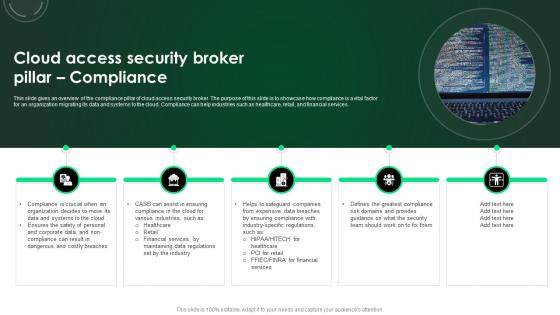
CASB 2 0 IT Cloud Access Security Broker Pillar Compliance
This slide gives an overview of the compliance pillar of cloud access security broker. The purpose of this slide is to showcase how compliance is a vital factor for an organization migrating its data and systems to the cloud. Compliance can help industries such as healthcare, retail, and financial services. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download CASB 2 0 IT Cloud Access Security Broker Pillar Compliance from Slidegeeks and deliver a wonderful presentation. This slide gives an overview of the compliance pillar of cloud access security broker. The purpose of this slide is to showcase how compliance is a vital factor for an organization migrating its data and systems to the cloud. Compliance can help industries such as healthcare, retail, and financial services.


 Continue with Email
Continue with Email

 Home
Home


































