Software Demonstration

Steps To Select Next Generation Secure Web Gateway Web Threat Protection System
This slide demonstrates the points to be kept in mind while choosing next generation secure web gateway. The purpose of this slide is to explain how to select a next generation SWG. These are adopt real cloud architecture, adapts to new threats, etc. Slidegeeks is here to make your presentations a breeze with Steps To Select Next Generation Secure Web Gateway Web Threat Protection System With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide demonstrates the points to be kept in mind while choosing next generation secure web gateway. The purpose of this slide is to explain how to select a next generation SWG. These are adopt real cloud architecture, adapts to new threats, etc.
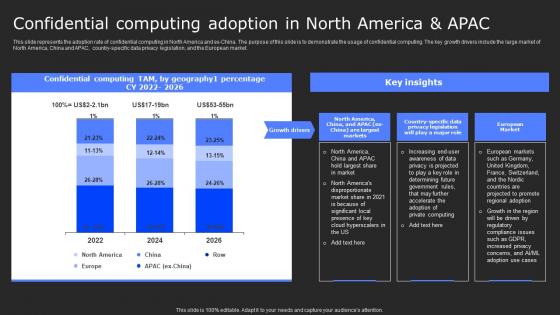
Confidential Computing Adoption In North Secure Computing Framework Template Pdf
This slide represents the adoption rate of confidential computing in North America and ex-China. The purpose of this slide is to demonstrate the usage of confidential computing. The key growth drivers include the large market of North America, China and APAC, country-specific data privacy legislation, and the European market. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Confidential Computing Adoption In North Secure Computing Framework Template Pdf can be your best option for delivering a presentation. Represent everything in detail using Confidential Computing Adoption In North Secure Computing Framework Template Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide represents the adoption rate of confidential computing in North America and ex-China. The purpose of this slide is to demonstrate the usage of confidential computing. The key growth drivers include the large market of North America, China and APAC, country-specific data privacy legislation, and the European market.
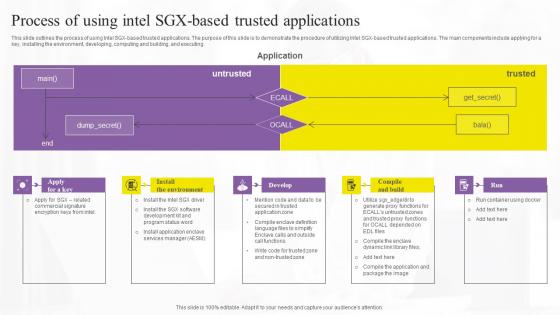
Process Of Using Intel Sgx Based Confidential Computing Technologies Pictures Pdf
This slide outlines the process of using Intel SGX-based trusted applications. The purpose of this slide is to demonstrate the procedure of utilizing Intel SGX-based trusted applications. The main components include applying for a key, installing the environment, developing, computing and building, and executing. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Process Of Using Intel Sgx Based Confidential Computing Technologies Pictures Pdf to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Process Of Using Intel Sgx Based Confidential Computing Technologies Pictures Pdf. This slide outlines the process of using Intel SGX-based trusted applications. The purpose of this slide is to demonstrate the procedure of utilizing Intel SGX-based trusted applications. The main components include applying for a key, installing the environment, developing, computing and building, and executing.
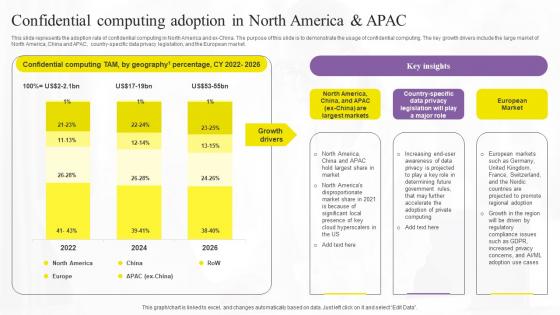
Confidential Computing Adoption In Confidential Computing Technologies Download Pdf
This slide represents the adoption rate of confidential computing in North America and ex-China. The purpose of this slide is to demonstrate the usage of confidential computing. The key growth drivers include the large market of North America, China and APAC, country-specific data privacy legislation, and the European market. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Confidential Computing Adoption In Confidential Computing Technologies Download Pdf can be your best option for delivering a presentation. Represent everything in detail using Confidential Computing Adoption In Confidential Computing Technologies Download Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide represents the adoption rate of confidential computing in North America and ex-China. The purpose of this slide is to demonstrate the usage of confidential computing. The key growth drivers include the large market of North America, China and APAC, country-specific data privacy legislation, and the European market.

