Team Hierarchy

In Depth Analysis Of Islamic Banking Overview Of Shariah Law And Its Role In Islamic Banking Elements PDF
This slide defines the details related to the Islamic religious law that governs aspects of daily life for Muslims and religious rituals. It includes details related to the Shariah law adopted by financial institutes such as banks. Get a simple yet stunning designed In Depth Analysis Of Islamic Banking Overview Of Shariah Law And Its Role In Islamic Banking Elements PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit In Depth Analysis Of Islamic Banking Overview Of Shariah Law And Its Role In Islamic Banking Elements PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide defines the details related to the Islamic religious law that governs aspects of daily life for Muslims and religious rituals. It includes details related to the Shariah law adopted by financial institutes such as banks.
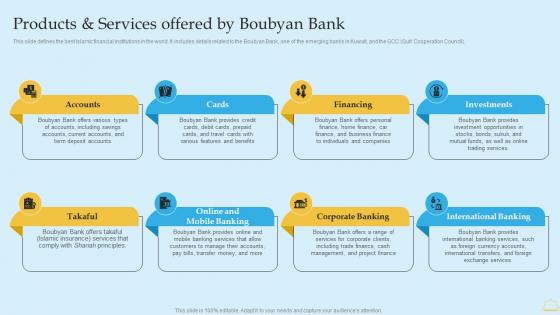
In Depth Analysis Of Islamic Banking Products And Services Offered By Boubyan Bank Rules PDF
This slide defines the best Islamic financial institutions in the world. It includes details related to the Boubyan Bank, one of the emerging banks in Kuwait, and the GCC Gulf Cooperation Council. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than In Depth Analysis Of Islamic Banking Products And Services Offered By Boubyan Bank Rules PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab In Depth Analysis Of Islamic Banking Products And Services Offered By Boubyan Bank Rules PDF today and make your presentation stand out from the rest. This slide defines the best Islamic financial institutions in the world. It includes details related to the Boubyan Bank, one of the emerging banks in Kuwait, and the GCC Gulf Cooperation Council.

Funding History Investor Funding Pitch Deck For Pinterests Expansion Portrait Pdf
This slide caters to the details related to the funding round announced by the company offering a visual bookmarking tool for saving and discovering creative ideas. It consists of information about IPO initial public offering, venture rounds, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Funding History Investor Funding Pitch Deck For Pinterests Expansion Portrait Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Funding History Investor Funding Pitch Deck For Pinterests Expansion Portrait Pdf today and make your presentation stand out from the rest. This slide caters to the details related to the funding round announced by the company offering a visual bookmarking tool for saving and discovering creative ideas. It consists of information about IPO initial public offering, venture rounds, etc.

Value Proposition Investor Funding Pitch Deck For Pinterests Expansion Infographics Pdf
This slide caters to the USP Unique Selling Proposition of the company offering image-sharing and social media services created to enable the saving and discovery of information on the internet using images, animated GIFs, and videos. Explore a selection of the finest Value Proposition Investor Funding Pitch Deck For Pinterests Expansion Infographics Pdf here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Value Proposition Investor Funding Pitch Deck For Pinterests Expansion Infographics Pdf to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide caters to the USP Unique Selling Proposition of the company offering image-sharing and social media services created to enable the saving and discovery of information on the internet using images, animated GIFs, and videos.
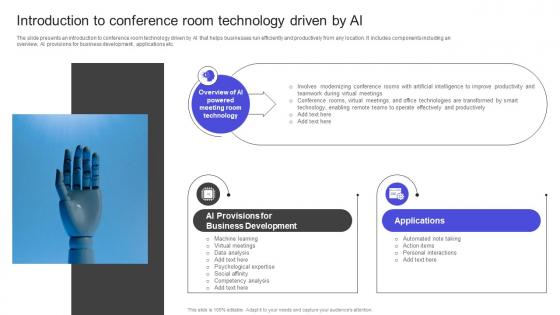
Strategies To Build Meaningful Introduction To Conference Room Technology Driven By Ai Pictures PDF
The slide presents an introduction to conference room technology driven by AI that helps businesses run efficiently and productively from any location. It includes components including an overview, AI provisions for business development , applications etc. This Strategies To Build Meaningful Introduction To Conference Room Technology Driven By Ai Pictures PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Strategies To Build Meaningful Introduction To Conference Room Technology Driven By Ai Pictures PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today The slide presents an introduction to conference room technology driven by AI that helps businesses run efficiently and productively from any location. It includes components including an overview, AI provisions for business development , applications etc.
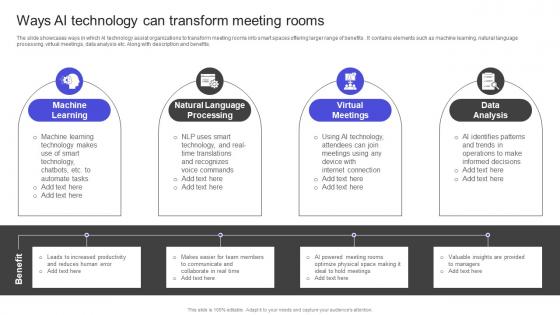
Strategies To Build Meaningful Ways Ai Technology Can Transform Meeting Rooms Summary PDF
The slide showcases ways in which AI technology assist organizations to transform meeting rooms into smart spaces offering larger range of benefits . It contains elements such as machine learning, natural language processing, virtual meetings, data analysis etc. Along with description and benefits. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Strategies To Build Meaningful Ways Ai Technology Can Transform Meeting Rooms Summary PDF With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Strategies To Build Meaningful Ways Ai Technology Can Transform Meeting Rooms Summary PDF today and make your presentation stand out from the rest The slide showcases ways in which AI technology assist organizations to transform meeting rooms into smart spaces offering larger range of benefits . It contains elements such as machine learning, natural language processing, virtual meetings, data analysis etc. Along with description and benefits.
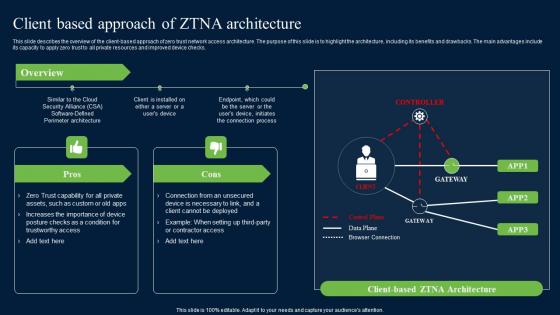
Client Based Approach Of ZTNA Zero Trust Network Security Demonstration Pdf
This slide describes the overview of the client-based approach of zero trust network access architecture. The purpose of this slide is to highlight the architecture, including its benefits and drawbacks. The main advantages include its capacity to apply zero trust to all private resources and improved device checks. Get a simple yet stunning designed Client Based Approach Of ZTNA Zero Trust Network Security Demonstration Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Client Based Approach Of ZTNA Zero Trust Network Security Demonstration Pdf can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide describes the overview of the client-based approach of zero trust network access architecture. The purpose of this slide is to highlight the architecture, including its benefits and drawbacks. The main advantages include its capacity to apply zero trust to all private resources and improved device checks.
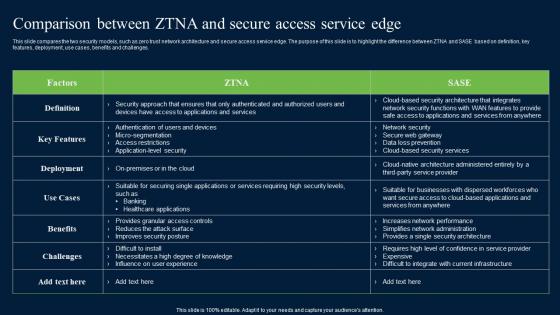
Comparison Between ZTNA And Secure Access Zero Trust Network Security Graphics Pdf
This slide compares the two security models, such as zero trust network architecture and secure access service edge. The purpose of this slide is to highlight the difference between ZTNA and SASE based on definition, key features, deployment, use cases, benefits and challenges. Slidegeeks is here to make your presentations a breeze with Comparison Between ZTNA And Secure Access Zero Trust Network Security Graphics Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide compares the two security models, such as zero trust network architecture and secure access service edge. The purpose of this slide is to highlight the difference between ZTNA and SASE based on definition, key features, deployment, use cases, benefits and challenges.

