Strategic Risk

Table Of Contents For Threat Intelligence Framework Ppt Slides
Retrieve professionally designed Table Of Contents For Threat Intelligence Framework Ppt Slides to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. Our Table Of Contents For Threat Intelligence Framework Ppt Slides are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
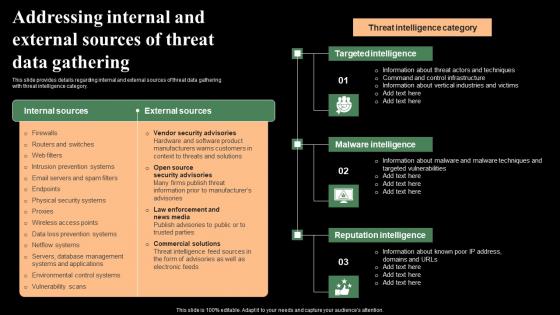
Addressing Internal And External Sources Of Threat Data Monitoring Digital Assets Demonstration Pdf
This slide provides details regarding internal and external sources of threat data gathering with threat intelligence category. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Addressing Internal And External Sources Of Threat Data Monitoring Digital Assets Demonstration Pdf to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Addressing Internal And External Sources Of Threat Data Monitoring Digital Assets Demonstration Pdf This slide provides details regarding internal and external sources of threat data gathering with threat intelligence category.
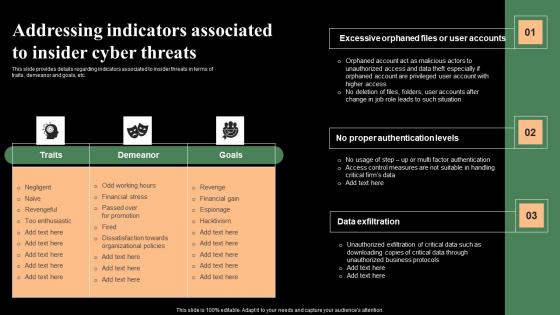
Addressing Indicators Associated To Insider Cyber Threats Monitoring Digital Assets Themes Pdf
This slide provides details regarding indicators associated to insider threats in terms of traits, demeanor and goals, etc. Presenting this PowerPoint presentation, titled Addressing Indicators Associated To Insider Cyber Threats Monitoring Digital Assets Themes Pdf with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Addressing Indicators Associated To Insider Cyber Threats Monitoring Digital Assets Themes Pdf Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Addressing Indicators Associated To Insider Cyber Threats Monitoring Digital Assets Themes Pdf that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide provides details regarding indicators associated to insider threats in terms of traits, demeanor and goals, etc.
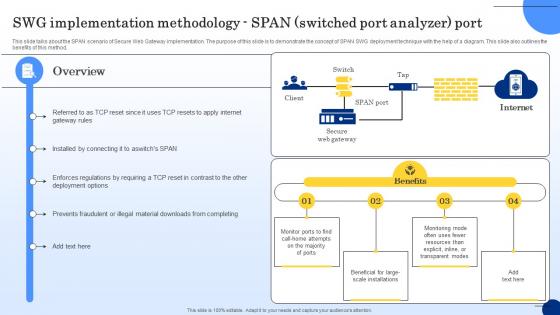
SWG Implementation Methodology Span Web Threat Protection System
This slide talks about the SPAN scenario of Secure Web Gateway implementation. The purpose of this slide is to demonstrate the concept of SPAN SWG deployment technique with the help of a diagram. This slide also outlines the benefits of this method. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than SWG Implementation Methodology Span Web Threat Protection System. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab SWG Implementation Methodology Span Web Threat Protection System today and make your presentation stand out from the rest This slide talks about the SPAN scenario of Secure Web Gateway implementation. The purpose of this slide is to demonstrate the concept of SPAN SWG deployment technique with the help of a diagram. This slide also outlines the benefits of this method.

Limitations Of Switched Port Analyzer Method Web Threat Protection System
This slide discusses drawbacks of Switched Port Analyzer method. The purpose of this slide is to explain why SPAN port is not considered as a real-time method. The limitations are unable to see all traffic, cause delays on network, etc. The Limitations Of Switched Port Analyzer Method Web Threat Protection System is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide discusses drawbacks of Switched Port Analyzer method. The purpose of this slide is to explain why SPAN port is not considered as a real-time method. The limitations are unable to see all traffic, cause delays on network, etc.

Secure Web Gateway Implementation Methodology Inline Web Threat Protection System
This slide talks about the inline scenario of Secure Web Gateway implementation. The purpose of this slide is to demonstrate the concept of inline SWG deployment technique with the help of a diagram. This slide also outlines the benefits of this method. Boost your pitch with our creative Secure Web Gateway Implementation Methodology Inline Web Threat Protection System. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide talks about the inline scenario of Secure Web Gateway implementation. The purpose of this slide is to demonstrate the concept of inline SWG deployment technique with the help of a diagram. This slide also outlines the benefits of this method.

Secure Web Gateway Training Program Web Threat Protection System
This slide represents the training program for the Secure Web Gateway. The main components of training program are agenda, system requirements, mode such as online, offline or recorded videos, and cost. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Secure Web Gateway Training Program Web Threat Protection System will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide represents the training program for the Secure Web Gateway. The main components of training program are agenda, system requirements, mode such as online, offline or recorded videos, and cost.

