Technology Security
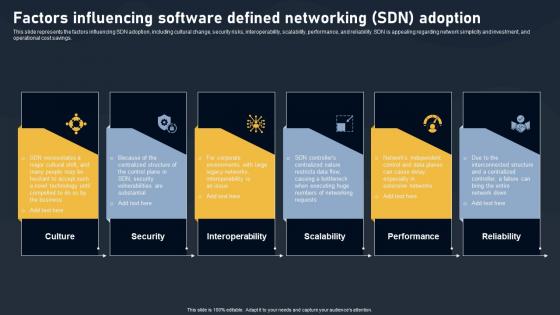
Factors Influencing Software Defined Networking Adoption SDN Building Blocks Template Pdf
This slide represents the factors influencing SDN adoption, including cultural change, security risks, interoperability, scalability, performance, and reliability. SDN is appealing regarding network simplicity and investment, and operational cost savings.Slidegeeks has constructed Factors Influencing Software Defined Networking Adoption SDN Building Blocks Template Pdf after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide represents the factors influencing SDN adoption, including cultural change, security risks, interoperability, scalability, performance, and reliability. SDN is appealing regarding network simplicity and investment, and operational cost savings.
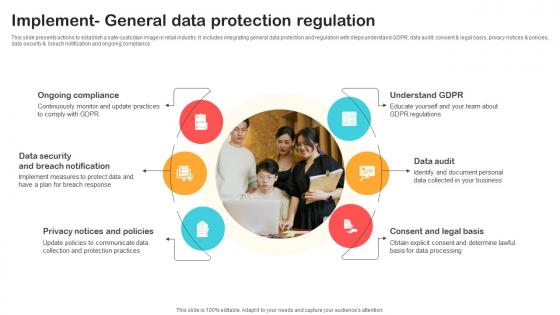
Implement General Data Protection Regulation Optimizing Retail Operations With Digital DT SS V
This slide presents actions to establish a safe-custodian image in retail industry. It includes integrating general data protection and regulation with steps understand GDPR, data audit, consent and legal basis, privacy notices and policies, data security and breach notification and ongoing compliance. Find a pre-designed and impeccable Implement General Data Protection Regulation Optimizing Retail Operations With Digital DT SS V. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide presents actions to establish a safe-custodian image in retail industry. It includes integrating general data protection and regulation with steps understand GDPR, data audit, consent and legal basis, privacy notices and policies, data security and breach notification and ongoing compliance.
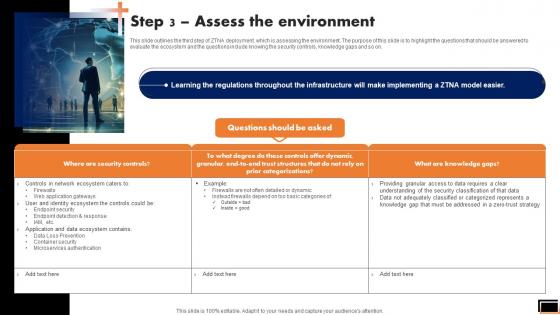
Step 3 Assess The Environment Software Defined Perimeter SDP
This slide outlines the third step of ZTNA deployment, which is assessing the environment. The purpose of this slide is to highlight the questions that should be answered to evaluate the ecosystem and the questions include knowing the security controls, knowledge gaps and so on. There are so many reasons you need a Step 3 Assess The Environment Software Defined Perimeter SDP. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide outlines the third step of ZTNA deployment, which is assessing the environment. The purpose of this slide is to highlight the questions that should be answered to evaluate the ecosystem and the questions include knowing the security controls, knowledge gaps and so on.

Value Proposition Usp Cloud Platform Provider Investor Funding Elevator Microsoft Pdf
This slide showcases unique selling propositions of solution offered by Machine Learning Software differentiates product from others. It includes its USPs such as collaborative workplace, increases performance and security features. Welcome to our selection of the Value Proposition Usp Cloud Platform Provider Investor Funding Elevator Microsoft Pdf. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today This slide showcases unique selling propositions of solution offered by Machine Learning Software differentiates product from others. It includes its USPs such as collaborative workplace, increases performance and security features.
Business Software Glitch Tracking Status Download PDF
This slide represents reason of defects with their weightage in software testing. It include factors such as design issue, security flaws, document issue, code related issue etc. Showcasing this set of slides titled Business Software Glitch Tracking Status Download PDF. The topics addressed in these templates are Requirements Misinterpretation, Architecture Design Issues, Code Related Issue . All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Statistical Analysis Challenges Data Analytics For Informed Decision Ppt Example
The purpose of this slide is to discuss the limitations of statistical analysis and their possible solutions. The challenges of statistical analytics are data integration and quality, skill gap, scalability, data security and budget constraints. Slidegeeks has constructed Statistical Analysis Challenges Data Analytics For Informed Decision Ppt Example after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. The purpose of this slide is to discuss the limitations of statistical analysis and their possible solutions. The challenges of statistical analytics are data integration and quality, skill gap, scalability, data security and budget constraints.

Implement General Data Protection Regulation DT SS V
This slide presents actions to establish a safe-custodian image in retail industry. It includes integrating general data protection and regulation with steps understand GDPR, data audit, consent and legal basis, privacy notices and policies, data security and breach notification and ongoing compliance. Find a pre-designed and impeccable Implement General Data Protection Regulation DT SS V. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide presents actions to establish a safe-custodian image in retail industry. It includes integrating general data protection and regulation with steps understand GDPR, data audit, consent and legal basis, privacy notices and policies, data security and breach notification and ongoing compliance.
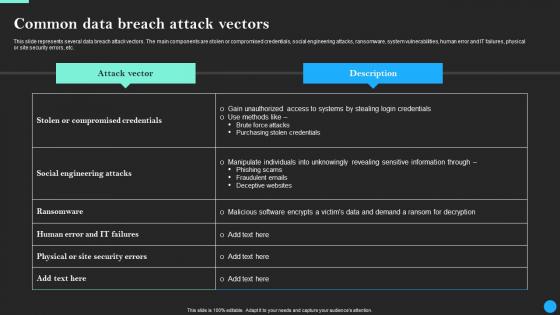
Common Data Breach Attack Vectors Data Breach Prevention Clipart Pdf
This slide represents several data breach attack vectors. The main components are stolen or compromised credentials, social engineering attacks, ransomware, system vulnerabilities, human error and IT failures, physical or site security errors, etc. Present like a pro with Common Data Breach Attack Vectors Data Breach Prevention Clipart Pdf Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide represents several data breach attack vectors. The main components are stolen or compromised credentials, social engineering attacks, ransomware, system vulnerabilities, human error and IT failures, physical or site security errors, etc.

