Security
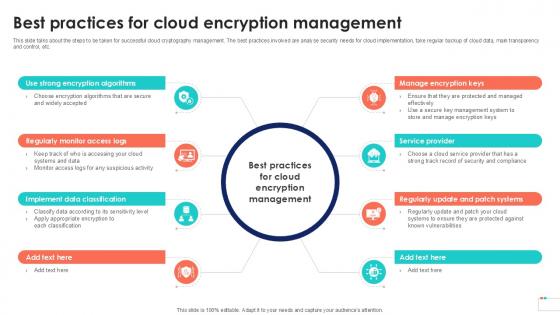
Best Practices For Cloud Encryption Data Security In Cloud Computing Ppt Template
This slide talks about the steps to be taken for successful cloud cryptography management. The best practices involved are analyse security needs for cloud implementation, take regular backup of cloud data, main transparency and control, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Best Practices For Cloud Encryption Data Security In Cloud Computing Ppt Template. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Best Practices For Cloud Encryption Data Security In Cloud Computing Ppt Template today and make your presentation stand out from the rest This slide talks about the steps to be taken for successful cloud cryptography management. The best practices involved are analyse security needs for cloud implementation, take regular backup of cloud data, main transparency and control, etc.

Cryptographic Algorithms Used In Data Security In Cloud Computing Ppt Slide
This slide talks about algorithms used for implementing cryptography in data security. The purpose of this slide is to explain the different implementation steps. The techniques discussed are RSA Rivest, Shamir, Adleman cryptographic algorithm and Data Encryption Standard algorithm. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Cryptographic Algorithms Used In Data Security In Cloud Computing Ppt Slide was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Cryptographic Algorithms Used In Data Security In Cloud Computing Ppt Slide This slide talks about algorithms used for implementing cryptography in data security. The purpose of this slide is to explain the different implementation steps. The techniques discussed are RSA Rivest, Shamir, Adleman cryptographic algorithm and Data Encryption Standard algorithm.

Methods Used By Symmetric Algorithm Data Security In Cloud Computing Ppt Sample
This slide talks about the various applications of symmetric algorithm in cloud cryptography. The purpose of this slide is to explain how this technique can help in providing security in cloud computing. These are encryption, access control, key management, etc. Create an editable Methods Used By Symmetric Algorithm Data Security In Cloud Computing Ppt Sample that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Methods Used By Symmetric Algorithm Data Security In Cloud Computing Ppt Sample is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide talks about the various applications of symmetric algorithm in cloud cryptography. The purpose of this slide is to explain how this technique can help in providing security in cloud computing. These are encryption, access control, key management, etc.
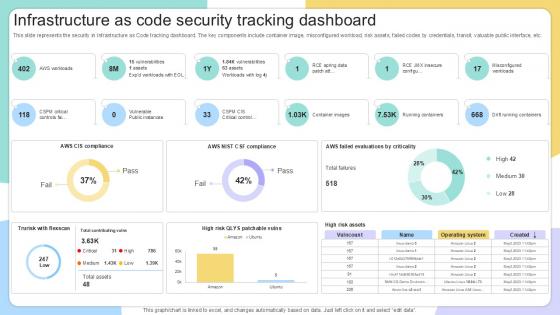
Infrastructure As Code Security IAC Tools For Performance Analysis PPT Slide
This slide represents the security in Infrastructure as Code tracking dashboard. The key components include container image, misconfigured workload, risk assets, failed codes by credentials, transit, valuable public interface, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Infrastructure As Code Security IAC Tools For Performance Analysis PPT Slide to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Infrastructure As Code Security IAC Tools For Performance Analysis PPT Slide. This slide represents the security in Infrastructure as Code tracking dashboard. The key components include container image, misconfigured workload, risk assets, failed codes by credentials, transit, valuable public interface, etc.

Industry Laws And Regulations In Global Security Industry PPT Slide IR SS V
The slide highlights industry laws and regulations in Defense industry. It is to ensure market stability, consumer protection and foster innovation while mitigating risks. It includes regulatory compliance and intellectual property, legal and regulatory. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Industry Laws And Regulations In Global Security Industry PPT Slide IR SS V template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Industry Laws And Regulations In Global Security Industry PPT Slide IR SS V that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers The slide highlights industry laws and regulations in Defense industry. It is to ensure market stability, consumer protection and foster innovation while mitigating risks. It includes regulatory compliance and intellectual property, legal and regulatory.

