Technology Security
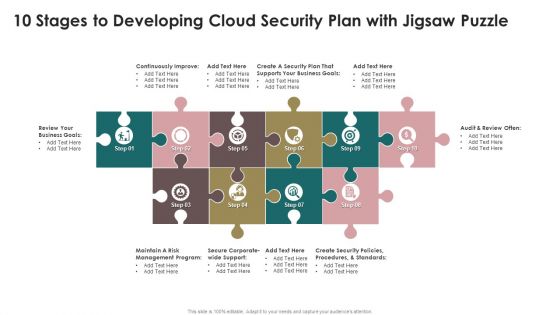
10 Stages To Developing Cloud Security Plan With Jigsaw Puzzle Themes PDF
Presenting 10 Stages To Developing Cloud Security Plan With Jigsaw Puzzle Themes PDF to dispense important information. This template comprises ten stages. It also presents valuable insights into the topics including Security Plan, Business Goals, Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
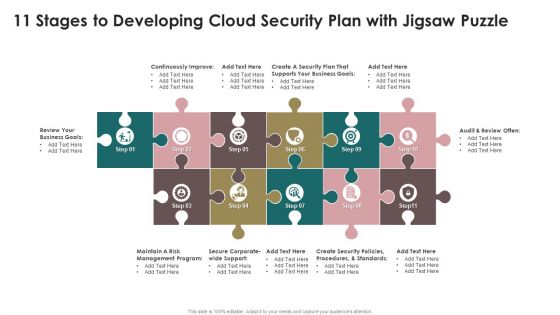
11 Stages To Developing Cloud Security Plan With Jigsaw Puzzle Topics PDF
Presenting 11 Stages To Developing Cloud Security Plan With Jigsaw Puzzle Topics PDF to dispense important information. This template comprises eleven stages. It also presents valuable insights into the topics including Security Plan, Business Goals, Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Training Program For Zero Trust Network Access Model Security Inspiration Pdf
This slide outlines the training program for implementing the zero-trust network access model in the organization. The purpose of this slide is to highlight the training agenda, objectives, system requirements, mode of training and cost of the training. Find a pre-designed and impeccable Training Program For Zero Trust Network Access Model Security Inspiration Pdf. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide outlines the training program for implementing the zero-trust network access model in the organization. The purpose of this slide is to highlight the training agenda, objectives, system requirements, mode of training and cost of the training.

Methods To Develop Measures And Ways To Mitigate Security Monitoring Challenges Background PDF
This slide provides information about the ways and measures through which the company and security monitoring managers can overcome the problems and issues related to Security Monitoring. Deliver an awe inspiring pitch with this creative methods to develop measures and ways to mitigate security monitoring challenges background pdf bundle. Topics like security monitoring challenges, employee management, malware attacks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
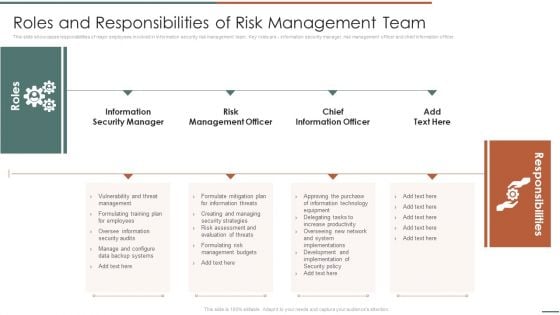
Information Security Risk Evaluation Roles And Responsibilities Of Risk Management Team Structure PDF
This slide showcases responsibilities of major employees involved in information security risk management team. Key roles are information security manager, risk management officer and chief information officer.Deliver an awe inspiring pitch with this creative Information Security Risk Evaluation Roles And Responsibilities Of Risk Management Team Structure PDF bundle. Topics like Information Security Manager, Risk Management, Chief Information can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Global Data Security Industry Report Overview Of Cybersecurity Market Landscape IR SS V
The slide highlights a comprehensive overview of the cyber security industry. The purpose of the slide is to provide insights to stakeholders enabling them to make strategic decisions. The slide covers market sizing, and statistics related to cybersecurity spending, cybercrimes, and venture funding. This modern and well-arranged Global Data Security Industry Report Overview Of Cybersecurity Market Landscape IR SS V provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. The slide highlights a comprehensive overview of the cyber security industry. The purpose of the slide is to provide insights to stakeholders enabling them to make strategic decisions. The slide covers market sizing, and statistics related to cybersecurity spending, cybercrimes, and venture funding.
Strategies To Mitigate Cyber Security Risks Optimizing Cybersecurity Framework Roadmap Ppt File Icon PDF
Presenting this set of slides with name strategies to mitigate cyber security risks optimizing cybersecurity framework roadmap ppt file icon pdf. The topics discussed in these slides are implement enterprise, security program, implement control environment, implement security processes. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
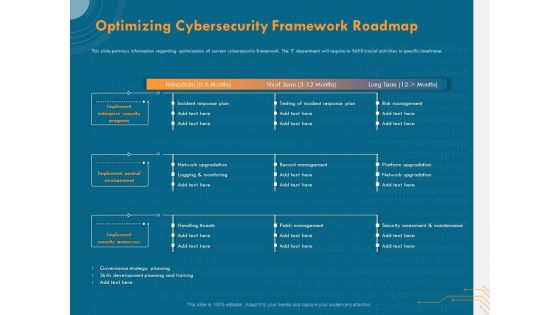
Cyber Security Implementation Framework Optimizing Cybersecurity Framework Roadmap Ppt Outline Background PDF
Presenting this set of slides with name cyber security implementation framework optimizing cybersecurity framework roadmap ppt outline background pdf. The topics discussed in these slides are implement enterprise security program, implement control environment, implement security processes, incident response plan, testing incident response plan, risk management. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Mastering Blockchain Wallets Mobile Wallets Key Security Issues And Solutions BCT SS V
This slide covers security concerns linked with mobile wallets and potential solutions to mitigate the risks. The purpose of this template is provide an overview on challenges associated such as lost or stolen devices, phishing scams, weak passwords along with risk involved with solutions to prevent risks and reduce its impact. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Mastering Blockchain Wallets Mobile Wallets Key Security Issues And Solutions BCT SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide covers security concerns linked with mobile wallets and potential solutions to mitigate the risks. The purpose of this template is provide an overview on challenges associated such as lost or stolen devices, phishing scams, weak passwords along with risk involved with solutions to prevent risks and reduce its impact.

