Talent Profile
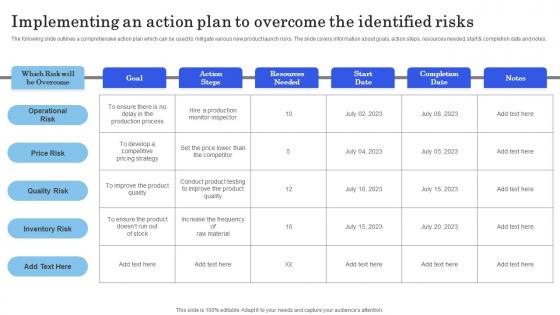
Launching New Commodity Implementing An Action Plan To Overcome The Identified Clipart Pdf
The following slide outlines a comprehensive action plan which can be used to mitigate various new product launch risks. The slide covers information about goals, action steps, resources needed, start and completion date and notes. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Launching New Commodity Implementing An Action Plan To Overcome The Identified Clipart Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. The following slide outlines a comprehensive action plan which can be used to mitigate various new product launch risks. The slide covers information about goals, action steps, resources needed, start and completion date and notes.
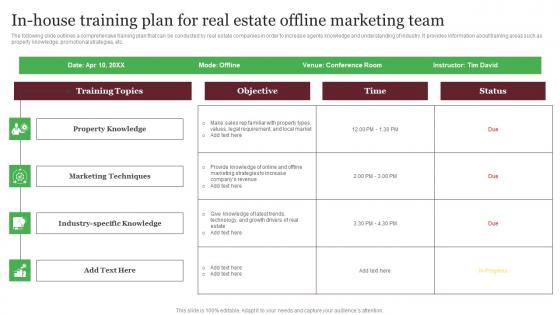
In House Training Plan For Real Estate Offline Marketing Team Out Of The Box Real Themes Pdf
The following slide outlines a comprehensive training plan that can be conducted by real estate companies in order to increase agents knowledge and understanding of industry. It provides information about training areas such as property knowledge, promotional strategies, etc. Explore a selection of the finest In House Training Plan For Real Estate Offline Marketing Team Out Of The Box Real Themes Pdf here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our In House Training Plan For Real Estate Offline Marketing Team Out Of The Box Real Themes Pdf to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. The following slide outlines a comprehensive training plan that can be conducted by real estate companies in order to increase agents knowledge and understanding of industry. It provides information about training areas such as property knowledge, promotional strategies, etc.

Introduction To Open House Event For Increasing Property Sales Out Of The Box Real Infographics Pdf
The following slide outlines comprehensive overview of open house event through which realtors can attract potential clients and increase property sales. The slide covers information about event details, property details, location, contact details, etc. Retrieve professionally designed Introduction To Open House Event For Increasing Property Sales Out Of The Box Real Infographics Pdf to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. The following slide outlines comprehensive overview of open house event through which realtors can attract potential clients and increase property sales. The slide covers information about event details, property details, location, contact details, etc.

Case Study Of Globally Brand Building Techniques To Gain Competitive Edge Mockup Pdf
The following slide outlines the case study of the coffee industrys most successful brand Starbucks. Details covered in this slide is related to the brand mission and vision statement, target audience, top competitors and brand identity, and positioning. Get a simple yet stunning designed Case Study Of Globally Brand Building Techniques To Gain Competitive Edge Mockup Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Case Study Of Globally Brand Building Techniques To Gain Competitive Edge Mockup Pdf can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. The following slide outlines the case study of the coffee industrys most successful brand Starbucks. Details covered in this slide is related to the brand mission and vision statement, target audience, top competitors and brand identity, and positioning.
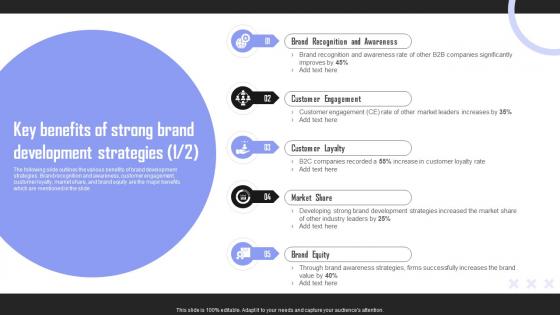
Key Benefits Of Strong Brand Building Techniques To Gain Competitive Edge Information Pdf
The following slide outlines the various benefits of brand development strategies. Brand recognition and awareness, customer engagement, customer loyalty, market share, and brand equity are the major benefits which are mentioned in the slide. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Key Benefits Of Strong Brand Building Techniques To Gain Competitive Edge Information Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. The following slide outlines the various benefits of brand development strategies. Brand recognition and awareness, customer engagement, customer loyalty, market share, and brand equity are the major benefits which are mentioned in the slide.