Integration Of SWG Inside SASE Architecture Web Threat Protection System
This slide represents the architecture of Relationship between Secure Access Service Edge and Secure Web Gateway integration. The purpose of this slide is to illustrate the collaboration of SASE and SWG inside a network. Key components included are websites, cloud apps, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Integration Of SWG Inside SASE Architecture Web Threat Protection System to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide represents the architecture of Relationship between Secure Access Service Edge and Secure Web Gateway integration. The purpose of this slide is to illustrate the collaboration of SASE and SWG inside a network. Key components included are websites, cloud apps, etc.

Secure Web Gateway Architecture And Working Web Threat Protection System
This slide demonstrates the working process of Secure Web Gateway by providing a visualization of its various components. The purpose of this slide is to explain how SWG works. Key points included are offices, private data centres, interface, etc. This Secure Web Gateway Architecture And Working Web Threat Protection System from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide demonstrates the working process of Secure Web Gateway by providing a visualization of its various components. The purpose of this slide is to explain how SWG works. Key points included are offices, private data centres, interface, etc.
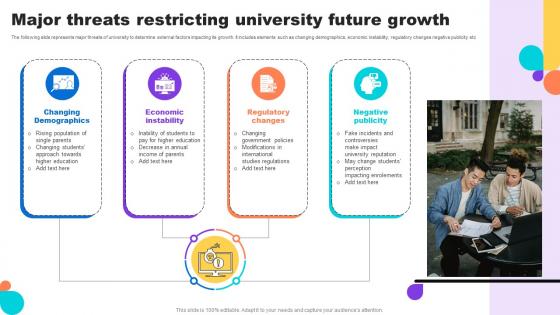
Major Threats Restricting University Future Growth Key Step To Implementation University Strategy SS V
The following slide represents major threats of university to determine external factors impacting its growth. It includes elements such as changing demographics, economic instability, regulatory changes negative publicity etcRetrieve professionally designed Major Threats Restricting University Future Growth Key Step To Implementation University Strategy SS V to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. The following slide represents major threats of university to determine external factors impacting its growth. It includes elements such as changing demographics, economic instability, regulatory changes negative publicity etc

University Marketing Guide Major Threats Restricting University Future Growth Strategy SS V
The following slide represents major threats of university to determine external factors impacting its growth. It includes elements such as changing demographics, economic instability, regulatory changes negative publicity etc. Slidegeeks has constructed University Marketing Guide Major Threats Restricting University Future Growth Strategy SS V after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. The following slide represents major threats of university to determine external factors impacting its growth. It includes elements such as changing demographics, economic instability, regulatory changes negative publicity etc.

Incident Management Process Safety Identifying The Workplace Hazard Structure PDF
The following slide identifies types of workplace hazard that may effect the organization, these hazards can be safety hazard, chemical hazards, biological hazards and other health hazards. Deliver and pitch your topic in the best possible manner with this incident management process safety identifying the workplace hazard structure pdf. Use them to share invaluable insights on safety hazards, chemical hazards, biological hazards, other health hazards and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
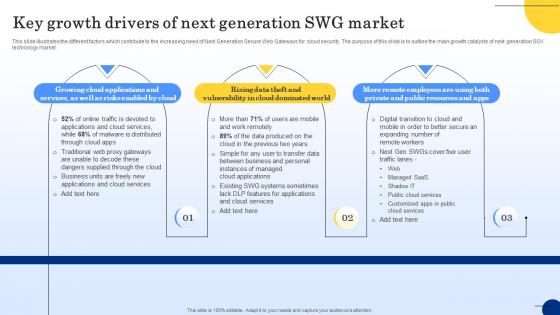
Key Growth Drivers Of Next Generation SWG Market Web Threat Protection System
This slide illustrates the different factors which contribute to the increasing need of Next Generation Secure Web Gateways for cloud security. The purpose of this slide is to outline the main growth catalysts of next generation SGV technology market. Explore a selection of the finest Key Growth Drivers Of Next Generation SWG Market Web Threat Protection System here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Key Growth Drivers Of Next Generation SWG Market Web Threat Protection System to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide illustrates the different factors which contribute to the increasing need of Next Generation Secure Web Gateways for cloud security. The purpose of this slide is to outline the main growth catalysts of next generation SGV technology market.

