Sensitivity Analysis
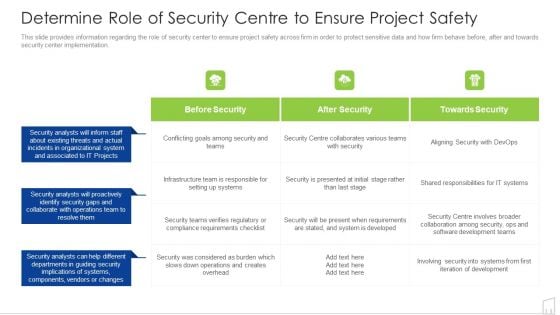
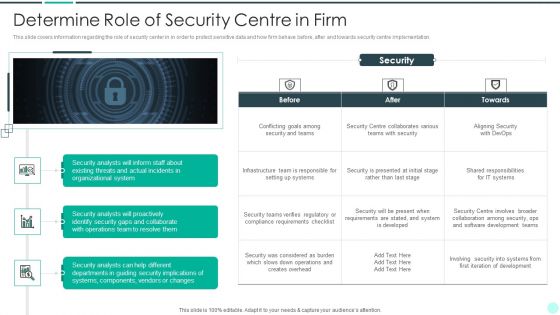
Determine Role Of Security Centre To Ensure Project Safety Ppt Professional Example PDF
This slide provides information regarding the role of security center to ensure project safety across firm in order to protect sensitive data and how firm behave before, after and towards security center implementation. Deliver an awe inspiring pitch with this creative determine role of security centre to ensure project safety ppt professional example pdf bundle. Topics like security, system, developed, requirements, teams can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
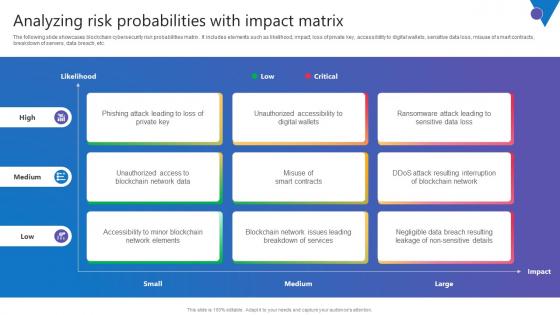
Analyzing Risk Probabilities Comprehensive Guide To Blockchain Digital Security Structure Pdf
The following slide showcases blockchain cybersecurity risk probabilities matrix . It includes elements such as likelihood, impact, loss of private key, accessibility to digital wallets, sensitive data loss, misuse of smart contracts, breakdown of servers, data breach, etc. Presenting this PowerPoint presentation, titled Analyzing Risk Probabilities Comprehensive Guide To Blockchain Digital Security Structure Pdf, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Analyzing Risk Probabilities Comprehensive Guide To Blockchain Digital Security Structure Pdf. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Analyzing Risk Probabilities Comprehensive Guide To Blockchain Digital Security Structure Pdf that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. The following slide showcases blockchain cybersecurity risk probabilities matrix . It includes elements such as likelihood, impact, loss of private key, accessibility to digital wallets, sensitive data loss, misuse of smart contracts, breakdown of servers, data breach, etc.
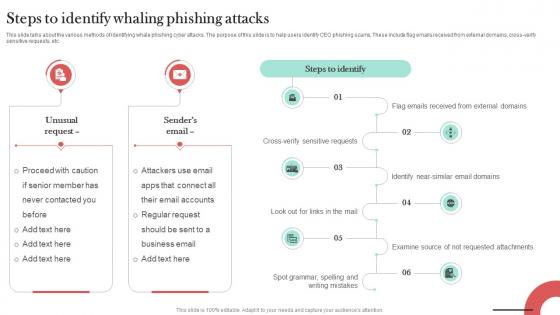
Steps To Identify Whaling Phishing Attacks Man In The Middle Phishing IT
This slide talks about the various methods of identifying whale phishing cyber attacks. The purpose of this slide is to help users identify CEO phishing scams. These include flag emails received from external domains, cross-verify sensitive requests, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Steps To Identify Whaling Phishing Attacks Man In The Middle Phishing IT is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Steps To Identify Whaling Phishing Attacks Man In The Middle Phishing IT and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide talks about the various methods of identifying whale phishing cyber attacks. The purpose of this slide is to help users identify CEO phishing scams. These include flag emails received from external domains, cross-verify sensitive requests, etc.
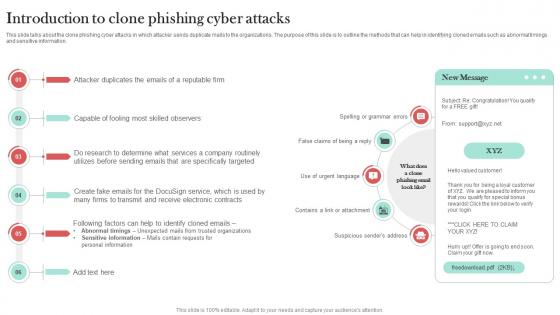
Introduction To Clone Phishing Cyber Man In The Middle Phishing IT
This slide talks about the clone phishing cyber attacks in which attacker sends duplicate mails to the organizations. The purpose of this slide is to outline the methods that can help in identifying cloned emails such as abnormal timings and sensitive information. This Introduction To Clone Phishing Cyber Man In The Middle Phishing IT from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide talks about the clone phishing cyber attacks in which attacker sends duplicate mails to the organizations. The purpose of this slide is to outline the methods that can help in identifying cloned emails such as abnormal timings and sensitive information.

Solutions To Overcome Dynamic Marketing Challenges Faced By Organizations Formats Pdf
The slide showcases real time marketing issues faced by organizations in order to promote their product or service. The slide contains challenges such as time sensitivity, relevance, resource allocation, etc., Along with descriptions and solutions. Showcasing this set of slides titled Solutions To Overcome Dynamic Marketing Challenges Faced By Organizations Formats Pdf. The topics addressed in these templates are Resource Allocation, Marketing Techniques, Opportunity. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. The slide showcases real time marketing issues faced by organizations in order to promote their product or service. The slide contains challenges such as time sensitivity, relevance, resource allocation, etc., Along with descriptions and solutions.

