Technology Security
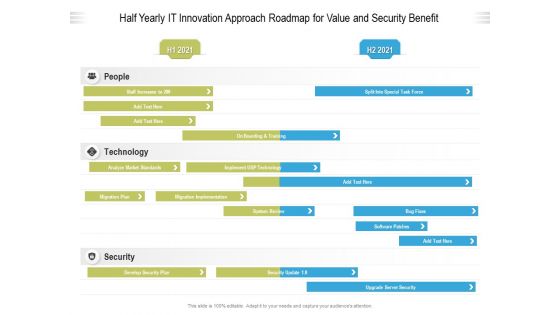
Half Yearly IT Innovation Approach Roadmap For Value And Security Benefit Professional
We present our half yearly it innovation approach roadmap for value and security benefit professional. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched half yearly it innovation approach roadmap for value and security benefit professional in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
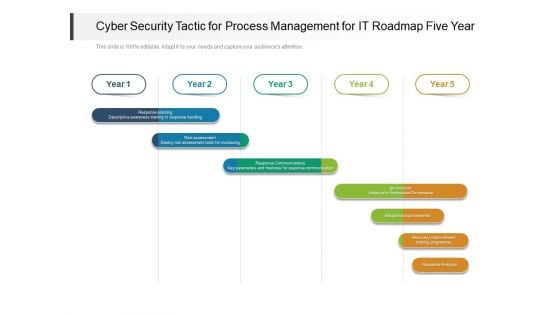
Cyber Security Tactic For Process Management For IT Roadmap Five Year Designs
We present our cyber security tactic for process management for it roadmap five year designs. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched cyber security tactic for process management for it roadmap five year designs in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
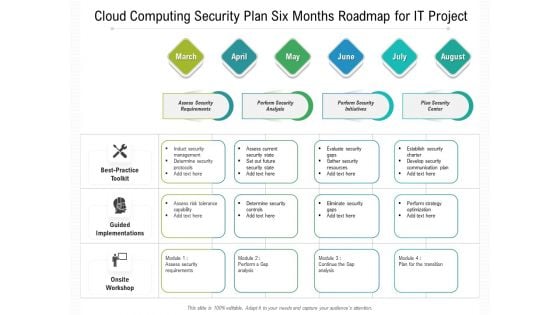
Cloud Computing Security Plan Six Months Roadmap For IT Project Template
We present our cloud computing security plan six months roadmap for it project template. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched cloud computing security plan six months roadmap for it project template in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Six Months Enterprise IT Automation Machinery Road Mapping With Security And Compliance Professional
We present our six months enterprise it automation machinery road mapping with security and compliance professional. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched six months enterprise it automation machinery road mapping with security and compliance professional in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Digitalization Of Operative Enterprises IT OT Convergence Security Objectives Challenges Catalysts And Benefits Download PDF
This slide covers objectives challenges catalysts and benefits of the security in IT or OT convergence and reduce systems cyberattack surface. This is a Digitalization Of Operative Enterprises IT OT Convergence Security Objectives Challenges Catalysts And Benefits Download PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Objectives, Challenges, Benefits. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
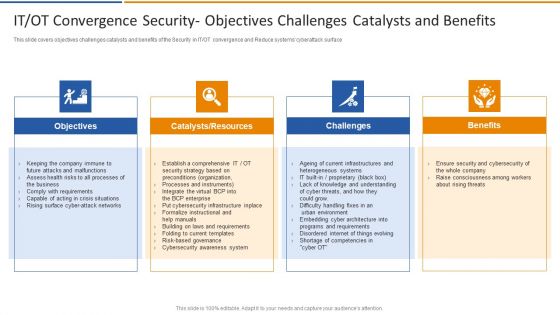
IT OT Convergence Security Objectives Challenges Smart Venture Digitial Transformation Designs PDF
This slide covers objectives challenges catalysts and benefits of the Security in IT or OT convergence and Reduce systems cyberattack surface. This is a IT OT Convergence Security Objectives Challenges Smart Venture Digitial Transformation Designs PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Objectives, Catalysts, Resources, Challenges, Benefits. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
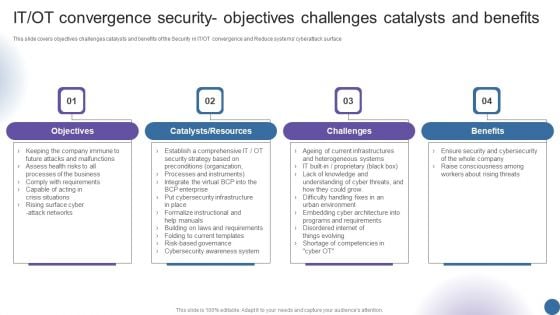
IT OT Convergence Security Objectives Challenges Managing Organizational Transformation Professional PDF
This slide covers objectives challenges catalysts and benefits of the Security in IT OT convergence and Reduce systems cyberattack surface. This is a IT OT Convergence Security Objectives Challenges Managing Organizational Transformation Professional PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Objectives, Catalysts Resources, Challenges, Benefits. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
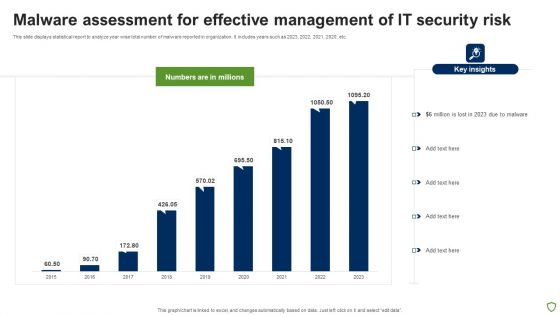
Malware Assessment For Effective Management Of IT Security Risk Portrait PDF
This slide displays statistical report to analyze year wise total number of malware reported in organization. It includes years such as 2023, 2022, 2021, 2020, etc. Showcasing this set of slides titled Malware Assessment For Effective Management Of IT Security Risk Portrait PDF. The topics addressed in these templates are Malware Assessment For Effective, Management IT Security Risk. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
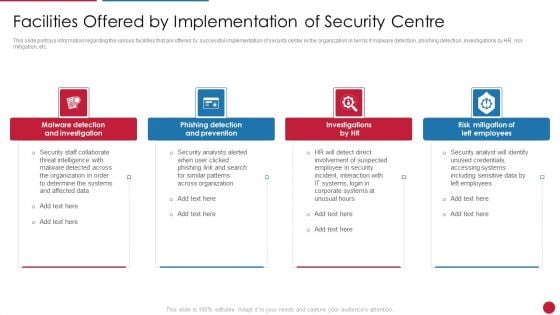
Facilitating IT Intelligence Architecture Facilities Offered By Implementation Of Security Centre Demonstration PDF
This slide portrays information regarding the various facilities that are offered by successful implementation of security center in the organization in terms if malware detection, phishing detection, investigations by HR, risk mitigation, etc. This is a Facilitating IT Intelligence Architecture Facilities Offered By Implementation Of Security Centre Demonstration PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Malware Detection And Investigation, Phishing Detection And Prevention, Risk Mitigation Of Left You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
