System Security

Quarterly Cybersecurity Training Program And Assessment Schedule Sheet Elements PDF
This slide covers annual awareness training program schedule for employees. It includes training for network security, cyber security fundamentals, insider threats, malicious code, etc.Showcasing this set of slides titled Quarterly Cybersecurity Training Program And Assessment Schedule Sheet Elements PDF. The topics addressed in these templates are Insider Threats, Network Security, Risk Assessment. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
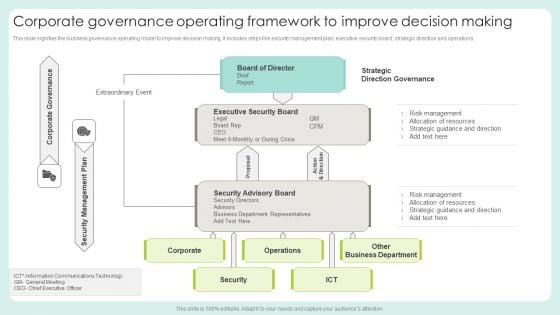
Corporate Governance Operating Framework To Improve Decision Making Diagrams PDF
This slide signifies the business governance operating model to improve decision making. It includes steps like security management plan, executive security board, strategic direction and operations.Pitch your topic with ease and precision using this Corporate Governance Operating Framework To Improve Decision Making Diagrams PDF. This layout presents information on Executive Security, Direction Governance, Communications Technology. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Essential Roles And Responsibilities Involved In Secops Elements PDF
This slide portrays information regarding the roles and responsibilities, qualification associated to staff available at Tier1, 2, 3, and 4 level at SOC structure.Deliver an awe inspiring pitch with this creative essential roles and responsibilities involved in secops elements pdf bundle. Topics like security incident responder, security alert investigator, security engineers can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
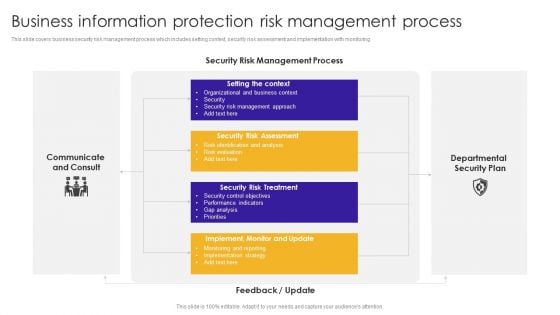
Business Information Protection Risk Management Process Structure PDF
This slide covers business security risk management process which includes setting context, security risk assessment and implementation with monitoring. Pitch your topic with ease and precision using this Business Information Protection Risk Management Process Structure PDF. This layout presents information on Organizational Business, Security Risk Assessment, Performance Indicators. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
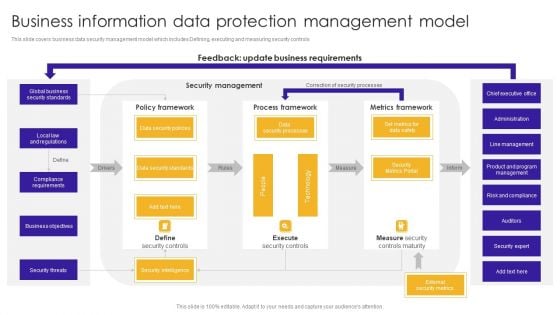
Business Information Data Protection Management Model Structure PDF
This slide covers business data security management model which includes Defining, executing and measuring security controls.Pitch your topic with ease and precision using this Business Information Data Protection Management Model Structure PDF. This layout presents information on Compliance Requirements, Security Standards, Controls Maturity. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
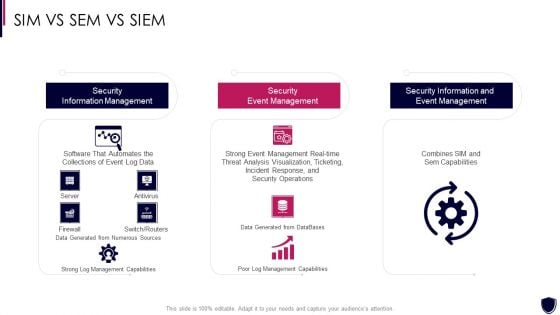
Enhancing Cyber Safety With Vulnerability Administration SIM Vs SEM Vs SIEM Brochure PDF
Presenting enhancing cyber safety with vulnerability administration sim vs sem vs siem brochure pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like security information management, security event management, security information and event management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
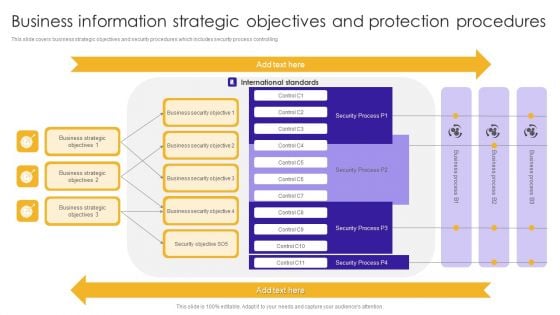
Business Information Strategic Objectives And Protection Procedures Portrait PDF
This slide covers business strategic objectives and security procedures which includes security process controlling.Pitch your topic with ease and precision using this Business Information Strategic Objectives And Protection Procedures Portrait PDF. This layout presents information on Business Security, Business Strategic, International Standards. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
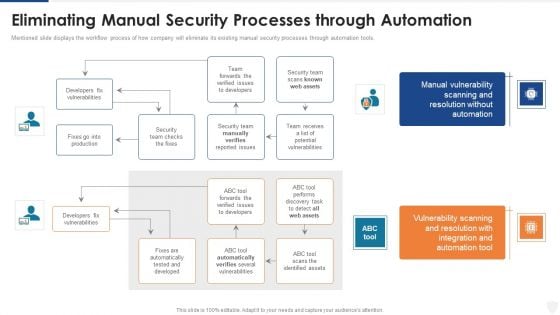
Defining Risk Events Based On Impact Size And Likelihood Of Occurrence Ppt Pictures Background PDF
Mentioned slide displays the workflow process of how company will eliminate its existing manual security processes through automation tools. Deliver and pitch your topic in the best possible manner with this eliminating manual security processes through automation ppt styles images pdf. Use them to share invaluable insights on security, team, production, developers and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
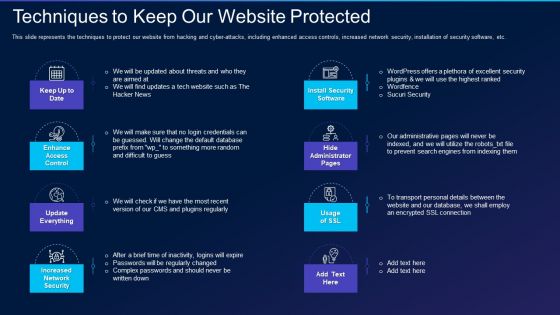