Organizational Network Security Awareness Staff Learning Table Of Contents Introduction PDF
Deliver and pitch your topic in the best possible manner with this organizational network security awareness staff learning table of contents introduction pdf. Use them to share invaluable insights on security awareness training, organization impact metrics, security awareness, communication plan, budget and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
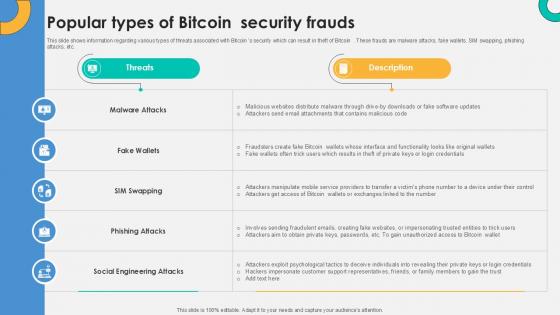
Popular Types Of Bitcoin Security Everything About Bitcoin PPT Slide Fin SS V
This slide shows information regarding various types of threats associated with Bitcoin s security which can result in theft of Bitcoin . These frauds are malware attacks, fake wallets, SIM swapping, phishing attacks, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Popular Types Of Bitcoin Security Everything About Bitcoin PPT Slide Fin SS V to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide shows information regarding various types of threats associated with Bitcoin s security which can result in theft of Bitcoin . These frauds are malware attacks, fake wallets, SIM swapping, phishing attacks, etc.

30 60 90 Days Plan Of Application Security Testing Ppt Powerpoint Sample
Find a pre-designed and impeccable 30 60 90 Days Plan Of Application Security Testing Ppt Powerpoint Sample. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. Our 30 60 90 Days Plan Of Application Security Testing Ppt Powerpoint Sample are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
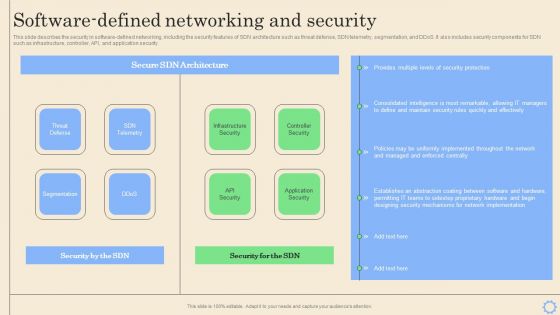
Software Defined Networking Development Strategies Software Defined Networking And Security Pictures PDF
This slide describes the security in software-defined networking, including the security features of SDN architecture such as threat defense, SDN telemetry, segmentation, and DDoS. It also includes security components for SDN such as infrastructure, controller, API, and application security. Want to ace your presentation in front of a live audience Our Software Defined Networking Development Strategies Software Defined Networking And Security Pictures PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.
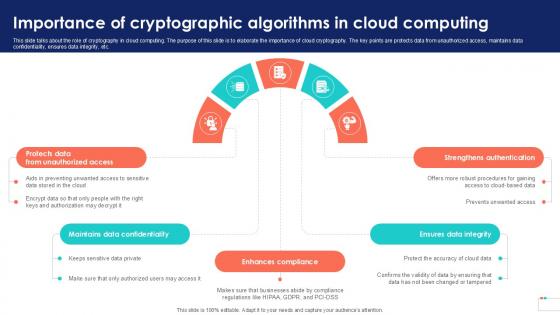
Importance Of Cryptographic Algorithms Data Security In Cloud Computing Ppt Presentation
This slide talks about the role of cryptography in cloud computing. The purpose of this slide is to elaborate the importance of cloud cryptography. The key points are protects data from unauthorized access, maintains data confidentiality, ensures data integrity, etc. Presenting this PowerPoint presentation, titled Importance Of Cryptographic Algorithms Data Security In Cloud Computing Ppt Presentation, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Importance Of Cryptographic Algorithms Data Security In Cloud Computing Ppt Presentation. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Importance Of Cryptographic Algorithms Data Security In Cloud Computing Ppt Presentation that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide talks about the role of cryptography in cloud computing. The purpose of this slide is to elaborate the importance of cloud cryptography. The key points are protects data from unauthorized access, maintains data confidentiality, ensures data integrity, etc.
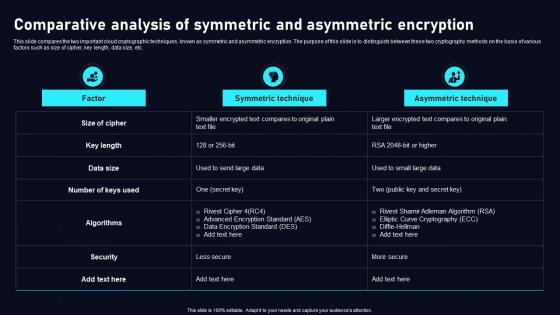
Comparative Analysis Of Symmetric Cloud Data Security Using Cryptography Clipart Pdf
This slide compares the two important cloud cryptographic techniques, known as symmetric and asymmetric encryption. The purpose of this slide is to distinguish between these two cryptography methods on the basis of various factors such as size of cipher, key length, data size, etc. Explore a selection of the finest Comparative Analysis Of Symmetric Cloud Data Security Using Cryptography Clipart Pdf here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Comparative Analysis Of Symmetric Cloud Data Security Using Cryptography Clipart Pdf to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide compares the two important cloud cryptographic techniques, known as symmetric and asymmetric encryption. The purpose of this slide is to distinguish between these two cryptography methods on the basis of various factors such as size of cipher, key length, data size, etc.