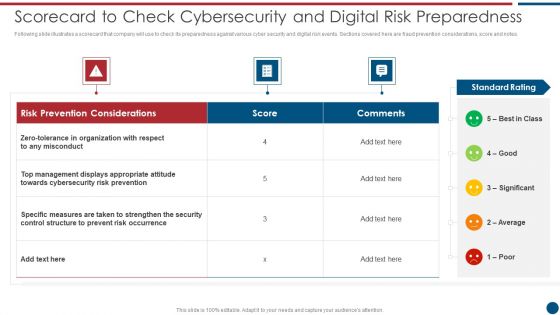
Risk Based Procedures To IT Security Scorecard To Check Cybersecurity And Digital Risk Preparedness Professional PDF
Following slide illustrates a scorecard that company will use to check its preparedness against various cyber security and digital risk events. Sections covered here are fraud prevention considerations, score and notes. Deliver and pitch your topic in the best possible manner with this Risk Based Procedures To IT Security Scorecard To Check Cybersecurity And Digital Risk Preparedness Professional PDF. Use them to share invaluable insights on Risk Prevention, Risk Prevention, Risk Occurrence and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
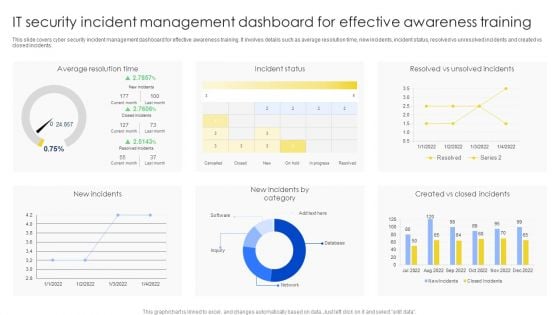
IT Security Incident Management Dashboard For Effective Awareness Training Pictures PDF
This slide covers cyber security incident management dashboard for effective awareness training. It involves details such as average resolution time, new incidents, incident status, resolved vs unresolved incidents and created vs closed incidents. Showcasing this set of slides titled IT Security Incident Management Dashboard For Effective Awareness Training Pictures PDF. The topics addressed in these templates are Average Resolution Time, Incident Status, New Incidents. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

IT Policies And Procedures Information Security Policy For Employees Download PDF
Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our IT Policies And Procedures Information Security Policy For Employees Download PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into IT Policies And Procedures Information Security Policy For Employees Download PDF.
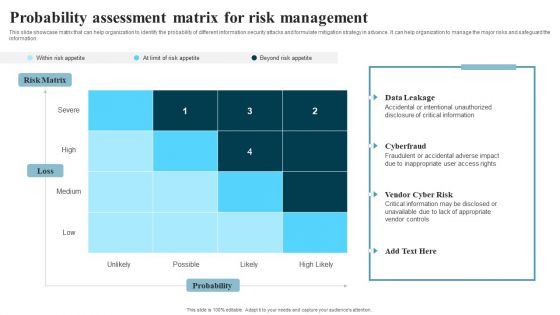
Developing IT Security Strategy Probability Assessment Matrix For Risk Management Formats PDF
This slide showcase matrix that can help organization to identify the probability of different information security attacks and formulate mitigation strategy in advance. It can help organization to manage the major risks and safeguard the information. Make sure to capture your audiences attention in your business displays with our gratis customizable Developing IT Security Strategy Probability Assessment Matrix For Risk Management Formats PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
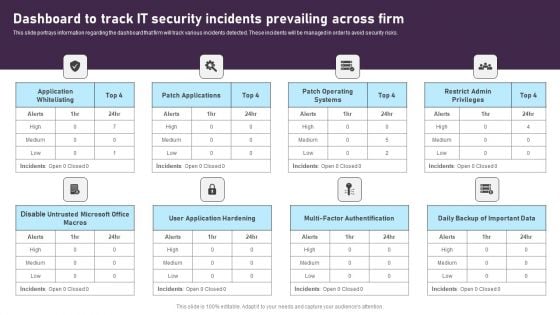
Dashboard To Track IT Security Incidents Prevailing Across Firm Inspiration PDF
This slide portrays information regarding the dashboard that firm will track various incidents detected. These incidents will be managed in order to avoid security risks. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Dashboard To Track IT Security Incidents Prevailing Across Firm Inspiration PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
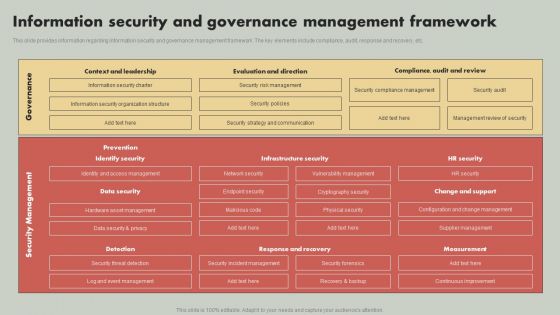
IT Reducing Costs And Management Tips Information Security And Governance Management Framework Demonstration PDF
This slide provides information regarding information security and governance management framework. The key elements include compliance, audit, response and recovery, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate IT Reducing Costs And Management Tips Information Security And Governance Management Framework Demonstration PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Artificial Intelligence For IT Operations Playbook Stage Five Security Breach Readiness Checklist Rules PDF
Purpose of this slide is to illustrate readiness checklist that will assist businesses in countering any security breach in advance. Readiness level will be evaluated based on different questions.Presenting Artificial Intelligence For IT Operations Playbook Stage Five Security Breach Readiness Checklist Rules PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Management Training, Potential Mitigation, Already Developed In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT System Risk Management Guide Prioritized Cyber Security Threats With Risk Mitigation Plan Ideas PDF
This slide highlights the cyber security threats with key risks and their mitigation plan and owner with risk reduction timeline. Welcome to our selection of the IT System Risk Management Guide Prioritized Cyber Security Threats With Risk Mitigation Plan Ideas PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.