Computer Keyboard With Security Keys PowerPoint Templates And PowerPoint Themes 0912
Computer Keyboard With Security Keys PowerPoint Templates And PowerPoint Themes 0912-Microsoft Powerpoint Templates and Background with Computer keyboard with security key Encourage your community to take action. Get them to back the cause you champion.
Security Systems Smart Grid Training Ppt PowerPoint Presentation Visual Aids Example File
This is a security systems smart grid training ppt powerpoint presentation visual aids example file. This is a ten stage process. The stages in this process are security systems, smart grid training.
Marketing Communications Collaboration Business Security System Process Management Ppt PowerPoint Presentation Graphics
This is a marketing communications collaboration business security system process management ppt powerpoint presentation graphics. This is a five stage process. The stages in this process are marketing communications collaboration, business security system, process management.
lead generation industry security outsourcing firms professional development ppt powerpoint presentation styles guide
This is a lead generation industry security outsourcing firms professional development ppt powerpoint presentation styles guide. This is a four stage process. The stages in this process are lead generation industry, security outsourcing firms, professional development.
Project Portfolio Management Digital Security Management Financial Planning Ppt PowerPoint Presentation Inspiration Icons
This is a project portfolio management digital security management financial planning ppt powerpoint presentation inspiration icons. This is a five stage process. The stages in this process are project portfolio management, digital security management, financial planning.
Business Business Relationship Marketing Monitor Employee Security Outsourcing Ppt PowerPoint Presentation Portfolio Graphics Template
This is a business business relationship marketing monitor employee security outsourcing ppt powerpoint presentation portfolio graphics template. This is a four stage process. The stages in this process are business business relationship marketing, monitor employee, security outsourcing.
Mobile Device Security Best Practices Ppt PowerPoint Presentation Outline Rules Cpb
This is a mobile device security best practices ppt powerpoint presentation outline rules cpb. This is a four stage process. The stages in this process are mobile device security best practices.
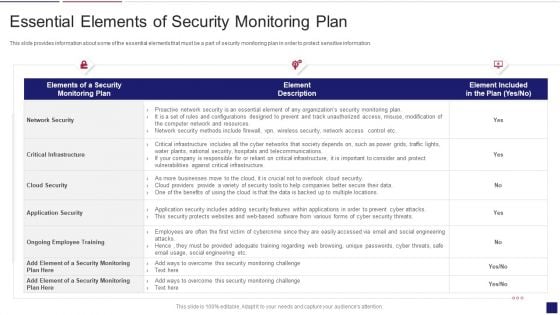
Continuous Development Evaluation Plan Eliminate Cyber Attacks Essential Elements Of Security Monitoring Elements PDF
This slide provides information about some of the essential elements that must be a part of security monitoring plan in order to protect sensitive information. Deliver an awe inspiring pitch with this creative continuous development evaluation plan eliminate cyber attacks essential elements of security monitoring elements pdf bundle. Topics like network security, critical infrastructure, application security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
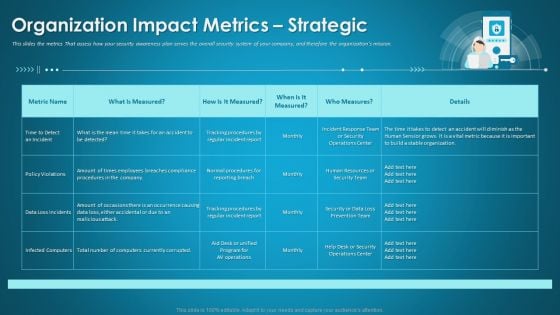
Organizational Network Security Awareness Staff Learning Organization Impact Metrics Strategic Structure PDF
This slides the metrics That assess how your security awareness plan serves the overall security system of your company, and therefore the organizations mission. Deliver and pitch your topic in the best possible manner with this organizational network security awareness staff learning organization impact metrics strategic structure pdf. Use them to share invaluable insights on human resources, security operations, organization and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Barriers To Cyber Security Incident Management Ppt Powerpoint Presentation File Professional Pdf
This slide represents the challenges faced by enterprises in managing cyber attacks to minimize its impact on business operations. It includes barriers related to people, technology, process etc. Find highly impressive Barriers To Cyber Security Incident Management Ppt Powerpoint Presentation File Professional Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Barriers To Cyber Security Incident Management Ppt Powerpoint Presentation File Professional Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide represents the challenges faced by enterprises in managing cyber attacks to minimize its impact on business operations. It includes barriers related to people, technology, process etc.
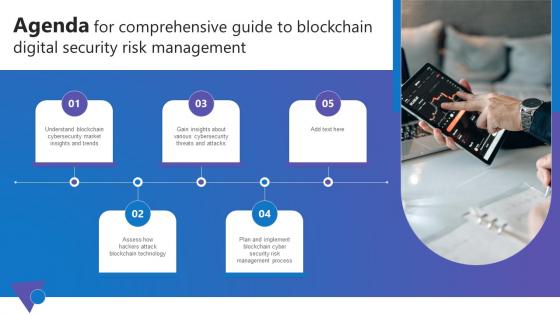
Agenda For Comprehensive Guide To Blockchain Digital Security Risk Management Structure Pdf
Slidegeeks has constructed Agenda For Comprehensive Guide To Blockchain Digital Security Risk Management Structure Pdf after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates. Our Agenda For Comprehensive Guide To Blockchain Digital Security Risk Management Structure Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Cloud Data Security Using Cryptography Ppt Powerpoint Presentation Complete Deck With Slides
This incisive,comprehensive Cloud Data Security Using Cryptography Ppt Powerpoint Presentation Complete Deck With Slides details important features of running a business. One learns about things like result areas,planning and strategic framework just a glance of this comprehensive deck of eighty five slides. Use this PPT template to present your unique perspective of business technicalities and experience the way a good presentation can give new meaning to similarly placed facts. Use this template to leave a roomful of people wondering at the expert you have gathered in closing a business deal. The completely editable and customisable nature of the presentation is a unique bonus. Download now. Our Cloud Data Security Using Cryptography Ppt Powerpoint Presentation Complete Deck With Slides are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
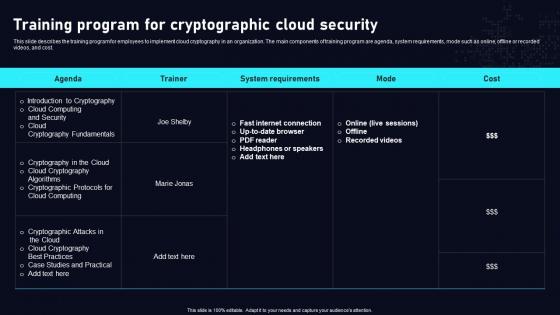
Training Program For Cryptographic Cloud Data Security Using Cryptography Sample Pdf
This slide describes the training program for employees to implement cloud cryptography in an organization. The main components of training program are agenda, system requirements, mode such as online, offline or recorded videos, and cost. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Training Program For Cryptographic Cloud Data Security Using Cryptography Sample Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Training Program For Cryptographic Cloud Data Security Using Cryptography Sample Pdf that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide describes the training program for employees to implement cloud cryptography in an organization. The main components of training program are agenda, system requirements, mode such as online, offline or recorded videos, and cost.