Secure Web Gateway Set Up Planning And Preparation Web Threat Protection System
This slide represents the procedure for implementing Secure Web Gateway in network. The purpose of this slide is to explain the planning and preparation phase of SWG set-up. The key points included are define scope of project, identify network architecture, etc. Get a simple yet stunning designed Secure Web Gateway Set Up Planning And Preparation Web Threat Protection System. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Secure Web Gateway Set Up Planning And Preparation Web Threat Protection System can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide represents the procedure for implementing Secure Web Gateway in network. The purpose of this slide is to explain the planning and preparation phase of SWG set-up. The key points included are define scope of project, identify network architecture, etc.
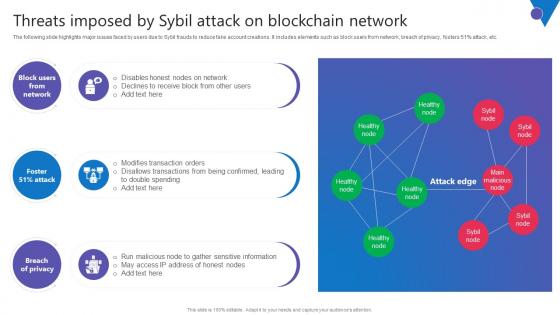
Threats Imposed By Sybil Attack Comprehensive Guide To Blockchain Digital Security Introduction Pdf
The following slide highlights major issues faced by users due to Sybil frauds to reduce fake account creations. It includes elements such as block users from network, breach of privacy, fosters 51percent attack, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Threats Imposed By Sybil Attack Comprehensive Guide To Blockchain Digital Security Introduction Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. The following slide highlights major issues faced by users due to Sybil frauds to reduce fake account creations. It includes elements such as block users from network, breach of privacy, fosters 51percent attack, etc.

Before Vs After Implementing Secure Web Gateway Web Threat Protection System
This slide compares the scenario after integrating SWG in organizational network. The purpose of this slide is to represent before and after situation based on several parameters. The factors used to do the comparison are cost, security, productivity, etc. Want to ace your presentation in front of a live audience Our Before Vs After Implementing Secure Web Gateway Web Threat Protection System can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide compares the scenario after integrating SWG in organizational network. The purpose of this slide is to represent before and after situation based on several parameters. The factors used to do the comparison are cost, security, productivity, etc.

Importance Of Secure Web Gateway For Businesses Web Threat Protection System
This slide talks about the role of Secure Web Gateway in organizations. The purpose of this slide is to explain why companies require SWG. The components covered are ID provider, data center, client connector, global policy engine, real-time analytics, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Importance Of Secure Web Gateway For Businesses Web Threat Protection System. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide talks about the role of Secure Web Gateway in organizations. The purpose of this slide is to explain why companies require SWG. The components covered are ID provider, data center, client connector, global policy engine, real-time analytics, etc.

Comparison Between Secure Web Gateway And Firewalls Web Threat Protection System
This slide demonstrates the concept of two security technologies named firewalls and Secure Web Gateways. The purpose of this slide is to compare firewalls and SWGs on the basis of various factors such as function, scope, granularity, features and deployment. Present like a pro with Comparison Between Secure Web Gateway And Firewalls Web Threat Protection System. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide demonstrates the concept of two security technologies named firewalls and Secure Web Gateways. The purpose of this slide is to compare firewalls and SWGs on the basis of various factors such as function, scope, granularity, features and deployment.

Introduction To Next Generation Secure Web Gateway Web Threat Protection System
This slide demonstrates the concept of Next Generation Secure Web Gateway solution. The purpose of this slide is to provide an overview of next generation SGVs. This slide also talks about the need of this security technology for cloud applications. This modern and well-arranged Introduction To Next Generation Secure Web Gateway Web Threat Protection System provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide demonstrates the concept of Next Generation Secure Web Gateway solution. The purpose of this slide is to provide an overview of next generation SGVs. This slide also talks about the need of this security technology for cloud applications.

Secure Web Gateway For Remote And On Site Workers Web Threat Protection System
This slide represents the on-premise and cloud based SWG technology solution for organizations. The purpose of this slide is to provide visualization of Secure Web Gateway structure enabling encrypted web surfing for both on-site and remote employees. Do you know about Slidesgeeks Secure Web Gateway For Remote And On Site Workers Web Threat Protection System These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide represents the on-premise and cloud based SWG technology solution for organizations. The purpose of this slide is to provide visualization of Secure Web Gateway structure enabling encrypted web surfing for both on-site and remote employees.

