Speech Bubbles
Introduction To Recommender Systems Use Cases Of Filtering Methods Diagrams Pdf
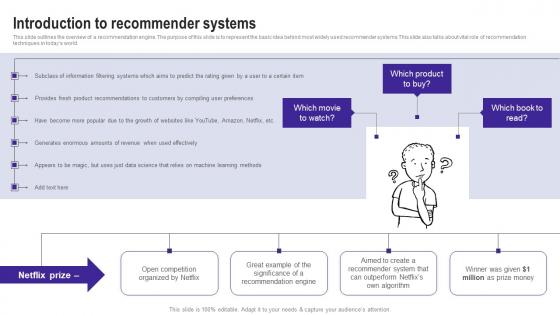
This slide outlines the overview of a recommendation engine. The purpose of this slide is to represent the basic idea behind most widely used recommender systems.This slide also talks about vital role of recommendation techniques in todays world. Take your projects to the next level with our ultimate collection of Introduction To Recommender Systems Use Cases Of Filtering Methods Diagrams Pdf. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest This slide outlines the overview of a recommendation engine. The purpose of this slide is to represent the basic idea behind most widely used recommender systems.This slide also talks about vital role of recommendation techniques in todays world.
Item Item Memory Based Collaborative Filtering Use Cases Of Filtering Methods Introduction Pdf
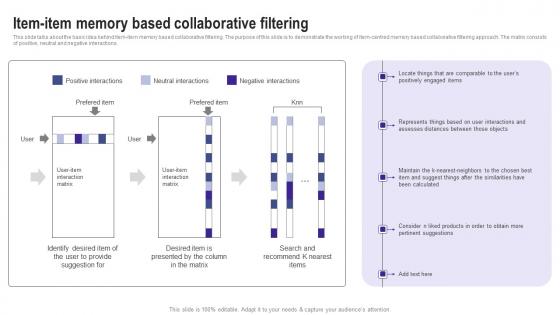
This slide talks about the basic idea behind item item memory based collaborative filtering. The purpose of this slide is to demonstrate the working of item centred memory based collaborative filtering approach. The matrix consists of positive, neutral and negative interactions. Find a pre designed and impeccable Item Item Memory Based Collaborative Filtering Use Cases Of Filtering Methods Introduction Pdf. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide talks about the basic idea behind item item memory based collaborative filtering. The purpose of this slide is to demonstrate the working of item centred memory based collaborative filtering approach. The matrix consists of positive, neutral and negative interactions.
Matrix Factorization And Embeddings Of Neural Nets Use Cases Of Filtering Methods Structure Pdf
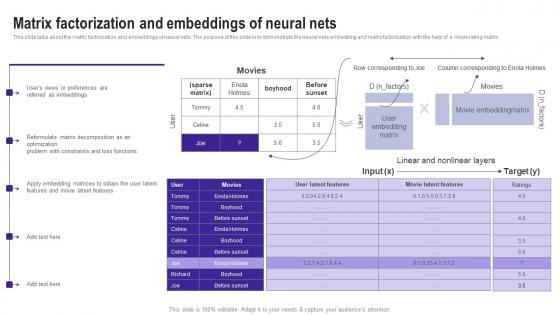
This slide talks about the matrix factorization and embeddings of neural nets. The purpose of this slide is to demonstrate the neural nets embedding and matrix factorization with the help of a movie rating matrix. Create an editable Matrix Factorization And Embeddings Of Neural Nets Use Cases Of Filtering Methods Structure Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Matrix Factorization And Embeddings Of Neural Nets Use Cases Of Filtering Methods Structure Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide talks about the matrix factorization and embeddings of neural nets. The purpose of this slide is to demonstrate the neural nets embedding and matrix factorization with the help of a movie rating matrix.
Memory Based Collaborative Filtering Techniques Use Cases Of Filtering Methods Rules Pdf
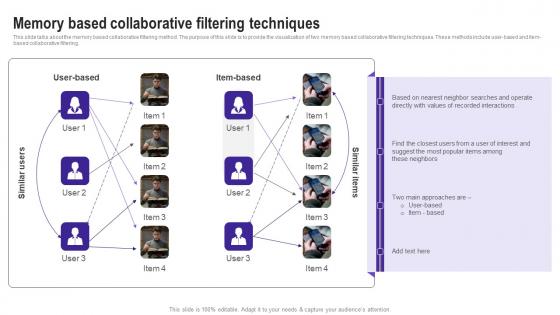
This slide talks about the memory based collaborative filtering method. The purpose of this slide is to provide the visualization of two memory based collaborative filtering techniques. These methods include user based and item based collaborative filtering. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Memory Based Collaborative Filtering Techniques Use Cases Of Filtering Methods Rules Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide talks about the memory based collaborative filtering method. The purpose of this slide is to provide the visualization of two memory based collaborative filtering techniques. These methods include user based and item based collaborative filtering.