Critical Principles Of Zero Trust Network Access Security Formats Pdf
This slide illustrates the key principles of zero trust network access model, including their impact. The purpose of this slide is to highlight the primary principles of the ZTNA model, including least privilege access, micro-segmentation, MFA, device validation, and monitoring everything. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Critical Principles Of Zero Trust Network Access Security Formats Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Critical Principles Of Zero Trust Network Access Security Formats Pdf today and make your presentation stand out from the rest This slide illustrates the key principles of zero trust network access model, including their impact. The purpose of this slide is to highlight the primary principles of the ZTNA model, including least privilege access, micro-segmentation, MFA, device validation, and monitoring everything.
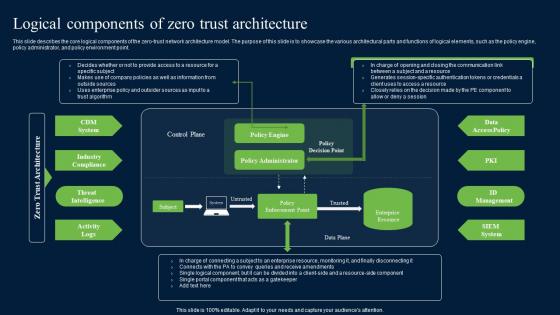
Logical Components Of Zero Trust Architecture Zero Trust Network Security Pictures Pdf
This slide describes the core logical components of the zero-trust network architecture model. The purpose of this slide is to showcase the various architectural parts and functions of logical elements, such as the policy engine, policy administrator, and policy environment point. This Logical Components Of Zero Trust Architecture Zero Trust Network Security Pictures Pdf is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Logical Components Of Zero Trust Architecture Zero Trust Network Security Pictures Pdf features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide describes the core logical components of the zero-trust network architecture model. The purpose of this slide is to showcase the various architectural parts and functions of logical elements, such as the policy engine, policy administrator, and policy environment point.
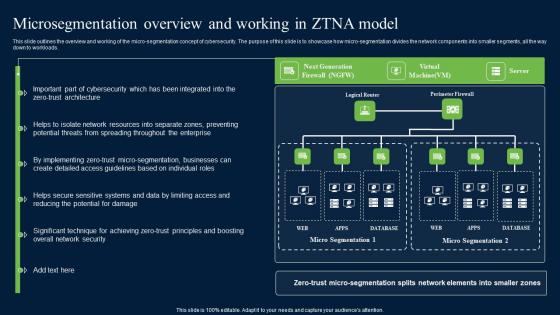
Microsegmentation Overview And Working In ZTNA Zero Trust Network Security Diagrams Pdf
This slide outlines the overview and working of the micro-segmentation concept of cybersecurity. The purpose of this slide is to showcase how micro-segmentation divides the network components into smaller segments, all the way down to workloads. Explore a selection of the finest Microsegmentation Overview And Working In ZTNA Zero Trust Network Security Diagrams Pdf here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Microsegmentation Overview And Working In ZTNA Zero Trust Network Security Diagrams Pdf to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide outlines the overview and working of the micro-segmentation concept of cybersecurity. The purpose of this slide is to showcase how micro-segmentation divides the network components into smaller segments, all the way down to workloads.

On Ramp Option 2 Applications And Data Zero Trust Network Security Sample Pdf
This slide describes the second on-ramp option, which is the applications and data of ZTNA implementation. The purpose of this slide is to give an overview of practices and technologies used in this approach, such as data classification, data loss prevention, authentication and authorization of microservices, container security, etc. The On Ramp Option 2 Applications And Data Zero Trust Network Security Sample Pdf is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide describes the second on-ramp option, which is the applications and data of ZTNA implementation. The purpose of this slide is to give an overview of practices and technologies used in this approach, such as data classification, data loss prevention, authentication and authorization of microservices, container security, etc.
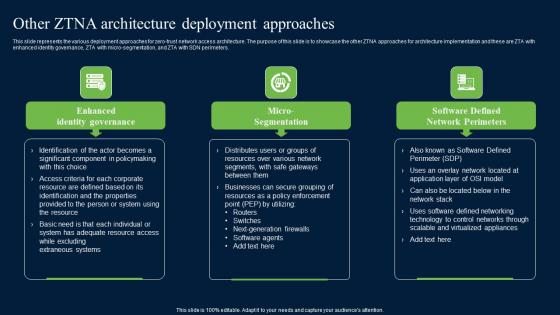
Other ZTNA Architecture Deployment Approaches Zero Trust Network Security Introduction Pdf
This slide represents the various deployment approaches for zero-trust network access architecture. The purpose of this slide is to showcase the other ZTNA approaches for architecture implementation and these are ZTA with enhanced identity governance, ZTA with micro-segmentation, and ZTA with SDN perimeters. Retrieve professionally designed Other ZTNA Architecture Deployment Approaches Zero Trust Network Security Introduction Pdf to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide represents the various deployment approaches for zero-trust network access architecture. The purpose of this slide is to showcase the other ZTNA approaches for architecture implementation and these are ZTA with enhanced identity governance, ZTA with micro-segmentation, and ZTA with SDN perimeters.
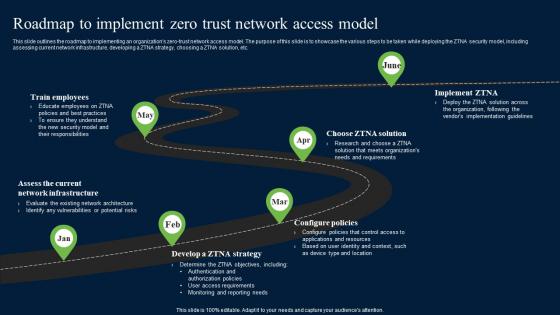
Roadmap To Implement Zero Trust Network Access Model Zero Trust Network Security Graphics Pdf
This slide outlines the roadmap to implementing an organizations zero-trust network access model. The purpose of this slide is to showcase the various steps to be taken while deploying the ZTNA security model, including assessing current network infrastructure, developing a ZTNA strategy, choosing a ZTNA solution, etc. This Roadmap To Implement Zero Trust Network Access Model Zero Trust Network Security Graphics Pdf from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide outlines the roadmap to implementing an organizations zero-trust network access model. The purpose of this slide is to showcase the various steps to be taken while deploying the ZTNA security model, including assessing current network infrastructure, developing a ZTNA strategy, choosing a ZTNA solution, etc.
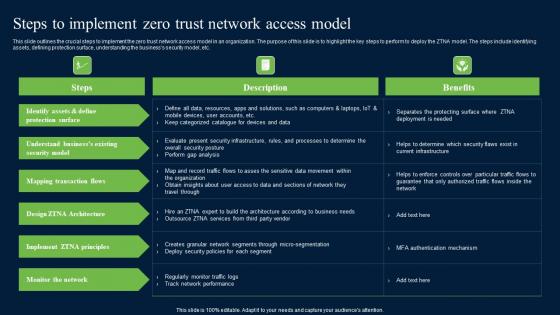
Steps To Implement Zero Trust Network Access Model Zero Trust Network Security Inspiration Pdf
This slide outlines the crucial steps to implement the zero trust network access model in an organization. The purpose of this slide is to highlight the key steps to perform to deploy the ZTNA model. The steps include identifying assets, defining protection surface, understanding the businesss security model, etc. Get a simple yet stunning designed Steps To Implement Zero Trust Network Access Model Zero Trust Network Security Inspiration Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Steps To Implement Zero Trust Network Access Model Zero Trust Network Security Inspiration Pdf can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide outlines the crucial steps to implement the zero trust network access model in an organization. The purpose of this slide is to highlight the key steps to perform to deploy the ZTNA model. The steps include identifying assets, defining protection surface, understanding the businesss security model, etc.