Steps To Employ Consumer Empathy In Marketing Themes PDF
The following slide enlists steps for employing empathy marketing to understand world from customer perspective and customize marketing to align experience. It covers sensitiveness to customer reality, provision of exceptional value and positive customer experience. Persuade your audience using this Steps To Employ Consumer Empathy In Marketing Themes PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Provide Exceptional Value, Positive Customer Experience, Sensitiveness To Customer Reality. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
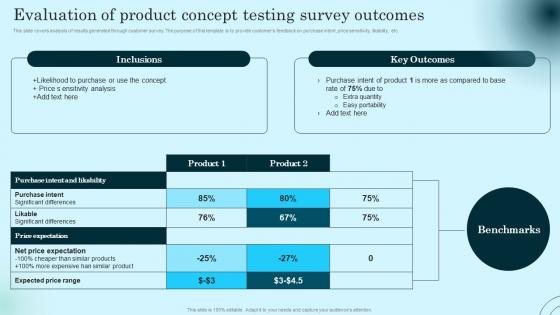
Evaluation Of Product Concept Testing Survey Comprehensive Guide To Product Lifecycle Slides Pdf
This slide covers analysis of results generated through customer survey. The purpose of this template is to provide customers feedback on purchase intent, price sensitivity, likability, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Evaluation Of Product Concept Testing Survey Comprehensive Guide To Product Lifecycle Slides Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Evaluation Of Product Concept Testing Survey Comprehensive Guide To Product Lifecycle Slides Pdf today and make your presentation stand out from the rest This slide covers analysis of results generated through customer survey. The purpose of this template is to provide customers feedback on purchase intent, price sensitivity, likability, etc.
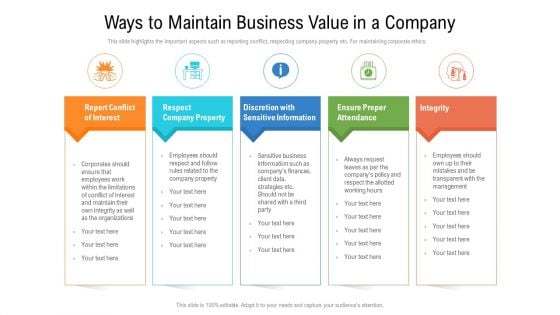
Ways To Maintain Business Value In A Company Ppt PowerPoint Presentation File Summary PDF
Presenting ways to maintain business value in a company ppt powerpoint presentation file summary pdf. to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including respect company property, report conflict of interest, discretion with sensitive information. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Using Behavioral Analytics For Multiple Transactions And Profiles Pictures PDF
The following slide illustrates usage of behavioral analytics for multiple transactions and profiles. It provides information about transaction, collaborative, behavior sorted, user defined, global intelligent, merchant, risk sensitivity, false positives, financial crimes, etc. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Using Behavioral Analytics For Multiple Transactions And Profiles Pictures PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.
Executing Advance Data Analytics At Workspace Determine Role Of Security Centre In Firm Sample PDF
This slide covers information regarding the role of security center in in order to protect sensitive data and how firm behave before, after and towards security centre implementation. This is a executing advance data analytics at workspace determine role of security centre in firm sample pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like determine role of security centre in firm. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
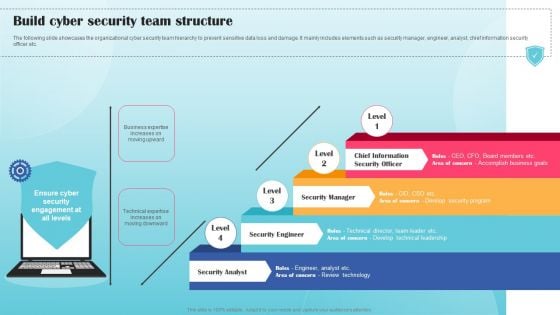
Build Cyber Security Team Structure Ppt PowerPoint Presentation File Example PDF
The following slide showcases the organizational cyber security team hierarchy to prevent sensitive data loss and damage. It mainly includes elements such as security manager, engineer, analyst, chief information security officer etc. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Build Cyber Security Team Structure Ppt PowerPoint Presentation File Example PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates

Credit Card Payment Processing Security Rules PDF
This slide outline the basics of payment processing security to protect business operations and sensitive consumer data. It includes secure data storage, payment data encryption and payment data tokenization. Presenting Credit Card Payment Processing Security Rules PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Secure Data Storage Vault, Payment Data Encryption, Payment Data Tokenization. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cloud Security Threats Contract Breaches With Clients Cloud Computing Security IT Ppt Ideas Introduction PDF
This slide defines the contract breaches with clients and customers that could be the biggest threat to the organizational data. Presenting cloud security threats contract breaches with clients cloud computing security it ppt ideas introduction pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like business, organization, sensitive data stored. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
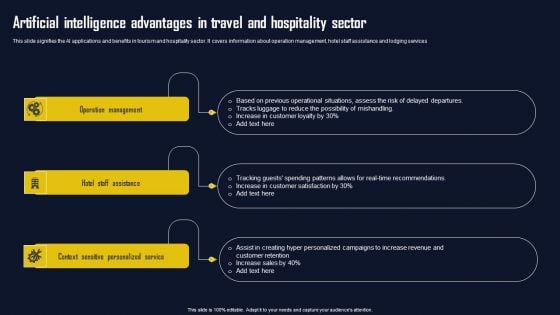
Artificial Intelligence Advantages In Travel And Hospitality Sector Brochure PDF
This slide signifies the AI applications and benefits in tourism and hospitality sector. It covers information about operation management, hotel staff assistance and lodging services Presenting Artificial Intelligence Advantages In Travel And Hospitality Sector Brochure PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Operation Management, Hotel Staff Assistance, Context Sensitive Personalized. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
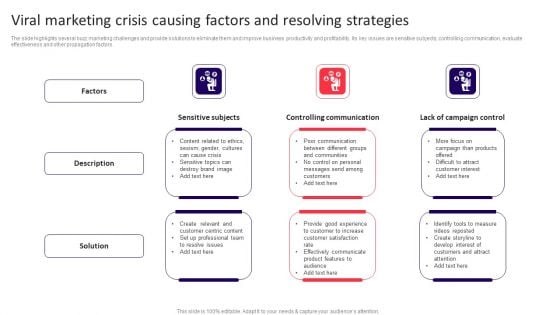
Viral Marketing Crisis Causing Factors And Resolving Strategies Infographics PDF
The slide highlights several buzz marketing challenges and provide solutions to eliminate them and improve business productivity and profitability. Its key issues are sensitive subjects, controlling communication, evaluate effectiveness and other propagation factors. Persuade your audience using this Viral Marketing Crisis Causing Factors And Resolving Strategies Infographics PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Factors, Description, Solution. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
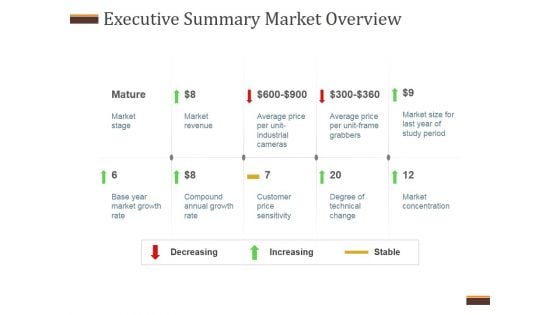
Executive Summary Market Overview Ppt PowerPoint Presentation Background Designs
This is a executive summary market overview ppt powerpoint presentation background designs. This is a ten stage process. The stages in this process are market stage, market revenue, base year market growth rate, compound annual growth rate, customer price sensitivity, degree of technical change, market concentration.