Data Breach Prevention Recognition Impact Of Security Awareness Training Sample PDF
This slide covers the good impact of security awareness program such as declining in the number of security threats which are phishing, network intrusion, inadvertent disclosure, stolen or lost devices or records and system misconfiguration. Deliver an awe-inspiring pitch with this creative data breach prevention recognition impact of security awareness training sample pdf bundle. Topics like security awareness program, security threats, network intrusion, inadvertent disclosure, system misconfiguration can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Global Data Security Industry Report Challenges Impeding Cybersecurity Industry Growth IR SS V
The purpose of the slide is to analyze challenges facing cybersecurity industry. It will assist stakeholders to devise effective strategies and solutions to overcome the repercussions. It covers restraints like shortage skills, rapidly evolving threat landscape, budget constraints, cloud security concerns, IoT and connected devices. Want to ace your presentation in front of a live audience Our Global Data Security Industry Report Challenges Impeding Cybersecurity Industry Growth IR SS V can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. The purpose of the slide is to analyze challenges facing cybersecurity industry. It will assist stakeholders to devise effective strategies and solutions to overcome the repercussions. It covers restraints like shortage skills, rapidly evolving threat landscape, budget constraints, cloud security concerns, IoT and connected devices.

Elliptic Curve Cryptography ECC Cloud Data Security Using Cryptography Brochure Pdf
This slide talks about the Elliptic Curve Cryptography algorithm. The purpose of this slide is to elaborate the different applications of ECC algorithm. The uses of this algorithm are key agreement, mobile devices, cryptocurrency, etc. Presenting this PowerPoint presentation, titled Elliptic Curve Cryptography ECC Cloud Data Security Using Cryptography Brochure Pdf, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Elliptic Curve Cryptography ECC Cloud Data Security Using Cryptography Brochure Pdf. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Elliptic Curve Cryptography ECC Cloud Data Security Using Cryptography Brochure Pdf that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide talks about the Elliptic Curve Cryptography algorithm. The purpose of this slide is to elaborate the different applications of ECC algorithm. The uses of this algorithm are key agreement, mobile devices, cryptocurrency, etc.
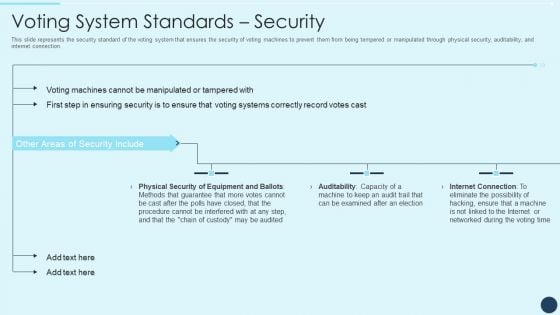
Electoral Mechanism IT Voting System Standards Security Ppt Professional Sample PDF
This slide represents the security standard of the voting system that ensures the security of voting machines to prevent them from being tempered or manipulated through physical security, auditability, and internet connection. Deliver an awe inspiring pitch with this creative electoral mechanism it voting system standards security ppt professional sample pdf bundle. Topics like physical security of equipment and ballots, auditability, internet connection can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Key Focus Areas In Digital Security And Access Management Ppt Visual Aids Model PDF
Showcasing this set of slides titled key focus areas in digital security and access management ppt visual aids model pdf. The topics addressed in these templates are digital security, cyber security, access management. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Guidelines To Create An Advanced Security Management Plan Table Of Contents Pictures PDF
Deliver an awe inspiring pitch with this creative guidelines to create an advanced security management plan table of contents pictures pdf bundle. Topics like essential elements, security management challenges, security management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Key Security Controls To Be Addressed In The Program Ppt Professional Vector PDF
Purpose of this slide is to provide information about key security controls that are to be addressed in companys information security program. Security controls covered are user application hardening, daily backups and patch applications. This is a key security controls to be addressed in the program ppt professional vector pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like key security controls to be addressed in the program. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
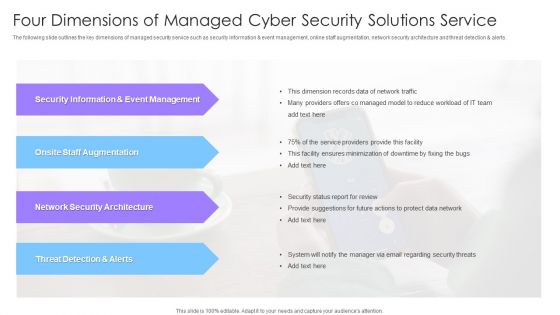
Four Dimensions Of Managed Cyber Security Solutions Service Ppt Pictures Model PDF
The following slide outlines the key dimensions of managed security service such as security information and event management, online staff augmentation, network security architecture and threat detection and alerts. Pitch your topic with ease and precision using this Four Dimensions Of Managed Cyber Security Solutions Service Ppt Pictures Model PDF. This layout presents information on Security Information, Event Management, Staff Augmentation. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
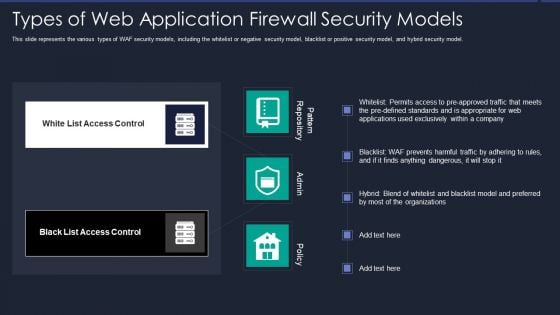
Web App Firewall Services IT Types Of Web Application Firewall Security Models Background PDF
This slide represents the various types of WAF security models, including the whitelist or negative security model, blacklist or positive security model, and hybrid security model. Presenting web app firewall services it types of web application firewall security models background pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like applications, organizations. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
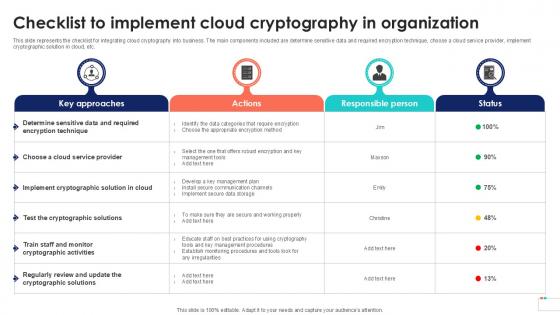
Checklist To Implement Cloud Data Security In Cloud Computing Ppt Powerpoint
This slide represents the checklist for integrating cloud cryptography into business. The main components included are determine sensitive data and required encryption technique, choose a cloud service provider, implement cryptographic solution in cloud, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Checklist To Implement Cloud Data Security In Cloud Computing Ppt Powerpoint can be your best option for delivering a presentation. Represent everything in detail using Checklist To Implement Cloud Data Security In Cloud Computing Ppt Powerpoint and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide represents the checklist for integrating cloud cryptography into business. The main components included are determine sensitive data and required encryption technique, choose a cloud service provider, implement cryptographic solution in cloud, etc.
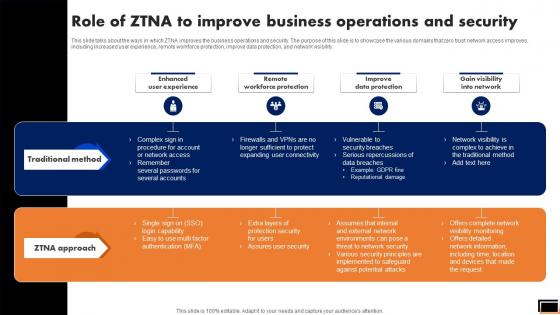
Role Of Ztna To Improve Business Operations And Security Software Defined Perimeter SDP
This slide talks about the ways in which ZTNA improves the business operations and security. The purpose of this slide is to showcase the various domains that zero trust network access improves, including increased user experience, remote workforce protection, improve data protection, and network visibility. Take your projects to the next level with our ultimate collection of Role Of Ztna To Improve Business Operations And Security Software Defined Perimeter SDP. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest This slide talks about the ways in which ZTNA improves the business operations and security. The purpose of this slide is to showcase the various domains that zero trust network access improves, including increased user experience, remote workforce protection, improve data protection, and network visibility.

