System Security
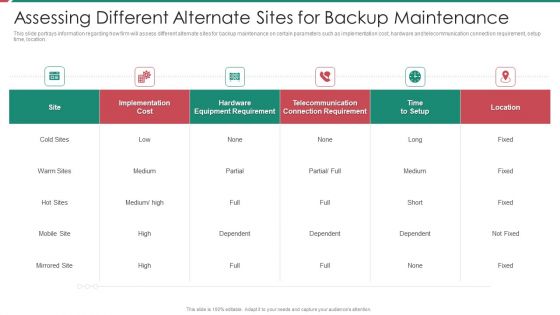
Security And Process Integration Assessing Different Alternate Sites For Backup Maintenance Formats PDF
This slide portrays information regarding how firm will assess different alternate sites for backup maintenance on certain parameters such as implementation cost, hardware and telecommunication connection requirement, setup time, location. Deliver and pitch your topic in the best possible manner with this security and process integration assessing different alternate sites for backup maintenance formats pdf. Use them to share invaluable insights on implementation, cost, location, telecommunication and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
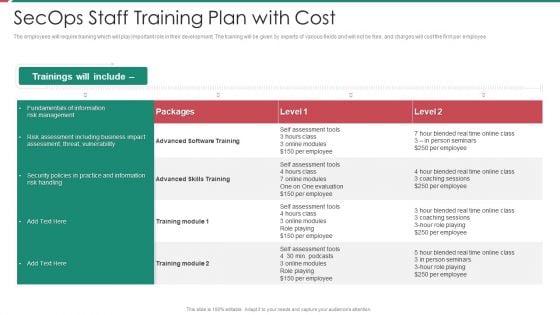
Security And Process Integration Secops Staff Training Plan With Cost Background PDF
The employees will require training which will play important role in their development. The training will be given by experts of various fields and will not be free, and charges will cost the firm per employee. Deliver an awe inspiring pitch with this creative security and process integration secops staff training plan with cost background pdf bundle. Topics like management, vulnerability, business, training can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
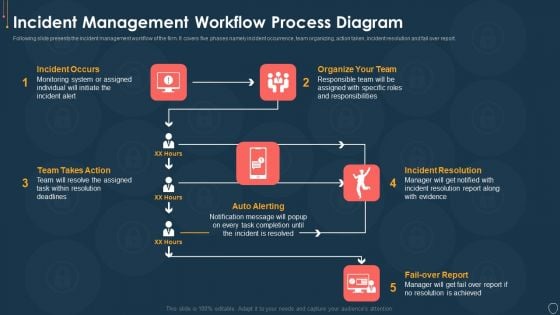
Cyber Security Risk Management Plan Incident Management Workflow Process Diagram Infographics PDF
Following slide presents the incident management workflow of the firm. It covers five phases namely incident occurrence, team organizing, action taken, incident resolution and fail over report. Presenting cyber security risk management plan incident management workflow process diagram infographics pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like fail over report, incident resolution, organize your team, incident occurs, team takes action. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
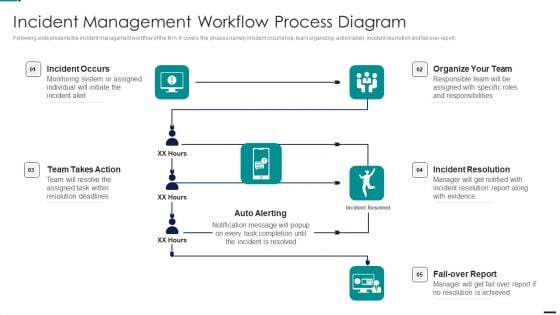
Risk Management Model For Data Security Incident Management Workflow Process Diagram Topics PDF
Following slide presents the incident management workflow of the firm. It covers five phases namely incident occurrence, team organizing, action taken, incident resolution and fail over report. Presenting Risk Management Model For Data Security Incident Management Workflow Process Diagram Topics PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Incident Occurs, Organize Team, Incident Resolution, Fail Over Report, Auto Alerting, Team Takes Action. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Four Steps Of Cyber Security Data Breach Threats Process Ppt Icon Format Ideas PDF
This slide covers steps utilised to breach data. It includes stages such as probing, performing initial attack, expansion of attacks and data lifting. Presenting Four Steps Of Cyber Security Data Breach Threats Process Ppt Icon Format Ideas PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Probe, Initial Attack, Expanded Attack, Data Lift. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
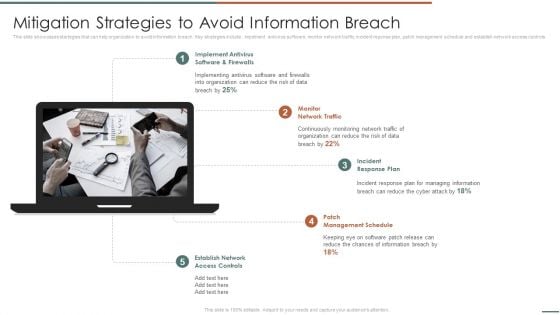
Information Security Risk Evaluation Mitigation Strategies To Avoid Information Breach Demonstration PDF
This slide showcases startegies that can help organization to avoid information breach. Key strategies include impelment antivirus software, monitor network traffic, incident reponse plan, patch management schedule and establish network access controls .This is a Information Security Risk Evaluation Mitigation Strategies To Avoid Information Breach Demonstration PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Management Schedule, Incident Response, Implement Antivirus . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
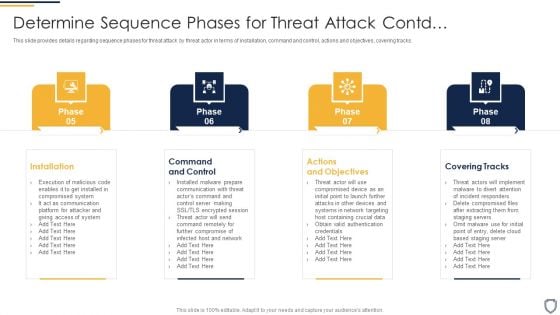
Corporate Security And Risk Management Determine Sequence Phases For Threat Attack Contd Mockup PDF
This slide provides details regarding sequence phases for threat attack by threat actor in terms of installation, command and control, actions and objectives, covering tracks. This is a corporate security and risk management determine sequence phases for threat attack contd mockup pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like installation, command and control, actions and objectives, covering tracks. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
