Technology Risk

ISO 9001 Quality Assurance Software Accreditation Root Causes To The Problem And Its Solutions Ideas PDF
This template covers root cause Problems of the organization and its Solutions after for successful implementation of the ISO 9001 standards. Presenting ISO 9001 Quality Assurance Software Accreditation Root Causes To The Problem And Its Solutions Ideas PDF to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like Root Cause, Proven Solution. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
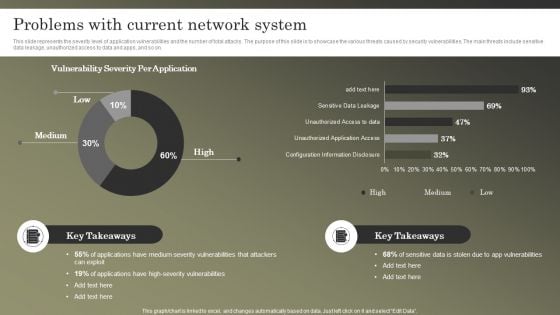
Cybersecurity Operations Cybersecops Problems With Current Network System Formats PDF
This slide represents the severity level of application vulnerabilities and the number of total attacks. The purpose of this slide is to showcase the various threats caused by security vulnerabilities. The main threats include sensitive data leakage, unauthorized access to data and apps, and so on. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Cybersecurity Operations Cybersecops Problems With Current Network System Formats PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Cybersecurity Operations Cybersecops Problems With Current Network System Formats PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.

Executing Security Management Program To Mitigate Threats And Safeguard Confidential Organizational Data Ppt PowerPoint Presentation Complete Deck
This complete deck acts as a great communication tool. It helps you in conveying your business message with personalized sets of graphics, icons etc. Comprising a set of fourtytwo slides, this complete deck can help you persuade your audience. It also induces strategic thinking as it has been thoroughly researched and put together by our experts. Not only is it easily downloadable but also editable. The color, graphics, theme any component can be altered to fit your individual needs. So grab it now.

Challenges Faced In Smart Packing And Its Solutions Optimizing Inventory Management IoT SS V
This slide provides an overview of the problems faced in smart packing. The slide showcases descriptions and solutions for issues such as data security, interoperability and cost. This modern and well-arranged Challenges Faced In Smart Packing And Its Solutions Optimizing Inventory Management IoT SS V provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide provides an overview of the problems faced in smart packing. The slide showcases descriptions and solutions for issues such as data security, interoperability and cost.
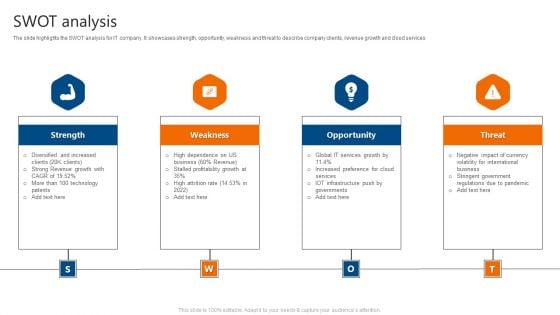
SWOT Analysis IT Software Development Company Profile Guidelines PDF
The slide highlights the SWOT analysis for IT company. It showcases strength, opportunity, weakness and threat to describe company clients, revenue growth and cloud services. Presenting SWOT Analysis IT Software Development Company Profile Guidelines PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Strength, Weakness, Opportunity, Threat. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
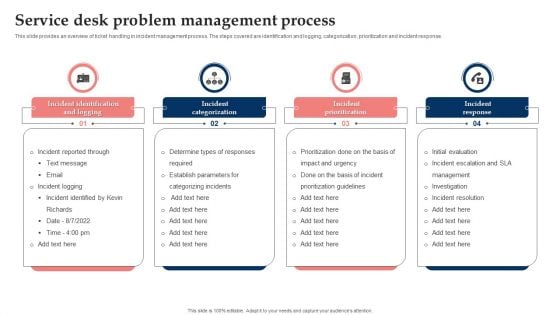
Service Desk Problem Management Process Elements PDF
This slide showcases service desk incident management process flowchart. It includes incident validation and approval, departmental reporting, assigning tasks to technicians, initial contact with customer, trouble shooting, incident resolution, etc. Showcasing this set of slides titled Service Desk Problem Management Process Elements PDF. The topics addressed in these templates are Departmental Reporting, Change Management, Interdepartmental Work Validation. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
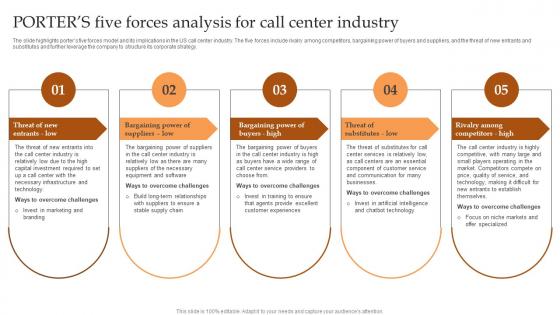
Porters Five Forces Analysis For Call Center Industry IT And Tech Support Business Introduction Pdf
The slide highlights porters five forces model and its implications in the US call center industry. The five forces include rivalry among competitors, bargaining power of buyers and suppliers, and the threat of new entrants and substitutes and further leverage the company to structure its corporate strategy. Take your projects to the next level with our ultimate collection of Porters Five Forces Analysis For Call Center Industry IT And Tech Support Business Introduction Pdf Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they well make your projects stand out from the rest. The slide highlights porters five forces model and its implications in the US call center industry. The five forces include rivalry among competitors, bargaining power of buyers and suppliers, and the threat of new entrants and substitutes and further leverage the company to structure its corporate strategy.