What Are Benefits Of Using Cloud Data Security Using Cryptography Sample Pdf
This slide talks about the advantages of cloud data encryption. The purpose of this slide is to outline the benefits of cloud cryptography. These key benefits include data protection, data privacy, trust, users, integrity, availability, etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our What Are Benefits Of Using Cloud Data Security Using Cryptography Sample Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into What Are Benefits Of Using Cloud Data Security Using Cryptography Sample Pdf This slide talks about the advantages of cloud data encryption. The purpose of this slide is to outline the benefits of cloud cryptography. These key benefits include data protection, data privacy, trust, users, integrity, availability, etc.

Security Management Plan Steps In Detail Risk Assessment And Analysis Summary PDF
This slide provides information about the third step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. Risk Assessment and Analysis. Deliver and pitch your topic in the best possible manner with this security management plan steps in detail risk assessment and analysis summary pdf. Use them to share invaluable insights on security management plan steps in detail risk assessment and analysis and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Building Trust With IoT Security Deploy Tools For Continuous Device Monitoring And Diagnostics IoT SS V
This slide exhibits key activities and tools for monitoring and diagnostics of IoT device security. It includes activities such as continuous monitoring, anomaly detection, vulnerability scanning, auditing and reporting, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Building Trust With IoT Security Deploy Tools For Continuous Device Monitoring And Diagnostics IoT SS V is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Building Trust With IoT Security Deploy Tools For Continuous Device Monitoring And Diagnostics IoT SS V and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide exhibits key activities and tools for monitoring and diagnostics of IoT device security. It includes activities such as continuous monitoring, anomaly detection, vulnerability scanning, auditing and reporting, etc.

Limit Company Liability Workplace Safety Protocol And Security Practices Demonstration Pdf
This slide highlights the positive impacts from the workplace safety which showcases reduce medical compensation, zero regulatory fines, few legal repercussion and reduce indirect costs. Explore a selection of the finest Limit Company Liability Workplace Safety Protocol And Security Practices Demonstration Pdf here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Limit Company Liability Workplace Safety Protocol And Security Practices Demonstration Pdf to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide highlights the positive impacts from the workplace safety which showcases reduce medical compensation, zero regulatory fines, few legal repercussion and reduce indirect costs.

