Technology Risk

Hazard Control Layout Powerpoint Presentation Templates
This is a hazard control layout powerpoint presentation templates. This is a six stage process. The stages in this process are define risk model, gather risk data, process risk data, stat monitoring, central data review, measure risk factors.

Cloud Security Threats Malware Attacks Sample PDF
This slide represents the malware threat of cloud security and how it can affect data stored on the cloud, further leading to company loss. This is a Cloud Security Threats Malware Attacks Sample PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Technology, Targets, Information. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Cyber Security Hazards Management Program Icon Slides PDF
Persuade your audience using this Cyber Security Hazards Management Program Icon Slides PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Cyber Security, Management Program. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
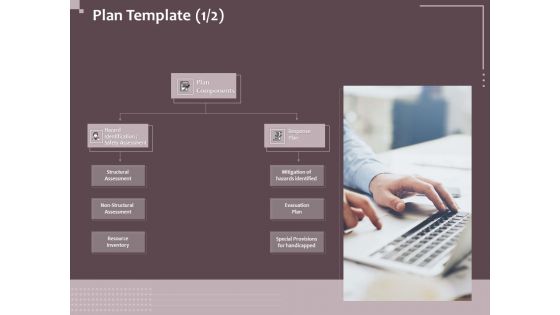
Hazard Administration Plan Components Ppt Styles Visuals PDF
Presenting this set of slides with name hazard administration plan components ppt styles visuals pdf. This is a three stage process. The stages in this process are hazard identification or safety assessment, response plan, assessment, mitigation. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Hazard Administration Purpose Ppt Infographic Template Example File
Presenting this set of slides with name hazard administration purpose ppt infographic template example file. This is a five stage process. The stages in this process are to respond in timely and efficient manner, to undertake the rescue operations, to minimize losses. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

The Problem Hospitality Management System Elevator Pitch Deck Graphics PDF
Following provides information about the major points faced by merchants such as old technology, poor order management and customer wait time. This is a The Problem Hospitality Management System Elevator Pitch Deck Graphics PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Old Technology, Poor Management Multiple Orders, Customer Wait Time. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
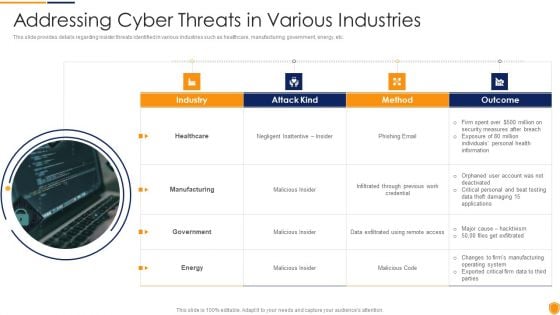
Mitigating Cybersecurity Threats And Vulnerabilities Addressing Cyber Threats Portrait PDF
This slide provides details regarding insider threats identified in various industries such as healthcare, manufacturing, government, energy, etc. This is a mitigating cybersecurity threats and vulnerabilities addressing cyber threats portrait pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like healthcare, manufacturing, government, energy. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

The Problem Point Of Sale Application Startup Fundraising Pitch Deck Introduction PDF
Following provides information about the major points faced by merchants such as old technology, poor order management and customer wait time.This is a The Problem Point Of Sale Application Startup Fundraising Pitch Deck Introduction PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Old Technology, Poor Management, Customer Wait Time. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cafe Point Of Sale System Pitch Deck The Problem Restaurant Pos System Pitch Deck Sample PDF
Following provides information about the major points faced by merchants such as old technology, poor order management and customer wait time.Presenting cafe point of sale system pitch deck the problem restaurant pos system pitch deck sample pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like old technology, poor management of multiple orders, customer wait time. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Security Threats Malware Attacks Cloud Computing Security IT Ppt Show Diagrams PDF