Effective Real Time Marketing Principles Sample SMS For Real Time Marketing Campaigns Professional Pdf
The following slide depicts examples of SMS campaigns to promote products and boost conversions. It includes elements such as welcome offers, time sensitive, personalized offers, sales and promos etc. Take your projects to the next level with our ultimate collection of Effective Real Time Marketing Principles Sample SMS For Real Time Marketing Campaigns Professional Pdf. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest The following slide depicts examples of SMS campaigns to promote products and boost conversions. It includes elements such as welcome offers, time sensitive, personalized offers, sales and promos etc.
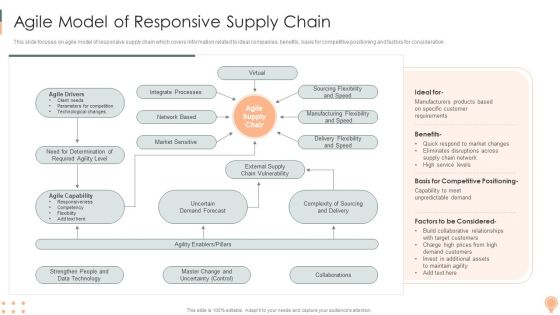
Supply Chain Approaches Agile Model Of Responsive Supply Chain Portrait PDF
This slide focuses on agile model of responsive supply chain which covers information related to ideal companies, benefits, basis for competitive positioning and factors for consideration.Deliver and pitch your topic in the best possible manner with this Supply Chain Approaches Agile Model Of Responsive Supply Chain Portrait PDF. Use them to share invaluable insights on Integrate Processes, Market Sensitive, Uncertain Demand and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
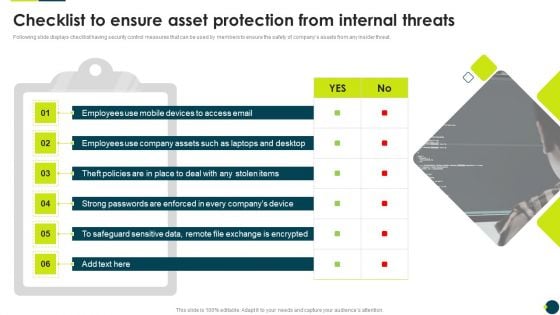
IT Threats Response Playbook Checklist To Ensure Asset Protection From Internal Threats Information PDF
Following slide displays checklist having security control measures that can be used by members to ensure the safety of companys assets from any insider threat.Deliver an awe inspiring pitch with this creative IT Threats Response Playbook Checklist To Ensure Asset Protection From Internal Threats Information PDF bundle. Topics like Safeguard Sensitive, Strong Passwords, Exchange Encrypted can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
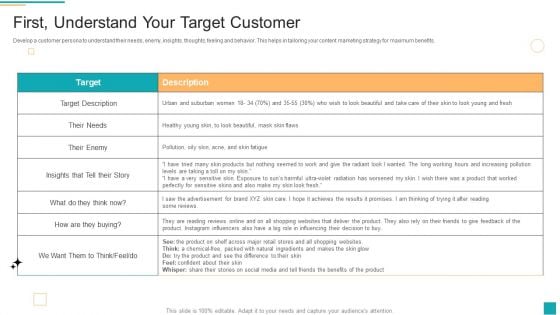
Business To Customer Online And Traditional First Understand Your Target Customer Brochure PDF
Develop a customer persona to understand their needs, enemy, insights, thoughts, feeling and behavior. This helps in tailoring your content marketing strategy for maximum benefits. Deliver an awe inspiring pitch with this creative Business To Customer Online And Traditional First Understand Your Target Customer Brochure PDF bundle. Topics like Perfectly Sensitive, Influencing Decision, Instagram Influencers can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Information Security Adhere To Strict Compliance Requirements Diagrams PDF
This slide shows that you can use a data classification engine to locate and categorize regulated and sensitive material also, compliance standards serve as a foundation. If you are looking for a format to display your unique thoughts, then the professionally designed Information Security Adhere To Strict Compliance Requirements Diagrams PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Information Security Adhere To Strict Compliance Requirements Diagrams PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Incident Response Techniques Deployement Key Issues Faced By Organization Due To Cybersecurity Incidents Infographics PDF
This slide shows the challenges faced by enterprise due to increase in cyber attacks. It includes cyber security incidents experienced by the organization such as cloud computing issues, theft of sensitive information, ransomware attacks etc. Get a simple yet stunning designed Incident Response Techniques Deployement Key Issues Faced By Organization Due To Cybersecurity Incidents Infographics PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Incident Response Techniques Deployement Key Issues Faced By Organization Due To Cybersecurity Incidents Infographics PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Fake Mobile Banking Apps To Steal Funds Ppt Summary Example PDF
This slide shows overview of how fake mobile banking applications works to steal users sensitive information and funds. It also includes details about channels used by hackers to distribute these applications. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Fake Mobile Banking Apps To Steal Funds Ppt Summary Example PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Fake Mobile Banking Apps To Steal Funds Ppt Summary Example PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
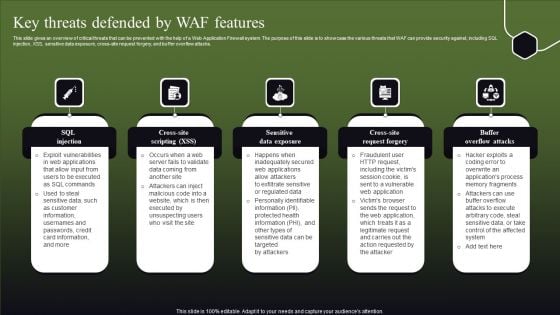
Key Threats Defended By WAF Features Ppt Pictures Elements PDF
This slide gives an overview of critical threats that can be prevented with the help of a Web Application Firewall system. The purpose of this slide is to showcase the various threats that WAF can provide security against, including SQL injection, XSS, sensitive data exposure, cross-site request forgery, and buffer overflow attacks. Explore a selection of the finest Key Threats Defended By WAF Features Ppt Pictures Elements PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Key Threats Defended By WAF Features Ppt Pictures Elements PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Agile Supply Chain Management Model Summary PDF
This slide shows the framework representing the management of agile supply chain. It includes four element of agile supply chain such as virtual, process alignment, network based and market sensitive. Pitch your topic with ease and precision using this Agile Supply Chain Management Model Summary PDF. This layout presents information on Virtual, Process Alignment, Network Based. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
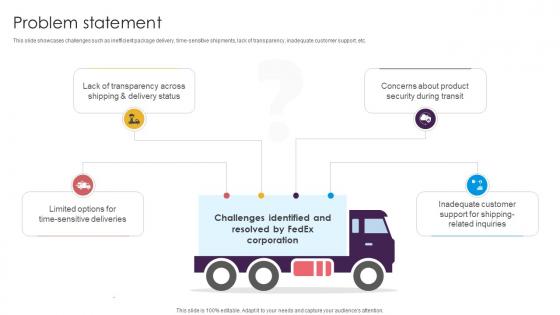
Problem Statement Delivery Service Provider Business Model BMC SS V
This slide showcases challenges such as inefficient package delivery, time-sensitive shipments, lack of transparency, inadequate customer support, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Problem Statement Delivery Service Provider Business Model BMC SS V can be your best option for delivering a presentation. Represent everything in detail using Problem Statement Delivery Service Provider Business Model BMC SS V and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide showcases challenges such as inefficient package delivery, time-sensitive shipments, lack of transparency, inadequate customer support, etc.

