Technology Security
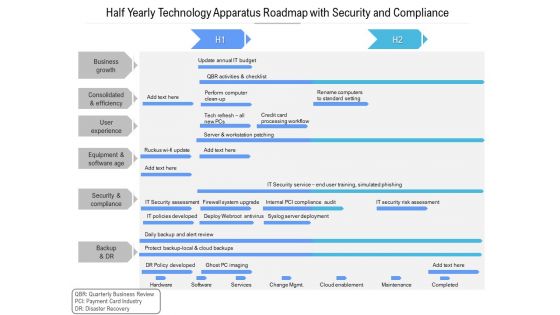
Half Yearly Technology Apparatus Roadmap With Security And Compliance Download
Presenting the half yearly technology apparatus roadmap with security and compliance download. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
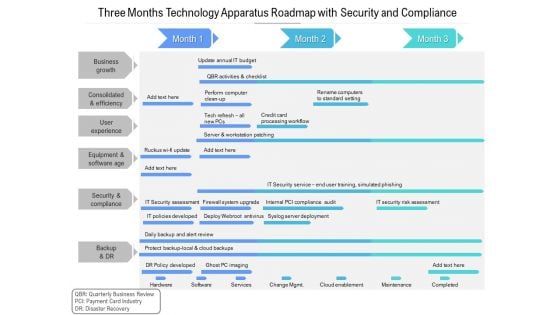
Three Months Technology Apparatus Roadmap With Security And Compliance Designs
Presenting the three months technology apparatus roadmap with security and compliance designs. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.

Security Management Technology Ppt PowerPoint Presentation Complete Deck With Slides
If designing a presentation takes a lot of your time and resources and you are looking for a better alternative, then this Security Management Technology Ppt PowerPoint Presentation Complete Deck With Slides is the right fit for you. This is a prefabricated set that can help you deliver a great presentation on the topic. All the seventeen slides included in this sample template can be used to present a birds-eye view of the topic. These slides are also fully editable, giving you enough freedom to add specific details to make this layout more suited to your business setting. Apart from the content, all other elements like color, design, theme are also replaceable and editable. This helps in designing a variety of presentations with a single layout. Not only this, you can use this PPT design in formats like PDF, PNG, and JPG once downloaded. Therefore, without any further ado, download and utilize this sample presentation as per your liking.
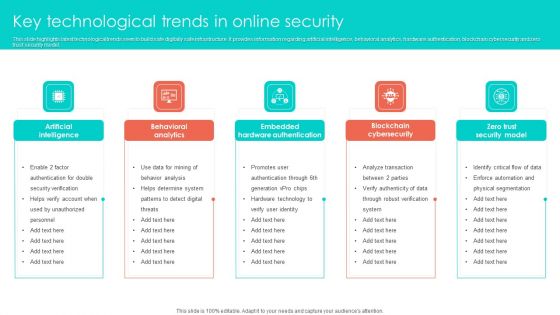
Key Technological Trends In Online Security Clipart PDF
This slide highlights latest technological trends seen to build safe digitally safe infrastructure. It provides information regarding artificial intelligence, behavioral analytics, hardware authentication, blockchain cybersecurity and zero trust security model. Persuade your audience using this Key Technological Trends In Online Security Clipart PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Behavioral Analytics, Artificial Intelligence, Embedded Hardware Authentication. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
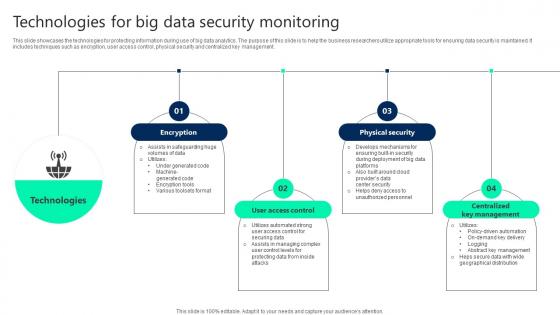
Technologies For Big Data Security Monitoring Summary pdf
This slide showcases the technologies for protecting information during use of big data analytics. The purpose of this slide is to help the business researchers utilize appropriate tools for ensuring data security is maintained. It includes techniques such as encryption, user access control, physical security and centralized key management. Showcasing this set of slides titled Technologies For Big Data Security Monitoring Summary pdf. The topics addressed in these templates are User Access Control, Physical Security, Centralized Key Management. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcases the technologies for protecting information during use of big data analytics. The purpose of this slide is to help the business researchers utilize appropriate tools for ensuring data security is maintained. It includes techniques such as encryption, user access control, physical security and centralized key management.

Chart Showing Technology Threats Methods And Technology For Cyber Security Ppt PowerPoint Presentation Ideas Slideshow PDF
Presenting chart showing technology threats methods and technology for cyber security ppt powerpoint presentation ideas slideshow pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including computer security attributes, attack methods, technology for internet security, confidentiality, integrity, privacy, availability. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Secure Email Technology PowerPoint Templates Ppt Backgrounds For Slides 0413
We present our Secure Email Technology PowerPoint Templates PPT Backgrounds For Slides 0413.Download our Technology PowerPoint Templates because Your audience will believe you are the cats whiskers. Download our Security PowerPoint Templates because Our PowerPoint Templates and Slides will provide you a launch platform. Give a lift off to your ideas and send them into orbit. Present our Communication PowerPoint Templates because Timeline crunches are a fact of life. Meet all deadlines using our PowerPoint Templates and Slides. Download our Business PowerPoint Templates because Our PowerPoint Templates and Slides will help you be quick off the draw. Just enter your specific text and see your points hit home. Download and present our Signs PowerPoint Templates because our PowerPoint Templates and Slides are the string of your bow. Fire of your ideas and conquer the podium.Use these PowerPoint slides for presentations relating to Illustration of envelope and email sign protect with padloc, security, communication, technology, business, signs. The prominent colors used in the PowerPoint template are Red, Gray, Yellow. Deal a decisive blow with our Secure Email Technology PowerPoint Templates Ppt Backgrounds For Slides 0413. Get clearlyahead in a critical event.

