Technology Security
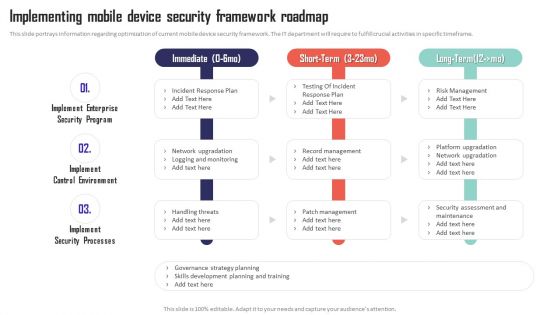
Mobile Device Management Implementing Mobile Device Security Framework Roadmap Pictures PDF
This slide portrays information regarding optimization of current mobile device security framework. The IT department will require to fulfill crucial activities in specific timeframe. Get a simple yet stunning designed Mobile Device Management Implementing Mobile Device Security Framework Roadmap Pictures PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Mobile Device Management Implementing Mobile Device Security Framework Roadmap Pictures PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Proposal For Enterprise Security System Next Step One Pager Sample Example Document
The following slide displays the next step that the organization has to take once the security proposal has been signed, these steps can be tem meeting ,on-site visit etc. Presenting you an exemplary Proposal For Enterprise Security System Next Step One Pager Sample Example Document. Our one pager comprises all the must have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Proposal For Enterprise Security System Next Step One Pager Sample Example Document brilliant piece now.
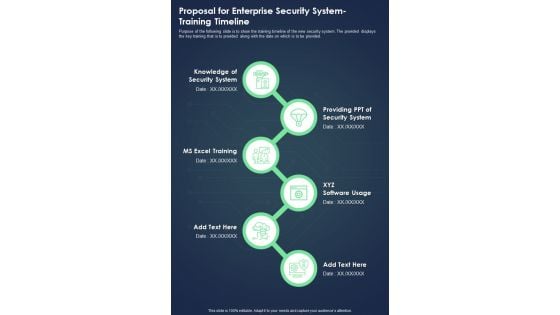
Proposal For Enterprise Security System Training Timeline One Pager Sample Example Document
Purpose of the following slide is to show the training timeline of the new security system. The provided displays the key training that is to provided along with the date on which is to be provided. Presenting you an exemplary Proposal For Enterprise Security System Training Timeline One Pager Sample Example Document. Our one pager comprises all the must have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Proposal For Enterprise Security System Training Timeline One Pager Sample Example Document brilliant piece now.

Proposal For Enterprise Security System Your Investment One Pager Sample Example Document
The following slide displays the investment required by the origination to implement the new security system Presenting you an exemplary Proposal For Enterprise Security System Your Investment One Pager Sample Example Document. Our one pager comprises all the must have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Proposal For Enterprise Security System Your Investment One Pager Sample Example Document brilliant piece now.

Next Step For Home Security Equipment Installation Proposal One Pager Sample Example Document
The following slide displays the next step that the organization has to take once the security proposal has been signed, these steps can be tem meeting ,on site visit etc. Presenting you an exemplary Next Step For Home Security Equipment Installation Proposal One Pager Sample Example Document. Our one pager comprises all the must have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Next Step For Home Security Equipment Installation Proposal One Pager Sample Example Document brilliant piece now.
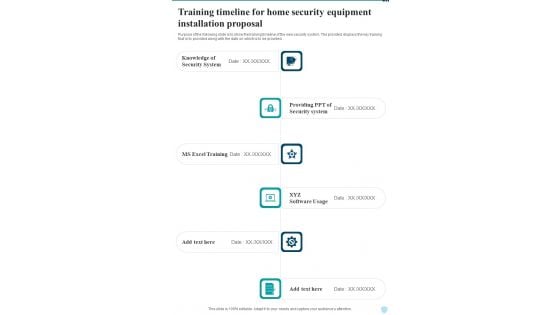
Training Timeline For Home Security Equipment Installation Proposal One Pager Sample Example Document
Purpose of the following slide is to show the training timeline of the new security system. The provided displays the key training that is to provided along with the date on which is to be provided. Presenting you an exemplary Training Timeline For Home Security Equipment Installation Proposal One Pager Sample Example Document. Our one pager comprises all the must have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Training Timeline For Home Security Equipment Installation Proposal One Pager Sample Example Document brilliant piece now.
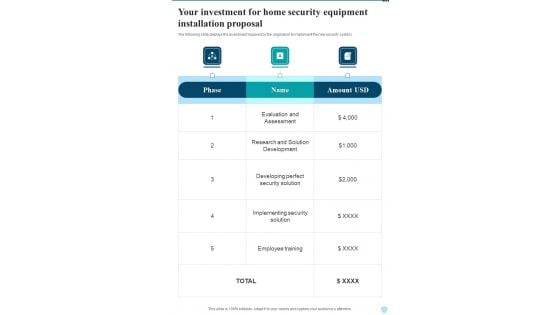
Your Investment For Home Security Equipment Installation Proposal One Pager Sample Example Document
The following slide displays the investment required by the origination to implement the new security system. Presenting you an exemplary Your Investment For Home Security Equipment Installation Proposal One Pager Sample Example Document. Our one pager comprises all the must have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Your Investment For Home Security Equipment Installation Proposal One Pager Sample Example Document brilliant piece now.
