System Security
Covid19 And Its Impact On Defense Global Security Industry PPT Example IR SS V
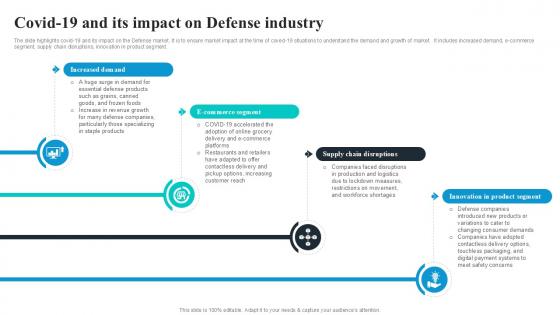
The slide highlights covid-19 and its impact on the Defense market. It is to ensure market impact at the time of coved-19 situations to understand the demand and growth of market. It includes increased demand, e-commerce segment, supply chain disruptions, innovation in product segment. Get a simple yet stunning designed Covid19 And Its Impact On Defense Global Security Industry PPT Example IR SS V. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Covid19 And Its Impact On Defense Global Security Industry PPT Example IR SS V can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. The slide highlights covid-19 and its impact on the Defense market. It is to ensure market impact at the time of coved-19 situations to understand the demand and growth of market. It includes increased demand, e-commerce segment, supply chain disruptions, innovation in product segment.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Way To Overcome Security Monitoring Themes PDF
This slide provides information about the way that the company and security monitoring manager must choose in order to solve the challenge problem related to Malware Attacks and other potential security monitoring challenges. The solution is to set up an advanced Cybersecurity Monitoring Plan in place with the help of a set series of steps mentioned in the slide. This is a continuous development evaluation plan eliminate cyber attacks way to overcome security monitoring themes pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like monitoring, systems, management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Security Business Marketing Plan Ppt PowerPoint Presentation Show Graphics Design Cpb
Presenting this set of slides with name security business marketing plan ppt powerpoint presentation show graphics design cpb. This is a three stage process. The stages in this process are security business marketing plan. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Five Steps Of Cyber Security With Icons Ppt PowerPoint Presentation Model Samples
Presenting this set of slides with name five steps of cyber security with icons ppt powerpoint presentation model samples. This is a five stage process. The stages in this process are security servery, solutions deployment, review and adjustment, monitoring and evaluation. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Crime Threat To Security Ppt PowerPoint Presentation Visual Aids Files
Presenting this set of slides with name cyber crime threat to security ppt powerpoint presentation visual aids files. This is a one stage process. The stage in this process is cyber crime threat to security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Infrastructure Growth Plan With Security And Capacity Ppt PowerPoint Presentation Portfolio Grid
Presenting this set of slides with name infrastructure growth plan with security and capacity ppt powerpoint presentation portfolio grid. This is a four stage process. The stages in this process are automation, capacity, security, flexibility. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Information Security Awareness Ppt PowerPoint Presentation Infographic Template Graphic Tips Cpb
Presenting this set of slides with name information security awareness ppt powerpoint presentation infographic template graphic tips cpb. This is a four stage process. The stages in this process are information security awareness. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Computer Bug And Cyber Security Vector Illustration Ppt PowerPoint Presentation Portfolio Skills PDF
Presenting this set of slides with name computer bug and cyber security vector illustration ppt powerpoint presentation portfolio skills pdf. This is a three stage process. The stages in this process are computer bug and cyber security vector illustration. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Security Risk Assessment Icon With Magnifying Glass Ppt PowerPoint Presentation File Templates PDF
Presenting this set of slides with name security risk assessment icon with magnifying glass ppt powerpoint presentation file templates pdf. This is a three stage process. The stages in this process are security risk assessment icon with magnifying glass. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Computer Security Shield With Bug Vector Icon Ppt PowerPoint Presentation File Professional PDF
Presenting this set of slides with name computer security shield with bug vector icon ppt powerpoint presentation file professional pdf. This is a three stage process. The stages in this process are computer security shield with bug vector icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Laptop Showing Security Shield Vector Icon Ppt PowerPoint Presentation Gallery Example Topics PDF
Presenting this set of slides with name laptop showing security shield vector icon ppt powerpoint presentation gallery example topics pdf. This is a three stage process. The stages in this process are laptop showing security shield vector icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Laptop With Security Shield Vector Icon Ppt PowerPoint Presentation File Microsoft PDF
Presenting this set of slides with name laptop with security shield vector icon ppt powerpoint presentation file microsoft pdf. This is a three stage process. The stages in this process are laptop with security shield vector icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Security Shield With Tick Mark Vector Icon Ppt PowerPoint Presentation File Templates PDF
Presenting this set of slides with name security shield with tick mark vector icon ppt powerpoint presentation file templates pdf. This is a three stage process. The stages in this process are security shield with tick mark vector icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Computer Security Incident Handling Determining Roles And Responsibilities For Risk Handling Mockup PDF