Monitoring Digital Assets To Enhance Cyber Security Ppt Powerpoint Presentation Complete Deck
Take advantage of this well-researched and professionally-designed Monitoring Digital Assets To Enhance Cyber Security Ppt Powerpoint Presentation Complete Deck to ace your next business meeting. Use this PPT complete deck to impress the management with your ideas for business growth and revenue increase. Use the twenty one-slide Template Bundle to leave no stone unturned as you present each step of your process. Employ the visual tools within the slides such as graphs, charts, and tables to ensure that the audience can never look away from the presentation. With attractive visuals, easy to understand structure, and your knowledge, your presentation will have the attention it deserves. Download this PPT Template from the link below. Our Monitoring Digital Assets To Enhance Cyber Security Ppt Powerpoint Presentation Complete Deck are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Client Testimonials Voice Assistance Security Platform Investor Funding Presentation Pictures Pdf
This slide showcases customer testimonials of customer which are using open source platform for virtual assistance application which is offered by business. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Client Testimonials Voice Assistance Security Platform Investor Funding Presentation Pictures Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Client Testimonials Voice Assistance Security Platform Investor Funding Presentation Pictures Pdf that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide showcases customer testimonials of customer which are using open source platform for virtual assistance application which is offered by business.

Table Of Contents Global Data Security Industry Report IR SS V
Slidegeeks has constructed Table Of Contents Global Data Security Industry Report IR SS V after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. Our Table Of Contents Global Data Security Industry Report IR SS V are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
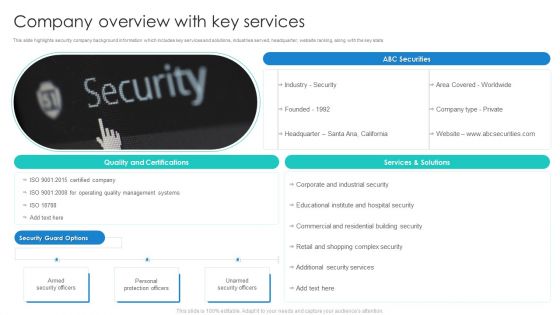
Manpower Corporate Security Business Profile Company Overview With Key Services Formats PDF
This slide highlights security company background information which includes key services and solutions, industries served, headquarter, website ranking, along with the key stats. Deliver an awe inspiring pitch with this creative Manpower Corporate Security Business Profile Company Overview With Key Services Formats PDF bundle. Topics like Armed Security Officer, Personal Protection Officers, Unarmed Security Officers can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Iot Device Monitoring Dashboard To Analyse Security Issues Iot Device Management Template Pdf
This slide includes a device monitoring dashboard to analyse network devices performance in various sites. It includes elements such as total sites, offline sites, sites with security issues, sites with major offline devices, site location, etc. This Iot Device Monitoring Dashboard To Analyse Security Issues Iot Device Management Template Pdf from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide includes a device monitoring dashboard to analyse network devices performance in various sites. It includes elements such as total sites, offline sites, sites with security issues, sites with major offline devices, site location, etc.

Future Of Digital Wallet Security And Safety In Depth Guide To Digital Wallets Fin SS V
This slide exhibits the future of digital wallet security using various technologies and regulations that help to promote the seamless working of online transactions. The major components are biometric authorization, government regulations, artificial intelligence, etc. Welcome to our selection of the Future Of Digital Wallet Security And Safety In Depth Guide To Digital Wallets Fin SS V. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide exhibits the future of digital wallet security using various technologies and regulations that help to promote the seamless working of online transactions. The major components are biometric authorization, government regulations, artificial intelligence, etc.