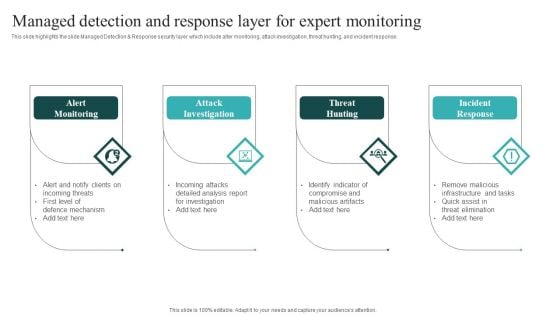
IT Security Automation Systems Guide Managed Detection And Response Layer For Expert Monitoring Download PDF
This slide highlights the slide Managed Detection and Response security layer which include alter monitoring, attack investigation, threat hunting, and incident response. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. IT Security Automation Systems Guide Managed Detection And Response Layer For Expert Monitoring Download PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
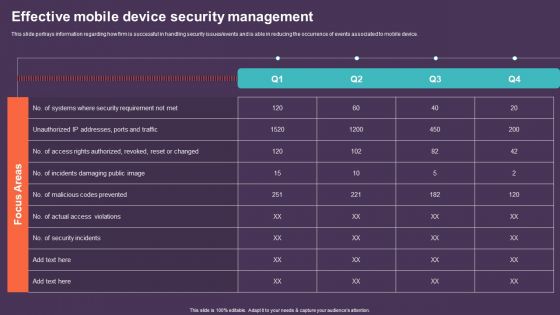
Mobile Device Management For Improving IT Operations Effective Mobile Device Security Mockup PDF
This slide portrays information regarding how firm is successful in handling security issues or events and is able in reducing the occurrence of events associated to mobile device. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Mobile Device Management For Improving IT Operations Effective Mobile Device Security Mockup PDF from Slidegeeks and deliver a wonderful presentation.

Strategic FM Services Security And Guarding Facility Management Services Demonstration PDF
This slide highlights the guarding and security services offered by the company which includes electronic surveillance, guarding and patrolling, fire safety and event safety services. Are you searching for a Strategic FM Services Security And Guarding Facility Management Services Demonstration PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Strategic FM Services Security And Guarding Facility Management Services Demonstration PDF from Slidegeeks today.
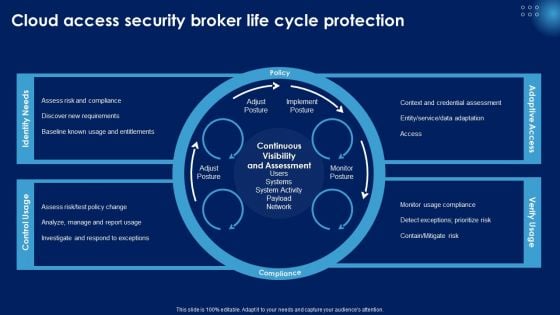
Cloud Access Security Broker Life Cycle Protection Ppt PowerPoint Presentation File Diagrams PDF
Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Cloud Access Security Broker Life Cycle Protection Ppt PowerPoint Presentation File Diagrams PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Cloud Access Security Broker Life Cycle Protection Ppt PowerPoint Presentation File Diagrams PDF.