Zero Trust Network Access User Flow Overview Download Pdf
This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office. Slidegeeks is here to make your presentations a breeze with Zero Trust Network Access User Flow Overview Download Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office.
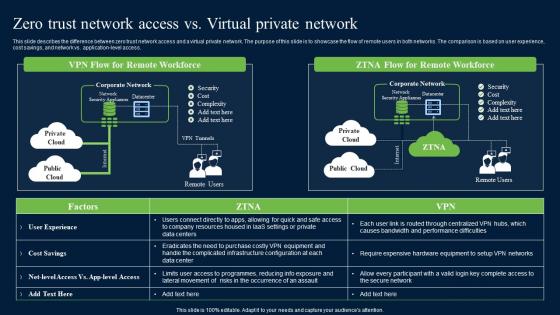
Zero Trust Network Access Vs Virtual Private Network Mockup Pdf
This slide describes the difference between zero trust network access and a virtual private network. The purpose of this slide is to showcase the flow of remote users in both networks. The comparison is based on user experience, cost savings, and network vs. application-level access. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Zero Trust Network Access Vs Virtual Private Network Mockup Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Zero Trust Network Access Vs Virtual Private Network Mockup Pdf today and make your presentation stand out from the rest This slide describes the difference between zero trust network access and a virtual private network. The purpose of this slide is to showcase the flow of remote users in both networks. The comparison is based on user experience, cost savings, and network vs. application-level access.
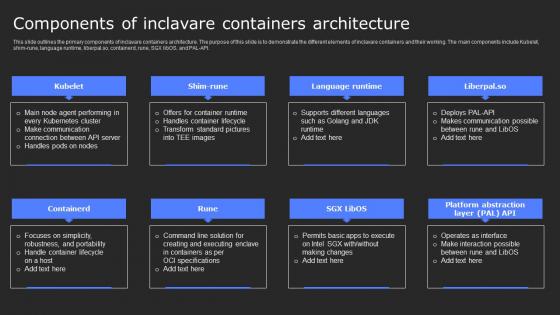
Components Of Inclavare Containers Secure Computing Framework Professional Pdf
This slide outlines the primary components of inclavare containers architecture. The purpose of this slide is to demonstrate the different elements of inclavare containers and their working. The main components include Kubelet, shim-rune, language runtime, liberpal.so, containerd, rune, SGX libOS, and PAL-API. Slidegeeks is here to make your presentations a breeze with Components Of Inclavare Containers Secure Computing Framework Professional Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide outlines the primary components of inclavare containers architecture. The purpose of this slide is to demonstrate the different elements of inclavare containers and their working. The main components include Kubelet, shim-rune, language runtime, liberpal.so, containerd, rune, SGX libOS, and PAL-API.
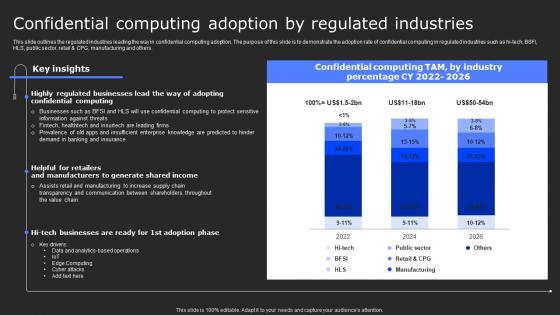
Confidential Computing Adoption By Secure Computing Framework Mockup Pdf
This slide outlines the regulated industries leading the way in confidential computing adoption. The purpose of this slide is to demonstrate the adoption rate of confidential computing in regulated industries such as hi-tech, BSFI, HLS, public sector, retail and CPG, manufacturing and others. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Confidential Computing Adoption By Secure Computing Framework Mockup Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Confidential Computing Adoption By Secure Computing Framework Mockup Pdf today and make your presentation stand out from the rest This slide outlines the regulated industries leading the way in confidential computing adoption. The purpose of this slide is to demonstrate the adoption rate of confidential computing in regulated industries such as hi-tech, BSFI, HLS, public sector, retail and CPG, manufacturing and others.
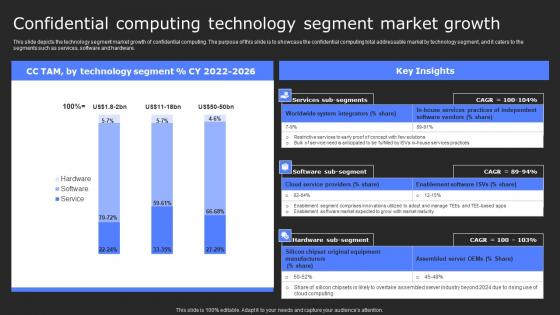
Confidential Computing Technology Segment Secure Computing Framework Diagrams Pdf
This slide depicts the technology segment market growth of confidential computing. The purpose of this slide is to showcase the confidential computing total addressable market by technology segment, and it caters to the segments such as services, software and hardware. Explore a selection of the finest Confidential Computing Technology Segment Secure Computing Framework Diagrams Pdf here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Confidential Computing Technology Segment Secure Computing Framework Diagrams Pdf to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide depicts the technology segment market growth of confidential computing. The purpose of this slide is to showcase the confidential computing total addressable market by technology segment, and it caters to the segments such as services, software and hardware.
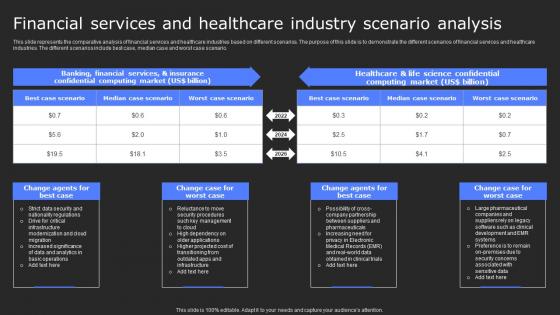
Financial Services And Healthcare Industry Scenario Secure Computing Framework Clipart Pdf
This slide represents the comparative analysis of financial services and healthcare industries based on different scenarios. The purpose of this slide is to demonstrate the different scenarios of financial services and healthcare industries. The different scenarios include best case, median case and worst case scenario. Retrieve professionally designed Financial Services And Healthcare Industry Scenario Secure Computing Framework Clipart Pdf to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide represents the comparative analysis of financial services and healthcare industries based on different scenarios. The purpose of this slide is to demonstrate the different scenarios of financial services and healthcare industries. The different scenarios include best case, median case and worst case scenario.
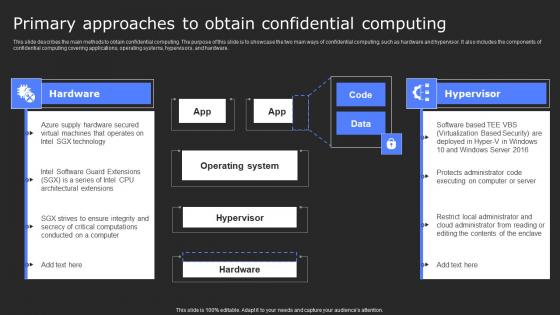
Primary Approaches To Obtain Confidential Computing Secure Computing Framework Graphics Pdf
This slide describes the main methods to obtain confidential computing. The purpose of this slide is to showcase the two main ways of confidential computing, such as hardware and hypervisor. It also includes the components of confidential computing covering applications, operating systems, hypervisors, and hardware. Slidegeeks is here to make your presentations a breeze with Primary Approaches To Obtain Confidential Computing Secure Computing Framework Graphics Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide describes the main methods to obtain confidential computing. The purpose of this slide is to showcase the two main ways of confidential computing, such as hardware and hypervisor. It also includes the components of confidential computing covering applications, operating systems, hypervisors, and hardware.
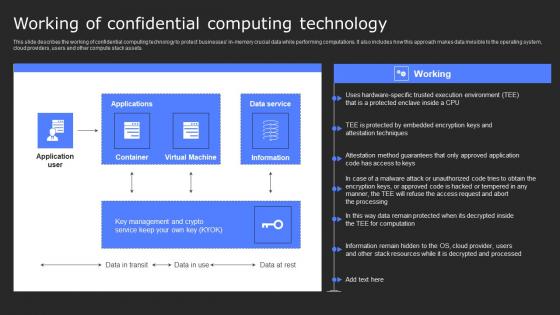
Working Of Confidential Computing Technology Secure Computing Framework Diagrams Pdf
This slide describes the working of confidential computing technology to protect businesses in-memory crucial data while performing computations. It also includes how this approach makes data invisible to the operating system, cloud providers, users and other compute stack assets. Slidegeeks is here to make your presentations a breeze with Working Of Confidential Computing Technology Secure Computing Framework Diagrams Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide describes the working of confidential computing technology to protect businesses in-memory crucial data while performing computations. It also includes how this approach makes data invisible to the operating system, cloud providers, users and other compute stack assets.