Data Stewardship In Business Processes Benefits Project Oriented Data Graphics Pdf
This slide outlines the advantages of the project oriented data stewardship model, including implementing data stewardship for a particular projects desired objective and then enhanced for a wider level, data stewardship and project success are inter connected, and so on. Explore a selection of the finest Data Stewardship In Business Processes Benefits Project Oriented Data Graphics Pdf here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Data Stewardship In Business Processes Benefits Project Oriented Data Graphics Pdf to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide outlines the advantages of the project oriented data stewardship model, including implementing data stewardship for a particular projects desired objective and then enhanced for a wider level, data stewardship and project success are inter connected, and so on.
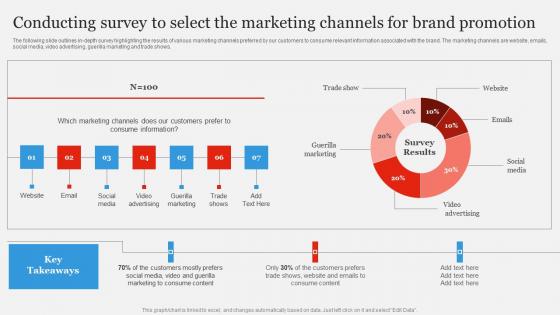
Conducting Survey Select The Marketing Branding Strategy To Gain Competitive Edge Clipart Pdf
The following slide outlines in depth survey highlighting the results of various marketing channels preferred by our customers to consume relevant information associated with the brand. The marketing channels are website, emails, social media, video advertising, guerilla marketing and trade shows. Get a simple yet stunning designed Conducting Survey Select The Marketing Branding Strategy To Gain Competitive Edge Clipart Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Conducting Survey Select The Marketing Branding Strategy To Gain Competitive Edge Clipart Pdf can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. The following slide outlines in depth survey highlighting the results of various marketing channels preferred by our customers to consume relevant information associated with the brand. The marketing channels are website, emails, social media, video advertising, guerilla marketing and trade shows.
Our Solution Value Based Investor Financing Pitch Deck Demonstration Pdf
The following slide outlines multiple solutions provided by our firm that can overcome problems faced by investors. The slide provides information about services rendered such as investment strategy, asset allocation, risk tolerance, asset and security selection, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Our Solution Value Based Investor Financing Pitch Deck Demonstration Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. The following slide outlines multiple solutions provided by our firm that can overcome problems faced by investors. The slide provides information about services rendered such as investment strategy, asset allocation, risk tolerance, asset and security selection, etc.
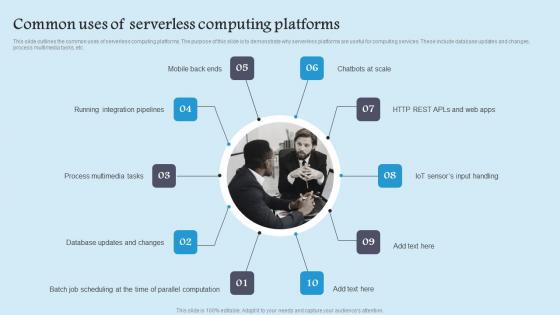
Common Uses Of Serverless Role Serverless Computing Modern Technology Download Pdf
This slide outlines the common uses of serverless computing platforms. The purpose of this slide is to demonstrate why serverless platforms are useful for computing services. These include database updates and changes, process multimedia tasks, etc. Explore a selection of the finest Common Uses Of Serverless Role Serverless Computing Modern Technology Download Pdf here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Common Uses Of Serverless Role Serverless Computing Modern Technology Download Pdf to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide outlines the common uses of serverless computing platforms. The purpose of this slide is to demonstrate why serverless platforms are useful for computing services. These include database updates and changes, process multimedia tasks, etc.
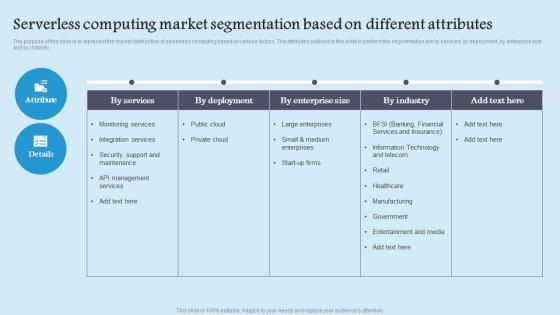
Serverless Computing Market Role Serverless Computing Modern Technology Diagrams Pdf
The purpose of this slide is to represent the market distribution of serverless computing based on various factors. The attributes outlined in this slide to perform the segmentation are by services, by deployment, by enterprise size and by industry. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Serverless Computing Market Role Serverless Computing Modern Technology Diagrams Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. The purpose of this slide is to represent the market distribution of serverless computing based on various factors. The attributes outlined in this slide to perform the segmentation are by services, by deployment, by enterprise size and by industry.
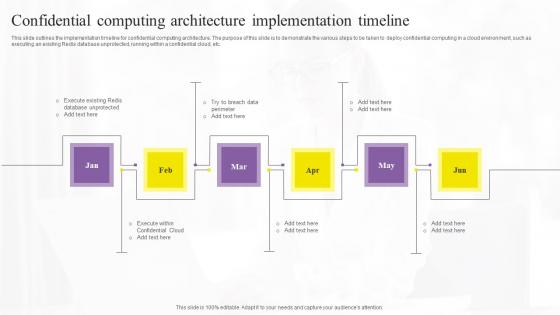
Confidential Computing Technologies Confidential Computing Architecture Topics Pdf
This slide outlines the implementation timeline for confidential computing architecture. The purpose of this slide is to demonstrate the various steps to be taken to deploy confidential computing in a cloud environment, such as executing an existing Redis database unprotected, running within a confidential cloud, etc. Explore a selection of the finest Confidential Computing Technologies Confidential Computing Architecture Topics Pdf here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Confidential Computing Technologies Confidential Computing Architecture Topics Pdf to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide outlines the implementation timeline for confidential computing architecture. The purpose of this slide is to demonstrate the various steps to be taken to deploy confidential computing in a cloud environment, such as executing an existing Redis database unprotected, running within a confidential cloud, etc.
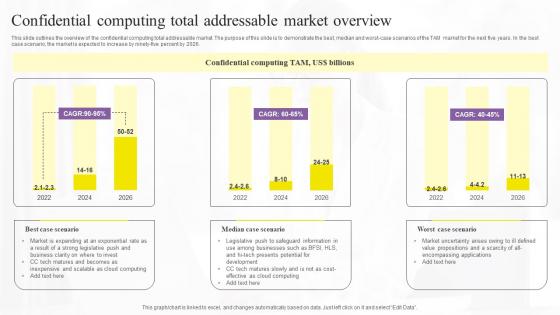
Confidential Computing Total Confidential Computing Technologies Formats Pdf
This slide outlines the overview of the confidential computing total addressable market. The purpose of this slide is to demonstrate the best, median and worst-case scenarios of the TAM market for the next five years. In the best case scenario, the market is expected to increase by ninety-five percent by 2026. Retrieve professionally designed Confidential Computing Total Confidential Computing Technologies Formats Pdf to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide outlines the overview of the confidential computing total addressable market. The purpose of this slide is to demonstrate the best, median and worst-case scenarios of the TAM market for the next five years. In the best case scenario, the market is expected to increase by ninety-five percent by 2026.
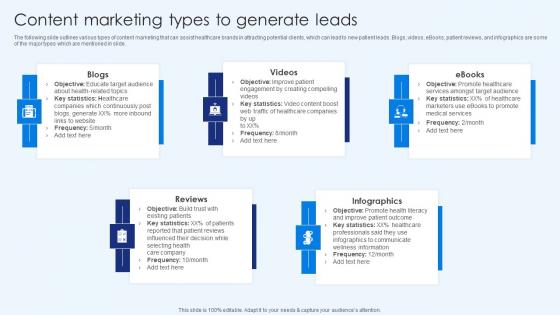
Content Marketing Types To Generate Leads Healthcare Promotion Background Pdf
The following slide outlines various types of content marketing that can assist healthcare brands in attracting potential clients, which can lead to new patient leads. Blogs, videos, eBooks, patient reviews, and infographics are some of the major types which are mentioned in slide. Get a simple yet stunning designed Determining Marketing Goals For Healthcare Company Healthcare Promotion Topics Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Determining Marketing Goals For Healthcare Company Healthcare Promotion Topics Pdf can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. The following slide outlines various types of content marketing that can assist healthcare brands in attracting potential clients, which can lead to new patient leads. Blogs, videos, eBooks, patient reviews, and infographics are some of the major types which are mentioned in slide.

Overview And Key Benefits Of Traditional Marketing Healthcare Promotion Ideas Pdf
The following slide outlines brief introduction to offline marketing in healthcare. The slide also provides information about key advantages of using offline marketing such as more wide reach, target messaging, brand credibility, and cost-effective. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Overview And Key Benefits Of Traditional Marketing Healthcare Promotion Ideas Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Overview And Key Benefits Of Traditional Marketing Healthcare Promotion Ideas Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today The following slide outlines brief introduction to offline marketing in healthcare. The slide also provides information about key advantages of using offline marketing such as more wide reach, target messaging, brand credibility, and cost-effective.