Cyber Exploitation IT Techniques To Keep Our Website Protected Brochure PDF
This slide represents the techniques to protect our website from hacking and cyber-attacks, including enhanced access controls, increased network security, installation of security software, etc. This is a cyber exploitation it techniques to keep our website protected brochure pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like install security software, hide administrator pages, enhance access control, update everything, increased network security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Effective IT Risk Management Process Roles And Responsibilities For Managing Elements PDF
Following slide demonstrates various roles and responsibilities for information security management. Responsibilities covered are security policy development, asset classification and security framework development. This is a effective it risk management process roles and responsibilities for managing elements pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like implementation, development, security, organizational, risk. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Main Advantages Of Software Harnessing The World Of Ethical Ppt Slide
This slide showcases the advantages of software security testing such as identifying weaknesses, enhancing security, ensuring compliance, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Main Advantages Of Software Harnessing The World Of Ethical Ppt Slide These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide showcases the advantages of software security testing such as identifying weaknesses, enhancing security, ensuring compliance, etc.

Cyber Exploitation IT Ethical Hacker And Why We Need Ethical Hacker Information PDF
This slide depicts the reasons to describe the need for ethical hacking, including identification and correction of security flaws, aid in development and quality control, and evaluation of the companys security and regulatory compliance. This is a cyber exploitation it ethical hacker and why we need ethical hacker information pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security flaws, development and quality control, evaluate security and regulatory compliance. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
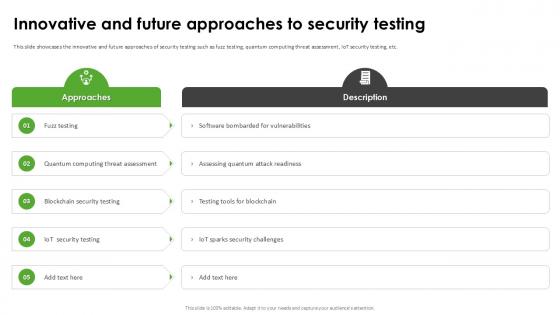
Innovative And Future Approaches Harnessing The World Of Ethical Ppt Slide
This slide showcases the innovative and future approaches of security testing such as fuzz testing, quantum computing threat assessment, IoT security testing, etc. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Innovative And Future Approaches Harnessing The World Of Ethical Ppt Slide and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide showcases the innovative and future approaches of security testing such as fuzz testing, quantum computing threat assessment, IoT security testing, etc.
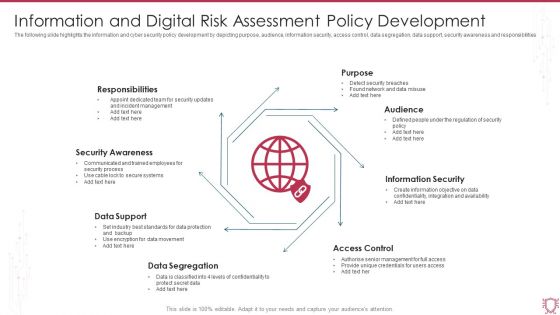
Information And Digital Risk Assessment Policy Development Ppt Portfolio Slideshow PDF
The following slide highlights the information and cyber security policy development by depicting purpose, audience, information security, access control, data segregation, data support, security awareness and responsibilities. Presenting Information And Digital Risk Assessment Policy Development Ppt Portfolio Slideshow PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Responsibilities, Security Awareness, Data Support, Data Segregation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
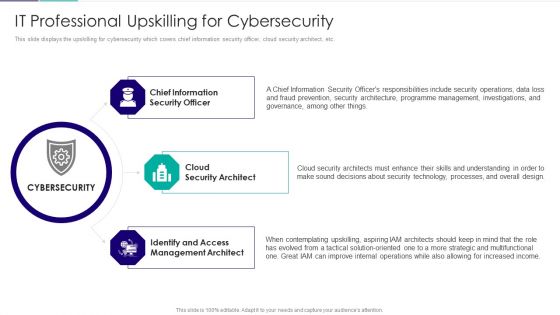
Role Of Technical Competence In Organizational It Professional Upskilling Inspiration PDF
This slide displays the upskilling for cybersecurity which covers chief information security officer, cloud security architect, etc.Presenting Role Of Technical Competence In Organizational It Professional Upskilling Inspiration PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Chief Information Security, Cloud Security Architect, Identify And Access Management Architect In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Mobile Depositing Presentation Powerpoint Templates
This is a mobile depositing presentation powerpoint templates. This is a four stage process. The stages in this process are cross selling, security services, mobile depositing, credit scoring.