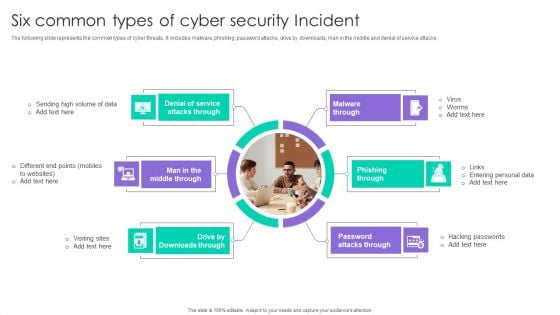
Six Common Types Of Cyber Security Incident Ppt Slides Graphics Tutorials PDF
The following slide represents the common types of cyber threats. It includes malware, phishing, password attacks, drive by downloads, man in the middle and denial of service attacks. Persuade your audience using this Six Common Types Of Cyber Security Incident Ppt Slides Graphics Tutorials PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Malware Through, Phishing Through, Password Attacks Through. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
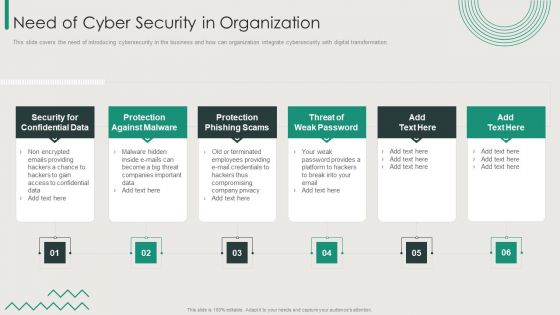
Organization Transition Need Of Cyber Security In Organization Ppt PowerPoint Presentation Gallery Themes PDF
This slide covers the need of introducing cybersecurity in the business and how can organization integrate cybersecurity with digital transformation. Presenting Organization Transition Need Of Cyber Security In Organization Ppt PowerPoint Presentation Gallery Themes PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Protection Against Malware, Protection Phishing Scams, Threat Weak Password. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
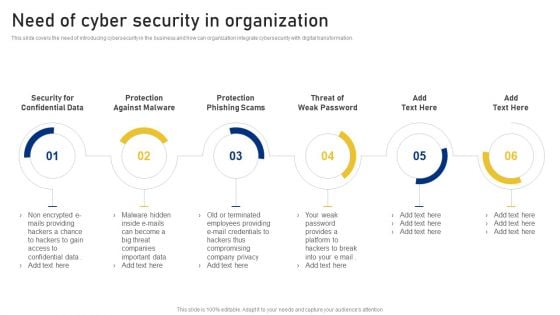
Reshaping Business In Digital Need Of Cyber Security In Organization Sample PDF
This slide covers the need of introducing cybersecurity in the business and how can organization integrate cybersecurity with digital transformation. This is a Reshaping Business In Digital Need Of Cyber Security In Organization Sample PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Protection Against Malware, Protection Phishing Scams, Threat Weak Password . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Organizing Security Awareness Various Techniques To Successfully Prevent Business Email Diagrams PDF
The purpose of this slide is to outline different techniques which can be used to protect organization from business email compromise attack. The techniques covered in the slide are sender policy framework SPF, using strong password policy and process for wire transfers. Find a pre-designed and impeccable Organizing Security Awareness Various Techniques To Successfully Prevent Business Email Diagrams PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
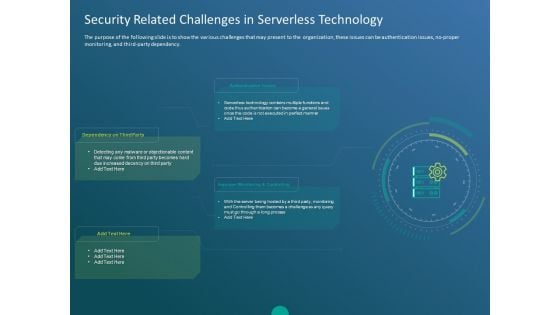
Functioning Of Serverless Computing Security Related Challenges In Serverless Technology Graphics PDF
The purpose of the following slide is to show the various challenges that may present to the organization, these issues can be authentication issues, no-proper monitoring, and third-party dependency. This is a functioning of serverless computing security related challenges in serverless technology graphics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like authentication issues, dependency third party, improper monitoring and controlling. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Online Payment Service Payment Security And Fraud Management Solutions End Structure PDF
From prevention to detection and resolution, Data Fraud Management solutions allow you to leverage proven technologies to create customized strategies that help limit losses while maintaining a high level of customer satisfaction. This is a online payment service payment security and fraud management solutions end structure pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like market basket analysis, optimization, geolocation analysis, customer velocity. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
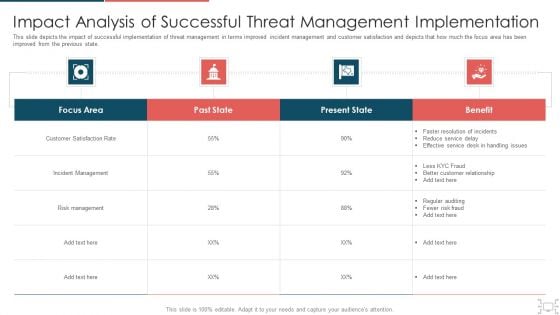
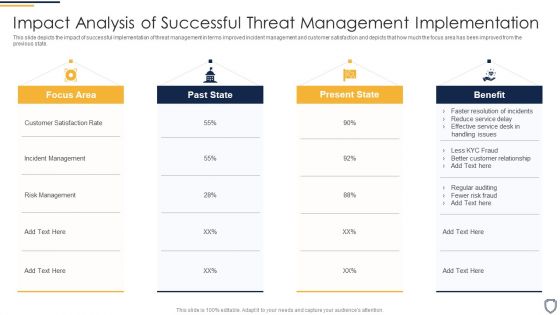
Cyber Security Administration In Organization Impact Analysis Of Successful Threat Management Ideas PDF
This slide depicts the impact of successful implementation of threat management in terms improved incident management and customer satisfaction and depicts that how much the focus area has been improved from the previous state. Deliver and pitch your topic in the best possible manner with this cyber security administration in organization impact analysis of successful threat management ideas pdf. Use them to share invaluable insights on handling, service, resolution, customer, relationship and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