Information Security Process To Manage Firms Sensitive Data Ppt Infographics Background Image PDF
This slide provides information about information security process in order to manage firms sensitive data in terms of privileged password management, network security audit checklist, etc. Deliver an awe inspiring pitch with this creative information security process to manage firms sensitive data ppt infographics background image pdf bundle. Topics like management, system, security, information can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
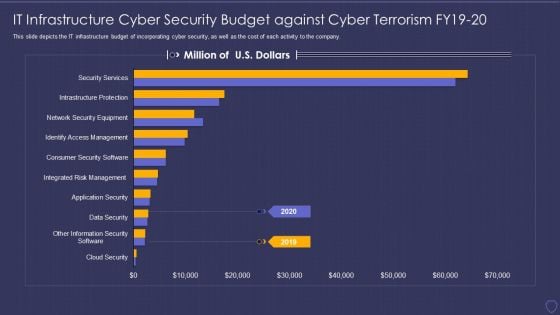
Global Cyber Terrorism Incidents On The Rise IT IT Infrastructure Cyber Security Budget Pictures PDF
This slide depicts the IT infrastructure budget of incorporating cyber security, as well as the cost of each activity to the company. Deliver an awe inspiring pitch with this creative global cyber terrorism incidents on the rise it it infrastructure cyber security budget pictures pdf bundle. Topics like data security, infrastructure protections, access management, security service can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Addressing Challenges In IoT Based Satellite Security IoT In Orbit Unleashing The Power IoT SS V
This slide highlights mitigation strategies to address satellite network security challenges to ensure data integrity and safeguarding communication. It includes challenges such as satellite network jamming, device damage, and unauthorized access. Find a pre-designed and impeccable Addressing Challenges In IoT Based Satellite Security IoT In Orbit Unleashing The Power IoT SS V. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide highlights mitigation strategies to address satellite network security challenges to ensure data integrity and safeguarding communication. It includes challenges such as satellite network jamming, device damage, and unauthorized access.
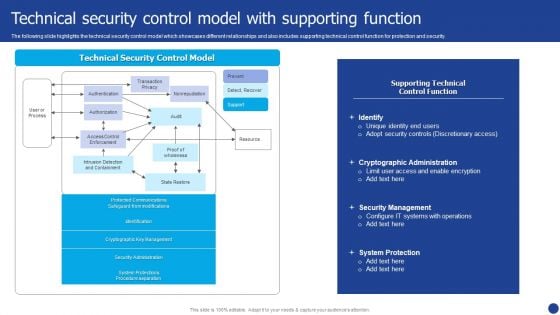
Information Technology Threat Mitigation Methods Technical Security Control Model With Supporting Function Introduction PDF
The following slide highlights the technical security control model which showcases different relationships and also includes supporting technical control function for protection and security. Deliver and pitch your topic in the best possible manner with this Information Technology Threat Mitigation Methods Technical Security Control Model With Supporting Function Introduction PDF. Use them to share invaluable insights on Cryptographic Administration, Security Management, System Protection and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
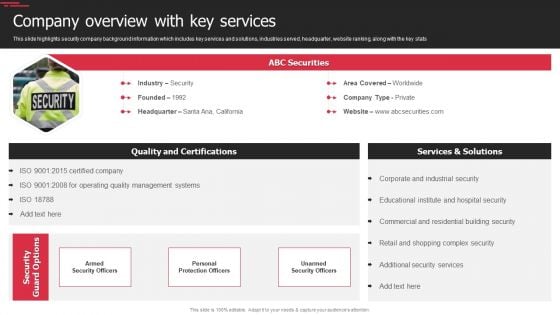
Security Agency Business Profile Company Overview With Key Services Inspiration PDF
This slide highlights security company background information which includes key services and solutions, industries served, headquarter, website ranking, along with the key stats. Deliver an awe inspiring pitch with this creative Security Agency Business Profile Company Overview With Key Services Inspiration PDF bundle. Topics like Quality Management Systems, Industrial Security, Security Services can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
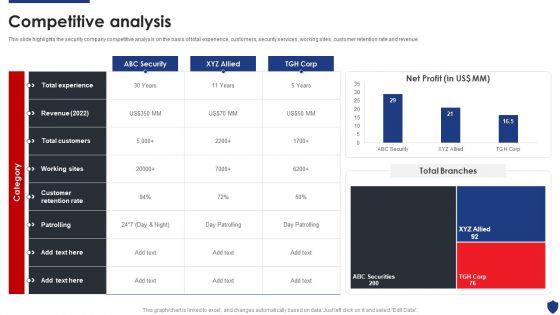
Security Officer Service Company Profile Competitive Analysis Ppt PowerPoint Presentation Gallery Rules PDF
This slide highlights the security company competitive analysis on the basis of total experience, customers, security services, working sites, customer retention rate and revenue. Deliver an awe inspiring pitch with this creative Security Officer Service Company Profile Competitive Analysis Ppt PowerPoint Presentation Gallery Rules PDF bundle. Topics like ABC Security, Total Experience, Total Customers can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Info Safety And ISO 27001 Performance Indicators To Measure Information Security Sample PDF
Following slide illustrates performance indicators for measuring information security controls. It includes controls details, performance indicator formula, target and periodicity. Deliver and pitch your topic in the best possible manner with this Info Safety And ISO 27001 Performance Indicators To Measure Information Security Sample PDF. Use them to share invaluable insights on Information Security Policy, Information Security Training, Asset Inventory and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

