Technology Security
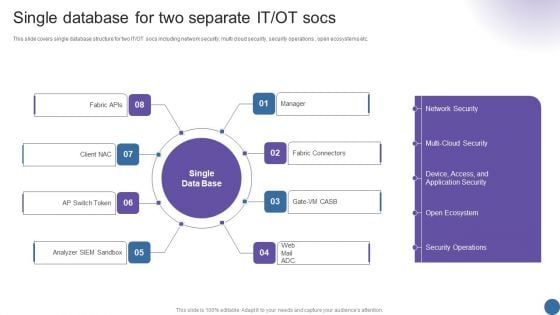
Single Database For Two Separate IT OT Socs Managing Organizational Transformation Professional PDF
This slide covers single database structure for two IT OT socs including network security, multi cloud security, security operations , open ecosystems etc. Presenting Single Database For Two Separate IT OT Socs Managing Organizational Transformation Professional PDF to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like Single Database, Two Separate, Fabric Connectors. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
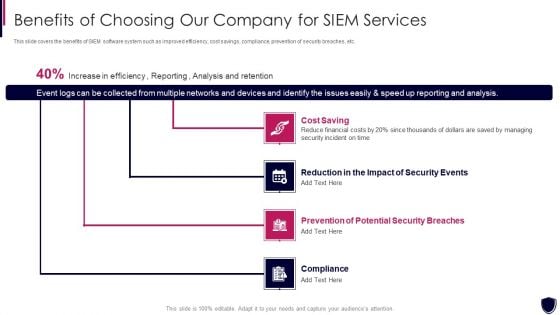
Enhancing Cyber Safety With Vulnerability Administration Benefits Of Choosing Our Company Inspiration PDF
This slide covers the benefits of SIEM software system such as improved efficiency, cost savings, compliance, prevention of security breaches, etc. Presenting enhancing cyber safety with vulnerability administration benefits of choosing our company inspiration pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like cost saving, reduction in the impact of security events, prevention of potential security breaches, compliance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
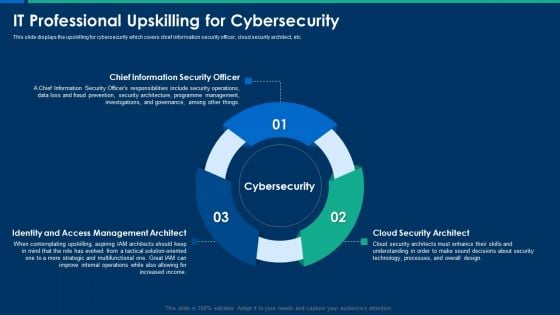
CIO Role In Digital Evolution IT Professional Upskilling For Cybersecurity Themes PDF
This slide displays the upskilling for cybersecurity which covers chief information security officer, cloud security architect, etc. This is a CIO Role In Digital Evolution IT Professional Upskilling For Cybersecurity Themes PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Chief Information, Management Architect, Cloud Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
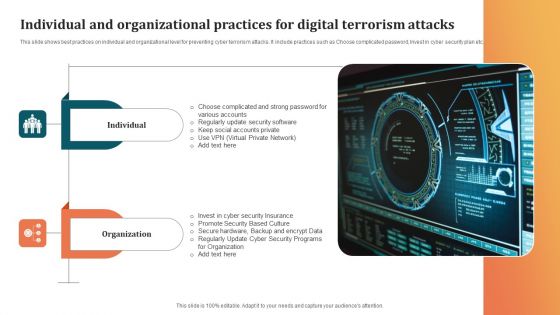
Individual And Organizational Practices For Digital Terrorism Attacks Microsoft PDF
This slide shows best practices on individual and organizational level for preventing cyber terrorism attacks. It include practices such as Choose complicated password, Invest in cyber security plan etc. Pitch your topic with ease and precision using this Individual And Organizational Practices For Digital Terrorism Attacks Microsoft PDF. This layout presents information on Organization, Promote Security, Security Insurance. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
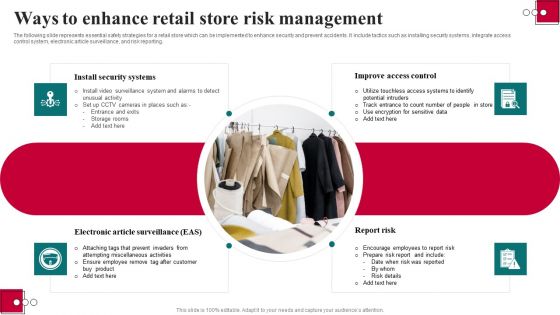
Ways To Enhance Retail Store Risk Management Introduction PDF
The following slide represents essential safety strategies for a retail store which can be implemented to enhance security and prevent accidents. It include tactics such as installing security systems, integrate access control system, electronic article surveillance, and risk reporting. Pitch your topic with ease and precision using this Ways To Enhance Retail Store Risk Management Introduction PDF. This layout presents information on Electronic Article Surveillance, Report Risk, Install Security Systems. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Influencer Marketing 4 Months Project Status Update Icon Slides PDF
This slide covers the four months project status update of software implementation project undertaken by the IT team. It includes various activities to be performed under IT help desk, web server, network and global security.Showcasing this set of slides titled Influencer Marketing 4 Months Project Status Update Icon Slides PDF. The topics addressed in these templates are Global Security, Network Speed, Security Plan . All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
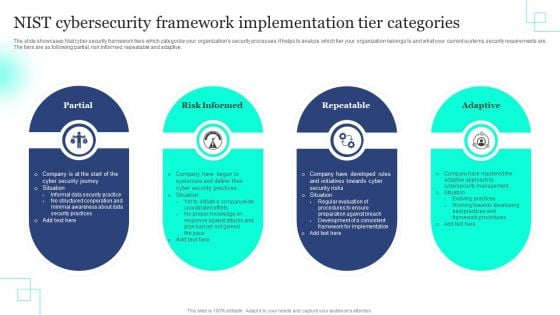
NIST Cybersecurity Framework Implementation Tier Categories Rules PDF
The slide showcases Nist cyber security framework tiers which categorize your organizations security processes, it helps to analyze which tier your organization belongs to and what your current systems security requirements are. The tiers are as following partial, risk informed, repeatable and adaptive. Persuade your audience using this NIST Cybersecurity Framework Implementation Tier Categories Rules PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Partial, Risk Informed, Repeatable . Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
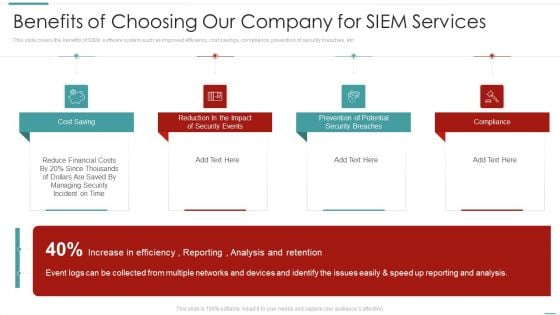
Risk Recognition Automation Benefits Of Choosing Our Company For Siem Services Ppt Gallery Design Inspiration PDF
This slide covers the benefits of SIEM software system such as improved efficiency, cost savings, compliance, prevention of security breaches, etc. This is a risk recognition automation benefits of choosing our company for siem services ppt gallery design inspiration pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cost saving, prevention of potential security breaches, compliance, reduction in the impact of security events. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
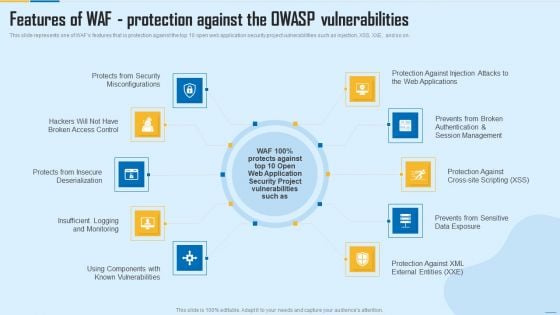
Features Of WAF Protection Against The Owasp Vulnerabilities WAF Platform Summary PDF
This slide represents one of WAFs features that is protection against the top 10 open web application security project vulnerabilities such as injection, XSS, XXE, and so on. This is a Features Of WAF Protection Against The Owasp Vulnerabilities WAF Platform Summary PDF template with various stages. Focus and dispense information on ten stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Misconfigurations, Session Management, Security Project. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