This slide represents the malware threat of cloud security and how it can affect data stored on the cloud, further leading to company loss. Presenting cloud security threats malware attacks cloud computing security it ppt show diagrams pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like cloud administrations, cyber criminals, technology. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Grid Computing For High Performance Solutions Grid Computing Types Collaborative Grid Introduction PDF
This slide represents the collaborative grid computing type that solves the problems through seamless cooperation. It uses numerous technologies to help users collaborate to remove regional barriers and improve the work experience. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Grid Computing For High Performance Solutions Grid Computing Types Collaborative Grid Introduction PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
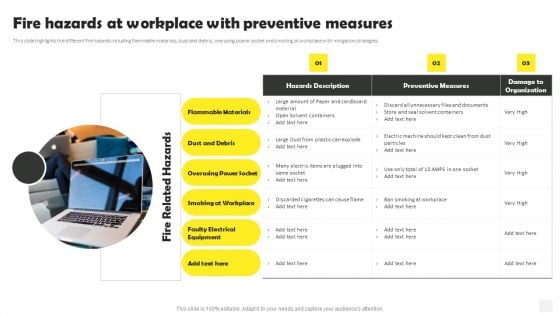
Occupational Health And Safety At Workplace Fire Hazards At Workplace With Preventive Inspiration PDF
This slide highlights the different fire hazards including flammable materials, dust and debris, overusing power socket and smoking at workplace with mitigation strategies. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Occupational Health And Safety At Workplace Fire Hazards At Workplace With Preventive Inspiration PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Cloud Security Threats Compliance Violations Demonstration PDF
This slide depicts the value of compliance violations threat of cloud security in a business and how fast an organization can switch to a non compliance state. This is a Cloud Security Threats Compliance Violations Demonstration PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Businesses, Organizations, Authentication Procedures. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
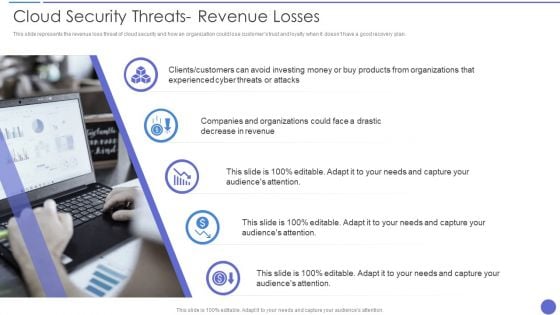
Cloud Security Threats Revenue Losses Themes PDF
This slide represents the revenue loss threat of cloud security and how an organization could lose customers trust and loyalty when it doesnt have a good recovery plan. Presenting Cloud Security Threats Revenue Losses Themes PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Organizations, Revenue, Investing Money. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Security Threats Shared Vulnerabilities Graphics PDF
This slide describes how organizations and providers share vulnerabilities of a system, so each party must take precautions to protect data. This is a Cloud Security Threats Shared Vulnerabilities Graphics PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Could, Organizations, Measures. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Threats Response Playbook Cyber Threat Facts Figures And Statistics Themes PDF
This slide portrays statistical information about cyber threats. Information covered is related data breach, ransomware attacks, cyberthreat complaints and phishing attack.This is a IT Threats Response Playbook Cyber Threat Facts Figures And Statistics Themes PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Ransomware Attacks, Cyberthreat Complaints, Trillion Annually. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Enterprise Problem Solving And Intellect Business Intelligence KPI Metrics Profit Ppt PowerPoint Presentation Infographic Template Portrait PDF
Presenting this set of slides with name enterprise problem solving and intellect business intelligence kpi metrics profit ppt powerpoint presentation infographic template portrait pdf. This is a four stage process. The stages in this process are days since last accident, net profit margin, remaining inventory, response time. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Steps Of Vulnerability Assessment With Creating Backups Ppt PowerPoint Presentation Model Background Images PDF