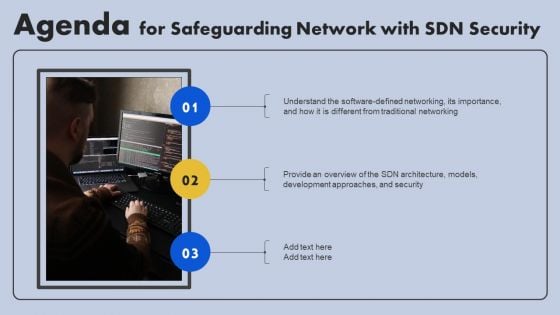
Agenda For Safeguarding Network With SDN Security Ppt Layouts Information PDF
If you are looking for a format to display your unique thoughts, then the professionally designed Agenda For Safeguarding Network With SDN Security Ppt Layouts Information PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Agenda For Safeguarding Network With SDN Security Ppt Layouts Information PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Workplace Facility Management Services Company Security And Guarding Facility Management Services Portrait PDF
This slide highlights the guarding and security services offered by the company which includes electronic surveillance, guarding and patrolling, fire safety and event safety services. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Workplace Facility Management Services Company Security And Guarding Facility Management Services Portrait PDF can be your best option for delivering a presentation. Represent everything in detail using Workplace Facility Management Services Company Security And Guarding Facility Management Services Portrait PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
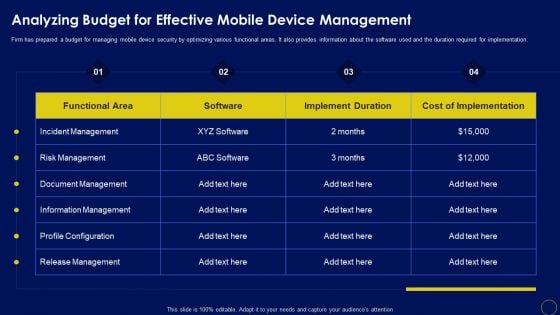
Analyzing Budget For Effective Mobile Device Management Business Mobile Device Security Clipart PDF
Firm has prepared a budget for managing mobile device security by optimizing various functional areas. It also provides information about the software used and the duration required for implementation. Explore a selection of the finest Analyzing Budget For Effective Mobile Device Management Business Mobile Device Security Clipart PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Analyzing Budget For Effective Mobile Device Management Business Mobile Device Security Clipart PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
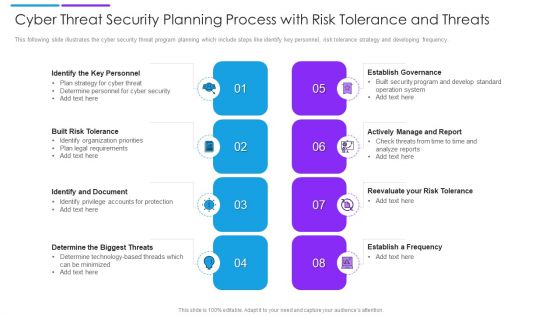
Cyber Threat Security Planning Process With Risk Tolerance And Threats Formats PDF
This following slide illustrates the cyber security threat program planning which include steps like identify key personnel, risk tolerance strategy and developing frequency. Persuade your audience using this cyber threat security planning process with risk tolerance and threats formats pdf. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including establish governance, actively manage and report, built risk tolerance. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
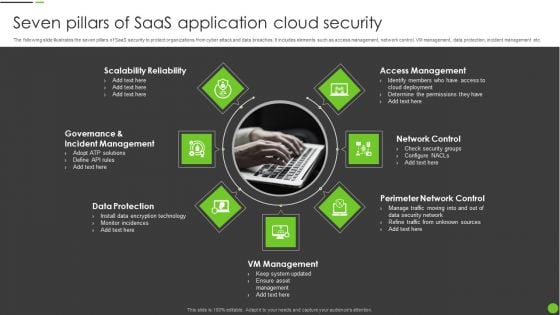
Seven Pillars Of Saas Application Cloud Security Ppt PowerPoint Presentation File Tips PDF
The following slide illustrates the seven pillars of SaaS security to protect organizations from cyber attack and data breaches. It includes elements such as access management, network control, VM management, data protection, incident management etc. Presenting Seven Pillars Of Saas Application Cloud Security Ppt PowerPoint Presentation File Tips PDF to dispense important information. This template comprises seven stages. It also presents valuable insights into the topics including VM Management, Data Protection, Network Control, Perimeter Network Control. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Security Use Cases Of Web Application Firewall Deployment WAF Platform Ideas PDF
This slide represents the security use cases of web application firewall and how it would stop cyberattacks such as DDoS attacks, malicious bot abuse, and customer data breaches. This is a Security Use Cases Of Web Application Firewall Deployment WAF Platform Ideas PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Mitigate Ddos Attacks, Prevent Customer Data Breach, Block Malicious Bot Abuse. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
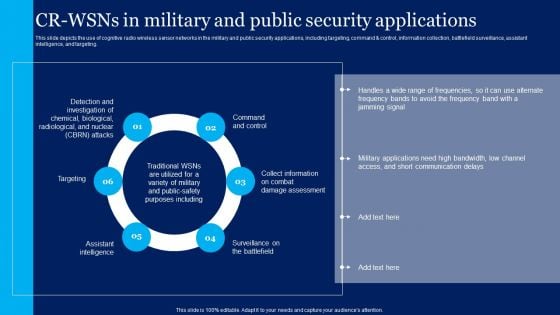
Cognitive Sensor Network CR Wsns In Military And Public Security Applications Template PDF
This slide depicts the use of cognitive radio wireless sensor networks in the military and public security applications, including targeting, command and control, information collection, battlefield surveillance, assistant intelligence, and targeting. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Cognitive Sensor Network CR Wsns In Military And Public Security Applications Template PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Cognitive Sensor Network CR Wsns In Military And Public Security Applications Template PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.
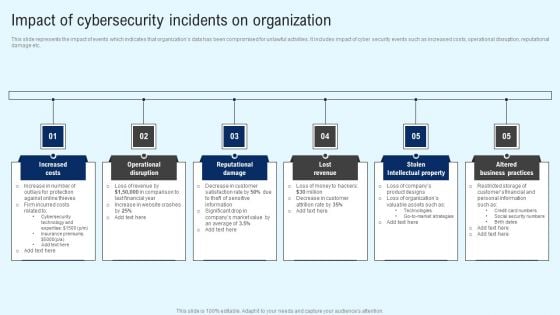
Implementing Cyber Security Incident Impact Of Cybersecurity Incidents On Organization Graphics PDF
This slide represents the impact of events which indicates that organizations data has been compromised for unlawful activities. It includes impact of cyber security events such as increased costs, operational disruption, reputational damage etc. Get a simple yet stunning designed Implementing Cyber Security Incident Impact Of Cybersecurity Incidents On Organization Graphics PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Implementing Cyber Security Incident Impact Of Cybersecurity Incidents On Organization Graphics PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Info Security Cyber Safety Tips Protection Against Cyberattacks Ppt PowerPoint Presentation Gallery Designs Download PDF
This slide represents various tips or procedures that can be followed to prevent an organizations cyber security from cyberattacks or cybercriminals. This is a info security cyber safety tips protection against cyberattacks ppt powerpoint presentation gallery designs download pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like protect the network, email attachment, time interval. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
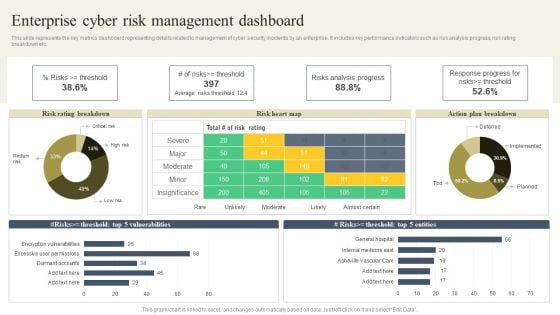
CYBER Security Breache Response Strategy Enterprise Cyber Risk Management Dashboard Summary PDF
This slide represents the key metrics dashboard representing details related to management of cyber security incidents by an enterprise. It includes key performance indicators such as risk analysis progress, risk rating breakdown etc. Are you searching for a CYBER Security Breache Response Strategy Enterprise Cyber Risk Management Dashboard Summary PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal. With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download CYBER Security Breache Response Strategy Enterprise Cyber Risk Management Dashboard Summary PDF from Slidegeeks today.