Common Data Breach Attack Vectors Data Fortification Strengthening Defenses
This slide represents several data breach attack vectors. The main components are stolen or compromised credentials, social engineering attacks, ransomware, system vulnerabilities, human error and IT failures, physical or site security errors, etc. Present like a pro with Common Data Breach Attack Vectors Data Fortification Strengthening Defenses. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide represents several data breach attack vectors. The main components are stolen or compromised credentials, social engineering attacks, ransomware, system vulnerabilities, human error and IT failures, physical or site security errors, etc.
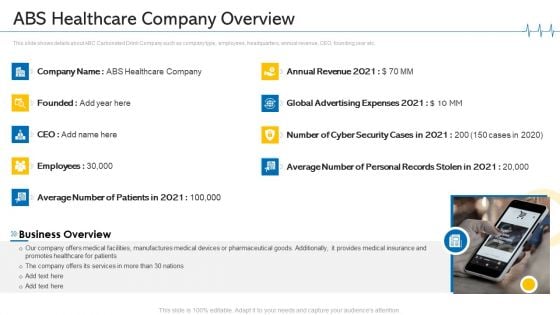
Minimize Cloud Risks Medical Care Business Case Competition ABS Healthcare Company Overview Introduction PDF
This slide shows details about ABC Carbonated Drink Company such as company type, employees, headquarters, annual revenue, CEO, founding year etc. This is a minimize cloud risks medical care business case competition ABS healthcare company overview introduction pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like business overview, annual revenue, cyber security cases, manufactures, global advertising expenses. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
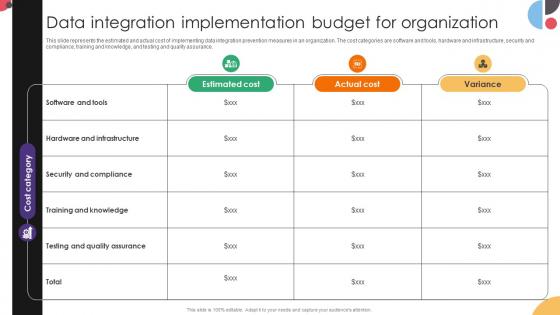
Data Integration Implementation Budget For Organization Data Integration Strategies For Business
This slide represents the estimated and actual cost of implementing data integration prevention measures in an organization. The cost categories are software and tools, hardware and infrastructure, security and compliance, training and knowledge, and testing and quality assurance. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Data Integration Implementation Budget For Organization Data Integration Strategies For Business and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide represents the estimated and actual cost of implementing data integration prevention measures in an organization. The cost categories are software and tools, hardware and infrastructure, security and compliance, training and knowledge, and testing and quality assurance.
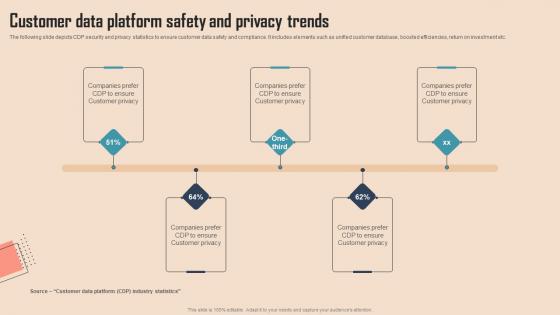
Customer Data Platform Safety And Comprehensive CDP Guide For Promoters Brochure Pdf
The following slide depicts CDP security and privacy statistics to ensure customer data safety and compliance. It includes elements such as unified customer database, boosted efficiencies, return on investment etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Customer Data Platform Safety And Comprehensive CDP Guide For Promoters Brochure Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. The following slide depicts CDP security and privacy statistics to ensure customer data safety and compliance. It includes elements such as unified customer database, boosted efficiencies, return on investment etc.

CASB 2 0 IT Reverse Proxy CASB Deployment Model
This slide outlines the overview of the reverse proxy cloud access security model broker. The purpose of this slide is to showcase overview of working and various types of reverse proxy CASB. The main types include regular reverse proxies and load balancers. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit CASB 2 0 IT Reverse Proxy CASB Deployment Model and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide outlines the overview of the reverse proxy cloud access security model broker. The purpose of this slide is to showcase overview of working and various types of reverse proxy CASB. The main types include regular reverse proxies and load balancers.
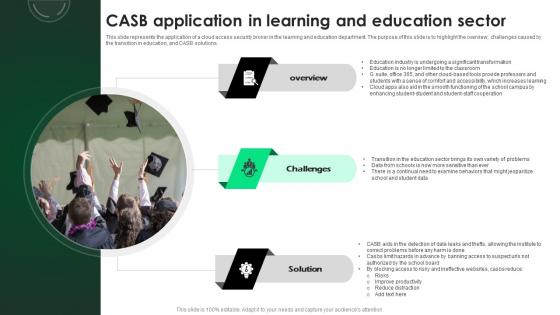
CASB 2 0 IT CASB Application In Learning And Education Sector
This slide represents the application of a cloud access security broker in the learning and education department. The purpose of this slide is to highlight the overview, challenges caused by the transition in education, and CASB solutions. Present like a pro with CASB 2 0 IT CASB Application In Learning And Education Sector. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide represents the application of a cloud access security broker in the learning and education department. The purpose of this slide is to highlight the overview, challenges caused by the transition in education, and CASB solutions.
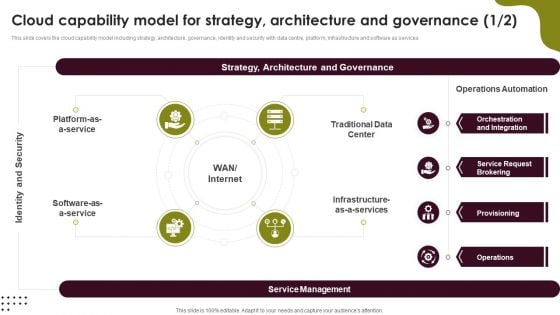
Cloud Computing Scalability Cloud Capability Model For Strategy Architecture Template PDF
This slide covers the cloud capability model including strategy, architecture, governance, identity and security with data centre, platform, infrastructure and software as services. There are so many reasons you need a Cloud Computing Scalability Cloud Capability Model For Strategy Architecture Template PDF. The first reason is you cant spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
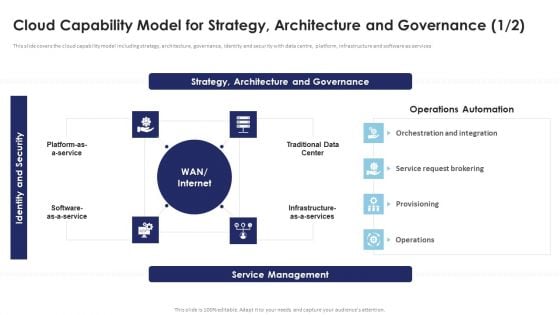
Multi Cloud Infrastructure Management Cloud Capability Model For Strategy Architecture Pictures PDF
This slide covers the cloud capability model including strategy, architecture, governance, identity and security with data centre, platform, infrastructure and software as services. There are so many reasons you need a Multi Cloud Infrastructure Management Cloud Capability Model For Strategy Architecture Pictures PDF. The first reason is you cant spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
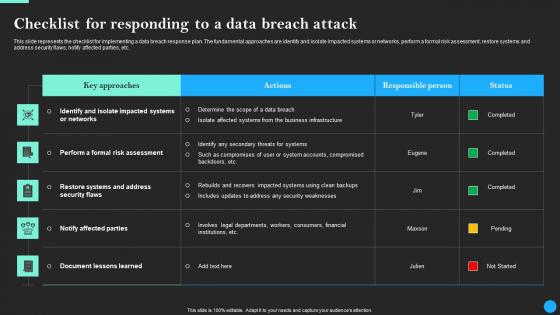
Checklist For Responding To A Data Breach Attack Data Breach Prevention Microsoft Pdf
This slide represents the checklist for implementing a data breach response plan. The fundamental approaches are identify and isolate impacted systems or networks, perform a formal risk assessment, restore systems and address security flaws, notify affected parties, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Checklist For Responding To A Data Breach Attack Data Breach Prevention Microsoft Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide represents the checklist for implementing a data breach response plan. The fundamental approaches are identify and isolate impacted systems or networks, perform a formal risk assessment, restore systems and address security flaws, notify affected parties, etc.