Presenting this set of slides with name steps of vulnerability assessment with creating backups ppt powerpoint presentation model background images pdf. This is a eight stage process. The stages in this process are build an inventory of all it assets, categorize by risk and priority, monitor and evaluate patch updates, create backups, implement configuration management, implement configuration management, maintained patches regularly, document patch management process. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Macro Environmental Level Threat Detection And Analysis Icon Demonstration PDF
Presenting Macro Environmental Level Threat Detection And Analysis Icon Demonstration PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Macro Environmental, Level Threat, Detection And Analysis. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Identifying Employees For Potential Insider Threat Icon Portrait PDF
Presenting Identifying Employees For Potential Insider Threat Icon Portrait PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Identifying Employees, Potential Insider, Threat Icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Threat Assessment Icon With Magnifying Glass Ppt Icon Topics PDF
Presenting Threat Assessment Icon With Magnifying Glass Ppt Icon Topics PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Threat Assessment Icon, Magnifying Glass. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Two Factor Authentication Icon For Cyber Threat Prevention Background PDF

Grid Computing Types Collaborative Grid Inspiration PDF
This slide represents the collaborative grid computing type that solves the problems through seamless cooperation. It uses numerous technologies to help users collaborate to remove regional barriers and improve the work experience. Present like a pro with Grid Computing Types Collaborative Grid Inspiration PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
Problem Analysis Overview Procedure Icon Summary PDF
Presenting Problem Analysis Overview Procedure Icon Summary PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Problem Analysis, Overview Procedure Icon . This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
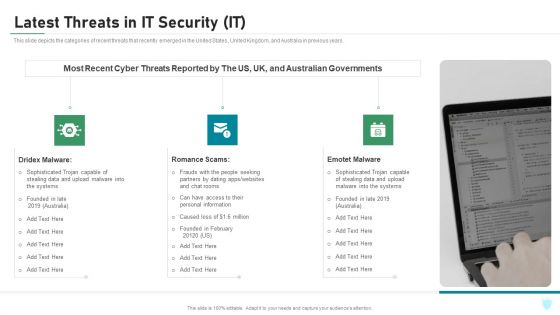
Latest Threats In IT Security IT Ppt Gallery Elements PDF
This slide depicts the categories of recent threats that recently emerged in the United States, United Kingdom, and Australia in previous years. Presenting latest threats in it security it ppt gallery elements pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like dridex malware, romance scams, emotet malware. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Insider Threat Icon For Financial Information Phishing Mockup PDF
Presenting Insider Threat Icon For Financial Information Phishing Mockup PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Insider Threat Icon, Financial Information Phishing. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Cyber Security Icon For Cyber Threat Prevention Information PDF
Presenting Cyber Security Icon For Cyber Threat Prevention Information PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Cyber Security, Icon Cyber Threat, Prevention. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cloud Security Threats Loss Of Data Guidelines PDF
This slide represents the data loss threat of cloud security it is essential to secure organization data and create backups. This is a Cloud Security Threats Loss Of Data Guidelines PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Strategies, Service Provider, Organization. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
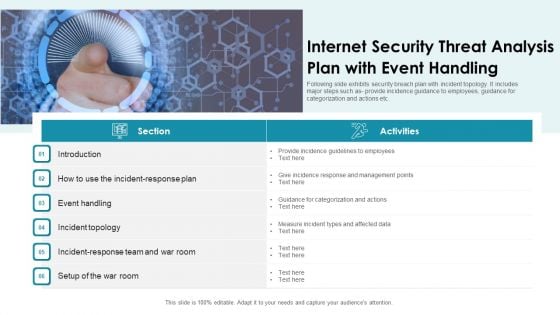
Internet Security Threat Analysis Plan With Event Handling Summary PDF
Following slide exhibits security breach plan with incident topology. It includes major steps such as- provide incidence guidance to employees, guidance for categorization and actions etc. Presenting internet security threat analysis plan with event handling summary pdf to dispense important information. This template comprises one stage. It also presents valuable insights into the topics including internet security threat analysis plan with event handling. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