Presenting this set of slides with name computer security incident handling determining roles and responsibilities for risk handling mockup pdf. This is a four stage process. The stages in this process are chief risk officer, chief information security officer, senior management and executive, line management. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Threat Detection Online Security Computer Program Ppt PowerPoint Presentation Professional Icon PDF
Presenting this set of slides with name threat detection online security computer program ppt powerpoint presentation professional icon pdf. This is a three stage process. The stages in this process are threat detection online security computer program. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Security Icon Showing Insurance Of Personal Property Ppt PowerPoint Presentation Model Visuals PDF
Presenting this set of slides with name security icon showing insurance of personal property ppt powerpoint presentation model visuals pdf. This is a three stage process. The stages in this process are security icon showing insurance of personal property. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Firewall For Online Data Security Vector Icon Ppt PowerPoint Presentation Ideas Sample PDF
Presenting this set of slides with name firewall for online data security vector icon ppt powerpoint presentation ideas sample pdf. This is a three stage process. The stages in this process are firewall for online data security vector icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Threat Scanning For IT Security Ppt PowerPoint Presentation Gallery Smartart PDF
Presenting this set of slides with name threat scanning for it security ppt powerpoint presentation gallery smartart pdf. This is a three stage process. The stages in this process are threat scanning for it security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Cyber Security Implementation Framework Determining Roles And Responsibilities For Risk Handling Icons PDF
Presenting this set of slides with name cyber security implementation framework determining roles and responsibilities for risk handling icons pdf. This is a four stage process. The stages in this process are chief risk officer, chief information security officer, senior management and executive, line management. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security Implementation Framework Analyzing IT Department On NIST Cybersecurity Framework Topics PDF
Presenting this set of slides with name cyber security implementation framework analyzing it department on nist cybersecurity framework topics pdf. This is a one stage process. The stages in this process are asset management, governance, data security, threat intelligence, incident response planning, incident recovery. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Security Shield With Dollar Sign Vector Icon Ppt PowerPoint Presentation Gallery Graphics Design PDF
Presenting this set of slides with name security shield with dollar sign vector icon ppt powerpoint presentation gallery graphics design pdf. This is a three stage process. The stages in this process are security shield with dollar sign vector icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Economic Planning And Security Vector Icon Ppt PowerPoint Presentation File Smartart PDF
Presenting this set of slides with name economic planning and security vector icon ppt powerpoint presentation file smartart pdf. This is a three stage process. The stages in this process are economic planning and security vector icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Financial Support And Economic Security Vector Icon Ppt PowerPoint Presentation File Files PDF
Presenting this set of slides with name financial support and economic security vector icon ppt powerpoint presentation file files pdf. This is a three stage process. The stages in this process are financial support and economic security vector icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Monetary And Economic Security Vector Icon Ppt PowerPoint Presentation File Themes PDF
Presenting this set of slides with name monetary and economic security vector icon ppt powerpoint presentation file themes pdf. This is a one stage process. The stage in this process is monetary and economic security vector icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Responsible Icon With Security Shield Ppt PowerPoint Presentation File Background Image PDF
Presenting this set of slides with name responsible icon with security shield ppt powerpoint presentation file background image pdf. This is a four stage process. The stages in this process are responsible icon with security shield. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Possible Security Threats Vector Icon Ppt PowerPoint Presentation Gallery Portrait PDF
Presenting this set of slides with name possible security threats vector icon ppt powerpoint presentation gallery portrait pdf. This is a three stage process. The stages in this process are possible security threats vector icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Best Data Security Software Client Testimonials For Company Online Database Proposal Topics PDF
Presenting this set of slides with name best data security software client testimonials for company online database proposal topics pdf. This is a two stage process. The stages in this process are client testimonials, company, online database security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
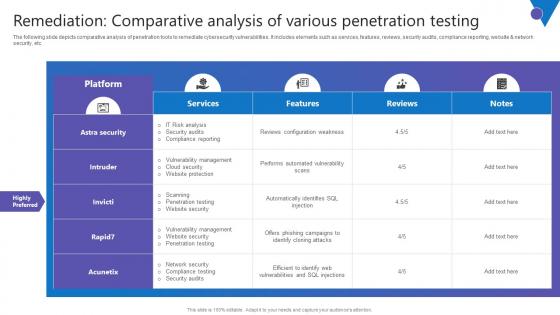
Remediation Comparative Analysis Comprehensive Guide To Blockchain Digital Security Portrait Pdf
The following slide depicts comparative analysis of penetration tools to remediate cybersecurity vulnerabilities. It includes elements such as services, features, reviews, security audits, compliance reporting, website and network security, etc. Take your projects to the next level with our ultimate collection of Remediation Comparative Analysis Comprehensive Guide To Blockchain Digital Security Portrait Pdf. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest The following slide depicts comparative analysis of penetration tools to remediate cybersecurity vulnerabilities. It includes elements such as services, features, reviews, security audits, compliance reporting, website and network security, etc.

