Strategic Goals
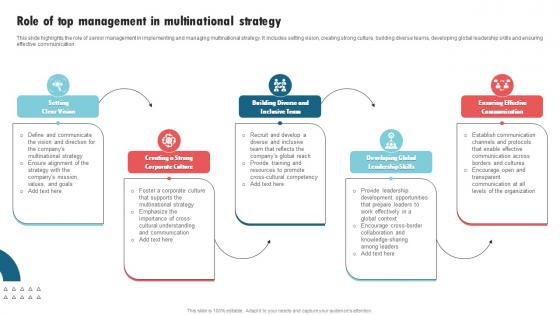
Role Of Top Management In Multinational Strategy International Strategy Corporations Summary Pdf
This slide highlights the role of senior management in implementing and managing multinational strategy. It includes setting vision, creating strong culture, building diverse teams, developing global leadership skills and ensuring effective communication. Create an editable Role Of Top Management In Multinational Strategy International Strategy Corporations Summary Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Role Of Top Management In Multinational Strategy International Strategy Corporations Summary Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide highlights the role of senior management in implementing and managing multinational strategy. It includes setting vision, creating strong culture, building diverse teams, developing global leadership skills and ensuring effective communication.

Overview Of Companys Official Twitter Account Twitter Promotional Techniques Summary Pdf
This slide provides snapshot of companys official twitter account. It also provides details regarding upgradations required to make it more efficient such as change in profile picture, company website link etc. If you are looking for a format to display your unique thoughts, then the professionally designed Overview Of Companys Official Twitter Account Twitter Promotional Techniques Summary Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Overview Of Companys Official Twitter Account Twitter Promotional Techniques Summary Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide provides snapshot of companys official twitter account. It also provides details regarding upgradations required to make it more efficient such as change in profile picture, company website link etc.
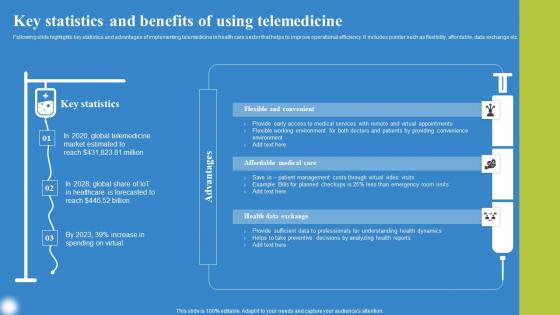
Key Statistics And Benefits Using Deploying IoT Solutions For Enhanced Healthcare Demonstration Pdf
Following slide highlights key statistics and advantages of implementing telemedicine in health care sector that helps to improve operational efficiency. It includes pointer such as flexibility, affordable, data exchange etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Key Statistics And Benefits Using Deploying IoT Solutions For Enhanced Healthcare Demonstration Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Key Statistics And Benefits Using Deploying IoT Solutions For Enhanced Healthcare Demonstration Pdf today and make your presentation stand out from the rest Following slide highlights key statistics and advantages of implementing telemedicine in health care sector that helps to improve operational efficiency. It includes pointer such as flexibility, affordable, data exchange etc.

Customer Referral Giveaways For Generating New Sales Techniques For Achieving Designs Pdf
This slide covers client referral contest strategy to sales. It also includes campaign details such as overview, benefits, suitability, guidelines, program success metrics, etc. Present like a pro with Customer Referral Giveaways For Generating New Sales Techniques For Achieving Designs Pdf Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide covers client referral contest strategy to sales. It also includes campaign details such as overview, benefits, suitability, guidelines, program success metrics, etc.

Agenda Overview Of Customer Adoption Process Formats Pdf
Find a pre designed and impeccable Agenda Overview Of Customer Adoption Process Formats Pdf. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. Our Agenda Overview Of Customer Adoption Process Formats Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Efficient Shopper Marketing Process For Enhancing Table Of Contents Introduction Pdf
Present like a pro with Efficient Shopper Marketing Process For Enhancing Table Of Contents Introduction Pdf Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. Our Efficient Shopper Marketing Process For Enhancing Table Of Contents Introduction Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
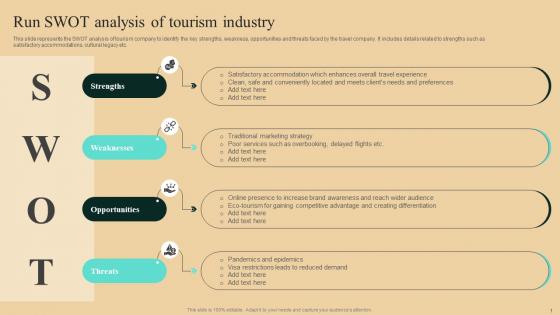
Guide To Winning Tourism Run Swot Analysis Of Tourism Industry Template Pdf
This slide represents the SWOT analysis of tourism company to identify the key strengths, weakness, opportunities and threats faced by the travel company. It includes details related to strengths such as satisfactory accommodations, cultural legacy etc. If you are looking for a format to display your unique thoughts, then the professionally designed Guide To Winning Tourism Run Swot Analysis Of Tourism Industry Template Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Guide To Winning Tourism Run Swot Analysis Of Tourism Industry Template Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide represents the SWOT analysis of tourism company to identify the key strengths, weakness, opportunities and threats faced by the travel company. It includes details related to strengths such as satisfactory accommodations, cultural legacy etc.

Agenda Guide To Winning Tourism Marketing Strategies For Customer Attraction Summary Pdf
Find a pre-designed and impeccable Agenda Guide To Winning Tourism Marketing Strategies For Customer Attraction Summary Pdf The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. Our Agenda Guide To Winning Tourism Marketing Strategies For Customer Attraction Summary Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Activities To Explore The Potential Digital Approaches To Increase Business Growth Template Pdf
Purpose of this slide is to showcase different activities that can be performed by managers to identify the potential of their digital strategy. It also includes details about the benefits that organization will experience after performing these activities. Explore a selection of the finest Activities To Explore The Potential Digital Approaches To Increase Business Growth Template Pdf here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Activities To Explore The Potential Digital Approaches To Increase Business Growth Template Pdf to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. Purpose of this slide is to showcase different activities that can be performed by managers to identify the potential of their digital strategy. It also includes details about the benefits that organization will experience after performing these activities.