Secured Laptop Technology PowerPoint Templates Ppt Backgrounds For Slides 0213
We present our Secured Laptop Technology PowerPoint Templates PPT Backgrounds For Slides 0213.Use our Technology PowerPoint Templates because Our PowerPoint Templates and Slides will fulfill your every need. Use them and effectively satisfy the desires of your audience. Present our Business PowerPoint Templates because They will bring a lot to the table. Their alluring flavours will make your audience salivate. Present our Signs PowerPoint Templates because You can Hit the nail on the head with our PowerPoint Templates and Slides. Embed your ideas in the minds of your audience. Download and present our Security PowerPoint Templates because You aspire to touch the sky with glory. Let our PowerPoint Templates and Slides provide the fuel for your ascent. Use our Shapes PowerPoint Templates because Our PowerPoint Templates and Slides team portray an attitude of elegance. Personify this quality by using them regularly.Use these PowerPoint slides for presentations relating to Notebook Lockable, technology, business, security, signs, shapes. The prominent colors used in the PowerPoint template are Red, Gray, Yellow. Get all factions to act together. Our Secured Laptop Technology PowerPoint Templates Ppt Backgrounds For Slides 0213 can help achieve a common cause.
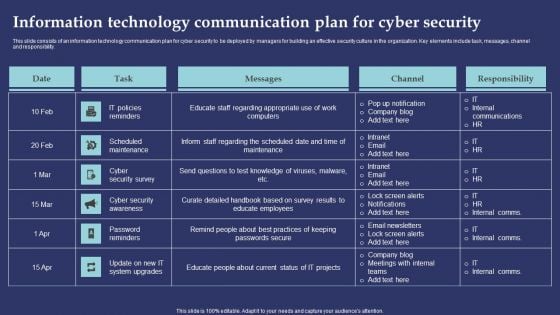
Information Technology Communication Plan For Cyber Security Information PDF
This slide consists of an information technology communication plan for cyber security to be deployed by managers for building an effective security culture in the organization. Key elements include task, messages, channel and responsibility. Showcasing this set of slides titled Information Technology Communication Plan For Cyber Security Information PDF. The topics addressed in these templates are IT Policies Reminders, Scheduled Maintenance, Cyber Security Survey. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
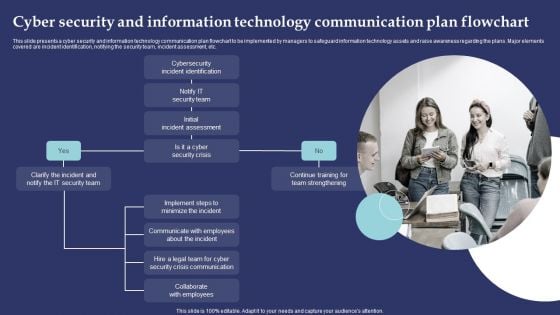
Cyber Security And Information Technology Communication Plan Flowchart Guidelines PDF
This slide presents a cyber security and information technology communication plan flowchart to be implemented by managers to safeguard information technology assets and raise awareness regarding the plans. Major elements covered are incident identification, notifying the security team, incident assessment, etc. Presenting Cyber Security And Information Technology Communication Plan Flowchart Guidelines PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Cybersecurity Incident Identification, Initial Incident Assessment, Continue Training Team Strengthening. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
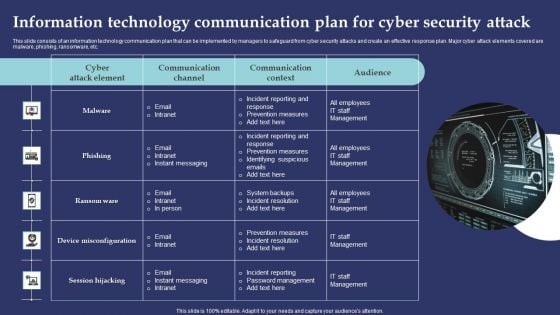
Information Technology Communication Plan For Cyber Security Attack Summary PDF
This slide consists of an information technology communication plan that can be implemented by managers to safeguard from cyber security attacks and create an effective response plan. Major cyber attack elements covered are malware, phishing, ransomware, etc. Presenting Information Technology Communication Plan For Cyber Security Attack Summary PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Incident Reporting Response, Prevention Measures, Incident Reporting. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Application Of Internet Security In Operational Technology Pictures Pdf
This slide showcase operational technology cyber risk strategy mapping to different project lifecycles from strategy, architecture, implementation, and operations phases to prevent, predict, detect and response adaptative security model.Showcasing this set of slides titled Application Of Internet Security In Operational Technology Pictures Pdf The topics addressed in these templates are Consequence Driven Scenarios, Execute Prioritized, Risk Identified All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcase operational technology cyber risk strategy mapping to different project lifecycles from strategy, architecture, implementation, and operations phases to prevent, predict, detect and response adaptative security model.