Primary Steps To Build Recommender System Use Cases Of Filtering Methods Portrait Pdf
This slide talks about four steps to build a recommender system. The purpose of this slide is to explain the procedure of developing a recommendation engine. These steps include pre processing, learning, evaluation and prediction. Get a simple yet stunning designed Primary Steps To Build Recommender System Use Cases Of Filtering Methods Portrait Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Primary Steps To Build Recommender System Use Cases Of Filtering Methods Portrait Pdf can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide talks about four steps to build a recommender system. The purpose of this slide is to explain the procedure of developing a recommendation engine. These steps include pre processing, learning, evaluation and prediction.
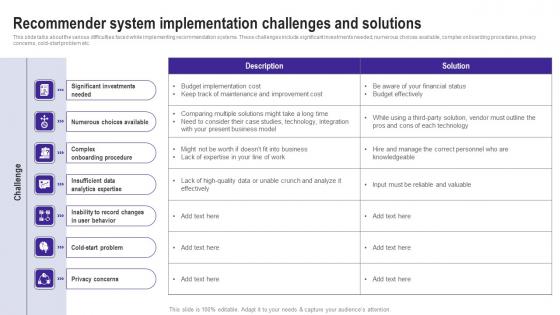
Recommender System Implementation Challenges Use Cases Of Filtering Methods Clipart Pdf
This slide talks about the various difficulties faced while implementing recommendation systems. These challenges include significant investments needed, numerous choices available, complex onboarding procedures, privacy concerns, cold start problem etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Recommender System Implementation Challenges Use Cases Of Filtering Methods Clipart Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide talks about the various difficulties faced while implementing recommendation systems. These challenges include significant investments needed, numerous choices available, complex onboarding procedures, privacy concerns, cold start problem etc.
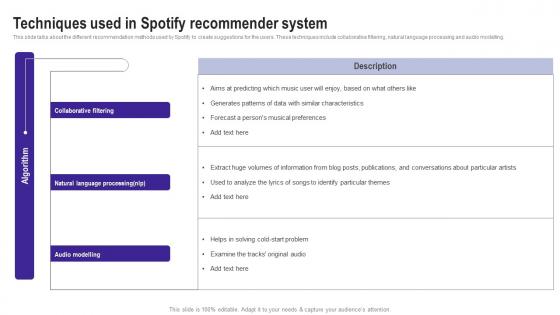
Techniques Used In Spotify Recommender System Use Cases Of Filtering Methods Designs Pdf
This slide talks about the different recommendation methods used by Spotify to create suggestions for the users. These techniques include collaborative filtering, natural language processing and audio modelling. Explore a selection of the finest Techniques Used In Spotify Recommender System Use Cases Of Filtering Methods Designs Pdf here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Techniques Used In Spotify Recommender System Use Cases Of Filtering Methods Designs Pdf to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide talks about the different recommendation methods used by Spotify to create suggestions for the users. These techniques include collaborative filtering, natural language processing and audio modelling.
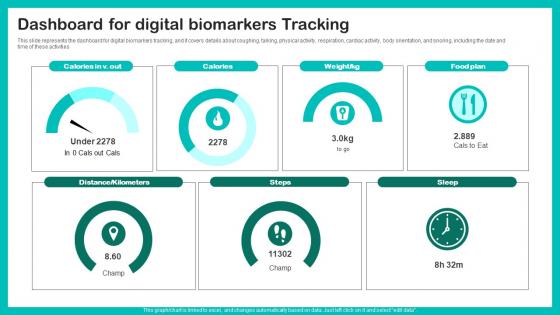
Digital Biomarkers For Personalized Health Insights Dashboard For Digital Biomarkers Template Pdf
This slide represents the dashboard for digital biomarkers tracking, and it covers details about coughing, talking, physical activity, respiration, cardiac activity, body orientation, and snoring, including the date and time of these activities Get a simple yet stunning designed Digital Biomarkers For Personalized Health Insights Dashboard For Digital Biomarkers Template Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Digital Biomarkers For Personalized Health Insights Dashboard For Digital Biomarkers Template Pdf can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide represents the dashboard for digital biomarkers tracking, and it covers details about coughing, talking, physical activity, respiration, cardiac activity, body orientation, and snoring, including the date and time of these activities
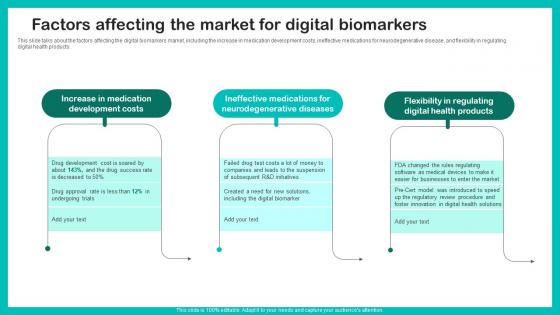
Factors Affecting The Market Digital Biomarkers For Personalized Health Insights Sample Pdf
This slide talks about the factors affecting the digital biomarkers market, including the increase in medication development costs, ineffective medications for neurodegenerative disease, and flexibility in regulating digital health products. Find highly impressive Factors Affecting The Market Digital Biomarkers For Personalized Health Insights Sample Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Factors Affecting The Market Digital Biomarkers For Personalized Health Insights Sample Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide talks about the factors affecting the digital biomarkers market, including the increase in medication development costs, ineffective medications for neurodegenerative disease, and flexibility in regulating digital health products.
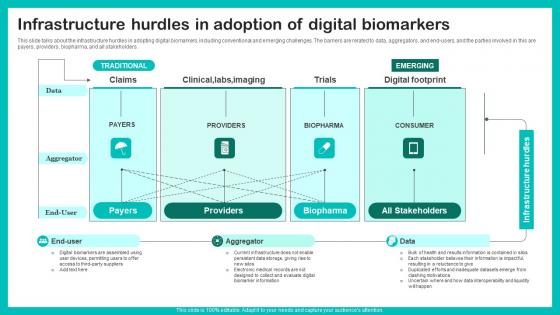
Infrastructure Hurdles Adoption Digital Biomarkers For Personalized Health Insights Designs Pdf