Steps To Structure An Effective Digital Approaches To Increase Business Growth Infographics Pdf
This slide provides information on the steps that can be followed by managers for effectively drafting a digital strategy. Steps covered are focusing on situational analysis, target market identification, content strategy development etc. The Steps To Structure An Effective Digital Approaches To Increase Business Growth Infographics Pdf is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide provides information on the steps that can be followed by managers for effectively drafting a digital strategy. Steps covered are focusing on situational analysis, target market identification, content strategy development etc.
Agenda Guide For Segmenting And Formulating Target Market Profile Icons Pdf
Find a pre designed and impeccable Agenda Guide For Segmenting And Formulating Target Market Profile Icons Pdf. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. Our Agenda Guide For Segmenting And Formulating Target Market Profile Icons Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
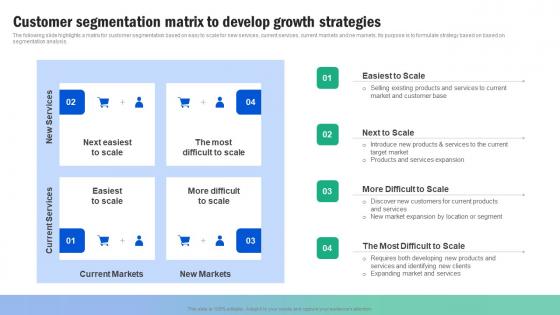
Customer Segmentation Matrix To Develop Growth Guide For Segmenting And Formulating Elements Pdf
The following slide highlights a matrix for customer segmentation based on easy to scale for new services, current services, current markets and ne markets. Its purpose is to formulate strategy based on based on segmentation analysis. Present like a pro with Customer Segmentation Matrix To Develop Growth Guide For Segmenting And Formulating Elements Pdf Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. The following slide highlights a matrix for customer segmentation based on easy to scale for new services, current services, current markets and ne markets. Its purpose is to formulate strategy based on based on segmentation analysis.

Guide For Segmenting And Formulating Target Market Profile Table Of Contents Pictures Pdf
Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Guide For Segmenting And Formulating Target Market Profile Table Of Contents Pictures Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. Our Guide For Segmenting And Formulating Target Market Profile Table Of Contents Pictures Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
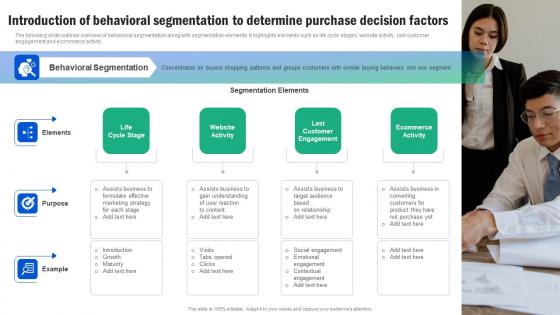
Introduction Of Behavioral Segmentation To Determine Guide For Segmenting And Formulating Brochure Pdf
The following slide outlines overview of behavioral segmentation along with segmentation elements. It highlights elements such as life cycle stages, website activity, last customer engagement and ecommerce activity. Make sure to capture your audiences attention in your business displays with our gratis customizable Introduction Of Behavioral Segmentation To Determine Guide For Segmenting And Formulating Brochure Pdf. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. The following slide outlines overview of behavioral segmentation along with segmentation elements. It highlights elements such as life cycle stages, website activity, last customer engagement and ecommerce activity.

Market Potential Automotive Designing Company Investor Funding Pitch Deck Pictures Pdf
This slide represents the data that signifies the total addressable market, serviceable available market, and serviceable obtainable market. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. DownloadMarket Potential Automotive Designing Company Investor Funding Pitch Deck Pictures Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide represents the data that signifies the total addressable market, serviceable available market, and serviceable obtainable market.
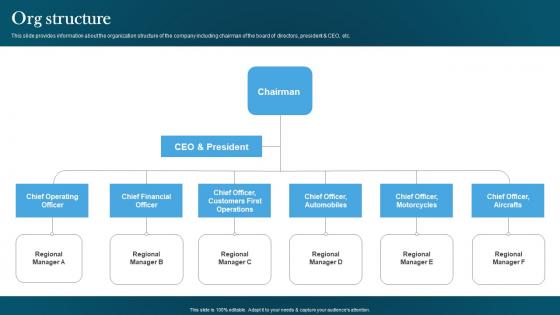
Org Structure Automotive Designing Company Investor Funding Pitch Deck Portrait Pdf
This slide provides information about the organization structure of the company including chairman of the board of directors, president and CEO, etc.Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforwardOrg Structure Automotive Designing Company Investor Funding Pitch Deck Portrait Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Org Structure Automotive Designing Company Investor Funding Pitch Deck Portrait Pdf that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide provides information about the organization structure of the company including chairman of the board of directors, president and CEO, etc.

Table Of Contents For In Depth Analysis Of Islamic Banking Financial Sector Formats PDF
Take your projects to the next level with our ultimate collection of Table Of Contents For In Depth Analysis Of Islamic Banking Financial Sector Formats PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they well make your projects stand out from the rest. Our Table Of Contents For In Depth Analysis Of Islamic Banking Financial Sector Formats PDF are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
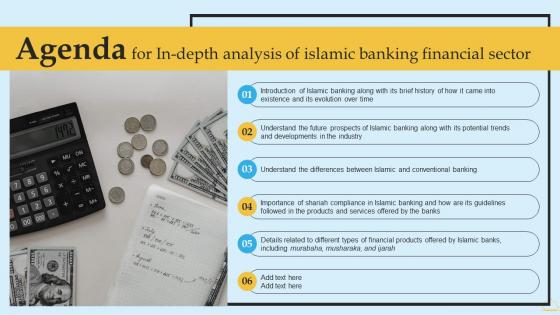
Agenda For In Depth Analysis Of Islamic Banking Financial Sector Themes PDF
Find a pre-designed and impeccable Agenda For In Depth Analysis Of Islamic Banking Financial Sector Themes PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide caters to the details related to the distribution of funds raised to maximize the companys potential. Key areas include research and development, marketing and sales, customer support, etc.