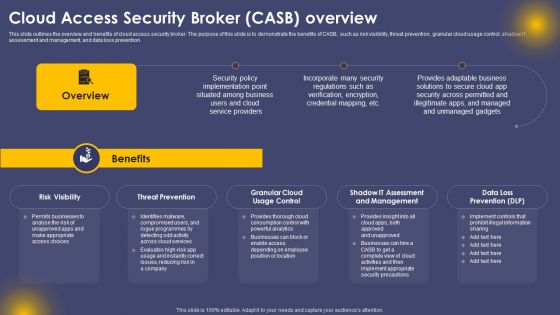
Cloud Access Security Broker Casb Overview Ppt Professional Design Inspiration PDF
This slide outlines the overview and benefits of cloud access security broker. The purpose of this slide is to demonstrate the benefits of CASB, such as risk visibility, threat prevention, granular cloud usage control, shadow IT assessment and management, and data loss prevention. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Cloud Access Security Broker Casb Overview Ppt Professional Design Inspiration PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Cloud Access Security Broker Casb Overview Ppt Professional Design Inspiration PDF today and make your presentation stand out from the rest.
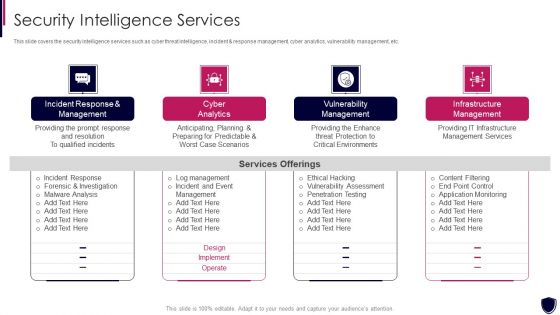
Enhancing Cyber Safety With Vulnerability Administration Security Intelligence Services Portrait PDF
This slide covers the security intelligence services such as cyber threat intelligence, incident and response management, cyber analytics, vulnerability management, etc. Presenting enhancing cyber safety with vulnerability administration security intelligence services portrait pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like incident response and management, cyber analytics, vulnerability management, infrastructure management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
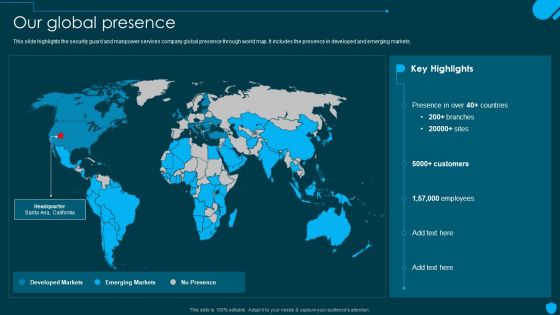
Security And Human Resource Services Business Profile Our Global Presence Graphics PDF
This slide highlights the security guard and manpower services company global presence through world map. It includes the presence in developed and emerging markets. This Security And Human Resource Services Business Profile Our Global Presence Graphics PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Security And Human Resource Services Business Profile Our Global Presence Graphics PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, dont wait, grab the presentation templates today.

Security And Human Resource Services Business Profile Staff Recruiting Criteria Graphics PDF
This slide highlights the security guard company staff recruiting criteria which includes age, medical category, height, records verification with authorized training centre. Are you searching for a Security And Human Resource Services Business Profile Staff Recruiting Criteria Graphics PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort youve put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Security And Human Resource Services Business Profile Staff Recruiting Criteria Graphics PDF from Slidegeeks today.