This slide talks about the infrastructure hurdles in adopting digital biomarkers, including conventional and emerging challenges. The barriers are related to data, aggregators, and end users, and the parties involved in this are payers, providers, biopharma, and all stakeholders. Make sure to capture your audiences attention in your business displays with our gratis customizable Infrastructure Hurdles Adoption Digital Biomarkers For Personalized Health Insights Designs Pdf. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide talks about the infrastructure hurdles in adopting digital biomarkers, including conventional and emerging challenges. The barriers are related to data, aggregators, and end users, and the parties involved in this are payers, providers, biopharma, and all stakeholders.
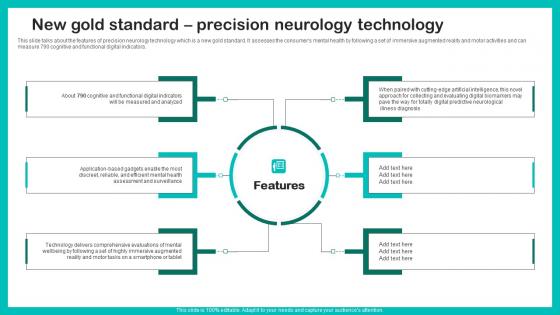
New Gold Standard Precision Digital Biomarkers For Personalized Health Insights Brochure Pdf
This slide talks about the features of precision neurology technology which is a new gold standard. It assesses the consumers mental health by following a set of immersive augmented reality and motor activities and can measure 790 cognitive and functional digital indicators. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download New Gold Standard Precision Digital Biomarkers For Personalized Health Insights Brochure Pdf from Slidegeeks and deliver a wonderful presentation. This slide talks about the features of precision neurology technology which is a new gold standard. It assesses the consumers mental health by following a set of immersive augmented reality and motor activities and can measure 790 cognitive and functional digital indicators.
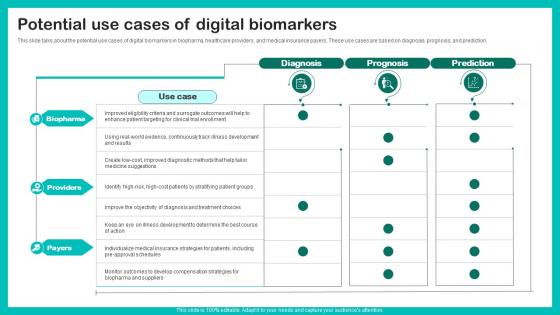
Potential Use Cases Digital Biomarkers For Personalized Health Insights Structure Pdf
This slide talks about the potential use cases of digital biomarkers in biopharma, healthcare providers, and medical insurance payers. These use cases are based on diagnosis, prognosis, and prediction. Retrieve professionally designed Potential Use Cases Digital Biomarkers For Personalized Health Insights Structure Pdf to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide talks about the potential use cases of digital biomarkers in biopharma, healthcare providers, and medical insurance payers. These use cases are based on diagnosis, prognosis, and prediction.
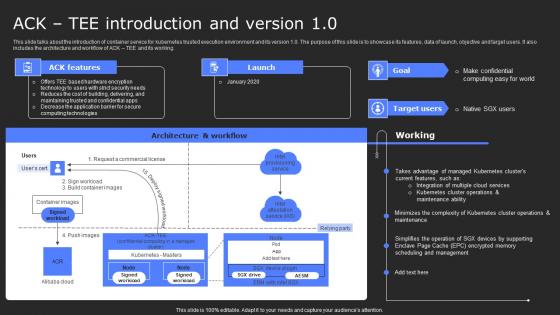
ACK Tee Introduction And Version 10 Secure Computing Framework Slides Pdf
This slide talks about the introduction of container service for kubernetes trusted execution environment and its version 1.0. The purpose of this slide is to showcase its features, data of launch, objective and target users. It also includes the architecture and workflow of ACK TEE and its working. Find a pre-designed and impeccable ACK Tee Introduction And Version 10 Secure Computing Framework Slides Pdf. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide talks about the introduction of container service for kubernetes trusted execution environment and its version 1.0. The purpose of this slide is to showcase its features, data of launch, objective and target users. It also includes the architecture and workflow of ACK TEE and its working.
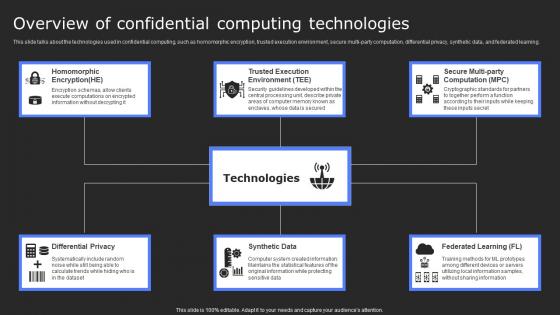
Overview Of Confidential Computing Technologies Secure Computing Framework Slides Pdf
This slide talks about the technologies used in confidential computing, such as homomorphic encryption, trusted execution environment, secure multi-party computation, differential privacy, synthetic data, and federated learning. Present like a pro with Overview Of Confidential Computing Technologies Secure Computing Framework Slides Pdf Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide talks about the technologies used in confidential computing, such as homomorphic encryption, trusted execution environment, secure multi-party computation, differential privacy, synthetic data, and federated learning.
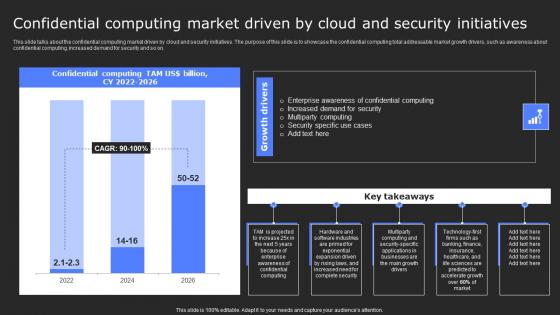
Secure Computing Framework Confidential Computing Market Driven By Mockup Pdf
This slide talks about the confidential computing market driven by cloud and security initiatives. The purpose of this slide is to showcase the confidential computing total addressable market growth drivers, such as awareness about confidential computing, increased demand for security and so on. Find a pre-designed and impeccable Secure Computing Framework Confidential Computing Market Driven By Mockup Pdf. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide talks about the confidential computing market driven by cloud and security initiatives. The purpose of this slide is to showcase the confidential computing total addressable market growth drivers, such as awareness about confidential computing, increased demand for security and so on.