Effective IT Risk Management Process Setting Scenario For Security Control Sample PDF
Following slide displays security control scenario setting. It includes scenario detail, category of security controls and controls description. Presenting effective it risk management process setting scenario for security control sample pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like technical controls, management controls, operational controls. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
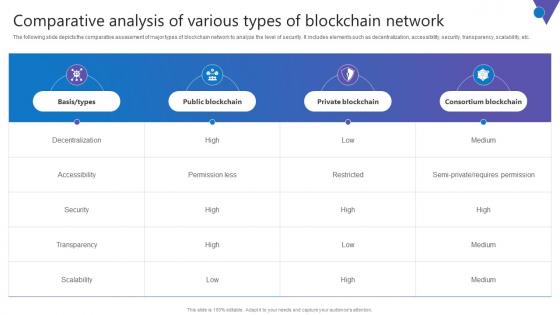
Comparative Analysis Of Various Comprehensive Guide To Blockchain Digital Security Slides Pdf
The following slide depicts the comparative assessment of major types of blockchain network to analyze the level of security. It includes elements such as decentralization, accessibility, security, transparency, scalability, etc. Find a pre designed and impeccable Comparative Analysis Of Various Comprehensive Guide To Blockchain Digital Security Slides Pdf. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. The following slide depicts the comparative assessment of major types of blockchain network to analyze the level of security. It includes elements such as decentralization, accessibility, security, transparency, scalability, etc.
Business Continuity Plan Information Security Ppt PowerPoint Presentation Gallery Layouts Cpb
Presenting this set of slides with name business continuity plan information security ppt powerpoint presentation gallery layouts cpb. This is an editable Powerpoint four stages graphic that deals with topics like business continuity plan information security to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
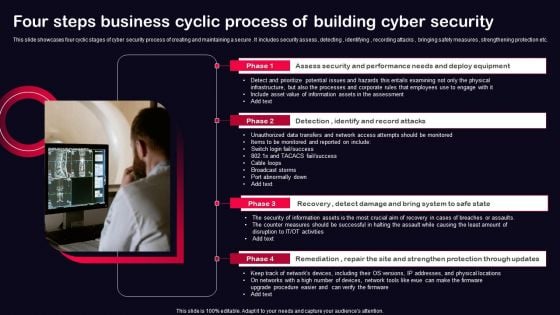
Four Steps Business Cyclic Process Of Building Cyber Security Ppt PowerPoint Presentation File Model PDF
This slide showcases four cyclic stages of cyber security process of creating and maintaining a secure . It includes security assess , detecting , identifying , recording attacks , bringing safety measures , strengthening protection etc. Presenting Four Steps Business Cyclic Process Of Building Cyber Security Ppt PowerPoint Presentation File Model PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Recovery, Remediation, Repair, Site And Strengthen, Protection Through Updates. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Risk Based Procedures To IT Security Gap Identification Current Approach Process Flaws And Cost Elements PDF
Purpose of this slide is to highlight the existing approach and process flaws along with the cost incur details. It also shows that company is treating security and privacy as after thoughts. Deliver an awe inspiring pitch with this creative Risk Based Procedures To IT Security Gap Identification Current Approach Process Flaws And Cost Elements PDF bundle. Topics like Cyberrisk Management, Security Organization, Technology Controls can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
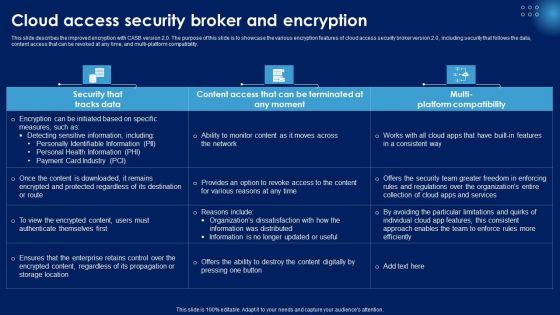
Cloud Access Security Broker And Encryption Ppt PowerPoint Presentation File Example PDF
This slide describes the improved encryption with CASB version 2.0. The purpose of this slide is to showcase the various encryption features of cloud access security broker version 2.0, including security that follows the data, content access that can be revoked at any time, and multi-platform compatibility. Presenting this PowerPoint presentation, titled Cloud Access Security Broker And Encryption Ppt PowerPoint Presentation File Example PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Cloud Access Security Broker And Encryption Ppt PowerPoint Presentation File Example PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Cloud Access Security Broker And Encryption Ppt PowerPoint Presentation File Example PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.