Types Of Plant Safety Measures Hazards Ideas PDF
This slide covers plant safety measures hazards. It is of three types that are physical, biological and chemical. Pitch your topic with ease and precision using this Types Of Plant Safety Measures Hazards Ideas PDF. This layout presents information on Physical, Biological, Chemical. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
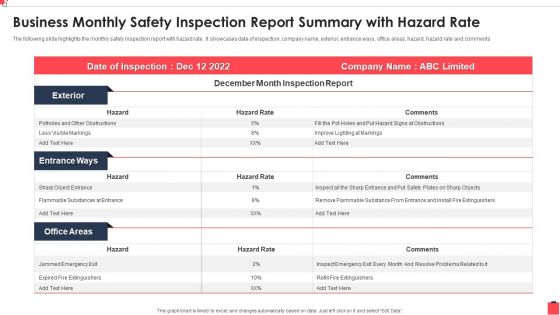
Business Monthly Safety Inspection Report Summary With Hazard Rate Guidelines PDF
The following slide highlights the monthly safety inspection report with hazard rate. It showcases date of inspection, company name, exterior, entrance ways, office areas, hazard, hazard rate and comments.Showcasing this set of slides titled Business Monthly Safety Inspection Report Summary With Hazard Rate Guidelines PDF The topics addressed in these templates are Exterior, Entrance Ways, Office Areas All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Workplace Safety Best Practices Hazard Identification And Control Measures Table Of Contents Background PDF
Whether you have daily or monthly meetings, a brilliant presentation is necessary. Workplace Safety Best Practices Hazard Identification And Control Measures Table Of Contents Background PDF can be your best option for delivering a presentation. Represent everything in detail using Workplace Safety Best Practices Hazard Identification And Control Measures Table Of Contents Background PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Four Computer Security Threats Rules PDF
This slide shows the 4 threats to cyber security. It includes phishing attacks, cloud jacking, IoT devices and insider threats.Pitch your topic with ease and precision using this Four Computer Security Threats Rules PDF This layout presents information on Data Manipulation, Attacker Attempts, Sensitive Information It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Business Threat Modeling Procedure Icon Designs PDF
Showcasing this set of slides titled Business Threat Modeling Procedure Icon Designs PDF. The topics addressed in these templates are Business Threat, Modeling Procedure Icon. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Business Major Threat Rating Icon Graphics PDF
Showcasing this set of slides titled Business Major Threat Rating Icon Graphics PDF. The topics addressed in these templates are Business Major, Threat Rating. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
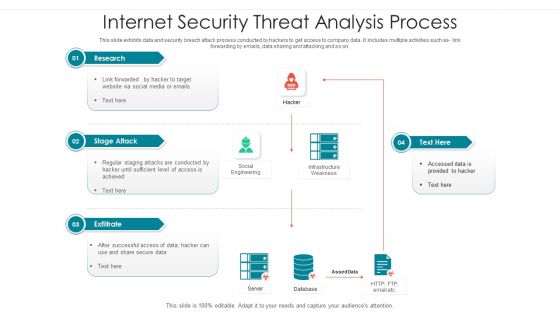
Internet Security Threat Analysis Process Brochure PDF
Following slide showcase how a data breach process is performed by hacker to collect and utilize company data. It includes following activities such as code integration with company software, so on. Showcasing this set of slides titled internet security threat analysis process brochure pdf. The topics addressed in these templates are supply chain attack, execution persistence, defense evasion, exfiltration, keyboard attack. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
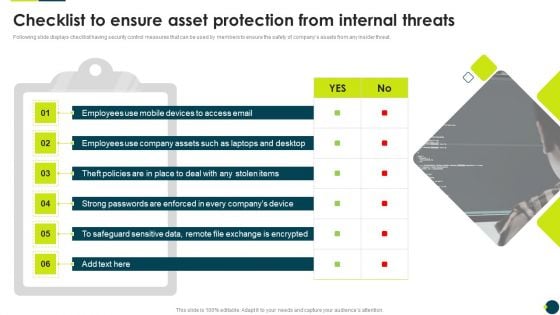
IT Threats Response Playbook Checklist To Ensure Asset Protection From Internal Threats Information PDF
Following slide displays checklist having security control measures that can be used by members to ensure the safety of companys assets from any insider threat.Deliver an awe inspiring pitch with this creative IT Threats Response Playbook Checklist To Ensure Asset Protection From Internal Threats Information PDF bundle. Topics like Safeguard Sensitive, Strong Passwords, Exchange Encrypted can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Integrating Logistics Automation Solution Expected Solutions To Day To Day Problems In Shipping Ppt Model Backgrounds PDF
This slide covers the expected solutions to daily problems of the shipping and logistics businesses such as congestion and accidents, transport costs etc. Want to ace your presentation in front of a live audience. Our Integrating Logistics Automation Solution Expected Solutions To Day To Day Problems In Shipping Ppt Model Backgrounds PDF can help you do that by engaging all the users towards you.. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.

Expected Solutions To Day To Day Problems In Shipping And Logistics Business Sample PDF
This slide covers the expected solutions to daily problems of the shipping and logistics businesses such as congestion and accidents, transport costs etc. Welcome to our selection of the Expected Solutions To Day To Day Problems In Shipping And Logistics Business Sample PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100precent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.
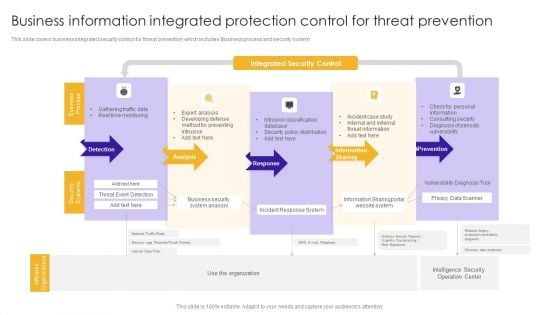
Business Information Integrated Protection Control For Threat Prevention Graphics PDF
This slide covers business integrated security control for threat prevention which includes Business process and security system.Pitch your topic with ease and precision using this Business Information Integrated Protection Control For Threat Prevention Graphics PDF. This layout presents information on Incident Response, Security Policy Distribution, Threat Information. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Event Threat In Mitigation Framework Icon Elements PDF
Showcasing this set of slides titled Event Threat In Mitigation Framework Icon Elements PDF. The topics addressed in these templates are Event Threat, In Mitigation, Framework Icon. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Event Threat Mitigation And Project Documentation Icon Diagrams PDF
Showcasing this set of slides titled Event Threat Mitigation And Project Documentation Icon Diagrams PDF. The topics addressed in these templates are Event Threat, Mitigation, Project Documentation Icon. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Bio Metrics Technology Icon Promoting Cyber Threat Prevention Designs PDF
Pitch your topic with ease and precision using this Bio Metrics Technology Icon Promoting Cyber Threat Prevention Designs PDF. This layout presents information on Bio Metrics Technology, Promoting Cyber Threat, Prevention. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
System Threat Organizational Prevention Based Strategy Guidelines PDF
Present the topic in a bit more detail with this System Threat Organizational Prevention Based Strategy Guidelines PDF. Use it as a tool for discussion and navigation on System Threat Organizational, Prevention Based Strategy. This template is free to edit as deemed fit for your organization. Therefore download it now.
Threat Intelligence Framework For Banks Icon Designs PDF
Showcasing this set of slides titled Threat Intelligence Framework For Banks Icon Designs PDF. The topics addressed in these templates are Threat Intelligence, Framework Banks Icon. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