SIEM Benefits Of Choosing Our Company For SIEM Services Ppt File Outfit PDF
This slide covers the benefits of SIEM software system such as improved efficiency, cost savings, compliance, prevention of security breaches, etc. Presenting siem benefits of choosing our company for siem services ppt file outfit pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like cost saving, reduction in the impact of security events, prevention of potential security breaches, compliance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
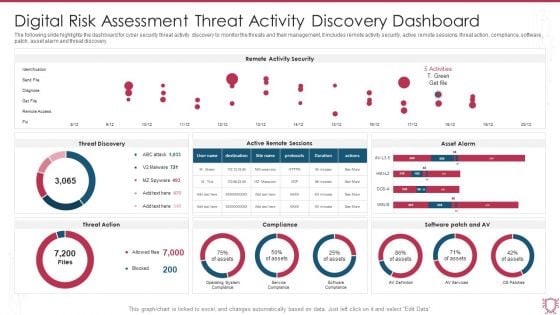
Digital Risk Assessment Threat Activity Discovery Dashboard Ppt Ideas Skills PDF
The following slide highlights the dashboard for cyber security threat activity discovery to monitor the threats and their management, it includes remote activity security, active remote sessions, threat action, compliance, software patch, asset alarm and threat discovery. Pitch your topic with ease and precision using this Digital Risk Assessment Threat Activity Discovery Dashboard Ppt Ideas Skills PDF. This layout presents information on Remote Activity Security, Threat Discovery, Asset Alarm. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Portable Home Safety Systems Company Profile Executive Leadership And Management Team Rules PDF
This slide highlights the security company leadership and management team which includes president and CEO, executive vice president of finance, EVP home security, chief administration officer. This is a Portable Home Safety Systems Company Profile Executive Leadership And Management Team Rules PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Finance, Home Security, Management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
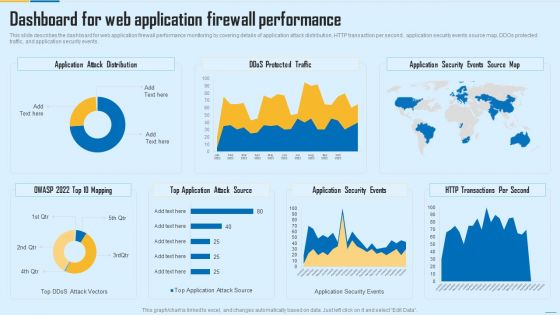
Dashboard For Web Application Firewall Performance WAF Platform Diagrams PDF
This slide describes the dashboard for web application firewall performance monitoring by covering details of application attack distribution, HTTP transaction per second, application security events source map, DDOs protected traffic, and application security events. Deliver an awe inspiring pitch with this creative Dashboard For Web Application Firewall Performance WAF Platform Diagrams PDF bundle. Topics like Application Attack Distribution, Application Security Events, Transactions Per Second can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Need For Ethical Hacking Ppt Gallery Portfolio PDF
This slide depicts the reasons to describe the need for ethical hacking, including identification and correction of security flaws, aid in development and quality control, and evaluation of the companys security and regulatory compliance. This is a need for ethical hacking ppt gallery portfolio pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like quality control, development, security, system, measures. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Process Of Digital Risk Assessment Management Ppt Summary Graphics PDF
The following slide highlights the process of cyber security asset management depicting four steps which include asset inventory, synchronization, security gaps and response to save assets and mitigate the risk in minimum time. Presenting Process Of Digital Risk Assessment Management Ppt Summary Graphics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Asset Inventory, Synchronization, Response, Security Gaps. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