Checklist For Responding To A Data Breach Attack Data Fortification Strengthening Defenses
This slide represents the checklist for implementing a data breach response plan. The fundamental approaches are identify and isolate impacted systems or networks, perform a formal risk assessment, restore systems and address security flaws, notify affected parties, etc.From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Checklist For Responding To A Data Breach Attack Data Fortification Strengthening Defenses will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide represents the checklist for implementing a data breach response plan. The fundamental approaches are identify and isolate impacted systems or networks, perform a formal risk assessment, restore systems and address security flaws, notify affected parties, etc.
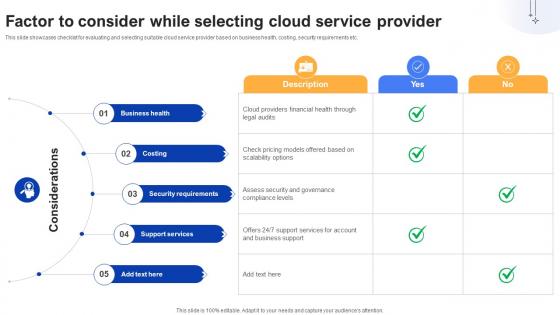
Effective Data Migration Factor To Consider While Selecting Cloud Service
This slide showcases checklist for evaluating and selecting suitable cloud service provider based on business health, costing, security requirements etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Effective Data Migration Factor To Consider While Selecting Cloud Service to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide showcases checklist for evaluating and selecting suitable cloud service provider based on business health, costing, security requirements etc.

Roadmap For Cloud Data Client Side Encryption PPT Presentation
This slide represents the roadmap to implement cryptographic cloud security in an organization. The main components included are determine sensitive data and required encryption technique, choose a cloud service provider, implement solution in cloud, etc. The Roadmap For Cloud Data Client Side Encryption PPT Presentation is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide represents the roadmap to implement cryptographic cloud security in an organization. The main components included are determine sensitive data and required encryption technique, choose a cloud service provider, implement solution in cloud, etc.
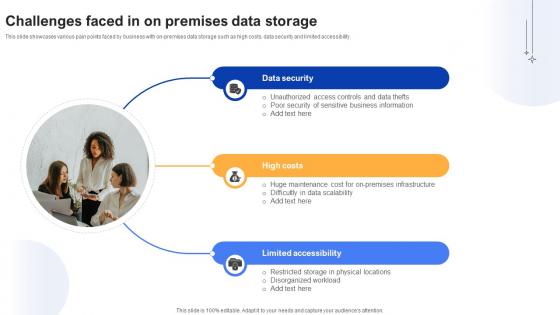
Effective Data Migration Challenges Faced In On Premises Data Storage
This slide showcases various pain points faced by business with on-premises data storage such as high costs, data security and limited accessibility. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Effective Data Migration Challenges Faced In On Premises Data Storage a try. Our experts have put a lot of knowledge and effort into creating this impeccable Effective Data Migration Challenges Faced In On Premises Data Storage. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide showcases various pain points faced by business with on-premises data storage such as high costs, data security and limited accessibility.
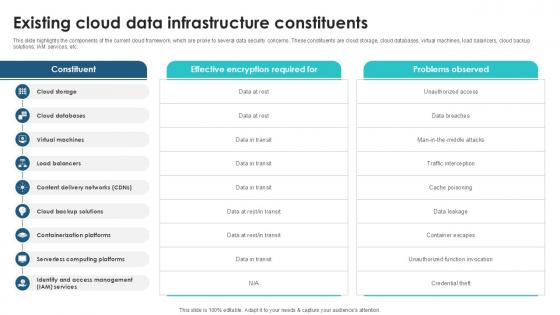
Existing Cloud Data Infrastructure Client Side Encryption PPT Sample
This slide highlights the components of the current cloud framework, which are prone to several data security concerns. These constituents are cloud storage, cloud databases, virtual machines, load balancers, cloud backup solutions, IAM services, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Existing Cloud Data Infrastructure Client Side Encryption PPT Sample. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide highlights the components of the current cloud framework, which are prone to several data security concerns. These constituents are cloud storage, cloud databases, virtual machines, load balancers, cloud backup solutions, IAM services, etc.

Types Of Information Leaked In Data Breach Data Fortification Strengthening Defenses
This slide outlines the different forms of information loss in a data security breach. The major types of data leaked are financial data, medical or personal health information, Personally Identifiable Information, vulnerable and sensitive data, etc. Present like a pro with Types Of Information Leaked In Data Breach Data Fortification Strengthening Defenses. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide outlines the different forms of information loss in a data security breach. The major types of data leaked are financial data, medical or personal health information, Personally Identifiable Information, vulnerable and sensitive data, etc.

