Technology Security
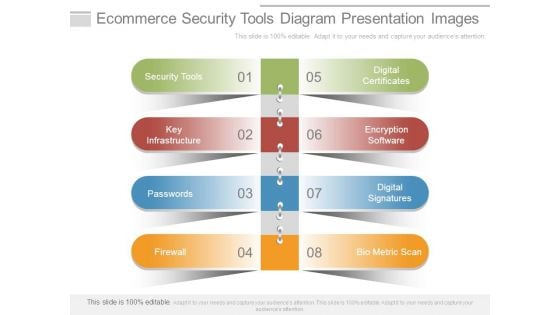
Ecommerce Security Tools Diagram Presentation Images
This is a ecommerce security tools diagram presentation images. This is a eight stage process. The stages in this process are security tools, key infrastructure, passwords, firewall, digital certificates, encryption software, digital signatures, bio metric scan.

Cloud Security Implementation Strategy Ppt Presentation
Icons Slide For Cloud Security Firewall Proposal
Elevate your presentations with our intuitive Icons Slide For Cloud Security Firewall Proposal template. Whether you are delivering a pitch, sharing data, or presenting ideas, our visually-stunning single-slide PPT template is the perfect tool to captivate your audience. With 100 percent editable features and a user-friendly interface, creating professional presentations has never been easier. Download now and leave a lasting impression. Our Icons Slide For Cloud Security Firewall Proposal are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Cloud Security Implementation Strategy Ppt Template

Security Risk Management Assessment Checklist Brochure PDF
This slide shows a security risk management assessment checklist with multiple categories. Deliver and pitch your topic in the best possible manner with this security risk management assessment checklist brochure pdf. Use them to share invaluable insights on security, management, requirements, organizations and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

What Is Cloud Security Guidelines PDF
This slide depicts the meaning of cloud security, and parties involve in a cloud security framework, such as customers and service providers. Deliver an awe inspiring pitch with this creative What Is Cloud Security Guidelines PDF bundle. Topics like Computing Systems, Protocols, Cloud Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
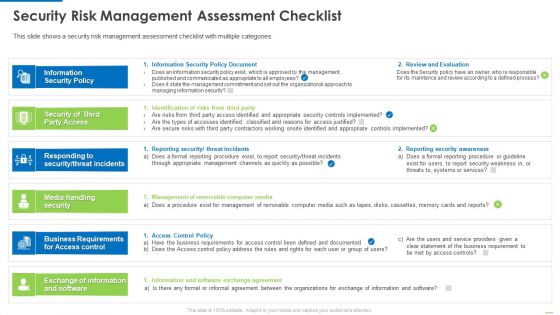
Security Risk Management Assessment Checklist Inspiration PDF
This is a security risk management assessment checklist inspiration pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like information security policy, security of third party access, media handling security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Risk Management Assessment Checklist Mockup PDF
This slide shows a security risk management assessment checklist with multiple categories. Deliver an awe inspiring pitch with this creative security risk management assessment checklist mockup pdf bundle. Topics like information security policy document, identification of risks from third party, reporting security threat incidents can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
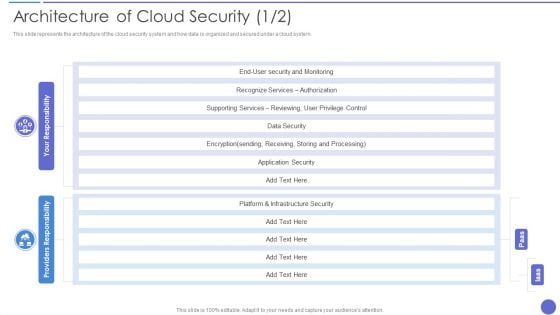
Architecture Of Cloud Security Ideas PDF
This slide represents the architecture of the cloud security system and how data is organized and secured under a cloud system. Deliver an awe inspiring pitch with this creative Architecture Of Cloud Security Ideas PDF bundle. Topics like Recognize Services, Supporting Services, Infrastructure Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