ESO System Center Team Roles And Responsibilities Ppt PowerPoint Presentation File Slides PDF
This slide covers enterprise security operation center team roles and responsibilities. It involves key roles such as incident responder, security investigator, advanced security analyst and SOC manager. Pitch your topic with ease and precision using this ESO System Center Team Roles And Responsibilities Ppt PowerPoint Presentation File Slides PDF. This layout presents information on SOC Team Roles, Responsibilities, Tier. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
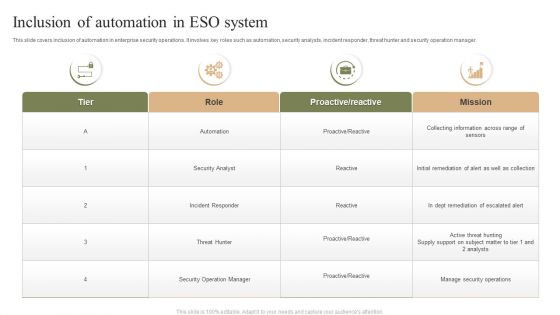
Inclusion Of Automation In ESO System Ppt PowerPoint Presentation File Maker PDF
This slide covers inclusion of automation in enterprise security operations. It involves key roles such as automation, security analysts, incident responder, threat hunter and security operation manager. Pitch your topic with ease and precision using this Inclusion Of Automation In ESO System Ppt PowerPoint Presentation File Maker PDF. This layout presents information on Mission, Role, Tier. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Cybersecurity Key Performance Indicators With Applications Summary Pdf
Pitch your topic with ease and precision using this Cybersecurity Key Performance Indicators With Applications Summary Pdf This layout presents information on Identify Weaknesses, Review Improvement, Security Policies It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide showcases the cyber security key performance indicators with applications which helps an organization to determine readiness. It include details such as security policies, identify weaknesses, obligation to compliance framework, etc.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring Tools Diagrams PDF
This slide provides information about some of the best security monitoring tools that are available with the security monitoring manager and what tool is selected by the security monitoring manager based on tool implementation costs, tool implementation time etc. Deliver an awe inspiring pitch with this creative continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring tools diagrams pdf bundle. Topics like cybersecurity monitoring tools to be implemented can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
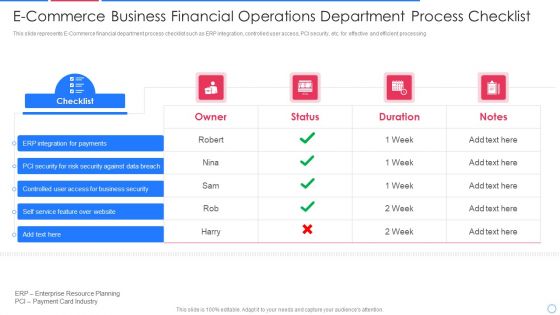
E Commerce Business Financial Operations Department Process Checklist Information PDF
This slide represents E-Commerce financial department process checklist such as ERP integration, controlled user access, PCI security, etc. for effective and efficient processing Pitch your topic with ease and precision using this e commerce business financial operations department process checklist information pdf This layout presents information on integration for payments, security for risk security against, controlled user access It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
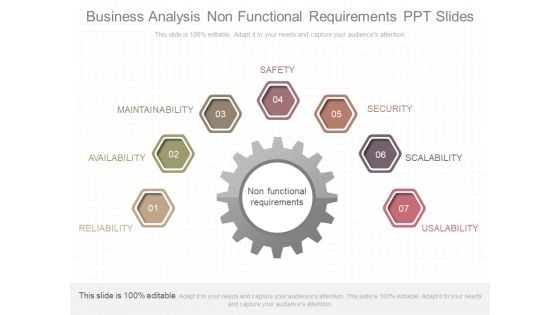
Business Analysis Non Functional Requirements Ppt Slides
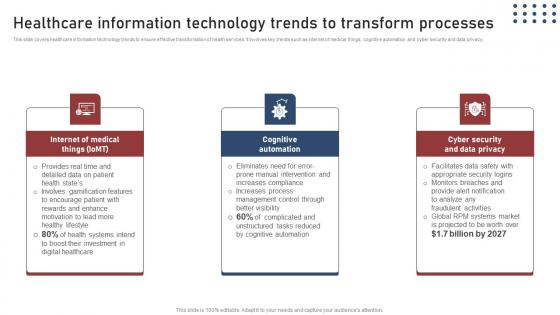
Healthcare Information Transforming Medical Workflows Via His Integration Designs Pdf
This slide covers healthcare information technology trends to ensure effective transformation of health services. It involves key trends such as internet of medical things, cognitive automation and cyber security and data privacy. If you are looking for a format to display your unique thoughts, then the professionally designed Healthcare Information Transforming Medical Workflows Via His Integration Designs Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Healthcare Information Transforming Medical Workflows Via His Integration Designs Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide covers healthcare information technology trends to ensure effective transformation of health services. It involves key trends such as internet of medical things, cognitive automation and cyber security and data privacy.
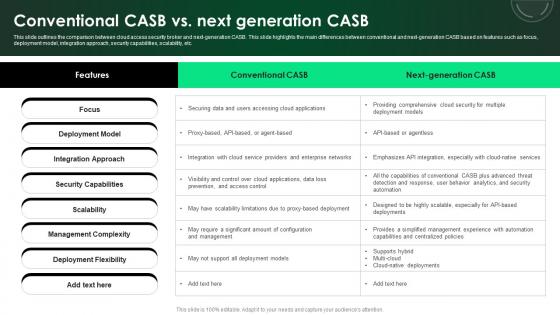
CASB 2 0 IT Conventional CASB Vs Next Generation CASB
This slide outlines the comparison between cloud access security broker and next-generation CASB. This slide highlights the main differences between conventional and next-generation CASB based on features such as focus, deployment model, integration approach, security capabilities, scalability, etc. Find a pre-designed and impeccable CASB 2 0 IT Conventional CASB Vs Next Generation CASB. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide outlines the comparison between cloud access security broker and next-generation CASB. This slide highlights the main differences between conventional and next-generation CASB based on features such as focus, deployment model, integration approach, security capabilities, scalability, etc.