In Depth Analysis Of Islamic Banking Financial Sector Table Of Contents Themes PDF
Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our In Depth Analysis Of Islamic Banking Financial Sector Table Of Contents Themes PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into In Depth Analysis Of Islamic Banking Financial Sector Table Of Contents Themes PDF Our In Depth Analysis Of Islamic Banking Financial Sector Table Of Contents Themes PDF are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
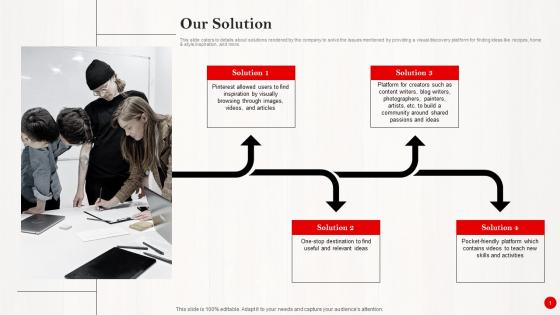
Our Solution Investor Funding Pitch Deck For Pinterests Expansion Microsoft Pdf
This slide caters to details about solutions rendered by the company to solve the issues mentioned by providing a visual discovery platform for finding ideas like recipes, home and style inspiration, and more. Make sure to capture your audiences attention in your business displays with our gratis customizable Our Solution Investor Funding Pitch Deck For Pinterests Expansion Microsoft Pdf. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide caters to details about solutions rendered by the company to solve the issues mentioned by providing a visual discovery platform for finding ideas like recipes, home and style inspiration, and more.
Agenda For Strategies To Build Meaningful Team Relationships Within Organizations Professional PDF
Find a pre-designed and impeccable Agenda For Strategies To Build Meaningful Team Relationships Within Organizations Professional PDF The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. Our Agenda For Strategies To Build Meaningful Team Relationships Within Organizations Professional PDF are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Strategies To Build Meaningful Introduction For Employee Training And Development In Firms Download PDF
The slide showcases overview of employee training and development initiated in organizations for betterment of employee upskilling and organizations growth . It contains elements such as overview of employee training and development and impact initiated on employees and organization. This modern and well-arranged Strategies To Build Meaningful Introduction For Employee Training And Development In Firms Download PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. The slide showcases overview of employee training and development initiated in organizations for betterment of employee upskilling and organizations growth . It contains elements such as overview of employee training and development and impact initiated on employees and organization.
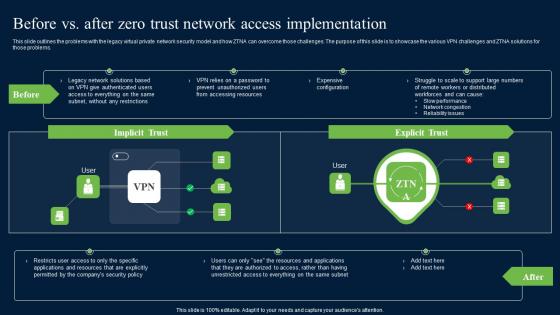
Before Vs After Zero Trust Network Access Brochure Pdf
This slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems. Create an editable Before Vs After Zero Trust Network Access Brochure Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Before Vs After Zero Trust Network Access Brochure Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems.

Case Study Intellectual Property Protection With Zero Trust Network Security Inspiration Pdf
This slide represents the case study for implementing the ZTNA security model into a food and beverage organization to secure intellectual property, supply chain and manufacturing. The purpose of this slide is to highlight the key requirements, solutions and impact of ZTNA implementation on the business. Want to ace your presentation in front of a live audience Our Case Study Intellectual Property Protection With Zero Trust Network Security Inspiration Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide represents the case study for implementing the ZTNA security model into a food and beverage organization to secure intellectual property, supply chain and manufacturing. The purpose of this slide is to highlight the key requirements, solutions and impact of ZTNA implementation on the business.
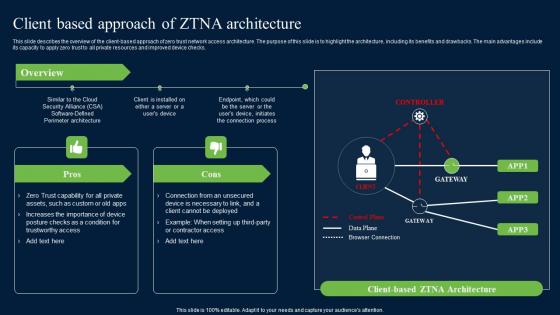
Client Based Approach Of ZTNA Zero Trust Network Security Demonstration Pdf
This slide describes the overview of the client-based approach of zero trust network access architecture. The purpose of this slide is to highlight the architecture, including its benefits and drawbacks. The main advantages include its capacity to apply zero trust to all private resources and improved device checks. Get a simple yet stunning designed Client Based Approach Of ZTNA Zero Trust Network Security Demonstration Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Client Based Approach Of ZTNA Zero Trust Network Security Demonstration Pdf can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide describes the overview of the client-based approach of zero trust network access architecture. The purpose of this slide is to highlight the architecture, including its benefits and drawbacks. The main advantages include its capacity to apply zero trust to all private resources and improved device checks.

Endpoint Initiated Zero Trust Network Topology Zero Trust Network Security Template Pdf
This slide describes the overview of the endpoint-initiated zero trust network topology model of ZTNA deployment. The purpose of this slide is to showcase the conceptual model of the approach along with its benefits and drawbacks. The model components include the end-user device, SDP controller, gateway, and directory. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Endpoint Initiated Zero Trust Network Topology Zero Trust Network Security Template Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide describes the overview of the endpoint-initiated zero trust network topology model of ZTNA deployment. The purpose of this slide is to showcase the conceptual model of the approach along with its benefits and drawbacks. The model components include the end-user device, SDP controller, gateway, and directory.
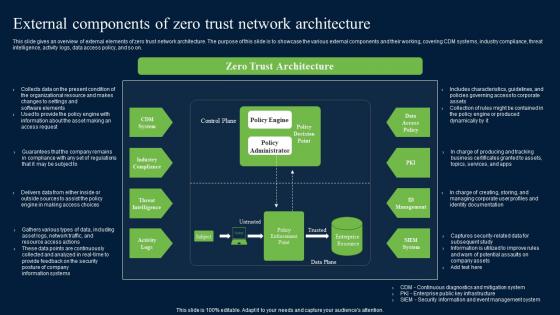
External Components Of Zero Trust Network Security Structure Pdf
This slide gives an overview of external elements of zero trust network architecture. The purpose of this slide is to showcase the various external components and their working, covering CDM systems, industry compliance, threat intelligence, activity logs, data access policy, and so on. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download External Components Of Zero Trust Network Security Structure Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide gives an overview of external elements of zero trust network architecture. The purpose of this slide is to showcase the various external components and their working, covering CDM systems, industry compliance, threat intelligence, activity logs, data access policy, and so on.
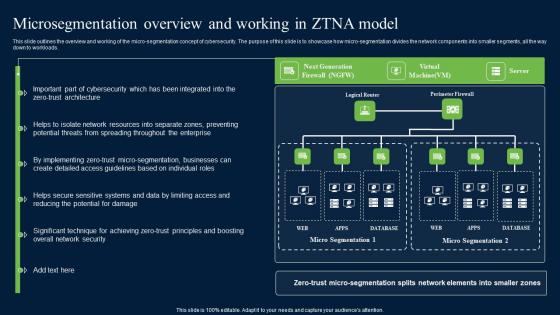
Microsegmentation Overview And Working In ZTNA Zero Trust Network Security Diagrams Pdf
This slide outlines the overview and working of the micro-segmentation concept of cybersecurity. The purpose of this slide is to showcase how micro-segmentation divides the network components into smaller segments, all the way down to workloads. Explore a selection of the finest Microsegmentation Overview And Working In ZTNA Zero Trust Network Security Diagrams Pdf here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Microsegmentation Overview And Working In ZTNA Zero Trust Network Security Diagrams Pdf to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide outlines the overview and working of the micro-segmentation concept of cybersecurity. The purpose of this slide is to showcase how micro-segmentation divides the network components into smaller segments, all the way down to workloads.