Challenges Faced In On Premises Data Storage Data Migration From On Premises
This slide showcases various pain points faced by business with on-premises data storage such as high costs, data security and limited accessibility. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Challenges Faced In On Premises Data Storage Data Migration From On Premises a try. Our experts have put a lot of knowledge and effort into creating this impeccable Challenges Faced In On Premises Data Storage Data Migration From On Premises. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide showcases various pain points faced by business with on-premises data storage such as high costs, data security and limited accessibility.
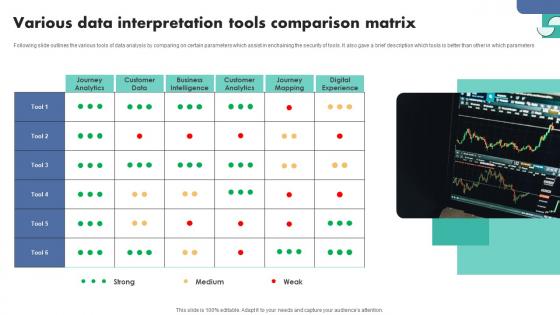
Various Data Interpretation Tools Comparison Matrix Ideas Pdf
Following slide outlines the various tools of data analysis by comparing on certain parameters which assist in enchaining the security of tools. It also gave a brief description which tools is better than other in which parameters.Showcasing this set of slides titled Various Data Interpretation Tools Comparison Matrix Ideas Pdf The topics addressed in these templates are Customer Data, Business Intelligence, Customer Analytics All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Following slide outlines the various tools of data analysis by comparing on certain parameters which assist in enchaining the security of tools. It also gave a brief description which tools is better than other in which parameters.
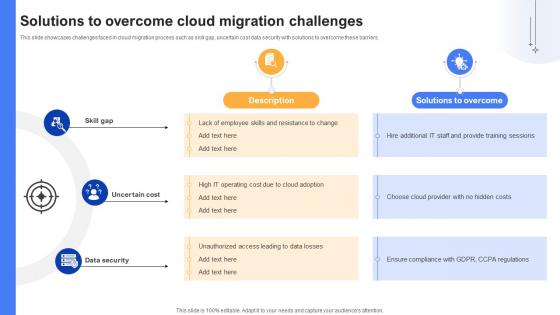
Effective Data Migration Solutions To Overcome Cloud Migration Challenges
This slide showcases challenges faced in cloud migration process such as skill gap, uncertain cost data security with solutions to overcome these barriers. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Effective Data Migration Solutions To Overcome Cloud Migration Challenges for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide showcases challenges faced in cloud migration process such as skill gap, uncertain cost data security with solutions to overcome these barriers.