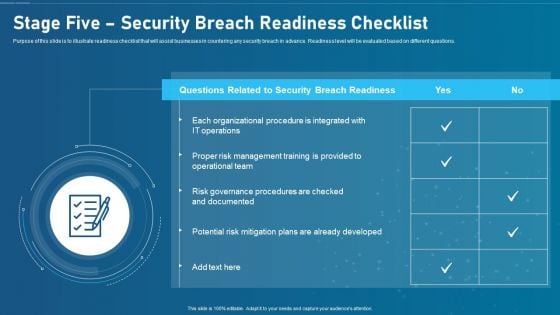
Artificial Intelligence Transformation Playbook Stage Five Security Breach Readiness Checklist Topics PDF
Purpose of this slide is to illustrate readiness checklist that will assist businesses in countering any security breach in advance. Readiness level will be evaluated based on different questions. This is a artificial intelligence transformation playbook stage five security breach readiness checklist topics pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like stage five security breach readiness checklist. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
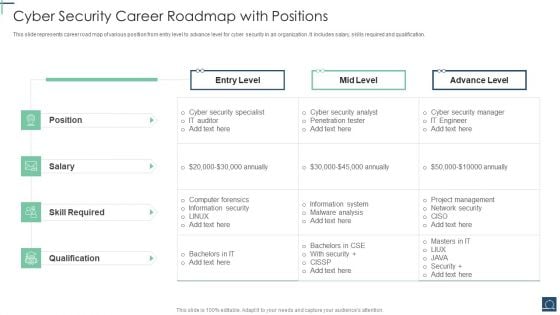
Cyber Security Career Roadmap With Positions Ppt PowerPoint Presentation File Portrait PDF
This slide represents career road map of various position from entry level to advance level for cyber security in an organization .It includes salary, skills required and qualification. Pitch your topic with ease and precision using this Cyber Security Career Roadmap With Positions Ppt PowerPoint Presentation File Portrait PDF. This layout presents information on Cyber Security Specialist, Skill Required, Advance Level. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Security And Surveillance Company Profile Executive Leadership And Management Team Demonstration PDF
This slide highlights the security company leadership and management team which includes president CEO, executive vice president of finance, EVP home security, chief administration officer. This is a Security And Surveillance Company Profile Executive Leadership And Management Team Demonstration PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Incentive Scheme, Referral Partners, Sales Strategy. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Major Saas Cloud Security Risk Summary Ppt PowerPoint Presentation File Guidelines PDF
The following slide illustrates some SaaS security threats to enhance security practices and eliminate them. It includes elements such as phishing, account takeovers, lack of transparency etc. Showcasing this set of slides titled Major Saas Cloud Security Risk Summary Ppt PowerPoint Presentation File Guidelines PDF. The topics addressed in these templates are Comprehending Risks, Phishing, Account Takeovers. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Multistep Process For Automating Cloud Security Operations Ppt Summary File Formats PDF
The following slide highlights four step process of cloud digitization of security systems. The various steps are container configure management, using infrastructure as code, automating asset tagging and vulnerability scanning where security analysts should implement automation. Persuade your audience using this Multistep Process For Automating Cloud Security Operations Ppt Summary File Formats PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Container Configure Management, Use Infrastructure Code, Automate Asset Tagging. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
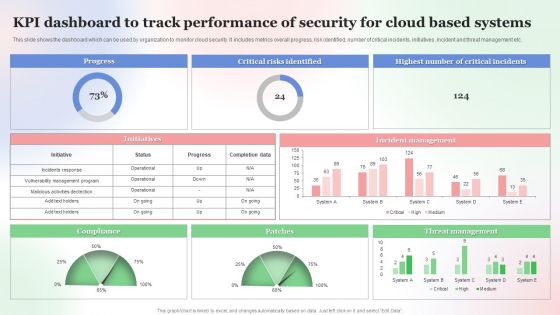
KPI Dashboard To Track Performance Of Security For Cloud Based Systems Clipart PDF
This slide shows the dashboard which can be used by organization to monitor cloud security. It includes metrics overall progress, risk identified, number of critical incidents, initiatives, incident and threat management etc. Showcasing this set of slides titled KPI Dashboard To Track Performance Of Security For Cloud Based Systems Clipart PDF. The topics addressed in these templates are Kpi Dashboard To Track, Performance Of Security, Cloud Based Systems . All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Table Of Contents For Cloud Computing Security IT Monitoring Ppt Styles Introduction PDF