Requirements For Appropriate Cloud Security Model Ppt PowerPoint Presentation File Gallery PDF
This slide outlines the different prerequisites organizations should consider when choosing a cloud security model and provider. The purpose of this slide is to showcase the various requirements a cloud security provider should possess, including visibility and threat detection, continuous compliance, data encryption and so on. There are so many reasons you need a Requirements For Appropriate Cloud Security Model Ppt PowerPoint Presentation File Gallery PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Cloud Access Security Broker Pillar Overview Ppt PowerPoint Presentation File Infographics PDF
This slide represents the four major pillars of cloud access security broker. The purpose of this slide is to showcase the main pillars of implementing a cloud access security broker. The pillars include compliance, visibility, threat protection, and data security. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Cloud Access Security Broker Pillar Overview Ppt PowerPoint Presentation File Infographics PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Cloud Access Security Broker Pillar Overview Ppt PowerPoint Presentation File Infographics PDF today and make your presentation stand out from the rest.

Global Data Security Industry Report Strategies And Recommendations For Cybersecurity Industry IR SS V
The purpose of the slide is to provide valuable recommendations and effective strategies for cybersecurity industry players to succeed in a dynamic and competitive market. It covers strategies such as. The Global Data Security Industry Report Strategies And Recommendations For Cybersecurity Industry IR SS V is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. The purpose of the slide is to provide valuable recommendations and effective strategies for cybersecurity industry players to succeed in a dynamic and competitive market. It covers strategies such as.

Developing Firm Security Strategy Plan How Firm Handle Various Insider Threats At Workplace Elements PDF
This slide provides information regarding how firm will handle insider threats through employee training, IT security and HR coordination, etc. This is a developing firm security strategy plan how firm handle various insider threats at workplace elements pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like employee training, it security and hr coordination, develop threat hunting team, implement user behavioral analytics. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
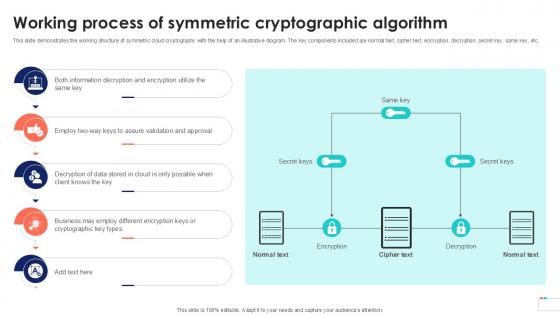
Working Process Of Symmetric Data Security In Cloud Computing Ppt Template
This slide demonstrates the working structure of symmetric cloud cryptography with the help of an illustrative diagram. The key components included are normal text, cipher text, encryption, decryption, secret key, same key, etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Working Process Of Symmetric Data Security In Cloud Computing Ppt Template was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Working Process Of Symmetric Data Security In Cloud Computing Ppt Template This slide demonstrates the working structure of symmetric cloud cryptography with the help of an illustrative diagram. The key components included are normal text, cipher text, encryption, decryption, secret key, same key, etc.