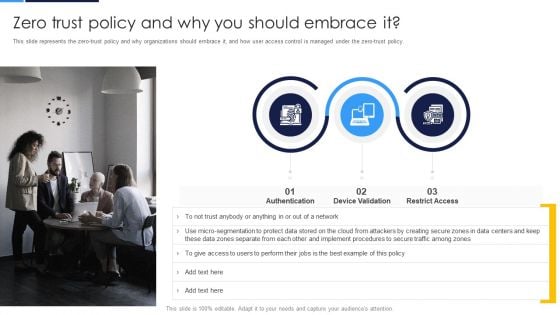
Cloud Security Assessment Zero Trust Policy And Why You Should Embrace It Designs PDF
This slide represents the zero trust policy and why organizations should embrace it, and how user access control is managed under the zero-trust policy.This is a Cloud Security Assessment Zero Trust Policy And Why You Should Embrace It Designs PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Best Example, Authentication, Implement Procedures. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
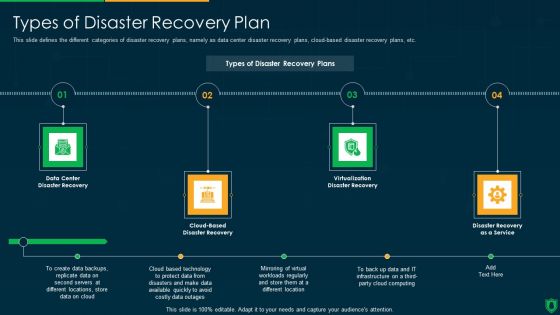
Info Security Types Of Disaster Recovery Plan Ppt PowerPoint Presentation File Clipart PDF
This slide defines the different categories of disaster recovery plans, namely as data center disaster recovery plans, cloud-based disaster recovery plans, etc. This is a info security types of disaster recovery plan ppt powerpoint presentation file clipart pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like data center, disaster recovery, cloud based, disaster recovery, virtualization disaster recovery, disaster recovery as a service. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
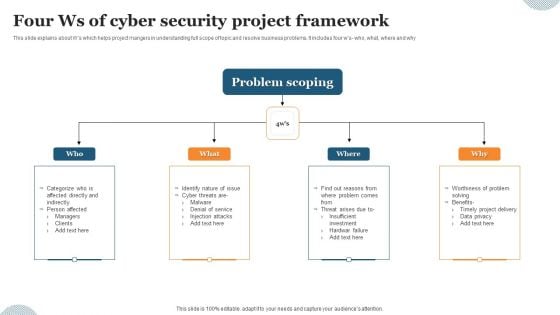
Four Ws Of Cyber Security Project Framework Ppt Pictures Graphic Images PDF
This slide explains about Ws which helps project mangers in understanding full scope of topic and resolve business problems. It includes four ws- who, what, where and why. Presenting Four Ws Of Cyber Security Project Framework Ppt Pictures Graphic Images PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Problem Scoping, Denial Service, Injection Attacks. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
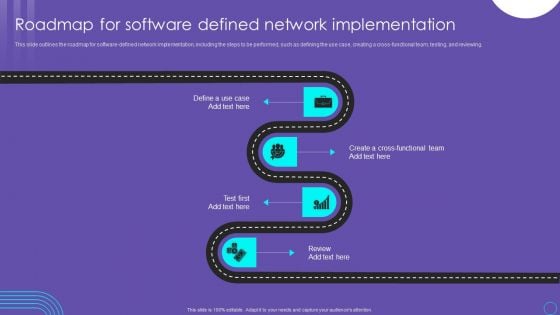
SDN Security Architecture Roadmap For Software Defined Network Implementation Slides PDF
This slide outlines the roadmap for software defined network implementation, including the steps to be performed, such as defining the use case, creating a cross functional team, testing, and reviewing. Find a pre designed and impeccable SDN Security Architecture Roadmap For Software Defined Network Implementation Slides PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
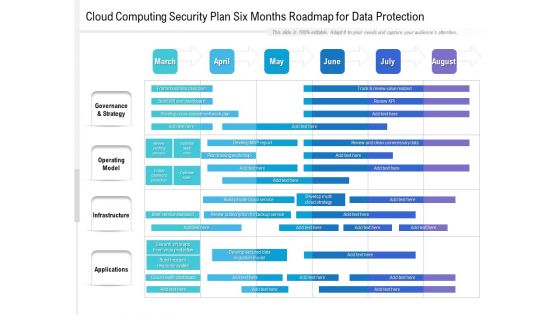
Cloud Computing Security Plan Six Months Roadmap For Data Protection Themes
Presenting our jaw dropping cloud computing security plan six months roadmap for data protection themes. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.
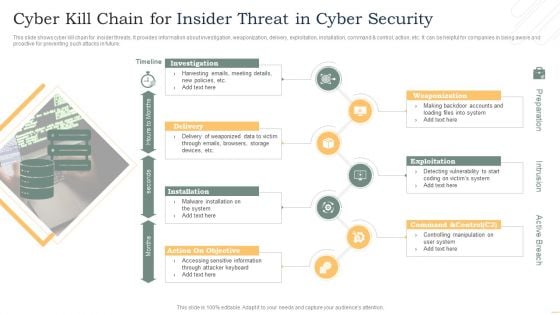
Cyber Kill Chain For Insider Threat In Cyber Security Slides PDF
This slide shows cyber kill chain for insider threats. It provides information about investigation, weaponization, delivery, exploitation, installation, command and control, action, etc. It can be helpful for companies in being aware and proactive for preventing such attacks in future. Presenting Cyber Kill Chain For Insider Threat In Cyber Security Slides PDF to dispense important information. This template comprises seven stages. It also presents valuable insights into the topics including Investigation, Delivery, Installation, Exploitation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Organizational Network Security Awareness Staff Learning Ppt PowerPoint Presentation Complete Deck With Slides
Pitch yourself both in-house and outside by utilizing this complete deck. This organizational network security awareness staff learning ppt powerpoint presentation complete deck with slides focuses on key fundamentals of the topic, displayed using different slides. With a total of fifty four slides, this template is the best tool you can use to persuade your audience. It will not only help you create great presentations but also induce strategic thinking because of its well-researched content and graphics. You can easily personalize any of the elements to suit your unique business setting. Additionally, it can be saved in PNG, JPG, and PDF formats to save your time and resources.