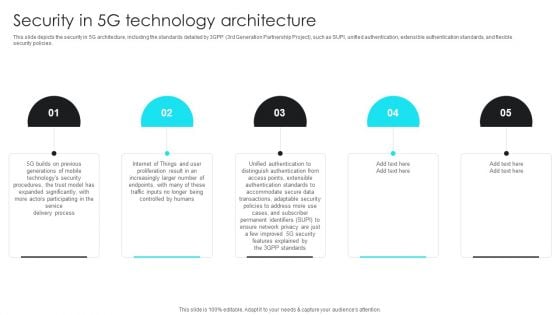
5G Network Operations Security In 5G Technology Architecture Template PDF
This slide depicts the security in 5G architecture, including the standards detailed by 3GPP 3rd Generation Partnership Project, such as SUPI, unified authentication, extensible authentication standards, and flexible security policies. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download 5G Network Operations Security In 5G Technology Architecture Template PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the 5G Network Operations Security In 5G Technology Architecture Template PDF.
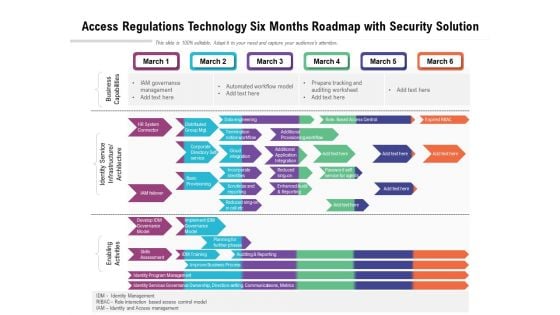
Access Regulations Technology Six Months Roadmap With Security Solution Brochure
Introducing our access regulations technology six months roadmap with security solution brochure. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.
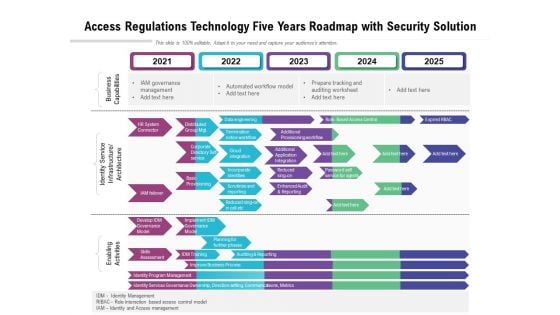
Access Regulations Technology Five Years Roadmap With Security Solution Inspiration
Presenting our innovatively structured access regulations technology five years roadmap with security solution inspiration Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.

Security In 5G Technology Architecture 5G Functional Architecture Formats PDF
This slide depicts the security in 5G architecture, including the standards detailed by 3GPP 3rd Generation Partnership Project, such as SUPI, unified authentication, extensible authentication standards, and flexible security policies.This is a Security In 5G Technology Architecture 5G Functional Architecture Formats PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Previous Generations, Distinguish Authentication, Transactions Adaptable. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
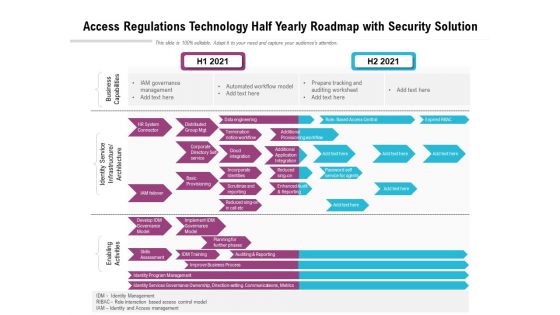
Access Regulations Technology Half Yearly Roadmap With Security Solution Guidelines
Presenting the access regulations technology half yearly roadmap with security solution guidelines. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
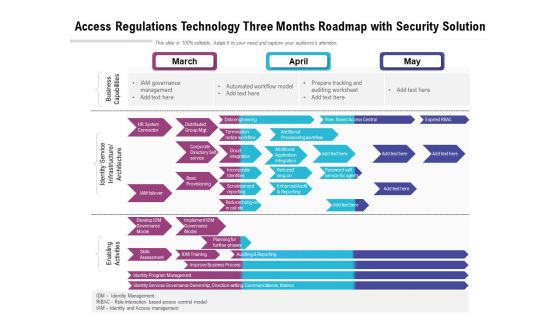
Access Regulations Technology Three Months Roadmap With Security Solution Guidelines
Presenting our jaw dropping access regulations technology three months roadmap with security solution guidelines. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.