SWOT Analysis Of HCL Plus Logistics Company Threats Rules PDF
This slide shows some threats that may effect the company in future course of time and impact the company profits. Some potential threats are Intense Competition from Rivalries , Rising Fuel Costs , Government Regulations and Currency Fluctuations etc. Deliver and pitch your topic in the best possible manner with this swot analysis of hcl plus logistics company threats rules pdf. Use them to share invaluable insights on technologies, market, technology, costs, customer and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
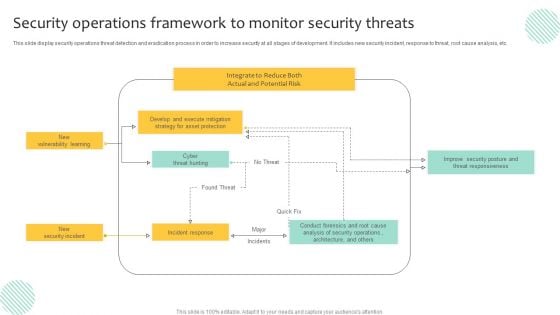
Security Operations Framework To Monitor Security Threats Demonstration PDF
This slide display security operations threat detection and eradication process in order to increase security at all stages of development. It includes new security incident, response to threat, root cause analysis, etc. Pitch your topic with ease and precision using this Security Operations Framework To Monitor Security Threats Demonstration PDF. This layout presents information on Execute Mitigation, Develop, Strategy. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
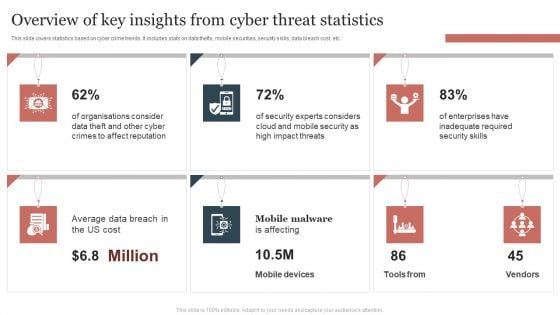
Overview Of Key Insights From Cyber Threat Statistics Themes PDF
This slide covers statistics based on cyber crime trends. It includes stats on data thefts, mobile securities, security skills, data breach cost, etc. Showcasing this set of slides titled Overview Of Key Insights From Cyber Threat Statistics Themes PDF. The topics addressed in these templates are Overview Of Key Insights, Cyber Threat Statistics . All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
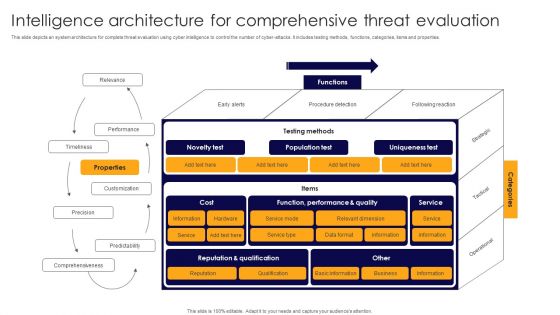
Intelligence Architecture For Comprehensive Threat Evaluation Mockup PDF
This slide depicts an system architecture for complete threat evaluation using cyber intelligence to control the number of cyber-attacks. It includes testing methods, functions, categories, items and properties. Showcasing this set of slides titled Intelligence Architecture For Comprehensive Threat Evaluation Mockup PDF. The topics addressed in these templates are Performance, Timeliness, Customization. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cybersecurity Operations Cybersecops Security Operations Threat Management Brochure PDF
This slide depicts the security operations threat management process. The purpose of this slide is to showcase the various stages and operations included in the security operations threat management process. The steps include discovery, preliminary investigation, triage, extended investigation, and contain and respond. The Cybersecurity Operations Cybersecops Security Operations Threat Management Brochure PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Real Time Assessment Of Security Threats Table Of Contents Real Time Assessment Of Security Threats Mockup PDF
Deliver an awe inspiring pitch with this creative real time assessment of security threats table of contents real time assessment of security threats mockup pdf bundle. Topics like company overview, challenges and solutions, services offered, siem hosting models, siem architecture can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
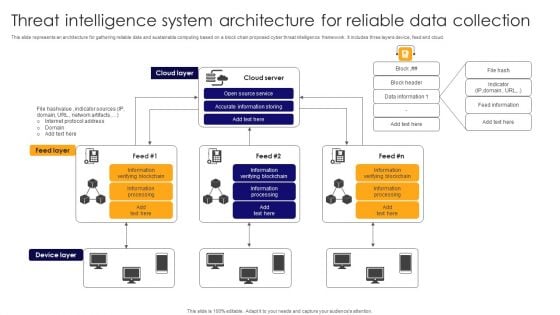