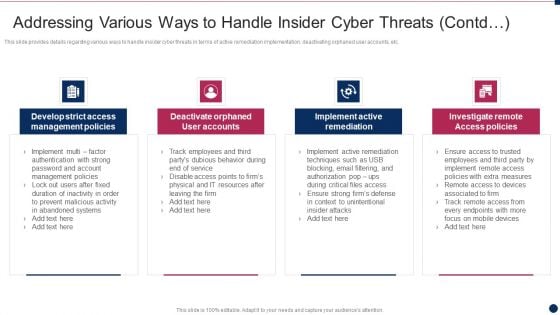
Threat Management At Workplace Addressing Various Ways To Handle Insider Cyber Threats Mockup Pdf
This slide provides details regarding various ways to handle insider cyber threats in terms of active remediation implementation, deactivating orphaned user accounts, etc. This is a threat management at workplace addressing various ways to handle insider cyber threats mockup pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like develop strict access management policies, implement active remediation, investigate remote access policies. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Threat Management At Workplace Various Types Of Workplace Violence And Threats Designs PDF
This slide provides details regarding various types of workplace violence threats created by people in terms of stalking, physical assault, harassment or intimidation, etc. This is a threat management at workplace various types of workplace violence and threats designs pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like harassment or intimidation, stalking, physical assault. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Secure Web Gateway Implementation Methodology Transparent Web Threat Protection System
This slide talks about the transparent scenario of Secure Web Gateway implementation. The purpose of this slide is to demonstrate the concept of transparent SWG deployment technique with the help of a diagram. This slide also outlines the benefits of this method. Create an editable Secure Web Gateway Implementation Methodology Transparent Web Threat Protection System that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Secure Web Gateway Implementation Methodology Transparent Web Threat Protection System is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide talks about the transparent scenario of Secure Web Gateway implementation. The purpose of this slide is to demonstrate the concept of transparent SWG deployment technique with the help of a diagram. This slide also outlines the benefits of this method.

O RAN Architecture Traditional Ran Overview And Problems Ppt Inspiration Designs PDF
This slide represents the overview of the traditional RAN system, including the problems associated with it. The problems include the degraded performance of the systems due to equipment from different vendors. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download O RAN Architecture Traditional Ran Overview And Problems Ppt Inspiration Designs PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the O RAN Architecture Traditional Ran Overview And Problems Ppt Inspiration Designs PDF.

Cyber Threat Prevention Ppt PowerPoint Presentation Complete Deck With Slides

Secure Web Gateway Implementation Methodology Explicit Web Threat Protection System
This slide talks about the inline scenario of Secure Web Gateway implementation. The purpose of this slide is to demonstrate the concept of inline SWG deployment technique with the help of a diagram. This slide also outlines the benefits of this method. Find a pre-designed and impeccable Secure Web Gateway Implementation Methodology Explicit Web Threat Protection System. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide talks about the inline scenario of Secure Web Gateway implementation. The purpose of this slide is to demonstrate the concept of inline SWG deployment technique with the help of a diagram. This slide also outlines the benefits of this method.
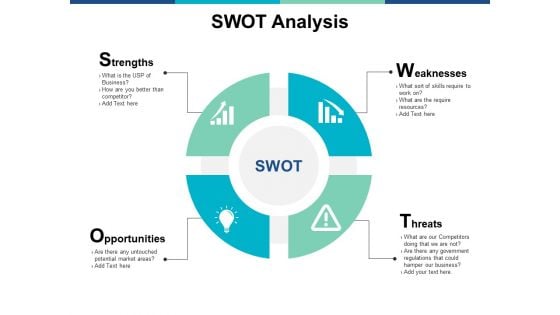
Swot Analysis Management Ppt PowerPoint Presentation Pictures Graphics Design
This is a swot analysis management ppt powerpoint presentation pictures graphics design. This is a four stage process. The stages in this process are strength, opportunity, weakness, threat, marketing.