About Cloud Computing Overview And Services Data Security In Cloud Computing Ppt Template
This slide talks about the meaning and operations of cloud computing. The purpose of this slide is to outline the services provided by cloud computing. These are Infrastructure as a Service IaaS, Platform as a Service PaaS, etc. Create an editable About Cloud Computing Overview And Services Data Security In Cloud Computing Ppt Template that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. About Cloud Computing Overview And Services Data Security In Cloud Computing Ppt Template is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide talks about the meaning and operations of cloud computing. The purpose of this slide is to outline the services provided by cloud computing. These are Infrastructure as a Service IaaS, Platform as a Service PaaS, etc.

How To Configure Firewall As A Service Fwaas Network Security Diagrams Pdf
This slide talks about the steps of configuring Firewall-as-a-Service. The purpose of this slide is to illustrate how FWaaS packages can be installed and configured. The key steps explained in this slide are enable FWaaS and configure FWaaS. Welcome to our selection of the How To Configure Firewall As A Service Fwaas Network Security Diagrams Pdf. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today This slide talks about the steps of configuring Firewall-as-a-Service. The purpose of this slide is to illustrate how FWaaS packages can be installed and configured. The key steps explained in this slide are enable FWaaS and configure FWaaS.
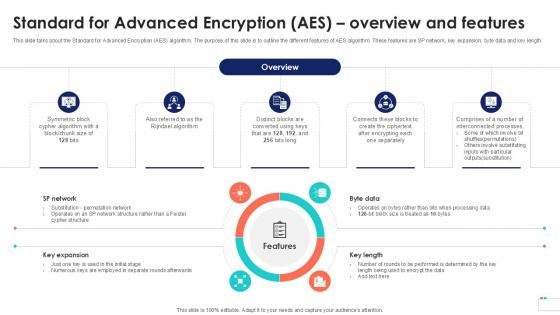
Standard For Advanced Encryption Data Security In Cloud Computing Ppt Sample
This slide talks about the Standard for Advanced Encryption AES algorithm. The purpose of this slide is to outline the different features of AES algorithm. These features are SP network, key expansion, byte data and key length. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Standard For Advanced Encryption Data Security In Cloud Computing Ppt Sample a try. Our experts have put a lot of knowledge and effort into creating this impeccable Standard For Advanced Encryption Data Security In Cloud Computing Ppt Sample. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide talks about the Standard for Advanced Encryption AES algorithm. The purpose of this slide is to outline the different features of AES algorithm. These features are SP network, key expansion, byte data and key length.
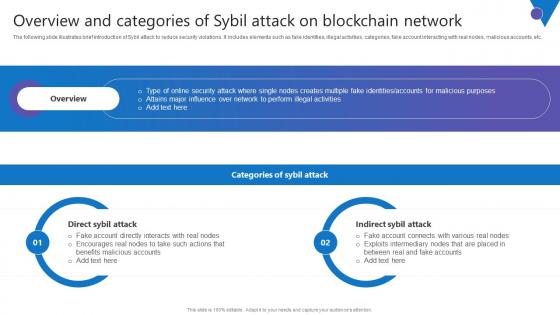
Overview Categories Sybil Comprehensive Guide To Blockchain Digital Security Elements Pdf
The following slide illustrates brief introduction of Sybil attack to reduce security violations. It includes elements such as fake identities, illegal activities, categories, fake account interacting with real nodes, malicious accounts, etc. Are you searching for a Overview Categories Sybil Comprehensive Guide To Blockchain Digital Security Elements Pdf that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Overview Categories Sybil Comprehensive Guide To Blockchain Digital Security Elements Pdf from Slidegeeks today. The following slide illustrates brief introduction of Sybil attack to reduce security violations. It includes elements such as fake identities, illegal activities, categories, fake account interacting with real nodes, malicious accounts, etc.