Workplace Safety Protocol And Security Practices Table Of Contents Themes Pdf
Slidegeeks is here to make your presentations a breeze with Workplace Safety Protocol And Security Practices Table Of Contents Themes Pdf With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first Our Workplace Safety Protocol And Security Practices Table Of Contents Themes Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Big Data Security Monitoring Ppt Powerpoint Presentation Complete Deck With Slides
Improve your presentation delivery using this Big Data Security Monitoring Ppt Powerpoint Presentation Complete Deck With Slides. Support your business vision and objectives using this well-structured PPT deck. This template offers a great starting point for delivering beautifully designed presentations on the topic of your choice. Comprising sixteen slides this professionally designed template is all you need to host discussion and meetings with collaborators. Each slide is self-explanatory and equipped with high-quality graphics that can be adjusted to your needs. Therefore, you will face no difficulty in portraying your desired content using this PPT slideshow. This PowerPoint slideshow contains every important element that you need for a great pitch. It is not only editable but also available for immediate download and utilization. The color, font size, background, shapes everything can be modified to create your unique presentation layout. Therefore, download it now. Our Big Data Security Monitoring Ppt Powerpoint Presentation Complete Deck With Slides are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Global Data Security Industry Report Regional Market Insights For Cybersecurity Industry IR SS V
The slide portrays a detailed overview of the cybersecurity industry. The purpose of the slide is to provide regional dynamics and assist stakeholders in developing regionally-tailored products and strategies to maximize market share. It covers regions such as North America, Asia Pacific, Europe, Latin America, and the Middle East and Africa. Explore a selection of the finest Global Data Security Industry Report Regional Market Insights For Cybersecurity Industry IR SS V here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Global Data Security Industry Report Regional Market Insights For Cybersecurity Industry IR SS V to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. The slide portrays a detailed overview of the cybersecurity industry. The purpose of the slide is to provide regional dynamics and assist stakeholders in developing regionally-tailored products and strategies to maximize market share. It covers regions such as North America, Asia Pacific, Europe, Latin America, and the Middle East and Africa.