Future Of Confidential Computing Technology Secure Multi Party Rules Pdf
This slide represents the future of confidential computing technology. The purpose of this slide is to demonstrate the state of confidential computing in the coming years. It also includes how it will protect sensitive data from malicious attacks in the cloud environment. Slidegeeks has constructed Future Of Confidential Computing Technology Secure Multi Party Rules Pdf after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide represents the future of confidential computing technology. The purpose of this slide is to demonstrate the state of confidential computing in the coming years. It also includes how it will protect sensitive data from malicious attacks in the cloud environment.
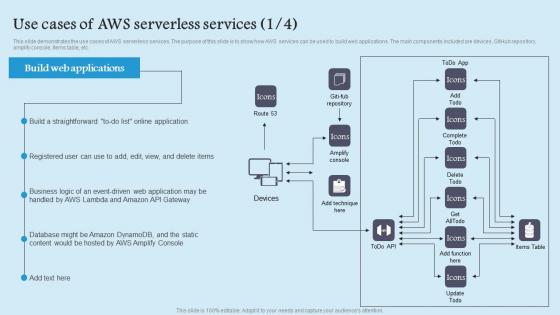
Use Cases Of Aws Serverless Role Serverless Computing Modern Technology Rules Pdf
This slide demonstrates the use cases of AWS serverless services. The purpose of this slide is to show how AWS services can be used to build web applications. The main components included are devices, GitHub repository, amplify console, items table, etc. Get a simple yet stunning designed Use Cases Of Aws Serverless Role Serverless Computing Modern Technology Rules Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Use Cases Of Aws Serverless Role Serverless Computing Modern Technology Rules Pdf can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide demonstrates the use cases of AWS serverless services. The purpose of this slide is to show how AWS services can be used to build web applications. The main components included are devices, GitHub repository, amplify console, items table, etc.
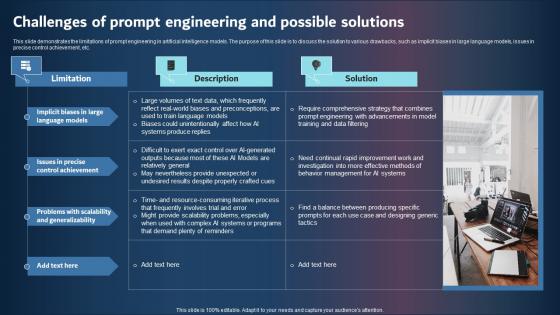
Challenges Of Prompt Engineering And Possible Solutions Inspiration PDF
This slide demonstrates the limitations of prompt engineering in artificial intelligence models. The purpose of this slide is to discuss the solution to various drawbacks, such as implicit biases in large language models, issues in precise control achievement, etc. Find highly impressive Challenges Of Prompt Engineering And Possible Solutions Inspiration Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Challenges Of Prompt Engineering And Possible Solutions Inspiration Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide demonstrates the limitations of prompt engineering in artificial intelligence models. The purpose of this slide is to discuss the solution to various drawbacks, such as implicit biases in large language models, issues in precise control achievement, etc.
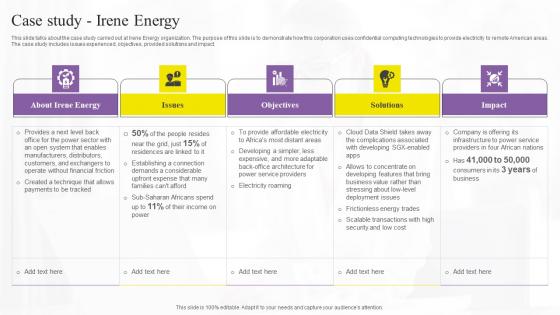
Case Study Irene Energy Confidential Computing Technologies Download Pdf
This slide talks about the case study carried out at Irene Energy organization. The purpose of this slide is to demonstrate how this corporation uses confidential computing technologies to provide electricity to remote American areas. The case study includes issues experienced, objectives, provided solutions and impact. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Case Study Irene Energy Confidential Computing Technologies Download Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Case Study Irene Energy Confidential Computing Technologies Download Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide talks about the case study carried out at Irene Energy organization. The purpose of this slide is to demonstrate how this corporation uses confidential computing technologies to provide electricity to remote American areas. The case study includes issues experienced, objectives, provided solutions and impact.
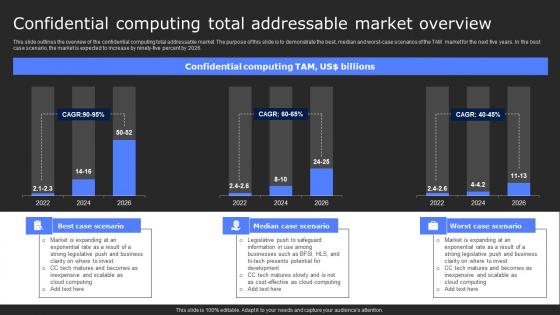
Confidential Computing Total Addressable Secure Computing Framework Themes Pdf
This slide outlines the overview of the confidential computing total addressable market. The purpose of this slide is to demonstrate the best, median and worst-case scenarios of the TAM market for the next five years. In the best case scenario, the market is expected to increase by ninety-five percent by 2026. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Confidential Computing Total Addressable Secure Computing Framework Themes Pdf from Slidegeeks and deliver a wonderful presentation. This slide outlines the overview of the confidential computing total addressable market. The purpose of this slide is to demonstrate the best, median and worst-case scenarios of the TAM market for the next five years. In the best case scenario, the market is expected to increase by ninety-five percent by 2026.
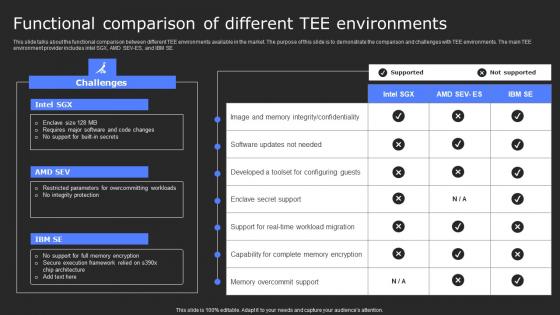
Functional Comparison Of Different Tee Secure Computing Framework Diagrams Pdf
This slide talks about the functional comparison between different TEE environments available in the market. The purpose of this slide is to demonstrate the comparison and challenges with TEE environments. The main TEE environment provider includes intel SGX, AMD SEV-ES, and IBM SE. Slidegeeks has constructed Functional Comparison Of Different Tee Secure Computing Framework Diagrams Pdf after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide talks about the functional comparison between different TEE environments available in the market. The purpose of this slide is to demonstrate the comparison and challenges with TEE environments. The main TEE environment provider includes intel SGX, AMD SEV-ES, and IBM SE.
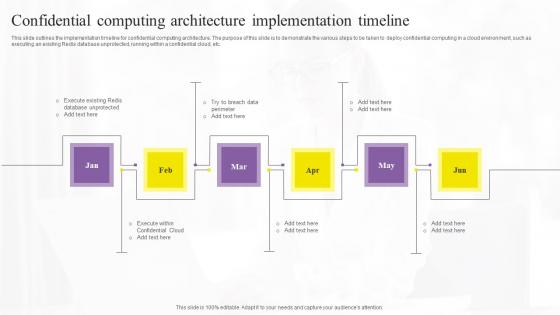
Confidential Computing Technologies Confidential Computing Architecture Topics Pdf
This slide outlines the implementation timeline for confidential computing architecture. The purpose of this slide is to demonstrate the various steps to be taken to deploy confidential computing in a cloud environment, such as executing an existing Redis database unprotected, running within a confidential cloud, etc. Explore a selection of the finest Confidential Computing Technologies Confidential Computing Architecture Topics Pdf here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Confidential Computing Technologies Confidential Computing Architecture Topics Pdf to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide outlines the implementation timeline for confidential computing architecture. The purpose of this slide is to demonstrate the various steps to be taken to deploy confidential computing in a cloud environment, such as executing an existing Redis database unprotected, running within a confidential cloud, etc.
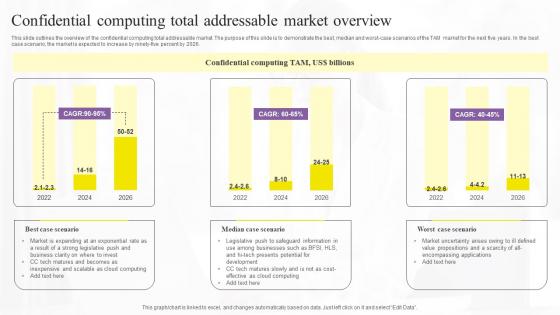
Confidential Computing Total Confidential Computing Technologies Formats Pdf
This slide outlines the overview of the confidential computing total addressable market. The purpose of this slide is to demonstrate the best, median and worst-case scenarios of the TAM market for the next five years. In the best case scenario, the market is expected to increase by ninety-five percent by 2026. Retrieve professionally designed Confidential Computing Total Confidential Computing Technologies Formats Pdf to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide outlines the overview of the confidential computing total addressable market. The purpose of this slide is to demonstrate the best, median and worst-case scenarios of the TAM market for the next five years. In the best case scenario, the market is expected to increase by ninety-five percent by 2026.
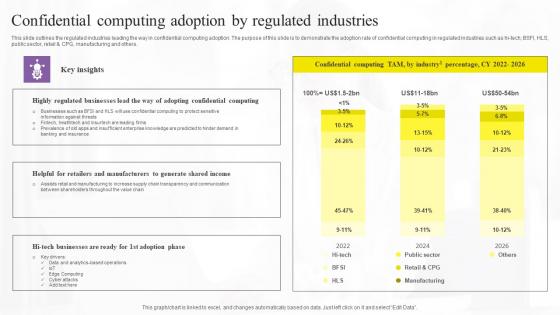
Confidential Computing Adoption By Confidential Computing Technologies Elements Pdf