Key Drivers Of Data Protection And Security Mechanism Infographics PDF
The following slide showcases data protection drivers to assist businesses with their legitimate use of personal data. The drivers covered are data location, sensitivity, protection, access and flow.Presenting Key Drivers Of Data Protection And Security Mechanism Infographics PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Data Location, Data Sensitivity, Data Protection. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
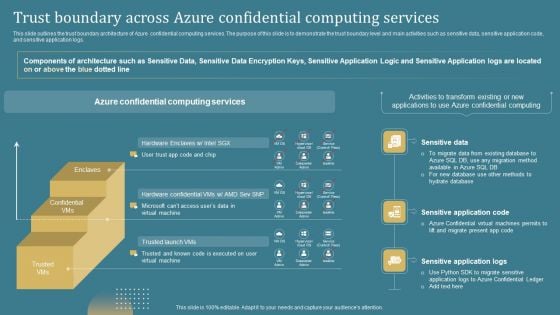
Confidential Computing System Technology Trust Boundary Across Azure Confidential Portrait PDF
This slide outlines the trust boundary architecture of Azure confidential computing services. The purpose of this slide is to demonstrate the trust boundary level and main activities such as sensitive data, sensitive application code, and sensitive application logs. Make sure to capture your audiences attention in your business displays with our gratis customizable Confidential Computing System Technology Trust Boundary Across Azure Confidential Portrait PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
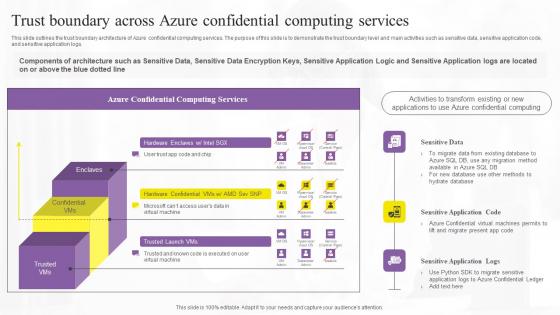
Trust Boundary Across Azure Confidential Computing Technologies Themes Pdf
This slide outlines the trust boundary architecture of Azure confidential computing services. The purpose of this slide is to demonstrate the trust boundary level and main activities such as sensitive data, sensitive application code, and sensitive application logs. Slidegeeks is here to make your presentations a breeze with Trust Boundary Across Azure Confidential Computing Technologies Themes Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide outlines the trust boundary architecture of Azure confidential computing services. The purpose of this slide is to demonstrate the trust boundary level and main activities such as sensitive data, sensitive application code, and sensitive application logs.
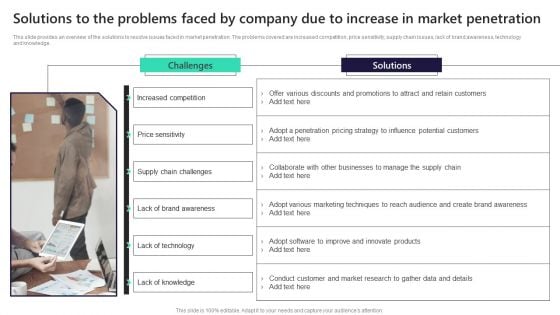
Solutions To The Problems Faced By Company Due To Increase In Market Penetration Themes PDF
This slide provides an overview of the solutions to resolve issues faced in market penetration. The problems covered are increased competition, price sensitivity, supply chain issues, lack of brand awareness, technology and knowledge. Retrieve professionally designed Solutions To The Problems Faced By Company Due To Increase In Market Penetration Themes PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
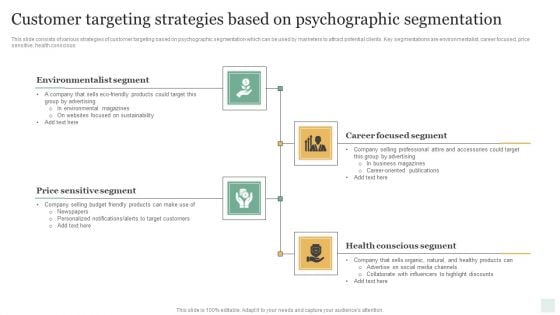
Customer Targeting Strategies Based On Psychographic Segmentation Elements PDF
This slide consists of various strategies of customer targeting based on psychographic segmentation which can be used by marketers to attract potential clients. Key segmentations are environmentalist, career focused, price sensitive, health conscious. Presenting Customer Targeting Strategies Based On Psychographic Segmentation Elements PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Environmentalist, Career Focused, Price Sensitive, Health Conscious. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
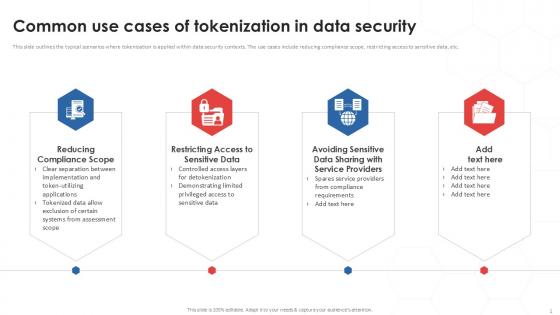
Common Use Cases Of Tokenization In Data Security PPT Template
This slide outlines the typical scenarios where tokenization is applied within data security contexts. The use cases include reducing compliance scope, restricting access to sensitive data, etc. Find a pre-designed and impeccable Common Use Cases Of Tokenization In Data Security PPT Template. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide outlines the typical scenarios where tokenization is applied within data security contexts. The use cases include reducing compliance scope, restricting access to sensitive data, etc.