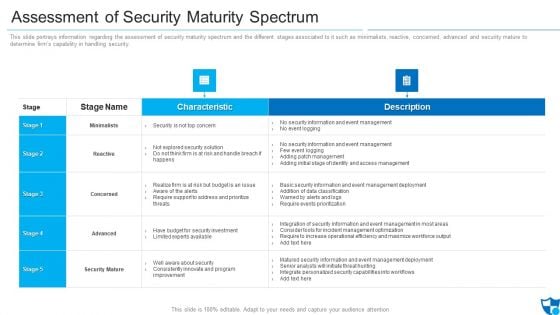
Assessment Of Security Maturity Spectrum Clipart PDF
This slide portrays information regarding the assessment of security maturity spectrum and the different stages associated to it such as minimalists, reactive, concerned, advanced and security mature to determine firms capability in handling security. Deliver an awe inspiring pitch with this creative assessment of security maturity spectrum clipart pdf bundle. Topics like security is not top concern, require support to address, improvement can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
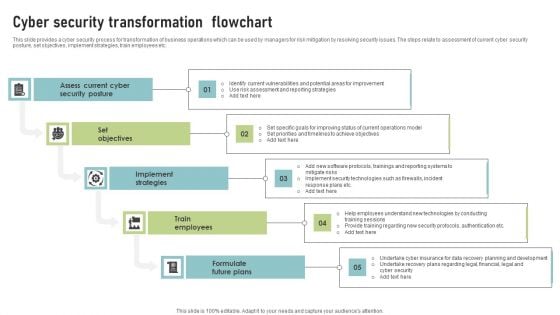
Cyber Security Transformation Flowchart Template PDF
This slide provides a cyber security process for transformation of business operations which can be used by managers for risk mitigation by resolving security issues. The steps relate to assessment of current cyber security posture, set objectives, implement strategies, train employees etc. Presenting Cyber Security Transformation Flowchart Template PDF to dispense important information. This template comprises Five stages. It also presents valuable insights into the topics including Assess Current Cyber, Security Posture, Set Objectives. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
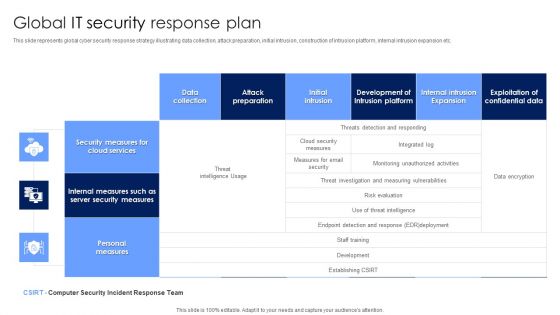
Global IT Security Response Plan Diagrams PDF
This slide represents global cyber security response strategy illustrating data collection, attack preparation, initial intrusion, construction of intrusion platform, internal intrusion expansion etc. Showcasing this set of slides titled Global IT Security Response Plan Diagrams PDF. The topics addressed in these templates are Security Measures, Cloud Services, Personal Measures. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Security Analysis Ppt PowerPoint Presentation Infographics
This is a security analysis ppt powerpoint presentation infographics. This is a two stage process. The stages in this process are business, finance, growth, analysis, success.
Security Analysis Ppt PowerPoint Presentation Background Image
This is a security analysis ppt powerpoint presentation background image. This is a two stage process. The stages in this process are business, analysis, strategic, finance, management.
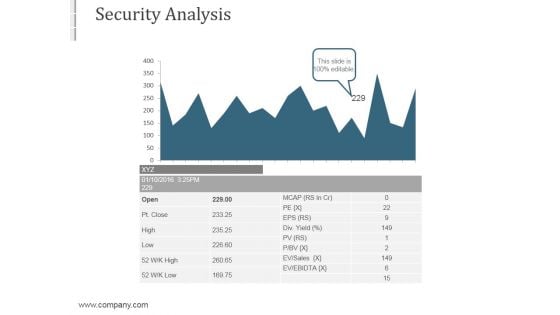
Security Analysis Ppt PowerPoint Presentation Guidelines
This is a security analysis ppt powerpoint presentation guidelines. This is a one stage process. The stages in this process are high risk, low risk.
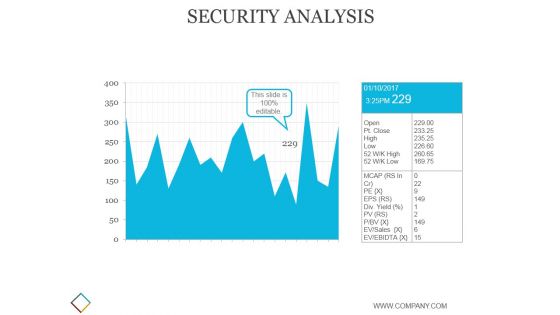
Security Analysis Ppt PowerPoint Presentation Slides
This is a security analysis ppt powerpoint presentation slides. This is a one stage process. The stages in this process are business, strategy, marketing, analysis, growth.
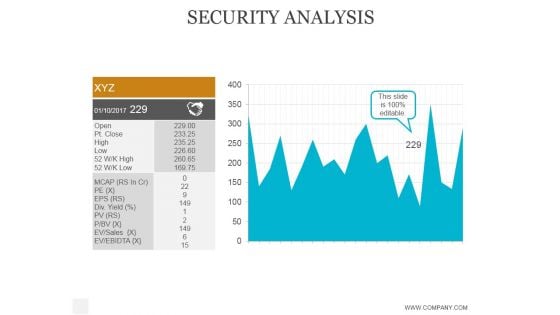
Security Analysis Ppt PowerPoint Presentation Layout
This is a security analysis ppt powerpoint presentation layout. This is a one stage process. The stages in this process are business, strategy, marketing, analysis, success.