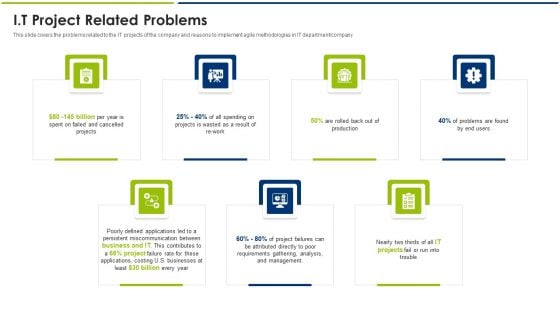
Agile Model IT Project Related Problems Ppt File Backgrounds PDF
This slide covers the problems related to the IT projects of the company and reasons to implement agile methodologies in IT department or company. This is a agile model it project related problems ppt file backgrounds pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like management, analysis, requirements, applications, businesses. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
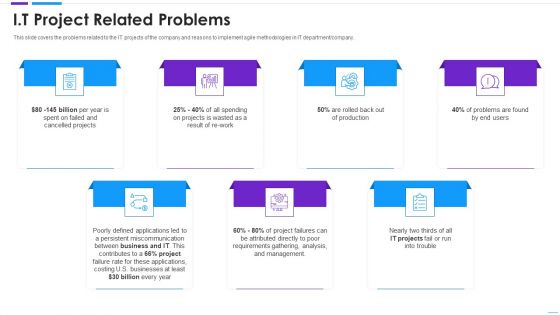
Agile Application Development It Project Related Problems Summary PDF
This slide covers the problems related to the IT projects of the company and reasons to implement agile methodologies in IT department or company. Presenting agile application development it project related problems summary pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like analysis, management, requirements, applications. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
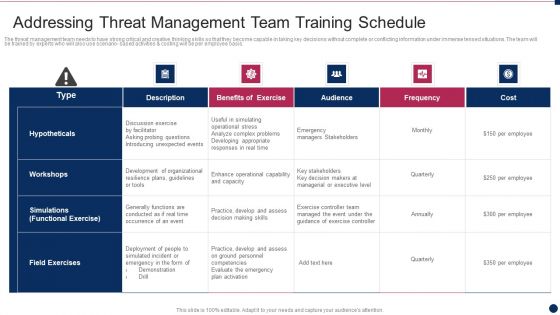
Threat Management At Workplace Addressing Threat Management Team Training Schedule Pictures Pdf
The threat management team needs to have strong critical and creative thinking skills so that they become capable in taking key decisions without complete or conflicting information under immense tensed situations. The team will be trained by experts who will also use scenario based activities and costing will be per employee basis. Deliver an awe inspiring pitch with this creative threat management at workplace addressing threat management team training schedule pictures pdf bundle. Topics like practice, develop and assess decision making skills, enhance operational capability and capacity, emergency managers stakeholders can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
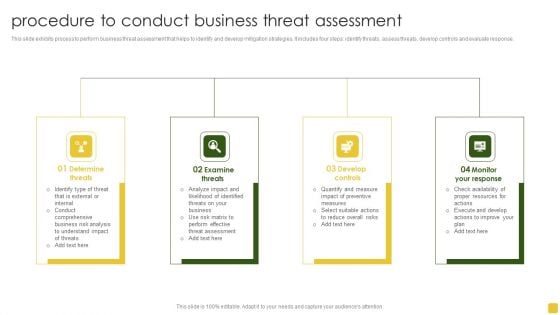
Procedure To Conduct Business Threat Assessment Topics PDF
This slide exhibits process to perform business threat assessment that helps to identify and develop mitigation strategies. It includes four steps identify threats, assess threats, develop controls and evaluate response.Presenting Procedure To Conduct Business Threat Assessment Topics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Determine Threats, Examine Threats, Develop Controls. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
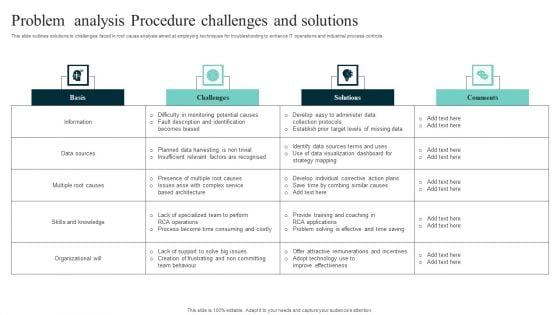
Problem Analysis Procedure Challenges And Solutions Themes PDF
This slide outlines solutions to challenges faced in root cause analysis aimed at employing techniques for troubleshooting to enhance IT operations and industrial process controls Showcasing this set of slides titled Problem Analysis Procedure Challenges And Solutions Themes PDF. The topics addressed in these templates are Data Sources, Information, Organizational. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Big Data Problem Ppt PowerPoint Presentation Slides Visuals Cpb
This is a big data problem ppt powerpoint presentation slides visuals cpb. This is a four stage process. The stages in this process are big data problem.