Vendor Selection Steps For Digital Risk Assessment Ppt Visual Aids Show PDF
The following slide highlights the Vendor selection steps for cyber security risk depicting assessment methodology, tailor assessment, risk questions, risk threshold and cyber security assessment, it helps company to select cyber security framework and customize it to their requirements. Presenting Vendor Selection Steps For Digital Risk Assessment Ppt Visual Aids Show PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Assessment Methodology, Risk QuestionsCyber Security Assessment. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
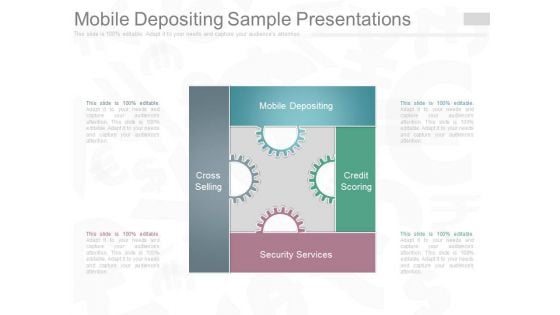
Mobile Depositing Sample Presentations
This is a mobile depositing sample presentations. This is a four stage process. The stages in this process are mobile depositing, credit scoring, security services, cross selling.
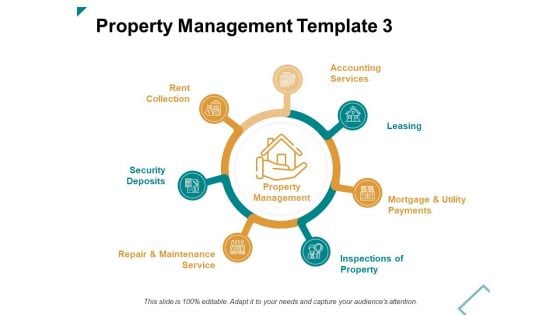
Property Management Template Ppt PowerPoint Presentation Pictures Format
This is a property management template ppt powerpoint presentation pictures format. This is a seven stage process. The stages in this process are security deposits, leasing, accounting services.

Nanorobotics In Healthcare And Medicine Timeline For Effective Nanorobot Utilization In Organization
Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Nanorobotics In Healthcare And Medicine Timeline For Effective Nanorobot Utilization In Organization. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Nanorobotics In Healthcare And Medicine Timeline For Effective Nanorobot Utilization In Organization today and make your presentation stand out from the rest This slide defines an all-inclusive timeline of steps in the execution of nanorobotics in healthcare and medicine by incorporating effective use of nanorobots within an organization. This ranges from preparation and research and eventually to the inclusion of nanorobotics with the existing healthcare systems. The timeline also identifies critical factors including security, regulatory compliance, testing, and safety procedures, where nanorobots would be applied safely and effectively.This slide is perfect for advanced medical technology presentations to help the stakeholders understand the systematic process of how nanorobotics could be introduced in healthcare solutions and paved their way for smooth adoption and use.
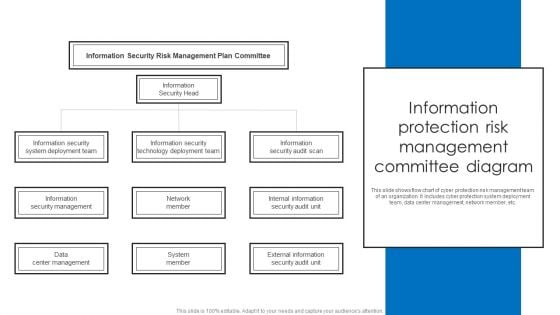
Information Protection Risk Management Committee Diagram Information PDF
This slide shows flow chart of cyber protection risk management team of an organization. It includes cyber protection system deployment team, data center management, network member, etc. Persuade your audience using this Information Protection Risk Management Committee Diagram Information PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Information Security Head, Information Security Audit Scan, Network Member. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
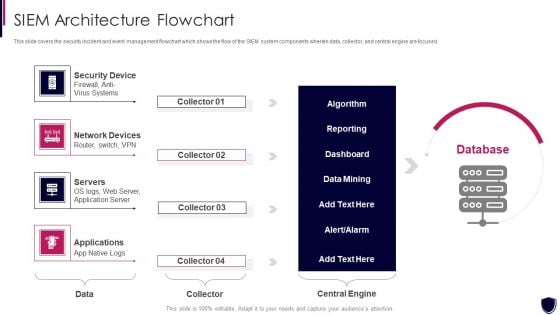
Enhancing Cyber Safety With Vulnerability Administration SIEM Architecture Flowchart Demonstration PDF
This slide covers the security incident and event management flowchart which shows the flow of the SIEM system components wherein data, collector, and central engine are focused. This is a enhancing cyber safety with vulnerability administration siem architecture flowchart demonstration pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security device, network devices, servers, applications. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
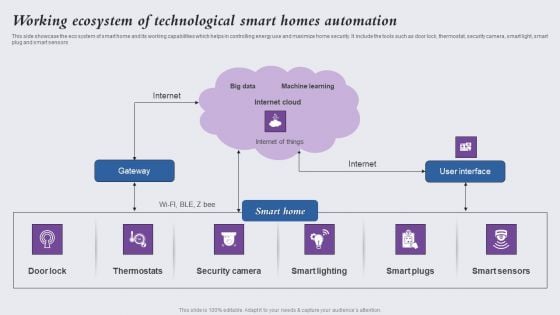
Working Ecosystem Of Technological Smart Homes Automation Elements PDF
This side showcase the eco system of smart home and its working capabilities which helps in controlling energy use and maximize home security. It include the tools such as door lock, thermostat, security camera, smart light, smart plug and smart sensors. Showcasing this set of slides titled Working Ecosystem Of Technological Smart Homes Automation Elements PDF. The topics addressed in these templates are Internet, Gateway, Thermostats. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
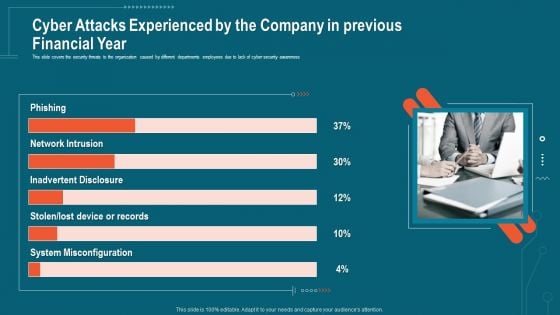
Companys Data Safety Recognition Cyber Attacks Experienced By The Company In Previous Financial Year Sample PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. This is a companys data safety recognition cyber attacks experienced by the company in previous financial year sample pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like system misconfiguration, inadvertent disclosure, network intrusion. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