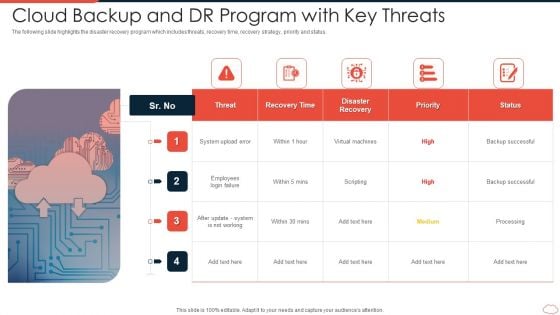
Cloud Backup And DR Program With Key Threats Topics PDF
The following slide highlights the disaster recovery program which includes threats, recovery time, recovery strategy, priority and status. Persuade your audience using this cloud backup and dr program with key threats topics pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including cloud backup and dr program with key threats. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Internet Security Threat Icon On Computer Elements PDF
Presenting internet security threat icon on computer elements pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including internet security threat icon on computer. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Digital Terrorism Threat Attacking Network Icon Brochure PDF
Presenting Digital Terrorism Threat Attacking Network Icon Brochure PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Digital Terrorism Threat Attacking, Network Icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Purpose Of IT Threats Response Playbook Professional PDF
This is a Purpose Of IT Threats Response Playbook Professional PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Standardized Cybersecurity, Future Security, Appropriate Manner. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
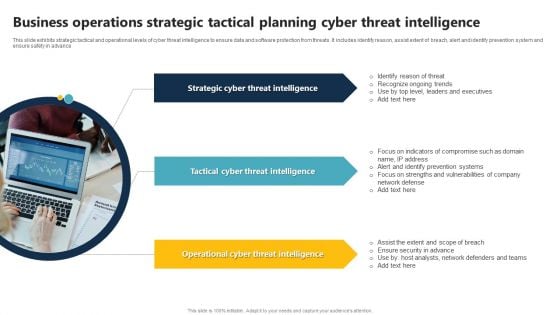
Business Operations Strategic Tactical Planning Cyber Threat Intelligence Summary PDF
This slide exhibits strategic tactical and operational levels of cyber threat intelligence to ensure data and software protection from threats. It includes identify reason, assist extent of breach, alert and identify prevention system and ensure safety in advance. Persuade your audience using this Business Operations Strategic Tactical Planning Cyber Threat Intelligence Summary PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Strategic Cyber Threat Intelligence, Tactical Cyber Threat Intelligence, Operational Cyber Threat Intelligence. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Sales Leads Online Ppt Powerpoint Presentation Styles Graphics Download Cpb
This is a sales leads online ppt powerpoint presentation styles graphics download cpb. This is a two stage process. The stages in this process are sales leads online.
Cyber Threat Organizational Prevention Based Strategy Icon Graphics PDF
Increase audience engagement and knowledge by dispensing information using Cyber Threat Organizational Prevention Based Strategy Icon Graphics PDF. This template helps you present information on three stages. You can also present information on Cyber Threat Organizational, Prevention Based Strategy Icon using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.

Cloud Security Threats Contract Breaches With Clients Download PDF
This slide defines the contract breaches with clients and customers that could be the biggest threat to the organizational data. Presenting Cloud Security Threats Contract Breaches With Clients Download PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Organization, Business Partners, Information Could. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Infra Cyber Security Icon For Eliminating Cyber Threats Designs PDF
Presenting Infra Cyber Security Icon For Eliminating Cyber Threats Designs PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Infra Cyber Security Icon, Eliminating Cyber Threats. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Business Threat Organizational Prevention Based Strategy Icon Pictures PDF
Introducing Business Threat Organizational Prevention Based Strategy Icon Pictures PDF. to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Business Threat Organizational, Prevention Based Strategy, using this template. Grab it now to reap its full benefits.