About Cloud Computing Overview Cloud Data Security Using Cryptography Pictures Pdf
This slide talks about the meaning and operations of cloud computing. The purpose of this slide is to outline the services provided by cloud computing. These are Infrastructure as a Service IaaS, Platform as a Service PaaS, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. About Cloud Computing Overview Cloud Data Security Using Cryptography Pictures Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide talks about the meaning and operations of cloud computing. The purpose of this slide is to outline the services provided by cloud computing. These are Infrastructure as a Service IaaS, Platform as a Service PaaS, etc.

Cryptographic Algorithms Used In Cloud Data Security Using Cryptography Themes Pdf
This slide talks about algorithms used for implementing cryptography in data security. The purpose of this slide is to explain the different implementation steps. The techniques discussed are RSA Rivest, Shamir, Adleman cryptographic algorithm and Data Encryption Standard algorithm. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Cryptographic Algorithms Used In Cloud Data Security Using Cryptography Themes Pdf from Slidegeeks and deliver a wonderful presentation. This slide talks about algorithms used for implementing cryptography in data security. The purpose of this slide is to explain the different implementation steps. The techniques discussed are RSA Rivest, Shamir, Adleman cryptographic algorithm and Data Encryption Standard algorithm.
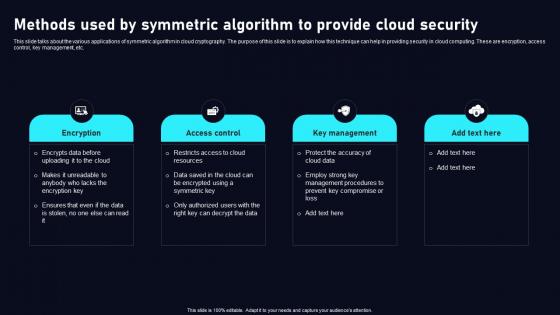
Methods Used By Symmetric Algorithm Cloud Data Security Using Cryptography Topics Pdf
This slide talks about the various applications of symmetric algorithm in cloud cryptography. The purpose of this slide is to explain how this technique can help in providing security in cloud computing. These are encryption, access control, key management, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Methods Used By Symmetric Algorithm Cloud Data Security Using Cryptography Topics Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide talks about the various applications of symmetric algorithm in cloud cryptography. The purpose of this slide is to explain how this technique can help in providing security in cloud computing. These are encryption, access control, key management, etc.
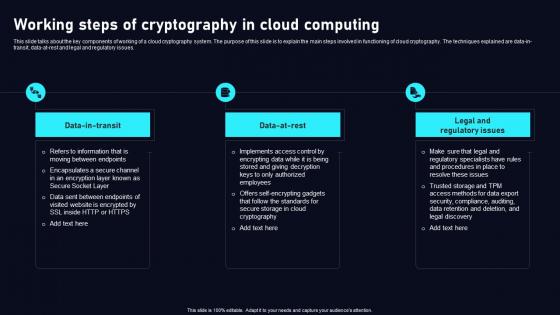
Working Steps Of Cryptography In Cloud Data Security Using Cryptography Infographics Pdf
This slide talks about the key components of working of a cloud cryptography system. The purpose of this slide is to explain the main steps involved in functioning of cloud cryptography. The techniques explained are data in transit, data at rest and legal and regulatory issues. There are so many reasons you need aWorking Steps Of Cryptography In Cloud Data Security Using Cryptography Infographics Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide talks about the key components of working of a cloud cryptography system. The purpose of this slide is to explain the main steps involved in functioning of cloud cryptography. The techniques explained are data in transit, data at rest and legal and regulatory issues.
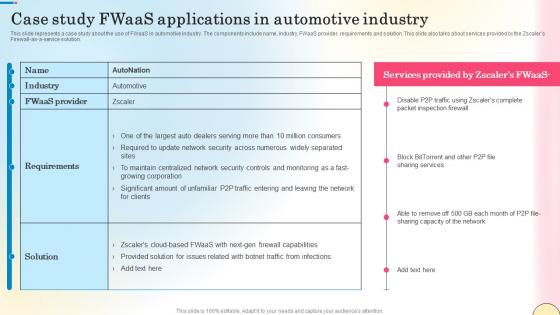
Case Study Fwaas Applications In Automotive Industry Network Security Clipart Pdf
This slide represents a case study about the use of FWaaS in automotive industry. The components include name, industry, FWaaS provider, requirements and solution. This slide also talks about services provided by the Zscalers Firewall-as-a-service solution. Present like a pro with Case Study Fwaas Applications In Automotive Industry Network Security Clipart Pdf Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide represents a case study about the use of FWaaS in automotive industry. The components include name, industry, FWaaS provider, requirements and solution. This slide also talks about services provided by the Zscalers Firewall-as-a-service solution.
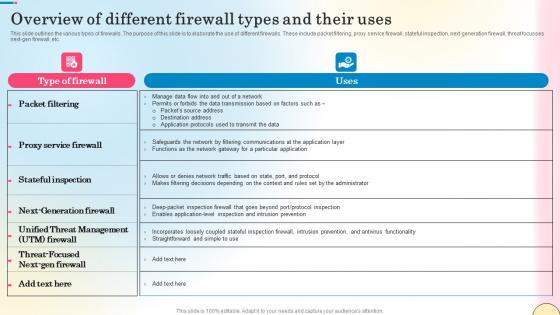
Overview Of Different Firewall Types And Their Uses Network Security Infographics Pdf
This slide talks about the role of Firewall-as-a-Service inside a secure access service edge framework. The purpose of this slide is to explain how FWaaS and SASE work together to provide network security. The components include SASE, Cloudflare Magic Firewall, etc. Find a pre-designed and impeccable Overview Of Different Firewall Types And Their Uses Network Security Infographics Pdf. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide talks about the role of Firewall-as-a-Service inside a secure access service edge framework. The purpose of this slide is to explain how FWaaS and SASE work together to provide network security. The components include SASE, Cloudflare Magic Firewall, etc.
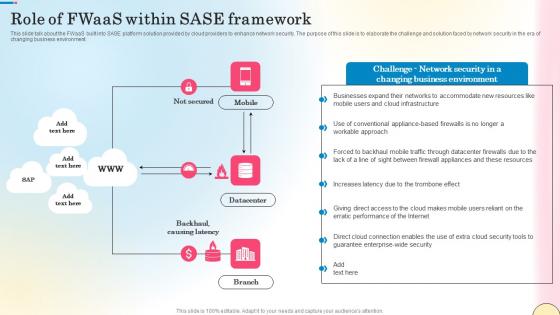
Role Of Fwaas Within Sase Framework Network Security Elements Pdf
This slide talk about the FWaaS built into SASE platform solution provided by cloud providers to enhance network security. The purpose of this slide is to elaborate the challenge and solution faced by network security in the era of changing business environment. Want to ace your presentation in front of a live audience Our Role Of Fwaas Within Sase Framework Network Security Elements Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide talk about the FWaaS built into SASE platform solution provided by cloud providers to enhance network security. The purpose of this slide is to elaborate the challenge and solution faced by network security in the era of changing business environment.
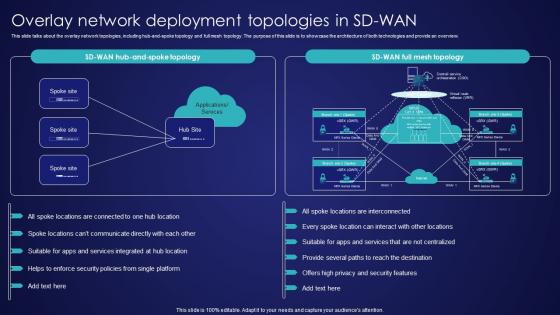
Overlay Network Deployment Topologies In SD Wan Wide Area Network Services Inspiration Pdf
This slide talks about the overlay network topologies, including hub-and-spoke topology and full mesh topology. The purpose of this slide is to showcase the architecture of both technologies and provide an overview. Make sure to capture your audiences attention in your business displays with our gratis customizable Overlay Network Deployment Topologies In SD Wan Wide Area Network Services Inspiration Pdf. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide talks about the overlay network topologies, including hub-and-spoke topology and full mesh topology. The purpose of this slide is to showcase the architecture of both technologies and provide an overview.
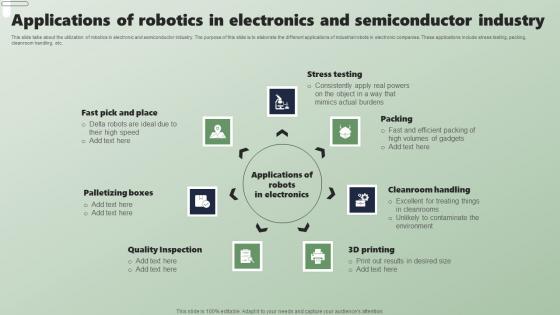
Applications Of Robotics In Electronics And Applications Of Industrial Robots Rules Pdf
This slide talks about the utilization of robotics in electronic and semiconductor industry. The purpose of this slide is to elaborate the different applications of industrial robots in electronic companies. These applications include stress testing, packing, cleanroom handling, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Applications Of Robotics In Electronics And Applications Of Industrial Robots Rules Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide talks about the utilization of robotics in electronic and semiconductor industry. The purpose of this slide is to elaborate the different applications of industrial robots in electronic companies. These applications include stress testing, packing, cleanroom handling, etc.