Overview And Key Benefits Of Using Healthcare Marketing Healthcare Promotion Professional Pdf
The following slide outlines brief introduction to healthcare marketing that can assist organizations in improving community relationships. It also covers information about major benefits of using medical care advertising such as competitive edge, improved public health, patient retention rate, etc. Get a simple yet stunning designed Overview And Key Benefits Of Using Healthcare Marketing Healthcare Promotion Professional Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Overview And Key Benefits Of Using Healthcare Marketing Healthcare Promotion Professional Pdf can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. The following slide outlines brief introduction to healthcare marketing that can assist organizations in improving community relationships. It also covers information about major benefits of using medical care advertising such as competitive edge, improved public health, patient retention rate, etc.
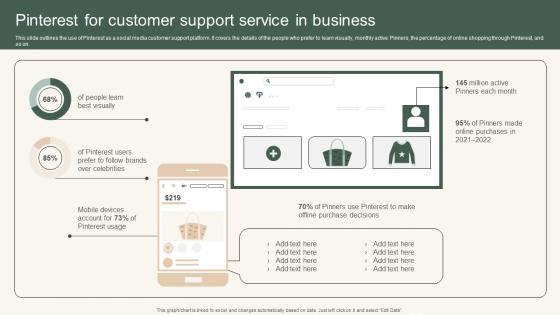
Pinterest For Customer Support Instant Messenger For Internal Business Operations Ideas Pdf
This slide outlines the use of Pinterest as a social media customer support platform. It covers the details of the people who prefer to learn visually, monthly active Pinners, the percentage of online shopping through Pinterest, and so on. Get a simple yet stunning designed Pinterest For Customer Support Instant Messenger For Internal Business Operations Ideas Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Pinterest For Customer Support Instant Messenger For Internal Business Operations Ideas Pdf can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide outlines the use of Pinterest as a social media customer support platform. It covers the details of the people who prefer to learn visually, monthly active Pinners, the percentage of online shopping through Pinterest, and so on.
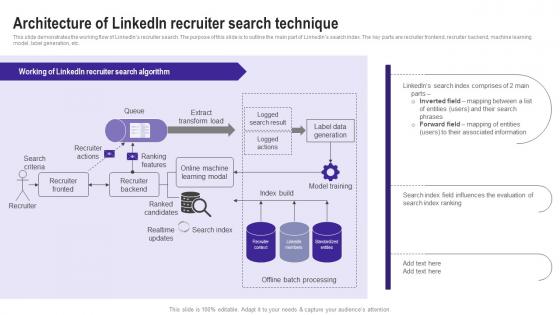
Architecture Of Linkedin Use Cases Of Filtering Methods Rules Pdf
This slide demonstrates the working flow of LinkedIns recruiter search. The purpose of this slide is to outline the main part of LinkedIns search index. The key parts are recruiter frontend, recruiter backend, machine learning model, label generation, etc. Get a simple yet stunning designed Architecture Of Linkedin Use Cases Of Filtering Methods Rules Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Architecture Of Linkedin Use Cases Of Filtering Methods Rules Pdf can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide demonstrates the working flow of LinkedIns recruiter search. The purpose of this slide is to outline the main part of LinkedIns search index. The key parts are recruiter frontend, recruiter backend, machine learning model, label generation, etc.
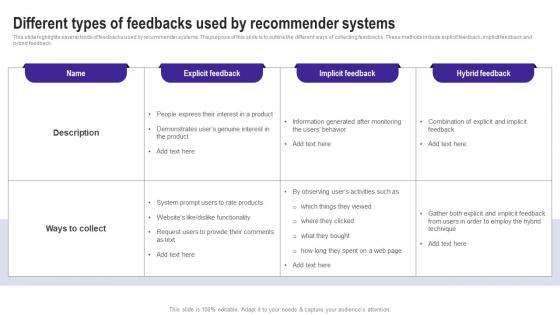
Different Types Of Feedbacks Used By Recommender Use Cases Of Filtering Methods Rules Pdf
This slide highlights several kinds of feedbacks used by recommender systems. The purpose of this slide is to outline the different ways of collecting feedbacks. These methods include explicit feedback, implicit feedback and hybrid feedback. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Different Types Of Feedbacks Used By Recommender Use Cases Of Filtering Methods Rules Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide highlights several kinds of feedbacks used by recommender systems. The purpose of this slide is to outline the different ways of collecting feedbacks. These methods include explicit feedback, implicit feedback and hybrid feedback.
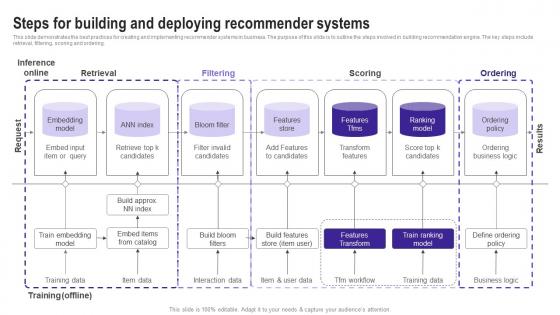
Steps For Building And Deploying Recommender Use Cases Of Filtering Methods Clipart Pdf
This slide demonstrates the best practices for creating and implementing recommender systems in business. The purpose of this slide is to outline the steps involved in building recommendation engine. The key steps include retrieval, filtering, scoring and ordering. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Steps For Building And Deploying Recommender Use Cases Of Filtering Methods Clipart Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide demonstrates the best practices for creating and implementing recommender systems in business. The purpose of this slide is to outline the steps involved in building recommendation engine. The key steps include retrieval, filtering, scoring and ordering.

Key Characteristics Of Modern ZTNA Solution Zero Trust Network Security Formats Pdf
This slide outlines the top features that a modern ZTNA model should include. This slide highlights the characteristics of modern ZTNA solutions, including data loss prevention, scalable performance, granular visibility and reporting, BYOD deployment options, advanced threat protection, and SASE offering. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Key Characteristics Of Modern ZTNA Solution Zero Trust Network Security Formats Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide outlines the top features that a modern ZTNA model should include. This slide highlights the characteristics of modern ZTNA solutions, including data loss prevention, scalable performance, granular visibility and reporting, BYOD deployment options, advanced threat protection, and SASE offering.
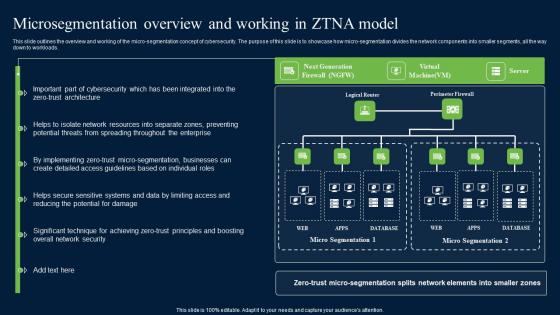
Microsegmentation Overview And Working In ZTNA Zero Trust Network Security Diagrams Pdf
This slide outlines the overview and working of the micro-segmentation concept of cybersecurity. The purpose of this slide is to showcase how micro-segmentation divides the network components into smaller segments, all the way down to workloads. Explore a selection of the finest Microsegmentation Overview And Working In ZTNA Zero Trust Network Security Diagrams Pdf here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Microsegmentation Overview And Working In ZTNA Zero Trust Network Security Diagrams Pdf to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide outlines the overview and working of the micro-segmentation concept of cybersecurity. The purpose of this slide is to showcase how micro-segmentation divides the network components into smaller segments, all the way down to workloads.