Cybersecurity Operations Cybersecops Secops Software Tools Based On Threats Introduction PDF
This slide talks about categorizing primary SecOps software tools based on threats. The purpose of this slide is to showcase the top software solutions for SecOps, including DNS security, network detection and response, anti-phishing, data discovery, and packet-level visibility. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Cybersecurity Operations Cybersecops Secops Software Tools Based On Threats Introduction PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
Swot Ppt PowerPoint Presentation Graphics
This is a swot ppt powerpoint presentation graphics. This is a four stage process. The stages in this process are strength, weakness, opportunity, threat.

Swot Ppt PowerPoint Presentation Inspiration Diagrams
This is a swot ppt powerpoint presentation inspiration diagrams. This is a four stage process. The stages in this process are strength, weakness, opportunity, threat.
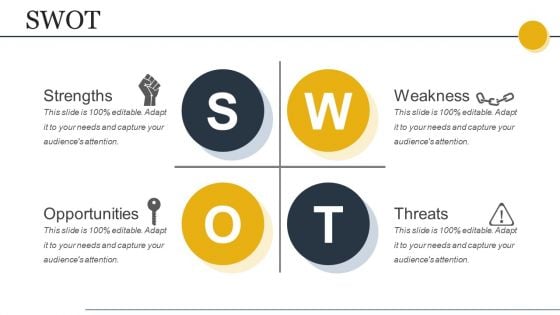
Swot Ppt PowerPoint Presentation Infographics Pictures
This is a swot ppt powerpoint presentation infographics pictures. This is a four stage process. The stages in this process are strengths, weakness, opportunities, threats.

Common Channel Conflict Ppt PowerPoint Presentation Styles Vector
This is a common channel conflict ppt powerpoint presentation styles vector. This is a four stage process. The stages in this process are strengths, weaknesses, opportunities, threats.
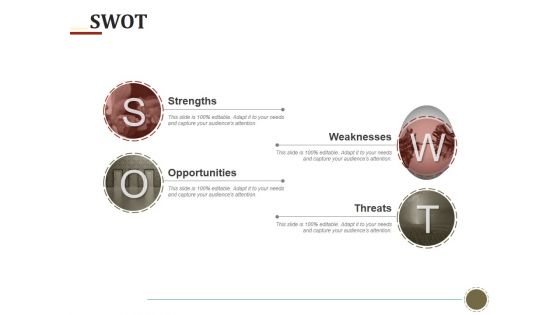
Swot Ppt PowerPoint Presentation Styles Pictures
This is a swot ppt powerpoint presentation styles pictures. This is a four stage process. The stages in this process are strengths, opportunities, weaknesses, threats.
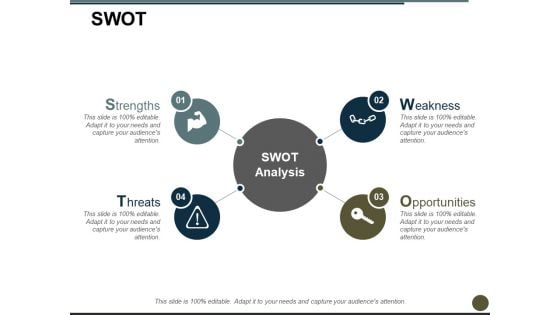
SWOT Ppt PowerPoint Presentation Gallery Graphics Pictures
This is a swot ppt powerpoint presentation gallery graphics pictures. This is a four stage process. The stages in this process are strengths, weakness, opportunities, threats, icon.