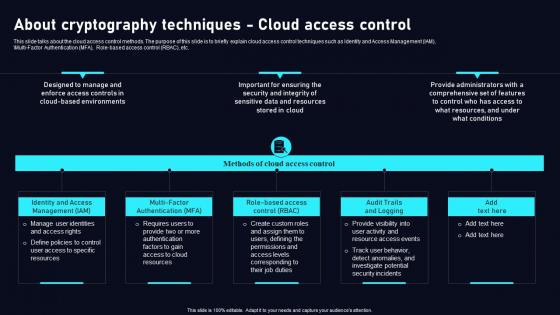
About Cryptography Techniques Cloud Data Security Using Cryptography Background Pdf
This slide talks about the cloud access control methods. The purpose of this slide is to briefly explain cloud access control techniques such as Identity and Access Management IAM, Multi Factor Authentication MFA, Role based access control RBAC, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than About Cryptography Techniques Cloud Data Security Using Cryptography Background Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab About Cryptography Techniques Cloud Data Security Using Cryptography Background Pdf today and make your presentation stand out from the rest This slide talks about the cloud access control methods. The purpose of this slide is to briefly explain cloud access control techniques such as Identity and Access Management IAM, Multi Factor Authentication MFA, Role based access control RBAC, etc.
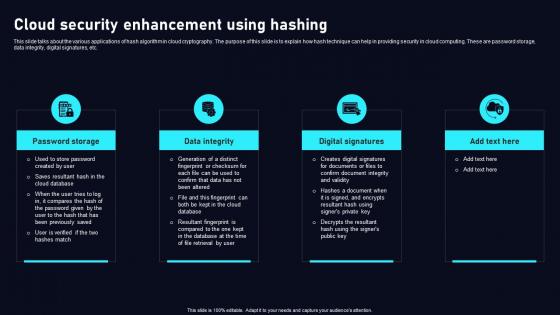
Cloud Security Enhancement Using Cloud Data Security Using Cryptography Elements Pdf
This slide talks about the various applications of hash algorithm in cloud cryptography. The purpose of this slide is to explain how hash technique can help in providing security in cloud computing. These are password storage, data integrity, digital signatures, etc. This Cloud Security Enhancement Using Cloud Data Security Using Cryptography Elements Pdf is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Cloud Security Enhancement Using Cloud Data Security Using Cryptography Elements Pdf features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide talks about the various applications of hash algorithm in cloud cryptography. The purpose of this slide is to explain how hash technique can help in providing security in cloud computing. These are password storage, data integrity, digital signatures, etc.
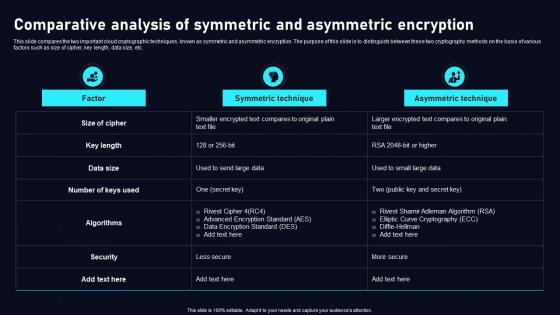
Comparative Analysis Of Symmetric Cloud Data Security Using Cryptography Clipart Pdf
This slide compares the two important cloud cryptographic techniques, known as symmetric and asymmetric encryption. The purpose of this slide is to distinguish between these two cryptography methods on the basis of various factors such as size of cipher, key length, data size, etc. Explore a selection of the finest Comparative Analysis Of Symmetric Cloud Data Security Using Cryptography Clipart Pdf here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Comparative Analysis Of Symmetric Cloud Data Security Using Cryptography Clipart Pdf to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide compares the two important cloud cryptographic techniques, known as symmetric and asymmetric encryption. The purpose of this slide is to distinguish between these two cryptography methods on the basis of various factors such as size of cipher, key length, data size, etc.
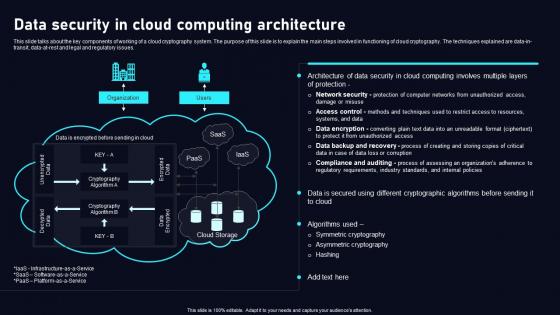
Data Security In Cloud Computing Cloud Data Security Using Cryptography Formats Pdf
This slide talks about the key components of working of a cloud cryptography system. The purpose of this slide is to explain the main steps involved in functioning of cloud cryptography. The techniques explained are data in transit, data at rest and legal and regulatory issues. Retrieve professionally designed Data Security In Cloud Computing Cloud Data Security Using Cryptography Formats Pdf to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide talks about the key components of working of a cloud cryptography system. The purpose of this slide is to explain the main steps involved in functioning of cloud cryptography. The techniques explained are data in transit, data at rest and legal and regulatory issues.
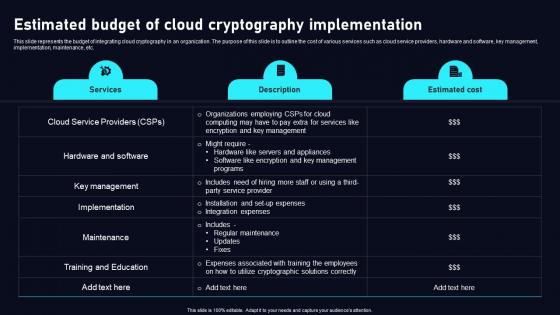
Estimated Budget Of Cloud Data Security Using Cryptography Brochure Pdf
This slide represents the budget of integrating cloud cryptography in an organization. The purpose of this slide is to outline the cost of various services such as cloud service providers, hardware and software, key management, implementation, maintenance, etc. This Estimated Budget Of Cloud Data Security Using Cryptography Brochure Pdf from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide represents the budget of integrating cloud cryptography in an organization. The purpose of this slide is to outline the cost of various services such as cloud service providers, hardware and software, key management, implementation, maintenance, etc.
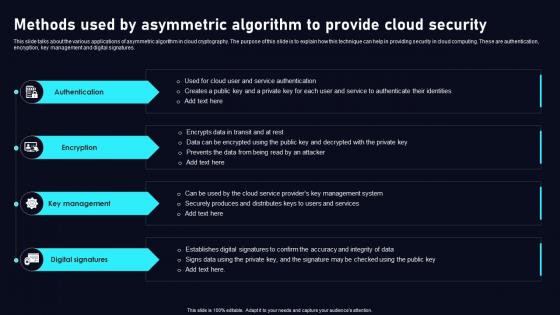
Methods Used By Asymmetric Algorithm Cloud Data Security Using Cryptography Inspiration Pdf
This slide talks about the various applications of asymmetric algorithm in cloud cryptography. The purpose of this slide is to explain how this technique can help in providing security in cloud computing. These are authentication, encryption, key management and digital signatures. Get a simple yet stunning designed Methods Used By Asymmetric Algorithm Cloud Data Security Using Cryptography Inspiration Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Methods Used By Asymmetric Algorithm Cloud Data Security Using Cryptography Inspiration Pdf can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide talks about the various applications of asymmetric algorithm in cloud cryptography. The purpose of this slide is to explain how this technique can help in providing security in cloud computing. These are authentication, encryption, key management and digital signatures.
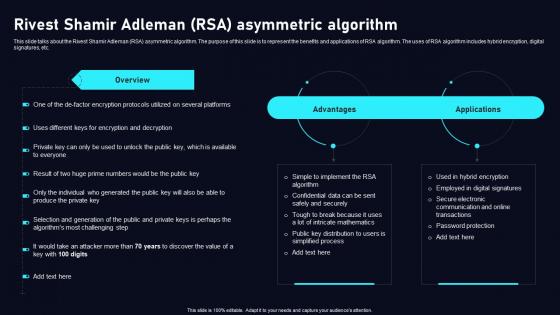
Rivest Shamir Adleman RSA Asymmetric Cloud Data Security Using Cryptography Slides Pdf
This slide talks about the Rivest Shamir Adleman RSA asymmetric algorithm. The purpose of this slide is to represent the benefits and applications of RSA algorithm. The uses of RSA algorithm includes hybrid encryption, digital signatures, etc. Slidegeeks is here to make your presentations a breeze with Rivest Shamir Adleman RSA Asymmetric Cloud Data Security Using Cryptography Slides Pdf With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide talks about the Rivest Shamir Adleman RSA asymmetric algorithm. The purpose of this slide is to represent the benefits and applications of RSA algorithm. The uses of RSA algorithm includes hybrid encryption, digital signatures, etc.