Key Facts Data Management Company Investor Funding Pitch Deck
The following slide showcases various statistics outlining company overview that assists investors to gain understanding of business performance. It consists of rightsizing savings, reverted deploys, effective cost per resource, production incidents by application or team and number of security lapses. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Key Facts Data Management Company Investor Funding Pitch Deck and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates The following slide showcases various statistics outlining company overview that assists investors to gain understanding of business performance. It consists of rightsizing savings, reverted deploys, effective cost per resource, production incidents by application or team and number of security lapses.
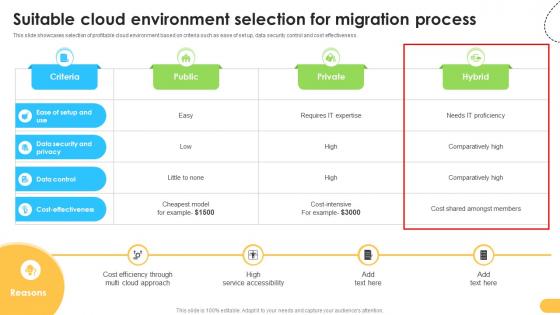
Suitable Cloud Environment Selection For Data Migration From On Premises
This slide showcases selection of profitable cloud environment based on criteria such as ease of set up, data security control and cost effectiveness. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Suitable Cloud Environment Selection For Data Migration From On Premises to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Suitable Cloud Environment Selection For Data Migration From On Premises. This slide showcases selection of profitable cloud environment based on criteria such as ease of set up, data security control and cost effectiveness.
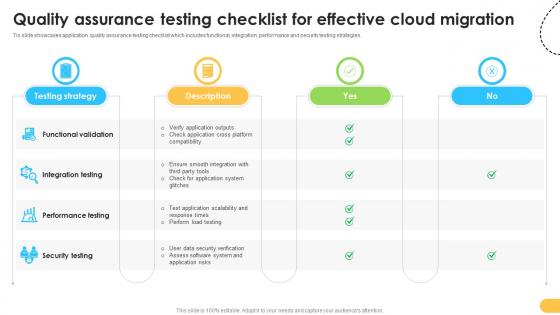
Quality Assurance Testing Checklist For Effective Data Migration From On Premises
Tis slide showcases application quality assurance testing checklist which includes functional, integration, performance and security testing strategies. The Quality Assurance Testing Checklist For Effective Data Migration From On Premises is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. Tis slide showcases application quality assurance testing checklist which includes functional, integration, performance and security testing strategies.
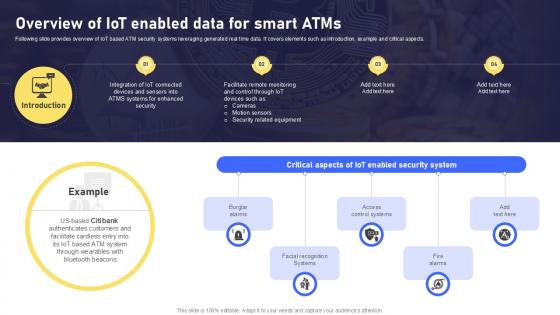
Overview Of IoT Enabled Data Banking Future With IoT Ppt Slide IoT SS V
Following slide provides overview of IoT based ATM security systems leveraging generated real time data. It covers elements such as introduction, example and critical aspects. Are you searching for a Overview Of IoT Enabled Data Banking Future With IoT Ppt Slide IoT SS V that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Overview Of IoT Enabled Data Banking Future With IoT Ppt Slide IoT SS V from Slidegeeks today. Following slide provides overview of IoT based ATM security systems leveraging generated real time data. It covers elements such as introduction, example and critical aspects.
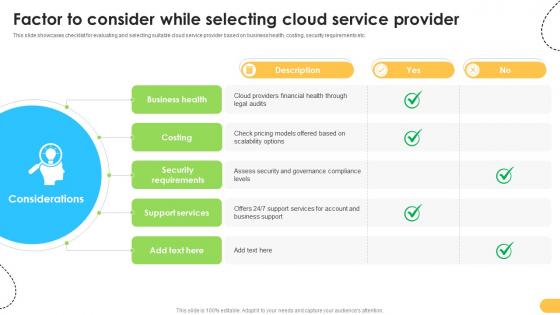
Factor To Consider While Selecting Cloud Data Migration From On Premises
This slide showcases checklist for evaluating and selecting suitable cloud service provider based on business health, costing, security requirements etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Factor To Consider While Selecting Cloud Data Migration From On Premises to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide showcases checklist for evaluating and selecting suitable cloud service provider based on business health, costing, security requirements etc.
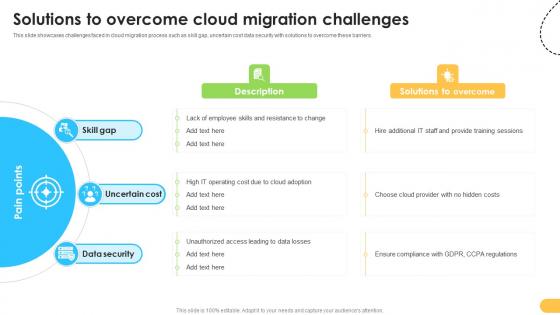
Solutions To Overcome Cloud Migration Challenges Data Migration From On Premises
This slide showcases challenges faced in cloud migration process such as skill gap, uncertain cost data security with solutions to overcome these barriers. Slidegeeks has constructed Solutions To Overcome Cloud Migration Challenges Data Migration From On Premises after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide showcases challenges faced in cloud migration process such as skill gap, uncertain cost data security with solutions to overcome these barriers.
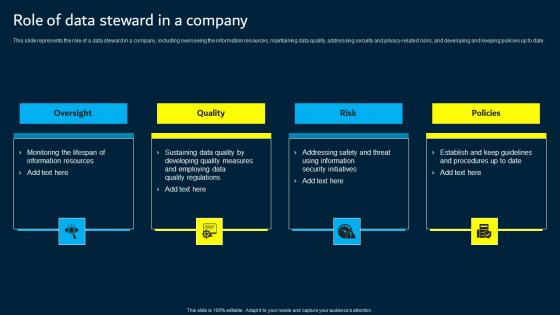
Role Of Data Steward In A Company Data Custodianship Brochure Pdf
This slide represents the role of a data steward in a company, including overseeing the information resources, maintaining data quality, addressing security and privacy related risks, and developing and keeping policies up to date. Retrieve professionally designed Role Of Data Steward In A Company Data Custodianship Brochure Pdf to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide represents the role of a data steward in a company, including overseeing the information resources, maintaining data quality, addressing security and privacy related risks, and developing and keeping policies up to date.
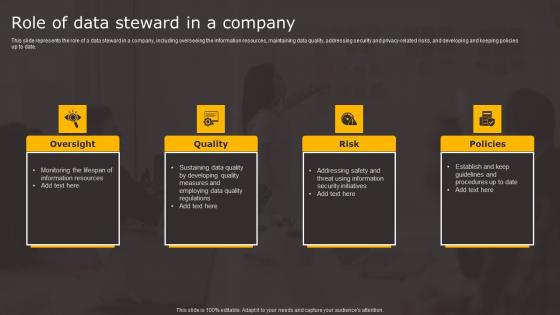
Data Stewardship In Business Processes Role Of Data Steward In A Company Background Pdf
This slide represents the role of a data steward in a company, including overseeing the information resources, maintaining data quality, addressing security and privacy related risks, and developing and keeping policies up to date. Make sure to capture your audiences attention in your business displays with our gratis customizable Data Stewardship In Business Processes Role Of Data Steward In A Company Background Pdf. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide represents the role of a data steward in a company, including overseeing the information resources, maintaining data quality, addressing security and privacy related risks, and developing and keeping policies up to date.
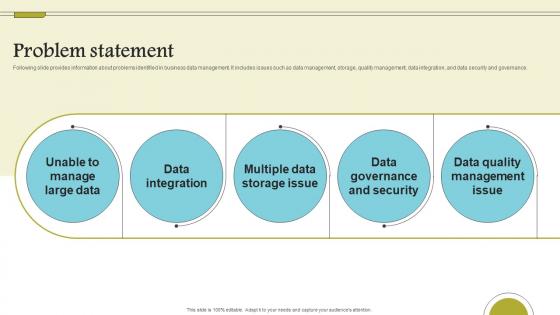
Problem Statement Cloud Data Computing Company Fund Raising Background PDF
Following slide provides information about problems identified in business data management. It includes issues such as data management, storage, quality management, data integration, and data security and governance. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Problem Statement Cloud Data Computing Company Fund Raising Background PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Problem Statement Cloud Data Computing Company Fund Raising Background PDF Following slide provides information about problems identified in business data management. It includes issues such as data management, storage, quality management, data integration, and data security and governance.
Data Breach Prevention Status Tracking Dashboard Data Fortification Strengthening Defenses
This slide represents the critical cyber security performance indicators for the organization. The key components include application health, encryption status, license consumption, windows defender, etc.Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Data Breach Prevention Status Tracking Dashboard Data Fortification Strengthening Defenses and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide represents the critical cyber security performance indicators for the organization. The key components include application health, encryption status, license consumption, windows defender, etc.
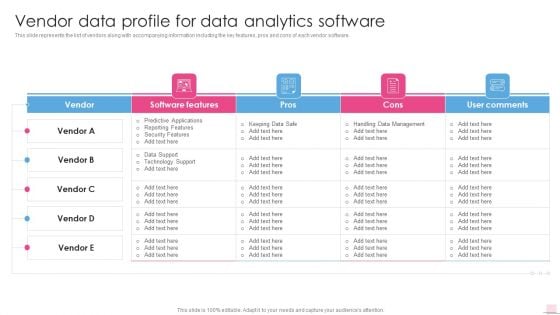
Vendor Data Profile For Data Analytics Software Business Analysis Modification Toolkit Topics PDF
This is a Vendor Data Profile For Data Analytics Software Business Analysis Modification Toolkit Topics PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Predictive Applications, Reporting Features, Security Features. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