IT Protection Cyber Security Cyber Threat Ppt PowerPoint Presentation Complete Deck
Presenting this set of slides with name it protection cyber security cyber threat ppt powerpoint presentation complete deck. The topics discussed in these slides are network protection, cyber security, cyber threat, laptop protected, security breach. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
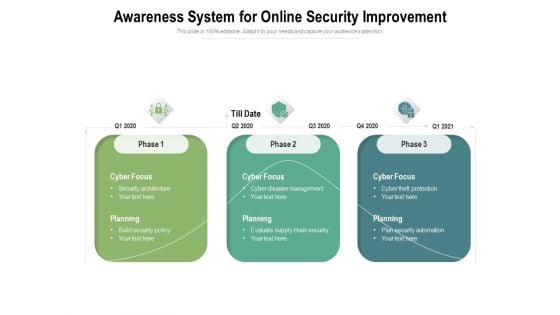
Awareness System For Online Security Improvement Ppt PowerPoint Presentation Show Samples PDF
Presenting this set of slides with name awareness system for online security improvement ppt powerpoint presentation show samples pdf. This is a three stage process. The stages in this process are cyber focus, planning, 2020, build security policy, security architecture, cyber disaster management, evaluate supply chain security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Customer Relationship Management Software Implementation Steps Enable Data Security Formats PDF
This slide covers two ways of enabling data security in CRM systems. It includes options such as IP restrictions and two-factor authentication. Deliver an awe inspiring pitch with this creative Customer Relationship Management Software Implementation Steps Enable Data Security Formats PDF bundle. Topics like Security And Compliance, Factor Authentication, Security Accounts can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