On Ramp Option 2 Applications And Data Zero Trust Network Security Sample Pdf
This slide describes the second on-ramp option, which is the applications and data of ZTNA implementation. The purpose of this slide is to give an overview of practices and technologies used in this approach, such as data classification, data loss prevention, authentication and authorization of microservices, container security, etc. The On Ramp Option 2 Applications And Data Zero Trust Network Security Sample Pdf is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide describes the second on-ramp option, which is the applications and data of ZTNA implementation. The purpose of this slide is to give an overview of practices and technologies used in this approach, such as data classification, data loss prevention, authentication and authorization of microservices, container security, etc.
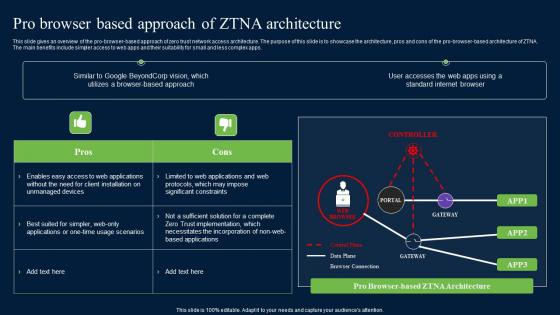
Pro Browser Based Approach Of ZTNA Architecture Zero Trust Network Security Formats Pdf
The main benefits include simpler access to web apps and their suitability for small and less complex apps. Presenting this PowerPoint presentation, titled Pro Browser Based Approach Of ZTNA Architecture Zero Trust Network Security Formats Pdf, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Pro Browser Based Approach Of ZTNA Architecture Zero Trust Network Security Formats Pdf. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Pro Browser Based Approach Of ZTNA Architecture Zero Trust Network Security Formats Pdf that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. The main benefits include simpler access to web apps and their suitability for small and less complex apps.
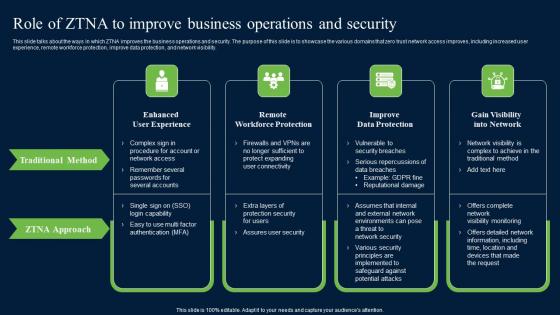
Role Of ZTNA To Improve Business Operations And Security Zero Trust Network Security Inspiration Pdf
This slide talks about the ways in which ZTNA improves the business operations and security. The purpose of this slide is to showcase the various domains that zero trust network access improves, including increased user experience, remote workforce protection, improve data protection, and network visibility. Take your projects to the next level with our ultimate collection of Role Of ZTNA To Improve Business Operations And Security Zero Trust Network Security Inspiration Pdf. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest This slide talks about the ways in which ZTNA improves the business operations and security. The purpose of this slide is to showcase the various domains that zero trust network access improves, including increased user experience, remote workforce protection, improve data protection, and network visibility.
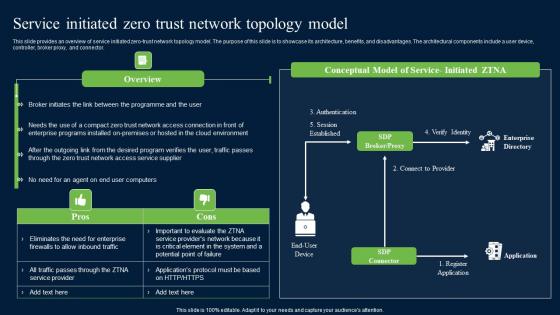
Service Initiated Zero Trust Network Topology Model Zero Trust Network Security Guidelines Pdf
This slide provides an overview of service initiated zero-trust network topology model. The purpose of this slide is to showcase its architecture, benefits, and disadvantages. The architectural components include a user device, controller, broker proxy, and connector. Find a pre-designed and impeccable Service Initiated Zero Trust Network Topology Model Zero Trust Network Security Guidelines Pdf. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide provides an overview of service initiated zero-trust network topology model. The purpose of this slide is to showcase its architecture, benefits, and disadvantages. The architectural components include a user device, controller, broker proxy, and connector.
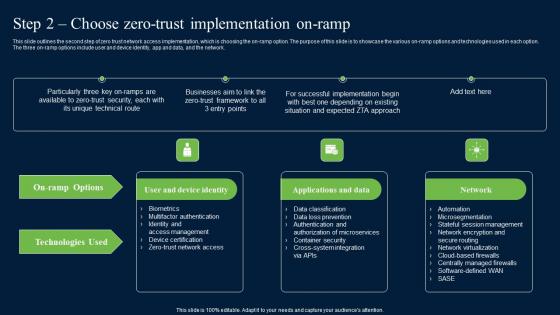
Step 2 Choose Zero Trust Implementation On Ramp Zero Trust Network Security Introduction Pdf
This slide outlines the second step of zero trust network access implementation, which is choosing the on-ramp option. The purpose of this slide is to showcase the various on-ramp options and technologies used in each option. The three on-ramp options include user and device identity, app and data, and the network. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Step 2 Choose Zero Trust Implementation On Ramp Zero Trust Network Security Introduction Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide outlines the second step of zero trust network access implementation, which is choosing the on-ramp option. The purpose of this slide is to showcase the various on-ramp options and technologies used in each option. The three on-ramp options include user and device identity, app and data, and the network.
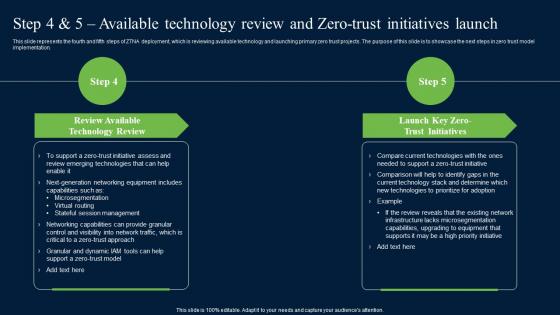
Step 4 And 5 Available Technology Review And Zero Trust Network Security Professional Pdf
This slide represents the fourth and fifth steps of ZTNA deployment, which is reviewing available technology and launching primary zero trust projects. The purpose of this slide is to showcase the next steps in zero trust model implementation. There are so many reasons you need a Step 4 And 5 Available Technology Review And Zero Trust Network Security Professional Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide represents the fourth and fifth steps of ZTNA deployment, which is reviewing available technology and launching primary zero trust projects. The purpose of this slide is to showcase the next steps in zero trust model implementation.