CASB 2 0 IT 30 60 90 Days Plan To Deploy CASB Model
This slide represents the 30-0-90 days plan to implement the cloud access security broker model in an organization. The purpose of this slide is to showcase the various steps to be taken to deploy CASB at the interval every 30 days. Boost your pitch with our creative CASB 2 0 IT 30 60 90 Days Plan To Deploy CASB Model. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide represents the 30-0-90 days plan to implement the cloud access security broker model in an organization. The purpose of this slide is to showcase the various steps to be taken to deploy CASB at the interval every 30 days.
Data Breach Prevention Status Tracking Dashboard Data Breach Prevention Information Pdf
This slide represents the critical cyber security performance indicators for the organization. The key components include application health, encryption status, license consumption, windows defender, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Data Breach Prevention Status Tracking Dashboard Data Breach Prevention Information Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Data Breach Prevention Status Tracking Dashboard Data Breach Prevention Information Pdf that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide represents the critical cyber security performance indicators for the organization. The key components include application health, encryption status, license consumption, windows defender, etc.
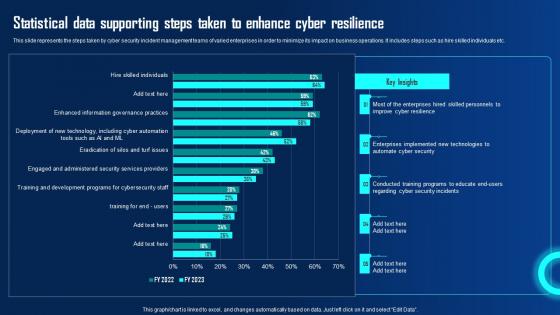
Statistical Data Supporting Steps Taken To Enhance Cyber Ppt Powerpoint Presentation File Outline Pdf
This slide represents the steps taken by cyber security incident management teams of varied enterprises in order to minimize its impact on business operations. It includes steps such as hire skilled individuals etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Statistical Data Supporting Steps Taken To Enhance Cyber Ppt Powerpoint Presentation File Outline Pdf from Slidegeeks and deliver a wonderful presentation. This slide represents the steps taken by cyber security incident management teams of varied enterprises in order to minimize its impact on business operations. It includes steps such as hire skilled individuals etc.
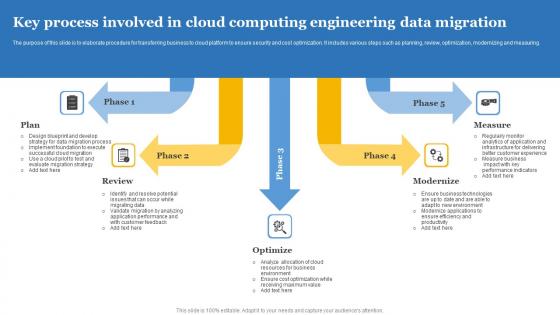
Key Process Involved In Cloud Computing Engineering Data Migration Mockup Pdf
The purpose of this slide is to elaborate procedure for transferring business to cloud platform to ensure security and cost optimization. It includes various steps such as planning, review, optimization, modernizing and measuring. Pitch your topic with ease and precision using this Key Process Involved In Cloud Computing Engineering Data Migration Mockup Pdf This layout presents information on Plan, Review, Optimize, Modernize, Measure It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. The purpose of this slide is to elaborate procedure for transferring business to cloud platform to ensure security and cost optimization. It includes various steps such as planning, review, optimization, modernizing and measuring.
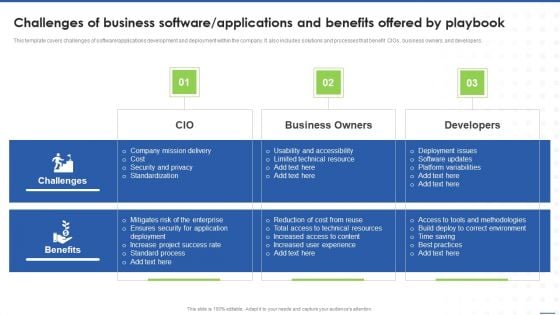
Challenges Of Business Software Applications And Benefits Offered By Playbook Mockup PDF
This template covers challenges of software applications development and deployment within the company. It also includes solutions and processes that benefit CIOs, business owners, and developers.Deliver an awe inspiring pitch with this creative Challenges Of Business Software Applications And Benefits Offered By Playbook Mockup PDF bundle. Topics like Company Mission, Security And Privacy, Limited Technical can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
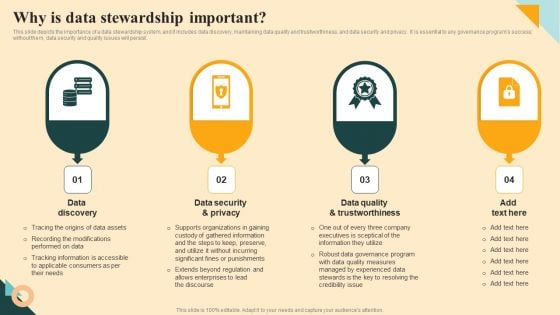
Why Is Data Stewardship Important Sample PDF
This slide depicts the importance of a data stewardship system, and it includes data discovery, maintaining data quality and trustworthiness, and data security and privacy. It is essential to any governance programs success without them, data security and quality issues will persist. Slidegeeks has constructed Why Is Data Stewardship Important Sample PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.
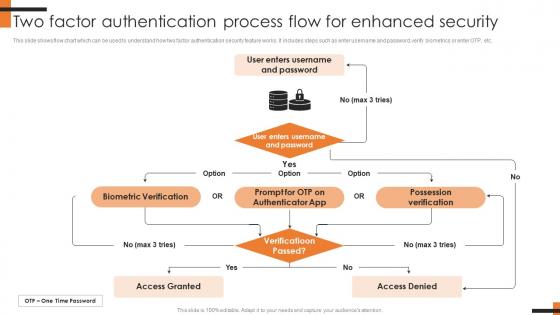
Two Factor Authentication Process Flow For Comprehensive Smartphone Banking Diagrams Pdf
This slide shows flow chart which can be used to understand how two factor authentication security feature works. It includes steps such as enter username and password, verify biometrics or enter OTP, etc. The Two Factor Authentication Process Flow For Comprehensive Smartphone Banking Diagrams Pdf is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide shows flow chart which can be used to understand how two factor authentication security feature works. It includes steps such as enter username and password, verify biometrics or enter OTP, etc.
RUP Methodology Management And Control Change Software Icons PDF
This slide represents how management and control change software is easy in the rational unified process methodology RUP also determines work and security domains.Deliver an awe inspiring pitch with this creative RUP Methodology Management And Control Change Software Icons PDF bundle. Topics like Unforeseen Effects On Applications, Management Is Critical, Domains Assuring can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
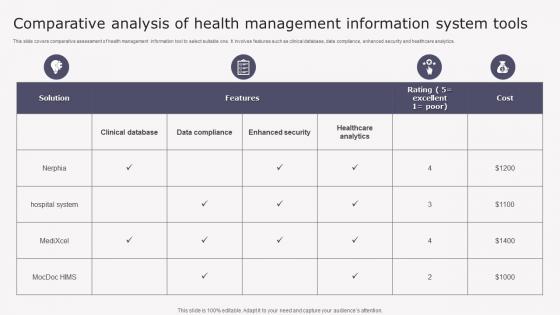
Transforming Medicare Services Using Health Comparative Analysis Health Background Pdf
This slide covers comparative assessment of health management information tool to select suitable one. It involves features such as clinical database, data compliance, enhanced security and healthcare analytics. Want to ace your presentation in front of a live audience Our Transforming Medicare Services Using Health Comparative Analysis Health Background Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use. This slide covers comparative assessment of health management information tool to select suitable one. It involves features such as clinical database, data compliance, enhanced security and healthcare analytics.
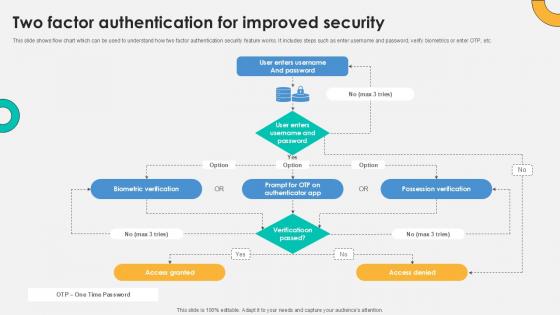
Two Factor Authentication For Everything About Bitcoin PPT Presentation Fin SS V
This slide shows flow chart which can be used to understand how two factor authentication security feature works. It includes steps such as enter username and password, verify biometrics or enter OTP, etc. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Two Factor Authentication For Everything About Bitcoin PPT Presentation Fin SS V and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide shows flow chart which can be used to understand how two factor authentication security feature works. It includes steps such as enter username and password, verify biometrics or enter OTP, etc.
Zero Trust Model Zero Trust Network Access Performance Tracking
This slide represents the performance tracking dashboard for zero trust network access. The purpose of this slide is to showcase the level of request modes, connected users, daily usage of the network, security rating, device risk and threat flow. The Zero Trust Model Zero Trust Network Access Performance Tracking is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide represents the performance tracking dashboard for zero trust network access. The purpose of this slide is to showcase the level of request modes, connected users, daily usage of the network, security rating, device risk and threat flow.
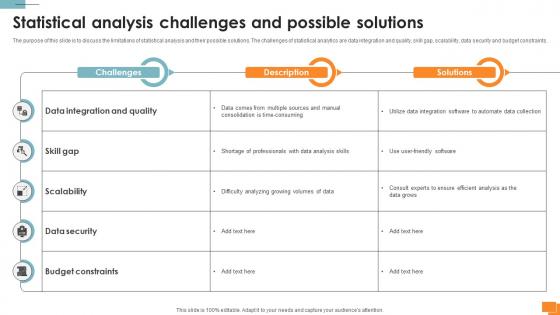
Statistical Tools For Evidence Statistical Analysis Challenges And Possible Solutions
The purpose of this slide is to discuss the limitations of statistical analysis and their possible solutions. The challenges of statistical analytics are data integration and quality, skill gap, scalability, data security and budget constraints. Take your projects to the next level with our ultimate collection of Statistical Tools For Evidence Statistical Analysis Challenges And Possible Solutions. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest The purpose of this slide is to discuss the limitations of statistical analysis and their possible solutions. The challenges of statistical analytics are data integration and quality, skill gap, scalability, data security and budget constraints.