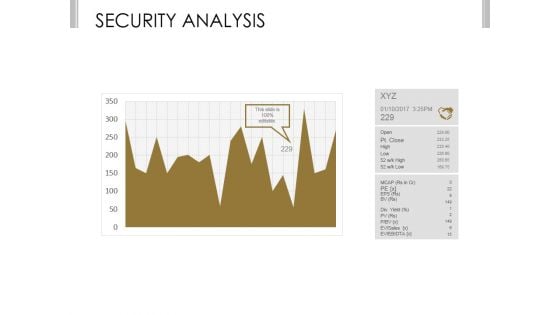
Security Analysis Ppt PowerPoint Presentation Deck
This is a security analysis ppt powerpoint presentation deck. This is a one stage process. The stages in this process are business, strategy, marketing, analysis, growth.
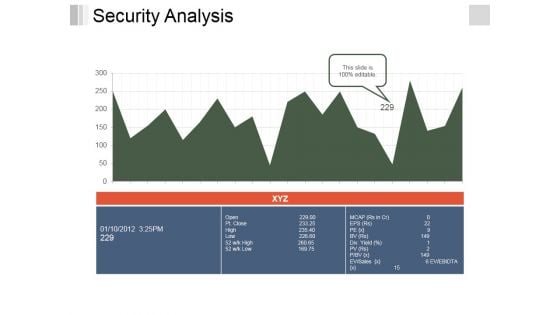
Security Analysis Ppt PowerPoint Presentation File Inspiration
This is a security analysis ppt powerpoint presentation file inspiration. This is a two stage process. The stages in this process are business, growth, analysis, strategy, management.
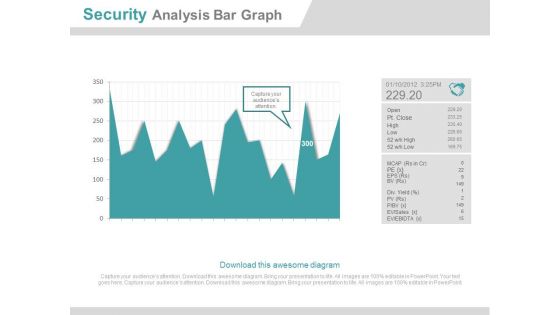
Security Analysis Bar Graph Ppt Slides
This is a security analysis bar chart ppt slides. This is a one stage process. The stages in this process are business, finance, marketing.
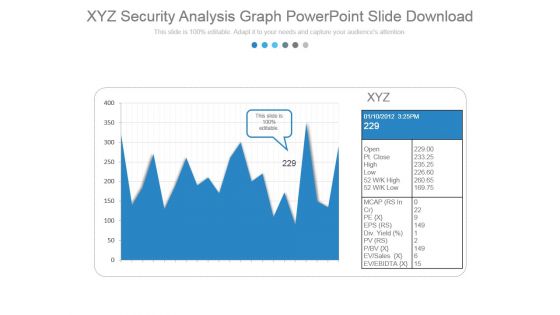
Xyz Security Analysis Graph Powerpoint Slide Download
This is a xyz security analysis graph powerpoint slide download. This is a two stage process. The stages in this process are business, marketing, growth, graph.
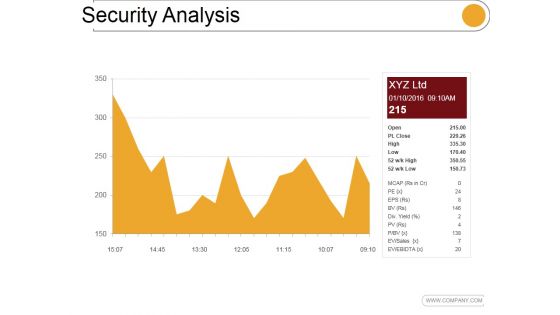
Security Analysis Ppt PowerPoint Presentation Show
This is a security analysis ppt powerpoint presentation show. This is a one stage process. The stages in this process are open, high, low, business, marketing.
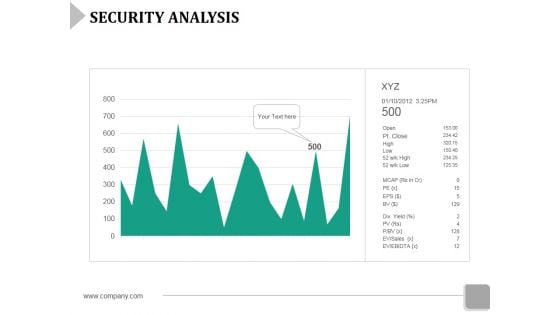
Security Analysis Ppt Powerpoint Presentation File Tips
This is a security analysis ppt powerpoint presentation file tips. This is a one stage process. The stages in this process are graph, marketing, business, growth, finance.