Step 6 And 7 Define Operational Changes And Zero Trust Network Security Diagrams Pdf
This slide outlines the sixth and seventh steps for ZTNA implementation, which are defining operational changes and implementing, rinsing and repeating the process. The purpose of this slide is to showcase the following steps in zero trust model deployment. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Step 6 And 7 Define Operational Changes And Zero Trust Network Security Diagrams Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Step 6 And 7 Define Operational Changes And Zero Trust Network Security Diagrams Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide outlines the sixth and seventh steps for ZTNA implementation, which are defining operational changes and implementing, rinsing and repeating the process. The purpose of this slide is to showcase the following steps in zero trust model deployment.
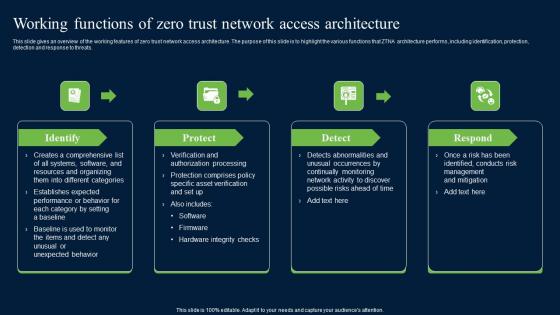
Working Functions Of Zero Trust Network Access Security Infographics Pdf
This slide gives an overview of the working features of zero trust network access architecture. The purpose of this slide is to highlight the various functions that ZTNA architecture performs, including identification, protection, detection and response to threats. Create an editable Working Functions Of Zero Trust Network Access Security Infographics Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Working Functions Of Zero Trust Network Access Security Infographics Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide gives an overview of the working features of zero trust network access architecture. The purpose of this slide is to highlight the various functions that ZTNA architecture performs, including identification, protection, detection and response to threats.