Important Touchpoints Of Customer Experience Journey Template Pdf
This slide talks about the different touchpoints of the customer experience journey. It includes the various stages such as awareness, consideration, purchase, after-sales or services and loyalty or expansion. The touch points are based on digital, physical, before, during and after purchase. Showcasing this set of slides titled Important Touchpoints Of Customer Experience Journey Template Pdf. The topics addressed in these templates are Awareness, Consideration, Purchase. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide talks about the different touchpoints of the customer experience journey. It includes the various stages such as awareness, consideration, purchase, after-sales or services and loyalty or expansion. The touch points are based on digital, physical, before, during and after purchase.
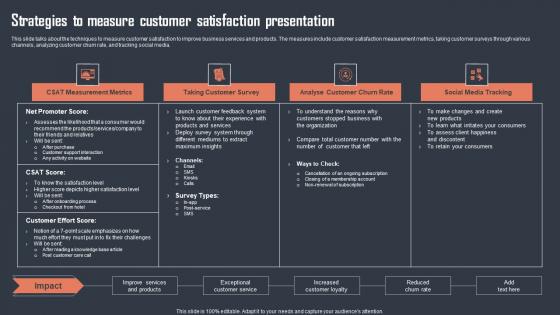
Strategies To Measure Customer Satisfaction Presentation Sample Pdf
This slide talks about the techniques to measure customer satisfaction to improve business services and products. The measures include customer satisfaction measurement metrics, taking customer surveys through various channels, analyzing customer churn rate, and tracking social media. Showcasing this set of slides titled Strategies To Measure Customer Satisfaction Presentation Sample Pdf. The topics addressed in these templates are Measurement Metrics, Taking Customer Survey. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide talks about the techniques to measure customer satisfaction to improve business services and products. The measures include customer satisfaction measurement metrics, taking customer surveys through various channels, analyzing customer churn rate, and tracking social media.

Features Of Next Generation Secure Web Gateway Web Threat Protection System
This slide talks about the various characteristics of next generation SGVs. These are cloud based architecture, AI and machine learning, zero-trust security, integrated data loss prevention, more visibility and control, advanced threat intelligence, etc. Find highly impressive Features Of Next Generation Secure Web Gateway Web Threat Protection System on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Features Of Next Generation Secure Web Gateway Web Threat Protection System for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide talks about the various characteristics of next generation SGVs. These are cloud based architecture, AI and machine learning, zero-trust security, integrated data loss prevention, more visibility and control, advanced threat intelligence, etc.

Importance Of Secure Web Gateway For Businesses Web Threat Protection System
This slide talks about the role of Secure Web Gateway in organizations. The purpose of this slide is to explain why companies require SWG. The components covered are ID provider, data center, client connector, global policy engine, real-time analytics, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Importance Of Secure Web Gateway For Businesses Web Threat Protection System. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide talks about the role of Secure Web Gateway in organizations. The purpose of this slide is to explain why companies require SWG. The components covered are ID provider, data center, client connector, global policy engine, real-time analytics, etc.

Secure Web Gateway Implementation Methodology Explicit Web Threat Protection System
This slide talks about the inline scenario of Secure Web Gateway implementation. The purpose of this slide is to demonstrate the concept of inline SWG deployment technique with the help of a diagram. This slide also outlines the benefits of this method. Find a pre-designed and impeccable Secure Web Gateway Implementation Methodology Explicit Web Threat Protection System. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide talks about the inline scenario of Secure Web Gateway implementation. The purpose of this slide is to demonstrate the concept of inline SWG deployment technique with the help of a diagram. This slide also outlines the benefits of this method.

About Identity Theft Overview And Techniques Man In The Middle Phishing IT
This slide talks about the major crime committed by phishers named as identity theft. The purpose of this slide is to outline the ways of stealing information such as robbery, computer fraud, social networking sites, mail theft and dumpster diving. Want to ace your presentation in front of a live audience Our About Identity Theft Overview And Techniques Man In The Middle Phishing IT can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide talks about the major crime committed by phishers named as identity theft. The purpose of this slide is to outline the ways of stealing information such as robbery, computer fraud, social networking sites, mail theft and dumpster diving.
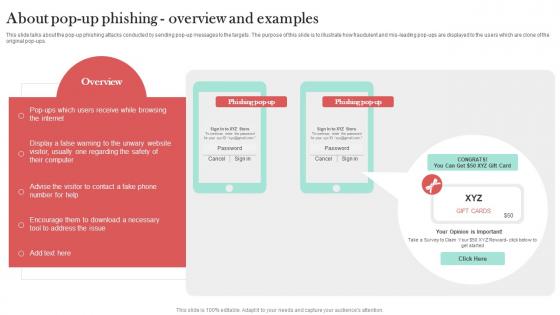
About Pop Up Phishing Overview And Examples Man In The Middle Phishing IT
This slide talks about the pop-up phishing attacks conducted by sending pop-up messages to the targets. The purpose of this slide is to illustrate how fraudulent and mis-leading pop-ups are displayed to the users which are clone of the original pop-ups. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. About Pop Up Phishing Overview And Examples Man In The Middle Phishing IT will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide talks about the pop-up phishing attacks conducted by sending pop-up messages to the targets. The purpose of this slide is to illustrate how fraudulent and mis-leading pop-ups are displayed to the users which are clone of the original pop-ups.