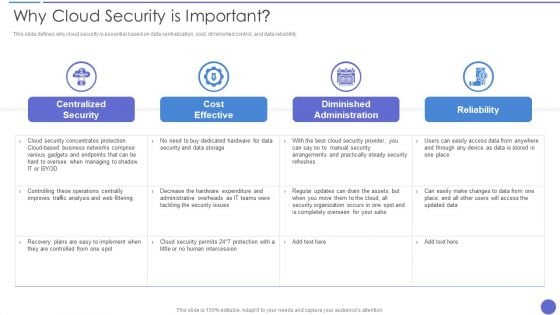
Why Cloud Security Is Important Demonstration PDF
This slide defines why cloud security is essential based on data centralization, cost, diminished control, and data reliability. Deliver an awe inspiring pitch with this creative Why Cloud Security Is Important Demonstration PDF bundle. Topics like Cost Effective, Centralized Security, Diminished Administration can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
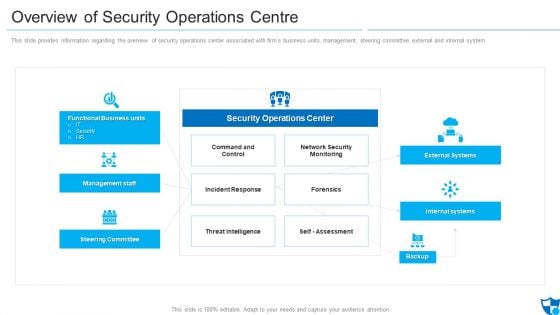
Overview Of Security Operations Centre Sample PDF
This slide provides information regarding the overview of security operations center associated with firms business units, management, steering committee, external and internal system.Deliver and pitch your topic in the best possible manner with this overview of security operations centre sample pdf. Use them to share invaluable insights on command and control, network security monitoring, threat intelligence and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
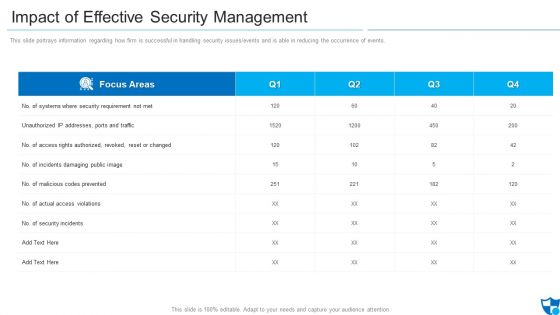
Impact Of Effective Security Management Information PDF
This slide portrays information regarding how firm is successful in handling security issues or events and is able in reducing the occurrence of events. Deliver and pitch your topic in the best possible manner with this impact of effective security management information pdf. Use them to share invaluable insights on malicious codes prevented, unauthorized ip addresses ports and traffic, security incidents and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Security Patch Management Template Presentation Images
This is a security patch management template presentation images. This is a six stage process. The stages in this process are testing, architecture, quality assurance, analysis, design, synthesis.
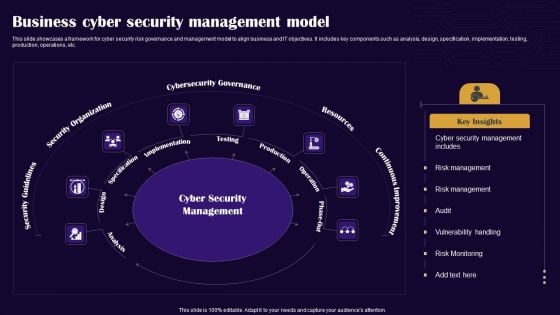
Business Cyber Security Management Model Graphics PDF
This slide showcases a framework for cyber security risk governance and management model to align business and IT objectives. It includes key components such as analysis, design, specification, implementation, testing, production, operations, etc. Presenting Business Cyber Security Management Model Graphics PDF to dispense important information. This template comprises eight stages. It also presents valuable insights into the topics including Security Guidelines, Security Organization, Cybersecurity Governance. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
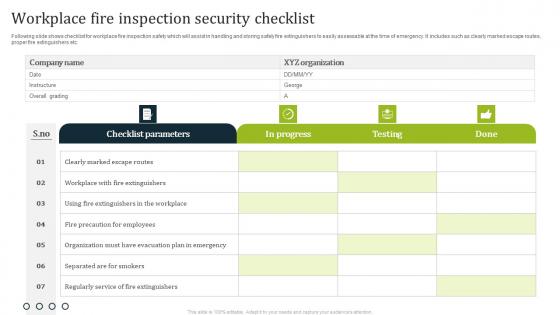
Workplace Fire Inspection Security Checklist Diagrams Pdf
Following slide shows checklist for workplace fire inspection safety which will assist in handling and storing safely fire extinguishers to easily assessable at the time of emergency. It includes such as clearly marked escape routes, proper fire extinguishers etc. Showcasing this set of slides titled Workplace Fire Inspection Security Checklist Diagrams Pdf. The topics addressed in these templates are Checklist Parameters, Done, Testing. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Following slide shows checklist for workplace fire inspection safety which will assist in handling and storing safely fire extinguishers to easily assessable at the time of emergency. It includes such as clearly marked escape routes, proper fire extinguishers etc.