IT Infrastructure IT Security IT Budget For Fy2020 Ppt Ideas Elements PDF
This slide represents the budget for IT infrastructure after implementing cyber security, and it also shows the amount each task will cost the company. Deliver an awe inspiring pitch with this creative it infrastructure it security it budget for fy2020 ppt ideas elements pdf bundle. Topics like cloud security, costs, software application, security services can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
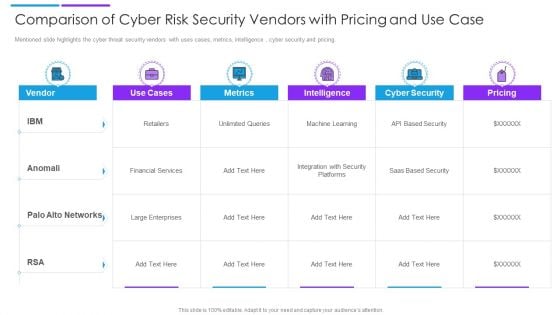
Comparison Of Cyber Risk Security Vendors With Pricing And Use Case Formats PDF
Mentioned slide highlights the cyber threat security vendors with uses cases, metrics, intelligence , cyber security and pricing. Pitch your topic with ease and precision using this comparison of cyber risk security vendors with pricing and use case formats pdf. This layout presents information on financial services, cyber security, intelligence. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
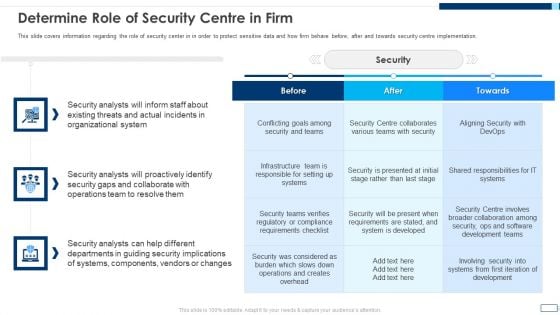
Evolving BI Infrastructure Determine Role Of Security Centre In Firm Summary PDF
This slide covers information regarding the role of security center in in order to protect sensitive data and how firm behave before, after and towards security centre implementation. Deliver an awe inspiring pitch with this creative evolving bi infrastructure determine role of security centre in firm summary pdf bundle. Topics like organizational, security analysts, collaborate can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
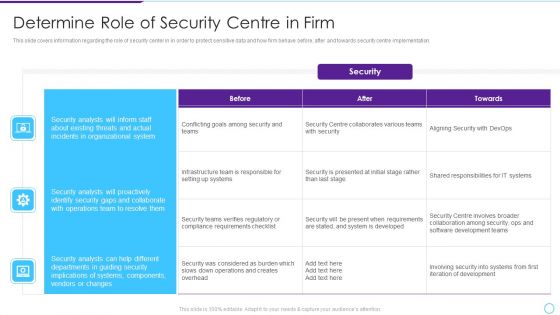
Intelligent Infrastructure Determine Role Of Security Centre In Firm Graphics PDF
This slide covers information regarding the role of security center in in order to protect sensitive data and how firm behave before, after and towards security centre implementation. Deliver an awe inspiring pitch with this creative Intelligent Infrastructure Determine Role Of Security Centre In Firm Graphics PDF bundle. Topics like Security, Organizational System, Operations Team, Conflicting Goals can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
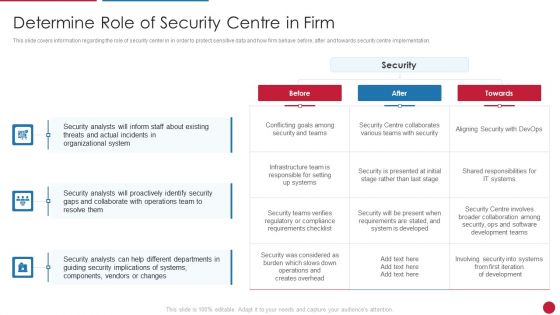
Facilitating IT Intelligence Architecture Determine Role Of Security Centre In Firm Demonstration PDF
This slide covers information regarding the role of security center in in order to protect sensitive data and how firm behave before, after and towards security centre implementation. Deliver an awe inspiring pitch with this creative Facilitating IT Intelligence Architecture Determine Role Of Security Centre In Firm Demonstration PDF bundle. Topics like Organizational System, Security Analysts, Collaborate With Operations can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
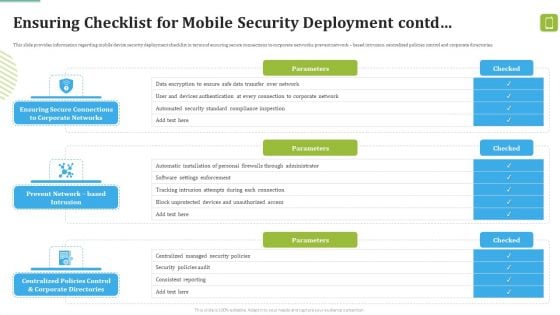
MDM Strategies At Office Ensuring Checklist For Mobile Security Deployment Contd Template PDF
This slide provides information regarding mobile device security deployment checklist in terms of device security, protection against malicious codes. Deliver and pitch your topic in the best possible manner with this MDM Strategies At Office Ensuring Checklist For Mobile Security Deployment Contd Template PDF. Use them to share invaluable insights on Against Malicious, Device Security, Automatic Configuration and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
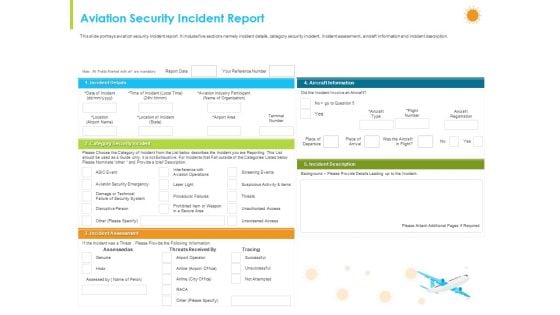
How Aviation Industry Coping With COVID 19 Pandemic Aviation Security Incident Report Template PDF
This slide portrays aviation security incident report. It include five sections namely incident details, category security incident, incident assessment, aircraft information and incident description.Deliver an awe inspiring pitch with this creative how aviation industry coping with COVID 19 pandemic aviation security incident report template pdf. bundle. Topics like suspicious activity and items, aircraft information, category security incident, incident assessment can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Intelligent Architecture Growing Cyber Security Issues Ppt Professional Design Templates PDF
The slide provides the major cyber security issues Unprecedented Attacks, Cyber Espionage, and Data Theft along with the split of total information security incidents by the type of incident Deliver an awe inspiring pitch with this creative intelligent architecture growing cyber security issues ppt professional design templates pdf bundle. Topics like organizations, cyber security, business can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
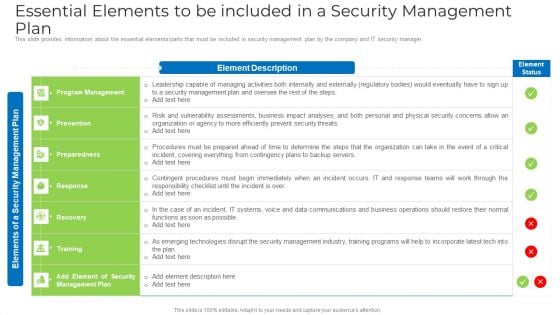
Essential Elements To Be Included In A Security Management Plan Elements PDF
This slide provides information about the essential elements or parts that must be included in security management plan by the company and IT security manager. Deliver an awe inspiring pitch with this creative essential elements to be included in a security management plan elements pdf bundle. Topics like risk, organization, security, systems, data communications can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