Stages For Minimizing Internet Security Threats Ideas PDF
Following slide exhibits steps for minimizing security and data breach. It includes major steps such as- malware protection and monitoring, source code assessment etc. Pitch your topic with ease and precision using this stages for minimizing internet security threats ideas pdf. This layout presents information on infrastructure management, cyber analysis, vulnerability management. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
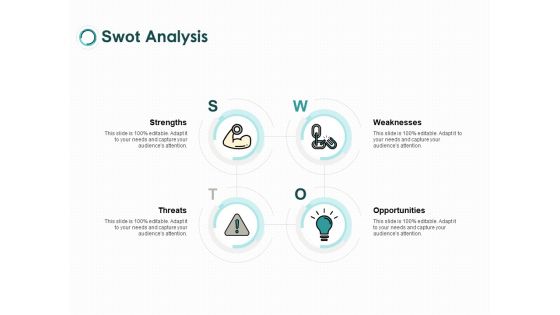
Swot Analysis Opportunities Ppt PowerPoint Presentation Professional Styles
Presenting this set of slides with name swot analysis opportunities ppt powerpoint presentation professional styles. This is a four stage process. The stages in this process are strength, opportunity, weakness, threat, marketing. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
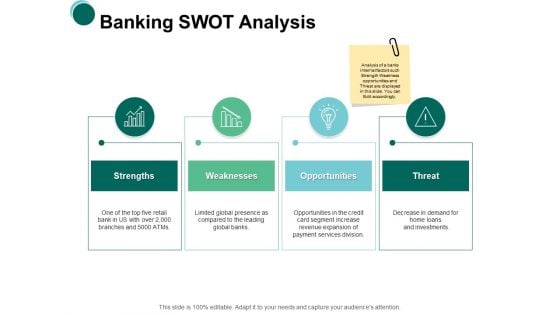
Banking Swot Analysis Opportunities Ppt PowerPoint Presentation Professional Topics
Presenting this set of slides with name banking swot analysis opportunities ppt powerpoint presentation professional topics. This is a four stage process. The stages in this process are strength, opportunity, weakness, threat, marketing. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Company Swot Analysis Strengths Ppt PowerPoint Presentation File Show
Presenting this set of slides with name company swot analysis strengths ppt powerpoint presentation file show. This is a four stage process. The stages in this process are strength, weakness, threat, opportunity, planning. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
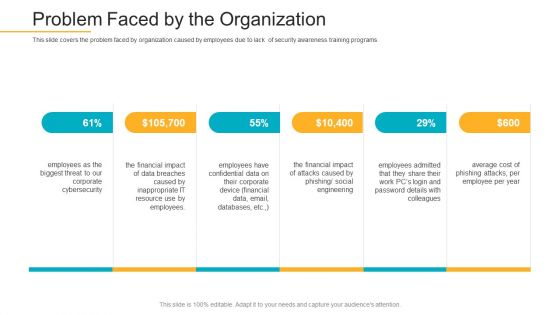
Data Breach Prevention Recognition Problem Faced By The Organization Elements PDF
This slide covers the problem faced by organization caused by employees due to lack of security awareness training programs. This is a data breach prevention recognition problem faced by the organization elements pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity, organization, problem, security awareness, training programs. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
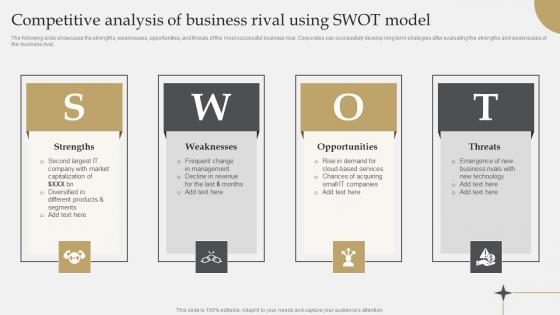
IT Industry Market Research Competitive Analysis Of Business Rival Using Swot Model Ideas Pdf
The following slide showcases the strengths, weaknesses, opportunities, and threats of the most successful business rival. Corporates can successfully develop long term strategies after evaluating the strengths and weaknesses of the business rival. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give IT Industry Market Research Competitive Analysis Of Business Rival Using Swot Model Ideas Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable IT Industry Market Research Competitive Analysis Of Business Rival Using Swot Model Ideas Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today. The following slide showcases the strengths, weaknesses, opportunities, and threats of the most successful business rival. Corporates can successfully develop long term strategies after evaluating the strengths and weaknesses of the business rival.