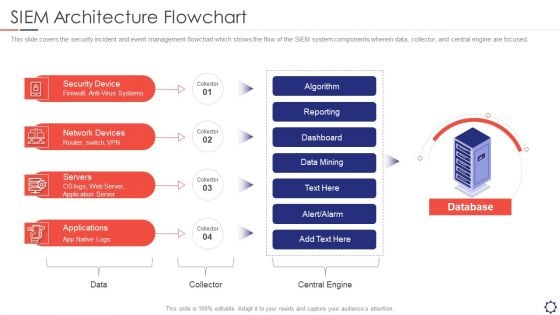
SIEM Architecture Flowchart Ppt Show Introduction PDF
This slide covers the security incident and event management flowchart which shows the flow of the SIEM system components wherein data, collector, and central engine are focused. This is a siem architecture flowchart ppt show introduction pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security device, network devices, servers, applications. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
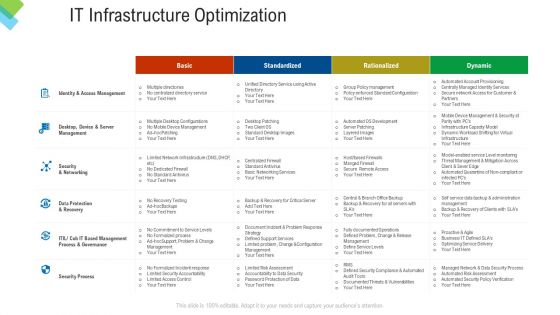
Construction Management Services IT Infrastructure Optimization Themes PDF
Deliver and pitch your topic in the best possible manner with this construction management services it infrastructure optimization themes pdf. Use them to share invaluable insights on security process, security and networking, management process, data protection, server management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
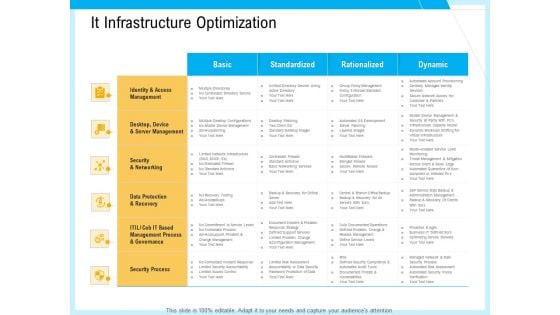
IT And Cloud Facilities Management It Infrastructure Optimization Ppt Model Slide PDF
Deliver an awe-inspiring pitch with this creative it and cloud facilities management it infrastructure optimization ppt model slide pdf bundle. Topics like standardized, rationalized, dynamic, identity and access management, security and networking, security process can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
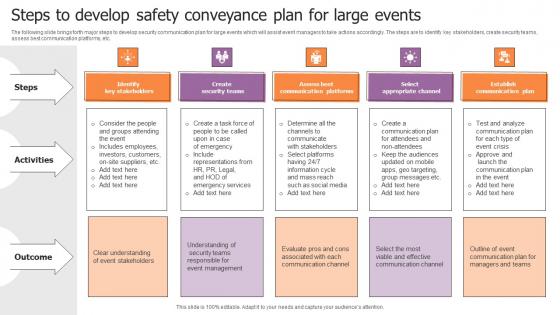
Steps To Develop Safety Conveyance Plan For Large Events Designs Pdf
The following slide brings forth major steps to develop security communication plan for large events which will assist event managers to take actions accordingly. The steps are to identify key stakeholders, create security teams, assess best communication platforms, etc. Showcasing this set of slides titled Steps To Develop Safety Conveyance Plan For Large Events Designs Pdf. The topics addressed in these templates are Identify Key Stakeholders, Create Security Teams, Select Appropriate Channel. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. The following slide brings forth major steps to develop security communication plan for large events which will assist event managers to take actions accordingly. The steps are to identify key stakeholders, create security teams, assess best communication platforms, etc.
Colorful Illustration Using Arrows Flow Chart Business Plan PowerPoint Templates
We present our colorful illustration using arrows flow chart business plan PowerPoint templates.Use our Arrows PowerPoint Templates because,You are the Champion of your team shall anoint. Use our Shapes PowerPoint Templates because, This will helps you to explore the minutest detail of each concept and follow the trail to its conclusion. Use our Signs PowerPoint Templates because,You can take it along a sure fire road to good profit. Use our Business PowerPoint Templates because, Spell out your advertising plans to increase market share. The feedback has been positive and productive Use our Process and Flows PowerPoint Templates because,They will Amplify your basic corporate concept and forefront the benefits of overlapping processes to arrive at common goals.Use these PowerPoint slides for presentations relating to 3d, background, colorful, communication, computing, concept, connection, data, database, design, development, digital, download, glossy, graphic, illustration, information, internet, isolated, network, networking, online, orange, plastic, security, segment, server, store, symbol, system, technology, upload, website,. The prominent colors used in the PowerPoint template are Green, Red, Black. People tell us our colorful illustration using arrows flow chart business plan PowerPoint templates are Spiffy. The feedback we get is that our data PowerPoint templates and PPT Slides are Versatile. People tell us our colorful illustration using arrows flow chart business plan PowerPoint templates are designed by a team of presentation professionals. Presenters tell us our concept PowerPoint templates and PPT Slides are Appealing. The feedback we get is that our colorful illustration using arrows flow chart business plan PowerPoint templates are Tranquil. Professionals tell us our concept PowerPoint templates and PPT Slides are Gorgeous. Burn away doubts with our Colorful Illustration Using Arrows Flow Chart Business Plan PowerPoint Templates. You will come out on top.