Estimated Impact Of Information Security Risk Management Plan Cybersecurity Risk Assessment Rules PDF
This slide showcases capabilities of organization regarding information and data security after risk management plan. Its key component are risk management functions, required standard rating and actual standard rating. Explore a selection of the finest Estimated Impact Of Information Security Risk Management Plan Cybersecurity Risk Assessment Rules PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Estimated Impact Of Information Security Risk Management Plan Cybersecurity Risk Assessment Rules PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
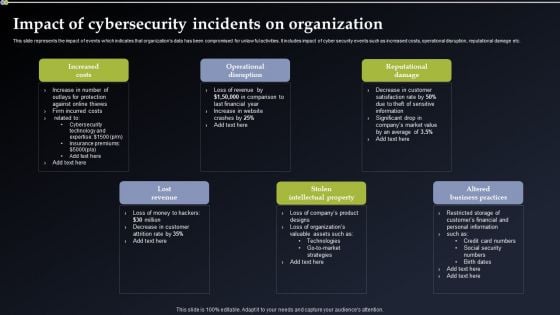
Deploying Cyber Security Incident Response Administration Impact Of Cybersecurity Incidents On Organization Microsoft PDF
This slide represents the impact of events which indicates that organizations data has been compromised for unlawful activities. It includes impact of cyber security events such as increased costs, operational disruption, reputational damage etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Deploying Cyber Security Incident Response Administration Impact Of Cybersecurity Incidents On Organization Microsoft PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Deploying Cyber Security Incident Response Administration Impact Of Cybersecurity Incidents On Organization Microsoft PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
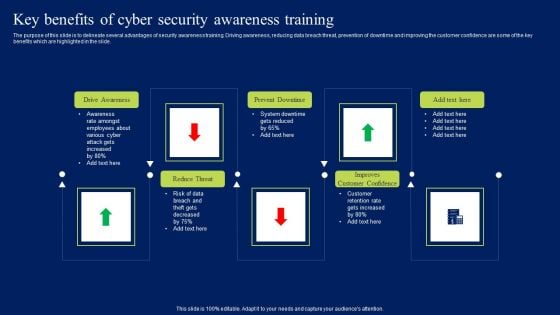
Key Benefits Of Cyber Security Awareness Training Ppt Model Mockup PDF
The purpose of this slide is to delineate several advantages of security awareness training. Driving awareness, reducing data breach threat, prevention of downtime and improving the customer confidence are some of the key benefits which are highlighted in the slide. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Key Benefits Of Cyber Security Awareness Training Ppt Model Mockup PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Key Benefits Of Cyber Security Awareness Training Ppt Model Mockup PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers
Deploying Cyber Security Incident Response Administration Enterprise Cyber Risk Management Dashboard Icons PDF
This slide represents the key metrics dashboard representing details related to management of cyber security incidents by an enterprise. It includes key performance indicators such as risk analysis progress, risk rating breakdown etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Deploying Cyber Security Incident Response Administration Enterprise Cyber Risk Management Dashboard Icons PDF can be your best option for delivering a presentation. Represent everything in detail using Deploying Cyber Security Incident Response Administration Enterprise Cyber Risk Management Dashboard Icons PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Shared Responsibility Chart For Saas Cloud Security Services Ppt PowerPoint Presentation File Outline PDF
The following slide highlights the responsibility chart for best application security services. It includes responsibilities such as data categorization and reporting, network control, end point safety etc. Showcasing this set of slides titled Shared Responsibility Chart For Saas Cloud Security Services Ppt PowerPoint Presentation File Outline PDF. The topics addressed in these templates are Application Level Controls, Cloud Customer, Data Categorization. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Security And Human Resource Services Business Profile Employees Rules And Regulations Clipart PDF
This slide highlights the security guard company rules and regulations which showcases In and out time, note visitor name, and wear uniform at working hours. If you are looking for a format to display your unique thoughts, then the professionally designed Security And Human Resource Services Business Profile Employees Rules And Regulations Clipart PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Security And Human Resource Services Business Profile Employees Rules And Regulations Clipart PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Security And Human Resource Services Business Profile Executive Leadership And Management Sample PDF
This slide highlights the security guard company management team which includes companys chairman and MD, head of security operations, training, strategic growth and site. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Security And Human Resource Services Business Profile Executive Leadership And Management Sample PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Prevention Of Information Key Benefits Of Cyber Security Awareness Training Inspiration PDF
The purpose of this slide is to delineate several advantages of security awareness training. Driving awareness, reducing data breach threat, prevention of downtime and improving the customer confidence are some of the key benefits which are highlighted in the slide. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Prevention Of Information Key Benefits Of Cyber Security Awareness Training Inspiration PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Prevention Of Information Key Benefits Of Cyber Security Awareness Training Inspiration PDF

Key To Money Savings Security PowerPoint Templates Ppt Backgrounds For Slides 1212
We present our Key To Money Savings Security PowerPoint Templates PPT Backgrounds For Slides 1212.Download and present our Money PowerPoint Templates because they will help you to organise the logic of your views. Download our Finance PowerPoint Templates because you envisage some areas of difficulty in the near future. The overall financial situation could be a source of worry. Download our Business PowerPoint Templates because it will demonstrate the strength of character under severe stress. Shine the torch ahead and bring the light to shine on all. Download our Services PowerPoint Templates because you understand the illness and its causes. Download our Marketing PowerPoint Templates because networking is an imperative in todays world. You need to access the views of others. Similarly you need to give access to them of your abilities.Use these PowerPoint slides for presentations relating to Financial money saveing security, money, business, marketing, services, finance . The prominent colors used in the PowerPoint template are Blue, Blue light, Yellow. We assure you our Key To Money Savings Security PowerPoint Templates PPT Backgrounds For Slides 1212 are Wonderful. Customers tell us our marketing PowerPoint templates and PPT Slides are readymade to fit into any presentation structure. You can be sure our Key To Money Savings Security PowerPoint Templates PPT Backgrounds For Slides 1212 are designed by a team of presentation professionals. People tell us our money PowerPoint templates and PPT Slides will get their audience's attention. Presenters tell us our Key To Money Savings Security PowerPoint Templates PPT Backgrounds For Slides 1212 are effectively colour coded to prioritise your plans They automatically highlight the sequence of events you desire. People tell us our services PowerPoint templates and PPT Slides are Amazing. Anything will not do for our Key To Money Savings Security PowerPoint Templates Ppt Backgrounds For Slides 1212. They are the answer for exacting demands.
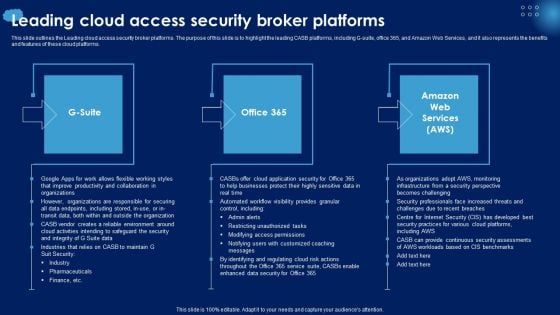
Leading Cloud Access Security Broker Platforms Ppt PowerPoint Presentation File Styles PDF
This slide outlines the Leading cloud access security broker platforms. The purpose of this slide is to highlight the leading CASB platforms, including G-suite, office 365, and Amazon Web Services, and it also represents the benefits and features of these cloud platforms. Are you searching for a Leading Cloud Access Security Broker Platforms Ppt PowerPoint Presentation File Styles PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Leading Cloud Access Security Broker Platforms Ppt PowerPoint Presentation File Styles PDF from Slidegeeks today.