On Ramp Option 1 User And Device Identity Zero Trust Network Security Mockup Pdf
This slide outlines the first on-ramp option of zero trust network access implementation, which is user and device identity. The purpose of this slide is to give an overview of the method, including the practices and technologies involved, such as biometrics, MFA, IAM, device certification and so on. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download On Ramp Option 1 User And Device Identity Zero Trust Network Security Mockup Pdf from Slidegeeks and deliver a wonderful presentation. This slide outlines the first on-ramp option of zero trust network access implementation, which is user and device identity. The purpose of this slide is to give an overview of the method, including the practices and technologies involved, such as biometrics, MFA, IAM, device certification and so on.
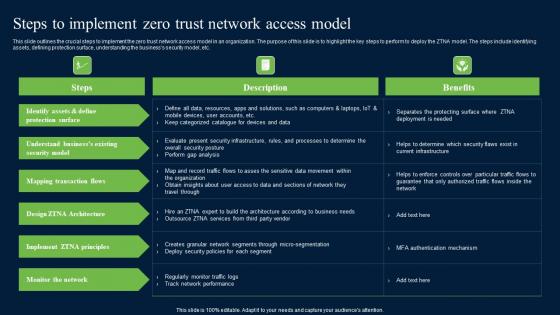
Steps To Implement Zero Trust Network Access Model Zero Trust Network Security Inspiration Pdf
This slide outlines the crucial steps to implement the zero trust network access model in an organization. The purpose of this slide is to highlight the key steps to perform to deploy the ZTNA model. The steps include identifying assets, defining protection surface, understanding the businesss security model, etc. Get a simple yet stunning designed Steps To Implement Zero Trust Network Access Model Zero Trust Network Security Inspiration Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Steps To Implement Zero Trust Network Access Model Zero Trust Network Security Inspiration Pdf can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide outlines the crucial steps to implement the zero trust network access model in an organization. The purpose of this slide is to highlight the key steps to perform to deploy the ZTNA model. The steps include identifying assets, defining protection surface, understanding the businesss security model, etc.
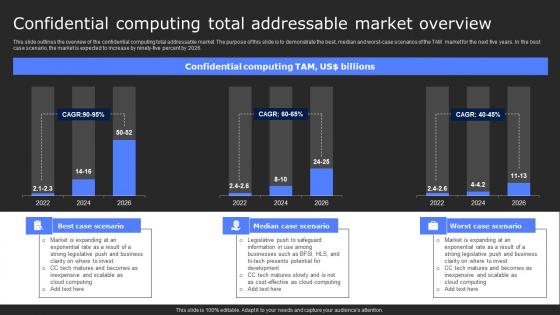
Confidential Computing Total Addressable Secure Computing Framework Themes Pdf
This slide outlines the overview of the confidential computing total addressable market. The purpose of this slide is to demonstrate the best, median and worst-case scenarios of the TAM market for the next five years. In the best case scenario, the market is expected to increase by ninety-five percent by 2026. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Confidential Computing Total Addressable Secure Computing Framework Themes Pdf from Slidegeeks and deliver a wonderful presentation. This slide outlines the overview of the confidential computing total addressable market. The purpose of this slide is to demonstrate the best, median and worst-case scenarios of the TAM market for the next five years. In the best case scenario, the market is expected to increase by ninety-five percent by 2026.
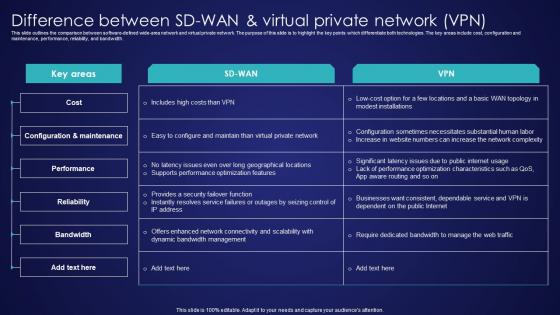
Difference Between SD Wan And Virtual Private Network Vpn Wide Area Network Services Template Pdf
This slide outlines the comparison between software-defined wide-area network and virtual private network. The purpose of this slide is to highlight the key points which differentiate both technologies. The key areas include cost, configuration and maintenance, performance, reliability, and bandwidth. Get a simple yet stunning designed Difference Between SD Wan And Virtual Private Network Vpn Wide Area Network Services Template Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Difference Between SD Wan And Virtual Private Network Vpn Wide Area Network Services Template Pdf can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide outlines the comparison between software-defined wide-area network and virtual private network. The purpose of this slide is to highlight the key points which differentiate both technologies. The key areas include cost, configuration and maintenance, performance, reliability, and bandwidth.

Local Marketing Overview Introduction To Niche Marketing Audience Segmentation Background Pdf
The following slide showcases brief outline of local marketing and some promotional tips to facilitate brand to connect with local communities. It includes elements such as offering printed materials, sponsoring sports events, organizing contests, suggestion box etc. Retrieve professionally designed Local Marketing Overview Introduction To Niche Marketing Audience Segmentation Background Pdf to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. The following slide showcases brief outline of local marketing and some promotional tips to facilitate brand to connect with local communities. It includes elements such as offering printed materials, sponsoring sports events, organizing contests, suggestion box etc.
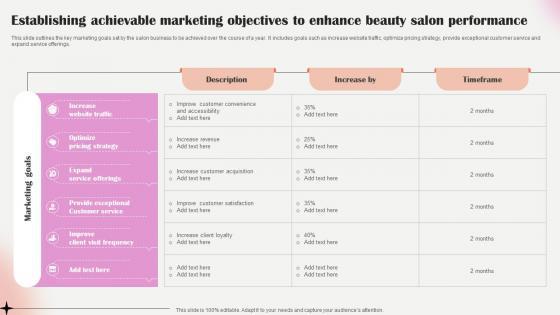
Salon Marketing Plan To Optimize Establishing Achievable Marketing Objectives Strategy SS V
This slide outlines the key marketing goals set by the salon business to be achieved over the course of a year. It includes goals such as increase website traffic, optimize pricing strategy, provide exceptional customer service and expand service offerings. Explore a selection of the finest Salon Marketing Plan To Optimize Establishing Achievable Marketing Objectives Strategy SS V here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Salon Marketing Plan To Optimize Establishing Achievable Marketing Objectives Strategy SS V to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide outlines the key marketing goals set by the salon business to be achieved over the course of a year. It includes goals such as increase website traffic, optimize pricing strategy, provide exceptional customer service and expand service offerings.
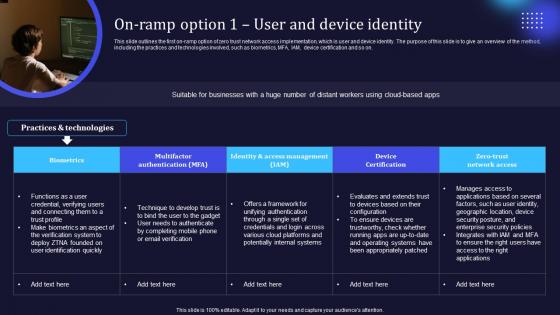
Zero Trust Model On Ramp Option 1 User And Device Identity
This slide outlines the first on-ramp option of zero trust network access implementation, which is user and device identity. The purpose of this slide is to give an overview of the method, including the practices and technologies involved, such as biometrics, MFA, IAM, device certification and so on. Retrieve professionally designed Zero Trust Model On Ramp Option 1 User And Device Identity to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide outlines the first on-ramp option of zero trust network access implementation, which is user and device identity. The purpose of this slide is to give an overview of the method, including the practices and technologies involved, such as biometrics, MFA, IAM, device certification and so on.