Online Payment Techniques Challenges Faced By Business In Adopting Cashless
Mentioned slide showcases various challenges in implementation of cashless payment system in business. It includes challenges such as customer restrain, high processing fees, security issues, difficulty to adopt cashless technology and regular internet services. Explore a selection of the finest Online Payment Techniques Challenges Faced By Business In Adopting Cashless here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Online Payment Techniques Challenges Faced By Business In Adopting Cashless to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. Mentioned slide showcases various challenges in implementation of cashless payment system in business. It includes challenges such as customer restrain, high processing fees, security issues, difficulty to adopt cashless technology and regular internet services.
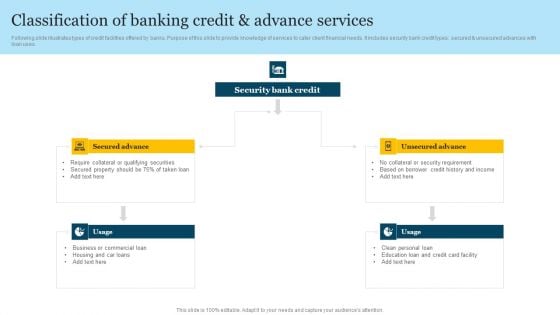
Classification Of Banking Credit And Advance Services Summary PDF
Following slide illustrates types of credit facilities offered by banks. Purpose of this slide to provide knowledge of services to cater client financial needs. It includes security bank credit types secured and unsecured advances with loan uses. Presenting Classification Of Banking Credit And Advance Services Summary PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Security Bank Credit, Security Requirement, Education Loan This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
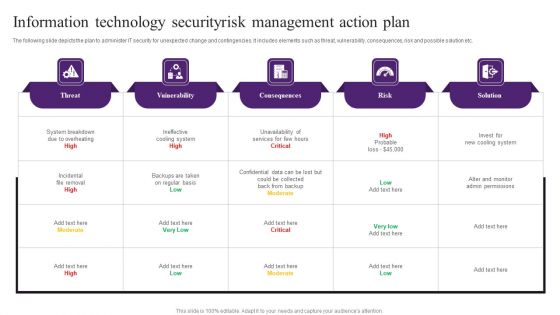
Information Technology Securityrisk Management Action Plan Themes PDF
The following slide depicts the plan to administer IT security for unexpected change and contingencies. It includes elements such as threat, vulnerability, consequences, risk and possible solution etc. Showcasing this set of slides titled Information Technology Securityrisk Management Action Plan Themes PDF. The topics addressed in these templates are Consequences, Vuinerability, System Breakdown. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Components Of SCM Connectivity Integration And Coordination Ppt PowerPoint Presentation File Pictures PDF
Persuade your audience using this components of scm connectivity integration and coordination ppt powerpoint presentation file pictures pdf. This PPT design covers seven stages, thus making it a great tool to use. It also caters to a variety of topics including transport connectivity, commercial integration, customs and security integration, regulatory integration, planning and funding integration, work practices integration, information system integration. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
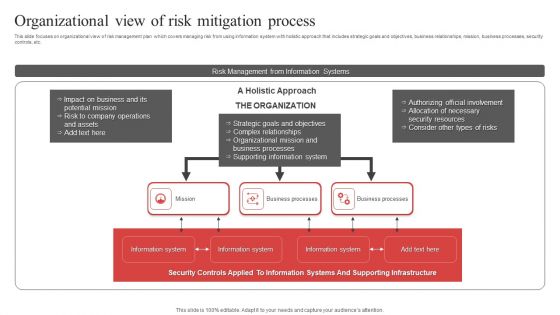
Organizational View Of Risk Mitigation Process Ppt PowerPoint Presentation File Example PDF
This slide focuses on organizational view of risk management plan which covers managing risk from using information system with holistic approach that includes strategic goals and objectives, business relationships, mission, business processes, security controls, etc. Pitch your topic with ease and precision using this Organizational View Of Risk Mitigation Process Ppt PowerPoint Presentation File Example PDF. This layout presents information on Information System, Business Processes, Mission. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
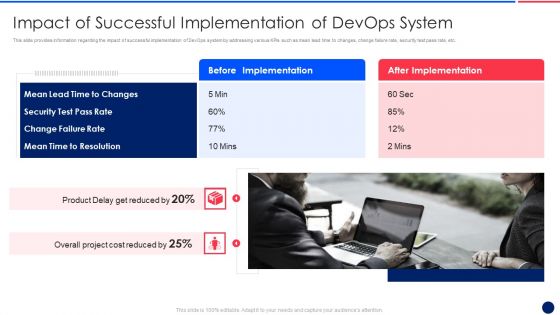
Key Components Critical To Devops Viability IT Impact Of Successful Implementation Background PDF
This slide provides information regarding the impact of successful implementation of DevOps system by addressing various KPIs such as mean lead time to changes, change failure rate, security test pass rate, etc. This is a key components critical to devops viability it impact of successful implementation background pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like impact of successful implementation of devops system. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
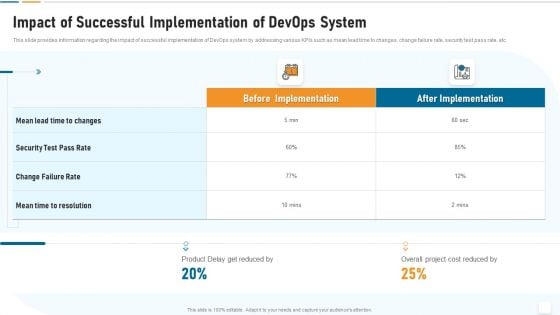
Strategic Development And Operations Execution IT Impact Of Successful Implementation Download PDF
This slide provides information regarding the impact of successful implementation of DevOps system by addressing various KPIs such as mean lead time to changes, change failure rate, security test pass rate, etc. Deliver and pitch your topic in the best possible manner with this strategic development and operations execution it impact of successful implementation download pdf. Use them to share invaluable insights on impact of successful implementation of devops system and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