SWOT Analysis To Understand The Global Security Industry PPT Slide IR SS V
Retrieve professionally designed SWOT Analysis To Understand The Global Security Industry PPT Slide IR SS V to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. Our SWOT Analysis To Understand The Global Security Industry PPT Slide IR SS V are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
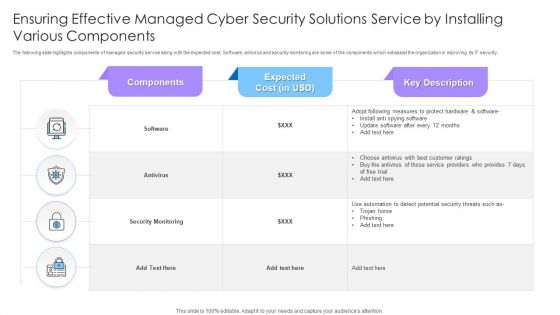
Ensuring Effective Managed Cyber Security Solutions Service By Installing Various Components Ppt Styles Example PDF
The following slide highlights components of managed security service along with the expected cost. Software, antivirus and security monitoring are some of the components which will assist the organization in improving its IT security. Showcasing this set of slides titled Ensuring Effective Managed Cyber Security Solutions Service By Installing Various Components Ppt Styles Example PDF. The topics addressed in these templates are Security Monitoring, Antivirus, Components. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
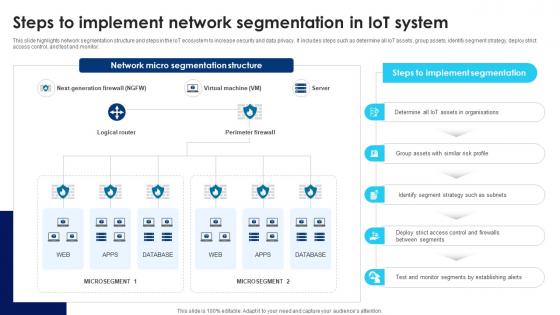
Building Trust With IoT Security Steps To Implement Network Segmentation In IoT System IoT SS V
This slide highlights network segmentation structure and steps in the IoT ecosystem to increase security and data privacy. It includes steps such as determine all IoT assets, group assets, identify segment strategy, deploy strict access control, and test and monitor. Slidegeeks is here to make your presentations a breeze with Building Trust With IoT Security Steps To Implement Network Segmentation In IoT System IoT SS V With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide highlights network segmentation structure and steps in the IoT ecosystem to increase security and data privacy. It includes steps such as determine all IoT assets, group assets, identify segment strategy, deploy strict access control, and test and monitor.
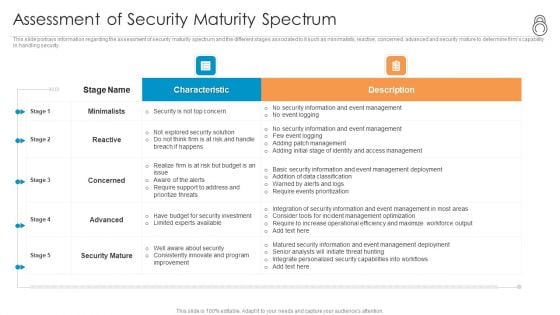
Enhanced Protection Corporate Event Administration Assessment Of Security Maturity Spectrum Background PDF
This slide portrays information regarding the assessment of security maturity spectrum and the different stages associated to it such as minimalists, reactive, concerned, advanced and security mature to determine firms capability in handling security. Deliver an awe inspiring pitch with this creative enhanced protection corporate event administration assessment of security maturity spectrum background pdf bundle. Topics like minimalists, reactive, concerned, advanced, security mature can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
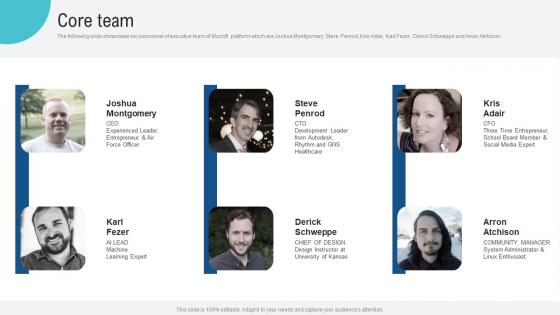
Core Team Voice Assistance Security Platform Investor Funding Presentation Mockup Pdf
The following slide showcases key personnel of executive team of Mycroft platform which are Joshua Montgomery, Steve Penrod, Kris Adair, Karl Fezer, Derick Schweppe and Arron Atchison. This modern and well arranged Core Team Voice Assistance Security Platform Investor Funding Presentation Mockup Pdf provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. The following slide showcases key personnel of executive team of Mycroft platform which are Joshua Montgomery, Steve Penrod, Kris Adair, Karl Fezer, Derick Schweppe and Arron Atchison.
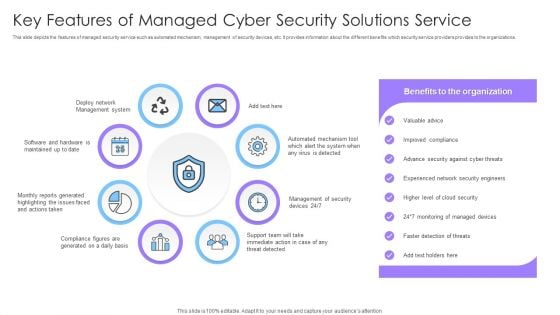
Key Features Of Managed Cyber Security Solutions Service Ppt Pictures Layouts PDF
This slide depicts the features of managed security service such as automated mechanism, management of security devices, etc. It provides information about the different benefits which security service providers provides to the organizations. Presenting Key Features Of Managed Cyber Security Solutions Service Ppt Pictures Layouts PDF to dispense important information. This template comprises eight stages. It also presents valuable insights into the topics including Deploy Network, Management System, Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Security Agency Business Profile Company Timeline From 1992 To 2022 Infographics PDF
This slide highlights the security company journey which showcases founding year, add armed security services in 2004, acquire GS security on 2015, add cash vans in 2016 and recruit personal protection officers. This is a Security Agency Business Profile Company Timeline From 1992 To 2022 Infographics PDF template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security, Expand Services, Protection Officers. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
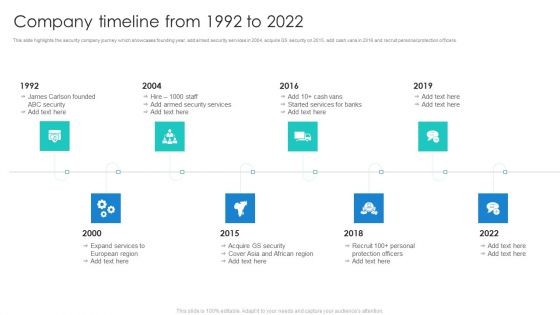
Manpower Corporate Security Business Profile Company Timeline From 1992 To 2022 Demonstration PDF
This slide highlights the security company journey which showcases founding year, add armed security services in 2004, acquire GS security on 2015, add cash vans in 2016 and recruit personal protection officers. This is a Manpower Corporate Security Business Profile Company Timeline From 1992 To 2022 Demonstration PDF template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Services, Protection Officers, Recruit. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
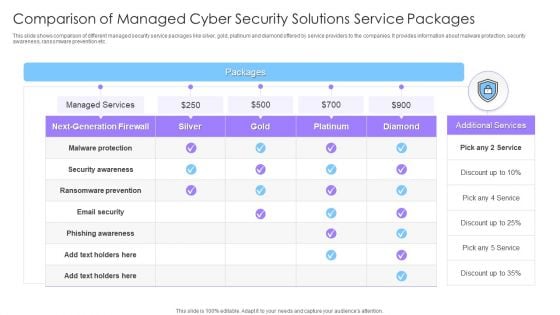
Comparison Of Managed Cyber Security Solutions Service Packages Ppt Ideas Mockup PDF
This slide shows comparison of different managed security service packages like silver, gold, platinum and diamond offered by service providers to the companies. It provides information about malware protection, security awareness, ransomware prevention etc. Pitch your topic with ease and precision using this Comparison Of Managed Cyber Security Solutions Service Packages Ppt Ideas Mockup PDF. This layout presents information on Email Security, Phishing Awareness, Security Awareness. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
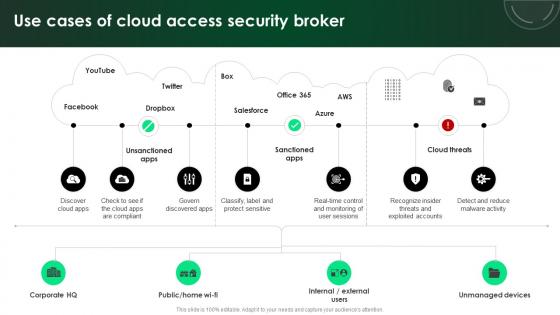
CASB 2 0 IT Use Cases Of Cloud Access Security Broker
This modern and well-arranged CASB 2 0 IT Use Cases Of Cloud Access Security Broker provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. Our CASB 2 0 IT Use Cases Of Cloud Access Security Broker are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Cyber Security Plan Road Map Of A Company Ppt PowerPoint Presentation Icon Show PDF
This slide represents 3 year cyber security plan road map of a company for website enhancement and implementing security to operational work with specific standards. It consists security standards, training and awareness phishing users and sensitive data management. Showcasing this set of slides titled Cyber Security Plan Road Map Of A Company Ppt PowerPoint Presentation Icon Show PDF. The topics addressed in these templates are Website Enhancement, Governance Subcommittee, Security Standards. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
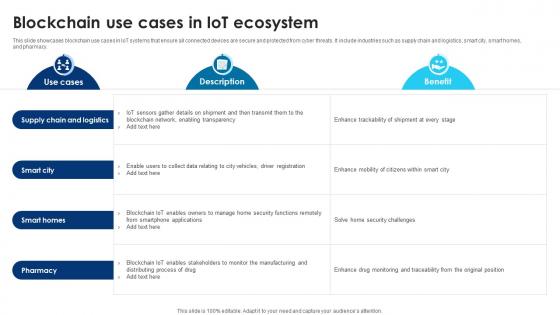
Building Trust With IoT Security Blockchain Use Cases In IoT Ecosystem IoT SS V
This slide showcases blockchain use cases in IoT systems that ensure all connected devices are secure and protected from cyber threats. It include industries such as supply chain and logistics, smart city, smart homes, and pharmacy. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Building Trust With IoT Security Blockchain Use Cases In IoT Ecosystem IoT SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide showcases blockchain use cases in IoT systems that ensure all connected devices are secure and protected from cyber threats. It include industries such as supply chain and logistics, smart city, smart homes, and pharmacy.