Corporate Security And Risk Management Impact Analysis Of Successful Threat Sample PDF
This slide depicts the impact of successful implementation of threat management in terms improved incident management and customer satisfaction and depicts that how much the focus area has been improved from the Deliver and pitch your topic in the best possible manner with this corporate security and risk management impact analysis of successful threat sample pdf. Use them to share invaluable insights on focus area, past state, present state, benefit and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Info Security Prepare A Disaster Recovery Plan Ppt PowerPoint Presentation File Portfolio PDF
This slide depicts what factors will be considered while preparing a recovery planning of an organization to come back to business quickly and effectively. This is a info security prepare a disaster recovery plan ppt powerpoint presentation file portfolio pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like disaster recovery, risk assessment report, identify importance assets, disaster recovery. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
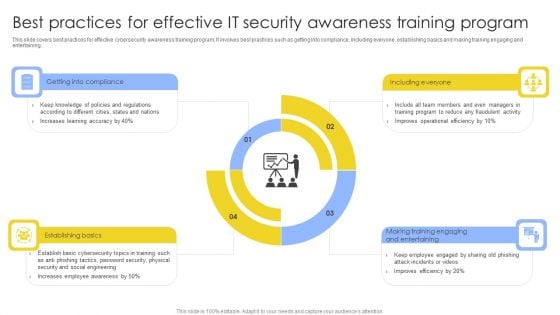
Best Practices For Effective IT Security Awareness Training Program Background PDF
This slide covers best practices for effective cybersecurity awareness training program. It involves best practices such as getting into compliance, including everyone, establishing basics and making training engaging and entertaining. Presenting Best Practices For Effective IT Security Awareness Training Program Background PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Getting Into Compliance, Including Everyone, Establishing Basics. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
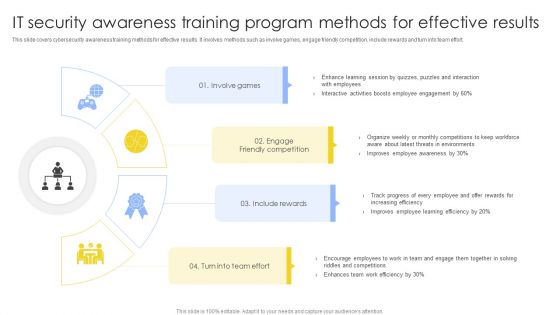
IT Security Awareness Training Program Methods For Effective Results Summary PDF
This slide covers cybersecurity awareness training methods for effective results. It involves methods such as involve games, engage friendly competition, include rewards and turn into team effort. Presenting IT Security Awareness Training Program Methods For Effective Results Summary PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Involve Games, Engage Friendly Competition, Include Rewards. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
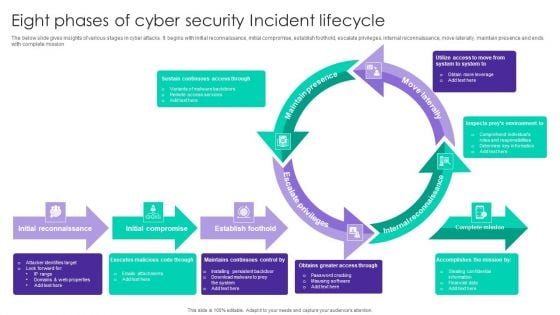
Eight Phases Of Cyber Security Incident Lifecycle Ppt Summary Portrait PDF
The below slide gives insights of various stages in cyber attacks. It begins with initial reconnaissance, initial compromise, establish foothold, escalate privileges, internal reconnaissance, move laterally, maintain presence and ends with complete mission. Presenting Eight Phases Of Cyber Security Incident Lifecycle Ppt Summary Portrait PDF to dispense important information. This template comprises eight stages. It also presents valuable insights into the topics including Maintain Presence, Move Laterally, Internal Reconnaissance. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Security Officer Service Company Profile Ppt PowerPoint Presentation Complete Deck With Slides
Pitch yourself both in house and outside by utilizing this complete deck. This Security Officer Service Company Profile Ppt PowerPoint Presentation Complete Deck With Slides focuses on key fundamentals of the topic, displayed using different slides. With a total of fourty four slides, this template is the best tool you can use to persuade your audience. It will not only help you create great presentations but also induce strategic thinking because of its well researched content and graphics. You can easily personalize any of the elements to suit your unique business setting. Additionally, it can be saved in PNG, JPG, and PDF formats to save your time and resources.

Data Safety Initiatives For Effective IT Security Threats Administration Ppt PowerPoint Presentation Complete Deck With Slides
Pitch yourself both in house and outside by utilizing this complete deck. This data safety initiatives for effective it security threats administration ppt powerpoint presentation complete deck with slides focuses on key fundamentals of the topic, displayed using different slides. With a total of fifty six slides, this template is the best tool you can use to persuade your audience. It will not only help you create great presentations but also induce strategic thinking because of its well researched content and graphics. You can easily personalize any of the elements to suit your unique business setting. Additionally, it can be saved in PNG, JPG, and PDF formats to save your time and resources.

Safety Breach Response Playbook Checklist For Work From Home Data Security Slides PDF
The Safety Breach Response Playbook Checklist For Work From Home Data Security Slides PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
Structured Networking Process Diagram 7 Stages Ppt Security Business Plan PowerPoint Slides
We present our structured networking process diagram 7 stages ppt security business plan PowerPoint Slides.Download our Business PowerPoint Templates because It will get your audience in sync. Use our Network Diagrams PowerPoint Templates because Our PowerPoint Templates and Slides will let you meet your Deadlines. Present our Shapes PowerPoint Templates because You can Hit a home run with our PowerPoint Templates and Slides. See your ideas sail into the minds of your audience. Download and present our Circle Charts PowerPoint Templates because Your ideas provide food for thought. Our PowerPoint Templates and Slides will help you create a dish to tickle the most discerning palate. Download our Curves and Lines PowerPoint Templates because Our PowerPoint Templates and Slides are topically designed to provide an attractive backdrop to any subject.Use these PowerPoint slides for presentations relating to art, business, button, chart, clip, communication, design, diagram, element, graph, graphic, green, icon, illustration, isolated, network, process, round, set, shape, shiny, symbol, teamwork, vector, web. The prominent colors used in the PowerPoint template are Gray, White, Black. Aim for the skies with our Structured Networking Process Diagram 7 Stages Ppt Security Business Plan PowerPoint Slides. You will come out on top.