Esteemed Clientele Carelulu Shareholders Fund Raising Pitch Deck Inspiration Pdf
The following slide showcases customer categories that uses products and services offered by company which provides an online marketplace that helps parents to find and compare childcare services nearby. Its customers segments consists of parents, childcare services and businesses. Get a simple yet stunning designed Esteemed Clientele Carelulu Shareholders Fund Raising Pitch Deck Inspiration Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Esteemed Clientele Carelulu Shareholders Fund Raising Pitch Deck Inspiration Pdf can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. The following slide showcases customer categories that uses products and services offered by company which provides an online marketplace that helps parents to find and compare childcare services nearby. Its customers segments consists of parents, childcare services and businesses.
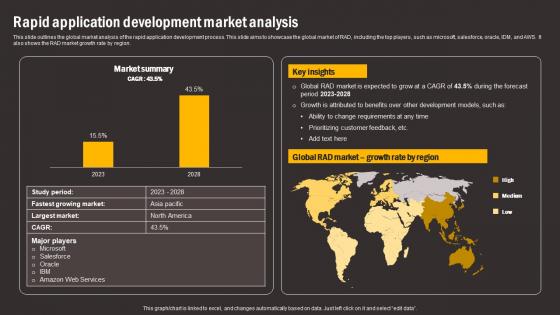
Rapid Application Development Market Comparing RAD And Other Software Template Pdf
This slide outlines the global market analysis of the rapid application development process. This slide aims to showcase the global market of RAD, including the top players, such as microsoft, salesforce, oracle, IDM, and AWS. It also shows the RAD market growth rate by region. Slidegeeks is here to make your presentations a breeze with Rapid Application Development Market Comparing RAD And Other Software Template Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide outlines the global market analysis of the rapid application development process. This slide aims to showcase the global market of RAD, including the top players, such as microsoft, salesforce, oracle, IDM, and AWS. It also shows the RAD market growth rate by region.
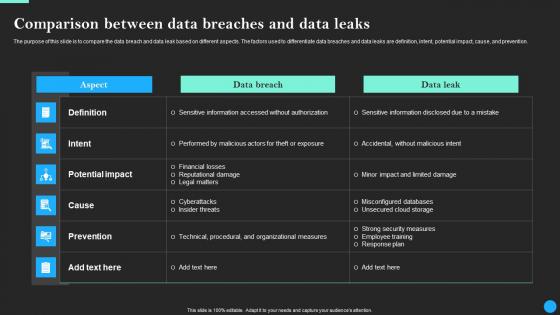
Comparison Between Data Breaches And Data Leaks Data Breach Prevention Download Pdf
The purpose of this slide is to compare the data breach and data leak based on different aspects. The factors used to differentiate data breaches and data leaks are definition, intent, potential impact, cause, and prevention. Slidegeeks is here to make your presentations a breeze with Comparison Between Data Breaches And Data Leaks Data Breach Prevention Download Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first The purpose of this slide is to compare the data breach and data leak based on different aspects. The factors used to differentiate data breaches and data leaks are definition, intent, potential impact, cause, and prevention.
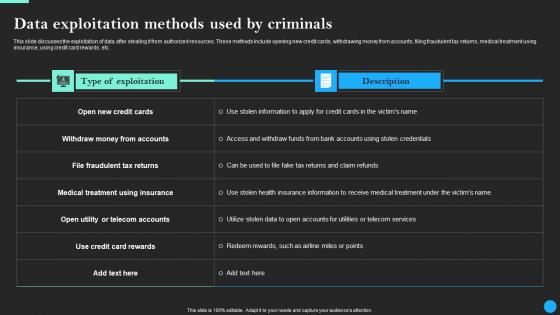
Data Exploitation Methods Used By Criminals Data Breach Prevention Portrait Pdf
This slide discusses the exploitation of data after stealing it from authorized resources. These methods include opening new credit cards, withdrawing money from accounts, filing fraudulent tax returns, medical treatment using insurance, using credit card rewards, etc. Explore a selection of the finest Data Exploitation Methods Used By Criminals Data Breach Prevention Portrait Pdf here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Data Exploitation Methods Used By Criminals Data Breach Prevention Portrait Pdf to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide discusses the exploitation of data after stealing it from authorized resources. These methods include opening new credit cards, withdrawing money from accounts, filing fraudulent tax returns, medical treatment using insurance, using credit card rewards, etc.
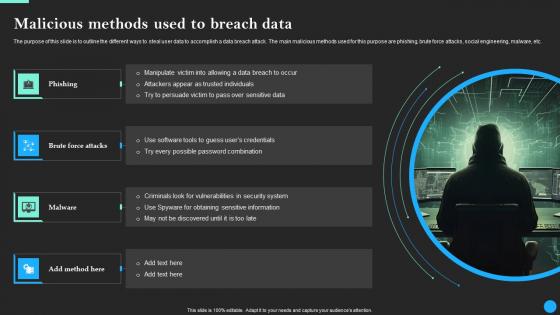
Malicious Methods Used To Breach Data Data Breach Prevention Topics Pdf
The purpose of this slide is to outline the different ways to steal user data to accomplish a data breach attack. The main malicious methods used for this purpose are phishing, brute force attacks, social engineering, malware, etc. This Malicious Methods Used To Breach Data Data Breach Prevention Topics Pdf from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. The purpose of this slide is to outline the different ways to steal user data to accomplish a data breach attack. The main malicious methods used for this purpose are phishing, brute force attacks, social engineering, malware, etc.
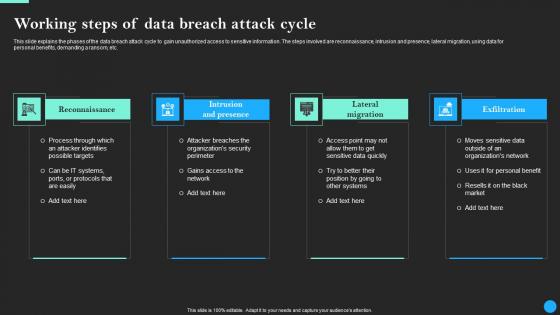
Working Steps Of Data Breach Attack Cycle Data Breach Prevention Infographics Pdf
This slide explains the phases of the data breach attack cycle to gain unauthorized access to sensitive information. The steps involved are reconnaissance, intrusion and presence, lateral migration, using data for personal benefits, demanding a ransom, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Working Steps Of Data Breach Attack Cycle Data Breach Prevention Infographics Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Working Steps Of Data Breach Attack Cycle Data Breach Prevention Infographics Pdf today and make your presentation stand out from the rest This slide explains the phases of the data breach attack cycle to gain unauthorized access to sensitive information. The steps involved are reconnaissance, intrusion and presence, lateral migration, using data for personal benefits, demanding a ransom, etc.
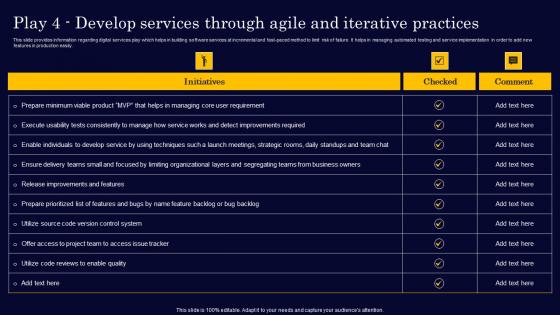
Play 4 Develop Services Through Agile And Iterative Gen Tech Stack Playbook Portrait Pdf
This slide provides information regarding digital services play which helps in building software services at incremental and fast-paced method to limit risk of failure. It helps in managing automated testing and service implementation in order to add new features in production easily. This Play 4 Develop Services Through Agile And Iterative Gen Tech Stack Playbook Portrait Pdf is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Play 4 Develop Services Through Agile And Iterative Gen Tech Stack Playbook Portrait Pdf features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide provides information regarding digital services play which helps in building software services at incremental and fast-paced method to limit risk of failure. It helps in managing automated testing and service implementation in order to add new features in production easily.
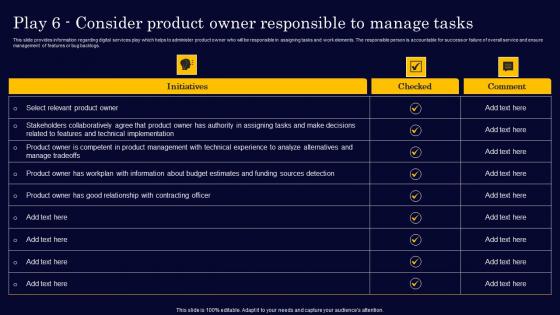
Play 6 Consider Product Owner Responsible To Manage Gen Tech Stack Playbook Slides Pdf
This slide provides information regarding digital services play which helps to administer product owner who will be responsible in assigning tasks and work elements. The responsible person is accountable for success or failure of overall service and ensure management of features or bug backlogs. Explore a selection of the finest Play 6 Consider Product Owner Responsible To Manage Gen Tech Stack Playbook Slides Pdf here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Play 6 Consider Product Owner Responsible To Manage Gen Tech Stack Playbook Slides Pdf to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide provides information regarding digital services play which helps to administer product owner who will be responsible in assigning tasks and work elements. The responsible person is accountable for success or failure of overall service and ensure management of features or bug backlogs.
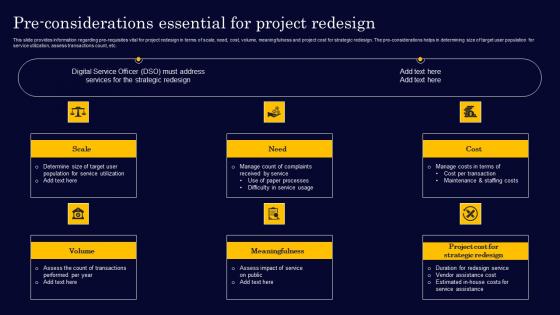
Pre Considerations Essential For Project Redesign Gen Tech Stack Playbook Pictures Pdf
This slide provides information regarding pre-requisites vital for project redesign in terms of scale, need, cost, volume, meaningfulness and project cost for strategic redesign. The pre-considerations helps in determining size of target user population for service utilization, assess transactions count, etc. Retrieve professionally designed Pre Considerations Essential For Project Redesign Gen Tech Stack Playbook Pictures Pdf to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide provides information regarding pre-requisites vital for project redesign in terms of scale, need, cost, volume, meaningfulness and project cost for strategic redesign. The pre-considerations helps in determining size of target user population for service utilization, assess transactions count, etc.
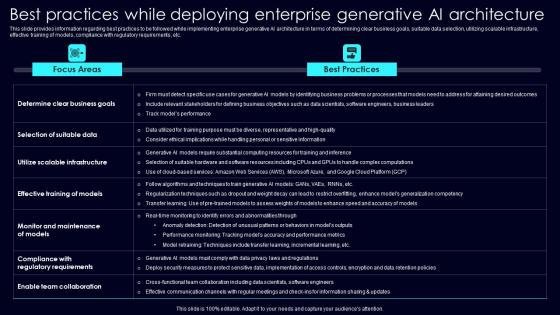
Best Practices While Deploying Exploring Rise Of Generative AI In Artificial Intelligence Microsoft Pdf
This slide provides information regarding best practices to be followed while implementing enterprise generative AI architecture in terms of determining clear business goals, suitable data selection, utilizing scalable infrastructure, effective training of models, compliance with regulatory requirements, etc. Slidegeeks is here to make your presentations a breeze with Best Practices While Deploying Exploring Rise Of Generative AI In Artificial Intelligence Microsoft Pdf With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide provides information regarding best practices to be followed while implementing enterprise generative AI architecture in terms of determining clear business goals, suitable data selection, utilizing scalable infrastructure, effective training of models, compliance with regulatory requirements, etc.