Clone Phishing Attacks Preventive Measures Man In The Middle Phishing IT
This slide talks about the various steps that can be taken to prevent clone phishing attacks. These include review senders address, preview links before opening them, use a password manager, investigate spoofed replies, double check URL addresses, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Clone Phishing Attacks Preventive Measures Man In The Middle Phishing IT. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide talks about the various steps that can be taken to prevent clone phishing attacks. These include review senders address, preview links before opening them, use a password manager, investigate spoofed replies, double check URL addresses, etc.
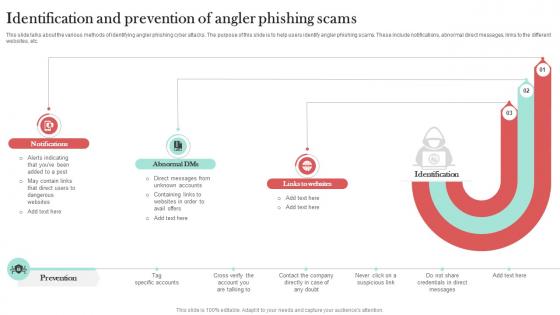
Identification And Prevention Of Angler Man In The Middle Phishing IT
This slide talks about the various methods of identifying angler phishing cyber attacks. The purpose of this slide is to help users identify angler phishing scams. These include notifications, abnormal direct messages, links to the different websites, etc. Slidegeeks has constructed Identification And Prevention Of Angler Man In The Middle Phishing IT after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide talks about the various methods of identifying angler phishing cyber attacks. The purpose of this slide is to help users identify angler phishing scams. These include notifications, abnormal direct messages, links to the different websites, etc.

Vishing Attacks Prevention Email Signing Man In The Middle Phishing IT
This slide talks about the techniques which can help in protecting organizations from phishing and vishing attacks. The purpose of this slide is to explain two important methods of preventing cyber scams. These techniques are email signing and code signing. The Vishing Attacks Prevention Email Signing Man In The Middle Phishing IT is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide talks about the techniques which can help in protecting organizations from phishing and vishing attacks. The purpose of this slide is to explain two important methods of preventing cyber scams. These techniques are email signing and code signing.
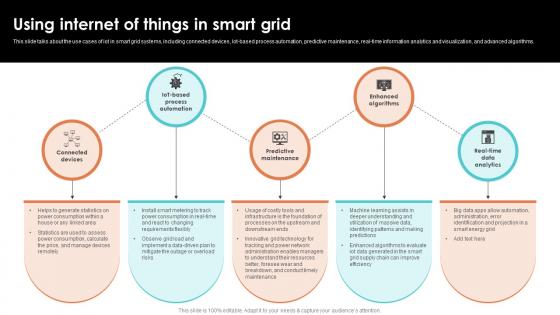
Using Internet Of Things In Smart Grid Smart Grid Working
This slide talks about the use cases of iot in smart grid systems, including connected devices, Iot based process automation, predictive maintenance, real time information analytics and visualization, and advanced algorithms. Find a pre designed and impeccable Using Internet Of Things In Smart Grid Smart Grid Working The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide talks about the use cases of iot in smart grid systems, including connected devices, Iot based process automation, predictive maintenance, real time information analytics and visualization, and advanced algorithms.

Zero Trust Network Access Role Of ZTNA To Improve Business Operations And Security
This slide talks about the ways in which ZTNA improves the business operations and security. The purpose of this slide is to showcase the various domains that zero trust network access improves, including increased user experience, remote workforce protection, improve data protection, and network visibility. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Zero Trust Network Access Role Of ZTNA To Improve Business Operations And Security will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide talks about the ways in which ZTNA improves the business operations and security. The purpose of this slide is to showcase the various domains that zero trust network access improves, including increased user experience, remote workforce protection, improve data protection, and network visibility.

CASB 2 0 IT Cloud Access Security Broker Pillar Data Security
This slide talks about the data security pillar of the cloud access security broker pillar. This slide highlights how CASB data security can help organizations improve their IT requirements and business operations and detect security breaches before they happen. The CASB 2 0 IT Cloud Access Security Broker Pillar Data Security is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide talks about the data security pillar of the cloud access security broker pillar. This slide highlights how CASB data security can help organizations improve their IT requirements and business operations and detect security breaches before they happen.

Web Access Control Solution Applications Of Secure Web Gateway In Various Industries
This slide talks about how Secure Web Gateway is used in several industrial domains. The purpose of this slide is to explain how SWG is used in different sectors. The industries covered are financial services, healthcare, education, manufacturing, etc. Present like a pro with Web Access Control Solution Applications Of Secure Web Gateway In Various Industries. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide talks about how Secure Web Gateway is used in several industrial domains. The purpose of this slide is to explain how SWG is used in different sectors. The industries covered are financial services, healthcare, education, manufacturing, etc.
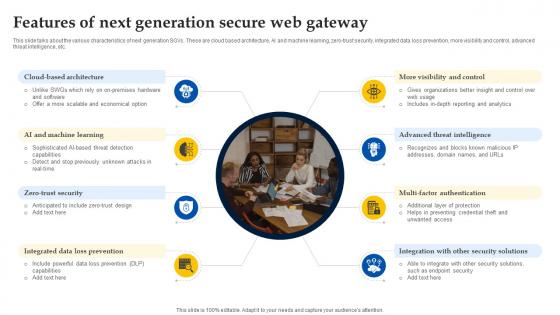
Web Access Control Solution Features Of Next Generation Secure Web Gateway
This slide talks about the various characteristics of next generation SGVs. These are cloud based architecture, AI and machine learning, zero-trust security, integrated data loss prevention, more visibility and control, advanced threat intelligence, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Web Access Control Solution Features Of Next Generation Secure Web Gateway to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide talks about the various characteristics of next generation SGVs. These are cloud based architecture, AI and machine learning, zero-trust security, integrated data loss prevention, more visibility and control, advanced threat intelligence, etc.
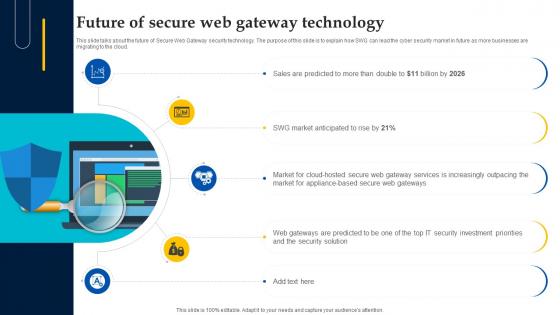
Web Access Control Solution Future Of Secure Web Gateway Technology
This slide talks about the future of Secure Web Gateway security technology. The purpose of this slide is to explain how SWG can lead the cyber security market in future as more businesses are migrating to the cloud. This modern and well-arranged Web Access Control Solution Future Of Secure Web Gateway Technology provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide talks about the future of Secure Web Gateway security technology. The purpose of this slide is to explain how SWG can lead the cyber security market in future as more businesses are migrating to the cloud.