Zero Trust Model Step 3 Assess The Environment
This slide outlines the third step of ZTNA deployment, which is assessing the environment. The purpose of this slide is to highlight the questions that should be answered to evaluate the ecosystem and the questions include knowing the security controls, knowledge gaps and so on. Get a simple yet stunning designed Zero Trust Model Step 3 Assess The Environment. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Zero Trust Model Step 3 Assess The Environment can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide outlines the third step of ZTNA deployment, which is assessing the environment. The purpose of this slide is to highlight the questions that should be answered to evaluate the ecosystem and the questions include knowing the security controls, knowledge gaps and so on.

Zero Trust Model Working Of Zero Trust Network Access Model
This slide outlines the working of zero trust network access. The purpose of this slide is to demonstrate the workflow of ZTNA, including the principles shared by all ZTNA architectures. The principles include no use of MPLS, hiding the IP addresses, securing devices, IDP and SSO platform, and so on. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Zero Trust Model Working Of Zero Trust Network Access Model to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide outlines the working of zero trust network access. The purpose of this slide is to demonstrate the workflow of ZTNA, including the principles shared by all ZTNA architectures. The principles include no use of MPLS, hiding the IP addresses, securing devices, IDP and SSO platform, and so on.

Zero Trust Model Zero Trust Network Access Architecture Workflow
This slide outlines the workflow of zero trust network access architecture. The purpose of this slide is to showcase the various steps of the ZTNA model workflow, including user authentication, grant access, monitoring of user sessions, and threat response. Explore a selection of the finest Zero Trust Model Zero Trust Network Access Architecture Workflow here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Zero Trust Model Zero Trust Network Access Architecture Workflow to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide outlines the workflow of zero trust network access architecture. The purpose of this slide is to showcase the various steps of the ZTNA model workflow, including user authentication, grant access, monitoring of user sessions, and threat response.
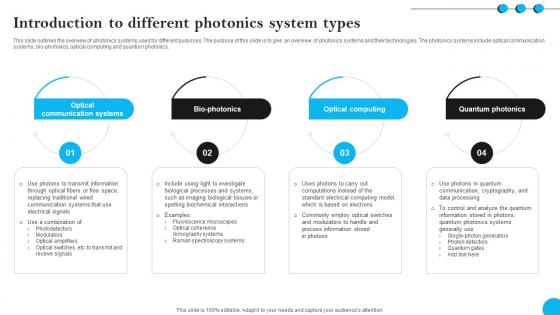
Fibers IT Introduction To Different Photonics System Types
This slide outlines the overview of photonics systems used for different purposes. The purpose of this slide is to give an overview of photonics systems and their technologies. The photonics systems include optical communication systems, bio-photonics, optical computing and quantum photonics. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Fibers IT Introduction To Different Photonics System Types to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide outlines the overview of photonics systems used for different purposes. The purpose of this slide is to give an overview of photonics systems and their technologies. The photonics systems include optical communication systems, bio-photonics, optical computing and quantum photonics.
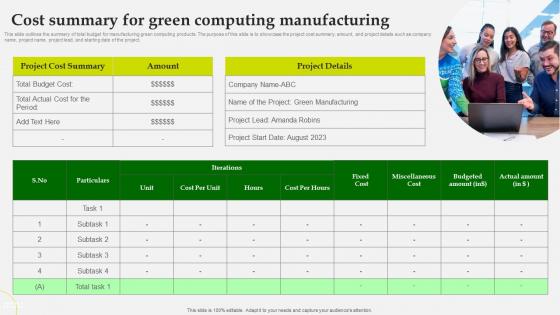
Green Computing Cost Summary For Green Computing Manufacturing
This slide outlines the summary of total budget for manufacturing green computing products. The purpose of this slide is to showcase the project cost summary, amount, and project details such as company name, project name, project lead, and starting date of the project. Get a simple yet stunning designed Green Computing Cost Summary For Green Computing Manufacturing It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Green Computing Cost Summary For Green Computing Manufacturing can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide outlines the summary of total budget for manufacturing green computing products. The purpose of this slide is to showcase the project cost summary, amount, and project details such as company name, project name, project lead, and starting date of the project.

Sustainable Green Computing Design Overview And Features
This slide outlines the overview of green design in green computing and its various aspects of it. The purpose of this slide is to give an overview of green design and its features, including product longevity, size, modularity, end-of-life, and packaging. Retrieve professionally designed Sustainable Green Computing Design Overview And Features to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide outlines the overview of green design in green computing and its various aspects of it. The purpose of this slide is to give an overview of green design and its features, including product longevity, size, modularity, end-of-life, and packaging.
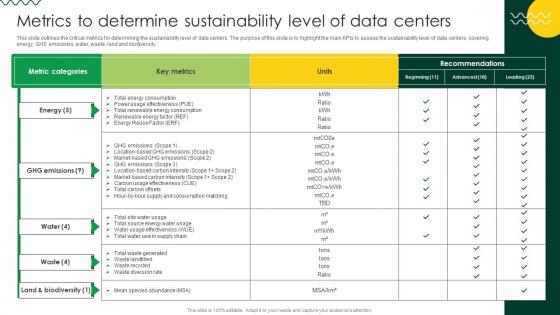
Sustainable Metrics To Determine Sustainability Level Of Data Centers
This slide outlines the critical metrics for determining the sustainability level of data centers. The purpose of this slide is to highlight the main KPIs to assess the sustainability level of data centers, covering energy, GHS emissions, water, waste, land and biodiversity. Get a simple yet stunning designed Sustainable Metrics To Determine Sustainability Level Of Data Centers. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Sustainable Metrics To Determine Sustainability Level Of Data Centers can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide outlines the critical metrics for determining the sustainability level of data centers. The purpose of this slide is to highlight the main KPIs to assess the sustainability level of data centers, covering energy, GHS emissions, water, waste, land and biodiversity.
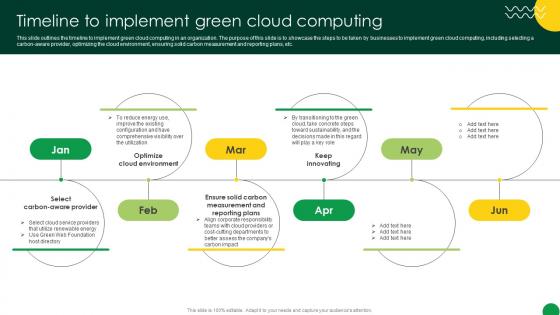
Sustainable Timeline To Implement Green Cloud Computing
This slide outlines the timeline to implement green cloud computing in an organization. The purpose of this slide is to showcase the steps to be taken by businesses to implement green cloud computing, including selecting a carbon-aware provider, optimizing the cloud environment, ensuring solid carbon measurement and reporting plans, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Sustainable Timeline To Implement Green Cloud Computing to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide outlines the timeline to implement green cloud computing in an organization. The purpose of this slide is to showcase the steps to be taken by businesses to implement green cloud computing, including selecting a carbon-aware provider, optimizing the cloud environment, ensuring solid carbon measurement and reporting plans, etc.