Zero Trust Network Access Architectural Models Ideas Pdf
This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption. There are so many reasons you need a Zero Trust Network Access Architectural Models Ideas Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption.
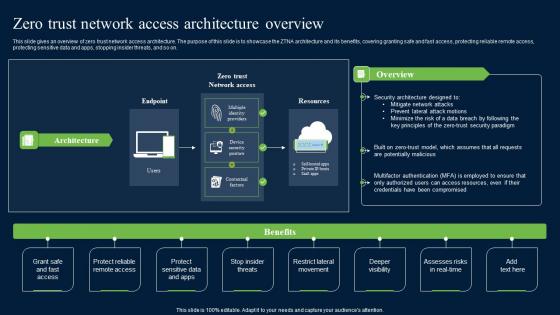
Zero Trust Network Security Access Architecture Overview Graphics Pdf
This slide gives an overview of zero trust network access architecture. The purpose of this slide is to showcase the ZTNA architecture and its benefits, covering granting safe and fast access, protecting reliable remote access, protecting sensitive data and apps, stopping insider threats, and so on. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Zero Trust Network Security Access Architecture Overview Graphics Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide gives an overview of zero trust network access architecture. The purpose of this slide is to showcase the ZTNA architecture and its benefits, covering granting safe and fast access, protecting reliable remote access, protecting sensitive data and apps, stopping insider threats, and so on.
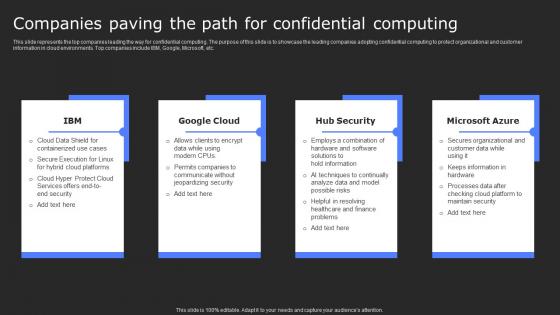
Companies Paving The Path For Confidential Secure Computing Framework Download Pdf
This slide represents the top companies leading the way for confidential computing. The purpose of this slide is to showcase the leading companies adopting confidential computing to protect organizational and customer information in cloud environments. Top companies include IBM, Google, Microsoft, etc. Present like a pro with Companies Paving The Path For Confidential Secure Computing Framework Download Pdf Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide represents the top companies leading the way for confidential computing. The purpose of this slide is to showcase the leading companies adopting confidential computing to protect organizational and customer information in cloud environments. Top companies include IBM, Google, Microsoft, etc.
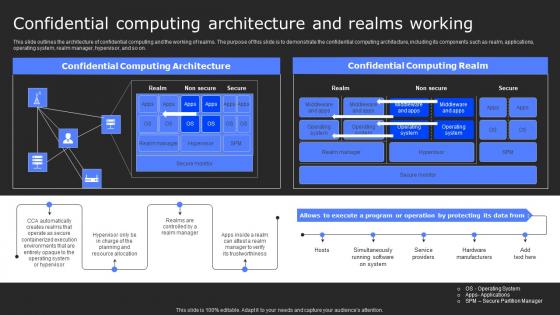
Confidential Computing Architecture And Secure Computing Framework Graphics Pdf
This slide outlines the architecture of confidential computing and the working of realms. The purpose of this slide is to demonstrate the confidential computing architecture, including its components such as realm, applications, operating system, realm manager, hypervisor, and so on. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Confidential Computing Architecture And Secure Computing Framework Graphics Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide outlines the architecture of confidential computing and the working of realms. The purpose of this slide is to demonstrate the confidential computing architecture, including its components such as realm, applications, operating system, realm manager, hypervisor, and so on.
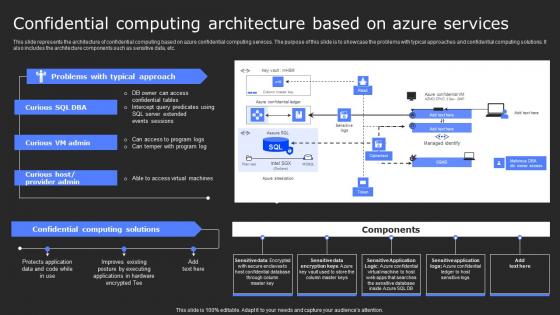
Confidential Computing Architecture Based On Secure Computing Framework Elements Pdf
This slide represents the architecture of confidential computing based on azure confidential computing services. The purpose of this slide is to showcase the problems with typical approaches and confidential computing solutions. It also includes the architecture components such as sensitive data, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Confidential Computing Architecture Based On Secure Computing Framework Elements Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Confidential Computing Architecture Based On Secure Computing Framework Elements Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide represents the architecture of confidential computing based on azure confidential computing services. The purpose of this slide is to showcase the problems with typical approaches and confidential computing solutions. It also includes the architecture components such as sensitive data, etc.
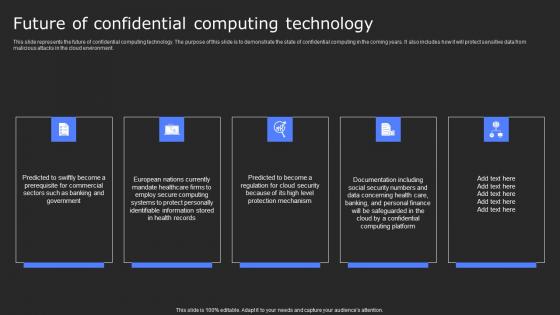
Future Of Confidential Computing Technology Secure Computing Framework Ideas Pdf
This slide represents the future of confidential computing technology. The purpose of this slide is to demonstrate the state of confidential computing in the coming years. It also includes how it will protect sensitive data from malicious attacks in the cloud environment. Presenting this PowerPoint presentation, titled Future Of Confidential Computing Technology Secure Computing Framework Ideas Pdf, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Future Of Confidential Computing Technology Secure Computing Framework Ideas Pdf. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Future Of Confidential Computing Technology Secure Computing Framework Ideas Pdf that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide represents the future of confidential computing technology. The purpose of this slide is to demonstrate the state of confidential computing in the coming years. It also includes how it will protect sensitive data from malicious attacks in the cloud environment.
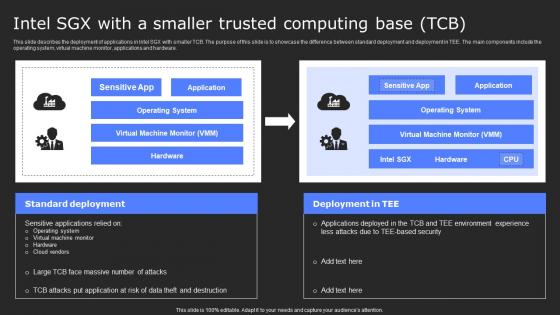
Intel Sgx With A Smaller Trusted Computing Base Tcb Secure Computing Framework Slides Pdf
This slide describes the deployment of applications in Intel SGX with smaller TCB. The purpose of this slide is to showcase the difference between standard deployment and deployment in TEE. The main components include the operating system, virtual machine monitor, applications and hardware. Find a pre-designed and impeccable Intel Sgx With A Smaller Trusted Computing Base Tcb Secure Computing Framework Slides Pdf. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide describes the deployment of applications in Intel SGX with smaller TCB. The purpose of this slide is to showcase the difference between standard deployment and deployment in TEE. The main components include the operating system, virtual machine monitor, applications and hardware.
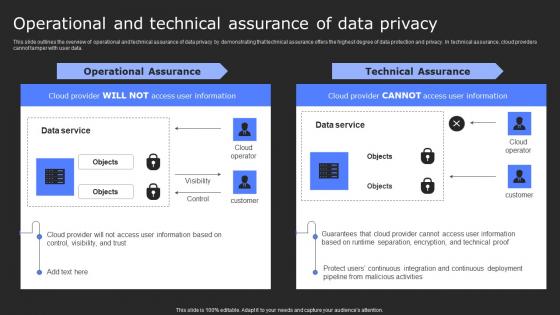
Operational And Technical Assurance Of Data Privacy Secure Computing Framework Mockup Pdf
This slide outlines the overview of operational and technical assurance of data privacy by demonstrating that technical assurance offers the highest degree of data protection and privacy. In technical assurance, cloud providers cannot tamper with user data. Get a simple yet stunning designed Operational And Technical Assurance Of Data Privacy Secure Computing Framework Mockup Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Operational And Technical Assurance Of Data Privacy Secure Computing Framework Mockup Pdf can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide outlines the overview of operational and technical assurance of data privacy by demonstrating that technical assurance offers the highest degree of data protection and privacy. In technical assurance, cloud providers cannot tamper with user data.

Process Of Using Intel Sgx Based Trusted Applications Secure Computing Framework Sample Pdf
This slide outlines the process of using intel sgx-based trusted applications. The purpose of this slide is to demonstrate the procedure of utilizing intel sgx-based trusted applications. The main components include applying for a key, installing the environment, developing, computing and building, and executing. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Process Of Using Intel Sgx Based Trusted Applications Secure Computing Framework Sample Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Process Of Using Intel Sgx Based Trusted Applications Secure Computing Framework Sample Pdf today and make your presentation stand out from the rest This slide outlines the process of using intel sgx-based trusted applications. The purpose of this slide is to demonstrate the procedure of utilizing intel sgx-based trusted applications. The main components include applying for a key, installing the environment, developing, computing and building, and executing.
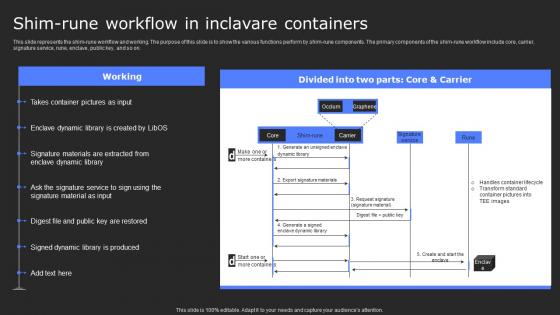
Shim Rune Workflow In Inclavare Containers Secure Computing Framework Infographics Pdf
This slide represents the shim-rune workflow and working. The purpose of this slide is to show the various functions perform by shim-rune components. The primary components of the shim-rune workflow include core, carrier, signature service, rune, enclave, public key, and so on. Create an editable Shim Rune Workflow In Inclavare Containers Secure Computing Framework Infographics Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Shim Rune Workflow In Inclavare Containers Secure Computing Framework Infographics Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide represents the shim-rune workflow and working. The purpose of this slide is to show the various functions perform by shim-rune components. The primary components of the shim-rune workflow include core, carrier, signature service, rune, enclave, public key, and so on.