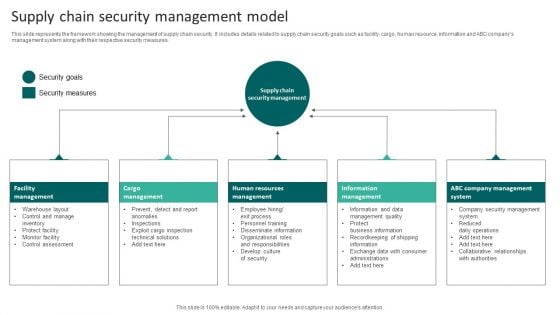
Supply Chain Security Management Model Infographics PDF
This slide represents the framework showing the management of supply chain security. It includes details related to supply chain security goals such as facility, cargo, human resource, information and ABC companys management system along with their respective security measures. Presenting Supply Chain Security Management Model Infographics PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Human Resources Management, Cargo Management, Facility Management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Information Security Risk Management Form Guidelines PDF
This slide shows information security risk acceptance form which contains accountable person details, risk acceptance summary, acceptance advantages, justification, advice, etc. This can benefit cyber security department in careful review prior to the acceptance of major risks involved. Pitch your topic with ease and precision using this Information Security Risk Management Form Guidelines PDF. This layout presents information on Risk Modification, Risk Acceptance, Cyber Security. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Main Data Security Tokenization Techniques PPT Powerpoint
This slide represents the various categories of tokenization. The purpose of this slide is to showcase the types of tokenization such as platform, utility, governance, non-fungible, etc. Boost your pitch with our creative Main Data Security Tokenization Techniques PPT Powerpoint. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide represents the various categories of tokenization. The purpose of this slide is to showcase the types of tokenization such as platform, utility, governance, non-fungible, etc.
Data Storage Security Management Icon Professional PDF
Presenting Data Storage Security Management Icon Professional PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Data Storage, Security, Management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
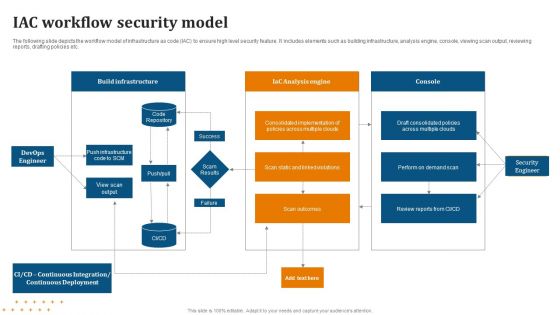
IAC Workflow Security Model Diagrams PDF
Showcasing this set of slides titled IAC Workflow Security Model Diagrams PDF. The topics addressed in these templates are Workflow, Security Model. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
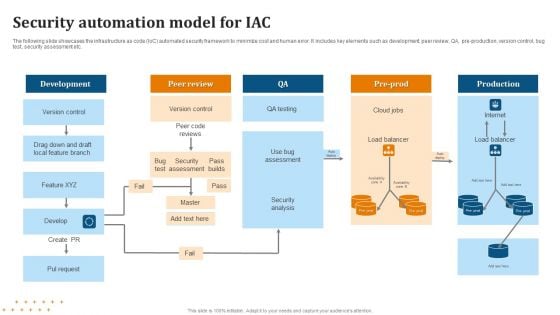
Security Automation Model For IAC Summary PDF
Pitch your topic with ease and precision using this Security Automation Model For IAC Summary PDF. This layout presents information on Security Automation, Model For IAC . It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Payment Card Security Processing Icon Portrait PDF
Presenting Payment Card Security Processing Icon Portrait PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Payment Card Security, Processing Icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Computer Safety And Security Icon Infographics PDF
Persuade your audience using this Computer Safety And Security Icon Infographics PDF This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Computer Safety, Security Icon Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
KPI Dashboard Metrics Security Icon Download PDF
Persuade your audience using this KPI Dashboard Metrics Security Icon Download PDF. This PPT design covers two stages, thus making it a great tool to use. It also caters to a variety of topics including Kpi Dashboard, Metrics Security Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
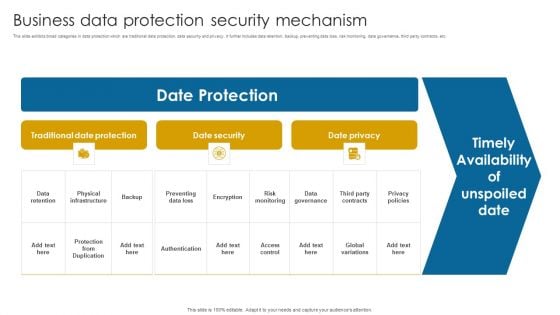
Business Data Protection Security Mechanism Portrait PDF
This slide exhibits broad categories in data protection which are traditional data protection, data security and privacy. It further includes data retention, backup, preventing data loss, risk monitoring, data governance, third party contracts, etc.Showcasing this set of slides titled Business Data Protection Security Mechanism Portrait PDF. The topics addressed in these templates are Data Retention, Physical Infrastructure, Date Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
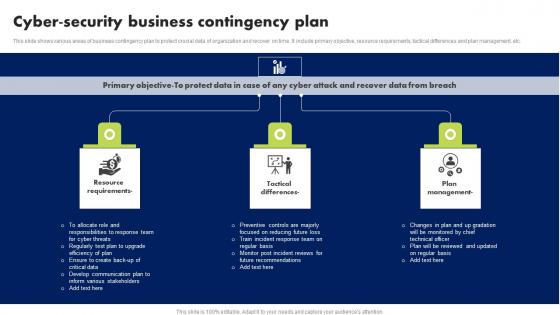
Cyber Security Business Contingency Plan Brochure Pdf
This slide shows various areas of business contingency plan to protect crucial data of organization and recover on time. It include primary objective, resource requirements, tactical differences and plan management, etc. Showcasing this set of slides titled Cyber Security Business Contingency Plan Brochure Pdf. The topics addressed in these templates are Resource Requirements, Tactical Differences, Plan Management. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide shows various areas of business contingency plan to protect crucial data of organization and recover on time. It include primary objective, resource requirements, tactical differences and plan management, etc.