Presenting table of contents for cloud computing security it monitoring ppt styles introduction pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like cloud security, business, implement, roadmap, data encryption. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Cybersecurity Dashboard For Threat Tracking In Electronic Information Security Ppt Ideas Graphics PDF
This slide depicts the dashboard for threat tracking in cyber security by covering monthly threat status, current risk status, threat based on the role, threats by owners, risk by threats, and threat report. Deliver an awe inspiring pitch with this creative cybersecurity dashboard for threat tracking in electronic information security ppt ideas graphics pdf bundle. Topics like dashboard for threat tracking in electronic information security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
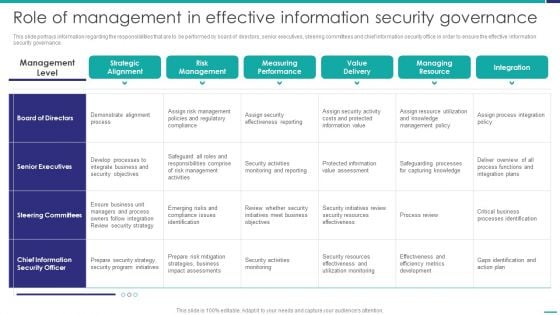
Role Of Management In Effective Governance Mobile Device Security Management Background PDF
This slide portrays information regarding the responsibilities that are to be performed by board of directors, senior executives, steering committees and chief information security office in order to ensure the effective information security governance. Deliver and pitch your topic in the best possible manner with this Role Of Management In Effective Governance Mobile Device Security Management Background PDF. Use them to share invaluable insights on Senior Executives, Steering Committees, Effectiveness Reporting and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Roles And Responsibilities Of Risk Management Team Information Security Risk Administration Designs PDF
This slide showcases responsibilities of major employees involved in information security risk management team. Key roles are - information security manager, risk management officer and chief information officer.Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Roles And Responsibilities Of Risk Management Team Information Security Risk Administration Designs PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
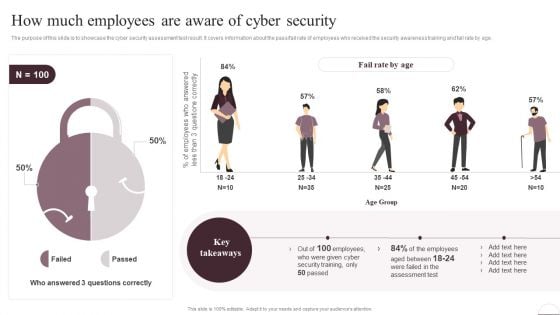
Prevention Of Information How Much Employees Are Aware Of Cyber Security Slides PDF
The purpose of this slide is to showcase the cyber security assessment test result. It covers information about the pass or fail rate of employees who received the security awareness training and fail rate by age. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Prevention Of Information How Much Employees Are Aware Of Cyber Security Slides PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates
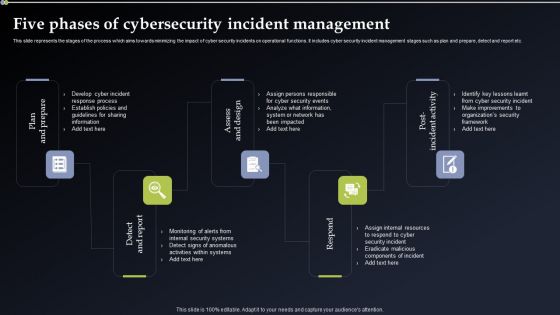
Deploying Cyber Security Incident Response Administration Five Phases Of Cybersecurity Incident Management Diagrams PDF
This slide represents the stages of the process which aims towards minimizing the impact of cyber security incidents on operational functions. It includes cyber security incident management stages such as plan and prepare, detect and report etc. There are so many reasons you need a Deploying Cyber Security Incident Response Administration Five Phases Of Cybersecurity Incident Management Diagrams PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
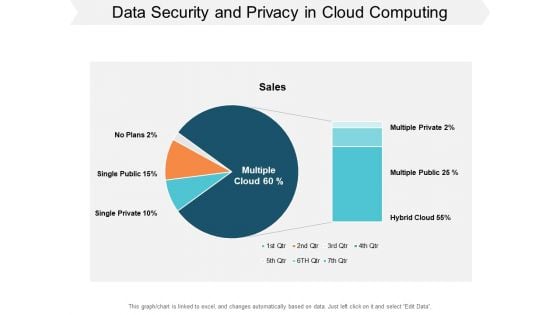
Data Security And Privacy In Cloud Computing Ppt PowerPoint Presentation Slides Graphic Tips
This is a data security and privacy in cloud computing ppt powerpoint presentation slides graphic tips. This is a two stage process. The stages in this process are cloud strategy, cloud planning, cloud management.