ChatGpt As Generative AI Tool Exploring Rise Of Generative AI In Artificial Intelligence Graphics Pdf
This slide provides information regarding ChatGPT platform in terms of its features such as capability to interact in conversational dialogue pattern along with functionalities such as text, language, dialogue generation, text summarization and classification. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than ChatGpt As Generative AI Tool Exploring Rise Of Generative AI In Artificial Intelligence Graphics Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab ChatGpt As Generative AI Tool Exploring Rise Of Generative AI In Artificial Intelligence Graphics Pdf today and make your presentation stand out from the rest This slide provides information regarding ChatGPT platform in terms of its features such as capability to interact in conversational dialogue pattern along with functionalities such as text, language, dialogue generation, text summarization and classification.
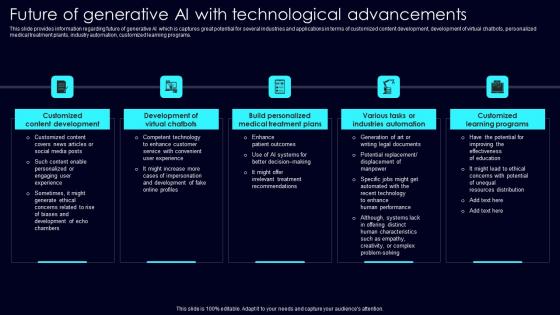
Future Of Generative AI Exploring Rise Of Generative AI In Artificial Intelligence Inspiration Pdf
This slide provides information regarding future of generative AI which is captures great potential for several industries and applications in terms of customized content development, development of virtual chatbots, personalized medical treatment plants, industry automation, customized learning programs. This Future Of Generative AI Exploring Rise Of Generative AI In Artificial Intelligence Inspiration Pdf is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Future Of Generative AI Exploring Rise Of Generative AI In Artificial Intelligence Inspiration Pdf features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide provides information regarding future of generative AI which is captures great potential for several industries and applications in terms of customized content development, development of virtual chatbots, personalized medical treatment plants, industry automation, customized learning programs.