Data Breach Prevention Strategies For Enterprises Data Fortification Strengthening Defenses
The purpose of this slide is to outline the data breach mitigation strategies for businesses. These include access control, encryption, web security solutions, network security, up-to-date software and hardware, preparation, training employees and users, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Data Breach Prevention Strategies For Enterprises Data Fortification Strengthening Defenses. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. The purpose of this slide is to outline the data breach mitigation strategies for businesses. These include access control, encryption, web security solutions, network security, up-to-date software and hardware, preparation, training employees and users, etc.
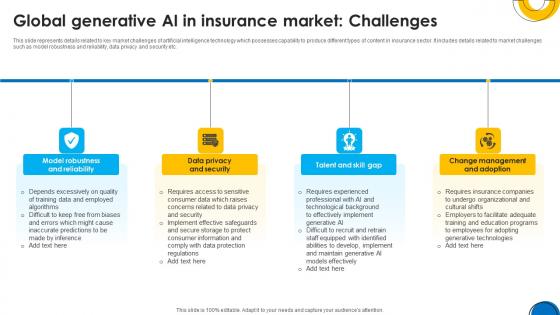
Implementing ChatGpt In Insurance Global Generative AI In Insurance Market ChatGpt SS V
This slide represents details related to key market challenges of artificial intelligence technology which possesses capability to produce different types of content in insurance sector. It includes details related to market challenges such as model robustness and reliability, data privacy and security etc. If you are looking for a format to display your unique thoughts, then the professionally designed Implementing ChatGpt In Insurance Global Generative AI In Insurance Market ChatGpt SS V is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Implementing ChatGpt In Insurance Global Generative AI In Insurance Market ChatGpt SS V and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide represents details related to key market challenges of artificial intelligence technology which possesses capability to produce different types of content in insurance sector. It includes details related to market challenges such as model robustness and reliability, data privacy and security etc.
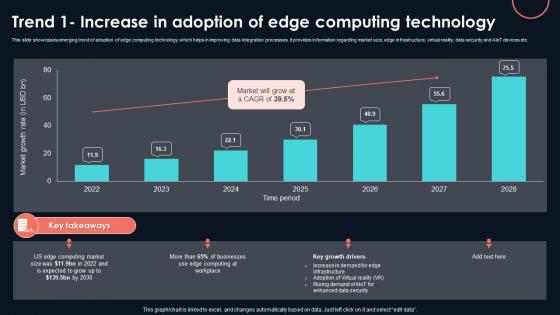
Trend 1 Increase In Adoption Of Edge Developing Strategic Insights Using Big Data Analytics SS V
This slide showcases emerging trend of adoption of edge computing technology which helps in improving data integration processes. It provides information regarding market size, edge infrastructure, virtual reality, data security and AIoT devices etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Trend 1 Increase In Adoption Of Edge Developing Strategic Insights Using Big Data Analytics SS V to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Trend 1 Increase In Adoption Of Edge Developing Strategic Insights Using Big Data Analytics SS V. This slide showcases emerging trend of adoption of edge computing technology which helps in improving data integration processes. It provides information regarding market size, edge infrastructure, virtual reality, data security and AIoT devices etc.
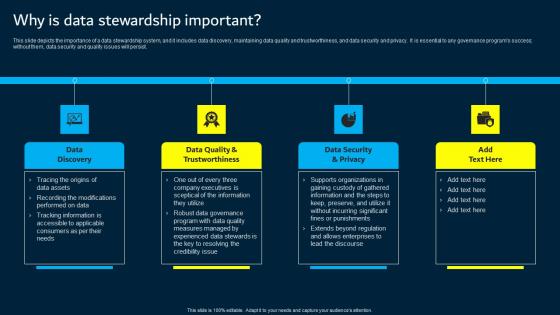
Why Is Data Stewardship Important Data Custodianship Formats Pdf
This slide depicts the importance of a data stewardship system, and it includes data discovery, maintaining data quality and trustworthiness, and data security and privacy. It is essential to any governance program s success without them, data security and quality issues will persist. Boost your pitch with our creative Why Is Data Stewardship Important Data Custodianship Formats Pdf. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide depicts the importance of a data stewardship system, and it includes data discovery, maintaining data quality and trustworthiness, and data security and privacy. It is essential to any governance program s success without them, data security and quality issues will persist.
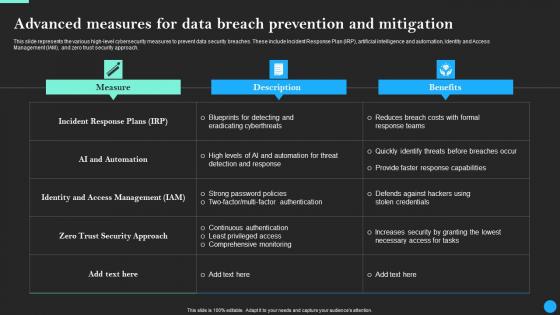
Advanced Measures For Data Breach Prevention Data Breach Prevention Inspiration Pdf
This slide represents the various high-level cybersecurity measures to prevent data security breaches. These include Incident Response Plan IRP, artificial intelligence and automation, Identity and Access Management IAM, and zero trust security approach. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Advanced Measures For Data Breach Prevention Data Breach Prevention Inspiration Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide represents the various high-level cybersecurity measures to prevent data security breaches. These include Incident Response Plan IRP, artificial intelligence and automation, Identity and Access Management IAM, and zero trust security approach.
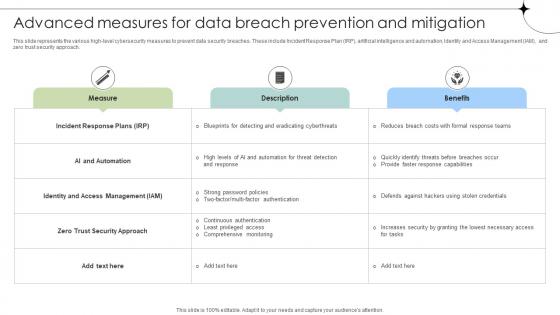
Advanced Measures For Data Breach Prevention And Mitigation Data Fortification Strengthening Defenses
This slide represents the various high-level cybersecurity measures to prevent data security breaches. These include Incident Response Plan IRP, artificial intelligence and automation, Identity and Access Management IAM, and zero trust security approach.Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Advanced Measures For Data Breach Prevention And Mitigation Data Fortification Strengthening Defenses for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide represents the various high-level cybersecurity measures to prevent data security breaches. These include Incident Response Plan IRP, artificial intelligence and automation, Identity and Access Management IAM, and zero trust security approach.