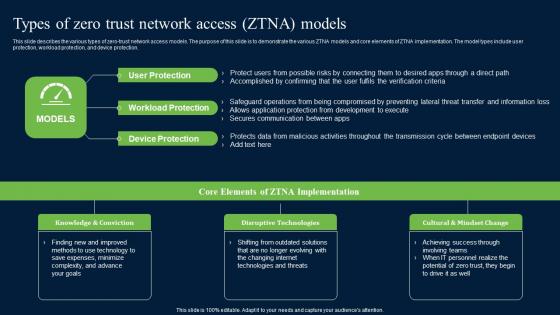
Types Of Zero Trust Network Access ZTNA Models Zero Trust Network Security Clipart Pdf
This slide describes the various types of zero-trust network access models. The purpose of this slide is to demonstrate the various ZTNA models and core elements of ZTNA implementation. The model types include user protection, workload protection, and device protection. Boost your pitch with our creative Types Of Zero Trust Network Access ZTNA Models Zero Trust Network Security Clipart Pdf. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide describes the various types of zero-trust network access models. The purpose of this slide is to demonstrate the various ZTNA models and core elements of ZTNA implementation. The model types include user protection, workload protection, and device protection.
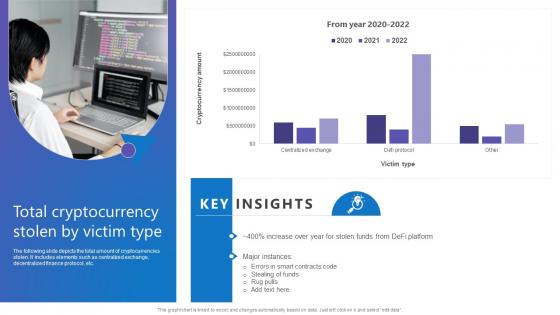
Total Cryptocurrency Stolen Comprehensive Guide To Blockchain Digital Security Information Pdf
The following slide depicts the total amount of cryptocurrencies stolen. It includes elements such as centralized exchange, decentralized finance protocol, etc. There are so many reasons you need a Total Cryptocurrency Stolen Comprehensive Guide To Blockchain Digital Security Information Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. The following slide depicts the total amount of cryptocurrencies stolen. It includes elements such as centralized exchange, decentralized finance protocol, etc.
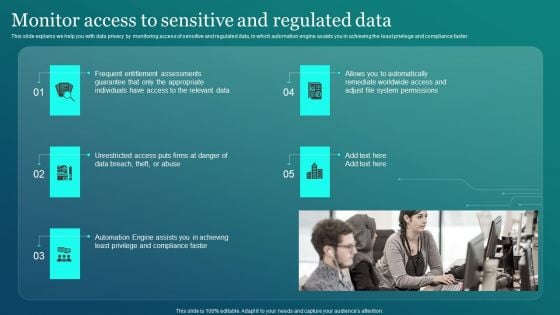
Information Security Monitor Access To Sensitive And Regulated Data Structure PDF
This slide explains we help you with data privacy by monitoring access of sensitive and regulated data, in which automation engine assists you in achieving the least privilege and compliance faster. The Information Security Monitor Access To Sensitive And Regulated Data Structure PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
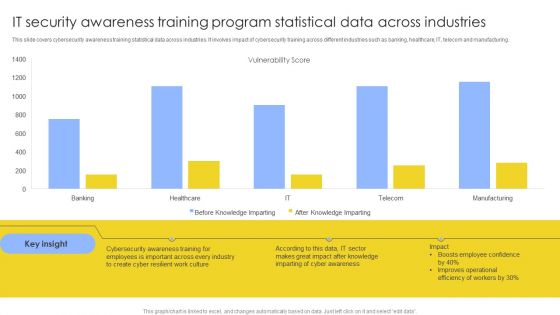
IT Security Awareness Training Program Statistical Data Across Industries Mockup PDF
This slide covers cybersecurity awareness training statistical data across industries. It involves impact of cybersecurity training across different industries such as banking, healthcare, IT, telecom and manufacturing. Showcasing this set of slides titled IT Security Awareness Training Program Statistical Data Across Industries Mockup PDF. The topics addressed in these templates are Vulnerability Score, Cyber Awareness, Improves Operational. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Organizing Security Awareness Training To Minimize Downtime Ppt PowerPoint Presentation Complete Deck With Slides
Use this Organizing Security Awareness Training To Minimize Downtime Ppt PowerPoint Presentation Complete Deck With Slides to ensure the business world gets to know you as a presentation expert with tremendous recall value. With its focus on providing the worlds best designs to highlight business ideas that have the potential to change the world, this PPT Template is sure to win you clients. The complete deck in seventy eight slides is a compendium of information, structured in a manner that provides the best framework for a presentation. Use this completely editable and customizable presentation to make an impact and improve your order book. Download now.

Business Mobile Device Security Management And Mitigation Ppt PowerPoint Presentation Complete Deck With Slides
If you are looking for Business Mobile Device Security Management And Mitigation Ppt PowerPoint Presentation Complete Deck With Slides to help improve your customer connect, this is the perfect option. Download this PowerPoint Template to make an effective observation on business strategies and policies. You can analyze techniques that prove beneficial or otherwise. You can easily monitor and compare other businesses on how they interact with customers and the industry benchmarks surrounding this with each of the sixty three slides of the complete deck a lesson the same. The 100 precent customizable feature of the presentation ensures that this has to be in your collection, at any cost. Download now.

Developing Information Technology Security Awareness Training Program For Employees Ppt PowerPoint Presentation Complete Deck With Slides
Use this Developing Information Technology Security Awareness Training Program For Employees Ppt PowerPoint Presentation Complete Deck With Slides to ensure the business world gets to know you as a presentation expert with tremendous recall value. With its focus on providing the worlds best designs to highlight business ideas that have the potential to change the world, this PPT Template is sure to win you clients. The complete deck in seventy one slides is a compendium of information, structured in a manner that provides the best framework for a presentation. Use this completely editable and customizable presentation to make an impact and improve your order book. Download now.