About Development And Operations Devops Introduction To MLOPs IT
This slide talks about development and operations. The purpose of this slide is to introduce the concept of development and operations devops and its importance in modern software development practices. Find a pre-designed and impeccable About Development And Operations Devops Introduction To MLOPs IT. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide talks about development and operations. The purpose of this slide is to introduce the concept of development and operations devops and its importance in modern software development practices.

Continuous Integration And Continuous Deployment CI CD For ML Introduction To MLOPs IT
This slide talks about adoption of Continuous Integration and Continuous Deployment CICD in the context of Machine Learning ML. CICD is a set of practices and tools that DevOps teams utilize to automate and streamline the software development process. Make sure to capture your audiences attention in your business displays with our gratis customizable Continuous Integration And Continuous Deployment CI CD For ML Introduction To MLOPs IT. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide talks about adoption of Continuous Integration and Continuous Deployment CICD in the context of Machine Learning ML. CICD is a set of practices and tools that DevOps teams utilize to automate and streamline the software development process.

About Identity Theft Overview And Techniques Data Fortification Strengthening Defenses
This slide talks about the major crime committed by phishers, named as identity theft. The purpose of this slide is to outline the ways of stealing information, such as robbery, computer fraud, social networking sites, mail theft, and dumpster diving.Create an editable About Identity Theft Overview And Techniques Data Fortification Strengthening Defenses that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. About Identity Theft Overview And Techniques Data Fortification Strengthening Defenses is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide talks about the major crime committed by phishers, named as identity theft. The purpose of this slide is to outline the ways of stealing information, such as robbery, computer fraud, social networking sites, mail theft, and dumpster diving.

About Cloud Cryptography Overview And Features Data Security In Cloud Computing Ppt Powerpoint
This slide talks about the cloud cryptography which helps in securing information travelling through cloud network. The purpose of this slide is to briefly explain the concept of cloud cryptography. This slide also outlines the features of this technology. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate About Cloud Cryptography Overview And Features Data Security In Cloud Computing Ppt Powerpoint for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide talks about the cloud cryptography which helps in securing information travelling through cloud network. The purpose of this slide is to briefly explain the concept of cloud cryptography. This slide also outlines the features of this technology.

About Cryptography Overview And Key Data Security In Cloud Computing Ppt Example
This slide talks about the concept of cryptography to secure the information sent to the recipient. The purpose of this slide is to represent the various principles of cryptography such as confidentiality, integrity, authentication, etc. Want to ace your presentation in front of a live audience Our About Cryptography Overview And Key Data Security In Cloud Computing Ppt Example can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide talks about the concept of cryptography to secure the information sent to the recipient. The purpose of this slide is to represent the various principles of cryptography such as confidentiality, integrity, authentication, etc.

Elliptic Curve Cryptography ECC Data Security In Cloud Computing Ppt Template
This slide talks about the Elliptic Curve Cryptography algorithm. The purpose of this slide is to elaborate the different applications of ECC algorithm. The uses of this algorithm are key agreement, mobile devices, cryptocurrency, etc. Welcome to our selection of the Elliptic Curve Cryptography ECC Data Security In Cloud Computing Ppt Template. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide talks about the Elliptic Curve Cryptography algorithm. The purpose of this slide is to elaborate the different applications of ECC algorithm. The uses of this algorithm are key agreement, mobile devices, cryptocurrency, etc.
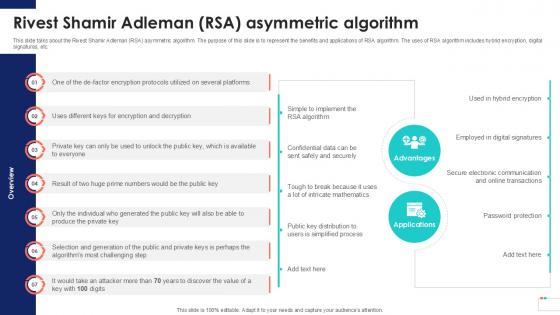
Rivest Shamir Adleman RSA Asymmetric Data Security In Cloud Computing Ppt Example
This slide talks about the Rivest Shamir Adleman RSA asymmetric algorithm. The purpose of this slide is to represent the benefits and applications of RSA algorithm. The uses of RSA algorithm includes hybrid encryption, digital signatures, etc. Want to ace your presentation in front of a live audience Our Rivest Shamir Adleman RSA Asymmetric Data Security In Cloud Computing Ppt Example can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide talks about the Rivest Shamir Adleman RSA asymmetric algorithm. The purpose of this slide is to represent the benefits and applications of RSA algorithm. The uses of RSA algorithm includes hybrid encryption, digital signatures, etc.
Organizational Manager Developing Long Term Sustainability Plans Icon Ppt Slide SS
The following slide showcases major steps to build corporate sustainability strategy. It provides information about talk, engage, assess, prioritize, commit, collaborate, measure, report, educate, etc. Slidegeeks has constructed Organizational Manager Developing Long Term Sustainability Plans Icon Ppt Slide SS after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. The following slide showcases major steps to build corporate sustainability strategy. It provides information about talk, engage, assess, prioritize, commit, collaborate, measure, report, educate, etc.
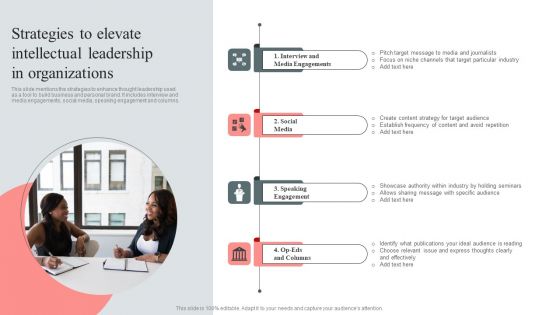
Strategies To Elevate Intellectual Leadership In Organizations Portrait PDF
This slide mentions the strategies to enhance thought leadership used as a tool to build business and personal brand. It includes interview and media engagements, social media, speaking engagement and columns. Presenting Strategies To Elevate Intellectual Leadership In Organizations Portrait PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Media Engagements, Speaking Engagement, Particular Industry. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Catch The Ladder Of Brain PowerPoint Templates Ppt Backgrounds For Slides 0513
OurCatch The Ladder Of Brain PowerPoint Templates PPT Backgrounds For Slides make good beasts of burden. Place all your demands on them. Deliver the right dose with our people PowerPoint Templates. Your ideas will get the correct illumination. Your abilities have been lying dormant. Awaken them with our business PowerPoint Templates. Escape from the humdrum with our Catch The Ladder Of Brain PowerPoint Templates Ppt Backgrounds For Slides 0513. Put in the element of excitement in your talk.