Security In 5G Technology Architecture 5G Network Structure Pictures PDF
This slide depicts the security in 5G architecture, including the standards detailed by 3GPP 3rd Generation Partnership Project, such as SUPI, unified authentication, extensible authentication standards, and flexible security policies.Retrieve professionally designed Security In 5G Technology Architecture 5G Network Structure Pictures PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You Do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
Cyber Security Technology For Data Protection Ppt PowerPoint Presentation Ideas Visual Aids PDF
Persuade your audience using this cyber security technology for data protection ppt powerpoint presentation ideas visual aids pdf. This PPT design covers two stages, thus making it a great tool to use. It also caters to a variety of topics including cyber security technology for data protection. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Table Of Contents For IT Security Technology Ppt Infographics Designs PDF
Presenting table of contents for it security technology ppt infographics designs pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like technology, business, security, budget. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Internet Of Things Security Technology Image For Mobile Application Download Pdf
Showcasing this set of slides titled Internet Of Things Security Technology Image For Mobile Application Download Pdf The topics addressed in these templates are Internet Of Things, Security Technology, Image For Mobile Application All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Our Internet Of Things Security Technology Image For Mobile Application Download Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Image For Blockchain Internet Of Things Security Technology For Business Professional Pdf
Showcasing this set of slides titled Image For Blockchain Internet Of Things Security Technology For Business Professional Pdf The topics addressed in these templates are Blockchain Internet, Things Security, Technology For Business All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Our Image For Blockchain Internet Of Things Security Technology For Business Professional Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Lockable Notebook Security Technology PowerPoint Templates Ppt Backgrounds For Slides 0213
We present our Lockable Notebook Security Technology PowerPoint Templates PPT Backgrounds For Slides 0213.Download our Computer PowerPoint Templates because Our PowerPoint Templates and Slides have the Brilliant backdrops. Guaranteed to illuminate the minds of your audience. Use our Internet PowerPoint Templates because Our PowerPoint Templates and Slides are specially created by a professional team with vast experience. They diligently strive to come up with the right vehicle for your brilliant Ideas. Present our Technology PowerPoint Templates because Our PowerPoint Templates and Slides are the chords of your song. String them along and provide the lilt to your views. Present our Security PowerPoint Templates because Watching this your Audience will Grab their eyeballs, they wont even blink. Use our Success PowerPoint Templates because You are working at that stage with an air of royalty. Let our PowerPoint Templates and Slides be the jewels in your crown.Use these PowerPoint slides for presentations relating to Notebook lockable pattern, security, internet, computer, technology, success. The prominent colors used in the PowerPoint template are Brown, Black, Yellow. The audience will always evince interest. Our Lockable Notebook Security Technology PowerPoint Templates Ppt Backgrounds For Slides 0213 will make them apply their minds.
Information Technology Team Data Security And Communication Plan Icon Graphics PDF
Presenting Information Technology Team Data Security And Communication Plan Icon Graphics PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Information Technology, Team Data Security, Communication Plan Icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Icon For Payment Security Technology In Market Investor Transactions Summary PDF
Presenting Icon For Payment Security Technology In Market Investor Transactions Summary PDF to dispense important information. This template comprises Four stages. It also presents valuable insights into the topics including Icon For Payment Security, Technology Market Investor, Transactions Summary. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Technology Problems IT Security Vector Icon Ppt PowerPoint Presentation Gallery Graphic Images PDF
Persuade your audience using this technology problems it security vector icon ppt powerpoint presentation gallery graphic images pdf. This PPT design covers two stages, thus making it a great tool to use. It also caters to a variety of topics including technology problems it security vector icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Image For Personal Biometrics Internet Of Things Security Technology Summary Pdf
Showcasing this set of slides titled Image For Personal Biometrics Internet Of Things Security Technology Summary Pdf The topics addressed in these templates are Image For Personal, Biometrics Internet, Security Technology All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Our Image For Personal Biometrics Internet Of Things Security Technology Summary Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Cyber Security Technology Trends Ppt PowerPoint Presentation Model Graphics Download Cpb
Presenting this set of slides with name cyber security technology trends ppt powerpoint presentation model graphics download cpb. This is an editable Powerpoint four stages graphic that deals with topics like cyber security technology trends to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
New Technology Handle Cyber Security Ppt PowerPoint Presentation Infographics Graphics Pictures Cpb
Presenting this set of slides with name new technology handle cyber security ppt powerpoint presentation infographics graphics pictures cpb. This is an editable Powerpoint three stages graphic that deals with topics like new technology handle cyber security to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
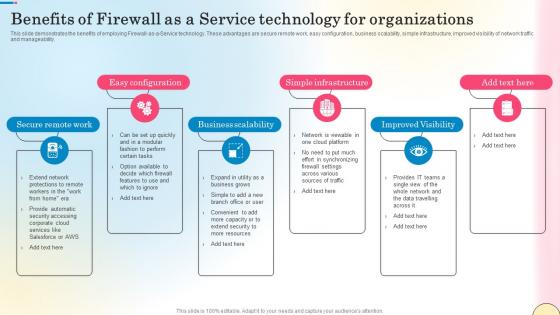
Benefits Of Firewall As A Service Technology For Network Security Inspiration Pdf
This slide demonstrates the benefits of employing Firewall-as-a-Service technology. These advantages are secure remote work, easy configuration, business scalability, simple infrastructure, improved visibility of network traffic and manageability. There are so many reasons you need a Benefits Of Firewall As A Service Technology For Network Security Inspiration Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide demonstrates the benefits of employing Firewall-as-a-Service technology. These advantages are secure remote work, easy configuration, business scalability, simple infrastructure, improved visibility of network traffic and manageability.