This slide outlines the regulated industries leading the way in confidential computing adoption. The purpose of this slide is to demonstrate the adoption rate of confidential computing in regulated industries such as hi-tech, BSFI, HLS, public sector, retail and CPG, manufacturing and others. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Confidential Computing Adoption By Confidential Computing Technologies Elements Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Confidential Computing Adoption By Confidential Computing Technologies Elements Pdf today and make your presentation stand out from the rest This slide outlines the regulated industries leading the way in confidential computing adoption. The purpose of this slide is to demonstrate the adoption rate of confidential computing in regulated industries such as hi-tech, BSFI, HLS, public sector, retail and CPG, manufacturing and others.
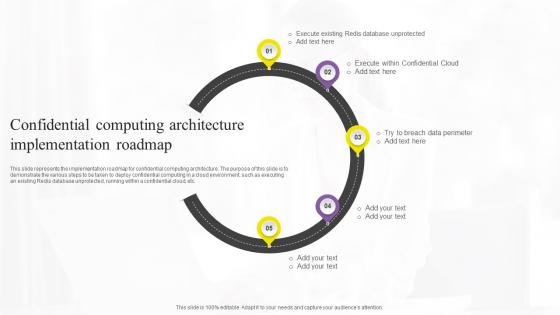
Confidential Computing Architecture Confidential Computing Technologies Diagrams Pdf
This slide represents the implementation roadmap for confidential computing architecture. The purpose of this slide is to demonstrate the various steps to be taken to deploy confidential computing in a cloud environment, such as executing an existing Redis database unprotected, running within a confidential cloud, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Confidential Computing Architecture Confidential Computing Technologies Diagrams Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide represents the implementation roadmap for confidential computing architecture. The purpose of this slide is to demonstrate the various steps to be taken to deploy confidential computing in a cloud environment, such as executing an existing Redis database unprotected, running within a confidential cloud, etc.
Logical Explanation Using Hands 6 Steps Flow Chart System PowerPoint Templates
We present our logical explanation using hands 6 steps flow chart system PowerPoint templates. Use our Handshake PowerPoint Templates because; Break it all down to Key Result Areas. Use our Process and Flows PowerPoint Templates because, Signpost your preferred roadmap to your eager co- travelers and demonstrate clearly how you intend to navigate them towards the desired corporate goal. Use our Business PowerPoint Templates because, Honesty is the best policy has an ardent follower in you. Use our Shapes PowerPoint Templates because, Saves your time a prized possession, an ideal aid to give an ideal presentation. Use our Signs PowerPoint Templates because, The Venn graphic comprising interlinking circles geometrically demonstrate how various functions operating independently, to a large extent, are essentially interdependent. Use these PowerPoint slides for presentations relating to Adult, alone, arranging, background, child, dirty, empty, family, handprint, hands, human, identity, illustration, isolated, messy, naked, objects, paint, palm, shape, simple, stage, stained, stamp, togetherness. The prominent colors used in the PowerPoint template are White, Blue, and Gray Grab the chance to use our Logical Explanation Using Hands 6 Steps Flow Chart System PowerPoint Templates. Dip your hand in the lucky basket.
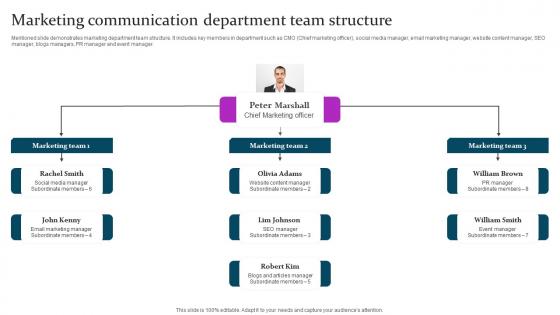
Marketing Communication Department Marketing Mix Communication Guide Client Structure Pdf
Mentioned slide demonstrates marketing department team structure. It includes key members in department such as CMO Chief marketing officer, social media manager, email marketing manager, website content manager, SEO manager, blogs managers, PR manager and event manager. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Marketing Communication Department Marketing Mix Communication Guide Client Structure Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Marketing Communication Department Marketing Mix Communication Guide Client Structure Pdf that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers Mentioned slide demonstrates marketing department team structure. It includes key members in department such as CMO Chief marketing officer, social media manager, email marketing manager, website content manager, SEO manager, blogs managers, PR manager and event manager.
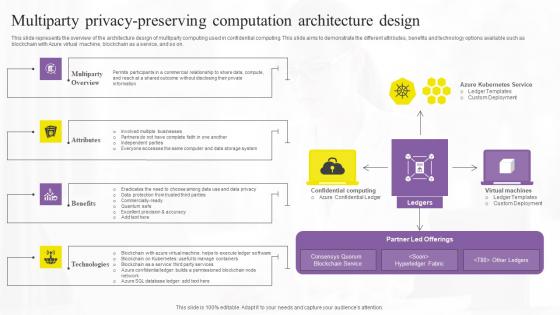
Multiparty Privacy Preserving Confidential Computing Technologies Rules Pdf
This slide represents the overview of the architecture design of multiparty computing used in confidential computing. This slide aims to demonstrate the different attributes, benefits and technology options available such as blockchain with Azure virtual machine, blockchain as a service, and so on. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Multiparty Privacy Preserving Confidential Computing Technologies Rules Pdf to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Multiparty Privacy Preserving Confidential Computing Technologies Rules Pdf. This slide represents the overview of the architecture design of multiparty computing used in confidential computing. This slide aims to demonstrate the different attributes, benefits and technology options available such as blockchain with Azure virtual machine, blockchain as a service, and so on.
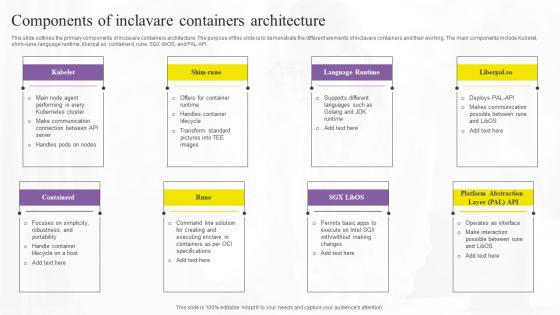
Components Of Inclavare Containers Confidential Computing Technologies Diagrams Pdf
This slide outlines the primary components of inclavare containers architecture. The purpose of this slide is to demonstrate the different elements of inclavare containers and their working. The main components include Kubelet, shim-rune, language runtime, liberpal.so, containerd, rune, SGX libOS, and PAL-API. Slidegeeks is here to make your presentations a breeze with Components Of Inclavare Containers Confidential Computing Technologies Diagrams Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide outlines the primary components of inclavare containers architecture. The purpose of this slide is to demonstrate the different elements of inclavare containers and their working. The main components include Kubelet, shim-rune, language runtime, liberpal.so, containerd, rune, SGX libOS, and PAL-API.
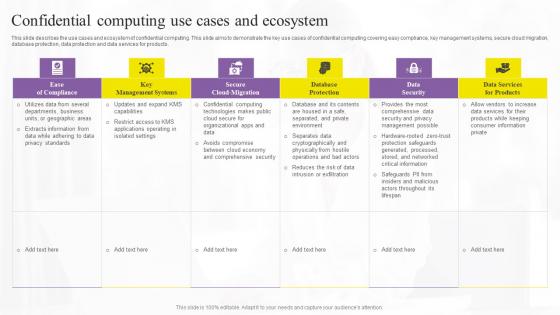
Confidential Computing Use Cases Confidential Computing Technologies Portrait Pdf
This slide describes the use cases and ecosystem of confidential computing. This slide aims to demonstrate the key use cases of confidential computing covering easy compliance, key management systems, secure cloud migration, database protection, data protection and data services for products. Slidegeeks has constructed Confidential Computing Use Cases Confidential Computing Technologies Portrait Pdf after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide describes the use cases and ecosystem of confidential computing. This slide aims to demonstrate the key use cases of confidential computing covering easy compliance, key management systems, secure cloud migration, database protection, data protection and data services for products.
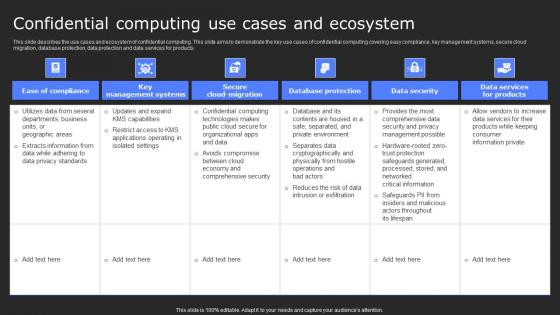
Confidential Computing Use Cases And Ecosystem Secure Computing Framework Guidelines Pdf
This slide describes the use cases and ecosystem of confidential computing. This slide aims to demonstrate the key use cases of confidential computing covering easy compliance, key management systems, secure cloud migration, database protection, data protection and data services for products. The Confidential Computing Use Cases And Ecosystem Secure Computing Framework Guidelines Pdf is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide describes the use cases and ecosystem of confidential computing. This slide aims to demonstrate the key use cases of confidential computing covering easy compliance, key management systems, secure cloud migration, database protection, data protection and data services for products.