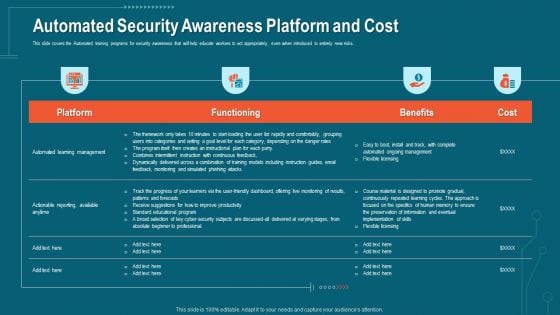
Companys Data Safety Recognition Automated Security Awareness Platform And Cost Demonstration PDF
This slide covers the Automated training programs for security awareness that will help educate workers to act appropriately, even when introduced to entirely new risks. Deliver an awe-inspiring pitch with this creative companys data safety recognition automated security awareness platform and cost demonstration pdf bundle. Topics like platform, functioning, benefits, cost can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
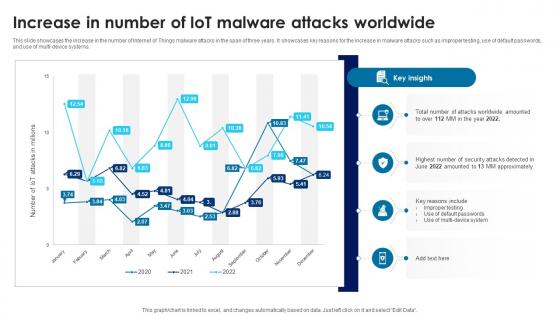
Building Trust With IoT Security Increase In Number Of IoT Malware Attacks Worldwide IoT SS V
This slide showcases the increase in the number of Internet of Things malware attacks in the span of three years. It showcases key reasons for the increase in malware attacks such as improper testing, use of default passwords, and use of multi-device systems. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Building Trust With IoT Security Increase In Number Of IoT Malware Attacks Worldwide IoT SS V to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide showcases the increase in the number of Internet of Things malware attacks in the span of three years. It showcases key reasons for the increase in malware attacks such as improper testing, use of default passwords, and use of multi-device systems.
Security Of Cloud Storage Virtual Cloud Network IT Ppt Icon Summary PDF
This slide depicts cloud storage security by describing the various security measures taken by the company to prevent information from malicious attacks while storing, transferring, and receiving it. Are you searching for a Security Of Cloud Storage Virtual Cloud Network IT Ppt Icon Summary PDF that is uncluttered, straightforward, and original It is easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, it is perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Security Of Cloud Storage Virtual Cloud Network IT Ppt Icon Summary PDF from Slidegeeks today.

Implementing Cybersecurity Awareness Program To Prevent Attacks Practices To Improve Security Awareness Level Slides PDF
The purpose of this slide is to outline different approaches used to enhance the cyber security awareness level. Creating security awareness program, conducting quarterly training session and implementing cyber security drills are some of the major approaches which are highlighted in the slide. Take your projects to the next level with our ultimate collection of Implementing Cybersecurity Awareness Program To Prevent Attacks Practices To Improve Security Awareness Level Slides PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest.

Implementing Cybersecurity Awareness Program To Prevent Attacks Roles And Responsibilities Of Cyber Security Team Information PDF
The purpose of this slide is to outline various roles and responsibilities of key stakeholders involve in the security awareness team. Chief information security officer CISO, cyber risk committee, cyber risk manager and security operations manager are some of the major stakeholders which are highlighted in the slide. Boost your pitch with our creative Implementing Cybersecurity Awareness Program To Prevent Attacks Roles And Responsibilities Of Cyber Security Team Information PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
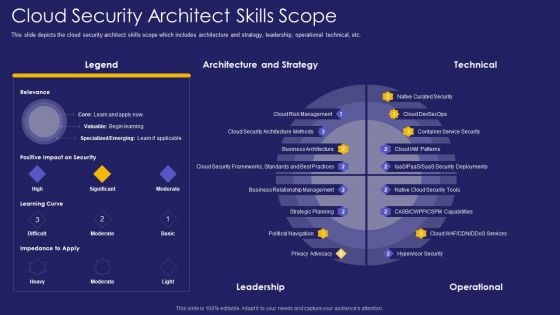
Role IT Team Digital Transformation Cloud Security Architect Skills Scope Rules PDF
This slide depicts the cloud security architect skills scope which includes architecture and strategy, leadership, operational technical, etc. Deliver an awe inspiring pitch with this creative role it team digital transformation cloud security architect skills scope rules pdf bundle. Topics like architecture, strategy, leadership can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

IT Security Hacker Altered Business Practices Due To Hacking Structure PDF
This slide represents that hackers forced the company to alter business practices followed by years and shut down online shopping stores in some regions.Deliver an awe inspiring pitch with this creative IT Security Hacker Altered Business Practices Due To Hacking Structure PDF bundle. Topics like Stored Information, Personal Information, Social Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
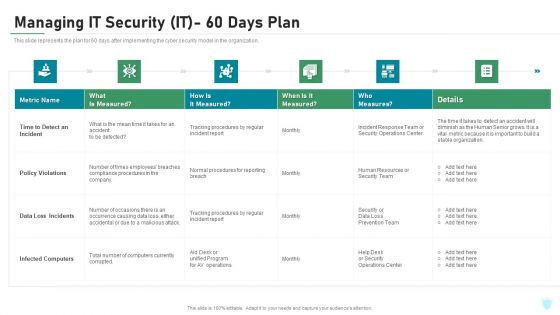
Managing IT Security IT 60 Days Plan Ppt Ideas Graphics PDF
This slide represents the plan for 60 days after implementing the cyber security model in the organization. Deliver an awe inspiring pitch with this creative managing it security it 60 days plan ppt ideas graphics pdf bundle. Topics like policy violations, infected computers, data loss incidents, time to detect an incident can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
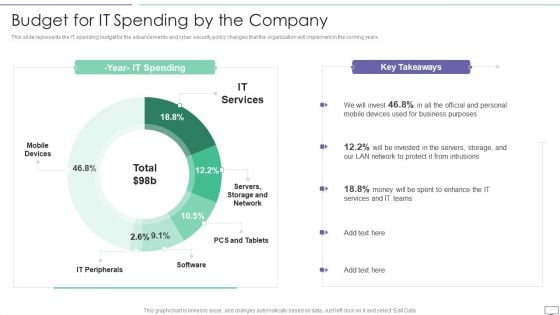
IT Security Hacker Budget For IT Spending By The Company Download PDF