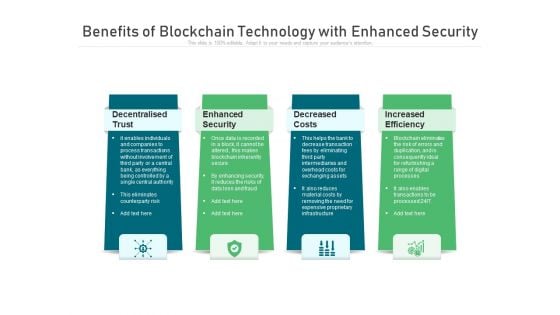
Benefits Of Blockchain Technology With Enhanced Security Ppt PowerPoint Presentation Gallery Infographics PDF
Presenting benefits of blockchain technology with enhanced security ppt powerpoint presentation gallery infographics pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including decentralised trust, enhanced security, decreased costs. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Barriers And Solutions Icons Slide Security Technology Ppt PowerPoint Presentation Model Information
Presenting this set of slides with name barriers and solutions icons slide security technology ppt powerpoint presentation model information. The topics discussed in these slides are technology, communication, planning, strategy, marketing. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
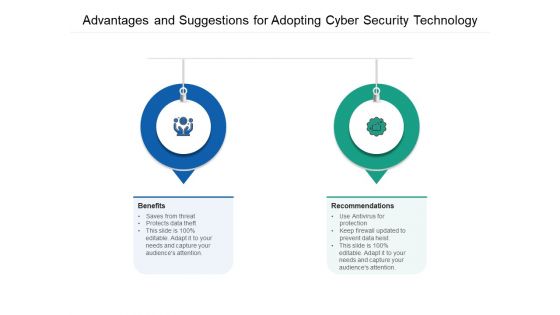
Advantages And Suggestions For Adopting Cyber Security Technology Ppt PowerPoint Presentation Gallery Example Topics PDF
Presenting advantages and suggestions for adopting cyber security technology ppt powerpoint presentation gallery example topics pdf to dispense important information. This template comprises two stages. It also presents valuable insights into the topics including benefits, recommendation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
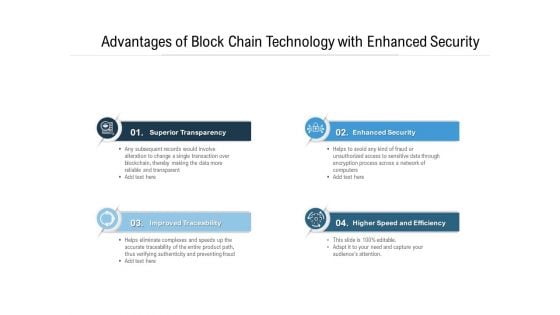
Advantages Of Block Chain Technology With Enhanced Security Ppt PowerPoint Presentation Gallery Good PDF
Presenting advantages of block chain technology with enhanced security ppt powerpoint presentation gallery good pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including transparency, traceability, efficiency. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
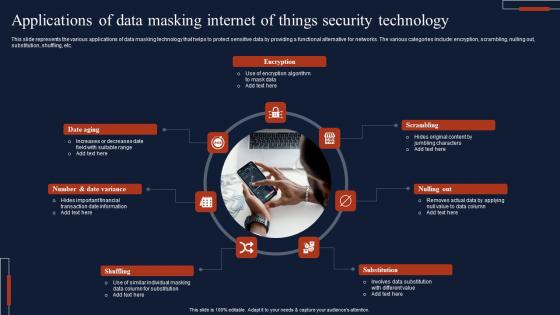
Applications Of Data Masking Internet Of Things Security Technology Topics Pdf
This slide represents the various applications of data masking technology that helps to protect sensitive data by providing a functional alternative for networks. The various categories include encryption, scrambling, nulling out, substitution, shuffling, etc. Showcasing this set of slides titled Applications Of Data Masking Internet Of Things Security Technology Topics Pdf The topics addressed in these templates are Encryption, Scrambling, Substitution, Shuffling All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide represents the various applications of data masking technology that helps to protect sensitive data by providing a functional alternative for networks. The various categories include encryption, scrambling, nulling out, substitution, shuffling, etc.

Cloud Technology Risks With Security Incident Management Ppt PowerPoint Presentation Gallery Graphics Template PDF
Presenting cloud technology risks with security incident management ppt powerpoint presentation gallery graphics template pdf. to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including identification and allowance, management interface vulnerability, security incident management, application security management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
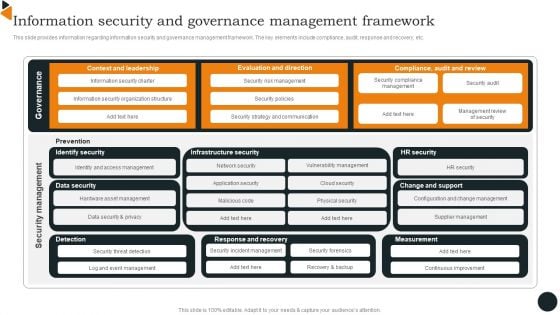
Chief Information Officers Guide On Technology Plan Information Security And Governance Formats PDF
This slide provides information regarding information security and governance management framework. The key elements include compliance, audit, response and recovery, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Chief Information Officers Guide On Technology Plan Information Security And Governance Formats PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Chief Information Officers Guide On Technology Plan Information Security And Governance Formats PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Top Firewall As A Service Technology Trends Network Security Mockup Pdf
This slide outlines the top Firewall-as-a-Service trends. The purpose of this slide is to briefly explain the top current FWaaS trends. These include firewalls remain important, zero trust in the cloud, isolation of security from the underlying infrastructure, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Top Firewall As A Service Technology Trends Network Security Mockup Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Top Firewall As A Service Technology Trends Network Security Mockup Pdf today and make your presentation stand out from the rest This slide outlines the top Firewall-as-a-Service trends. The purpose of this slide is to briefly explain the top current FWaaS trends. These include firewalls remain important, zero trust in the cloud, isolation of security from the underlying infrastructure, etc.