Threat Intelligence System Architecture For Reliable Data Collection Pictures PDF
This slide represents an architecture for gathering reliable data and sustainable computing based on a block chain proposed cyber threat intelligence framework . It includes three layers device, feed and cloud. Showcasing this set of slides titled Threat Intelligence System Architecture For Reliable Data Collection Pictures PDF. The topics addressed in these templates are Cloud Server, Accurate Information Storing, Open Source Service. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
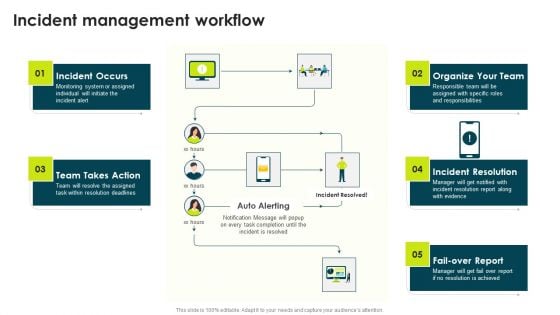
IT Threats Response Playbook Incident Management Workflow Themes PDF
Deliver an awe inspiring pitch with this creative IT Threats Response Playbook Incident Management Workflow Themes PDF bundle. Topics like Incident Occurs, Incident Resolution, Resolution Achieved can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
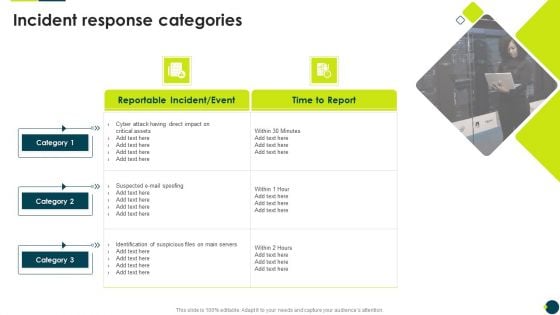
IT Threats Response Playbook Incident Response Categories Rules PDF
Deliver and pitch your topic in the best possible manner with this IT Threats Response Playbook Incident Response Categories Rules PDF. Use them to share invaluable insights on Identification Suspicious, Direct Impact, Time To Report and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
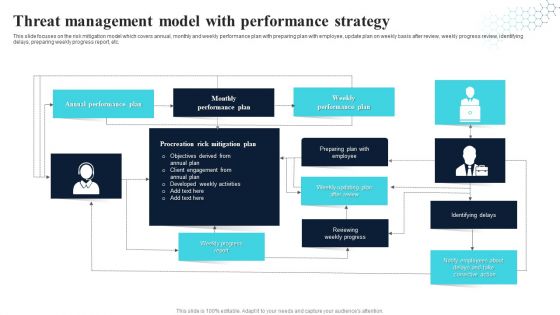
Threat Management Model With Performance Strategy Topics PDF
Showcasing this set of slides titled Threat Management Model With Performance Strategy Topics PDF. The topics addressed in these templates are Monthly Performance Plan, Weekly Performance Plan, Annual Performance Plan. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Solution Assessment Investor Problems Icon Microsoft PDF
Showcasing this set of slides titled Solution Assessment Investor Problems Icon Microsoft PDF. The topics addressed in these templates are Solution Assessment, Investor Problems Icon. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
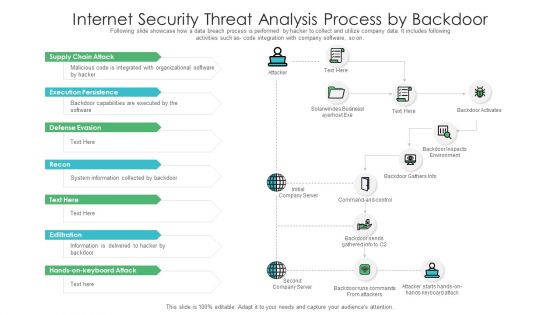
Internet Security Threat Analysis Process By Backdoor Graphics PDF
This slide exhibits data and security breach attack process conducted by hackers to get access to company data. It includes multiple activities such as link forwarding by emails, data sharing and attacking and so on. Showcasing this set of slides titled internet security threat analysis process by backdoor graphics pdf. The topics addressed in these templates are exfiltrate, stage attack, research. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
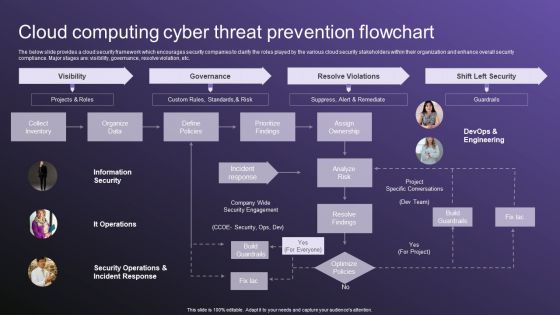
Cloud Computing Cyber Threat Prevention Flowchart Slides PDF
The below slide provides a cloud security framework which encourages security companies to clarify the roles played by the various cloud security stakeholders within their organization and enhance overall security compliance. Major stages are visibility, governance, resolve violation, etc. Showcasing this set of slides titled Cloud Computing Cyber Threat Prevention Flowchart Slides PDF. The topics addressed in these templates are Visibility, Governance, Resolve Violations. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Secure Web Gateway Implementation Methodology Transparent Web Threat Protection System