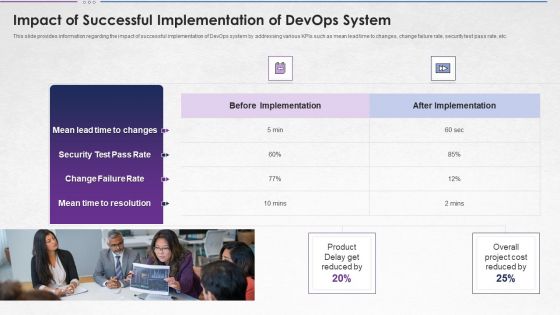
Steps For Devops Implementation IT Impact Of Successful Implementation Designs PDF
This slide provides information regarding the impact of successful implementation of DevOps system by addressing various KPIs such as mean lead time to changes, change failure rate, security test pass rate, etc. Presenting steps for devops implementation it impact of successful implementation designs pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like impact of successful implementation of devops system. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Examples Of Data Breaches Ppt PowerPoint Presentation Summary Portrait PDF
Presenting this set of slides with name examples of data breaches ppt powerpoint presentation summary portrait pdf. This is a five stage process. The stages in this process are inadequate cyber secure technology, lack of skilled human resource, security projects may fail if they are not financially supported adequately, security program is not aligned to business objective . This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Types Of Data Breach Ppt PowerPoint Presentation Inspiration Ideas PDF
Presenting this set of slides with name types of data breach ppt powerpoint presentation inspiration ideas pdf. This is a five stage process. The stages in this process are inadequate cyber secure technology, lack of skilled human resource, security projects may fail if they are not financially supported adequately, security program is not aligned to business objective . This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Global Cyber Terrorism Incidents On The Rise IT Techniques To Protect SCADA Elements PDF
This slide depicts the techniques to protect SCADA from cyber-attacks which include security training of employees, strict firewalls. This is a global cyber terrorism incidents on the rise it techniques to protect scada elements pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security training of employee, access controls, strict firewalls, network security procedures. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
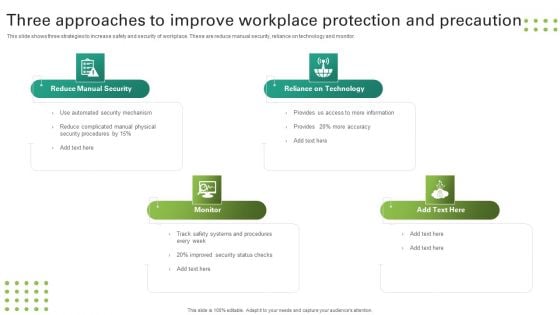
Three Approaches To Improve Workplace Protection And Precaution Background PDF
This slide shows three strategies to increase safety and security of workplace. These are reduce manual security, reliance on technology and monitor. Persuade your audience using this Three Approaches To Improve Workplace Protection And Precaution Background PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Reduce Manual Security, Reliance On Technology, Monitor. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Key Strategies For Data Protection And Privacy Rules PDF
The following slide showcases some techniques to ensure data security and privacy. It includes elements such as authentication, data encryption, network security, access controls etc. Persuade your audience using this Key Strategies For Data Protection And Privacy Rules PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Authentication, Data Encryption, Network Security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
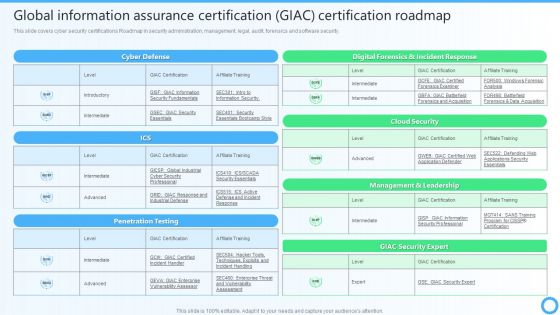
Global Information Assurance Certification GIAC Certification Roadmap IT Certifications To Enhance Template PDF
This slide covers cyber security certifications Roadmap in security administration, management, legal, audit, forensics and software security.This Global Information Assurance Certification GIAC Certification Roadmap IT Certifications To Enhance Template PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
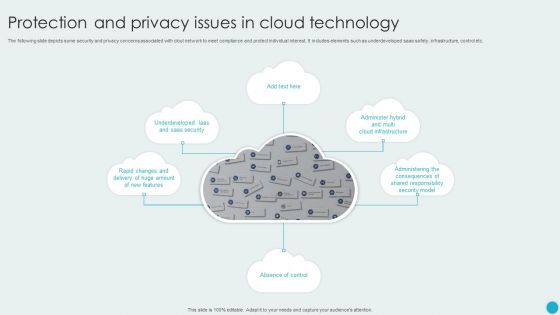
Protection And Privacy Issues In Cloud Technology Rules PDF
The following slide depicts some security and privacy concerns associated with clout network to meet compliance and protect individual interest. It includes elements such as underdeveloped saas safety, infrastructure, control etc. Persuade your audience using this Protection And Privacy Issues In Cloud Technology Rules PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Absence Of Control, Saas Security, Security Model. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
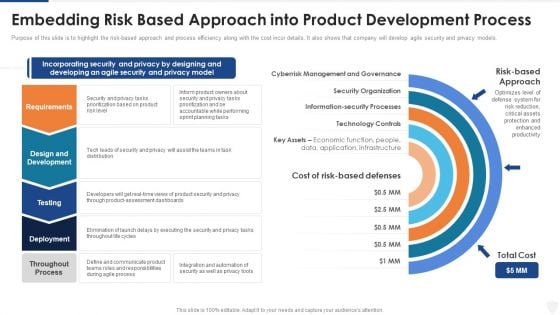
Embedding Risk Based Approach Into Product Development Process Ppt Model Files PDF