Business Analysis Ability Mapping Model With Techniques Sample Pdf
This slide shows the techniques for mapping business analysis competencies. The purpose of this slides to enhance usability and scalability .It includes various methods of business task under cyber security , data analytics, scrum,etc. Showcasing this set of slides titled Business Analysis Ability Mapping Model With Techniques Sample Pdf The topics addressed in these templates are Business Competency, Proficiency Scale, Specialized Areas All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide shows the techniques for mapping business analysis competencies. The purpose of this slides to enhance usability and scalability .It includes various methods of business task under cyber security , data analytics, scrum,etc.
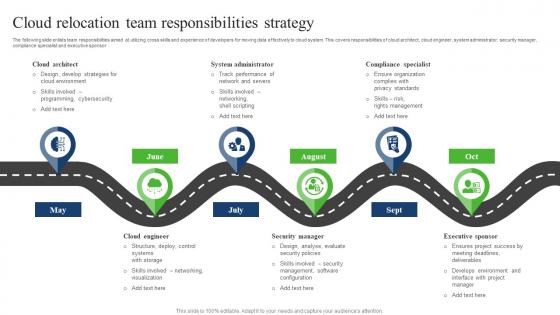
Cloud Relocation Team Responsibilities Strategy Slides Pdf
The following slide enlists team responsibilities aimed at utilizing cross skills and experience of developers for moving data effectively to cloud system. This covers responsibilities of cloud architect, cloud engineer, system administrator, security manager, compliance specialist and executive sponsor. Showcasing this set of slides titled Cloud Relocation Team Responsibilities Strategy Slides Pdf. The topics addressed in these templates are Cloud Architect, Cloud Relocation, Team Responsibilities Strategy. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. The following slide enlists team responsibilities aimed at utilizing cross skills and experience of developers for moving data effectively to cloud system. This covers responsibilities of cloud architect, cloud engineer, system administrator, security manager, compliance specialist and executive sponsor.