Information Security Cyber Safety Tips Protection Against Cyberattacks Ppt Slides Ideas PDF
Presenting information security cyber safety tips protection against cyberattacks ppt slides ideas pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like network, protect, systems, sources. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Data Protection Security Controls Ppt PowerPoint Presentation File Designs Cpb Pdf
Presenting this set of slides with name data protection security controls ppt powerpoint presentation file designs cpb pdf. This is an editable Powerpoint five stages graphic that deals with topics like data protection security controls to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Cloud Security Standards And Control Frameworks Ppt PowerPoint Presentation File Icon PDF
This slide provides an overview of the cloud security protocols and control frameworks. The purpose of this slide is to showcase the various information security standards and control frameworks, including ISO-27001, ISO-27017, ISO-27018, GDPR, SOC reporting, PCI DSS, and HIPAA. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Cloud Security Standards And Control Frameworks Ppt PowerPoint Presentation File Icon PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.
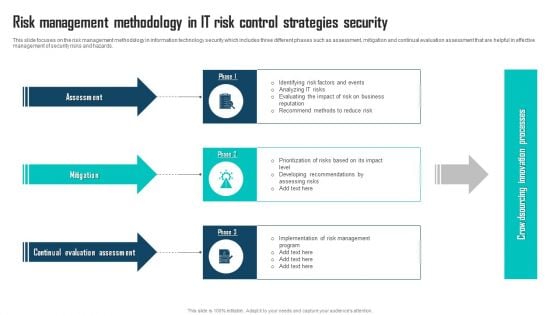
Risk Management Methodology In IT Risk Control Strategies Security Ppt Inspiration Background PDF
This slide focuses on the risk management methodology in information technology security which includes three different phases such as assessment, mitigation and continual evaluation assessment that are helpful in effective management of security risks and hazards. Showcasing this set of slides titled Risk Management Methodology In IT Risk Control Strategies Security Ppt Inspiration Background PDF. The topics addressed in these templates are Assessment, Mitigation, Continual Evaluation Assessment. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
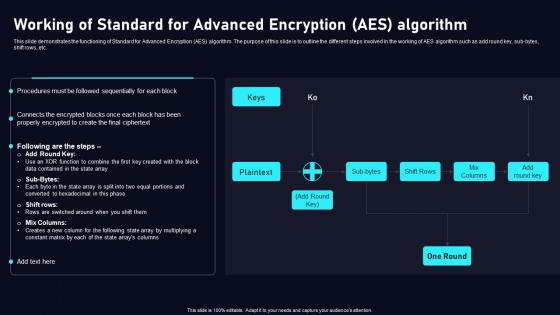
Working Of Standard For Advanced Cloud Data Security Using Cryptography Diagrams Pdf
This slide demonstrates the functioning of Standard for Advanced Encryption AES algorithm. The purpose of this slide is to outline the different steps involved in the working of AES algorithm such as add round key, sub bytes, shift rows, etc. Create an editableWorking Of Standard For Advanced Cloud Data Security Using Cryptography Diagrams Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save timeWorking Of Standard For Advanced Cloud Data Security Using Cryptography Diagrams Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide demonstrates the functioning of Standard for Advanced Encryption AES algorithm. The purpose of this slide is to outline the different steps involved in the working of AES algorithm such as add round key, sub bytes, shift rows, etc.
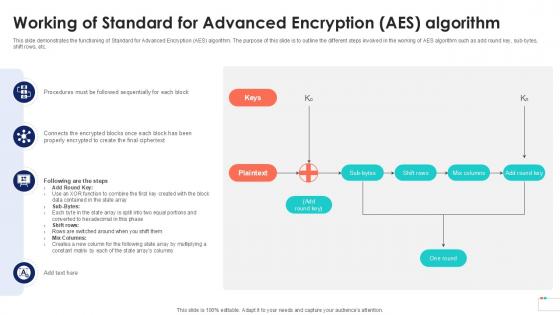
Working Of Standard For Advanced Encryption Data Security In Cloud Computing Ppt Presentation
This slide demonstrates the functioning of Standard for Advanced Encryption AES algorithm. The purpose of this slide is to outline the different steps involved in the working of AES algorithm such as add round key, sub-bytes, shift rows, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Working Of Standard For Advanced Encryption Data Security In Cloud Computing Ppt Presentation template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Working Of Standard For Advanced Encryption Data Security In Cloud Computing Ppt Presentation that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide demonstrates the functioning of Standard for Advanced Encryption AES algorithm. The purpose of this slide is to outline the different steps involved in the working of AES algorithm such as add round key, sub-bytes, shift rows, etc.