Purpose of this slide is to highlight the risk based approach and process efficiency along with the cost incur details. It also shows that company will develop agile security and privacy models. Presenting embedding risk based approach into product development process ppt model files pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like technology controls, information security processes, security organization, economic. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
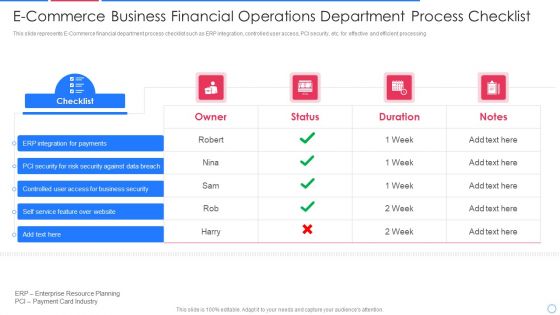
E Commerce Business Financial Operations Department Process Checklist Information PDF
This slide represents E-Commerce financial department process checklist such as ERP integration, controlled user access, PCI security, etc. for effective and efficient processing Pitch your topic with ease and precision using this e commerce business financial operations department process checklist information pdf This layout presents information on integration for payments, security for risk security against, controlled user access It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
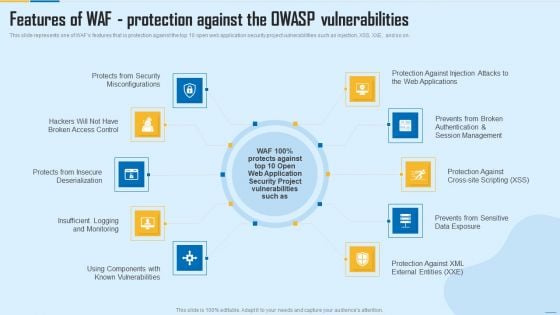
Features Of WAF Protection Against The Owasp Vulnerabilities WAF Platform Summary PDF
This slide represents one of WAFs features that is protection against the top 10 open web application security project vulnerabilities such as injection, XSS, XXE, and so on. This is a Features Of WAF Protection Against The Owasp Vulnerabilities WAF Platform Summary PDF template with various stages. Focus and dispense information on ten stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Misconfigurations, Session Management, Security Project. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
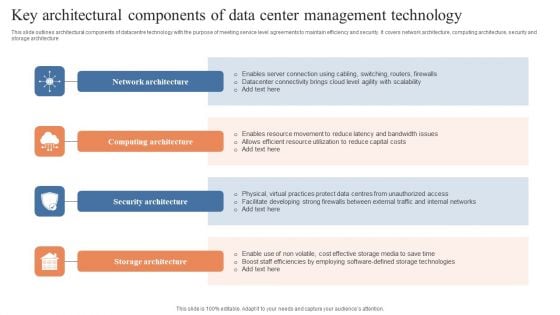
Key Architectural Components Of Data Center Management Technology Introduction PDF
This slide outlines architectural components of datacentre technology with the purpose of meeting service level agreements to maintain efficiency and security. It covers network architecture, computing architecture, security and storage architecture. Presenting Key Architectural Components Of Data Center Management Technology Introduction PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Network Architecture, Computing Architecture, Security Architecture. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
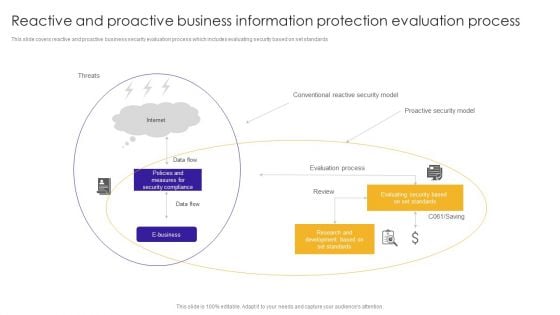
Reactive And Proactive Business Information Protection Evaluation Process Sample PDF
This slide covers reactive and proactive business security evaluation process which includes evaluating security based on set standards. Persuade your audience using this Reactive And Proactive Business Information Protection Evaluation Process Sample PDF. This PPT design covers one stage, thus making it a great tool to use. It also caters to a variety of topics including Conventional Reactive, Proactive Security, Evaluation Process. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
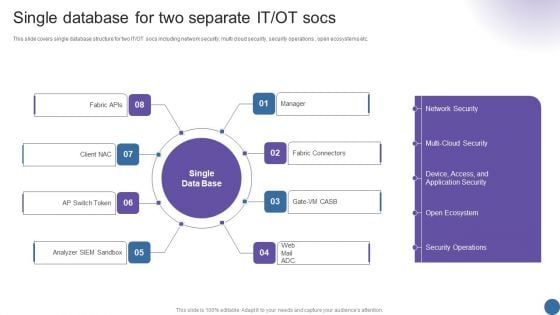
Single Database For Two Separate IT OT Socs Managing Organizational Transformation Professional PDF
This slide covers single database structure for two IT OT socs including network security, multi cloud security, security operations , open ecosystems etc. Presenting Single Database For Two Separate IT OT Socs Managing Organizational Transformation Professional PDF to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like Single Database, Two Separate, Fabric Connectors. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
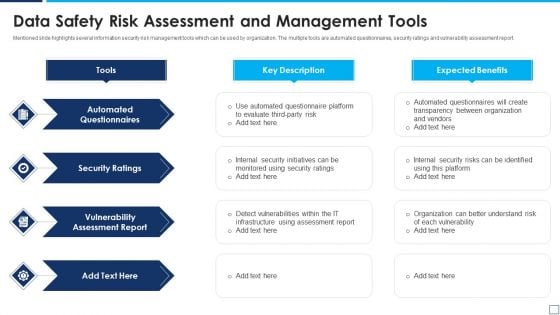
Data Safety Risk Assessment And Management Tools Demonstration PDF
Mentioned slide highlights several information security risk management tools which can be used by organization. The multiple tools are automated questionnaires, security ratings and vulnerability assessment report. Presenting data safety risk assessment and management tools demonstration pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including automated questionnaires, security ratings, vulnerability assessment report. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
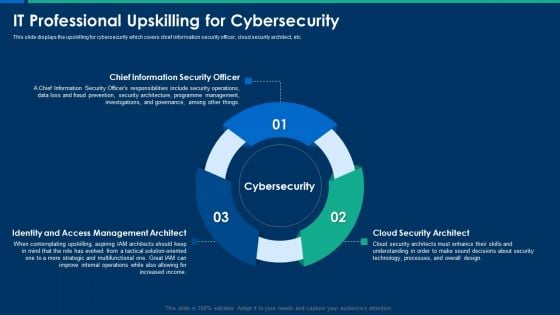
CIO Role In Digital Evolution IT Professional Upskilling For Cybersecurity Themes PDF