Developing IT Security Strategy To Prevent Data Assets Ppt PowerPoint Presentation Complete Deck With Slides
Use this Developing IT Security Strategy To Prevent Data Assets Ppt PowerPoint Presentation Complete Deck With Slides to ensure the business world gets to know you as a presentation expert with tremendous recall value. With its focus on providing the worlds best designs to highlight business ideas that have the potential to change the world, this PPT Template is sure to win you clients. The complete deck in seventy one slides is a compendium of information, structured in a manner that provides the best framework for a presentation. Use this completely editable and customizable presentation to make an impact and improve your order book. Download now.

Increasing Information Security Awareness In Company Using Various Techniques Complete Deck
Use this Increasing Information Security Awareness In Company Using Various Techniques Complete Deck to ensure the business world gets to know you as a presentation expert with tremendous recall value. With its focus on providing the worlds best designs to highlight business ideas that have the potential to change the world, this PPT Template is sure to win you clients. The complete deck in fifteen slides is a compendium of information, structured in a manner that provides the best framework for a presentation. Use this completely editable and customizable presentation to make an impact and improve your order book. Download now.
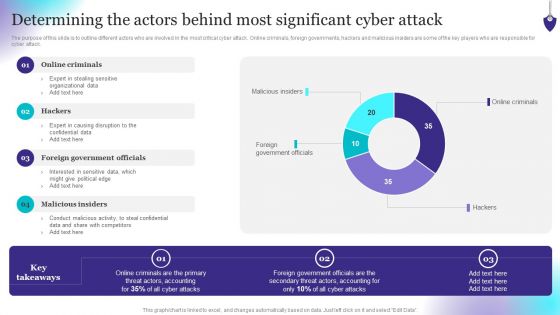
Organizing Security Awareness Determining The Actors Behind Most Significant Cyber Mockup PDF
The purpose of this slide is to outline different actors who are involved in the most critical cyber attack. Online criminals, foreign governments, hackers and malicious insiders are some of the key players who are responsible for cyber attack. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Organizing Security Awareness Determining The Actors Behind Most Significant Cyber Mockup PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
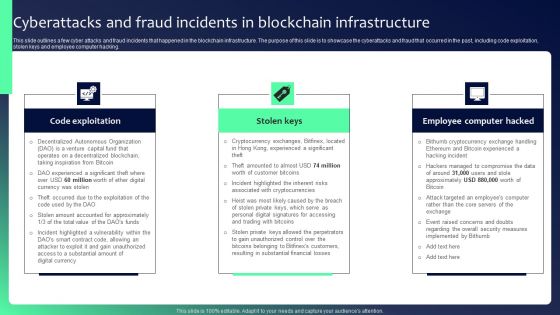
Blockchain Security Solutions Deployment Cyberattacks And Fraud Incidents In Blockchain Clipart PDF
This slide outlines a few cyber attacks and fraud incidents that happened in the blockchain infrastructure. The purpose of this slide is to showcase the cyberattacks and fraud that occurred in the past, including code exploitation, stolen keys and employee computer hacking. There are so many reasons you need a Blockchain Security Solutions Deployment Cyberattacks And Fraud Incidents In Blockchain Clipart PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
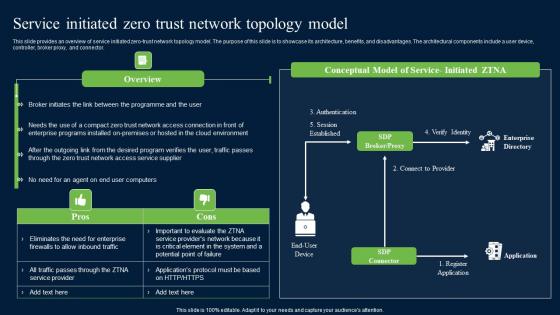
Service Initiated Zero Trust Network Topology Model Zero Trust Network Security Guidelines Pdf
This slide provides an overview of service initiated zero-trust network topology model. The purpose of this slide is to showcase its architecture, benefits, and disadvantages. The architectural components include a user device, controller, broker proxy, and connector. Find a pre-designed and impeccable Service Initiated Zero Trust Network Topology Model Zero Trust Network Security Guidelines Pdf. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide provides an overview of service initiated zero-trust network topology model. The purpose of this slide is to showcase its architecture, benefits, and disadvantages. The architectural components include a user device, controller, broker proxy, and connector.