This slide represents the IT spending budget for the advancements and cyber security policy changes that the organization will implement in the coming years.Deliver an awe inspiring pitch with this creative IT Security Hacker Budget For IT Spending By The Company Download PDF bundle. Topics like Business Purposes, Protect Intrusions, Services Teams can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Comparison Of Various Security Awareness Training Software Ppt Model Aids PDF
The purpose of this slide is to drawn comparison of multiple software which can be used to provide cyber security training to the key stakeholders. Information covered in this slide is related to phishing simulations, security reporting, individualized security training plan etc. Boost your pitch with our creative Comparison Of Various Security Awareness Training Software Ppt Model Aids PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
Six Steps Of System Development Service Delivery And Data Security Ppt PowerPoint Presentation Icon Slide Download
This is a six steps of system development service delivery and data security ppt powerpoint presentation icon slide download. This is a six stage process. The stages in this process are risk management, risk factors, risk variable.
Data Protection Security Controls Ppt PowerPoint Presentation File Designs Cpb Pdf
Presenting this set of slides with name data protection security controls ppt powerpoint presentation file designs cpb pdf. This is an editable Powerpoint five stages graphic that deals with topics like data protection security controls to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
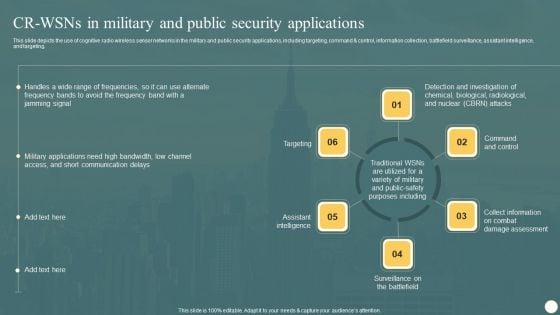
Cognitive Radio Network IT CR WSNS In Military And Public Security Applications Graphics PDF
This slide depicts the use of cognitive radio wireless sensor networks in the military and public security applications, including targeting, command and control, information collection, battlefield surveillance, assistant intelligence, and targeting. Presenting this PowerPoint presentation, titled Cognitive Radio Network IT CR WSNS In Military And Public Security Applications Graphics PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Cognitive Radio Network IT CR WSNS In Military And Public Security Applications Graphics PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Cognitive Radio Network IT CR WSNS In Military And Public Security Applications Graphics PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.

IT Development Company Pitch Deck Problems Faced By Companies Security Introduction PDF
This is a it development company pitch deck problems faced by companies security introduction pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like poor network security, backup issues, software concerns, qualified experience. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
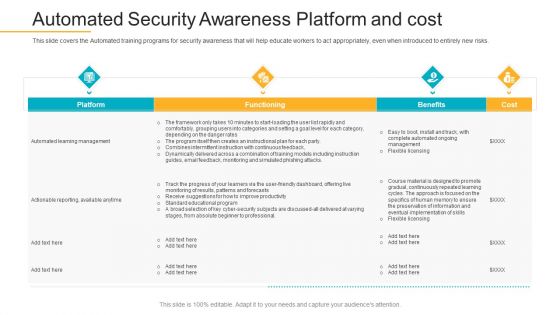
Data Breach Prevention Recognition Automated Security Awareness Platform And Cost Slides PDF
This slide covers the Automated training programs for security awareness that will help educate workers to act appropriately, even when introduced to entirely new risks. Deliver an awe-inspiring pitch with this creative data breach prevention recognition automated security awareness platform and cost slides pdf bundle. Topics like platform, functioning, benefits, cost can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cloud Information Security Software As A Service Saas Ppt Designs PDF
This slide describes the software-as-a-service responsibilities in the cloud security environment. It also shows the advantages and disadvantages of the SaaS model. Deliver and pitch your topic in the best possible manner with this Cloud Information Security Software As A Service Saas Ppt Designs PDF. Use them to share invaluable insights on Saas Service, Providers Crucial, Providers Server and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Introduction To Smart Locks Used For Enhancing Safety And Security Utilizing Smart Appliances IoT SS V
This slide provides an overview of the smart lock system used for increased security. The slide includes features of the smart lock security system that are it helps in real-time monitoring, improve connectivity, create entry codes and allow auto-lock settings. Get a simple yet stunning designed Introduction To Smart Locks Used For Enhancing Safety And Security Utilizing Smart Appliances IoT SS V. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Introduction To Smart Locks Used For Enhancing Safety And Security Utilizing Smart Appliances IoT SS V can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide provides an overview of the smart lock system used for increased security. The slide includes features of the smart lock security system that are it helps in real-time monitoring, improve connectivity, create entry codes and allow auto-lock settings.