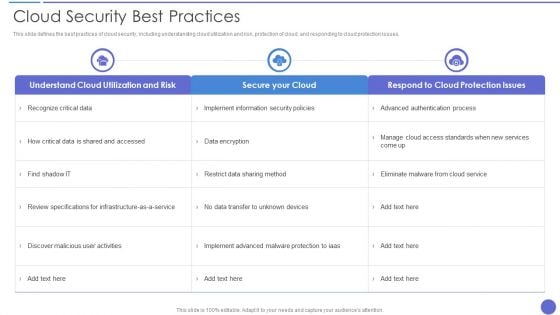
Cloud Security Best Practices Themes PDF
This slide defines the best practices of cloud security, including understanding cloud utilization and risk, protection of cloud, and responding to cloud protection issues. Deliver and pitch your topic in the best possible manner with this Cloud Security Best Practices Themes PDF. Use them to share invaluable insights on Secure Your Cloud, Data Encryption, Recognize Critical Data and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
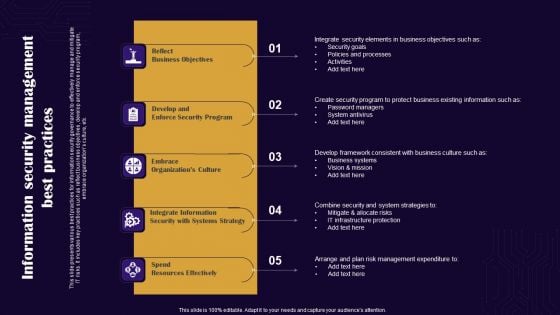
Information Security Management Best Practices Themes PDF
This slide presents various best practices for information security governance to effectively manage and mitigate IT risks. It includes key practices such as reflect business objectives, develop and enforce security program, embrace organizations culture, etc. Presenting Information Security Management Best Practices Themes PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Reflect Business Objectives, Spend Resources Effectively, Embrace Organizations Culture. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
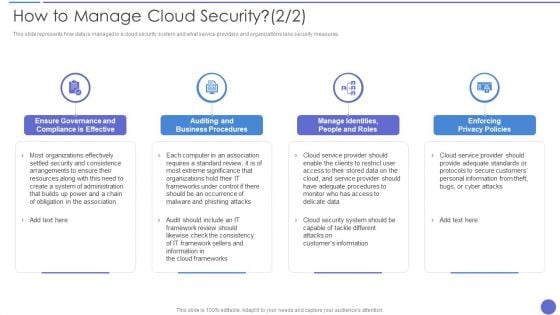
How To Manage Cloud Security Topics PDF
This slide represents how data is managed in a cloud security system and what service providers and organizations take security measures. This is a How To Manage Cloud Security Topics PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Enforcing Privacy Policies, Auditing And Business Procedures, Organizations. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
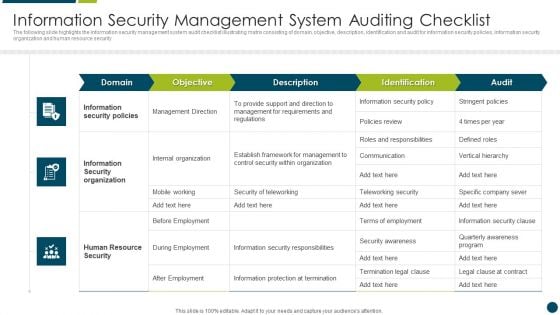
Information Security Management System Auditing Brochure PDF
The following slide highlights the information security management system audit process illustrating information security system details, information collection, statement o applicability review, audit scope, risk management analysis, gap analysis, business continuity and contingency plan review, mitigation strategy and compliance audit activities PresentingInformation Security Management System Auditing Brochure PDF to dispense important information. This template comprises eight stages. It also presents valuable insights into the topics including Risk Management Analysis, Information Collection, Mitigation Strategy. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully
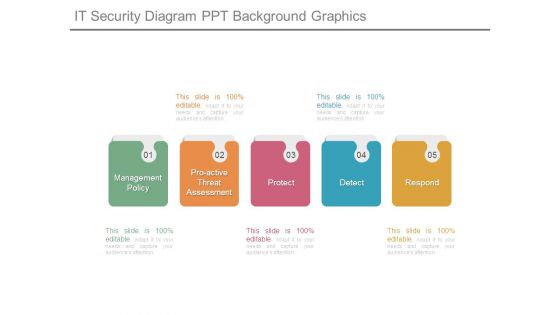
It Security Diagram Ppt Background Graphics
This is a it security diagram ppt background graphics. This is a five stage process. The stages in this process are management policy, proactive threat assessment, protect, detect, respond.