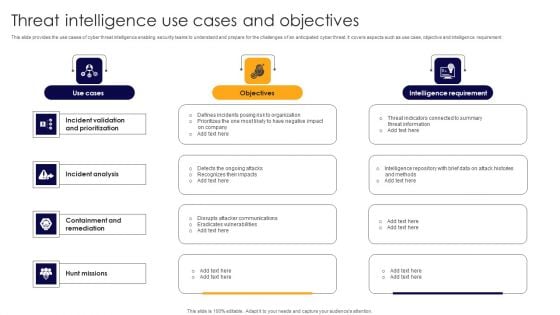
Threat Intelligence Use Cases And Objectives Demonstration PDF
This slide provides the use cases of cyber threat intelligence enabling security teams to understand and prepare for the challenges of an anticipated cyber threat. It covers aspects such as use case, objective and intelligence requirement. Presenting Threat Intelligence Use Cases And Objectives Demonstration PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Incident Analysis, Containment Remediation, Hunt Missions. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Icon For Major Threat Business Investment Introduction PDF
Persuade your audience using this Icon For Major Threat Business Investment Introduction PDF. This PPT design covers Three stages, thus making it a great tool to use. It also caters to a variety of topics including Icon For Major, Threat Business Investment. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Icon For Major Threat Payment Process Structure PDF
Presenting Icon For Major Threat Payment Process Structure PDF to dispense important information. This template comprises Three stages. It also presents valuable insights into the topics including Icon For Major, Threat Payment Process. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Major Threat Business And Finance Icon Portrait PDF
Persuade your audience using this Major Threat Business And Finance Icon Portrait PDF. This PPT design covers Three stages, thus making it a great tool to use. It also caters to a variety of topics including Major Threat, Business And Finance. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
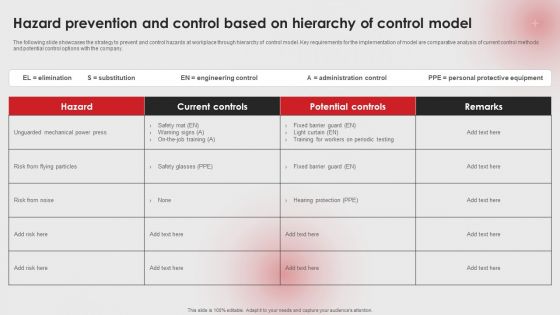
Hazard Prevention And Control Based On Hierarchy Of Control Model Ppt PowerPoint Presentation File Infographic Template PDF
The following slide showcases the strategy to prevent and control hazards at workplace through hierarchy of control model. Key requirements for the implementation of model are comparative analysis of current control methods and potential control options with the company. This Hazard Prevention And Control Based On Hierarchy Of Control Model Ppt PowerPoint Presentation File Infographic Template PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
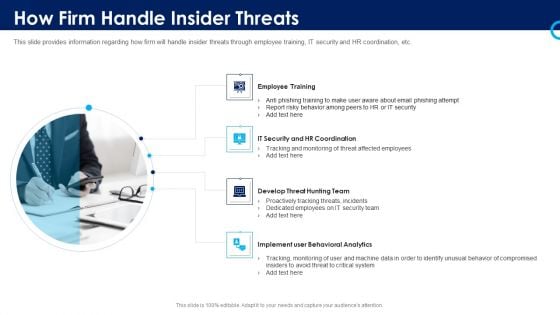
Organizational Security Solutions How Firm Handle Insider Threats Introduction PDF
This slide provides information regarding how firm will handle insider threats through employee training, IT security and HR coordination, etc. This is a organizational security solutions how firm handle insider threats introduction pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like employee training, it security and hr coordination, develop threat hunting team, implement user behavioral analytics. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Data Interpretation And Analysis Playbook How To Fix The Business Intelligence Problem Data Analytics Playbook Sample PDF
This template covers the solution for BI problems such as analytics transformation and business intelligence program. It also depicts that switching to next-generation analytics platform that gives business users data-driven insights. Presenting data interpretation and analysis playbook how to fix the business intelligence problem data analytics playbook sample pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like analytics, business intelligence, predictive analytics. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
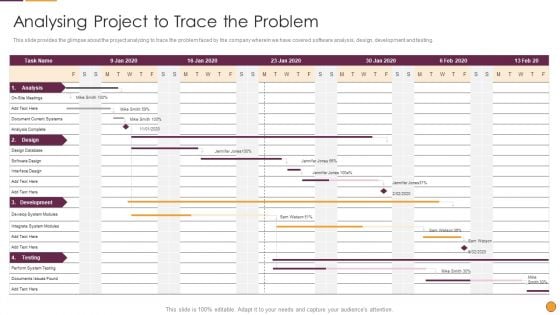
Process Enhancement Program Success Analysing Project To Trace The Problem Formats PDF
This slide provides the glimpse about the project analyzing to trace the problem faced by the company wherein we have covered software analysis, design, development and testing. Deliver an awe inspiring pitch with this creative Process Enhancement Program Success Analysing Project To Trace The Problem Formats PDF bundle. Topics like Design Database, Integrate System, Documents Issues can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Picture Of Virus Detected With Threat Symbol Ppt PowerPoint Presentation Gallery Show PDF
Presenting picture of virus detected with threat symbol ppt powerpoint presentation gallery show pdf to dispense important information. This template comprises two stages. It also presents valuable insights into the topics including picture of virus detected with threat symbol. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Criminal With Threat And Exclamation Mark Vector Icon Ppt PowerPoint Presentation Slides Good PDF
Presenting criminal with threat and exclamation mark vector icon ppt powerpoint presentation slides good pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including criminal with threat and exclamation mark vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Top 5 Issues In Security Problem Management Ppt Slides Show PDF
Presenting Top 5 Issues In Security Problem Management Ppt Slides Show PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Lack Threat Program, No Operational Exercises, Security Program. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Challenges Faced By Our Clients Template 1 Ppt PowerPoint Presentation Gallery Grid
This is a challenges faced by our clients template 1 ppt powerpoint presentation gallery grid. This is a two stage process. The stages in this process are big data challenges, big data opportunity, goal.