Business Plan For Managed Cyber Security Solutions Service Ppt Infographic Template Topics PDF
This slide outlines the business plan for managed security service which includes services such as antivirus, anti-malware, anti-spam etc. it also provides information about the total cost of services, status of purchase, security goal, etc. Pitch your topic with ease and precision using this Business Plan For Managed Cyber Security Solutions Service Ppt Infographic Template Topics PDF. This layout presents information on Revenue, Security Goal, IT Security Budget. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Complete Beginners Guide Popular Types Of Bitcoin Security Frauds Fin SS V
This slide shows information regarding various types of threats associated with Bitcoins security which can result in theft of Bitcoin . These frauds are malware attacks, fake wallets, SIM swapping, phishing attacks, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Complete Beginners Guide Popular Types Of Bitcoin Security Frauds Fin SS V to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Complete Beginners Guide Popular Types Of Bitcoin Security Frauds Fin SS V. This slide shows information regarding various types of threats associated with Bitcoins security which can result in theft of Bitcoin . These frauds are malware attacks, fake wallets, SIM swapping, phishing attacks, etc.

Key Solutions To Manage Saas Cloud Security Issues Ppt PowerPoint Presentation Gallery Visuals PDF
The following slide highlights multiple solutions to prevent security risks and issues. It also includes elements such as risk evaluation, security awareness, checklist, policies and regulation, recovery plan etc. Presenting Key Solutions To Manage Saas Cloud Security Issues Ppt PowerPoint Presentation Gallery Visuals PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Risk Evaluation, Security Awareness, Security Checklist, Policies And Regulation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Saas Cloud Security Implementation Checklist For Managers Ppt PowerPoint Presentation File Professional PDF
The following slide represents checklist for SaaS security implementation and assessment. It includes activities such as run security test, training staff, planning backup, installing automated security alert along with their status. Presenting Saas Cloud Security Implementation Checklist For Managers Ppt PowerPoint Presentation File Professional PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Run Security Test, Planned Backup, New Threats. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Comparative Analysis Of Digital Security Metrics For Small Businesses Icons Pdf
Pitch your topic with ease and precision using this Comparative Analysis Of Digital Security Metrics For Small Businesses Icons Pdf This layout presents information on Futuristic Approach, Data Driven Decisions, Exposed Assets It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide showcases the comparative analysis of cybersecurity KPIs for small businesses which helps an organization to carefully choose, select the best metric to track performance. It include details such as goal oriented, actionable, easy to understand, etc.