Zero Trust Network Access Comparative Assessment Of ZTNA Version 1 0 And 2 0
This slide represents the comparison between zero trust network access versions 1.0 and 2.0. The purpose of this slide is to demonstrate the overview of both versions, including differences. It also includes the architecture of both versions of zero-trust network access. This Zero Trust Network Access Comparative Assessment Of ZTNA Version 1 0 And 2 0 is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Zero Trust Network Access Comparative Assessment Of ZTNA Version 1 0 And 2 0 features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide represents the comparison between zero trust network access versions 1.0 and 2.0. The purpose of this slide is to demonstrate the overview of both versions, including differences. It also includes the architecture of both versions of zero-trust network access.

Optimizing Client Lead Handling Effective Strategy For Qualified Leads Generation Graphics Pdf
This slide covers 4 major ways of generating qualified leads. It includes steps such as creating a customer-centric message, demonstrating how products and services will help customers, trial and error iterations for creating a message and using Forresters checklist for reviewing the message. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Optimizing Client Lead Handling Effective Strategy For Qualified Leads Generation Graphics Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Optimizing Client Lead Handling Effective Strategy For Qualified Leads Generation Graphics Pdf today and make your presentation stand out from the rest. This slide covers 4 major ways of generating qualified leads. It includes steps such as creating a customer-centric message, demonstrating how products and services will help customers, trial and error iterations for creating a message and using Forresters checklist for reviewing the message.
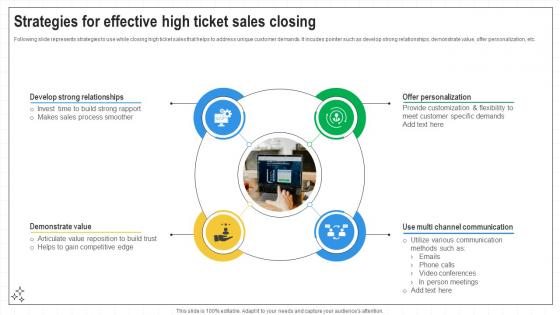
Closing Techniques To Seal Strategies For Effective High Ticket Sales Closing SA SS V
Following slide represents strategies to use while closing high ticket sales that helps to address unique customer demands. It incudes pointer such as develop strong relationships, demonstrate value, offer personalization, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Closing Techniques To Seal Strategies For Effective High Ticket Sales Closing SA SS V a try. Our experts have put a lot of knowledge and effort into creating this impeccable Closing Techniques To Seal Strategies For Effective High Ticket Sales Closing SA SS V. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today Following slide represents strategies to use while closing high ticket sales that helps to address unique customer demands. It incudes pointer such as develop strong relationships, demonstrate value, offer personalization, etc.
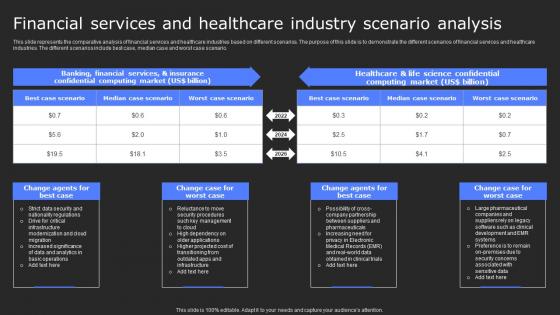
Financial Services And Healthcare Industry Scenario Secure Computing Framework Clipart Pdf
This slide represents the comparative analysis of financial services and healthcare industries based on different scenarios. The purpose of this slide is to demonstrate the different scenarios of financial services and healthcare industries. The different scenarios include best case, median case and worst case scenario. Retrieve professionally designed Financial Services And Healthcare Industry Scenario Secure Computing Framework Clipart Pdf to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide represents the comparative analysis of financial services and healthcare industries based on different scenarios. The purpose of this slide is to demonstrate the different scenarios of financial services and healthcare industries. The different scenarios include best case, median case and worst case scenario.
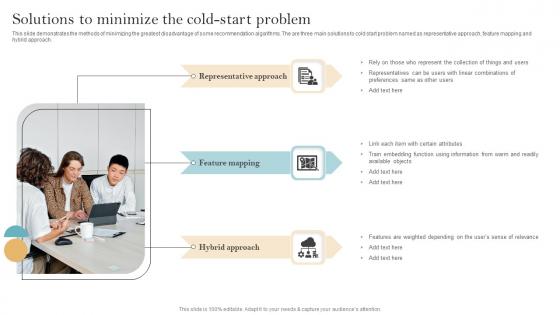
Recommender System Implementation Solutions To Minimize The Cold Start Problem Summary Pdf
This slide demonstrates the methods of minimizing the greatest disadvantage of some recommendation algorithms. The are three main solutions to cold start problem named as representative approach, feature mapping and hybrid approach. If you are looking for a format to display your unique thoughts, then the professionally designed Recommender System Implementation Solutions To Minimize The Cold Start Problem Summary Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Recommender System Implementation Solutions To Minimize The Cold Start Problem Summary Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide demonstrates the methods of minimizing the greatest disadvantage of some recommendation algorithms. The are three main solutions to cold start problem named as representative approach, feature mapping and hybrid approach.
8 Diverging Factors Arrow Flow Chart Circular Process PowerPoint Slides
We present our 8 diverging factors arrow flow chart Circular Process PowerPoint Slides.Download and present our Arrows PowerPoint Templates because the vision of being the market leader is clear to you. Use our Circle Charts PowerPoint Templates because this amazing layout demonstrates how they all combine to form the final product. Present our Shapes PowerPoint Templates because the colour coding of our templates are specifically designed to highlight you points. Download our Business PowerPoint Templates because The foundation of the structure of your business is resilient and dependable. Convey this confidence to your colleagues and assure them of a great and enduring future. Present our Flow Charts PowerPoint Templates because you can Refine them all as you take them through the numerous filtering stages of the funnel of your quality control process.Use these PowerPoint slides for presentations relating to abstract, arrow, brochure, business, businessman, button, chart, circle, company, cyclic, data, demonstration, diagram, economic, financial, five, glossy, goal, graph, illustration, info, information, investment, man, manage, marketing, model, navigation, option, part, people, person, pie, presentation, process, result, section, segmented, sharing, silhouette, sphere, statistics, stock, strategy, template, variation, vector, wheel. The prominent colors used in the PowerPoint template are Red, Pink, Purple. Presenters tell us our 8 diverging factors arrow flow chart Circular Process PowerPoint Slides are Second to none. You can be sure our company PowerPoint templates and PPT Slides are Upbeat. Professionals tell us our 8 diverging factors arrow flow chart Circular Process PowerPoint Slides are incredible easy to use. People tell us our circle PowerPoint templates and PPT Slides are Sparkling. People tell us our 8 diverging factors arrow flow chart Circular Process PowerPoint Slides are Cheerful. Professionals tell us our button PowerPoint templates and PPT Slides are Appealing. Facilitate the assimilation of your ideas. Our 8 Diverging Factors Arrow Flow Chart Circular Process PowerPoint Slides make it esier to digest.
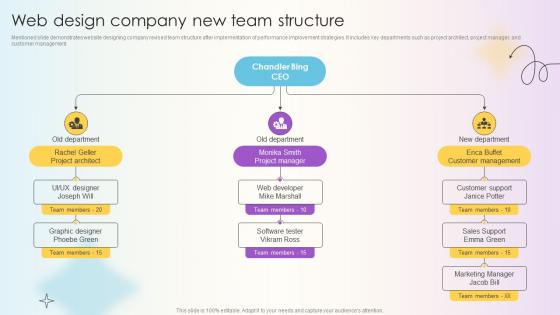
Managing Technical And Non Technical Web Design Company New Team Structure
Mentioned slide demonstrates website designing company revised team structure after implementation of performance improvement strategies. It includes key departments such as project architect, project manager, and customer management. If you are looking for a format to display your unique thoughts, then the professionally designed Managing Technical And Non Technical Web Design Company New Team Structure is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Managing Technical And Non Technical Web Design Company New Team Structure and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. Mentioned slide demonstrates website designing company revised team structure after implementation of performance improvement strategies. It includes key departments such as project architect, project manager, and customer management.
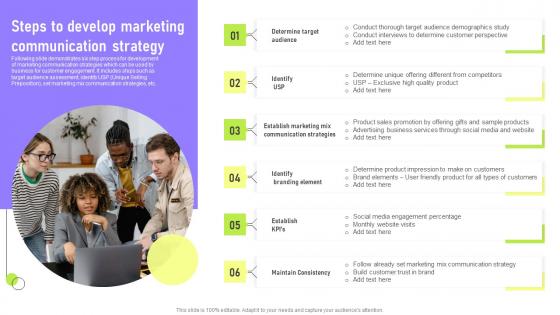
Steps To Develop Marketing Deployment Of Marketing Communication Elements Pdf
Following slide demonstrates six step process for development of marketing communication strategies which can be used by business for customer engagement. It includes steps such as target audience assessment, identify USP Unique Selling Preposition, set marketing mix communication strategies, etc. This Steps To Develop Marketing Deployment Of Marketing Communication Elements Pdf is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Steps To Develop Marketing Deployment Of Marketing Communication Elements Pdf features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today Following slide demonstrates six step process for development of marketing communication strategies which can be used by business for customer engagement. It includes steps such as target audience assessment, identify USP Unique Selling Preposition, set marketing mix communication strategies, etc.
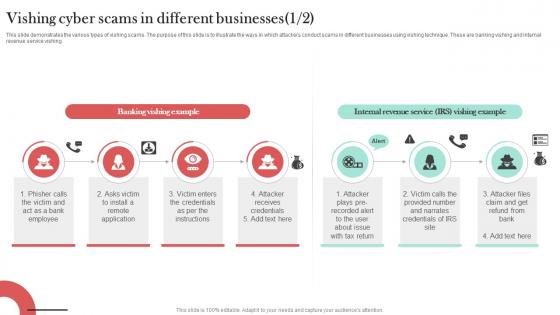
Vishing Cyber Scams In Different Businesses Man In The Middle Phishing IT
This slide demonstrates the various types of vishing scams. The purpose of this slide is to illustrate the ways in which attackers conduct scams in different businesses using vishing technique. These are banking vishing and internal revenue service vishing. Are you searching for a Vishing Cyber Scams In Different Businesses Man In The Middle Phishing IT that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Vishing Cyber Scams In Different Businesses Man In The Middle Phishing IT from Slidegeeks today. This slide demonstrates the various types of vishing scams. The purpose of this slide is to illustrate the ways in which attackers conduct scams in different businesses using vishing technique. These are banking vishing and internal revenue service vishing.