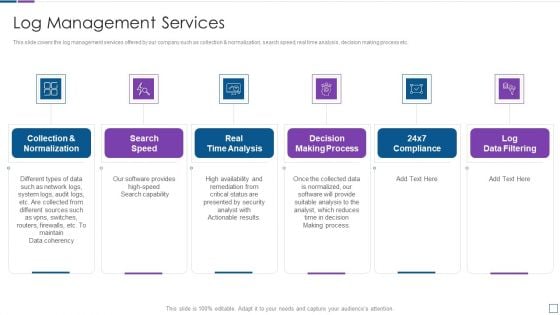
Real Time Assessment Of Security Threats Log Management Services Information PDF
This slide covers the log management services offered by our company such as collection and normalization, search speed, real time analysis, decision making process etc. Presenting real time assessment of security threats log management services information pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like collection and normalization, real time analysis, decision making process, log data filtering. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
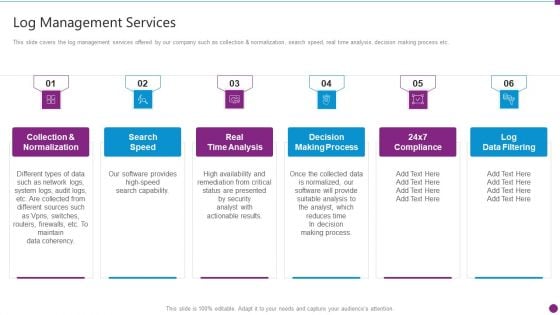
Security Information And Event Management Strategies For Financial Audit And Compliance Log Management Services Microsoft PDF
This slide covers the log management services offered by our company such as collection and normalization, search speed, real time analysis, decision making process etc. This is a security information and event management strategies for financial audit and compliance log management services microsoft pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like collection and normalization, search speed, real time analysis, decision making process, log data filtering. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
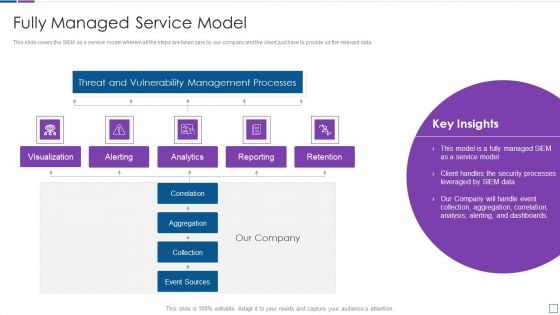
Real Time Assessment Of Security Threats Fully Managed Service Model Demonstration PDF
This slide covers the SIEM as a service model wherein all the steps are taken care by our company and the client just have to provide us the relevant data. Deliver an awe inspiring pitch with this creative real time assessment of security threats fully managed service model demonstration pdf bundle. Topics like threat and vulnerability management processes, reporting, retention, correlation, collection can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Information Security Accountability Principle Of GDPR Law Ppt PowerPoint Presentation File Backgrounds PDF
This slide shows the accountability principle, which implies that the data controller or organization is responsible for adhering to all the standards of GDPR and showing compliance if required. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Information Security Accountability Principle Of GDPR Law Ppt PowerPoint Presentation File Backgrounds PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Implementing Security Management Strategy To Mitigate Risk Ppt PowerPoint Presentation Complete Deck With Slides
Pitch yourself both in house and outside by utilizing this complete deck. This implementing security management strategy to mitigate risk ppt powerpoint presentation complete deck with slides focuses on key fundamentals of the topic, displayed using different slides. With a total of fortytwo slides, this template is the best tool you can use to persuade your audience. It will not only help you create great presentations but also induce strategic thinking because of its well researched content and graphics. You can easily personalize any of the elements to suit your unique business setting. Additionally, it can be saved in PNG, JPG, and PDF formats to save your time and resources.

Methods To Develop Advanced IT Security Monitoring Plan Ppt PowerPoint Presentation Complete Deck With Slides
Pitch yourself both in house and outside by utilizing this complete deck. This methods to develop advanced it security monitoring plan ppt powerpoint presentation complete deck with slides focuses on key fundamentals of the topic, displayed using different slides. With a total of fourty four slides, this template is the best tool you can use to persuade your audience. It will not only help you create great presentations but also induce strategic thinking because of its well researched content and graphics. You can easily personalize any of the elements to suit your unique business setting. Additionally, it can be saved in PNG, JPG, and PDF formats to save your time and resources.

Smart Home Security Solutions Company Profile Ppt PowerPoint Presentation Complete Deck With Slides
Pitch yourself both in house and outside by utilizing this complete deck. This Smart Home Security Solutions Company Profile Ppt PowerPoint Presentation Complete Deck With Slides focuses on key fundamentals of the topic, displayed using different slides. With a total of fourty one slides, this template is the best tool you can use to persuade your audience. It will not only help you create great presentations but also induce strategic thinking because of its well researched content and graphics. You can easily personalize any of the elements to suit your unique business setting. Additionally, it can be saved in PNG, JPG, and PDF formats to save your time and resources.

Risk Based Procedures To IT Security Ppt PowerPoint Presentation Complete Deck With Slides
Pitch yourself both in house and outside by utilizing this complete deck. This Risk Based Procedures To IT Security Ppt PowerPoint Presentation Complete Deck With Slides focuses on key fundamentals of the topic, displayed using different slides. With a total of fifty four slides, this template is the best tool you can use to persuade your audience. It will not only help you create great presentations but also induce strategic thinking because of its well researched content and graphics. You can easily personalize any of the elements to suit your unique business setting. Additionally, it can be saved in PNG, JPG, and PDF formats to save your time and resources.