This slide talks about the transparent scenario of Secure Web Gateway implementation. The purpose of this slide is to demonstrate the concept of transparent SWG deployment technique with the help of a diagram. This slide also outlines the benefits of this method. Create an editable Secure Web Gateway Implementation Methodology Transparent Web Threat Protection System that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Secure Web Gateway Implementation Methodology Transparent Web Threat Protection System is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide talks about the transparent scenario of Secure Web Gateway implementation. The purpose of this slide is to demonstrate the concept of transparent SWG deployment technique with the help of a diagram. This slide also outlines the benefits of this method.
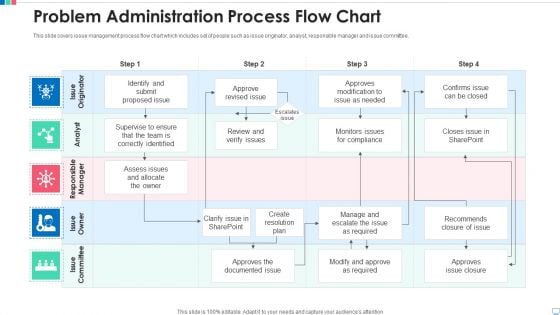
Problem Administration Process Flow Chart Pictures PDF
This slide covers issue management process flow chart which includes set of people such as issue originator, analyst, responsible manager and issue committee. Pitch your topic with ease and precision using this problem administration process flow chart pictures pdf. This layout presents information on problem administration process flow chart. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Secure Web Gateway Implementation Methodology Explicit Web Threat Protection System
This slide talks about the inline scenario of Secure Web Gateway implementation. The purpose of this slide is to demonstrate the concept of inline SWG deployment technique with the help of a diagram. This slide also outlines the benefits of this method. Find a pre-designed and impeccable Secure Web Gateway Implementation Methodology Explicit Web Threat Protection System. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide talks about the inline scenario of Secure Web Gateway implementation. The purpose of this slide is to demonstrate the concept of inline SWG deployment technique with the help of a diagram. This slide also outlines the benefits of this method.
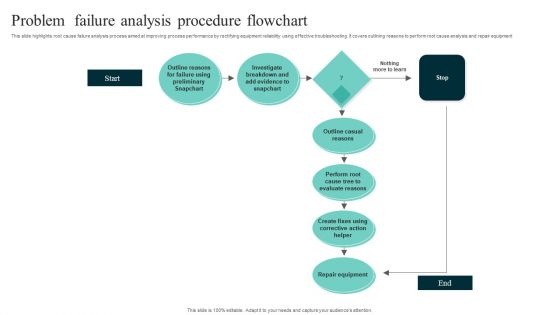
Problem Failure Analysis Procedure Flowchart Designs PDF
This slide highlights root cause failure analysis process aimed at improving process performance by rectifying equipment reliability using effective troubleshooting. It covers outlining reasons to perform root cause analysis and repair equipment. Showcasing this set of slides titled Problem Failure Analysis Procedure Flowchart Designs PDF. The topics addressed in these templates are Evaluate Reasons, Problem Failure Analysis, Procedure Flowchart. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
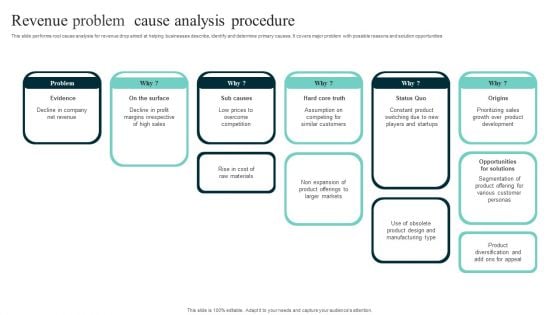
Revenue Problem Cause Analysis Procedure Background PDF
This slide performs root cause analysis for revenue drop aimed at helping businesses describe, identify and determine primary causes. It covers major problem with possible reasons and solution opportunities. Pitch your topic with ease and precision using this Revenue Problem Cause Analysis Procedure Background PDF. This layout presents information on Raw Materials, Product Offerings, Product Development. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
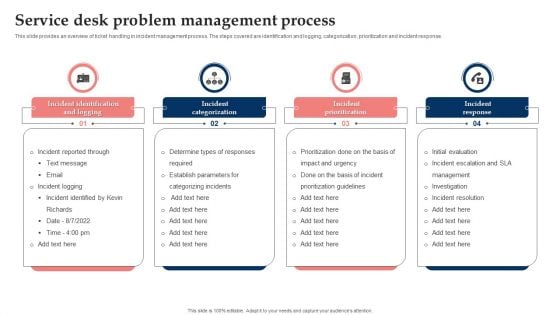
Service Desk Problem Management Process Elements PDF