About Phishing Attacks Overview And Impact Man In The Middle Phishing IT
This slide demonstrates the overview of cyber phishing attacks. The purpose of this slide is to talk about the effectiveness of phishing scams. This slide also outlines the issues which can be caused by phishing attacks such as disclosure of private data, etc. Get a simple yet stunning designed About Phishing Attacks Overview And Impact Man In The Middle Phishing IT. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit About Phishing Attacks Overview And Impact Man In The Middle Phishing IT can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide demonstrates the overview of cyber phishing attacks. The purpose of this slide is to talk about the effectiveness of phishing scams. This slide also outlines the issues which can be caused by phishing attacks such as disclosure of private data, etc.

Examples Of Clone Phishing Cyber Scams Man In The Middle Phishing IT
This slide demonstrates the various examples of clone phishing cyber scams. The purpose of this slide is to illustrate different types of clone phishing emails targeting different individuals. These include customer support scams, fake virus scams and refund scams. This Examples Of Clone Phishing Cyber Scams Man In The Middle Phishing IT is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Examples Of Clone Phishing Cyber Scams Man In The Middle Phishing IT features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide demonstrates the various examples of clone phishing cyber scams. The purpose of this slide is to illustrate different types of clone phishing emails targeting different individuals. These include customer support scams, fake virus scams and refund scams.
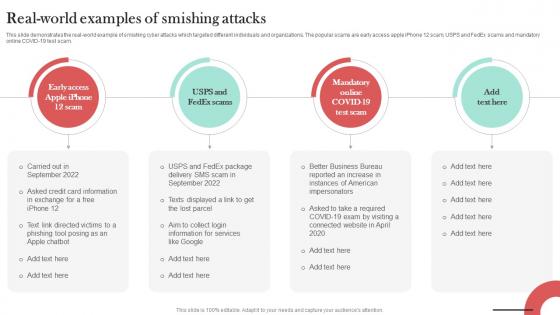
Real World Examples Of Smishing Attacks Man In The Middle Phishing IT
This slide demonstrates the real-world example of smishing cyber attacks which targeted different individuals and organizations. The popular scams are early access apple iPhone 12 scam, USPS and FedEx scams and mandatory online COVID-19 test scam. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Real World Examples Of Smishing Attacks Man In The Middle Phishing IT. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Real World Examples Of Smishing Attacks Man In The Middle Phishing IT today and make your presentation stand out from the rest This slide demonstrates the real-world example of smishing cyber attacks which targeted different individuals and organizations. The popular scams are early access apple iPhone 12 scam, USPS and FedEx scams and mandatory online COVID-19 test scam.

Resources And Training That Companies Man In The Middle Phishing IT
This slide demonstrates the resources and training that can be provided by companies to their staff. These include employee training, check to see if youve already been breached, be aware of the various phishing attacks, invest in security education, etc. Find highly impressive Resources And Training That Companies Man In The Middle Phishing IT on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Resources And Training That Companies Man In The Middle Phishing IT for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide demonstrates the resources and training that can be provided by companies to their staff. These include employee training, check to see if youve already been breached, be aware of the various phishing attacks, invest in security education, etc.
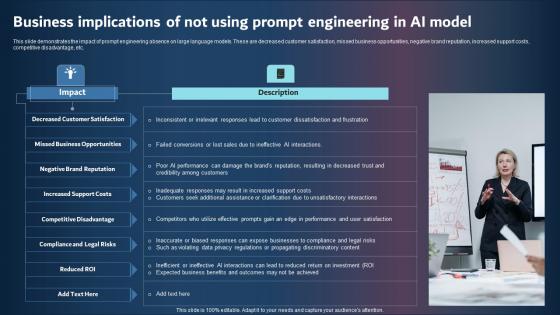
Business Implications Of Not Using Prompt Engineering In AI Model Information PDF
This slide demonstrates the impact of prompt engineering absence on large language models. These are decreased customer satisfaction, missed business opportunities, negative brand reputation, increased support costs, competitive disadvantage, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Business Implications Of Not Using Prompt Engineering In AI Model Information Pdf can be your best option for delivering a presentation. Represent everything in detail using Business Implications Of Not Using Prompt Engineering In AI Model Information Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide demonstrates the impact of prompt engineering absence on large language models. These are decreased customer satisfaction, missed business opportunities, negative brand reputation, increased support costs, competitive disadvantage, etc.
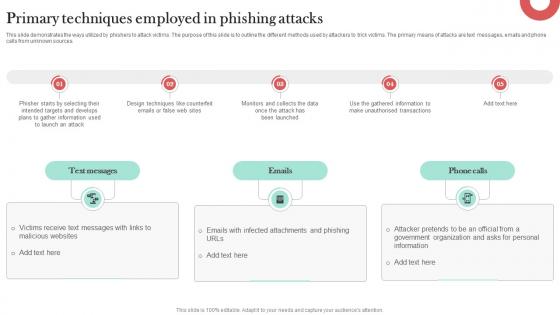
Primary Techniques Employed In Phishing Man In The Middle Phishing IT
This slide demonstrates the ways utilized by phishers to attack victims. The purpose of this slide is to outline the different methods used by attackers to trick victims. The primary means of attacks are text messages, emails and phone calls from unknown sources. Slidegeeks is here to make your presentations a breeze with Primary Techniques Employed In Phishing Man In The Middle Phishing IT With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide demonstrates the ways utilized by phishers to attack victims. The purpose of this slide is to outline the different methods used by attackers to trick victims. The primary means of attacks are text messages, emails and phone calls from unknown sources.