Winning Strategies To Improve Organization Data Security Pictures PDF
The following slide highlights a winning strategy to avoid data security breach in the organization. Businesses can protect the confidential data by following strategies such as security audit, establishing strong password, back up sensitive data, and improve cyber-security. Presenting Winning Strategies To Improve Organization Data Security Pictures PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Security Audit, Establish Strong, Sensitive Data. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
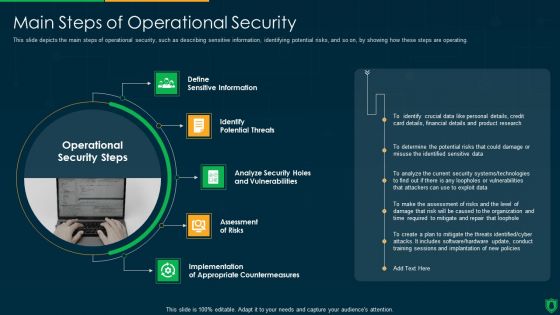
Info Security Main Steps Of Operational Security Ppt PowerPoint Presentation File Summary PDF
This slide depicts the main steps of operational security, such as describing sensitive information, identifying potential risks, and so on, by showing how these steps are operating. This is a info security main steps of operational security ppt powerpoint presentation file summary pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like define sensitive information, identify potential threats, assessment risks, implementation. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
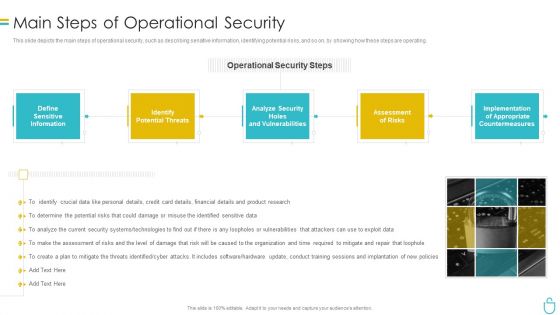
Information Security Main Steps Of Operational Security Ppt Inspiration Show PDF
This slide depicts the main steps of operational security, such as describing sensitive information, identifying potential risks, and so on, by showing how these steps are operating. Presenting information security main steps of operational security ppt inspiration show pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like sensitive information, potential threats, analyze security, assessment of risks, implementation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
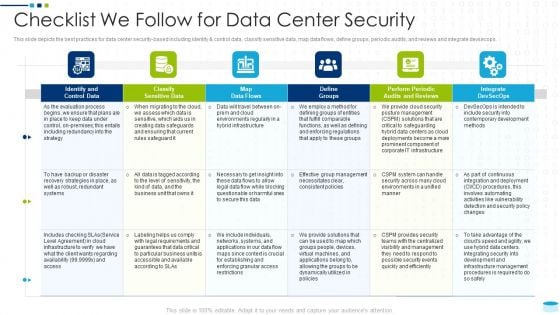
Data Center Infrastructure Management IT Checklist We Follow For Data Center Security Formats PDF
This slide depicts the best practices for data center security based including identity and control data, classify sensitive data, map data flows, define groups, periodic audits, and reviews and integrate devsecops. Deliver an awe inspiring pitch with this creative data center infrastructure management it checklist we follow for data center security formats pdf bundle. Topics like identity and control data, classify sensitive data, map data flows, define groups, periodic audits and reviews, integrate devsecops can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
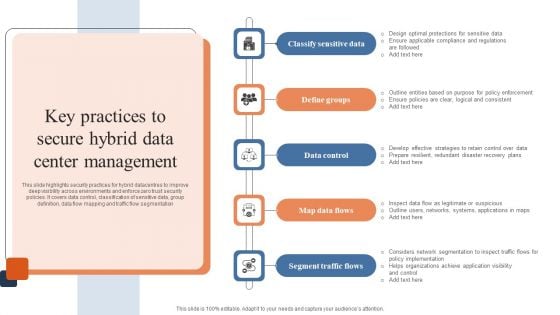
Key Practices To Secure Hybrid Data Center Management Ideas PDF
This slide highlights security practices for hybrid datacentres to improve deep visibility across environments and enforce zero trust security policies. It covers data control, classification of sensitive data, group definition, data flow mapping and traffic flow segmentation. Presenting Key Practices To Secure Hybrid Data Center Management Ideas PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Classify Sensitive Data, Define Groups, Data Control. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
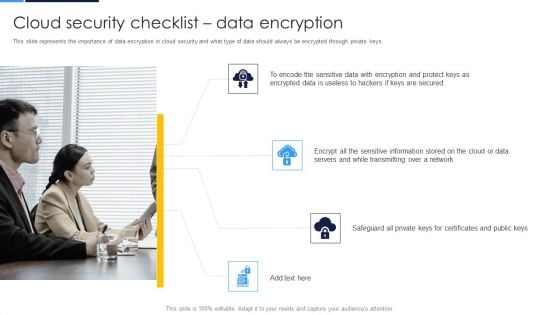
Cloud Security Assessment Cloud Security Checklist Data Encryption Brochure PDF
This slide represents the importance of data encryption in cloud security and what type of data should always be encrypted through private keys.This is a Cloud Security Assessment Cloud Security Checklist Data Encryption Brochure PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Sensitive Data, Encrypted Data, Sensitive Information You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
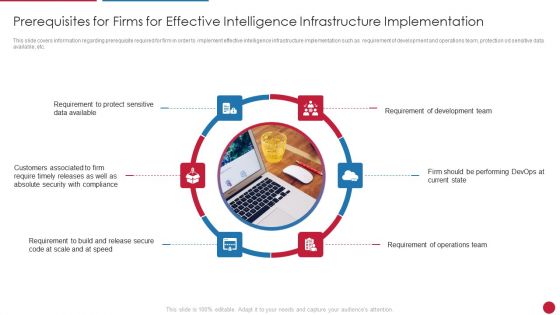
Facilitating IT Intelligence Architecture Prerequisites For Firms For Effective Intelligence Infrastructure Formats PDF
This slide covers information regarding prerequisite required for firm in order to implement effective intelligence infrastructure implementation such as requirement of development and operations team, protection od sensitive data available, etc.This is a Facilitating IT Intelligence Architecture Prerequisites For Firms For Effective Intelligence Infrastructure Formats PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Requirement To Protect Sensitive, Customers Associated, Requirement To Build And Release You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
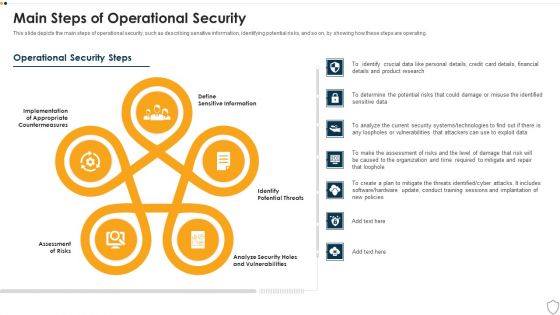
IT Security Main Steps Of Operational Security Ppt Show Design Inspiration PDF
This slide depicts the main steps of operational security, such as describing sensitive information, identifying potential risks, and so on, by showing how these steps are operating. Presenting it security main steps of operational security ppt show design inspiration pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like assessment of risks, potential threats, sensitive information, analyze security holes and vulnerabilities, implementation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Terrorism Assault Phishing Cyber Terrorism Tool Slides PDF
This slide describes phishing in which an attacker tricks a victim to open an email, provide card credentials or any sensitive information.Presenting cyber terrorism assault phishing cyber terrorism tool slides pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like attacker poses, sensitive information, business that are victims In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
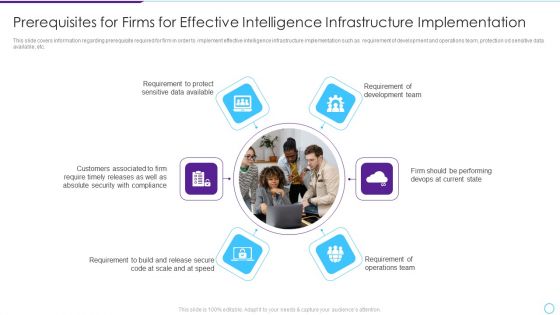
Intelligent Infrastructure Prerequisites For Firms For Effective Intelligence Infrastructure Rules PDF
This slide covers information regarding prerequisite required for firm in order to implement effective intelligence infrastructure implementation such as requirement of development and operations team, protection od sensitive data available, etc. Presenting Intelligent Infrastructure Prerequisites For Firms For Effective Intelligence Infrastructure Rules PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Protect Sensitive Data Available, Customers Associated, Absolute Security, Build And Release Secure. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Sample SMS For Real Time Marketing Campaigns Ppt Pictures Information PDF
The following slide depicts examples of SMS campaigns to promote products and boost conversions. It includes elements such as welcome offers, time sensitive, personalized offers, sales and promos etc. This Sample SMS For Real Time Marketing Campaigns Ppt Pictures Information PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Sample SMS For Real Time Marketing Campaigns Ppt Pictures Information PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today