Page Experience Signals In Google Search Console Training Ppt
This slide covers search signals for page experience largely known as core web vitals. It also includes KPIs such as mobile-friendly experience, safe browsing experience, HTTPS security and no intrusive interstitials.

Stock Photo Ball With Big Data Text For Data Protection Concept PowerPoint Slide
Graphic of ball with big data text has been used to craft this power point template. This image template contains the concept of data protection. Use this image for data security related topics in any presentation.
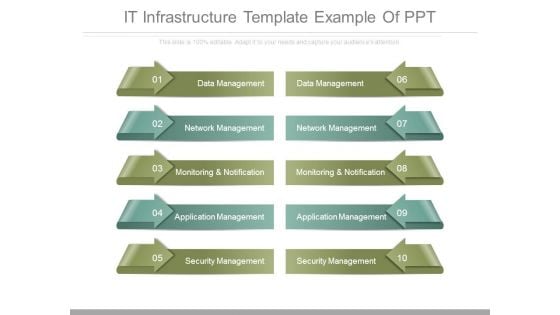
It Infrastructure Template Example Of Ppt
This is a it infrastructure template example of ppt. This is a ten stage process. The stages in this process are data management, network management, monitoring and notification, application management, security management.

Market Opportunity Forecasts Example Presentation Visual Aids
This is a market opportunity forecasts example presentation visual aids. This is a eight stage process. The stages in this process are security audit, system integration, consoling training, solution architecture, analysis, account based intelligence, tools, models and forecasting.
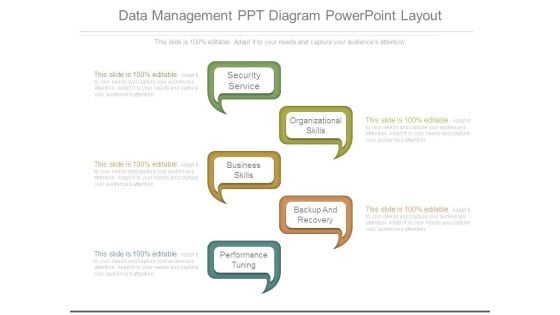
Data Management Ppt Diagram Powerpoint Layout
This is a data management ppt diagram powerpoint layout. This is a five stage process. The stages in this process are security service, organizational skills, business skills, backup and recovery, performance tuning.