Key Characteristics Of Modern Ztna Solution Software Defined Perimeter SDP
This slide outlines the top features that a modern ZTNA model should include. This slide highlights the characteristics of modern ZTNA solutions, including data loss prevention, scalable performance, granular visibility and reporting, BYOD deployment options, advanced threat protection, and SASE offering. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Key Characteristics Of Modern Ztna Solution Software Defined Perimeter SDP to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide outlines the top features that a modern ZTNA model should include. This slide highlights the characteristics of modern ZTNA solutions, including data loss prevention, scalable performance, granular visibility and reporting, BYOD deployment options, advanced threat protection, and SASE offering.
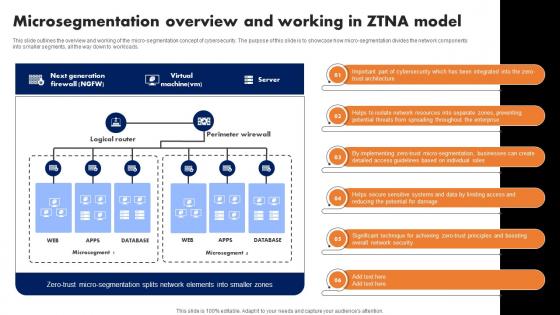
Microsegmentation Overview And Working In Ztna Model Software Defined Perimeter SDP
This slide outlines the overview and working of the micro-segmentation concept of cybersecurity. The purpose of this slide is to showcase how micro-segmentation divides the network components into smaller segments, all the way down to workloads. Explore a selection of the finest Microsegmentation Overview And Working In Ztna Model Software Defined Perimeter SDP here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Microsegmentation Overview And Working In Ztna Model Software Defined Perimeter SDP to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide outlines the overview and working of the micro-segmentation concept of cybersecurity. The purpose of this slide is to showcase how micro-segmentation divides the network components into smaller segments, all the way down to workloads.
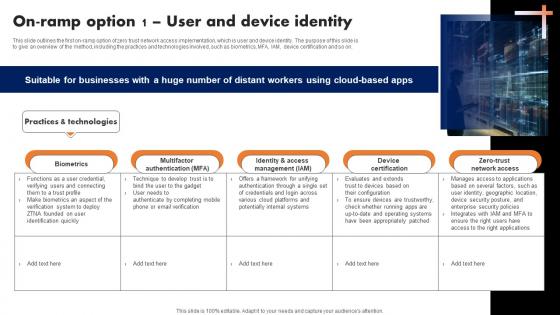
On Ramp Option 1 User And Device Identity Software Defined Perimeter SDP
This slide outlines the first on-ramp option of zero trust network access implementation, which is user and device identity. The purpose of this slide is to give an overview of the method, including the practices and technologies involved, such as biometrics, MFA, IAM, device certification and so on. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download On Ramp Option 1 User And Device Identity Software Defined Perimeter SDP from Slidegeeks and deliver a wonderful presentation. This slide outlines the first on-ramp option of zero trust network access implementation, which is user and device identity. The purpose of this slide is to give an overview of the method, including the practices and technologies involved, such as biometrics, MFA, IAM, device certification and so on.

Step 6 And 7 Define Operational Changes And Implement Rinse Repeat Software Defined Perimeter SDP
This slide outlines the sixth and seventh steps for ZTNA implementation, which are defining operational changes and implementing, rinsing and repeating the process. The purpose of this slide is to showcase the following steps in zero trust model deployment. Get a simple yet stunning designed Step 6 And 7 Define Operational Changes And Implement Rinse Repeat Software Defined Perimeter SDP. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Step 6 And 7 Define Operational Changes And Implement Rinse Repeat Software Defined Perimeter SDP can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide outlines the sixth and seventh steps for ZTNA implementation, which are defining operational changes and implementing, rinsing and repeating the process. The purpose of this slide is to showcase the following steps in zero trust model deployment.
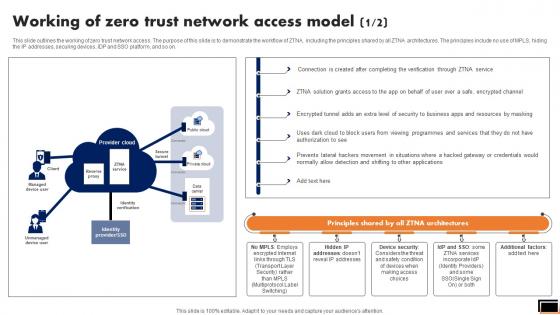
Working Of Zero Trust Network Access Model Software Defined Perimeter SDP
This slide outlines the working of zero trust network access. The purpose of this slide is to demonstrate the workflow of ZTNA, including the principles shared by all ZTNA architectures. The principles include no use of MPLS, hiding the IP addresses, securing devices, IDP and SSO platform, and so on. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Working Of Zero Trust Network Access Model Software Defined Perimeter SDP to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide outlines the working of zero trust network access. The purpose of this slide is to demonstrate the workflow of ZTNA, including the principles shared by all ZTNA architectures. The principles include no use of MPLS, hiding the IP addresses, securing devices, IDP and SSO platform, and so on.

Zero Trust Network Access Architecture Workflow Software Defined Perimeter SDP
This slide outlines the workflow of zero trust network access architecture. The purpose of this slide is to showcase the various steps of the ZTNA model workflow, including user authentication, grant access, monitoring of user sessions, and threat response. Explore a selection of the finest Zero Trust Network Access Architecture Workflow Software Defined Perimeter SDP here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Zero Trust Network Access Architecture Workflow Software Defined Perimeter SDP to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide outlines the workflow of zero trust network access architecture. The purpose of this slide is to showcase the various steps of the ZTNA model workflow, including user authentication, grant access, monitoring of user sessions, and threat response.

Key Benefits For Samsung Artik Customers Exploring Google Cloud IoT Platform
This slide outlines the various advantages for customers of Samsung ARTIK. The purpose of this slide is to highlight the key benefits for Samsung ARTIK customers which include quicker pace, amplified speed of application, etc. Retrieve professionally designed Key Benefits For Samsung Artik Customers Exploring Google Cloud IoT Platform to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide outlines the various advantages for customers of Samsung ARTIK. The purpose of this slide is to highlight the key benefits for Samsung ARTIK customers which include quicker pace, amplified speed of application, etc.
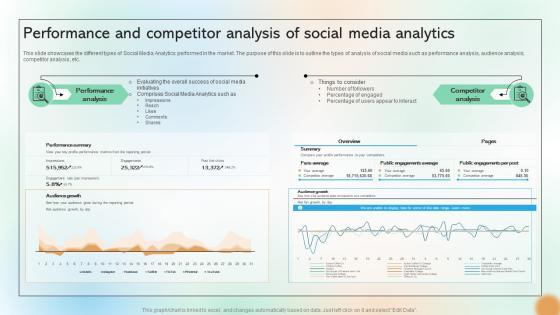
Performance And Competitor Analysis Of Social Media Analytics Cracking The Code Of Social Media
This slide showcases the different types of Social Media Analytics performed in the market. The purpose of this slide is to outline the types of analysis of social media such as performance analysis, audience analysis, competitor analysis, etc. Get a simple yet stunning designed Performance And Competitor Analysis Of Social Media Analytics Cracking The Code Of Social Media. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Performance And Competitor Analysis Of Social Media Analytics Cracking The Code Of Social Media can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide showcases the different types of Social Media Analytics performed in the market. The purpose of this slide is to outline the types of analysis of social media such as performance analysis, audience analysis, competitor analysis, etc.