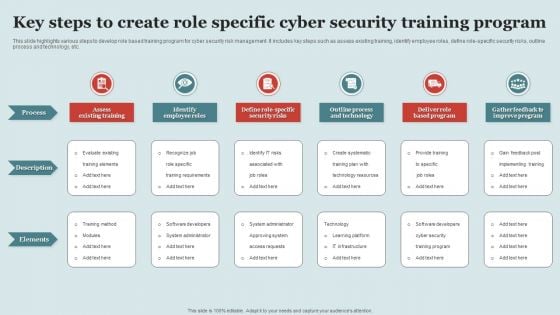
Key Steps To Create Role Specific Cyber Security Training Program Structure PDF
This slide highlights various steps to develop role based training program for cyber security risk management. It includes key steps such as assess existing training, identify employee roles, define role-specific security risks, outline process and technology, etc. Persuade your audience using this Key Steps To Create Role Specific Cyber Security Training Program Structure PDF This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Process, Description, Elements. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Information Security Controls Framework Ppt PowerPoint Presentation Infographic Template Gallery Cpb
Presenting this set of slides with name information security controls framework ppt powerpoint presentation infographic template gallery cpb. This is an editable Powerpoint eleven stages graphic that deals with topics like information security controls framework to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Way To Overcome Security Monitoring Challenges Setting Up An Advanced Cybersecurity Monitoring Plan Professional PDF
Presenting way to overcome security monitoring challenges setting up an advanced cybersecurity monitoring plan professional pdf to provide visual cues and insights. Share and navigate important information on nine stages that need your due attention. This template can be used to pitch topics like monitoring all systems, monitoring network traffic, monitoring user activity. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
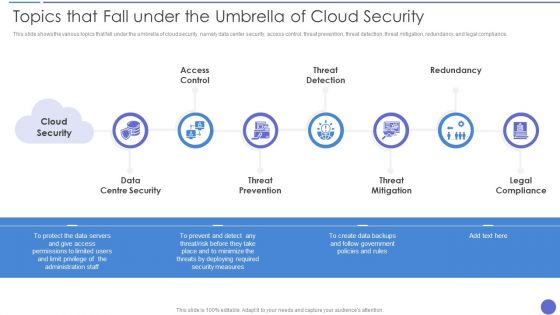
Topics That Fall Under The Umbrella Of Cloud Security Formats PDF
This slide shows the various topics that fall under the umbrella of cloud security, namely data center security, access control, threat prevention, threat detection, threat mitigation, redundancy, and legal compliance. This is a Topics That Fall Under The Umbrella Of Cloud Security Formats PDF template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Threat Prevention, Threat Mitigation, Legal Compliance. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
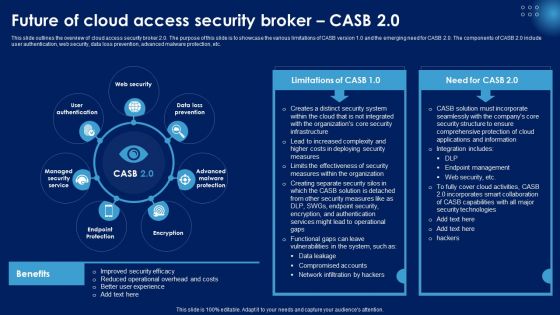
Future Of Cloud Access Security Broker CASB 2 0 Ppt PowerPoint Presentation File Outline PDF
This slide outlines the overview of cloud access security broker 2.0. The purpose of this slide is to showcase the various limitations of CASB version 1.0 and the emerging need for CASB 2.0. The components of CASB 2.0 include user authentication, web security, data loss prevention, advanced malware protection, etc. Explore a selection of the finest Future Of Cloud Access Security Broker CASB 2 0 Ppt PowerPoint Presentation File Outline PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Future Of Cloud Access Security Broker CASB 2 0 Ppt PowerPoint Presentation File Outline PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
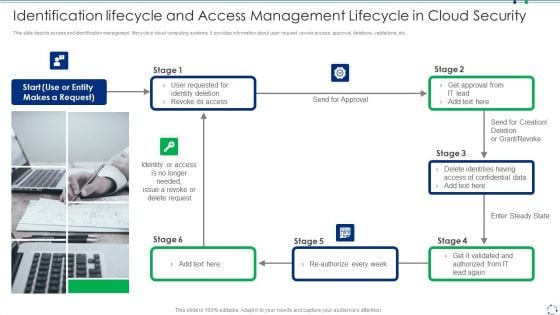
Identification Lifecycle And Access Management Lifecycle In Cloud Security Guidelines PDF
This slide depicts access and identification management lifecycle in cloud computing systems. It provides information about user request, revoke access, approval, deletions, validations, etc.Presenting identification lifecycle and access management lifecycle in cloud security guidelines pdf to dispense important information. This template comprises one stage. It also presents valuable insights into the topics including identity deletion, revoke its access, identity or access This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