Optimization Of IoT Remote Monitoring Edge Ai Used To Reduce Cost And Bandwidth IoT SS V
This slide provides an overview of the edge AI used to enhance data security and improve monitoring. The slide further covers working and benefits that are it provide greater speed, and provides real-time insights. This modern and well-arranged Optimization Of IoT Remote Monitoring Edge Ai Used To Reduce Cost And Bandwidth IoT SS V provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide provides an overview of the edge AI used to enhance data security and improve monitoring. The slide further covers working and benefits that are it provide greater speed, and provides real-time insights.
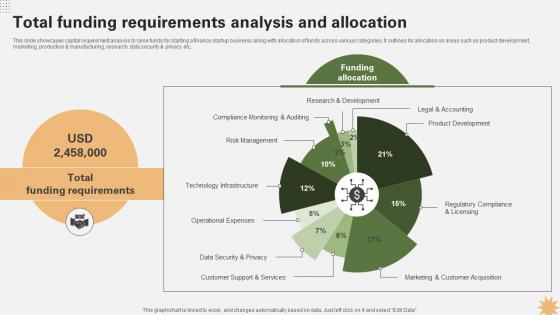
Total Funding Requirements Analysis And Allocation Strategy For Launching A Financial Strategy SS V
This slide showcases capital requirement analysis to raise funds for starting a finance startup business along with allocation of funds across various categories. It outlines its allocation on areas such as product development, marketing, production and manufacturing, research, data security and privacy etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Total Funding Requirements Analysis And Allocation Strategy For Launching A Financial Strategy SS V from Slidegeeks and deliver a wonderful presentation. This slide showcases capital requirement analysis to raise funds for starting a finance startup business along with allocation of funds across various categories. It outlines its allocation on areas such as product development, marketing, production and manufacturing, research, data security and privacy etc..
Comparative Analysis Of Health Transforming Medical Workflows Via His Integration Icons Pdf
This slide covers comparative assessment of health management information tool to select suitable one. It involves features such as clinical database, data compliance, enhanced security and healthcare analytics. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Comparative Analysis Of Health Transforming Medical Workflows Via His Integration Icons Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Comparative Analysis Of Health Transforming Medical Workflows Via His Integration Icons Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide covers comparative assessment of health management information tool to select suitable one. It involves features such as clinical database, data compliance, enhanced security and healthcare analytics.

Comparative Analysis Health Healthcare Information Tech To Enhance Medical Facilities Diagrams Pdf
This slide covers comparative assessment of health management information tool to select suitable one. It involves features such as clinical database, data compliance, enhanced security and healthcare analytics. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Comparative Analysis Health Healthcare Information Tech To Enhance Medical Facilities Diagrams Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Comparative Analysis Health Healthcare Information Tech To Enhance Medical Facilities Diagrams Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide covers comparative assessment of health management information tool to select suitable one. It involves features such as clinical database, data compliance, enhanced security and healthcare analytics.

Infrastructure Management Overview Playbook For Strategic Actions To Improve IT Performance Structure Pdf
This slide provides information regarding the various roles considered as critical for successful infrastructure management in terms of release manager, automation architectintegration specialist, software testerdeveloper and security engineer. Explore a selection of the finest Infrastructure Management Overview Playbook For Strategic Actions To Improve IT Performance Structure Pdf here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Infrastructure Management Overview Playbook For Strategic Actions To Improve IT Performance Structure Pdf to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide provides information regarding the various roles considered as critical for successful infrastructure management in terms of release manager, automation architectintegration specialist, software testerdeveloper and security engineer.
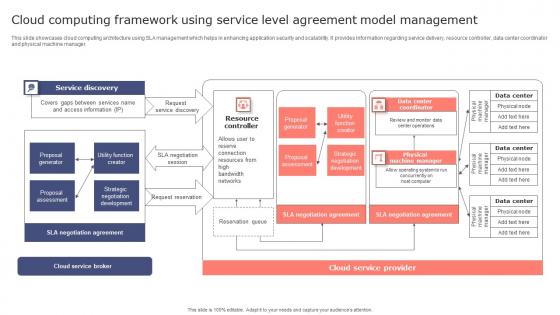
Cloud Computing Framework Using Service Level Agreement Model Management Topics Pdf
This slide showcases cloud computing architecture using SLA management which helps in enhancing application security and scalability. It provides information regarding service delivery, resource controller, data center coordinator and physical machine manager. Showcasing this set of slides titled Cloud Computing Framework Using Service Level Agreement Model Management Topics Pdf. The topics addressed in these templates are Service Discovery, Resource Controller. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcases cloud computing architecture using SLA management which helps in enhancing application security and scalability. It provides information regarding service delivery, resource controller, data center coordinator and physical machine manager.

Addressing Solutions For Erp Integration Challenges Erp And Digital Transformation For Maximizing DT SS V
This slide presents solutions to address various issues regarding enterprise integration in digital transformation. It includes resistance to change, data integration and quality issues, vendor selection and compatibility, inadequate talent and training, security and data privacy concerns, legacy systems and technical debt, and user adoption and training.Find a pre-designed and impeccable Addressing Solutions For Erp Integration Challenges Erp And Digital Transformation For Maximizing DT SS V. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide presents solutions to address various issues regarding enterprise integration in digital transformation. It includes resistance to change, data integration and quality issues, vendor selection and compatibility, inadequate talent and training, security and data privacy concerns, legacy systems and technical debt, and user adoption and training.
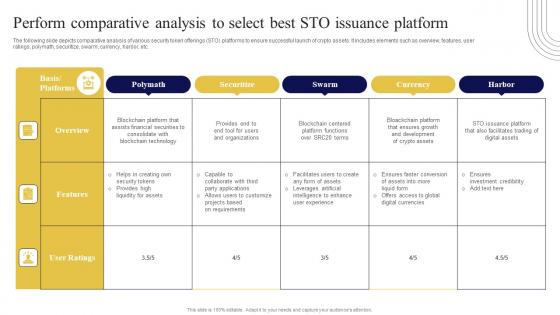
Perform Comparative Analysis To Select Exploring Investment Opportunities Download Pdf
The following slide depicts comparative analysis of various security token offerings STO platforms to ensure successful launch of crypto assets. It includes elements such as overview, features, user ratings, polymath, securitize, swarm, currency, harbor, etc. Get a simple yet stunning designed Perform Comparative Analysis To Select Exploring Investment Opportunities Download Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Perform Comparative Analysis To Select Exploring Investment Opportunities Download Pdf can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. The following slide depicts comparative analysis of various security token offerings STO platforms to ensure successful launch of crypto assets. It includes elements such as overview, features, user ratings, polymath, securitize, swarm, currency, harbor, etc.

Growth Restraints Of Product Analytics Market Product Analytics Implementation Data Analytics V
This slide outlines major growth restraints that may hinder increased use of product analytics to boost sales. It covers arguments such as privacy and security issues, data integration from silos and lack of skilled professionals This Growth Restraints Of Product Analytics Market Product Analytics Implementation Data Analytics V is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Growth Restraints Of Product Analytics Market Product Analytics Implementation Data Analytics V features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide outlines major growth restraints that may hinder increased use of product analytics to boost sales. It covers arguments such as privacy and security issues, data integration from silos and lack of skilled professionals


 Continue with Email
Continue with Email

 Home
Home


