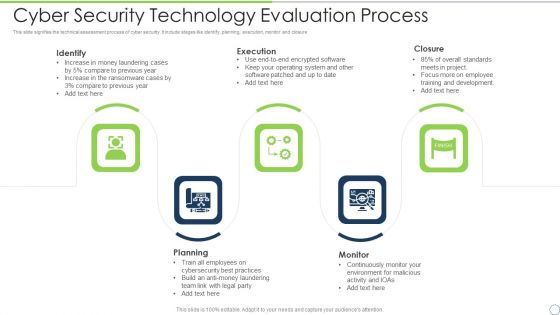
Cyber Security Technology Evaluation Process Ppt PowerPoint Presentation File Visual Aids PDF
This slide signifies the technical assessment process of cyber security. It include stages like identify, planning, execution, monitor and closure. Persuade your audience using this cyber security technology evaluation process ppt powerpoint presentation file visual aids pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including identify, execution, closure, monitor, planning. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
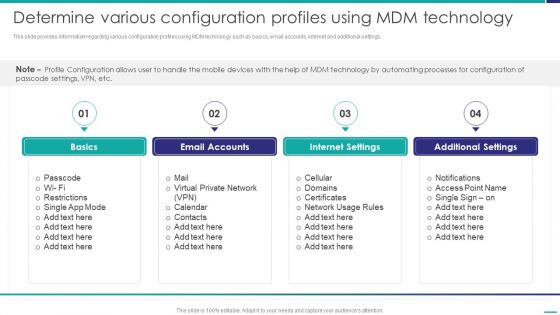
Determine Various Configuration Profiles Using MDM Technology Mobile Device Security Management Infographics PDF
This slide provides information regarding various configuration profiles using MDM technology such as basics, email accounts, internet and additional settings. Presenting Determine Various Configuration Profiles Using MDM Technology Mobile Device Security Management Infographics PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Restrictions, Internet Settings, Additional Settings. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
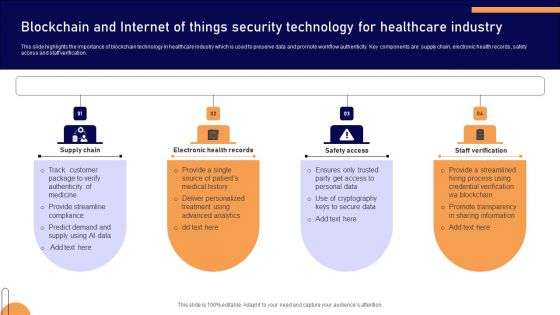
Blockchain And Internet Of Things Security Technology For Healthcare Industry Mockup PDF
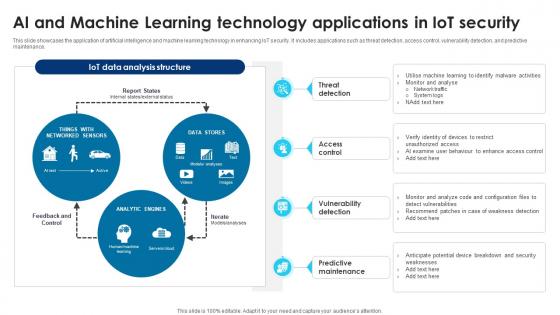
Building Trust With IoT Security AI And Machine Learning Technology Applications In IoT Security IoT SS V
This slide showcases the application of artificial intelligence and machine learning technology in enhancing IoT security. It includes applications such as threat detection, access control, vulnerability detection, and predictive maintenance. Boost your pitch with our creative Building Trust With IoT Security AI And Machine Learning Technology Applications In IoT Security IoT SS V. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide showcases the application of artificial intelligence and machine learning technology in enhancing IoT security. It includes applications such as threat detection, access control, vulnerability detection, and predictive maintenance.
Data Transfer Security Using Distributed Ledger Technology Icon Topics Pdf
Pitch your topic with ease and precision using this Data Transfer Security Using Distributed Ledger Technology Icon Topics Pdf This layout presents information on Data Transfer Security, Distributed Ledger, Technology Icon It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our Data Transfer Security Using Distributed Ledger Technology Icon Topics Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Ecommerce Payment Security Using Distributed Ledger Technology Icon Portrait Pdf
Showcasing this set of slides titled Ecommerce Payment Security Using Distributed Ledger Technology Icon Portrait Pdf The topics addressed in these templates are Ecommerce Payment Security, Distributed Ledger, Technology Icon All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Our Ecommerce Payment Security Using Distributed Ledger Technology Icon Portrait Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
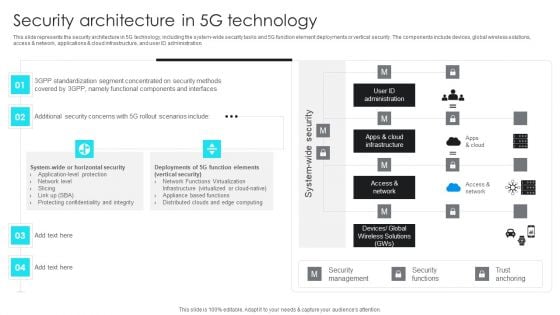
5G Network Operations Security Architecture In 5G Technology Inspiration PDF
This slide represents the security architecture in 5G technology, including the system-wide security tasks and 5G function element deployments or vertical security. The components include devices, global wireless solutions, access and network, applications cloud infrastructure, and user ID administration. Presenting this PowerPoint presentation, titled 5G Network Operations Security Architecture In 5G Technology Inspiration PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this 5G Network Operations Security Architecture In 5G Technology Inspiration PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable 5G Network Operations Security Architecture In 5G Technology Inspiration PDFthat is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.