Data Security Privacy Ppt PowerPoint Presentation Summary Vector Cpb Pdf Pdf
Presenting this set of slides with name data security privacy ppt powerpoint presentation summary vector cpb pdf pdf. This is an editable Powerpoint four stages graphic that deals with topics like data security privacy to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Elements Information Security Program Ppt PowerPoint Presentation Ideas Background Images Cpb Pdf
Presenting this set of slides with name elements information security program ppt powerpoint presentation ideas background images cpb pdf. This is an editable Powerpoint four stages graphic that deals with topics like elements information security program to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
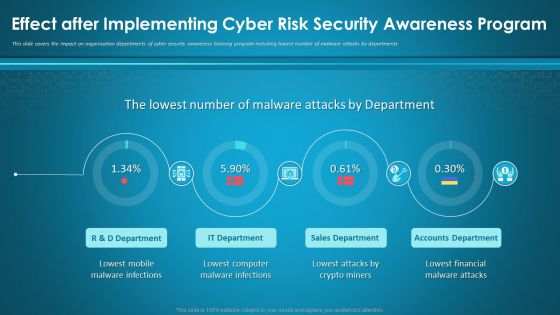
Effect After Implementing Cyber Risk Security Awareness Program Ppt Layouts Visuals PDF
This slide covers the impact on organization departments of cyber security awareness training program including lowest number of malware attacks by departments. Deliver an awe-inspiring pitch with this creative effect after implementing cyber risk security awareness program ppt layouts visuals pdf bundle. Topics like mobile, sales department, accounts department, financial, computer can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
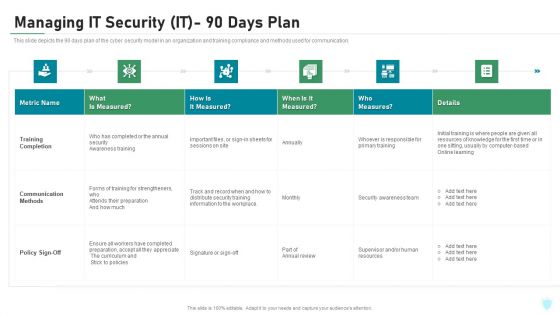
Managing IT Security IT 90 Days Plan Ppt Layouts Picture PDF
This slide depicts the 90 days plan of the cyber security model in an organization and training compliance and methods used for communication. Deliver and pitch your topic in the best possible manner with this managing it security it 90 days plan ppt layouts picture pdf. Use them to share invaluable insights on training completion, communication methods, policy sign off and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
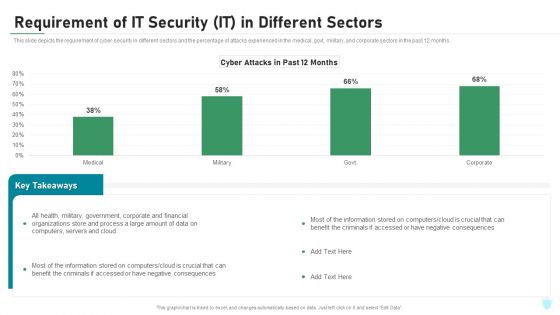
Requirement Of IT Security IT In Different Sectors Ppt Inspiration Deck PDF
This slide depicts the requirement of cyber security in different sectors and the percentage of attacks experienced in the medical, govt, military, and corporate sectors in the past 12 months. Deliver an awe inspiring pitch with this creative requirement of it security it in different sectors ppt inspiration deck pdf bundle. Topics like corporate, financial, organizations, process, computers, servers can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
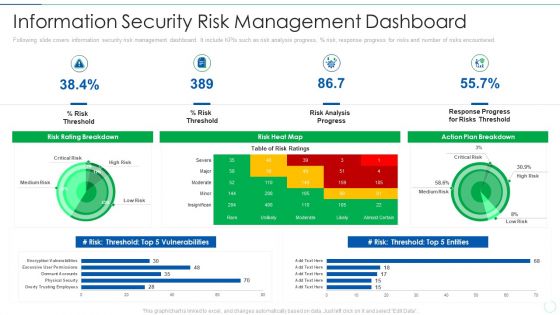
Effective IT Risk Management Process Information Security Risk Management Brochure PDF
Following slide covers information security risk management dashboard. It include KPIs such as risk analysis progress, percentage risk, response progress for risks and number of risks encountered. Deliver an awe inspiring pitch with this creative effective it risk management process information security risk management brochure pdf bundle. Topics like analysis, plan, risk, progress can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
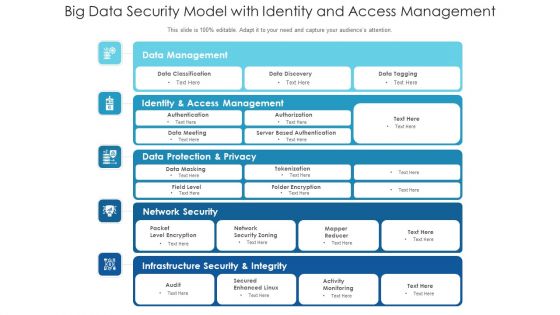
Big Data Security Model With Identity And Access Management Ppt PowerPoint Presentation Inspiration Good PDF
Pitch your topic with ease and precision using this big data security model with identity and access management ppt powerpoint presentation inspiration good pdf. This layout presents information on identity and access management, data protection and privacy, infrastructure security and integrity. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
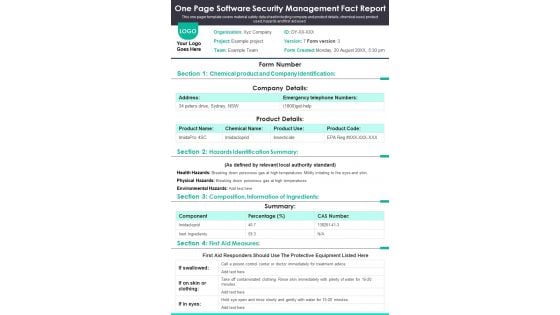
One Page Software Security Management Fact Report PDF Document PPT Template