Technical Stack For Evaluating Confidential Secure Computing Framework Information Pdf
This slide depicts the technical stack while assessing confidential computing solutions. The stack divides these solutions into four levels, including application software vendors, infrastructure providers, hardware vendors, and cryptographic building blocks. Want to ace your presentation in front of a live audience Our Technical Stack For Evaluating Confidential Secure Computing Framework Information Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide depicts the technical stack while assessing confidential computing solutions. The stack divides these solutions into four levels, including application software vendors, infrastructure providers, hardware vendors, and cryptographic building blocks.
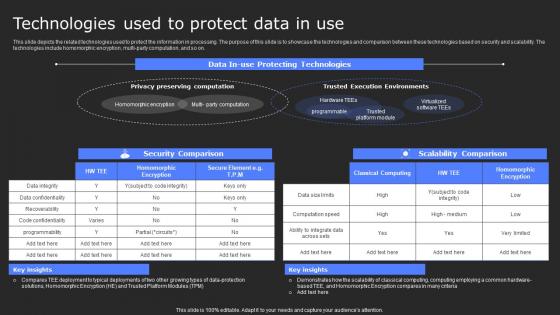
Technologies Used To Protect Data In Use Secure Computing Framework Diagrams Pdf
This slide depicts the related technologies used to protect the information in processing. The purpose of this slide is to showcase the technologies and comparison between these technologies based on security and scalability. The technologies include homomorphic encryption, multi-party computation, and so on. There are so many reasons you need a Technologies Used To Protect Data In Use Secure Computing Framework Diagrams Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide depicts the related technologies used to protect the information in processing. The purpose of this slide is to showcase the technologies and comparison between these technologies based on security and scalability. The technologies include homomorphic encryption, multi-party computation, and so on.
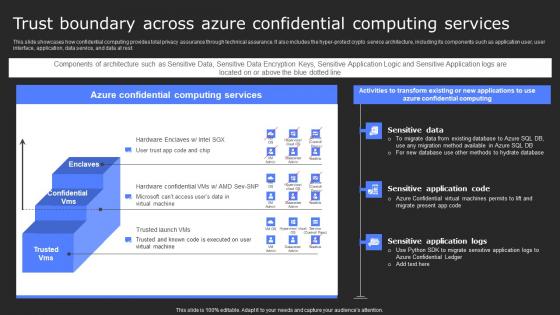
Trust Boundary Across Azure Confidential Services Secure Computing Framework Sample Pdf
This slide showcases how confidential computing provides total privacy assurance through technical assurance. It also includes the hyper-protect crypto service architecture, including its components such as application user, user interface, application, data service, and data at rest. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Trust Boundary Across Azure Confidential Services Secure Computing Framework Sample Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Trust Boundary Across Azure Confidential Services Secure Computing Framework Sample Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide showcases how confidential computing provides total privacy assurance through technical assurance. It also includes the hyper-protect crypto service architecture, including its components such as application user, user interface, application, data service, and data at rest.

Trusted Execution Environment Tee Hardware Secure Computing Framework Graphics Pdf
This slide represents the trusted execution environment hardware platform used in confidential computing. The TEE environment is supported by three hardware platforms covering Intel SGX, ARM TrustZone, and Advanced Micro Devices AMD. Get a simple yet stunning designed Trusted Execution Environment Tee Hardware Secure Computing Framework Graphics Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Trusted Execution Environment Tee Hardware Secure Computing Framework Graphics Pdf can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide represents the trusted execution environment hardware platform used in confidential computing. The TEE environment is supported by three hardware platforms covering Intel SGX, ARM TrustZone, and Advanced Micro Devices AMD.

About Cryptography Overview Cloud Data Security Using Cryptography Designs Pdf
This slide talks about the concept of cryptography to secure the information sent to the recipient. The purpose of this slide is to represent the various principles of cryptography such as confidentiality, integrity, authentication, etc. Slidegeeks is here to make your presentations a breeze with About Cryptography Overview Cloud Data Security Using Cryptography Designs Pdf With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide talks about the concept of cryptography to secure the information sent to the recipient. The purpose of this slide is to represent the various principles of cryptography such as confidentiality, integrity, authentication, etc.
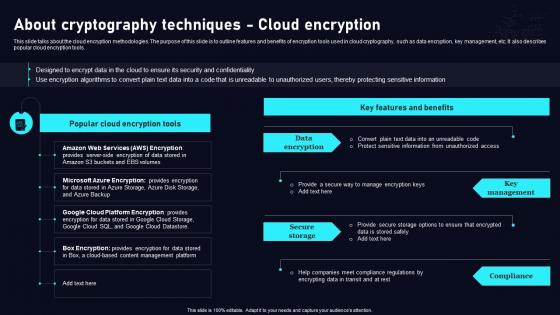
Cloud Data Security Using Cryptography About Cryptography Techniques Cloud Download Pdf
This slide talks about the cloud encryption methodologies. The purpose of this slide is to outline features and benefits of encryption tools used in cloud cryptography, such as data encryption, key management, etc. It also describes popular cloud encryption tools. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Cloud Data Security Using Cryptography About Cryptography Techniques Cloud Download Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Cloud Data Security Using Cryptography About Cryptography Techniques Cloud Download Pdf This slide talks about the cloud encryption methodologies. The purpose of this slide is to outline features and benefits of encryption tools used in cloud cryptography, such as data encryption, key management, etc. It also describes popular cloud encryption tools.
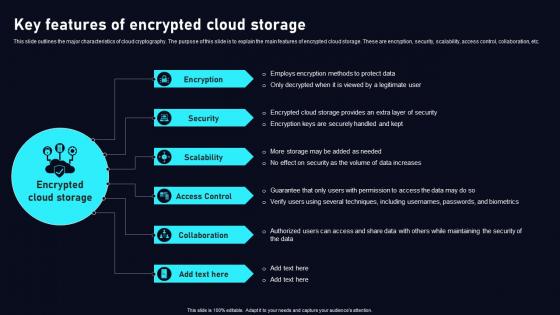
Key Features Of Encrypted Cloud Storage Cloud Data Security Using Cryptography Portrait Pdf
This slide outlines the major characteristics of cloud cryptography. The purpose of this slide is to explain the main features of encrypted cloud storage. These are encryption, security, scalability, access control, collaboration, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Key Features Of Encrypted Cloud Storage Cloud Data Security Using Cryptography Portrait Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide outlines the major characteristics of cloud cryptography. The purpose of this slide is to explain the main features of encrypted cloud storage. These are encryption, security, scalability, access control, collaboration, etc.