Upgrading Total Project Safety IT Addressing Various Threats Affecting It Project Safety Designs PDF
This slide provides information regarding various IT threats existing at workplace disrupting IT project safety such as general and criminal IT threats. This is a upgrading total project safety it addressing various threats affecting it project safety designs pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like general it threats, criminal it threats. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Logistics Management Services Swot Elements PDF
Presenting logistics management services swot elements pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like strength, weakness, opportunity, threat. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Internal And External Logistics Management Procedure SWOT Information PDF
Presenting internal and external logistics management procedure swot information pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like strength, weakness, opportunity, threat. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Agenda Of How To Intensify Project Threats Portrait PDF
This is a agenda of how to intensify project threats portrait pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like agenda of how to intensify project threats. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Upgrading Total Project Safety IT Determine Phases Of Threat Attack Disrupting Project Safety Contd Elements PDF
This slide provides information regarding various phases for threat attack disrupting IT project safety in terms of installation, command and control, actions and objectives, covering tracks. This is a upgrading total project safety it determine phases of threat attack disrupting project safety contd elements pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like installation, command and control, actions and objectives, covering tracks. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
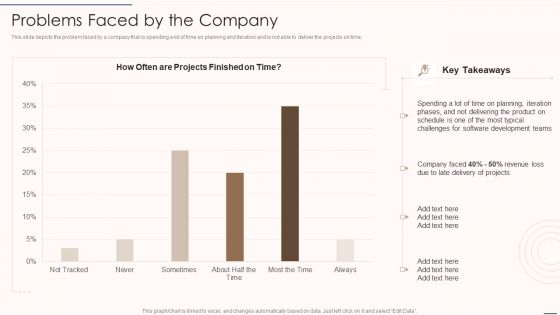
Rapid Application Building Framework Problems Faced By The Company Guidelines PDF
This slide depicts the problem faced by a company that is spending a lot of time on planning and iteration and is not able to deliver the projects on time.Deliver and pitch your topic in the best possible manner with this Rapid Application Building Framework Problems Faced By The Company Guidelines PDF. Use them to share invaluable insights on Planning Iteration, Delivering The Product, Software Development and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Project Security Administration IT Determine Phases Of Threat Attack Disrupting Project Safety Contd Icons PDF
This slide provides information regarding various phases for threat attack disrupting IT project safety in terms of installation, command and control, actions and objectives, covering tracks. Presenting project security administration it determine phases of threat attack disrupting project safety contd icons pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like installation, command and control, actions and objectives, covering tracks. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

CASB 2 0 IT CASB Deployment With Optional Components Pricing
This slide outlines the pricing of CASB deployment with optional or add-on components. The purpose of this slide is to showcase the pricing of additional components in CASB deployment, including data security subscription, support, threat protection subscription, data retention, and so on. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than CASB 2 0 IT CASB Deployment With Optional Components Pricing. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab CASB 2 0 IT CASB Deployment With Optional Components Pricing today and make your presentation stand out from the rest This slide outlines the pricing of CASB deployment with optional or add-on components. The purpose of this slide is to showcase the pricing of additional components in CASB deployment, including data security subscription, support, threat protection subscription, data retention, and so on.
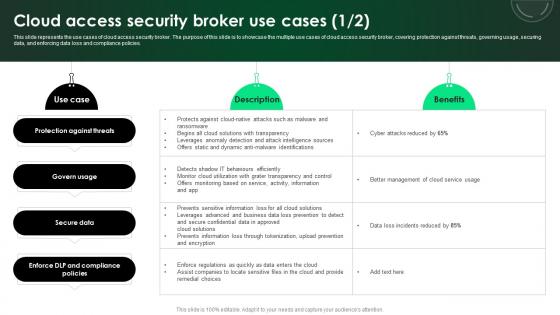
CASB 2 0 IT Cloud Access Security Broker Use Cases
This slide represents the use cases of cloud access security broker. The purpose of this slide is to showcase the multiple use cases of cloud access security broker, covering protection against threats, governing usage, securing data, and enforcing data loss and compliance policies. Presenting this PowerPoint presentation, titled CASB 2 0 IT Cloud Access Security Broker Use Cases, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this CASB 2 0 IT Cloud Access Security Broker Use Cases. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable CASB 2 0 IT Cloud Access Security Broker Use Cases that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide represents the use cases of cloud access security broker. The purpose of this slide is to showcase the multiple use cases of cloud access security broker, covering protection against threats, governing usage, securing data, and enforcing data loss and compliance policies.