Presenting you a fantastic One Page Software Security Management Fact Report PDF Document PPT Template. This one-pager document is crafted on hours of research and professional design efforts to ensure you have the best resource. It is completely editable and its design allow you to rehash its elements to suit your needs. Get this One Page Software Security Management Fact Report PDF Document PPT Template Download now.

Companys Data Safety Recognition The ROI Of Security Awareness Training Brochure PDF
This slide covers the security awareness rate of interest calculations including typical cyber risk management factor for a trained, cyber-conscious workforce. Deliver and pitch your topic in the best possible manner with this companys data safety recognition the roi of security awareness training brochure pdf. Use them to share invaluable insights on large organizations, small organizations and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
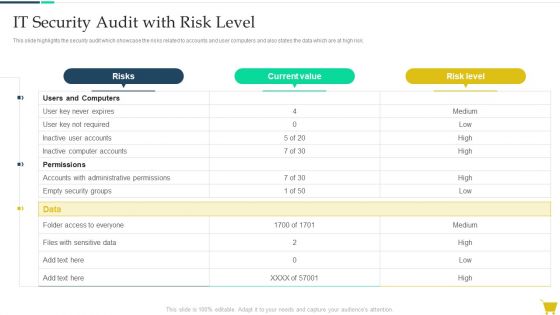
Complete Online Marketing Audit Guide IT Security Audit With Risk Level Clipart PDF
This slide highlights the security audit which showcase the risks related to accounts and user computers and also states the data which are at high risk. Deliver and pitch your topic in the best possible manner with this Complete Online Marketing Audit Guide IT Security Audit With Risk Level Clipart PDF. Use them to share invaluable insights on Risks, Current Value, Risk Level and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
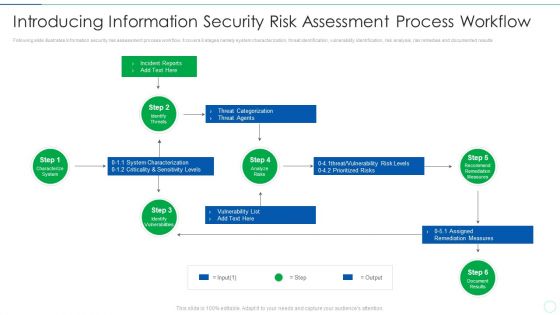
Effective IT Risk Management Process Introducing Information Security Risk Designs PDF
Following slide illustrates information security risk assessment process workflow. It covers 6 stages namely system characterization, threat identification, vulnerability identification, risk analysis, risk remedies and documented results Deliver an awe inspiring pitch with this creative effective it risk management process information security risk assessment formats pdf bundle. Topics like system, risks, measures can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Investment And Security Analysis Portfolio Management Ppt PowerPoint Presentation Complete Deck With Slides
This is a investment and security analysis portfolio management ppt powerpoint presentation complete deck with slides. This is a one stage process. The stages in this process are planning, business, strategy, management, marketing.

Comparative Analysis Email Security Network Gateway Ppt Outline Graphics Template PDF
The following slide showcases comparison of email security gateways along with features rating and price. Main gateways included are mimecast, ironscales, avanan and trustifi. Showcasing this set of slides titled Comparative Analysis Email Security Network Gateway Ppt Outline Graphics Template PDF. The topics addressed in these templates are Gateway Device Establishment, Establish Strong, Identity For Gateway. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

IoT Device Management Fundamentals IoT Device Authentication Methods To Ensure Data Security IoT Ss V
This slide showcases several IoT device authentication models for standardise and secure communication between machines. It included modules such as X.509 certificates, hardware security module, trusted platform module, and symmetric keys. Slidegeeks has constructed IoT Device Management Fundamentals IoT Device Authentication Methods To Ensure Data Security IoT SS V after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide showcases several IoT device authentication models for standardise and secure communication between machines. It included modules such as X.509 certificates, hardware security module, trusted platform module, and symmetric keys.