Methods Of Software Risk Assessment Ppt Powerpoint Guide
This is a methods of software risk assessment ppt powerpoint guide. This is a seven stage process. The stages in this process are risk management, risk assessment, risk identification, risk periodization, security requirements, external review, penetration testing.
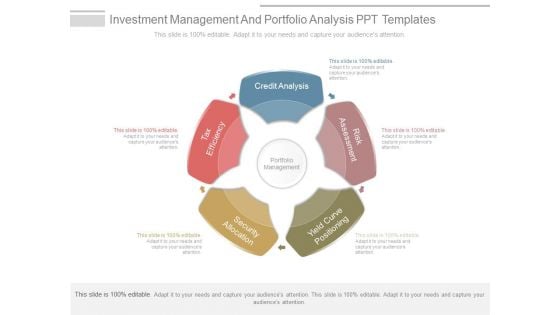
Investment Management And Portfolio Analysis Ppt Templates
This is a investment management and portfolio analysis ppt templates. This is a five stage process. The stages in this process are credit analysis, risk assessment, yield curve positioning, security allocation, tax efficiency, portfolio management.

Project Context For Firewall Migration Proposal
This slide highlights the project context for the firewall migration proposal. It includes the requirements of the client company and the key deliverables by the service provider organization, such as advanced security features, security ecosystem components, etc.Unleash your creativity with our Project Context For Firewall Migration Proposal single-slide PPT template. Whether you are a seasoned presenter or a newbie, our editable and visually-stunning template will make your presentations shine. This template is versatile and easy to use. Make your presentations unforgettable with our premium template and leave a lasting impression on your audience. This slide highlights the project context for the firewall migration proposal. It includes the requirements of the client company and the key deliverables by the service provider organization, such as advanced security features, security ecosystem components, etc.

Monitor And Assess Vendor Risk Management Ppt PowerPoint Presentation File Infographics PDF
The following slide showcases vendor risk analysis checklist to ensure customer data safety. It includes key elements such as information security and privacy, physical assets, web application, infrastructure security etc. The following slide showcases vendor risk analysis checklist to ensure customer data safety. It includes key elements such as information security and privacy, physical assets, web application, infrastructure security etc. Boost your pitch with our creative Monitor And Assess Vendor Risk Management Ppt PowerPoint Presentation File Infographics PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Web Consulting Business Cybersecurity Issues Overview And Key Statistics
Mentioned slide provides introduction about cyber security issues. It includes key elements such as description, types of security issue, key facts, and negative impact on business. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Web Consulting Business Cybersecurity Issues Overview And Key Statistics to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. Mentioned slide provides introduction about cyber security issues. It includes key elements such as description, types of security issue, key facts, and negative impact on business.

Comprehensive Guide For Website Cybersecurity Issues Overview And Key Statistics
Mentioned slide provides introduction about cyber security issues. It includes key elements such as description, types of security issue, key facts, and negative impact on business. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Comprehensive Guide For Website Cybersecurity Issues Overview And Key Statistics to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. Mentioned slide provides introduction about cyber security issues. It includes key elements such as description, types of security issue, key facts, and negative impact on business.
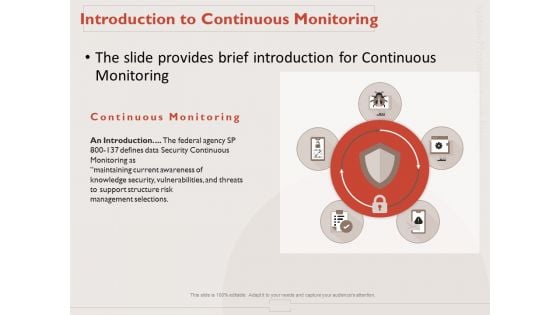
Monitoring Computer Software Application Introduction To Continuous Monitoring Ppt PowerPoint Presentation Model Files PDF
Presenting this set of slides with name monitoring computer software application introduction to continuous monitoring ppt powerpoint presentation model files pdf. This is a five stage process. The stages in this process are introduction, data security continuous monitoring, maintaining current awareness, knowledge security, vulnerabilities, and threats, support structure, risk management selections. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Our Services Ppt PowerPoint Presentation Model Grid
This is a our services ppt powerpoint presentation model grid. This is a four stage process. The stages in this process are digital advertising, digital care package, marketing and analytics , security maintenance.