This slide showcases service desk incident management process flowchart. It includes incident validation and approval, departmental reporting, assigning tasks to technicians, initial contact with customer, trouble shooting, incident resolution, etc. Showcasing this set of slides titled Service Desk Problem Management Process Elements PDF. The topics addressed in these templates are Departmental Reporting, Change Management, Interdepartmental Work Validation. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
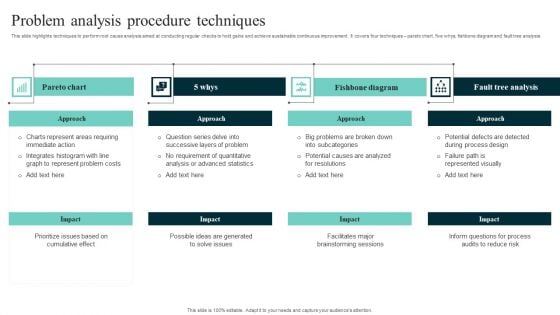
Problem Analysis Procedure Techniques Structure PDF
This slide highlights techniques to perform root cause analysis aimed at conducting regular checks to hold gains and achieve sustainable continuous improvement. It covers four techniques pareto chart, five whys, fishbone diagram and fault tree analysis. Showcasing this set of slides titled Problem Analysis Procedure Techniques Structure PDF. The topics addressed in these templates are Fault Tree Analysis, Fishbone Diagram, Process Design. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
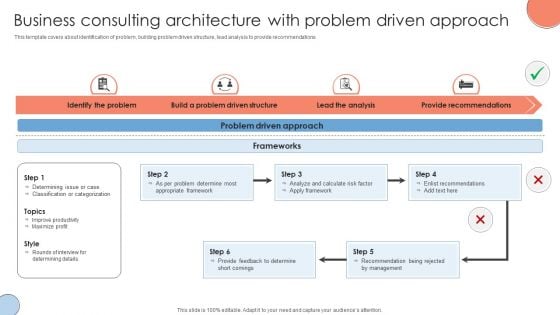
Business Consulting Architecture With Problem Driven Approach Summary PDF
This template covers about identification of problem, building problem driven structure, lead analysis to provide recommendations. Pitch your topic with ease and precision using this Business Consulting Architecture With Problem Driven Approach Summary PDF. This layout presents information on Identify Problem, Problem Driven Structure, Lead Analysis. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
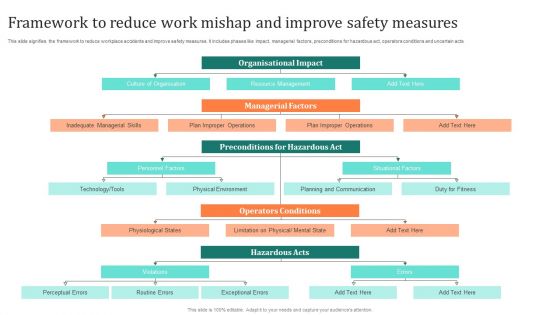
Framework To Reduce Work Mishap And Improve Safety Measures Pictures PDF
This slide signifies the framework to reduce workplace accidents and improve safety measures. It includes phases like impact, managerial factors, preconditions for hazardous act, operators conditions and uncertain acts Showcasing this set of slides titled Framework To Reduce Work Mishap And Improve Safety Measures Pictures PDF. The topics addressed in these templates are Organisational Impact, Culture Organisation, Resource Management. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
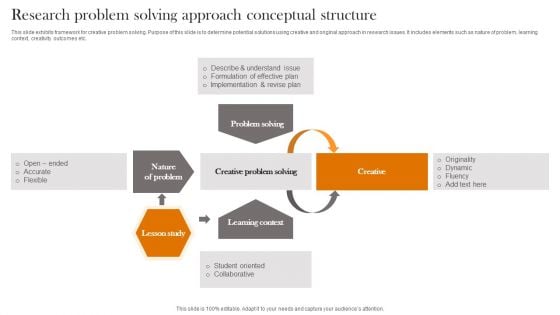
Research Problem Solving Approach Conceptual Structure Portrait PDF
This slide exhibits framework for creative problem solving. Purpose of this slide is to determine potential solutions using creative and original approach in research issues. It includes elements such as nature of problem, learning context, creativity outcomes etc. Showcasing this set of slides titled Research Problem Solving Approach Conceptual Structure Portrait PDF. The topics addressed in these templates are Problem Solving, Creative Problem Solving, Learning Context. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Problem And Recommendation 2 Absence Of Automated Logistics Icons PDF
This slide shows the problem that the company is facing related to absence of automated logistics. Also, some recommendations are provided to solve the problem. Deliver and pitch your topic in the best possible manner with this problem and recommendation 2 absence of automated logistics icons pdf. Use them to share invaluable insights on organizational, systems, warehouse, management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.


 Continue with Email
Continue with Email

 Home
Home


