Tools Provided By Google To Prevent Man In The Middle Phishing IT
This slide demonstrates the different tools provided by Google to prevent and report cyber phishing scams. These include to spot phishing mails with the help of Gmail, utilize safe browsing in chrome, look for unsafe saved passwords, password alert for chrome, etc. Welcome to our selection of the Tools Provided By Google To Prevent Man In The Middle Phishing IT. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide demonstrates the different tools provided by Google to prevent and report cyber phishing scams. These include to spot phishing mails with the help of Gmail, utilize safe browsing in chrome, look for unsafe saved passwords, password alert for chrome, etc.
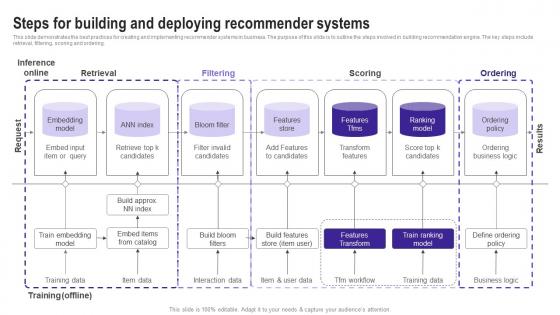
Steps For Building And Deploying Recommender Use Cases Of Filtering Methods Clipart Pdf
This slide demonstrates the best practices for creating and implementing recommender systems in business. The purpose of this slide is to outline the steps involved in building recommendation engine. The key steps include retrieval, filtering, scoring and ordering. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Steps For Building And Deploying Recommender Use Cases Of Filtering Methods Clipart Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide demonstrates the best practices for creating and implementing recommender systems in business. The purpose of this slide is to outline the steps involved in building recommendation engine. The key steps include retrieval, filtering, scoring and ordering.
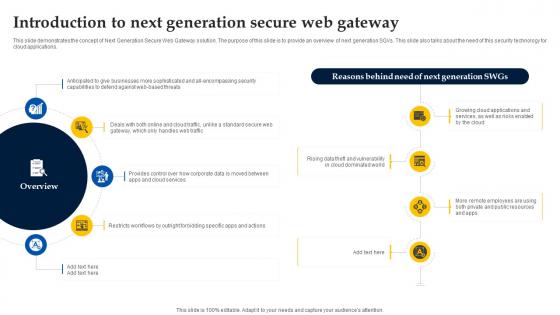
Web Access Control Solution Introduction To Next Generation Secure Web Gateway
This slide demonstrates the concept of Next Generation Secure Web Gateway solution. The purpose of this slide is to provide an overview of next generation SGVs. This slide also talks about the need of this security technology for cloud applications. Are you searching for a Web Access Control Solution Introduction To Next Generation Secure Web Gateway that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Web Access Control Solution Introduction To Next Generation Secure Web Gateway from Slidegeeks today. This slide demonstrates the concept of Next Generation Secure Web Gateway solution. The purpose of this slide is to provide an overview of next generation SGVs. This slide also talks about the need of this security technology for cloud applications.
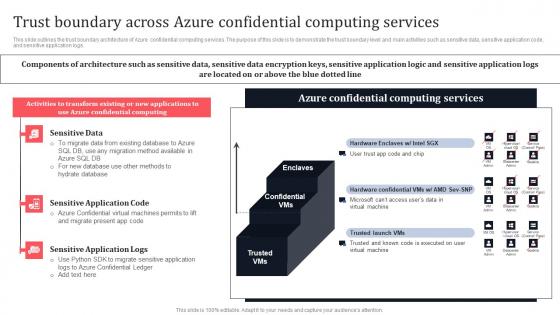
Trust Boundary Across Azure Confidential Computing Services Secure Multi Party Ideas Pdf
This slide outlines the trust boundary architecture of Azure confidential computing services. The purpose of this slide is to demonstrate the trust boundary level and main activities such as sensitive data, sensitive application code, and sensitive application logs. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Trust Boundary Across Azure Confidential Computing Services Secure Multi Party Ideas Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide outlines the trust boundary architecture of Azure confidential computing services. The purpose of this slide is to demonstrate the trust boundary level and main activities such as sensitive data, sensitive application code, and sensitive application logs.
Linear Flow Arrow 4 Stages Online Flowchart Maker PowerPoint Slides
We present our linear flow arrow 4 stages online flowchart maker PowerPoint Slides. Use our Success PowerPoint Templates because; demonstrate how you think out of the box. Use our Arrows PowerPoint Templates because, The Venn graphic comprising interlinking circles geometrically demonstrate how various functions operating independently, to a large extent, are essentially interdependent. Use our Business PowerPoint Templates because, Marketing Strategy Business Template: - Maximizing sales of your product is the intended destination. Use our Shapes PowerPoint Templates because; Use this template containing to highlight the key issues of your presentation. Use our Process and Flows PowerPoint Templates because, there are different paths to gain the necessary knowledge to achieved it. Use these PowerPoint slides for presentations relating to 3d, abstract, around, arrows, business, center, circle, circular, concept, connections, curve, cycle, directions, distribution, illustration, management, middle, objects, plan, process, recycle, rounded, shadows, space, system. The prominent colors used in the PowerPoint template are Red, Black, and Gray Be as fastidious as you want to be. Our Linear Flow Arrow 4 Stages Online Flowchart Maker PowerPoint Slides will be more than a match.

Zero Trust Network Access ZTNA Introduction Graphics Pdf
This slide represents the overview of zero trust network access, including its, benefits and principles. The purpose of this slide is to demonstrate the overview, principles and benefits of ZTNA. The primary benefits include seamless user experience, effortless scale, no need for legacy applications, etc. Find highly impressive Zero Trust Network Access ZTNA Introduction Graphics Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Zero Trust Network Access ZTNA Introduction Graphics Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide represents the overview of zero trust network access, including its, benefits and principles. The purpose of this slide is to demonstrate the overview, principles and benefits of ZTNA. The primary benefits include seamless user experience, effortless scale, no need for legacy applications, etc.
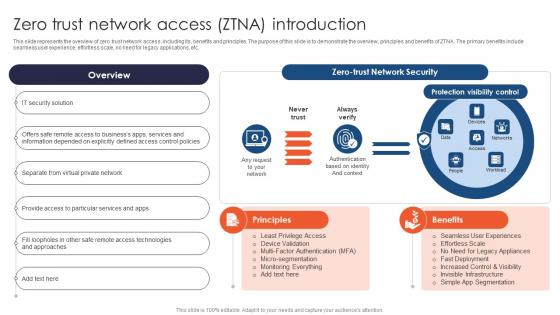
Zero Trust Network Access ZTNA Introduction Ppt File Infographic Template
This slide represents the overview of zero trust network access, including its, benefits and principles. The purpose of this slide is to demonstrate the overview, principles and benefits of ZTNA. The primary benefits include seamless user experience, effortless scale, no need for legacy applications, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Zero Trust Network Access ZTNA Introduction Ppt File Infographic Template to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Zero Trust Network Access ZTNA Introduction Ppt File Infographic Template. This slide represents the overview of zero trust network access, including its, benefits and principles. The purpose of this slide is to demonstrate the overview, principles and benefits of ZTNA. The primary benefits include seamless user experience, effortless scale, no need for legacy applications, etc.
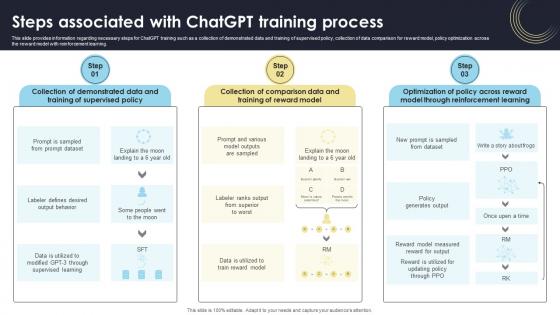
Steps Associated With ChatGPT Training Process How Generative AI Tools Work AI SS V
This slide provides information regarding necessary steps for ChatGPT training such as a collection of demonstrated data and training of supervised policy, collection of data comparison for reward model, policy optimization across the reward model with reinforcement learning. This Steps Associated With ChatGPT Training Process How Generative AI Tools Work AI SS V is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Steps Associated With ChatGPT Training Process How Generative AI Tools Work AI SS V features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide provides information regarding necessary steps for ChatGPT training such as a collection of demonstrated data and training of supervised policy, collection of data comparison for reward model, policy optimization across the reward model with reinforcement learning.