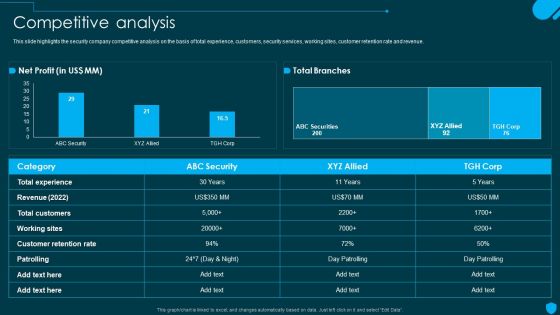
Security And Human Resource Services Business Profile Competitive Analysis Elements PDF
This slide highlights the security company competitive analysis on the basis of total experience, customers, security services, working sites, customer retention rate and revenue. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Security And Human Resource Services Business Profile Competitive Analysis Elements PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
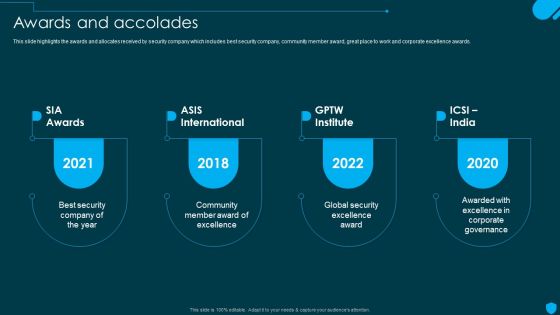
Security And Human Resource Services Business Profile Awards And Accolades Elements PDF
This slide highlights the awards and allocates received by security company which includes best security company, community member award, great place to work and corporate excellence awards. Boost your pitch with our creative Security And Human Resource Services Business Profile Awards And Accolades Elements PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you dont have to invest time in any additional work. Just grab the template now and use them.

Challenge And Solutions 2 Cloud Threats And Security Ppt Outline Design Inspiration PDF
This slide shows the problem that the company is facing related to cloud threats and security issues due to improper encryption and password protection. Additionally, the slide covers the key majors solutions which the company needs to follow. Deliver an awe inspiring pitch with this creative challenge and solutions 2 cloud threats and security ppt outline design inspiration pdf bundle. Topics like implement data encryption techniques to eliminate risk of infiltration, security and compliance risks are major considerations for the company, professional business can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
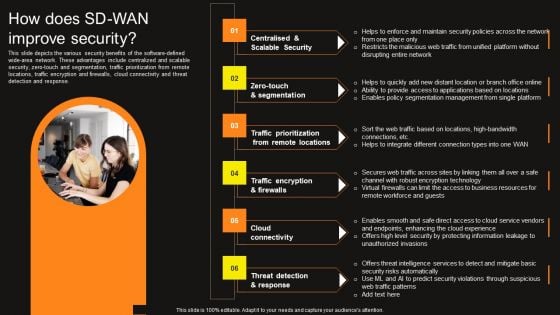
Virtual WAN Architecture How Does SD WAN Improve Security Professional PDF
This slide depicts the various security benefits of the software-defined wide-area network. These advantages include centralized and scalable security, zero-touch and segmentation, traffic prioritization from remote locations, traffic encryption and firewalls, cloud connectivity and threat detection and response. Find a pre-designed and impeccable Virtual WAN Architecture How Does SD WAN Improve Security Professional PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Mobile Device Management Ensuring Checklist For Mobile Security Deployment Elements PDF
This slide provides information regarding mobile device compliance and policy enforcement with automated device setup, dynamic workflows and policies, etc. This slide provides information regarding mobile device security deployment checklist in terms of device security, protection against malicious codes. There are so many reasons you need a Mobile Device Management Ensuring Checklist For Mobile Security Deployment Elements PDF. The first reason is you cant spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.


 Continue with Email
Continue with Email

 Home
Home


