Intelligence Initiatives For Threat Prevention Icon Elements PDF
Presenting Intelligence Initiatives For Threat Prevention Icon Elements PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Intelligence Initiatives, Threat Prevention Icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Mitigating Cybersecurity Threats And Vulnerabilities Addressing Indicators Associated Icons PDF
This slide provides details regarding indicators associated to insider threats in terms of traits, demeanor and goals, etc. Presenting mitigating cybersecurity threats and vulnerabilities addressing indicators associated icons pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like user accounts, authentication levels, data exfiltration. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

SWOT Analysis Threats In An Airline Company Summary PDF
The slide shows the key future opportunity points for the company, which will be positive sign for the company for its growth. Major points includes growth in US airlines industry, growing worlds economy, recent acquisitions and merger etc. Presenting swot analysis threats in an airline company summary pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like high level of debt and other obligations, environmental laws, dependent on the price and availability of aircraft fuel. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
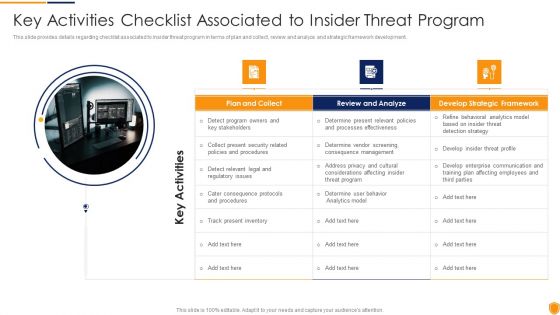
Mitigating Cybersecurity Threats And Vulnerabilities Key Activities Checklist Diagrams PDF
This slide provides details regarding checklist associated to insider threat program in terms of plan and collect, review and analyze and strategic framework development. This is a mitigating cybersecurity threats and vulnerabilities key activities checklist diagrams pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like plan and collect, review and analyze, develop strategic framework. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
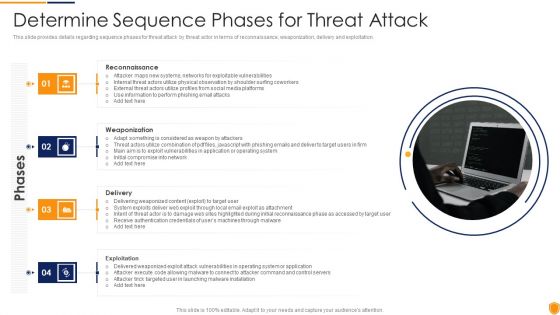
Mitigating Cybersecurity Threats And Vulnerabilities Determine Sequence Phases Elements PDF
This slide provides details regarding sequence phases for threat attack by threat actor in terms of reconnaissance, weaponization, delivery and exploitation. This is a mitigating cybersecurity threats and vulnerabilities determine sequence phases elements pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like reconnaissance, weaponization, delivery, exploitation. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
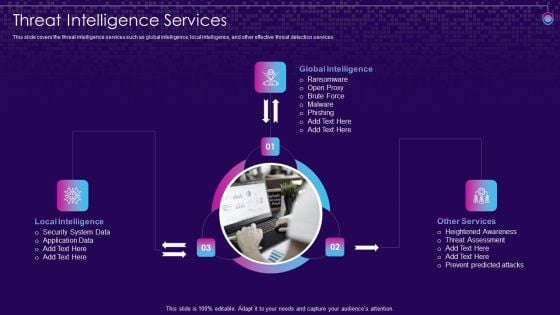
SIEM Services Threat Intelligence Services Ppt Infographic Template Mockup PDF
This slide covers the threat intelligence services such as global intelligence, local intelligence, and other effective threat detection services. This is a siem services threat intelligence services ppt infographic template mockup pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like local intelligence, global intelligence, other services. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
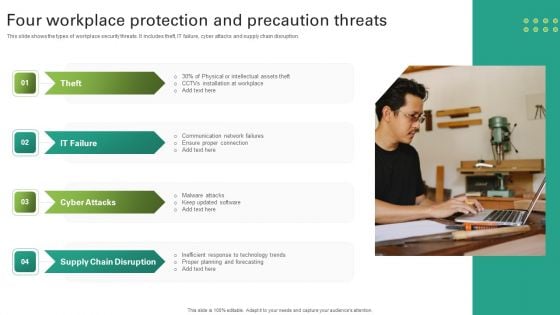
Four Workplace Protection And Precaution Threats Template PDF
This slide shows the types of workplace security threats. It includes theft, IT failure, cyber attacks and supply chain disruption. Presenting Four Workplace Protection And Precaution Threats Template PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Theft, It Failure, Cyber Attacks. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