White Rose Is Symbol Of Peace PowerPoint Templates Ppt Backgrounds For Slides 0613
Your Message Paves The Way To Success. Let Our Nature Powerpoint Templates Be The Rungs Of Your Ladder. Breathe Life Into Your Talk With Our Environment Powerpoint Templates. They Will Add To The Reality Of Your Message. Give it your all with our White Rose Is Symbol Of Peace PowerPoint Templates Ppt Backgrounds For Slides 0613. They will back you every inch of the way.
Take A Pledge For Business Success PowerPoint Templates Ppt Backgrounds For Slides 0613
Our Take A Pledge For Business Success PowerPoint Templates PPT Backgrounds For Slides are a wonder drug. They help cure almost any malaise. Drum up support with our teamwork PowerPoint Templates. They will come in droves to stand by you. Drum it up with our business PowerPoint Templates. Your thoughts will raise the tempo. Escape from the humdrum with our Take A Pledge For Business Success PowerPoint Templates Ppt Backgrounds For Slides 0613. Put in the element of excitement in your talk.

Fix The Problem Of Business PowerPoint Templates Ppt Backgrounds For Slides 0613
Touch base with our Fix The Problem Of Business PowerPoint Templates PPT Backgrounds For Slides. Review your growth with your audience. Take a deep dive with our Communication PowerPoint Templates. Get into the nitty-gritty of it all. Plan your storyboard with our People PowerPoint Templates. Give an outline to the solutions you have. Escape from the humdrum with our Fix The Problem Of Business PowerPoint Templates Ppt Backgrounds For Slides 0613. Put in the element of excitement in your talk.
Four Steps Of Problem Solving Process Ppt Summary Icons PDF
Presenting this set of slides with name four steps of problem solving process ppt summary icons pdf. This is a four stage process. The stages in this process are get clarity on the conflict, talk to the other person, work towards a solution, listen to the other side. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
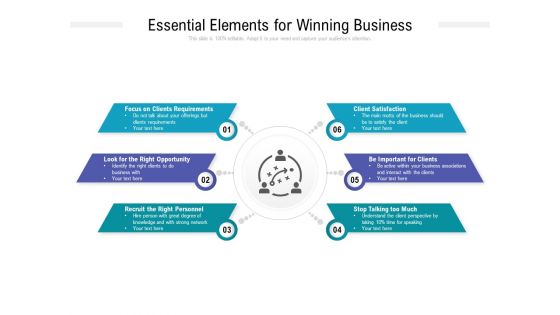
Essential Elements For Winning Business Ppt PowerPoint Presentation Summary Templates PDF
Presenting this set of slides with name essential elements for winning business ppt powerpoint presentation summary templates pdf. This is a six stage process. The stages in this process are focus on clients requirements, look for the right opportunity, recruit the right personnel, client satisfaction, be important for clients, stop talking too much. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Key Strategies To Successful Business Development Ppt PowerPoint Presentation Icon Examples PDF
Presenting this set of slides with name key strategies to successful business development ppt powerpoint presentation icon examples pdf. This is a six stage process. The stages in this process are focus on clients requirements, look for the right opportunity, recruit the right personnel, client satisfaction, be important for clients, stop talking too much. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
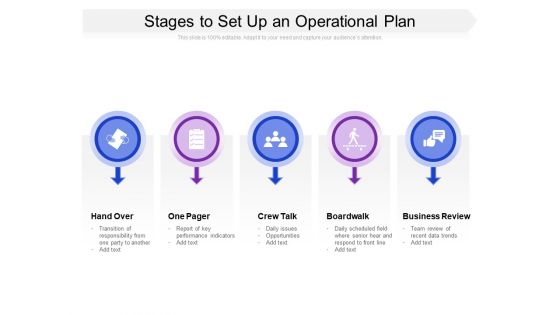
Stages To Set Up An Operational Plan Ppt PowerPoint Presentation Professional Template PDF
Presenting this set of slides with name stages to set up an operational plan ppt powerpoint presentation professional template pdf. This is a five stage process. The stages in this process are hand over, one pager, crew talk, boardwalk, business review, report of key performance indicators, daily issues, opportunities, daily scheduled field where senior hear and respond, team review of recent data trends. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Leaky Bucket Approach For Job Problems And Financial Issues Ppt PowerPoint Presentation Infographic Template Aids PDF
Presenting this set of slides with name leaky bucket approach for job problems and financial issues ppt powerpoint presentation infographic template aids pdf. The topics discussed in these slides are family relationship stress, job problems, normal, rest and relaxation, talking to trusted people, doing something you enjoy, good time management, relaxed, financial issues, dealing with changes, lack of sleep, poor diet. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
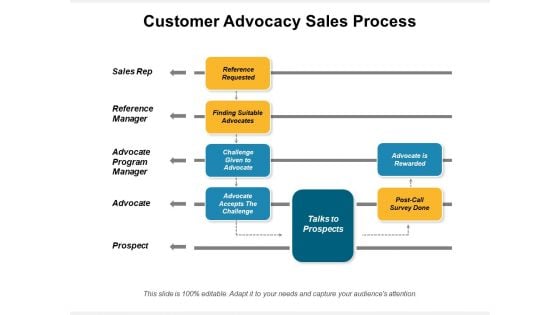
Customer Advocacy Sales Process Ppt PowerPoint Presentation File Images PDF
Presenting this set of slides with name customer advocacy sales process ppt powerpoint presentation file images pdf. The topics discussed in these slides are sales rep, reference manager, advocate program manager, advocate, prospect, reference requested, finding suitable advocates, challenge given to advocate, advocate accepts the challenge, talks to prospects, advocate is rewarded. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Terms Of Social Media Engagement With Icons Ppt PowerPoint Presentation Professional Graphics PDF
Presenting terms of social media engagement with icons ppt powerpoint presentation professional graphics pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including community catalyzing in terms of meaningful interactions, be unique in offering, listening to audience, dont involve in formal talk. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.


 Continue with Email
Continue with Email

 Home
Home


