Execution Of Product Lifecycle Evaluation Of Product Concept Testing Survey Elements Pdf
This slide covers analysis of results generated through customer survey. The purpose of this template is to provide customers feedback on purchase intent, price sensitivity, likability, etc. Slidegeeks is here to make your presentations a breeze with Execution Of Product Lifecycle Evaluation Of Product Concept Testing Survey Elements Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first. This slide covers analysis of results generated through customer survey. The purpose of this template is to provide customers feedback on purchase intent, price sensitivity, likability, etc.
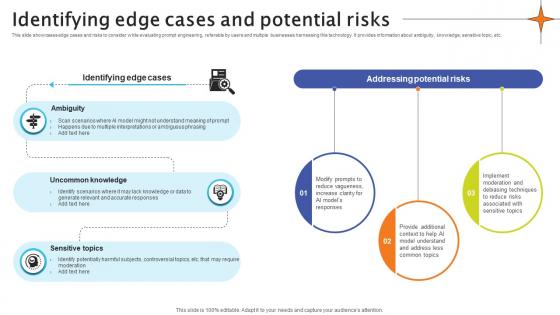
Identifying Edge Cases And Potential Risks Crafting Interactions A Guide AI SS V
This slide showcases edge cases and risks to consider while evaluating prompt engineering, referable by users and multiple businesses harnessing this technology. It provides information about ambiguity, knowledge, sensitive topic, etc. This modern and well-arranged Identifying Edge Cases And Potential Risks Crafting Interactions A Guide AI SS V provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide showcases edge cases and risks to consider while evaluating prompt engineering, referable by users and multiple businesses harnessing this technology. It provides information about ambiguity, knowledge, sensitive topic, etc.
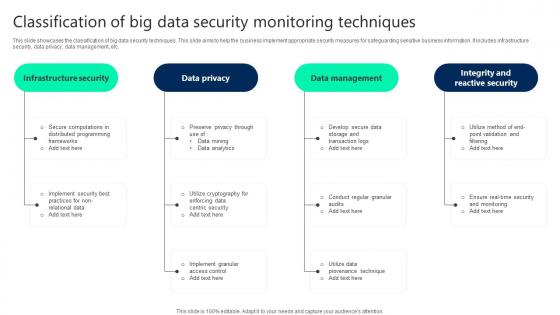
Classification Of Big Data Security Monitoring Techniques Professional pdf
This slide showcases the classification of big data security techniques. This slide aims to help the business implement appropriate security measures for safeguarding sensitive business information. It includes infrastructure security, data privacy, data management, etc. Pitch your topic with ease and precision using this Classification Of Big Data Security Monitoring Techniques Professional pdf. This layout presents information on Infrastructure Security, Data Privacy, Data Management. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide showcases the classification of big data security techniques. This slide aims to help the business implement appropriate security measures for safeguarding sensitive business information. It includes infrastructure security, data privacy, data management, etc.
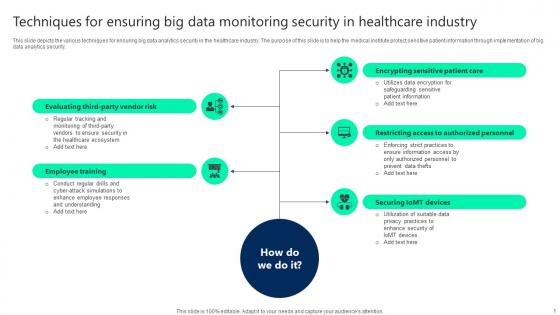
Techniques For Ensuring Big Data Monitoring Security In Healthcare Industry Infographics pdf
This slide depicts the various techniques for ensuring big data analytics security in the healthcare industry. The purpose of this slide is to help the medical institute protect sensitive patient information through implementation of big data analytics security. Pitch your topic with ease and precision using this Techniques For Ensuring Big Data Monitoring Security In Healthcare Industry Infographics pdf. This layout presents information on Employee Training, Securing Iomt Devices, Restricting Access. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide depicts the various techniques for ensuring big data analytics security in the healthcare industry. The purpose of this slide is to help the medical institute protect sensitive patient information through implementation of big data analytics security.
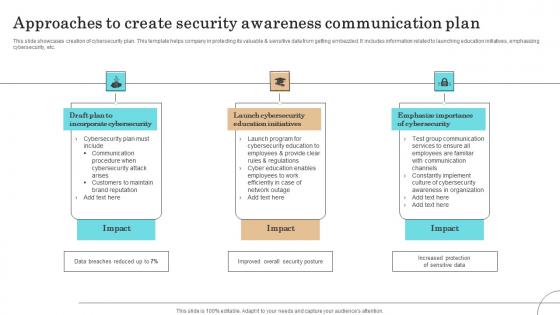
Approaches To Create Security Awareness Communication Plan Professional Pdf
This slide showcases creation of cybersecurity plan. This template helps company in protecting its valuable sensitive data from getting embezzled. It includes information related to launching education initiatives, emphasizing cybersecurity, etc.Showcasing this set of slides titled Approaches To Create Security Awareness Communication Plan Professional Pdf The topics addressed in these templates are Incorporate Cybersecurity, Launch Cybersecurity, Education Initiatives All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcases creation of cybersecurity plan. This template helps company in protecting its valuable sensitive data from getting embezzled. It includes information related to launching education initiatives, emphasizing cybersecurity, etc.