Benefits Of Zero Trust Network Security Portrait Pdf
This slide represents the benefits of zero trust network access, a component of SASE technology. The purpose of this slide is to demonstrate the multiple benefits of ZTNA to businesses and users. It also caters to the security benefits such as increased control and visibility, invisible infrastructure, and simple app segmentation. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Benefits Of Zero Trust Network Security Portrait Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide represents the benefits of zero trust network access, a component of SASE technology. The purpose of this slide is to demonstrate the multiple benefits of ZTNA to businesses and users. It also caters to the security benefits such as increased control AND visibility, invisible infrastructure, and simple app segmentation.
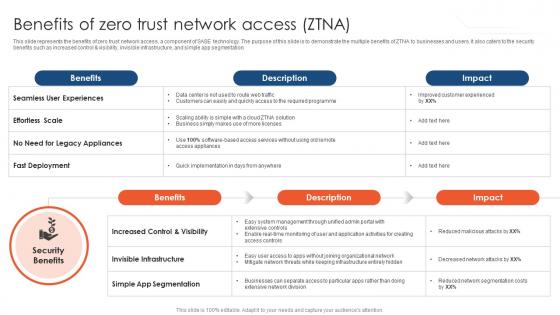
Zero Trust Network Access Benefits Of Zero Trust Network Access ZTNA
This slide represents the benefits of zero trust network access, a component of SASE technology. The purpose of this slide is to demonstrate the multiple benefits of ZTNA to businesses and users. It also caters to the security benefits such as increased control and visibility, invisible infrastructure, and simple app segmentation. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Zero Trust Network Access Benefits Of Zero Trust Network Access ZTNA template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Zero Trust Network Access Benefits Of Zero Trust Network Access ZTNA that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide represents the benefits of zero trust network access, a component of SASE technology. The purpose of this slide is to demonstrate the multiple benefits of ZTNA to businesses and users. It also caters to the security benefits such as increased control and visibility, invisible infrastructure, and simple app segmentation.
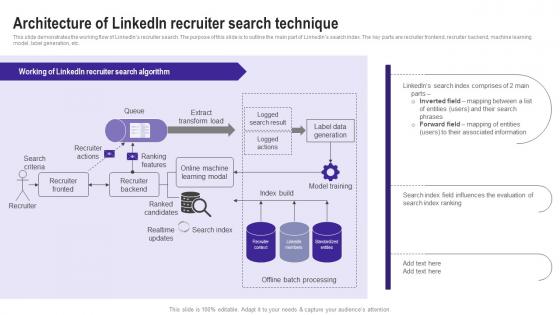
Architecture Of Linkedin Use Cases Of Filtering Methods Rules Pdf
This slide demonstrates the working flow of LinkedIns recruiter search. The purpose of this slide is to outline the main part of LinkedIns search index. The key parts are recruiter frontend, recruiter backend, machine learning model, label generation, etc. Get a simple yet stunning designed Architecture Of Linkedin Use Cases Of Filtering Methods Rules Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Architecture Of Linkedin Use Cases Of Filtering Methods Rules Pdf can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide demonstrates the working flow of LinkedIns recruiter search. The purpose of this slide is to outline the main part of LinkedIns search index. The key parts are recruiter frontend, recruiter backend, machine learning model, label generation, etc.
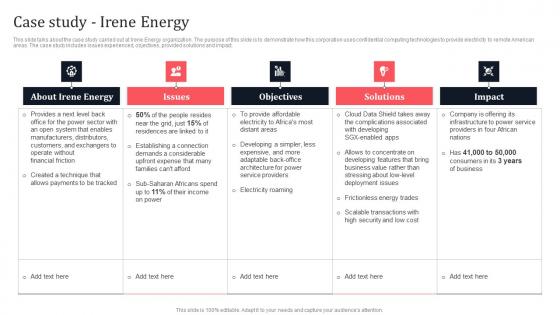
Case Study Irene Energy Secure Multi Party Sample Pdf
This slide talks about the case study carried out at Irene Energy organization. The purpose of this slide is to demonstrate how this corporation uses confidential computing technologies to provide electricity to remote American areas. The case study includes issues experienced, objectives, provided solutions and impact. Create an editable Case Study Irene Energy Secure Multi Party Sample Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Case Study Irene Energy Secure Multi Party Sample Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide talks about the case study carried out at Irene Energy organization. The purpose of this slide is to demonstrate how this corporation uses confidential computing technologies to provide electricity to remote American areas. The case study includes issues experienced, objectives, provided solutions and impact.

Comparison Between Secure Web Gateway And Firewalls Web Threat Protection System
This slide demonstrates the concept of two security technologies named firewalls and Secure Web Gateways. The purpose of this slide is to compare firewalls and SWGs on the basis of various factors such as function, scope, granularity, features and deployment. Present like a pro with Comparison Between Secure Web Gateway And Firewalls Web Threat Protection System. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide demonstrates the concept of two security technologies named firewalls and Secure Web Gateways. The purpose of this slide is to compare firewalls and SWGs on the basis of various factors such as function, scope, granularity, features and deployment.
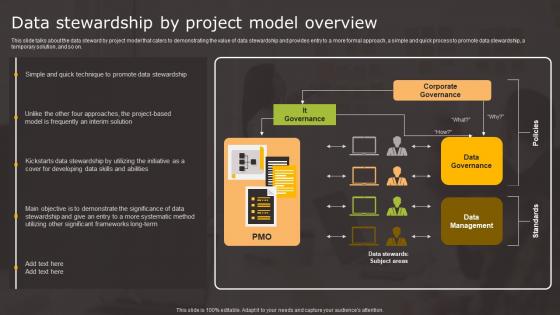
Data Stewardship By Project Data Stewardship In Business Processes Template Pdf
This slide talks about the data steward by project model that caters to demonstrating the value of data stewardship and provides entry to a more formal approach, a simple and quick process to promote data stewardship, a temporary solution, and so on. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Data Stewardship By Project Data Stewardship In Business Processes Template Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide talks about the data steward by project model that caters to demonstrating the value of data stewardship and provides entry to a more formal approach, a simple and quick process to promote data stewardship, a temporary solution, and so on.
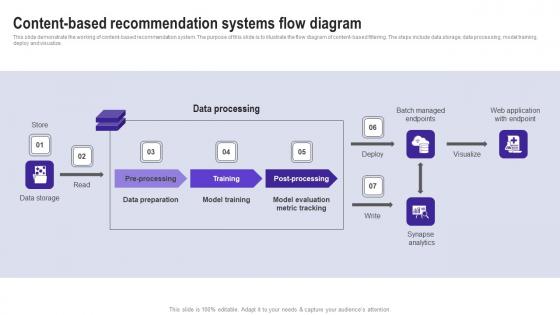
Content Based Recommendation Systems Flow Diagram Use Cases Of Filtering Methods Mockup Pdf
This slide demonstrate the working of content based recommendation system. The purpose of this slide is to illustrate the flow diagram of content based filtering. The steps include data storage, data processing, model training, deploy and visualize. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Content Based Recommendation Systems Flow Diagram Use Cases Of Filtering Methods Mockup Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide demonstrate the working of content based recommendation system. The purpose of this slide is to illustrate the flow diagram of content based filtering. The steps include data storage, data processing, model training, deploy and visualize.
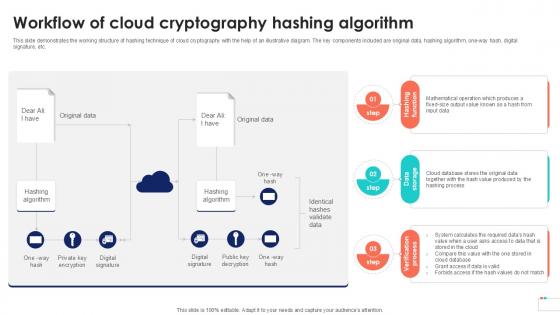
Workflow Of Cloud Cryptography Data Security In Cloud Computing Ppt Example
This slide demonstrates the working structure of hashing technique of cloud cryptography with the help of an illustrative diagram. The key components included are original data, hashing algorithm, one-way hash, digital signature, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Workflow Of Cloud Cryptography Data Security In Cloud Computing Ppt Example is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Workflow Of Cloud Cryptography Data Security In Cloud Computing Ppt Example and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide demonstrates the working structure of hashing technique of cloud cryptography with the help of an illustrative diagram. The key components included are original data, hashing algorithm, one-way hash, digital signature, etc.
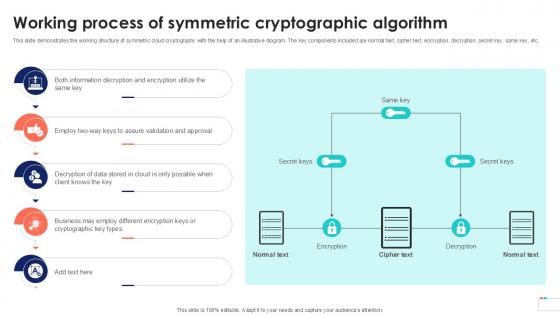
Working Process Of Symmetric Data Security In Cloud Computing Ppt Template
This slide demonstrates the working structure of symmetric cloud cryptography with the help of an illustrative diagram. The key components included are normal text, cipher text, encryption, decryption, secret key, same key, etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Working Process Of Symmetric Data Security In Cloud Computing Ppt Template was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Working Process Of Symmetric Data Security In Cloud Computing Ppt Template This slide demonstrates the working structure of symmetric cloud cryptography with the help of an illustrative diagram. The key components included are normal text, cipher text, encryption, decryption, secret key, same key, etc.