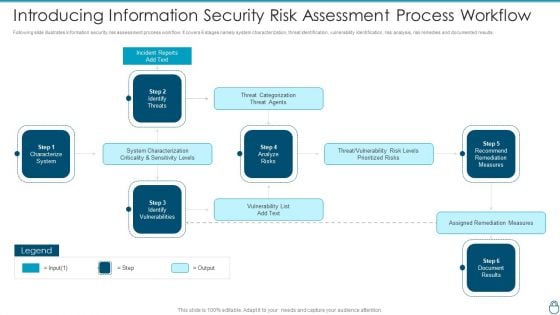
Cybersecurity Risk Administration Plan Introducing Information Security Risk Assessment Process Workflow Slides PDF
Following slide illustrates information security risk assessment process workflow. It covers 6 stages namely system characterization, threat identification, vulnerability identification, risk analysis, risk remedies and documented results.Deliver and pitch your topic in the best possible manner with this Cybersecurity Risk Administration Plan Introducing Information Security Risk Assessment Process Workflow Slides PDF Use them to share invaluable insights on System Characterization, Threat Categorization, Recommend Remediation Measures and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cloud Information Security Phase 3 Respond To Cloud Protection Issues Ppt Layouts Influencers PDF
This slide represents phase 3 of cloud security, such as respond to cloud protection issues. It includes an advanced authentication process, manages cloud access standards when new services come up, and eliminates malware from cloud services. Deliver and pitch your topic in the best possible manner with this Cloud Information Security Phase 3 Respond To Cloud Protection Issues Ppt Layouts Influencers PDF. Use them to share invaluable insights on Advanced Authentication, Cloud Access, Eliminate Malware and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cloud Security Assessment Phase 3 Respond To Cloud Protection Issues Topics PDF
This slide represents phase 3 of cloud security, such as respond to cloud protection issues. It includes an advanced authentication process, manages cloud access standards when new services come up, and eliminates malware from cloud services.Deliver and pitch your topic in the best possible manner with this Cloud Security Assessment Phase 3 Respond To Cloud Protection Issues Topics PDF Use them to share invaluable insights on Authentication Process, Access Standards, Eliminate Malware and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
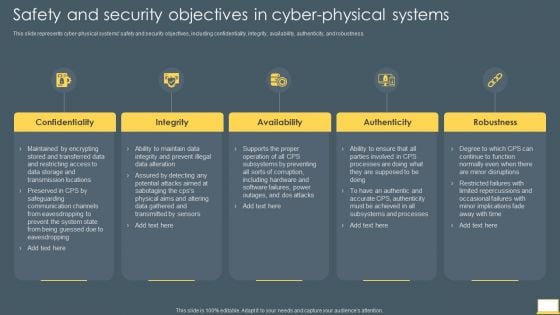
Cyber Intelligent Computing System Safety And Security Objectives In Cyber Physical Systems Ideas PDF
This slide represents cyber physical systems safety and security objectives, including confidentiality, integrity, availability, authenticity, and robustness. Presenting Cyber Intelligent Computing System Safety And Security Objectives In Cyber Physical Systems Ideas PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Availability, Authenticity, Robustness, Integrity. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
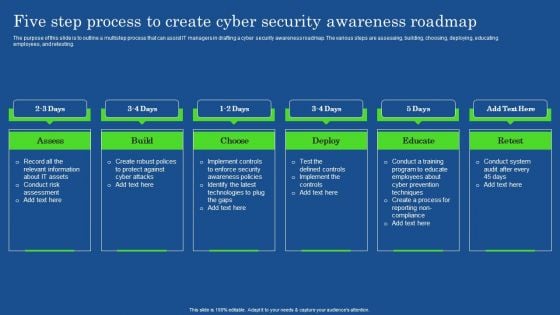
Five Step Process To Create Cyber Security Awareness Roadmap Microsoft PDF
The purpose of this slide is to outline a multistep process that can assist IT managers in drafting a cyber security awareness roadmap. The various steps are assessing, building, choosing, deploying, educating employees, and retesting. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Five Step Process To Create Cyber Security Awareness Roadmap Microsoft PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Five Step Process To Create Cyber Security Awareness Roadmap Microsoft PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers
Executing Security Management Program To Mitigate Threats And Safeguard Confidential Organizational Data Icons Slide Inspiration PDF
Introducing our well designed Executing security management program to mitigate threats and safeguard confidential organizational data icons slide inspiration pdf set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.