Common Use Cases Of Tokenization In Data Security Securing Your Data Ppt Sample
This slide outlines the typical scenarios where tokenization is applied within data security contexts. The use cases include reducing compliance scope, restricting access to sensitive data, etc. Slidegeeks is here to make your presentations a breeze with Common Use Cases Of Tokenization In Data Security Securing Your Data Ppt Sample With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide outlines the typical scenarios where tokenization is applied within data security contexts. The use cases include reducing compliance scope, restricting access to sensitive data, etc.
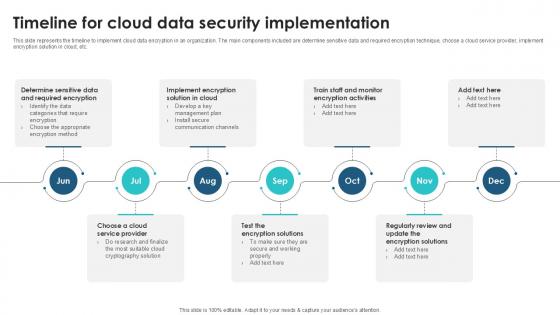
Timeline For Cloud Data Security Client Side Encryption PPT Example
This slide represents the timeline to implement cloud data encryption in an organization. The main components included are determine sensitive data and required encryption technique, choose a cloud service provider, implement encryption solution in cloud, etc. Slidegeeks has constructed Timeline For Cloud Data Security Client Side Encryption PPT Example after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide represents the timeline to implement cloud data encryption in an organization. The main components included are determine sensitive data and required encryption technique, choose a cloud service provider, implement encryption solution in cloud, etc.
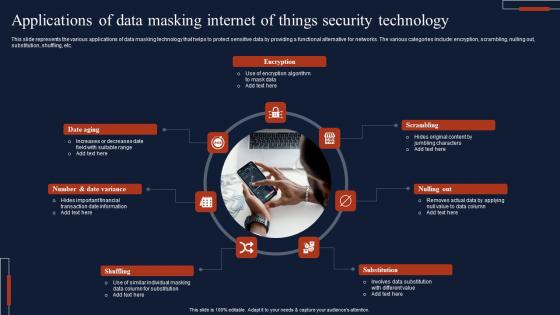
Applications Of Data Masking Internet Of Things Security Technology Topics Pdf
This slide represents the various applications of data masking technology that helps to protect sensitive data by providing a functional alternative for networks. The various categories include encryption, scrambling, nulling out, substitution, shuffling, etc. Showcasing this set of slides titled Applications Of Data Masking Internet Of Things Security Technology Topics Pdf The topics addressed in these templates are Encryption, Scrambling, Substitution, Shuffling All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide represents the various applications of data masking technology that helps to protect sensitive data by providing a functional alternative for networks. The various categories include encryption, scrambling, nulling out, substitution, shuffling, etc.
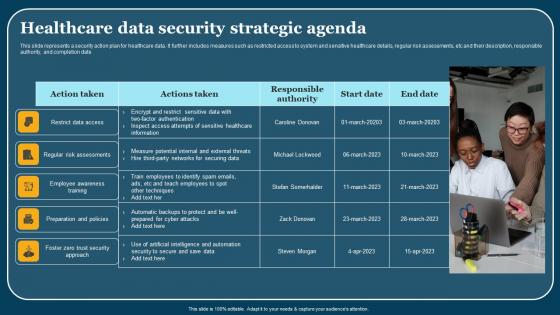
Healthcare Data Security Strategic Agenda Themes Pdf
This slide represents a security action plan for healthcare data. It further includes measures such as restricted access to system and sensitive healthcare details, regular risk assessments, etc and their description, responsible authority, and completion date. Showcasing this set of slides titled Healthcare Data Security Strategic Agenda Themes Pdf. The topics addressed in these templates are Employee Awareness Training, Action Taken. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide represents a security action plan for healthcare data. It further includes measures such as restricted access to system and sensitive healthcare details, regular risk assessments, etc and their description, responsible authority, and completion date.
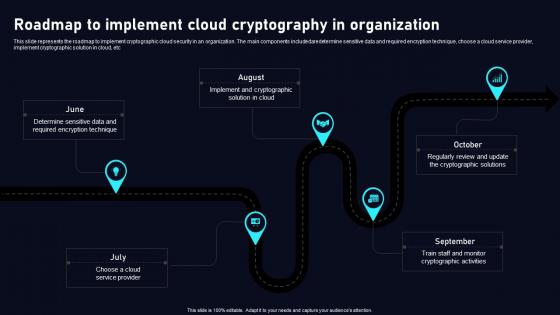
Roadmap To Implement Cloud Data Security Using Cryptography Information Pdf
This slide represents the roadmap to implement cryptographic cloud security in an organization. The main components includedaredetermine sensitive data and required encryption technique, choose a cloud service provider, implement cryptographic solution in cloud, etc Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Roadmap To Implement Cloud Data Security Using Cryptography Information Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Roadmap To Implement Cloud Data Security Using Cryptography Information Pdf today and make your presentation stand out from the rest This slide represents the roadmap to implement cryptographic cloud security in an organization. The main components includedaredetermine sensitive data and required encryption technique, choose a cloud service provider, implement cryptographic solution in cloud, etc