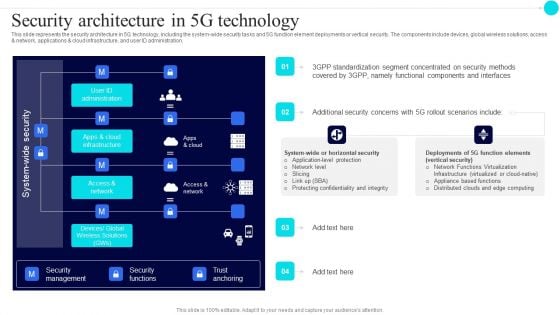
Security Architecture In 5G Technology 5G Functional Architecture Topics PDF
This slide represents the security architecture in 5G technology, including the system-wide security tasks and 5G function element deployments or vertical security. The components include devices, global wireless solutions, access and network, applications and cloud infrastructure, and user ID administration.Deliver an awe inspiring pitch with this creative Security Architecture In 5G Technology 5G Functional Architecture Topics PDF bundle. Topics like Standardization Segment, Concentrated Security, Components Interfaces can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
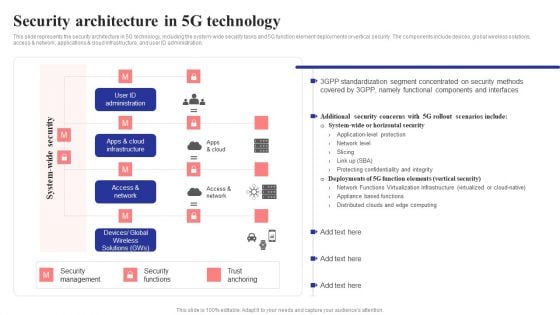
Security Architecture In 5G Technology 5G Network Structure Background PDF
This slide represents the security architecture in 5G technology, including the system-wide security tasks and 5G function element deployments or vertical security. The components include devices, global wireless solutions, access network, applications cloud infrastructure, and user ID administration.Are you searching for a Security Architecture In 5G Technology 5G Network Structure Background PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Security Architecture In 5G Technology 5G Network Structure Background PDF from Slidegeeks today.

Improving Security By Green Computing Technology Eco Friendly Computing IT
This slide outlines how green computing can improve security. The purpose of this slide is to showcase the pillars of data security, security concerns and solution, and different antivirus software that can help users to protect their computers and networks.Are you searching for a Improving Security By Green Computing Technology Eco Friendly Computing IT that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Improving Security By Green Computing Technology Eco Friendly Computing IT from Slidegeeks today. This slide outlines how green computing can improve security. The purpose of this slide is to showcase the pillars of data security, security concerns and solution, and different antivirus software that can help users to protect their computers and networks.

Solar Computing IT Improving Security By Green Computing Technology
This slide outlines how green computing can improve security. The purpose of this slide is to showcase the pillars of data security, security concerns and solution, and different antivirus software that can help users to protect their computers and networks. Are you searching for a Solar Computing IT Improving Security By Green Computing Technology that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Solar Computing IT Improving Security By Green Computing Technology from Slidegeeks today. This slide outlines how green computing can improve security. The purpose of this slide is to showcase the pillars of data security, security concerns and solution, and different antivirus software that can help users to protect their computers and networks.

Green Computing Improving Security By Green Computing Technology
This slide outlineshow green computing can improve security. The purpose of this slide is to showcase the pillars of data security, security concerns and solution, and different antivirus software that can help users to protect their computers and networks. The Green Computing Improving Security By Green Computing Technology is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide outlineshow green computing can improve security. The purpose of this slide is to showcase the pillars of data security, security concerns and solution, and different antivirus software that can help users to protect their computers and networks.
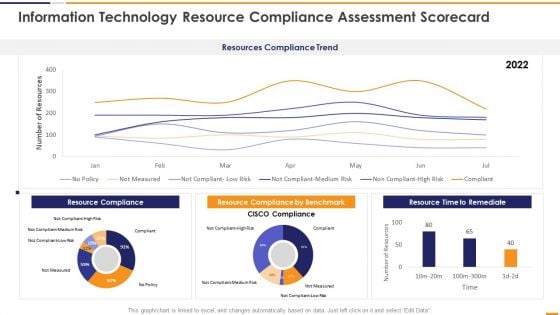
IT Security Evaluation Scorecard Information Technology Resource Compliance Background PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver and pitch your topic in the best possible manner with this IT Security Evaluation Scorecard Information Technology Resource Compliance Background PDF. Use them to share invaluable insights on Resources Compliance Trend, Resource Compliance 2022, Resource Compliance Benchmark, Resource Time Remediate and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
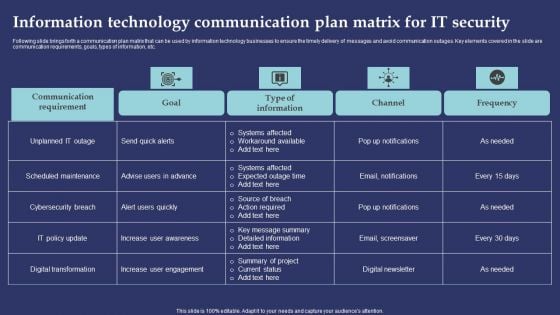
Information Technology Communication Plan Matrix For It Security Professional PDF
Following slide brings forth a communication plan matrix that can be used by information technology businesses to ensure the timely delivery of messages and avoid communication outages. Key elements covered in the slide are communication requirements, goals, types of information, etc. Showcasing this set of slides titled Information Technology Communication Plan Matrix For It Security Professional PDF. The topics addressed in these templates are Systems Affected, Workaround Available, Action Required. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