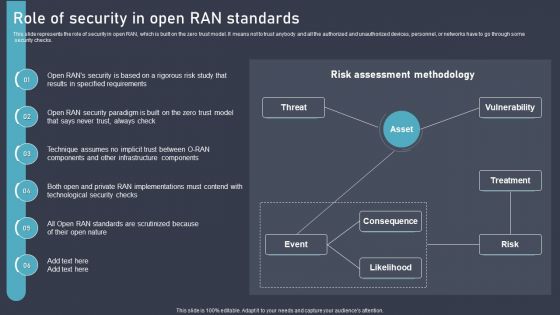
O RAN Architecture Role Of Security In Open RAN Standards Ppt Infographics Topics PDF
This slide represents the role of security in open RAN, which is built on the zero trust model. It means not to trust anybody and all the authorized and unauthorized devices, personnel, or networks have to go through some security checks. Retrieve professionally designed O RAN Architecture Role Of Security In Open RAN Standards Ppt Infographics Topics PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You dont have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Key Security Considerations For 5G For Threat Handling 5G Network Architecture Instructions Diagrams PDF
This slide provides details regarding key security considerations associated to 5G in order to handle threats such as data breach, denial of service, unauthorized activities, etc. Deliver and pitch your topic in the best possible manner with this Key Security Considerations For 5G For Threat Handling 5G Network Architecture Instructions Diagrams PDF. Use them to share invaluable insights on Nodes Authentication, Rule Consistency, Policy Enforcement and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
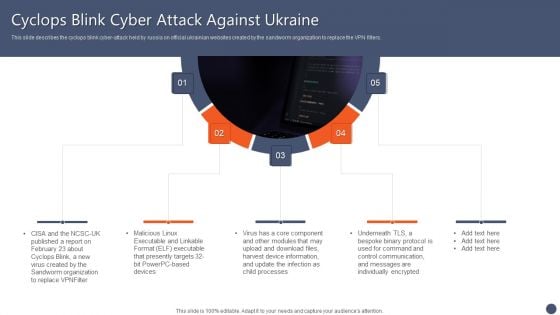
Series Of Cyber Security Attacks Against Ukraine 2022 Cyclops Blink Cyber Attack Against Ukraine Sample PDF
This slide describes the cyclops blink cyber attack held by russia on official ukrainian websites created by the sandworm organization to replace the VPN filters. Get a simple yet stunning designed Series Of Cyber Security Attacks Series Of Cyber Security Attacks Against Ukraine 2022 Cyclops Blink Cyber Attack Against Ukraine Sample PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Series Of Cyber Security Attacks Against Ukraine 2022 Cyclops Blink Cyber Attack Against Ukraine Sample PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
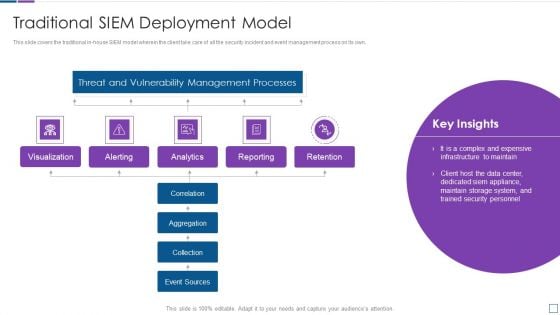
Real Time Assessment Of Security Threats Traditional SIEM Deployment Model Background PDF
This slide covers the traditional in house SIEM model wherein the client take care of all the security incident and event management process on its own. Deliver and pitch your topic in the best possible manner with this real time assessment of security threats traditional siem deployment model background pdf. Use them to share invaluable insights on threat and vulnerability management processes, visualization, retention, analytics and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Real Time Assessment Of Security Threats Cloud SIEM Model Icons PDF
This slide covers the cloud SIEM and self managed model wherein the client take care of mostly all the security incident and event management process on its own except aggregation and collection. Deliver and pitch your topic in the best possible manner with this real time assessment of security threats cloud siem model icons pdf. Use them to share invaluable insights on threat and vulnerability management processes, aggregation, collection, correlation and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
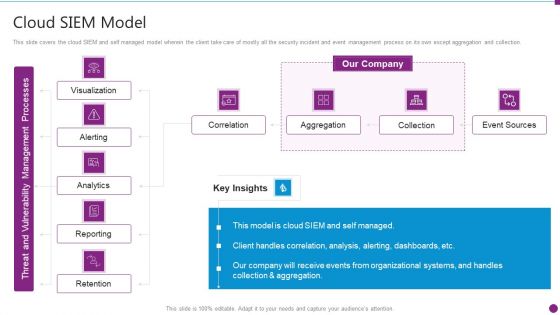
Security Information And Event Management Strategies For Financial Audit And Compliance Cloud SIEM Model Diagrams PDF
This slide covers the cloud SIEM and self managed model wherein the client take care of mostly all the security incident and event management process on its own except aggregation and collection. Deliver and pitch your topic in the best possible manner with this security information and event management strategies for financial audit and compliance cloud siem model diagrams pdf. Use them to share invaluable insights on visualization, alerting, analytics, reporting, retention and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
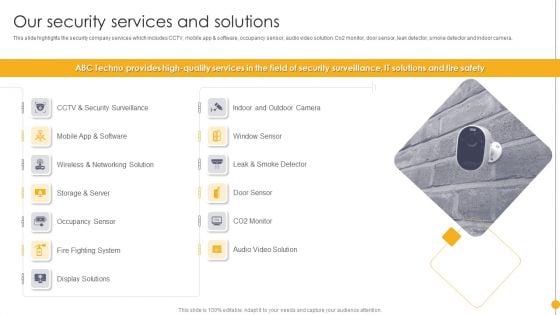
Portable Home Safety Systems Company Profile Our Security Services And Solutions Information PDF
This slide highlights the security company services which includes CCTV, mobile app and software, occupancy sensor, audio video solution. Co2 monitor, door sensor, leak detector, smoke detector and indoor camera. Deliver and pitch your topic in the best possible manner with this Portable Home Safety Systems Company Profile Our Security Services And Solutions Information PDF. Use them to share invaluable insights on Window Sensor, Door Sensor, Occupancy Sensor, Display Solutions and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
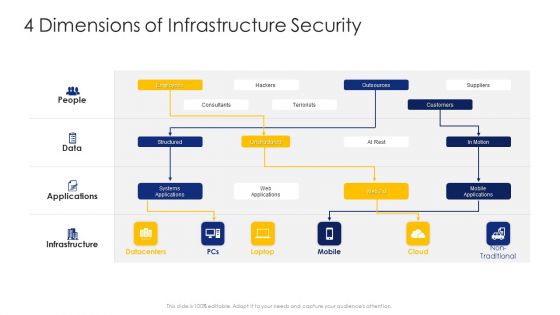
Construction Engineering And Industrial Facility Management 4 Dimensions Of Infrastructure Security Graphics PDF
Deliver an awe inspiring pitch with this creative construction engineering and industrial facility management 4 dimensions of infrastructure security graphics pdf bundle. Topics like structured, unstructured, systems applications can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Table Of Contents KYC Transaction Monitoring System For Business Security Designs PDF
Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Table Of Contents KYC Transaction Monitoring System For Business Security Designs PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Table Of Contents KYC Transaction Monitoring System For Business Security Designs PDF today and make your presentation stand out from the rest.


 Continue with Email
Continue with Email

 Home
Home


