Generative AI Architecture Deployment Exploring Rise Of Generative AI In Artificial Intelligence Rules Pdf
This slide provides information regarding the deployment and integration layers associated with generative AI architecture. This layer comprises of several elements. It also highlights about the key steps associated with the layer. Explore a selection of the finest Generative AI Architecture Deployment Exploring Rise Of Generative AI In Artificial Intelligence Rules Pdf here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Generative AI Architecture Deployment Exploring Rise Of Generative AI In Artificial Intelligence Rules Pdf to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide provides information regarding the deployment and integration layers associated with generative AI architecture. This layer comprises of several elements. It also highlights about the key steps associated with the layer.

Generative AI Overview Pros Exploring Rise Of Generative AI In Artificial Intelligence Clipart Pdf
This slide provides information regarding generative AI technology that enables AI model to generate content in terms of images, videos, speech, text or software code. It also highlights pros and cons associated to the technology. This Generative AI Overview Pros Exploring Rise Of Generative AI In Artificial Intelligence Clipart Pdf from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide provides information regarding generative AI technology that enables AI model to generate content in terms of images, videos, speech, text or software code. It also highlights pros and cons associated to the technology.
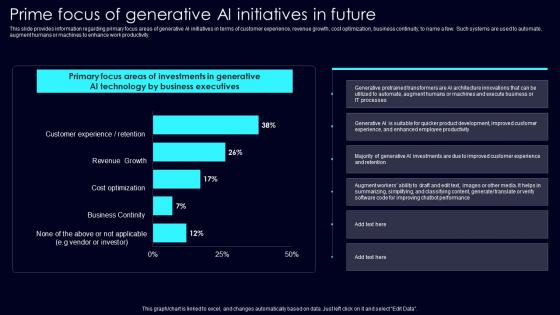
Prime Focus Of Generative Exploring Rise Of Generative AI In Artificial Intelligence Professional Pdf
This slide provides information regarding primary focus areas of generative AI initiatives in terms of customer experience, revenue growth, cost optimization, business continuity, to name a few. Such systems are used to automate, augment humans or machines to enhance work productivity. Slidegeeks is here to make your presentations a breeze with Prime Focus Of Generative Exploring Rise Of Generative AI In Artificial Intelligence Professional Pdf With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide provides information regarding primary focus areas of generative AI initiatives in terms of customer experience, revenue growth, cost optimization, business continuity, to name a few. Such systems are used to automate, augment humans or machines to enhance work productivity.
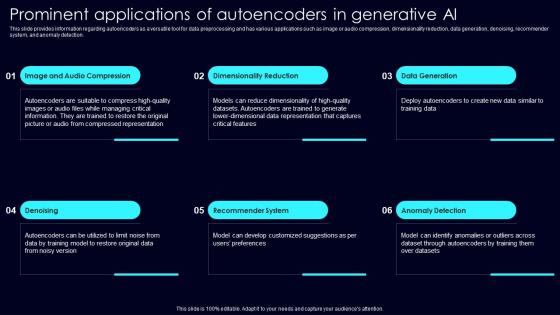
Prominent Applications Exploring Rise Of Generative AI In Artificial Intelligence Professional Pdf
This slide provides information regarding autoencoders as a versatile tool for data preprocessing and has various applications such as image or audio compression, dimensionality reduction, data generation, denoising, recommender system, and anomaly detection. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Prominent Applications Exploring Rise Of Generative AI In Artificial Intelligence Professional Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Prominent Applications Exploring Rise Of Generative AI In Artificial Intelligence Professional Pdf today and make your presentation stand out from the rest This slide provides information regarding autoencoders as a versatile tool for data preprocessing and has various applications such as image or audio compression, dimensionality reduction, data generation, denoising, recommender system, and anomaly detection.

Synthesia AI Generative AI Exploring Rise Of Generative AI In Artificial Intelligence Sample Pdf
This slide provides information regarding the potential video generation platform Synthesia AI which enables users to create professional videos by transforming text into speech. It is suitable for marketers, recruiters, and bloggers. The slide also highlights pros and cons associated to it. This Synthesia AI Generative AI Exploring Rise Of Generative AI In Artificial Intelligence Sample Pdf is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Synthesia AI Generative AI Exploring Rise Of Generative AI In Artificial Intelligence Sample Pdf features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide provides information regarding the potential video generation platform Synthesia AI which enables users to create professional videos by transforming text into speech. It is suitable for marketers, recruiters, and bloggers. The slide also highlights pros and cons associated to it.
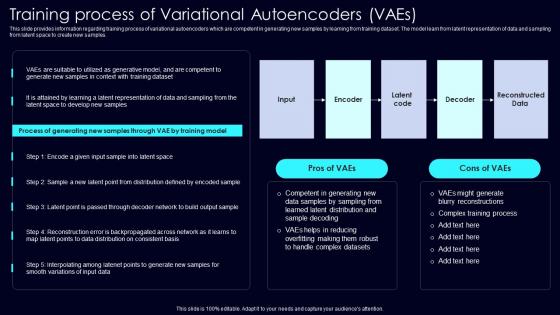
Training Process Of Variational Exploring Rise Of Generative AI In Artificial Intelligence Portrait Pdf
This slide provides information regarding training process of variational autoencoders which are competent in generating new samples by learning from training dataset. The model learn from latent representation of data and sampling from latent space to create new samples. Explore a selection of the finest Training Process Of Variational Exploring Rise Of Generative AI In Artificial Intelligence Portrait Pdf here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Training Process Of Variational Exploring Rise Of Generative AI In Artificial Intelligence Portrait Pdf to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide provides information regarding training process of variational autoencoders which are competent in generating new samples by learning from training dataset. The model learn from latent representation of data and sampling from latent space to create new samples.
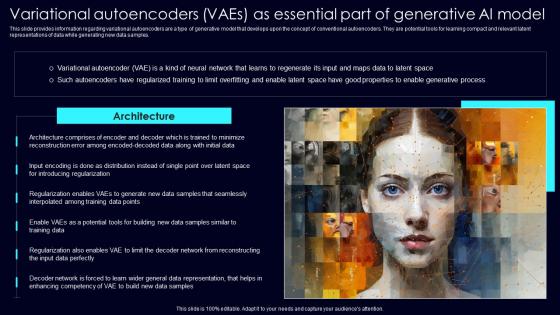
Variational Autoencoders Vaes Exploring Rise Of Generative AI In Artificial Intelligence Mockup Pdf
This slide provides information regarding variational autoencoders are a type of generative model that develops upon the concept of conventional autoencoders. They are potential tools for learning compact and relevant latent representations of data while generating new data samples. This Variational Autoencoders Vaes Exploring Rise Of Generative AI In Artificial Intelligence Mockup Pdf from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide provides information regarding variational autoencoders are a type of generative model that develops upon the concept of conventional autoencoders. They are potential tools for learning compact and relevant latent representations of data while generating new data samples.
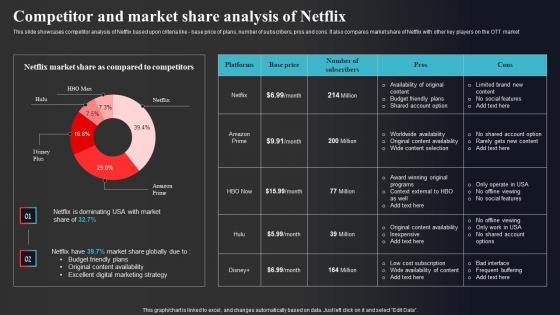
Competitor And Market Share Analysis Of Netflix Enhancing Online Visibility Template Pdf
This slide showcases competitor analysis of Netflix based upon criteria like - base price of plans, number of subscribers, pros and cons. It also compares market share of Netflix with other key players on the OTT market Explore a selection of the finest Competitor And Market Share Analysis Of Netflix Enhancing Online Visibility Template Pdf here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Competitor And Market Share Analysis Of Netflix Enhancing Online Visibility Template Pdf to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide showcases competitor analysis of Netflix based upon criteria like - base price of plans, number of subscribers, pros and cons. It also compares market share of Netflix with other key players on the OTT market
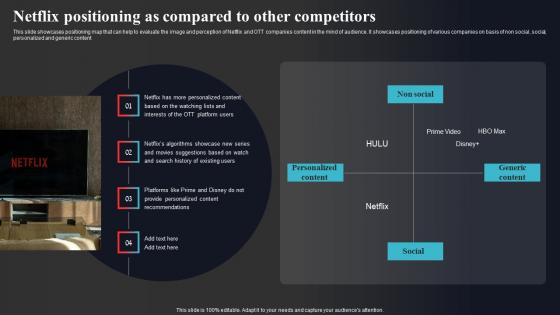
Netflix Positioning As Compared To Other Competitors Enhancing Online Visibility Sample Pdf
This slide showcases positioning map that can help to evaluate the image and perception of Netflix and OTT companies content in the mind of audience. It showcases positioning of various companies on basis of non social, social, personalized and generic content Get a simple yet stunning designed Netflix Positioning As Compared To Other Competitors Enhancing Online Visibility Sample Pdf It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Netflix Positioning As Compared To Other Competitors Enhancing Online Visibility Sample Pdf can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide showcases positioning map that can help to evaluate the image and perception of Netflix and OTT companies content in the mind of audience. It showcases positioning of various companies on basis of non social, social, personalized and generic content

Polls Conducted By Netflix On Social Media Platforms Enhancing Online Visibility Structure Pdf
This slide showcases social media polls conducted by Netflix on twitter to know opinions of potential customers.This strategy have helped Netflix to engage with audience on social media platform and improve awareness about platform Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Polls Conducted By Netflix On Social Media Platforms Enhancing Online Visibility Structure Pdf With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Polls Conducted By Netflix On Social Media Platforms Enhancing Online Visibility Structure Pdf today and make your presentation stand out from the rest. This slide showcases social media polls conducted by Netflix on twitter to know opinions of potential customers.This strategy have helped Netflix to engage with audience on social media platform and improve awareness about platform

Case Study Apple Line And Brand Extension Strategy Launching New Product Brand Introduction Pdf
This slide showcases example of apple brand category and line extension that they used to expand in market and increase awareness about brand. Its key elements are Apple mac, iPhone, iPad, iPod and watch, category extension and line extension Slidegeeks is here to make your presentations a breeze with Case Study Apple Line And Brand Extension Strategy Launching New Product Brand Introduction Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first. This slide showcases example of apple brand category and line extension that they used to expand in market and increase awareness about brand. Its key elements are Apple mac, iPhone, iPad, iPod and watch, category extension and line extension