International Organization Standardization 270001 Performance Indicators To Measure Information Security Controls Clipart PDF
Following slide illustrates performance indicators for measuring information security controls. It includes controls details, performance indicator formula, target and periodicity. Deliver and pitch your topic in the best possible manner with this international organization standardization 270001 performance indicators to measure information security controls clipart pdf. Use them to share invaluable insights on information security policy, information security training, incident response and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Methods To Develop Measures And Ways To Mitigate Security Monitoring Challenges Background PDF
This slide provides information about the ways and measures through which the company and security monitoring managers can overcome the problems and issues related to Security Monitoring. Deliver an awe inspiring pitch with this creative methods to develop measures and ways to mitigate security monitoring challenges background pdf bundle. Topics like security monitoring challenges, employee management, malware attacks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Difference Between Cloud Security Solutions And Traditional It Solutions Pictures PDF
This slide represents the difference between cloud security solutions and traditional IT solutions based on information centers, cost, scalability, and expenses. Deliver an awe inspiring pitch with this creative Difference Between Cloud Security Solutions And Traditional It Solutions Pictures PDF bundle. Topics like Traditional It Security, Cloud Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
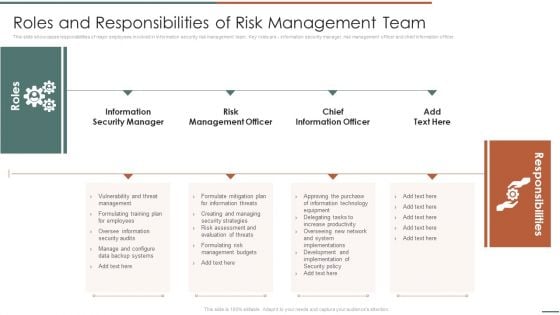
Information Security Risk Evaluation Roles And Responsibilities Of Risk Management Team Structure PDF
This slide showcases responsibilities of major employees involved in information security risk management team. Key roles are information security manager, risk management officer and chief information officer.Deliver an awe inspiring pitch with this creative Information Security Risk Evaluation Roles And Responsibilities Of Risk Management Team Structure PDF bundle. Topics like Information Security Manager, Risk Management, Chief Information can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Mastering Blockchain Wallets Mobile Wallets Key Security Issues And Solutions BCT SS V
This slide covers security concerns linked with mobile wallets and potential solutions to mitigate the risks. The purpose of this template is provide an overview on challenges associated such as lost or stolen devices, phishing scams, weak passwords along with risk involved with solutions to prevent risks and reduce its impact. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Mastering Blockchain Wallets Mobile Wallets Key Security Issues And Solutions BCT SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide covers security concerns linked with mobile wallets and potential solutions to mitigate the risks. The purpose of this template is provide an overview on challenges associated such as lost or stolen devices, phishing scams, weak passwords along with risk involved with solutions to prevent risks and reduce its impact.

Organizational Network Security Awareness Staff Learning Table Of Contents Introduction PDF
Deliver and pitch your topic in the best possible manner with this organizational network security awareness staff learning table of contents introduction pdf. Use them to share invaluable insights on security awareness training, organization impact metrics, security awareness, communication plan, budget and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
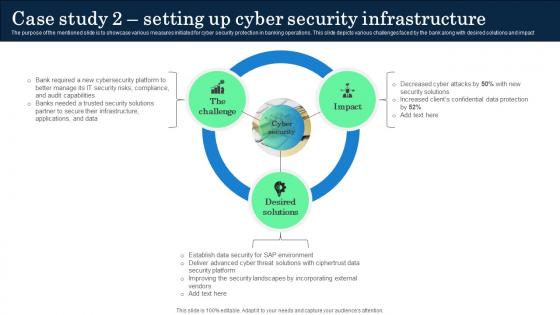
Case Study 2 Setting Up Cyber Security Infrastructure Incorporating Banking Operational Growth
The purpose of the mentioned slide is to showcase various measures initiated for cyber security protection in banking operations. This slide depicts various challenges faced by the bank along with desired solutions and impact. Present like a pro with Case Study 2 Setting Up Cyber Security Infrastructure Incorporating Banking Operational Growth. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. The purpose of the mentioned slide is to showcase various measures initiated for cyber security protection in banking operations. This slide depicts various challenges faced by the bank along with desired solutions and impact
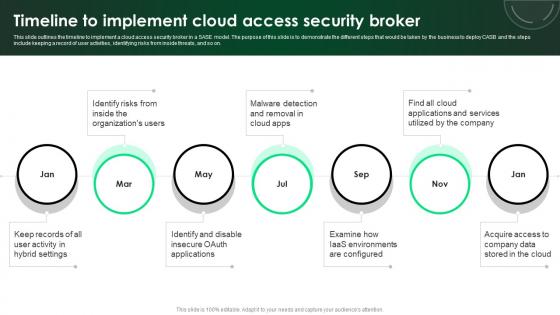
CASB 2 0 IT Timeline To Implement Cloud Access Security Broker
This slide outlines the timeline to implement a cloud access security broker in a SASE model. The purpose of this slide is to demonstrate the different steps that would be taken by the business to deploy CASB and the steps include keeping a record of user activities, identifying risks from inside threats, and so on. Make sure to capture your audiences attention in your business displays with our gratis customizable CASB 2 0 IT Timeline To Implement Cloud Access Security Broker. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide outlines the timeline to implement a cloud access security broker in a SASE model. The purpose of this slide is to demonstrate the different steps that would be taken by the business to deploy CASB and the steps include keeping a record of user activities, identifying risks from inside threats, and so on.
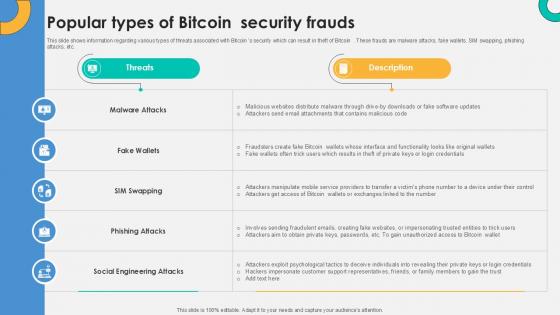
Popular Types Of Bitcoin Security Everything About Bitcoin PPT Slide Fin SS V
This slide shows information regarding various types of threats associated with Bitcoin s security which can result in theft of Bitcoin . These frauds are malware attacks, fake wallets, SIM swapping, phishing attacks, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Popular Types Of Bitcoin Security Everything About Bitcoin PPT Slide Fin SS V to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide shows information regarding various types of threats associated with Bitcoin s security which can result in theft of Bitcoin . These frauds are malware attacks, fake wallets, SIM swapping, phishing attacks, etc.