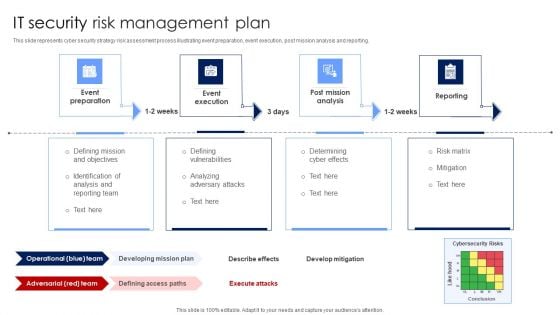
IT Security Risk Management Plan Mockup PDF
This slide represents cyber security strategy risk assessment process illustrating event preparation, event execution, post mission analysis and reporting. Presenting IT Security Risk Management Plan Mockup PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Post Mission Analysis, Reporting, Event Execution. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
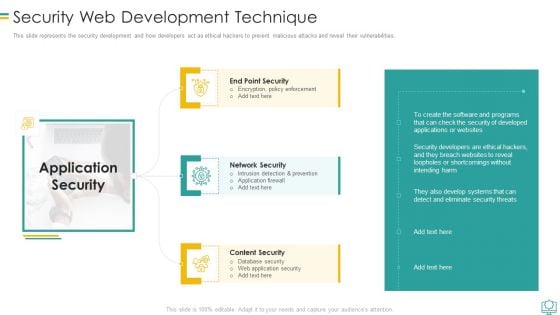
Security Web Development Technique Mockup PDF
This slide represents the security development and how developers act as ethical hackers to prevent malicious attacks and reveal their vulnerabilities.This is a Security Web Development Technique Mockup PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Intrusion Detection And Prevention, Encryption Policy Enforcement, Database Security You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
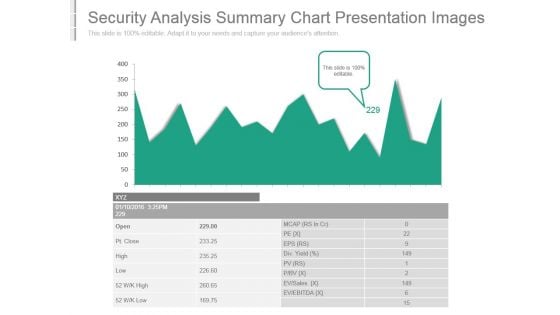
Security Analysis Summary Chart Presentation Images
This is a security analysis summary chart presentation images. This is a one stage process. The stages in this process are ev ebitda, ev sales, div yield, open, pt close, high, low, mcap, eps.
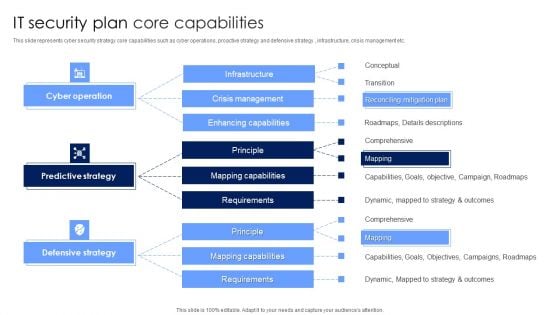
IT Security Plan Core Capabilities Rules PDF
This slide represents cyber security strategy core capabilities such as cyber operations, proactive strategy and defensive strategy , infrastructure, crisis management etc. Showcasing this set of slides titled IT Security Plan Core Capabilities Rules PDF. The topics addressed in these templates are Defensive Strategy, Predictive Strategy, Cyber Operation. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
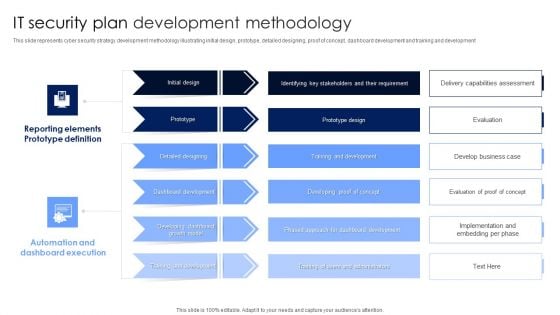
IT Security Plan Development Methodology Microsoft PDF
This slide represents cyber security strategy development methodology illustrating initial design, prototype, detailed designing, proof of concept, dashboard development and training and development. Pitch your topic with ease and precision using this IT Security Plan Development Methodology Microsoft PDF. This layout presents information on Automation And Dashboard Execution, Reporting Elements Prototype Definition, Dashboard Development. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
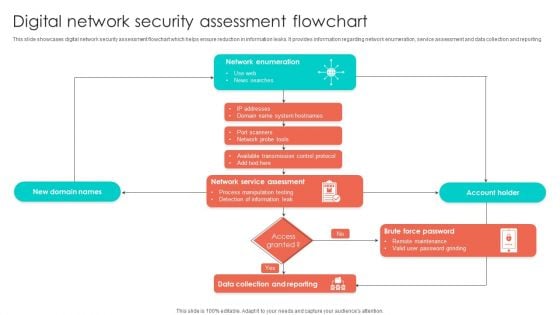
Digital Network Security Assessment Flowchart Structure PDF
This slide showcases digital network security assessment flowchart which helps ensure reduction in information leaks. It provides information regarding network enumeration, service assessment and data collection and reporting. Showcasing this set of slides titled Digital Network Security Assessment Flowchart Structure PDF. The topics addressed in these templates are Account Holder, Information Leak, Network Service Assessment. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Four Computer Security Threats Rules PDF
This slide shows the 4 threats to cyber security. It includes phishing attacks, cloud jacking, IoT devices and insider threats.Pitch your topic with ease and precision using this Four Computer Security Threats Rules PDF This layout presents information on Data Manipulation, Attacker Attempts, Sensitive Information It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