Security Management Plan Steps In Detail Evaluating Information Processing Assets Graphics PDF
This slide provides information about the second step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. Evaluating Information Processing Assets. Deliver and pitch your topic in the best possible manner with this security management plan steps in detail evaluating information processing assets graphics pdf. Use them to share invaluable insights on security management plan steps in detail evaluating information processing assets and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Security Management Plan Steps In Detail Remote Access Control Mockup PDF
This slide provides information about the sixth step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. Remote Access Control. Deliver an awe inspiring pitch with this creative security management plan steps in detail remote access control mockup pdf bundle. Topics like security management plan steps in detail remote access control can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Management Plan Steps In Detail Adopting Access Controls Microsoft PDF
This slide provides information about the fifth step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. Adopting Access Controls. Deliver an awe inspiring pitch with this creative security management plan steps in detail adopting access controls microsoft pdf bundle. Topics like implementation costs, security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Management Plan Steps In Detail Remote Access Control Topics PDF
This slide provides information about the sixth step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Remote Access Control. Deliver and pitch your topic in the best possible manner with this security management plan steps in detail remote access control topics pdf. Use them to share invaluable insights on requirement, security, implementation cost and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
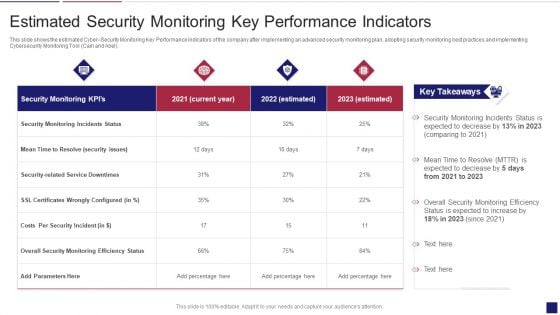
Continuous Development Evaluation Plan Eliminate Cyber Attacks Estimated Security Monitoring Designs PDF
This slide shows the estimated Cyber Security Monitoring Key Performance Indicators of the company after implementing an advanced security monitoring plan, adopting security monitoring best practices and implementing Cybersecurity Monitoring Tool Cain and Abel. Deliver and pitch your topic in the best possible manner with this continuous development evaluation plan eliminate cyber attacks estimated security monitoring designs pdf. Use them to share invaluable insights on estimated security monitoring key performance indicators and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
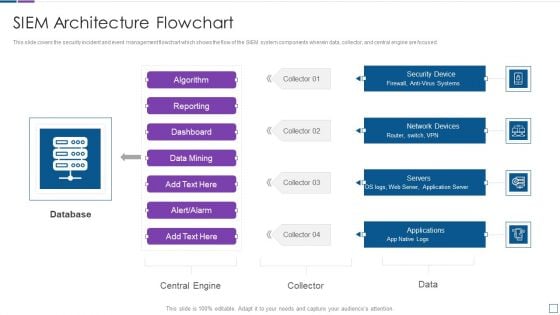
Real Time Assessment Of Security Threats SIEM Architecture Flowchart Sample PDF
This slide covers the security incident and event management flowchart which shows the flow of the SIEM system components wherein data, collector, and central engine are focused. Deliver an awe inspiring pitch with this creative real time assessment of security threats siem architecture flowchart sample pdf bundle. Topics like database, network devices, security device, servers, applications can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
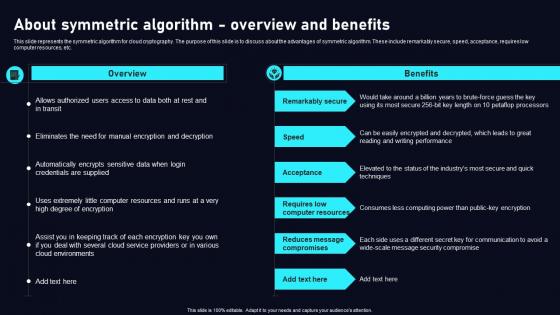
About Symmetric Algorithm Overview Cloud Data Security Using Cryptography Microsoft Pdf
This slide represents the symmetric algorithm for cloud cryptography. The purpose of this slide is to discuss about the advantages of symmetric algorithm. These include remarkably secure, speed, acceptance, requires low computer resources, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. About Symmetric Algorithm Overview Cloud Data Security Using Cryptography Microsoft Pdf can be your best option for delivering a presentation. Represent everything in detail using About Symmetric Algorithm Overview Cloud Data Security Using Cryptography Microsoft Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide represents the symmetric algorithm for cloud cryptography. The purpose of this slide is to discuss about the advantages of symmetric algorithm. These include remarkably secure, speed, acceptance, requires low computer resources, etc.
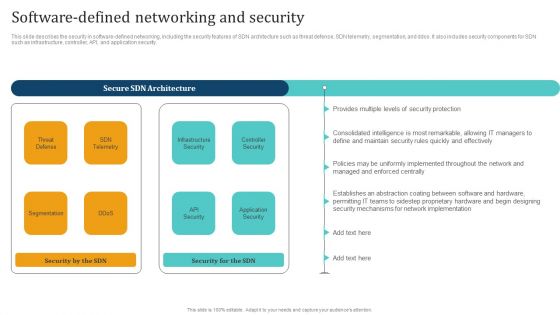
Empowering Network Agility Through SDN Software Defined Networking And Security Rules PDF
This slide describes the security in software defined networking, including the security features of SDN architecture such as threat defense, SDN telemetry, segmentation, and ddos. It also includes security components for SDN such as infrastructure, controller, API, and application security. Welcome to our selection of the Empowering Network Agility Through SDN Software Defined Networking And Security Rules PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.
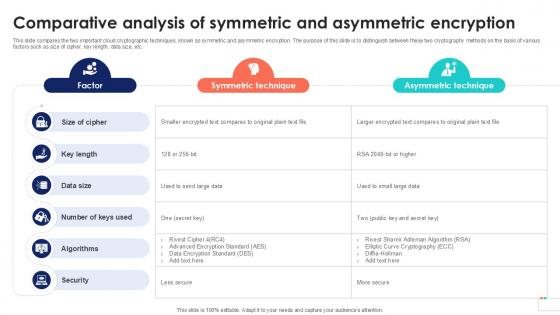
Comparative Analysis Of Symmetric Data Security In Cloud Computing Ppt Sample
This slide compares the two important cloud cryptographic techniques, known as symmetric and asymmetric encryption. The purpose of this slide is to distinguish between these two cryptography methods on the basis of various factors such as size of cipher, key length, data size, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Comparative Analysis Of Symmetric Data Security In Cloud Computing Ppt Sample. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide compares the two important cloud cryptographic techniques, known as symmetric and asymmetric encryption. The purpose of this slide is to distinguish between these two cryptography methods on the basis of various factors such as size of cipher, key length, data size, etc.
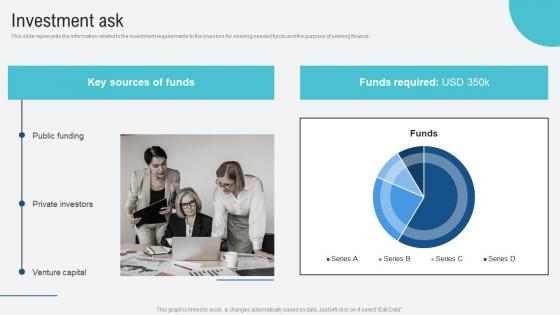
Investment Ask Voice Assistance Security Platform Investor Funding Presentation Elements Pdf
This slide represents the information related to the investment requirements to the investors for seeking needed funds and the purpose of seeking finance. Are you searching for a Investment Ask Voice Assistance Security Platform Investor Funding Presentation Elements Pdf that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Investment Ask Voice Assistance Security Platform Investor Funding Presentation Elements Pdf from Slidegeeks today. This slide represents the information related to the investment requirements to the investors for seeking needed funds and the purpose of seeking finance.


 Continue with Email
Continue with Email

 Home
Home


