Audit Committee Corporate Priorities Ppt Examples
This is a audit committee corporate priorities ppt examples. This is a nine stage process. The stages in this process are audit committee, corporate priorities, programmed statements, business plan, senior management committee, security committee, senior executive committee, people management committee.
Portfolio Administration Plan Layout Powerpoint Slide Background Designs
This is a portfolio administration plan layout powerpoint slide background designs. This is a six stage process. The stages in this process are customer value, competitor analysis, strategy action, market analysis, asset management, security selection.
E Commerce Circle Examples Ppt Powerpoint Slides
This is a e commerce circle examples ppt powerpoint slides. This is a seven stage process. The stages in this process are business e commerce, security services, web hosting, shopping cart, web design, merchant processing, online marketing, data storage.
Seo Based Ecommerce Model For Marketing Ppt Presentation Design
This is a seo based ecommerce model for marketing ppt presentation design. This is a seven stage process. The stages in this process are security service, web hosting, shopping cart, web design, merchant processing, online marketing, data storage.
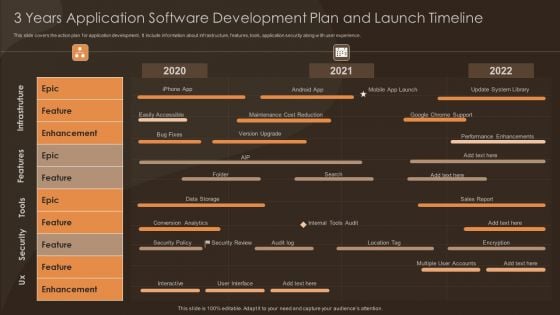
3 Years Application Software Development Plan And Launch Timeline Themes PDF
This slide covers the action plan for application development. It include information about infrastructure, features, tools, application security along with user experience. Showcasing this set of slides titled 3 Years Application Software Development Plan And Launch Timeline Themes PDF. The topics addressed in these templates are Security, Enhancement, Internal Tools Audit. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Database Platform Powerpoint Slides Themes
This is a database platform powerpoint slides themes. This is a four stage process. The stages in this process are database platform, data warehouse platform, security and identity, development.
Enterprise Architecture Strategy Ppt Powerpoint Slides Designs
This is a enterprise architecture strategy ppt powerpoint slides designs. This is a six stage process. The stages in this process are business view, business layer, data layer, security layer, business architecture, process layer.
Sample Information Management System Powerpoint Guide
This is a sample information management system powerpoint guide. This is a five stage process. The stages in this process are collection and processing, integration , information security , analysis , interface and display.
Business Financial Growth Ppt Powerpoint Graphics
This is a business financial growth ppt powerpoint graphics. This is a five stage process. The stages in this process are financial growth, investment, reporting, growth, security and analysis.
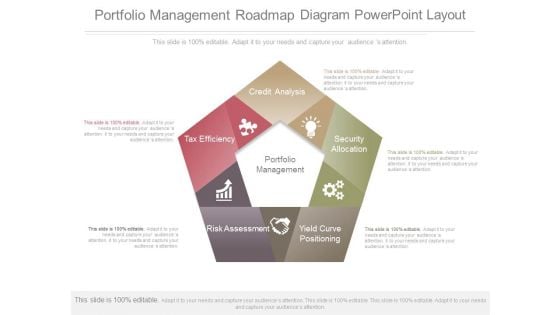
Portfolio Management Roadmap Diagram Powerpoint Layout
This is a portfolio management roadmap diagram powerpoint layout. This is a five stage process. The stages in this process are portfolio management, tax efficiency, credit analysis, security allocation, yield curve positioning, risk assessment.
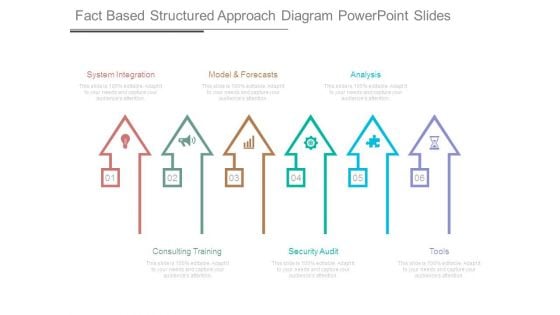
Fact Based Structured Approach Diagram Powerpoint Slides
This is a fact based structured approach diagram powerpoint slides. This is a six stage process. The stages in this process are system integration, model and forecasts, analysis, consulting training, security audit, tools.
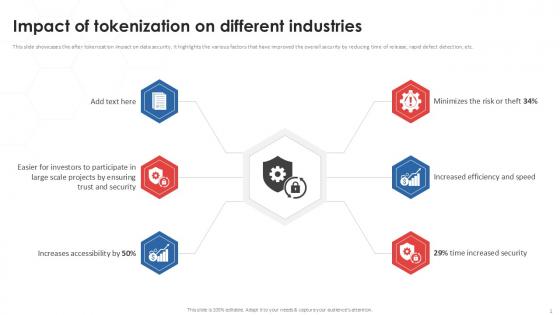
Impact Of Tokenization On Different Industries PPT Template
This slide showcases the after tokenization impact on data security. It highlights the various factors that have improved the overall security by reducing time of release, rapid defect detection, etc. Find a pre-designed and impeccable Impact Of Tokenization On Different Industries PPT Template. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide showcases the after tokenization impact on data security. It highlights the various factors that have improved the overall security by reducing time of release, rapid defect detection, etc.
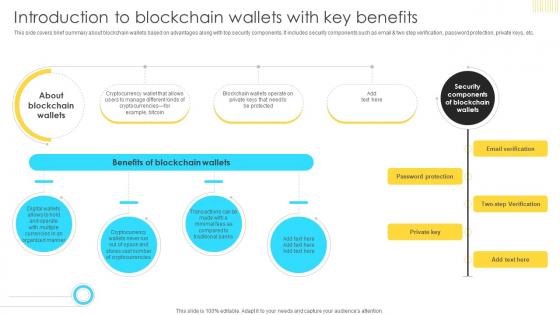
Mastering Blockchain Wallets Introduction To Blockchain Wallets With Key BCT SS V
This side covers brief summary about blockchain wallets based on advantages along with top security components. It includes security components such as email and two step verification, password protection, private keys, etc Do you know about Slidesgeeks Mastering Blockchain Wallets Introduction To Blockchain Wallets With Key BCT SS V These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This side covers brief summary about blockchain wallets based on advantages along with top security components. It includes security components such as email and two step verification, password protection, private keys, etc