Dashboard To Track IT Security Playbook For Strategic Actions To Improve IT Performance Summary Pdf
This slide portrays information regarding the dashboard that firm will track various incidents detected. These incidents will be managed in order to avoid security risks. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Dashboard To Track IT Security Playbook For Strategic Actions To Improve IT Performance Summary Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide portrays information regarding the dashboard that firm will track various incidents detected. These incidents will be managed in order to avoid security risks.

Cryptographic Algorithms Used In Cloud Data Security Using Cryptography Themes Pdf
This slide talks about algorithms used for implementing cryptography in data security. The purpose of this slide is to explain the different implementation steps. The techniques discussed are RSA Rivest, Shamir, Adleman cryptographic algorithm and Data Encryption Standard algorithm. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Cryptographic Algorithms Used In Cloud Data Security Using Cryptography Themes Pdf from Slidegeeks and deliver a wonderful presentation. This slide talks about algorithms used for implementing cryptography in data security. The purpose of this slide is to explain the different implementation steps. The techniques discussed are RSA Rivest, Shamir, Adleman cryptographic algorithm and Data Encryption Standard algorithm.

Introduction To Smart Doorbells Used For Maintaining Security Utilizing Smart Appliances IoT SS V
This slide provides an overview of the video doorbells used to enhance security. The slide includes features of smart doorbells that are motion detection, video storage, multi-user functionality, night vision camera, etc. There are so many reasons you need a Introduction To Smart Doorbells Used For Maintaining Security Utilizing Smart Appliances IoT SS V. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide provides an overview of the video doorbells used to enhance security. The slide includes features of smart doorbells that are motion detection, video storage, multi-user functionality, night vision camera, etc.
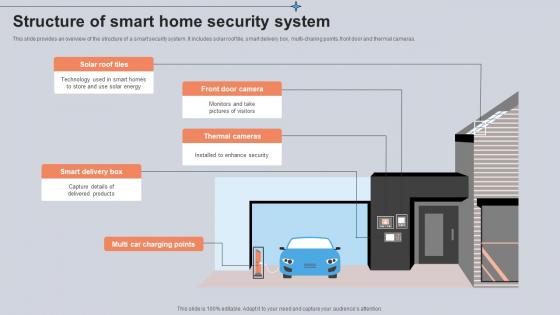
Structure Of Smart Home Security System Utilizing Smart Appliances IoT SS V
This slide provides an overview of the structure of a smart security system. It includes solar roof tile, smart delivery box, multi-charing points, front door and thermal cameras. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Structure Of Smart Home Security System Utilizing Smart Appliances IoT SS V for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide provides an overview of the structure of a smart security system. It includes solar roof tile, smart delivery box, multi-charing points, front door and thermal cameras.

Overview Need For Implementing Data Security Across Retail DT SS V
This slide analyses the need of implementing data security initiatives to address key customer data challenges in retail industry. It also mentions types of customer data collected such as account, location, browsing, and profile.Make sure to capture your audiences attention in your business displays with our gratis customizable Overview Need For Implementing Data Security Across Retail DT SS V. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide analyses the need of implementing data security initiatives to address key customer data challenges in retail industry. It also mentions types of customer data collected such as account, location, browsing, and profile.

Email Security Market Research Report Industry Trends Ppt Infographics Styles PDF
Presenting this set of slides with name email security market research report industry trends ppt infographics styles pdf. This is a six stage process. The stages in this process are balance between risk and resilience, supply chain security, security adaptive approach. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Global Cloud Based Email Security Market Industry Trends Ppt Professional Example PDF
Presenting this set of slides with name global cloud based email security market industry trends ppt professional example pdf. This is a six stage process. The stages in this process are balance between risk and resilience, supply chain security, security adaptive approach. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Strategies To Mitigate Cyber Security Risks Optimizing Cybersecurity Framework Roadmap Ppt File Icon PDF
Presenting this set of slides with name strategies to mitigate cyber security risks optimizing cybersecurity framework roadmap ppt file icon pdf. The topics discussed in these slides are implement enterprise, security program, implement control environment, implement security processes. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.


 Continue with Email
Continue with Email

 Home
Home


