This slide displays the upskilling for cybersecurity which covers chief information security officer, cloud security architect, etc. This is a CIO Role In Digital Evolution IT Professional Upskilling For Cybersecurity Themes PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Chief Information, Management Architect, Cloud Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Process Of Digital Risk Assessment Management Ppt Summary Graphics PDF
The following slide highlights the process of cyber security asset management depicting four steps which include asset inventory, synchronization, security gaps and response to save assets and mitigate the risk in minimum time. Presenting Process Of Digital Risk Assessment Management Ppt Summary Graphics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Asset Inventory, Synchronization, Response, Security Gaps. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
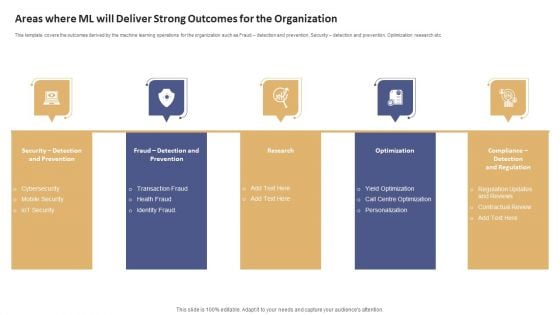
Data Processing Services Delivery Areas Where ML Will Deliver Strong Outcomes Background PDF
This template covers the outcomes derived by the machine learning operations for the organization such as Fraud detection and prevention, Security detection and prevention, Optimization research etc. Presenting Data Processing Services Delivery Areas Where ML Will Deliver Strong Outcomes Background PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Cybersecurity, Mobile Security, IoT Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Digital Risk Assessment Threat Mitigation Strategies Ppt Show Images PDF
The following slide highlights the six strategies for cyber security threat mitigation illustrating risk assessment, access control, security solution, patch management, traffic monitoring and incident response. Presenting Digital Risk Assessment Threat Mitigation Strategies Ppt Show Images PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Risk Assessment, Access Control, Patch Management, Security Solution. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
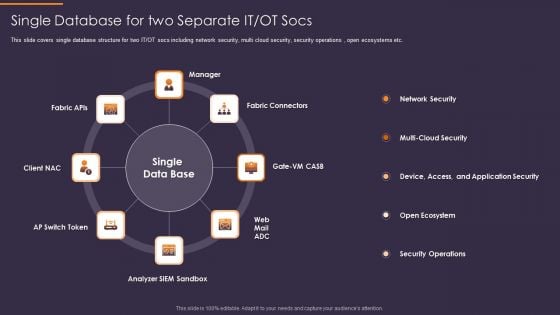
Convergence Strategy Information Single Database For Two Separate IT OT Socs Rules PDF
This slide covers single database structure for two IT or OT socs including network security, multi cloud security, security operations , open ecosystems etc. Presenting Convergence Strategy Information Single Database For Two Separate IT OT Socs Rules PDF to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like Fabric Connectors, Analyzer SIEM Sandbox, AP Switch Token, Client NAC, Fabric APIs. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Cloud Intelligence Framework For Application Consumption Determining The Suitable Software For Organization Icons PDF
The slide provides the key features comparison of various software that will help the company to achieve its objective of process automation and data security. Deliver and pitch your topic in the best possible manner with this cloud intelligence framework for application consumption determining the suitable software for organization icons pdf. Use them to share invaluable insights on process automation, data security, improve productivity, process automation and data security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
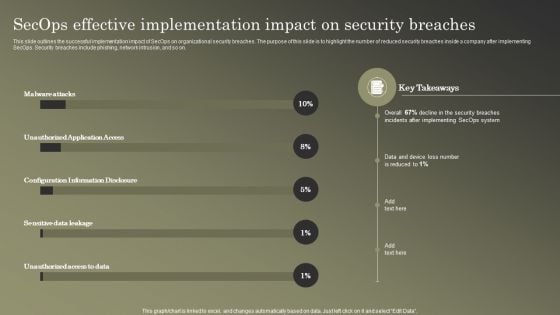
Cybersecurity Operations Cybersecops Secops Effective Implementation Impact Summary PDF
This slide outlines the successful implementation impact of SecOps on organizational security breaches. The purpose of this slide is to highlight the number of reduced security breaches inside a company after implementing SecOps. Security breaches include phishing, network intrusion, and so on. Make sure to capture your audiences attention in your business displays with our gratis customizable Cybersecurity Operations Cybersecops Secops Effective Implementation Impact Summary PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Cybersecurity Key Performance Indicators With Applications Summary Pdf
Pitch your topic with ease and precision using this Cybersecurity Key Performance Indicators With Applications Summary Pdf This layout presents information on Identify Weaknesses, Review Improvement, Security Policies It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide showcases the cyber security key performance indicators with applications which helps an organization to determine readiness. It include details such as security policies, identify weaknesses, obligation to compliance framework, etc.
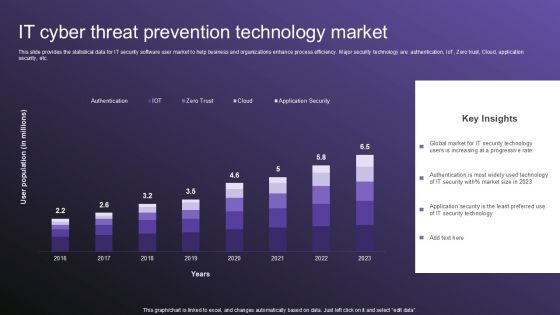
IT Cyber Threat Prevention Technology Market Topics PDF


 Continue with Email
Continue with Email

 Home
Home


