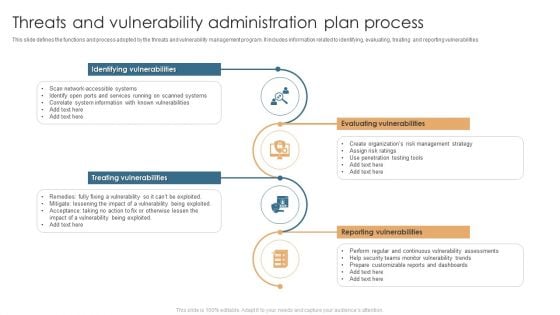
Threats And Vulnerability Administration Plan Process Guidelines PDF
This slide defines the functions and process adopted by the threats and vulnerability management program. It includes information related to identifying, evaluating, treating and reporting vulnerabilities. Presenting Threats And Vulnerability Administration Plan Process Guidelines PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Evaluating Vulnerabilities, Reporting Vulnerabilities, Treating Vulnerabilities, Identifying Vulnerabilities. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Analysis Of Opportunities Ppt Powerpoint Presentation Inspiration Graphic Tips
This is a analysis of opportunities ppt powerpoint presentation inspiration graphic tips. This is a four stage process. The stages in this process are analysis of opportunities, management, marketing, business, strategy.
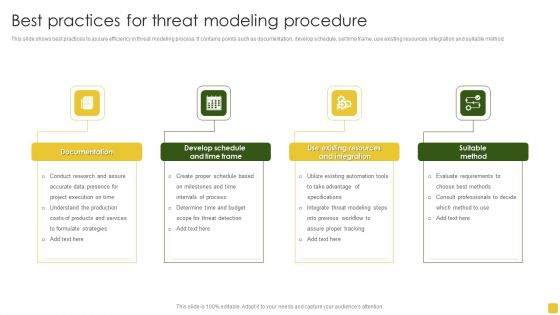
Best Practices For Threat Modeling Procedure Themes PDF
This slide shows best practices to assure efficiency in threat modeling process. It contains points such as documentation, develop schedule, set time frame, use existing resources, integration and suitable method.Presenting Best Practices For Threat Modeling Procedure Themes PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Project Execution, Determine Budget, Existing Resources. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
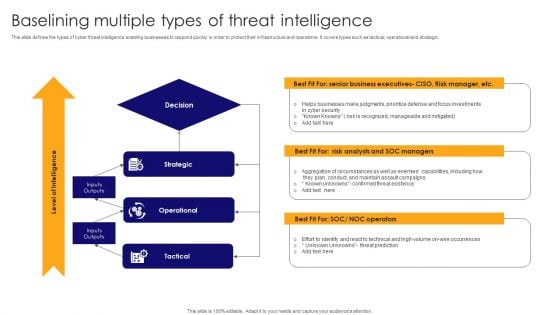
Baselining Multiple Types Of Threat Intelligence Pictures PDF
This slide defines the types of cyber threat intelligence enabling businesses to respond quickly in order to protect their infrastructure and operations. It covers types such as tactical, operational and strategic. Presenting Baselining Multiple Types Of Threat Intelligence Pictures PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Strategic, Operational, Tactical . This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
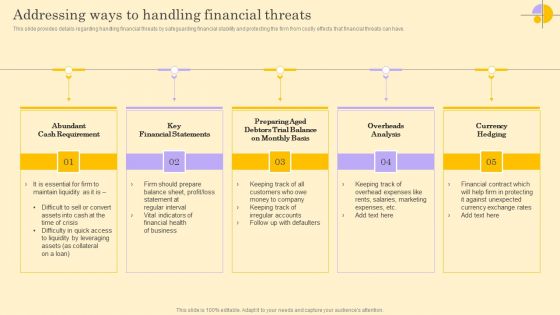
Addressing Ways To Handling Financial Threats Ideas PDF
This slide provides details regarding handling financial threats by safeguarding financial stability and protecting the firm from costly effects that financial threats can have. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Addressing Ways To Handling Financial Threats Ideas PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Online Crime With Eye And Threat Symbol Ppt PowerPoint Presentation File Background PDF
Persuade your audience using this online crime with eye and threat symbol ppt powerpoint presentation file background pdf. This PPT design covers two stages, thus making it a great tool to use. It also caters to a variety of topics including online crime with eye and threat symbol. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.


 Continue with Email
Continue with Email

 Home
Home


