Third Party Tools For Resource Maximization In Social Media Cracking The Code Of Social Media
This slide outlines the third party tools for resource maximization in social media. The purpose of this slide is to highlight the third party tools for resource maximization such as artificial intelligence, chatbots, interactive voice response, etc. Get a simple yet stunning designed Third Party Tools For Resource Maximization In Social Media Cracking The Code Of Social Media. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Third Party Tools For Resource Maximization In Social Media Cracking The Code Of Social Media can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide outlines the third party tools for resource maximization in social media. The purpose of this slide is to highlight the third party tools for resource maximization such as artificial intelligence, chatbots, interactive voice response, etc.
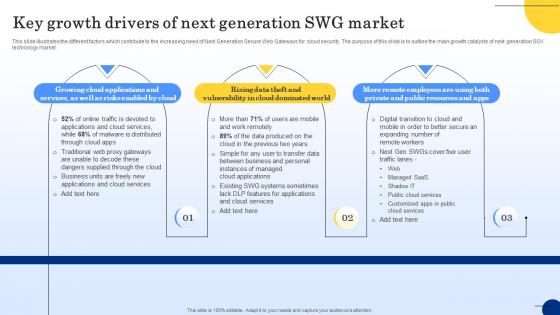
Key Growth Drivers Of Next Generation SWG Market Web Threat Protection System
This slide illustrates the different factors which contribute to the increasing need of Next Generation Secure Web Gateways for cloud security. The purpose of this slide is to outline the main growth catalysts of next generation SGV technology market. Explore a selection of the finest Key Growth Drivers Of Next Generation SWG Market Web Threat Protection System here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Key Growth Drivers Of Next Generation SWG Market Web Threat Protection System to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide illustrates the different factors which contribute to the increasing need of Next Generation Secure Web Gateways for cloud security. The purpose of this slide is to outline the main growth catalysts of next generation SGV technology market.