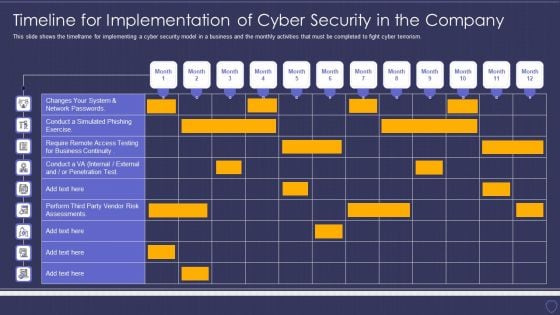
Global Cyber Terrorism Incidents On The Rise IT Timeline For Implementation Of Cyber Security Download PDF
This slide shows the timeframe for implementing a cyber security model in a business and the monthly activities that must be completed to fight cyber terrorism. Deliver and pitch your topic in the best possible manner with this global cyber terrorism incidents on the rise it timeline for implementation of cyber security download pdf. Use them to share invaluable insights on business, network, perform and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
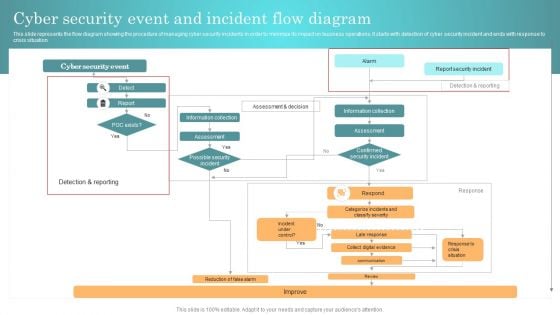
Incident Response Techniques Deployement Cyber Security Event And Incident Flow Diagram Structure PDF
This slide represents the flow diagram showing the procedure of managing cyber security incidents in order to minimize its impact on business operations. It starts with detection of cyber security incident and ends with response to crisis situation. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Incident Response Techniques Deployement Cyber Security Event And Incident Flow Diagram Structure PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Incident Response Techniques Deployement Cyber Security Event And Incident Flow Diagram Structure PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.
Guidelines For Business Data Security Vector Icon Ppt PowerPoint Presentation Gallery Layout Ideas PDF
Persuade your audience using this guidelines for business data security vector icon ppt powerpoint presentation gallery layout ideas pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including guidelines for business data security vector icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Data Management And Security With Contract File Vector Icon Ppt PowerPoint Presentation Gallery Display PDF
Persuade your audience using this data management and security with contract file vector icon ppt powerpoint presentation gallery display pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including data management and security with contract file vector icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Management Plan Framework For Data Security Ppt Inspiration Background Designs PDF
Persuade your audience using this management plan framework for data security ppt inspiration background designs pdf. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including procedures, data security, framework. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
3 Months Timeline Saas Data Security Ppt PowerPoint Presentation Gallery Master Slide PDF
Persuade your audience using this 3 months timeline saas data security ppt powerpoint presentation gallery master slide pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including 3 months timeline saas data security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
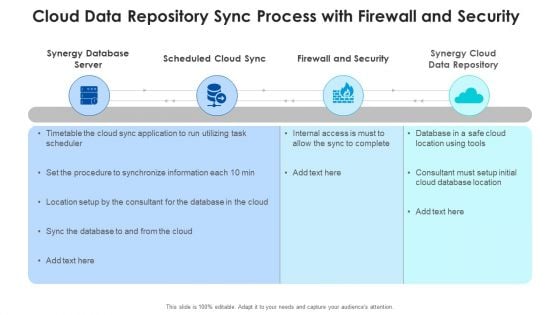
Cloud Data Repository Sync Process With Firewall And Security Brochure PDF
Presenting cloud data repository sync process with firewall and security brochure pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including synergy database server, scheduled cloud sync, firewall and security, synergy cloud data repository . This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Risk Management Model For Data Security System Management Checklist With Key Activities Guidelines PDF
Following slide displays system management checklist. It includes system management activities and frequency of performing them. Deliver an awe inspiring pitch with this creative Risk Management Model For Data Security System Management Checklist With Key Activities Guidelines PDF bundle. Topics like System Monitoring, Data Backup, Security Patches, Virus Scanning can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Business Intelligence With Data Governance And Security Ppt PowerPoint Presentation Infographics Example PDF
Pitch your topic with ease and precision using this business intelligence with data governance and security ppt powerpoint presentation infographics example pdf. This layout presents information on data governance, data discovery, data quality management, connected clouds, security. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.


 Continue with Email
Continue with Email

 Home
Home


