Roadmap For Cloud Data Client Side Encryption PPT Presentation
This slide represents the roadmap to implement cryptographic cloud security in an organization. The main components included are determine sensitive data and required encryption technique, choose a cloud service provider, implement solution in cloud, etc. The Roadmap For Cloud Data Client Side Encryption PPT Presentation is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide represents the roadmap to implement cryptographic cloud security in an organization. The main components included are determine sensitive data and required encryption technique, choose a cloud service provider, implement solution in cloud, etc.
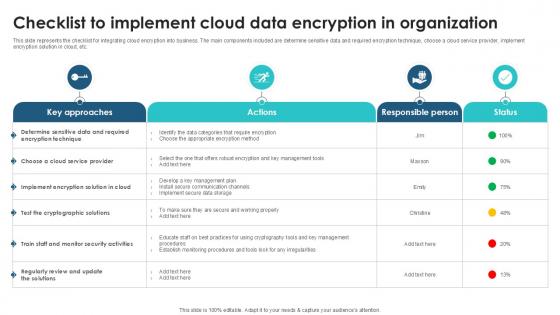
Checklist To Implement Cloud Data Client Side Encryption PPT Template
This slide represents the checklist for integrating cloud encryption into business. The main components included are determine sensitive data and required encryption technique, choose a cloud service provider, implement encryption solution in cloud, etc. Want to ace your presentation in front of a live audience Our Checklist To Implement Cloud Data Client Side Encryption PPT Template can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide represents the checklist for integrating cloud encryption into business. The main components included are determine sensitive data and required encryption technique, choose a cloud service provider, implement encryption solution in cloud, etc.

Roadmap To Implement Cloud Data Security In Cloud Computing Ppt Slide
This slide represents the roadmap to implement cryptographic cloud security in an organization. The main components included are determine sensitive data and required encryption technique, choose a cloud service provider, implement cryptographic solution in cloud, etc. There are so many reasons you need a Roadmap To Implement Cloud Data Security In Cloud Computing Ppt Slide. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide represents the roadmap to implement cryptographic cloud security in an organization. The main components included are determine sensitive data and required encryption technique, choose a cloud service provider, implement cryptographic solution in cloud, etc.
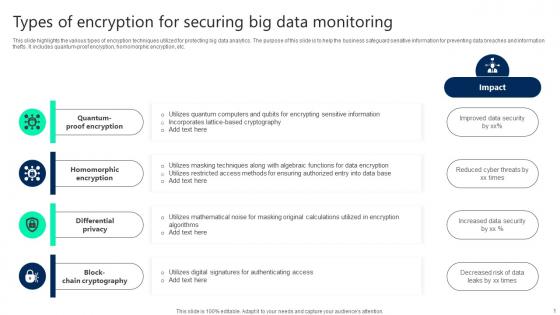
Types Of Encryption For Securing Big Data Monitoring Topics pdf
This slide highlights the various types of encryption techniques utilized for protecting big data analytics. The purpose of this slide is to help the business safeguard sensitive information for preventing data breaches and information thefts. It includes quantum-proof encryption, homomorphic encryption, etc. Showcasing this set of slides titled Types Of Encryption For Securing Big Data Monitoring Topics pdf. The topics addressed in these templates are Quantum Proof Encryption, Homomorphic Encryption, Differential Privacy. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide highlights the various types of encryption techniques utilized for protecting big data analytics. The purpose of this slide is to help the business safeguard sensitive information for preventing data breaches and information thefts. It includes quantum-proof encryption, homomorphic encryption, etc.

Types Of Information Leaked In Data Breach Data Fortification Strengthening Defenses
This slide outlines the different forms of information loss in a data security breach. The major types of data leaked are financial data, medical or personal health information, Personally Identifiable Information, vulnerable and sensitive data, etc. Present like a pro with Types Of Information Leaked In Data Breach Data Fortification Strengthening Defenses. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide outlines the different forms of information loss in a data security breach. The major types of data leaked are financial data, medical or personal health information, Personally Identifiable Information, vulnerable and sensitive data, etc.

Data Breach Prevention Strategies For Users Data Breach Prevention Sample Pdf
This slide represents the strategies to protect users from data breaches. These include use unique passwords, two-factor authentication, only submit sensitive data on HTTPS websites, software and hardware updates, encrypt hard drives, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Data Breach Prevention Strategies For Users Data Breach Prevention Sample Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide represents the strategies to protect users from data breaches. These include use unique passwords, two-factor authentication, only submit sensitive data on HTTPS websites, software and hardware updates, encrypt hard drives, etc.

Roadmap To Implement Tokenization For Data Security Securing Your Data Ppt Sample
This slide outlines the deployment for tokenization. The purpose of this slide is to highlight the steps that an organization should take while implementing tokenization including, generating tokens, identifying sensitive data, etc. Boost your pitch with our creative Roadmap To Implement Tokenization For Data Security Securing Your Data Ppt Sample Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide outlines the deployment for tokenization. The purpose of this slide is to highlight the steps that an organization should take while implementing tokenization including, generating tokens, identifying sensitive data, etc.


 Continue with Email
Continue with Email

 Home
Home


