Prominent Users Of Secure Web Gateway Web Threat Protection System
This slide outlines the various Secure Web Gateway clients. The purpose of this slide is to explain how different users are utilizing SWG in their organizations. These are IT security experts, network administrators, compliance officers, HR managers, etc. Retrieve professionally designed Prominent Users Of Secure Web Gateway Web Threat Protection System to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide outlines the various Secure Web Gateway clients. The purpose of this slide is to explain how different users are utilizing SWG in their organizations. These are IT security experts, network administrators, compliance officers, HR managers, etc.
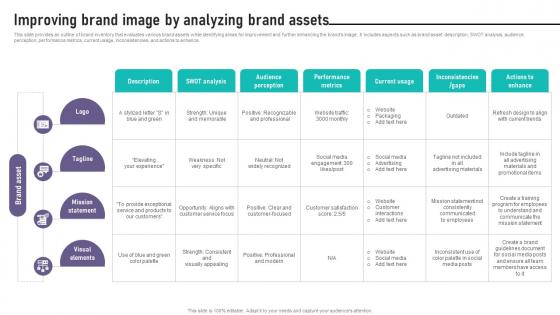
Brand Equity Management To Raise Recognition Improving Brand Image By Analyzing
This slide provides an outline of brand inventory that evaluates various brand assets while identifying areas for improvement and further enhancing the brands image. It includes aspects such as brand asset, description, SWOT analysis, audience perception, performance metrics, current usage, inconsistencies, and actions to enhance. Get a simple yet stunning designed Brand Equity Management To Raise Recognition Improving Brand Image By Analyzing. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Brand Equity Management To Raise Recognition Improving Brand Image By Analyzing can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide provides an outline of brand inventory that evaluates various brand assets while identifying areas for improvement and further enhancing the brands image. It includes aspects such as brand asset, description, SWOT analysis, audience perception, performance metrics, current usage, inconsistencies, and actions to enhance.
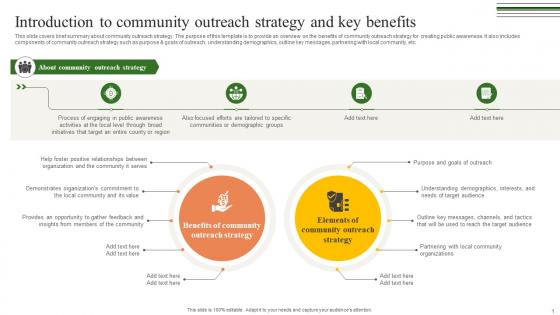
Introduction To Community Outreach Building A Winning Community Outreach Strategy SS V
This slide covers brief summary about community outreach strategy. The purpose of this template is to provide an overview on the benefits of community outreach strategy for creating public awareness. It also includes components of community outreach strategy such as purpose and goals of outreach, understanding demographics, outline key messages, partnering with local community, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Introduction To Community Outreach Building A Winning Community Outreach Strategy SS V to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide covers brief summary about community outreach strategy. The purpose of this template is to provide an overview on the benefits of community outreach strategy for creating public awareness. It also includes components of community outreach strategy such as purpose and goals of outreach, understanding demographics, outline key messages, partnering with local community, etc.
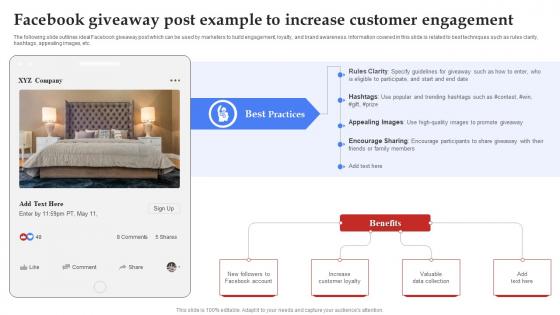
Facebook Marketing Plan Facebook Giveaway Post Example To Increase Strategy SS V
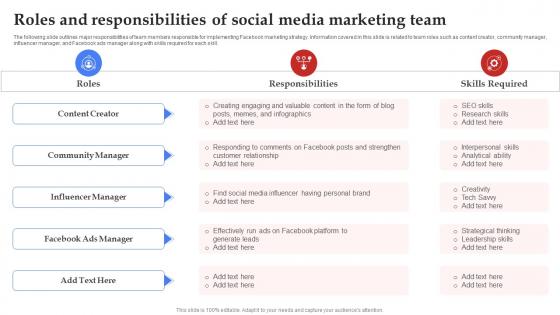
Facebook Marketing Plan For Ecommerce Roles And Responsibilities Of Social Strategy SS V
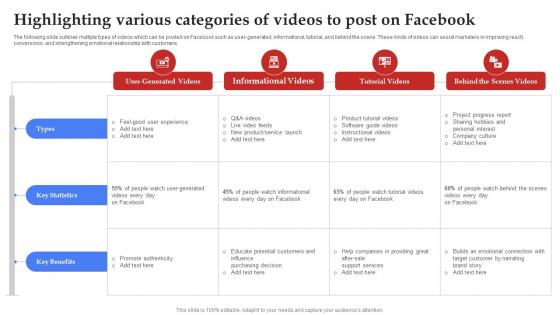
Facebook Marketing Plan Highlighting Various Categories Of Videos To Post Strategy SS V
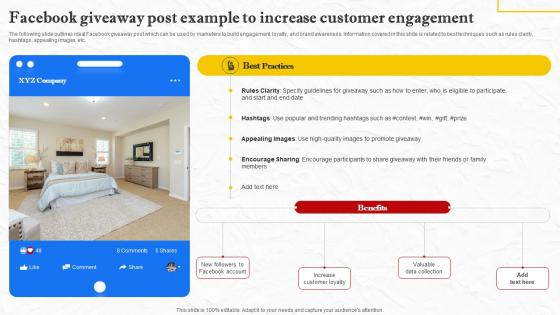
Facebook Marketing Techniques Facebook Giveaway Post Example To Increase Strategy SS V
The following slide outlines ideal Facebook giveaway post which can be used by marketers to build engagement, loyalty, and brand awareness. Information covered in this slide is related to best techniques such as rules clarity, hashtags, appealing images, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Facebook Marketing Techniques Facebook Giveaway Post Example To Increase Strategy SS V to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. The following slide outlines ideal Facebook giveaway post which can be used by marketers to build engagement, loyalty, and brand awareness. Information covered in this slide is related to best techniques such as rules clarity, hashtags, appealing images, etc.
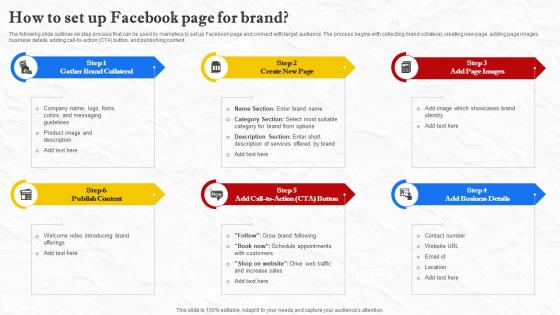
Facebook Marketing Techniques How To Set Up Facebook Page For Brand Strategy SS V
The following slide outlines six step process that can be used by marketers to set up Facebook page and connect with target audience. The process begins with collecting brand collateral, creating new page, adding page images, business details, adding call-to-action CTA button, and publishing content. Retrieve professionally designed Facebook Marketing Techniques How To Set Up Facebook Page For Brand Strategy SS V to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. The following slide outlines six step process that can be used by marketers to set up Facebook page and connect with target audience. The process begins with collecting brand collateral, creating new page, adding page images, business details, adding call-to-action CTA button, and publishing content.
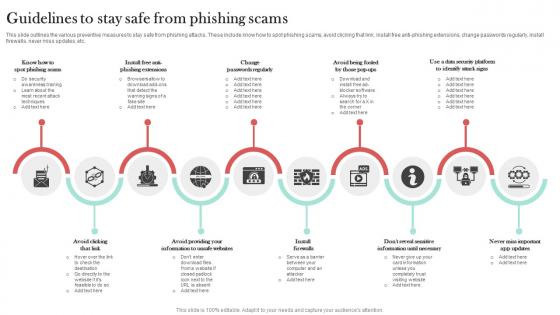
Guidelines To Stay Safe From Phishing Scams Man In The Middle Phishing IT
This slide outlines the various preventive measures to stay safe from phishing attacks. These include know how to spot phishing scams, avoid clicking that link, install free anti-phishing extensions, change passwords regularly, install firewalls, never miss updates, etc. Explore a selection of the finest Guidelines To Stay Safe From Phishing Scams Man In The Middle Phishing IT here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Guidelines To Stay Safe From Phishing Scams Man In The Middle Phishing IT to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide outlines the various preventive measures to stay safe from phishing attacks. These include know how to spot phishing scams, avoid clicking that link, install free anti-phishing extensions, change passwords regularly, install firewalls, never miss updates, etc.
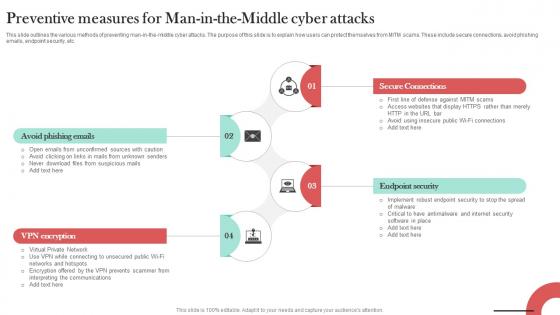
Preventive Measures For Man In The Middle Man In The Middle Phishing IT
This slide outlines the various methods of preventing man-in-the-middle cyber attacks. The purpose of this slide is to explain how users can protect themselves from MITM scams. These include secure connections, avoid phishing emails, endpoint security, etc. Get a simple yet stunning designed Preventive Measures For Man In The Middle Man In The Middle Phishing IT. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Preventive Measures For Man In The Middle Man In The Middle Phishing IT can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide outlines the various methods of preventing man-in-the-middle cyber attacks. The purpose of this slide is to explain how users can protect themselves from MITM scams. These include secure connections, avoid phishing emails, endpoint security, etc.
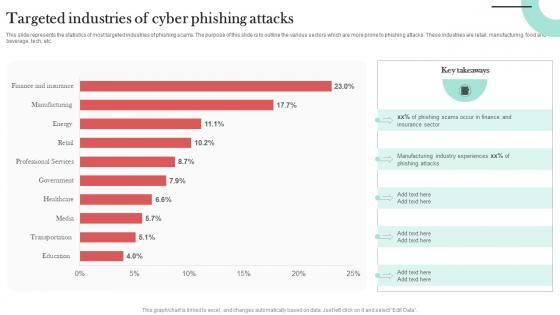
Targeted Industries Of Cyber Phishing Man In The Middle Phishing IT
This slide represents the statistics of most targeted industries of phishing scams. The purpose of this slide is to outline the various sectors which are more prone to phishing attacks. These industries are retail, manufacturing, food and beverage, tech, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Targeted Industries Of Cyber Phishing Man In The Middle Phishing IT to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide represents the statistics of most targeted industries of phishing scams. The purpose of this slide is to outline the various sectors which are more prone to phishing attacks. These industries are retail, manufacturing, food and beverage, tech, etc.

Warning Signs Of Pop Up Phishing Scams Man In The Middle Phishing IT
This slide outlines the various warning signs which helps in identifying pop-up phishing cyber attacks. These include terrible pop-up advertisement, warnings to act fast, immediate scan of computer virus, pop-ups are difficult to close and unpopular company names. Retrieve professionally designed Warning Signs Of Pop Up Phishing Scams Man In The Middle Phishing IT to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide outlines the various warning signs which helps in identifying pop-up phishing cyber attacks. These include terrible pop-up advertisement, warnings to act fast, immediate scan of computer virus, pop-ups are difficult to close and unpopular company names.

Zero Trust Network Access Checklist To Build Zero Trust Network Access Architecture
This slide outlines the checklist to develop a zero-trust network access architecture. The purpose of this slide is to define the various measures organizations should take while building a ZTNA architecture. The measures include knowing the architecture, creating a strong device identity, and so on. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Zero Trust Network Access Checklist To Build Zero Trust Network Access Architecture to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide outlines the checklist to develop a zero-trust network access architecture. The purpose of this slide is to define the various measures organizations should take while building a ZTNA architecture. The measures include knowing the architecture, creating a strong device identity, and so on.

Zero Trust Network Access Roadmap To Implement Zero Trust Network Access Model


 Continue with Email
Continue with Email

 Home
Home


