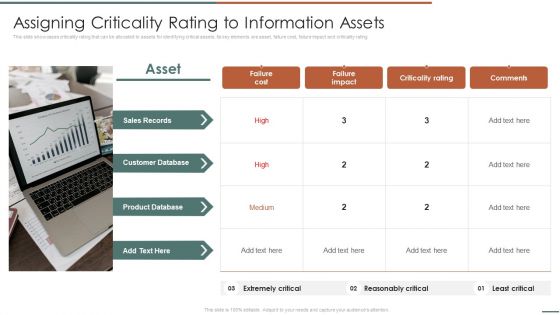
Information Security Risk Evaluation Assigning Criticality Rating To Information Assets Template PDF
This slide showcases criticality rating that can be allocated to assets for identifying critical assets. Its key elements are asset, failure cost, failure impact and criticality rating.Presenting Information Security Risk Evaluation Assigning Criticality Rating To Information Assets Template PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Customer Database, Product Database, Sales Records. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
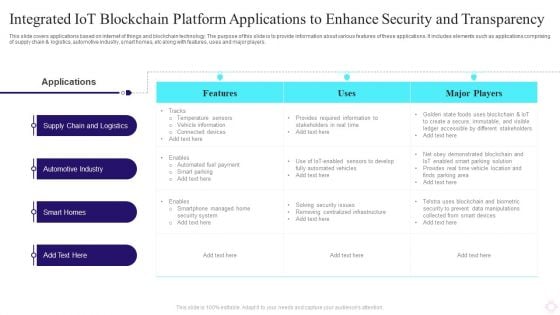
Integrated IOT Blockchain Platform Applications To Enhance Security And Transparency Portrait PDF
This slide covers applications based on internet of things and blockchain technology. The purpose of this slide is to provide information about various features of these applications. It includes elements such as applications comprising of supply chain and logistics, automotive industry, smart homes, etc along with features, uses and major players. Pitch your topic with ease and precision using this Integrated IOT Blockchain Platform Applications To Enhance Security And Transparency Portrait PDF. This layout presents information on Automotive Industry, Smart Homes, Applications. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
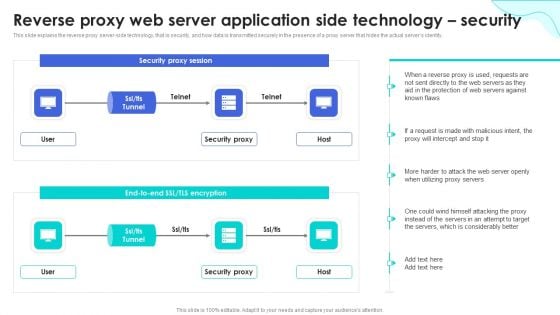
Reverse Proxy Web Server Reverse Proxy Web Server Application Side Technology Security Designs PDF
This slide represents the reverse proxy server-side technology, which is load balancing, and how reverse proxy side servers help high-traffic websites manage traffic. The Reverse Proxy Web Server Reverse Proxy Web Server Application Side Technology Security Designs PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
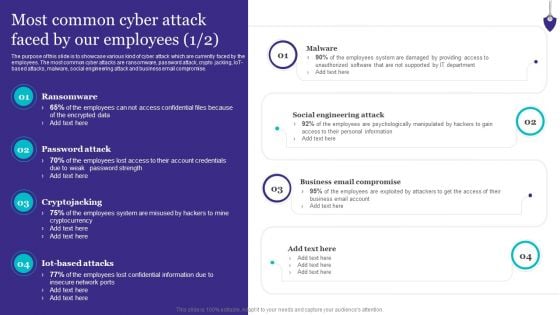
Organizing Security Awareness Most Common Cyber Attack Faced By Our Employees Mockup PDF
The Organizing Security Awareness Most Common Cyber Attack Faced By Our Employees Mockup PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
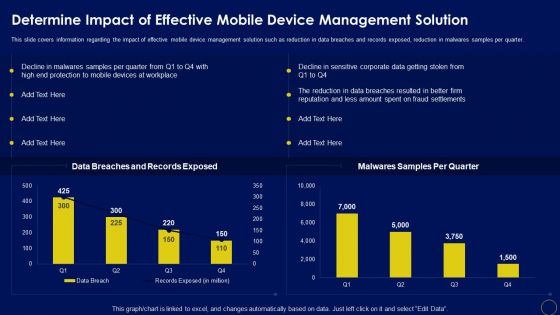
Determine Impact Of Effective Mobile Device Management Solution Business Mobile Device Security Guidelines PDF
This slide covers information regarding the impact of effective mobile device management solution such as reduction in data breaches and records exposed, reduction in malwares samples per quarter. The Determine Impact Of Effective Mobile Device Management Solution Business Mobile Device Security Guidelines PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
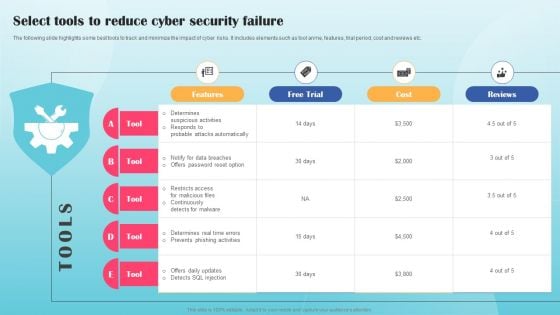
Select Tools To Reduce Cyber Security Failure Ppt PowerPoint Presentation File Show PDF
The following slide highlights some best tools to track and minimize the impact of cyber risks. It includes elements such as tool anme, features, trial period, cost and reviews etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Select Tools To Reduce Cyber Security Failure Ppt PowerPoint Presentation File Show PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Security Software Company Investor Funding Pitch Deck Competitive Analysis Themes PDF
The following slide will assist an IT company to show the investors or audience a complete view of its competitive landscape based on elements like leaders by category, company, their market capitalization and revenue. There are so many reasons you need a Security Software Company Investor Funding Pitch Deck Competitive Analysis Themes PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
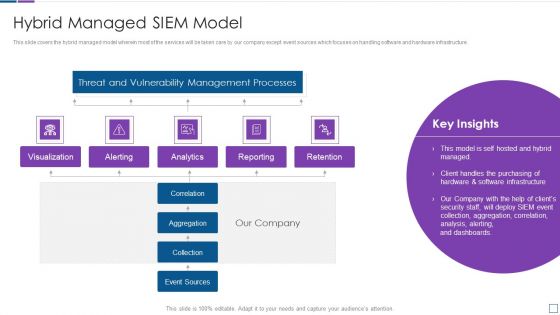
Real Time Assessment Of Security Threats Hybrid Managed SIEM Model Brochure PDF
This slide covers the hybrid managed model wherein most of the services will be taken care by our company except event sources which focuses on handling software and hardware infrastructure. Deliver an awe inspiring pitch with this creative real time assessment of security threats hybrid managed siem model brochure pdf bundle. Topics like threat and vulnerability management processes, reporting, retention, correlation, collection can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
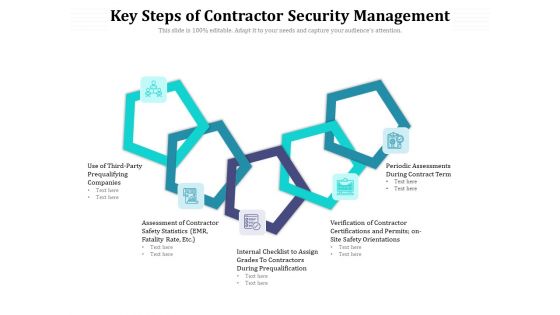
Key Steps Of Contractor Security Management Ppt PowerPoint Presentation Inspiration Show PDF
Presenting this set of slides with name key steps of contractor security management ppt powerpoint presentation inspiration show pdf. This is a five stage process. The stages in this process are use of third party prequalifying companies, assessment of contractor safety statistics, internal checklist to assign grades to contractors during prequalification, verification of contractor certifications and permits on site safety orientations, periodic assessments during contract term. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Redesigning Business Process By Ensuring Data Privacy And Security Ppt Portfolio Elements PDF
Mentioned slide provides information about the measures organization will take to ensure data privacy and protection. Strategic service planning, data innovation, data management and integration are the key initiatives covered in the slide. Slidegeeks is here to make your presentations a breeze with Redesigning Business Process By Ensuring Data Privacy And Security Ppt Portfolio Elements PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.


 Continue with Email
Continue with Email

 Home
Home


