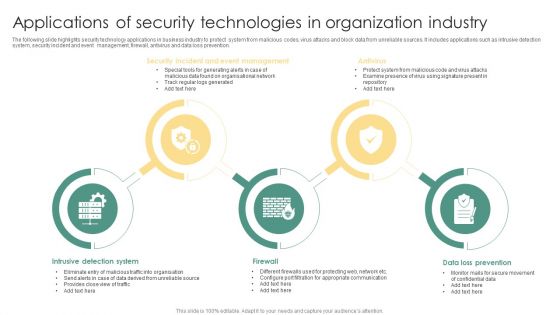
Applications Of Security Technologies In Organization Industry Ppt Summary Rules PDF
The following slide highlights security technology applications in business industry to protect system from malicious codes, virus attacks and block data from unreliable sources. It includes applications such as intrusive detection system, security incident and event management, firewall, antivirus and data loss prevention. Presenting Applications Of Security Technologies In Organization Industry Ppt Summary Rules PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Security Incident, Event Management, Antivirus, Firewall. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cybersecurity Operations Cybersecops Tools And Technologies Used In Security Mockup PDF
This slide highlights the crucial tools and technologies used in the SecOps environment. The purpose of this slide is to showcase the various tools and techniques a SOC requires. The main tools include log collection and management, vulnerability management, security information, and event management, etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Cybersecurity Operations Cybersecops Tools And Technologies Used In Security Mockup PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Cybersecurity Operations Cybersecops Tools And Technologies Used In Security Mockup PDF

Future Of Secure Web Gateway Technology Web Threat Protection System
This slide talks about the future of Secure Web Gateway security technology. The purpose of this slide is to explain how SWG can lead the cyber security market in future as more businesses are migrating to the cloud. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Future Of Secure Web Gateway Technology Web Threat Protection System and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide talks about the future of Secure Web Gateway security technology. The purpose of this slide is to explain how SWG can lead the cyber security market in future as more businesses are migrating to the cloud.
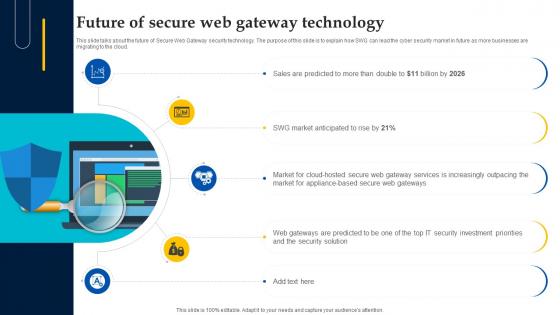
Web Access Control Solution Future Of Secure Web Gateway Technology
This slide talks about the future of Secure Web Gateway security technology. The purpose of this slide is to explain how SWG can lead the cyber security market in future as more businesses are migrating to the cloud. This modern and well-arranged Web Access Control Solution Future Of Secure Web Gateway Technology provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide talks about the future of Secure Web Gateway security technology. The purpose of this slide is to explain how SWG can lead the cyber security market in future as more businesses are migrating to the cloud.

Introduction To Secure Web Gateway Technology Web Threat Protection System
This slide talks about the network security solution called Secure Web Gateway. The purpose of this slide is to outline the various benefits of SWG. This slide also represents different working components of SWG such as traffic inspection, malware protection, etc. This Introduction To Secure Web Gateway Technology Web Threat Protection System is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Introduction To Secure Web Gateway Technology Web Threat Protection System features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide talks about the network security solution called Secure Web Gateway. The purpose of this slide is to outline the various benefits of SWG. This slide also represents different working components of SWG such as traffic inspection, malware protection, etc.
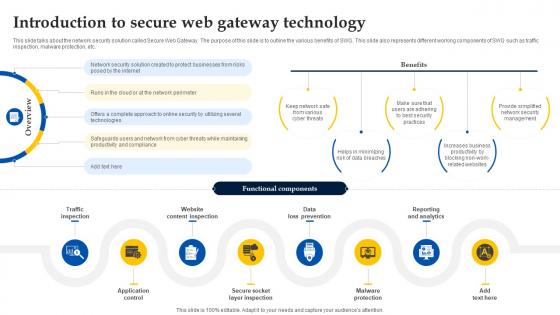
Web Access Control Solution Introduction To Secure Web Gateway Technology
This slide talks about the network security solution called Secure Web Gateway. The purpose of this slide is to outline the various benefits of SWG. This slide also represents different working components of SWG such as traffic inspection, malware protection, etc. Retrieve professionally designed Web Access Control Solution Introduction To Secure Web Gateway Technology to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide talks about the network security solution called Secure Web Gateway. The purpose of this slide is to outline the various benefits of SWG. This slide also represents different working components of SWG such as traffic inspection, malware protection, etc.
VPN Secure Technology Vector Icon Ppt PowerPoint Presentation Summary Ideas PDF
Persuade your audience using this vpn secure technology vector icon ppt powerpoint presentation summary ideas pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including vpn secure, technology vector icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.


 Continue with Email
Continue with Email

 Home
Home


