Methods To Overcome Cloud Data Security Using Cryptography Infographics Pdf
The purpose of this slide is to elaborate some ways that cloud cryptography can help overcome cloud data security challenges. The key points mentioned in this slide are confidentiality, integrity, access control and key management. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Methods To Overcome Cloud Data Security Using Cryptography Infographics Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Methods To Overcome Cloud Data Security Using Cryptography Infographics Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today The purpose of this slide is to elaborate some ways that cloud cryptography can help overcome cloud data security challenges. The key points mentioned in this slide are confidentiality, integrity, access control and key management.
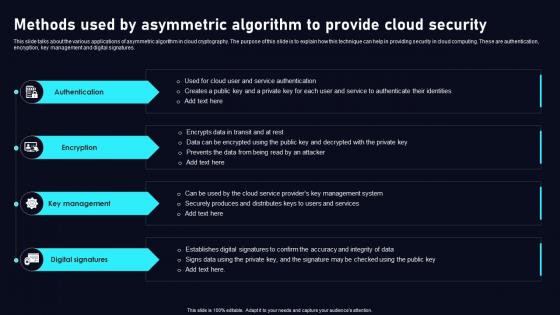
Methods Used By Asymmetric Algorithm Cloud Data Security Using Cryptography Inspiration Pdf
This slide talks about the various applications of asymmetric algorithm in cloud cryptography. The purpose of this slide is to explain how this technique can help in providing security in cloud computing. These are authentication, encryption, key management and digital signatures. Get a simple yet stunning designed Methods Used By Asymmetric Algorithm Cloud Data Security Using Cryptography Inspiration Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Methods Used By Asymmetric Algorithm Cloud Data Security Using Cryptography Inspiration Pdf can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide talks about the various applications of asymmetric algorithm in cloud cryptography. The purpose of this slide is to explain how this technique can help in providing security in cloud computing. These are authentication, encryption, key management and digital signatures.
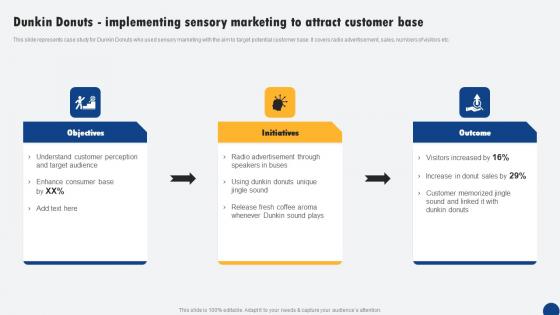
Dunkin Donuts Implementing Sensory Marketing To Driven Digital Marketing Inspiration Pdf
This slide represents case study for Dunkin Donuts who used sensory marketing with the aim to target potential customer base. It covers radio advertisement, sales, numbers of visitors etc. There are so many reasons you need a Dunkin Donuts Implementing Sensory Marketing To Driven Digital Marketing Inspiration Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide represents case study for Dunkin Donuts who used sensory marketing with the aim to target potential customer base. It covers radio advertisement, sales, numbers of visitors etc.
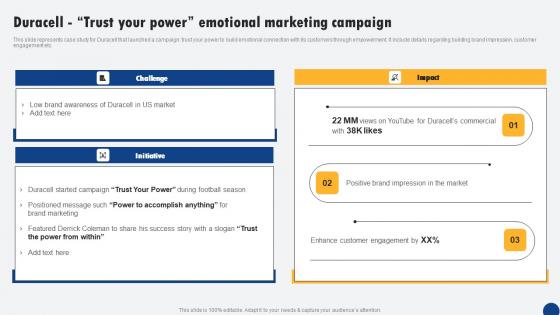
Duracell Trust Your Power Emotional Marketing Driven Digital Marketing Professional Pdf
This slide represents case study for Duracell that launched a campaign trust your power to build emotional connection with its customers through empowerment. It include details regarding building brand impression, customer engagement etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Duracell Trust Your Power Emotional Marketing Driven Digital Marketing Professional Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Duracell Trust Your Power Emotional Marketing Driven Digital Marketing Professional Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide represents case study for Duracell that launched a campaign trust your power to build emotional connection with its customers through empowerment. It include details regarding building brand impression, customer engagement etc.
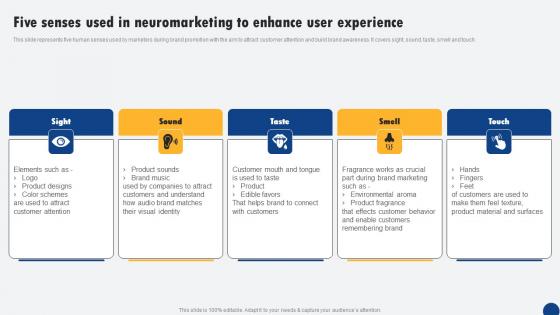
Five Senses Used In Neuromarketing To Enhance User Driven Digital Marketing Elements Pdf
This slide represents five human senses used by marketers during brand promotion with the aim to attract customer attention and build brand awareness. It covers sight, sound, taste, smell and touch. Slidegeeks is here to make your presentations a breeze with Five Senses Used In Neuromarketing To Enhance User Driven Digital Marketing Elements Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide represents five human senses used by marketers during brand promotion with the aim to attract customer attention and build brand awareness. It covers sight, sound, taste, smell and touch.

How Neuromarketing Helps In Enhancing Advertising Driven Digital Marketing Download Pdf
This slide represents example for brand advertisement that used neuromarketing to enhance ROI return on investment. It includes behavioral research, EEG Electroencephalography etc. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit How Neuromarketing Helps In Enhancing Advertising Driven Digital Marketing Download Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide represents example for brand advertisement that used neuromarketing to enhance ROI return on investment. It includes behavioral research, EEG Electroencephalography etc.
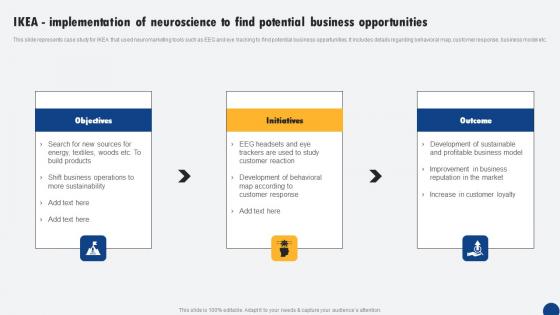
IKEA Implementation Of Neuroscience To Find Potential Driven Digital Marketing Topics Pdf
This slide represents case study for IKEA that used neuromarketing tools such as EEG and eye tracking to find potential business opportunities. It includes details regarding behavioral map, customer response, business model etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward IKEA Implementation Of Neuroscience To Find Potential Driven Digital Marketing Topics Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal IKEA Implementation Of Neuroscience To Find Potential Driven Digital Marketing Topics Pdf that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide represents case study for IKEA that used neuromarketing tools such as EEG and eye tracking to find potential business opportunities. It includes details regarding behavioral map, customer response, business model etc.


 Continue with Email
Continue with Email

 Home
Home


