Empowering The Future Challenges And Solutions In Advanced Metering Infrastructure IoT SS V
This slide exhibits AMI system challenges and appropriate solutions to enhance grid reliability. It includes challenges such as communication network challenges, network-based security threats, security standards, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Empowering The Future Challenges And Solutions In Advanced Metering Infrastructure IoT SS V. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Empowering The Future Challenges And Solutions In Advanced Metering Infrastructure IoT SS V today and make your presentation stand out from the rest This slide exhibits AMI system challenges and appropriate solutions to enhance grid reliability. It includes challenges such as communication network challenges, network-based security threats, security standards, etc.
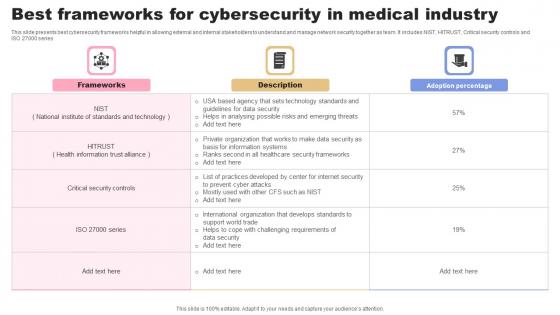
Best Frameworks For Cybersecurity In Medical Industry Guidelines Pdf
This slide presents best cybersecurity frameworks helpful in allowing external and internal stakeholders to understand and manage network security together as team. It includes NIST, HITRUST, Critical security controls and ISO 27000 series Showcasing this set of slides titled Best Frameworks For Cybersecurity In Medical Industry Guidelines Pdf. The topics addressed in these templates are Frameworks, Description, Adoption Percentage. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide presents best cybersecurity frameworks helpful in allowing external and internal stakeholders to understand and manage network security together as team. It includes NIST, HITRUST, Critical security controls and ISO 27000 series
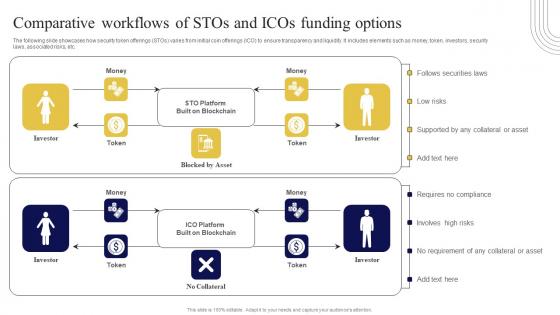
Comparative Workflows Of Stos And Icos Exploring Investment Opportunities Professional Pdf
The following slide showcases how security token offerings STOs varies from initial coin offerings ICO to ensure transparency and liquidity. It includes elements such as money, token, investors, security laws, associated risks, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Comparative Workflows Of Stos And Icos Exploring Investment Opportunities Professional Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Comparative Workflows Of Stos And Icos Exploring Investment Opportunities Professional Pdf today and make your presentation stand out from the rest The following slide showcases how security token offerings STOs varies from initial coin offerings ICO to ensure transparency and liquidity. It includes elements such as money, token, investors, security laws, associated risks, etc.
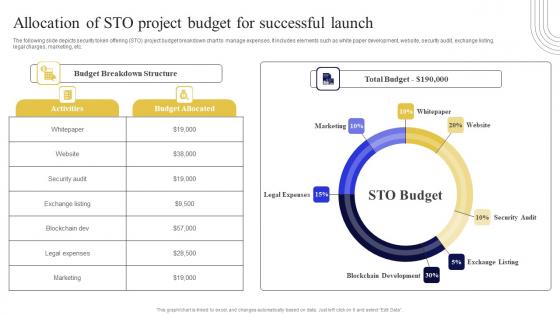
Allocation Of STO Project Budget For Exploring Investment Opportunities Demonstration Pdf
The following slide depicts security token offering STO project budget breakdown chart to manage expenses. It includes elements such as white paper development, website, security audit, exchange listing, legal charges, marketing, etc. Create an editable Allocation Of STO Project Budget For Exploring Investment Opportunities Demonstration Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Allocation Of STO Project Budget For Exploring Investment Opportunities Demonstration Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. The following slide depicts security token offering STO project budget breakdown chart to manage expenses. It includes elements such as white paper development, website, security audit, exchange listing, legal charges, marketing, etc.

Managing Technical And Non Cybersecurity Issues Overview And Key Statistics
Mentioned slide provides introduction about cyber security issues. It includes key elements such as description, types of security issue, key facts, and negative impact on business. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Managing Technical And Non Cybersecurity Issues Overview And Key Statistics was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Managing Technical And Non Cybersecurity Issues Overview And Key Statistics. Mentioned slide provides introduction about cyber security issues. It includes key elements such as description, types of security issue, key facts, and negative impact on business.


 Continue with Email
Continue with Email

 Home
Home


