Recommendation Techniques Approaches To Setup Recommender System In Business Elements PDF
This slide demonstrates various approaches that can be used to setup a recommender system . These methods include using an already existing system, building your own solution, consulting experts and arranging competitions to get a good recommender. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Recommendation Techniques Approaches To Setup Recommender System In Business Elements PDF can be your best option for delivering a presentation. Represent everything in detail using Recommendation Techniques Approaches To Setup Recommender System In Business Elements PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide demonstrates various approaches that can be used to setup a recommender system . These methods include using an already existing system, building your own solution, consulting experts and arranging competitions to get a good recommender.
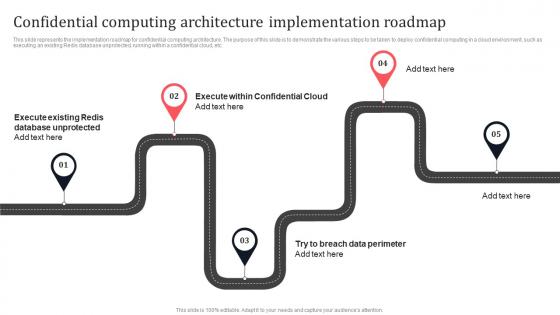
Confidential Computing Architecture Implementation Roadmap Secure Multi Party Formats Pdf
This slide represents the implementation roadmap for confidential computing architecture. The purpose of this slide is to demonstrate the various steps to be taken to deploy confidential computing in a cloud environment, such as executing an existing Redis database unprotected, running within a confidential cloud, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Confidential Computing Architecture Implementation Roadmap Secure Multi Party Formats Pdf can be your best option for delivering a presentation. Represent everything in detail using Confidential Computing Architecture Implementation Roadmap Secure Multi Party Formats Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide represents the implementation roadmap for confidential computing architecture. The purpose of this slide is to demonstrate the various steps to be taken to deploy confidential computing in a cloud environment, such as executing an existing Redis database unprotected, running within a confidential cloud, etc.
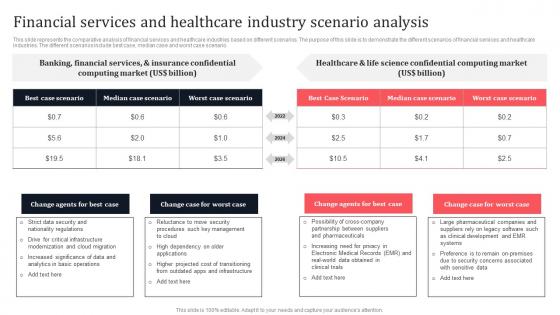
Financial Services And Healthcare Industry Scenario Analysis Secure Multi Party Sample Pdf
This slide represents the comparative analysis of financial services and healthcare industries based on different scenarios. The purpose of this slide is to demonstrate the different scenarios of financial services and healthcare industries. The different scenarios include best case, median case and worst case scenario. The Financial Services And Healthcare Industry Scenario Analysis Secure Multi Party Sample Pdf is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide represents the comparative analysis of financial services and healthcare industries based on different scenarios. The purpose of this slide is to demonstrate the different scenarios of financial services and healthcare industries. The different scenarios include best case, median case and worst case scenario.

Cryptographic Cloud Security Solution Cloud Data Security Using Cryptography Inspiration Pdf
This slide demonstrates the top cloud cryptography solution providers. The purpose of this slide is to outline the price and features of these service providers. These include Amazon Web Services Key Management Service AWS KMS, Microsoft Azure Key Vault, Google Cloud KMS, etc. The Cryptographic Cloud Security Solution Cloud Data Security Using Cryptography Inspiration Pdf is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide demonstrates the top cloud cryptography solution providers. The purpose of this slide is to outline the price and features of these service providers. These include Amazon Web Services Key Management Service AWS KMS, Microsoft Azure Key Vault, Google Cloud KMS, etc.

Web Access Control Solution Best Practices For Secure Web Gateway Implementation
This slide outlines various measures to be taken to maintain and enhance the functionality of Secure Web Gateway. The purpose of this slide is to demonstrate best practices for SWG. These are perform a risk assessment, deploy safe setups, monitor and analyse traffic, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Web Access Control Solution Best Practices For Secure Web Gateway Implementation can be your best option for delivering a presentation. Represent everything in detail using Web Access Control Solution Best Practices For Secure Web Gateway Implementation and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide outlines various measures to be taken to maintain and enhance the functionality of Secure Web Gateway. The purpose of this slide is to demonstrate best practices for SWG. These are perform a risk assessment, deploy safe setups, monitor and analyse traffic, etc.

Web Access Control Solution Steps To Select Next Generation Secure Web Gateway
This slide demonstrates the points to be kept in mind while choosing next generation secure web gateway. The purpose of this slide is to explain how to select a next generation SWG. These are adopt real cloud architecture, adapts to new threats, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Web Access Control Solution Steps To Select Next Generation Secure Web Gateway can be your best option for delivering a presentation. Represent everything in detail using Web Access Control Solution Steps To Select Next Generation Secure Web Gateway and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide demonstrates the points to be kept in mind while choosing next generation secure web gateway. The purpose of this slide is to explain how to select a next generation SWG. These are adopt real cloud architecture, adapts to new threats, etc.
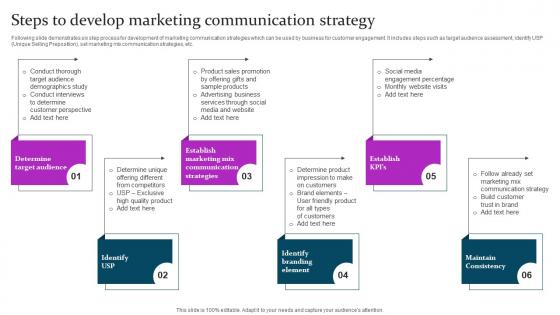
Marketing Mix Communication Guide Client Steps To Develop Marketing Download Pdf
Following slide demonstrates six step process for development of marketing communication strategies which can be used by business for customer engagement. It includes steps such as target audience assessment, identify USP Unique Selling Preposition, set marketing mix communication strategies, etc. This Marketing Mix Communication Guide Client Steps To Develop Marketing Download Pdf from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. Following slide demonstrates six step process for development of marketing communication strategies which can be used by business for customer engagement. It includes steps such as target audience assessment, identify USP Unique Selling Preposition, set marketing mix communication strategies, etc.

Network Security Using Firewall As A Service Table Of Contents Designs Pdf
This slide demonstrates the flow of traffic within a network secured with firewall. The purpose of this slide is to illustrate the meaning of good and bad traffic. This slide also highlights the factors which are used to analyze the nature of data packets. This Network Security Using Firewall As A Service Table Of Contents Designs Pdf from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide demonstrates the flow of traffic within a network secured with firewall. The purpose of this slide is to illustrate the meaning of good and bad traffic. This slide also highlights the factors which are used to analyze the nature of data packets.


 Continue with Email
Continue with Email

 Home
Home


