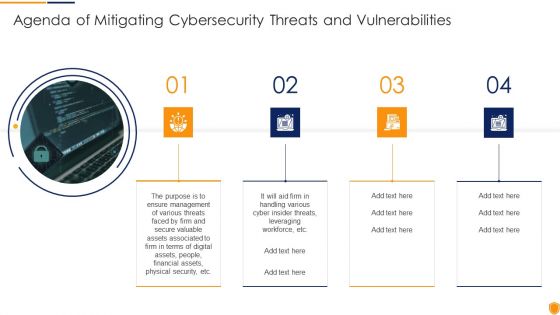
Agenda Of Mitigating Cybersecurity Threats And Vulnerabilities Guidelines PDF
Presenting agenda of mitigating cybersecurity threats and vulnerabilities guidelines pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like agenda of mitigating cybersecurity threats and vulnerabilities. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Table Of Contents Mitigating Cybersecurity Threats And Vulnerabilities Portrait PDF
Presenting table of contents mitigating cybersecurity threats and vulnerabilities portrait pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like current scenario assessment, secure digital assets, physical security, natural calamity threats. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
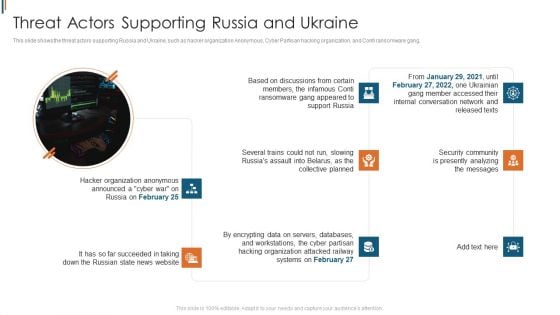
Ukraine Cyberwarfare Threat Actors Supporting Russia And Ukraine Graphics Pdf
This slide shows the threat actors supporting Russia and Ukraine, such as hacker organization Anonymous, Cyber Partisan hacking organization, and Conti ransomware gang. This is a ukraine cyberwarfare threat actors supporting russia and ukraine graphics pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security community is presently analyzing the messages, hacker organization anonymous announced, several trains could not run, slowing russias assault. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
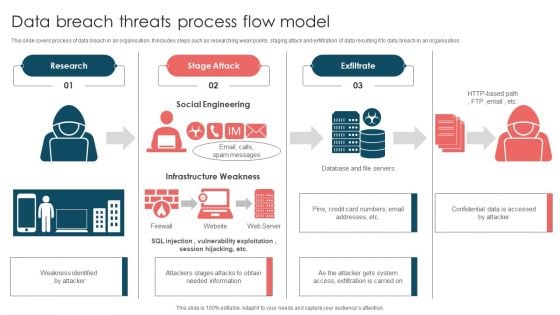
Data Breach Threats Process Flow Model Ppt Model Maker PDF
This slide covers process of data breach in an organisation. It includes steps such as researching weak points, staging attack and exfiltration of data resulting it to data breach in an organisation. Persuade your audience using this Data Breach Threats Process Flow Model Ppt Model Maker PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Research, Stage Attack, Exfiltrate, Social Engineering. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Safety And Security Threat Report With Action Plan Mockup PDF
This slide shows report which can be used by an organization to prepare server security threat report. It includes date, time, description, action plan and remarks related to incident. Presenting Safety And Security Threat Report With Action Plan Mockup PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Action Plan, Remarks, Diagnostic. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
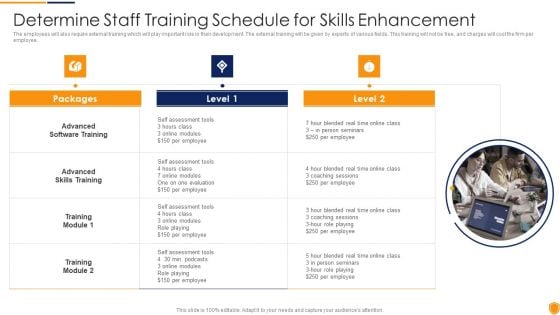
Mitigating Cybersecurity Threats And Vulnerabilities Determine Staff Training Rules PDF
The employees will also require external training which will play important role in their development. The external training will be given by experts of various fields. This training will not be free, and charges will cost the firm per employee. This is a mitigating cybersecurity threats and vulnerabilities determine staff training rules pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like advanced software training, advanced skills training, training module. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
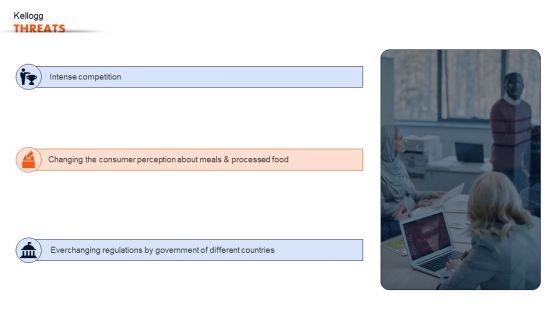
Ready To Eat Food Market Analysis Kellogg Threats Guidelines PDF
Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Ready To Eat Food Market Analysis Kellogg Threats Guidelines PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
Service Desk Problem Management Icon Formats PDF
Presenting Service Desk Problem Management Icon Formats PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Service Desk Problem Management Icon, Retain Customers. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Mitigating Cybersecurity Threats And Vulnerabilities Table Of Contents Infographics PDF
Presenting mitigating cybersecurity threats and vulnerabilities table of contents infographics pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like leveraging workforce, budget assessment, dashboard, impact assessment. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
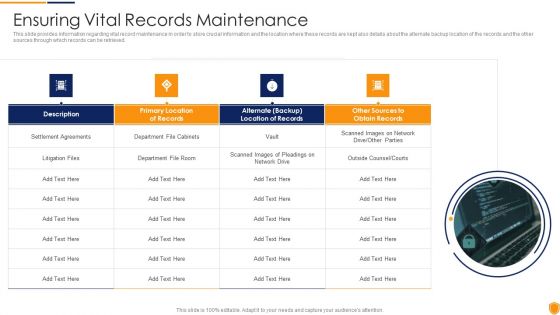
Mitigating Cybersecurity Threats And Vulnerabilities Ensuring Vital Records Inspiration PDF
This slide provides information regarding vital record maintenance in order to store crucial information and the location where these records are kept also details about the alternate backup location of the records and the other sources through which records can be retrieved. This is a mitigating cybersecurity threats and vulnerabilities ensuring vital records inspiration pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like ensuring vital records maintenance. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
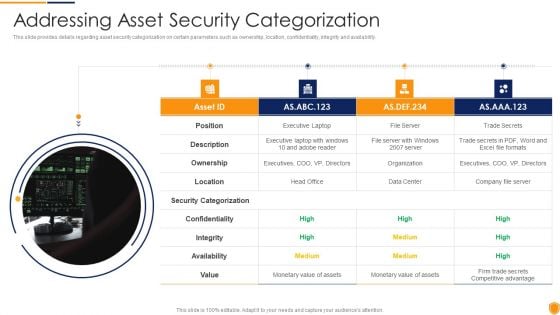
Mitigating Cybersecurity Threats And Vulnerabilities Addressing Asset Security Elements PDF
This slide provides details regarding asset security categorization on certain parameters such as ownership, location, confidentiality, integrity and availability. This is a mitigating cybersecurity threats and vulnerabilities addressing asset security elements pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like ownership, location, integrity, security categorization. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Business Problems And Their Solutions Icons PDF
This slide provides the business problems Delivery in bad weather, Odd time delivery, uncertainty etc. and their solutions like delivery by car, 24 or 7 delivery etc. This is a business problems and their solutions icons pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like problem, solution. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Mitigating Cybersecurity Threats And Vulnerabilities Incident Reporting Themes PDF
This slide will help in providing an overview of the various reported incidents, average cost per incident and number of people involved in the various incidents across different departments. Presenting mitigating cybersecurity threats and vulnerabilities incident reporting themes pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like incident reporting by different departments. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Insider Threat Detection In Computer System Icon Sample PDF
Persuade your audience using this Insider Threat Detection In Computer System Icon Sample PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Insider Threat Detection, Computer System, Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.


 Continue with Email
Continue with Email

 Home
Home


