Case Study Coca Cola Product Line Extension Strategy Launching New Product Brand Mockup Pdf
This slide showcases product line extension strategy example which helped Coca Cola to launch multiple products in market and gain competitive edge. Its key elements are company name, attributes, goal o extension strategy and company overview Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Case Study Coca Cola Product Line Extension Strategy Launching New Product Brand Mockup Pdf With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Case Study Coca Cola Product Line Extension Strategy Launching New Product Brand Mockup Pdf today and make your presentation stand out from the rest. This slide showcases product line extension strategy example which helped Coca Cola to launch multiple products in market and gain competitive edge. Its key elements are company name, attributes, goal o extension strategy and company overview
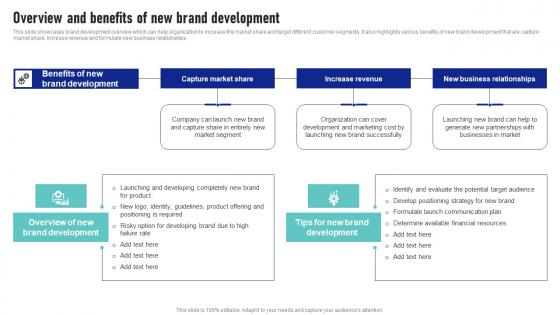
Overview And Benefits Of New Brand Development Launching New Product Brand Information Pdf
This slide showcases brand development overview which can help organization to increase the market share and target different customer segments. It also highlights various benefits of new brand development that are capture market share, increase revenue and formulate new business relationships This Overview And Benefits Of New Brand Development Launching New Product Brand Information Pdf from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide showcases brand development overview which can help organization to increase the market share and target different customer segments. It also highlights various benefits of new brand development that are capture market share, increase revenue and formulate new business relationships
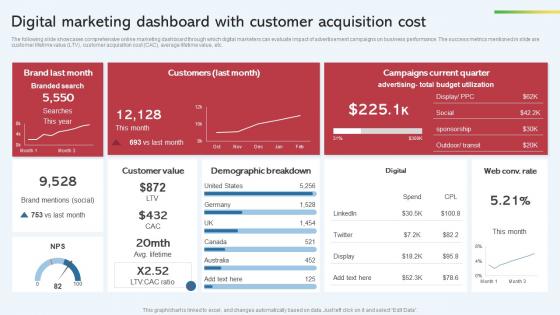
Digital Marketing Dashboard With Customer Acquisition Cost Effective Startup Promotion Plan Formats Pdf
The following slide showcases comprehensive online marketing dashboard through which digital marketers can evaluate impact of advertisement campaigns on business performance. The success metrics mentioned in slide are customer lifetime value LTV, customer acquisition cost CAC, average lifetime value, etc. Slidegeeks is here to make your presentations a breeze with Digital Marketing Dashboard With Customer Acquisition Cost Effective Startup Promotion Plan Formats Pdf With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first. The following slide showcases comprehensive online marketing dashboard through which digital marketers can evaluate impact of advertisement campaigns on business performance. The success metrics mentioned in slide are customer lifetime value LTV, customer acquisition cost CAC, average lifetime value, etc.
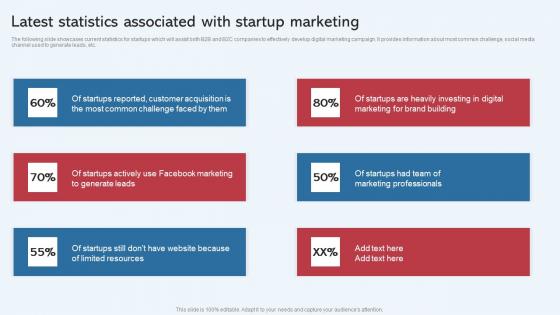
Latest Statistics Associated With Startup Marketing Effective Startup Promotion Plan Download Pdf
The following slide showcases current statistics for startups which will assist both B2B and B2C companies to effectively develop digital marketing campaign. It provides information about most common challenge, social media channel used to generate leads, etc. This Latest Statistics Associated With Startup Marketing Effective Startup Promotion Plan Download Pdf is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Latest Statistics Associated With Startup Marketing Effective Startup Promotion Plan Download Pdf features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today. The following slide showcases current statistics for startups which will assist both B2B and B2C companies to effectively develop digital marketing campaign. It provides information about most common challenge, social media channel used to generate leads, etc.
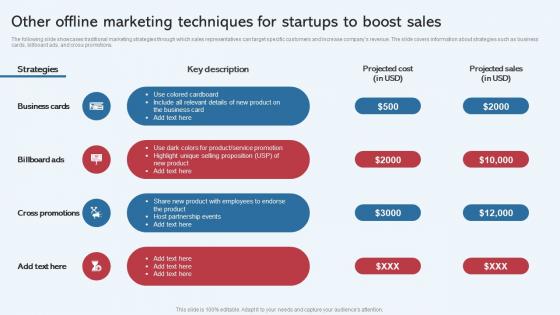
Other Offline Marketing Techniques For Startups To Boost Effective Startup Promotion Plan Diagrams Pdf
The following slide showcases traditional marketing strategies through which sales representatives can target specific customers and increase companys revenue. The slide covers information about strategies such as business cards, billboard ads, and cross promotions. Retrieve professionally designed Other Offline Marketing Techniques For Startups To Boost Effective Startup Promotion Plan Diagrams Pdf to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. The following slide showcases traditional marketing strategies through which sales representatives can target specific customers and increase companys revenue. The slide covers information about strategies such as business cards, billboard ads, and cross promotions.
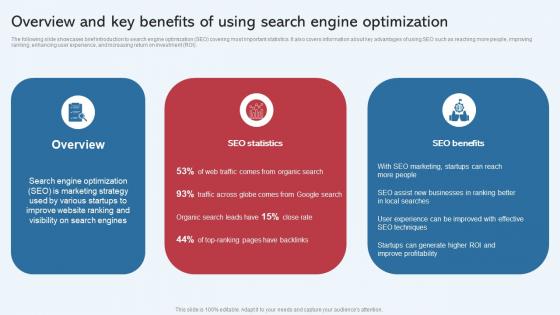
Overview And Key Benefits Of Using Search Engine Effective Startup Promotion Plan Graphics Pdf
The following slide showcases brief introduction to search engine optimization SEO covering most important statistics. It also covers information about key advantages of using SEO such as reaching more people, improving ranking, enhancing user experience, and increasing return on investment ROI. This Overview And Key Benefits Of Using Search Engine Effective Startup Promotion Plan Graphics Pdf from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. The following slide showcases brief introduction to search engine optimization SEO covering most important statistics. It also covers information about key advantages of using SEO such as reaching more people, improving ranking, enhancing user experience, and increasing return on investment ROI.
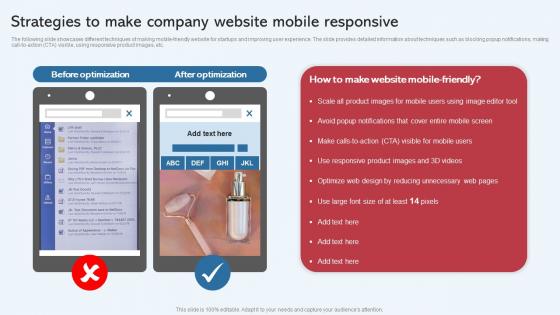
Strategies To Make Company Website Mobile Responsive Effective Startup Promotion Plan Elements Pdf
The following slide showcases different techniques of making mobile friendly website for startups and improving user experience. The slide provides detailed information about techniques such as blocking popup notifications, making call to action CTA visible, using responsive product images, etc. Get a simple yet stunning designed Strategies To Make Company Website Mobile Responsive Effective Startup Promotion Plan Elements Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Strategies To Make Company Website Mobile Responsive Effective Startup Promotion Plan Elements Pdf can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. The following slide showcases different techniques of making mobile friendly website for startups and improving user experience. The slide provides detailed information about techniques such as blocking popup notifications, making call to action CTA visible, using responsive product images, etc.


 Continue with Email
Continue with Email

 Home
Home


