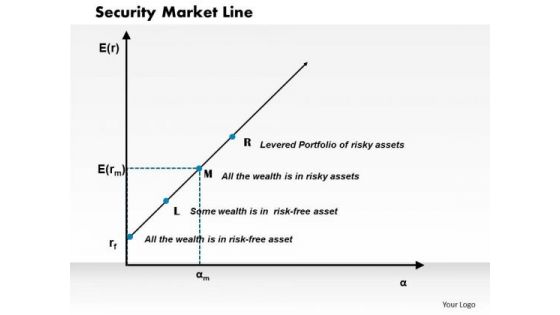
Business Framework Security Market Line PowerPoint Presentation
This diagram displays graph of security market line. You can use line graph to plot changes in data over time, such as monthly revenue and earnings changes or daily changes in stock market prices.

Cyber Security Incident Response Lifecycle Information PDF
This slide represents the lifecycle of incident response which enables organizations to quickly detect and halt attacks, minimize damage and prevent future attacks of same type. It includes four phases of cyber security incident response such as preparation, detection and analysis etc. Presenting this PowerPoint presentation, titled Cyber Security Incident Response Lifecycle Information PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Cyber Security Incident Response Lifecycle Information PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Cyber Security Incident Response Lifecycle Information PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.

Enterprise Cloud Security Solutions Professional PDF
This slide describes the enterprise cloud security solutions, including multi factor authentication, managing accounts and service proactively, being careful about shadow IT, and analyzing the cost benefits of hybrid cloud. Deliver an awe inspiring pitch with this creative Enterprise Cloud Security Solutions Professional PDF bundle. Topics like Services Proactively, Analyze Cost Benefits, Authentication Processes can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Flag American Security PowerPoint Presentation Slides C
Microsoft PowerPoint Slides and Backgrounds with flag american with gun creative actual for designer Distill your thoughts with our Flag American Security PowerPoint Presentation Slides C. They will draw outthe essence of it all.

Credit Card Payment Processing Security Rules PDF
This slide outline the basics of payment processing security to protect business operations and sensitive consumer data. It includes secure data storage, payment data encryption and payment data tokenization. Presenting Credit Card Payment Processing Security Rules PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Secure Data Storage Vault, Payment Data Encryption, Payment Data Tokenization. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Security Encryption Ppt PowerPoint Presentation Layouts Cpb
Presenting this set of slides with name security encryption ppt powerpoint presentation layouts cpb. This is an editable Powerpoint four stages graphic that deals with topics like security encryption to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
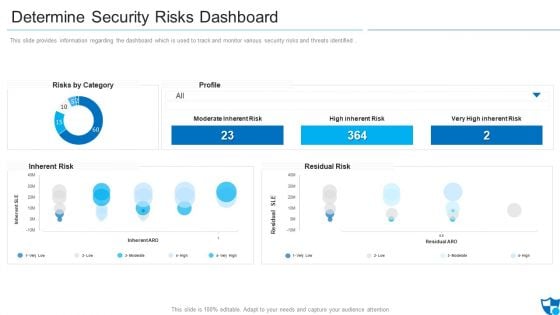
Determine Security Risks Dashboard Introduction PDF
This slide provides information regarding the dashboard which is used to track and monitor various security risks and threats identified.Deliver and pitch your topic in the best possible manner with this determine security risks dashboard introduction pdf. Use them to share invaluable insights on moderate inherent risk, high inherent risk, very high inherent risk and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
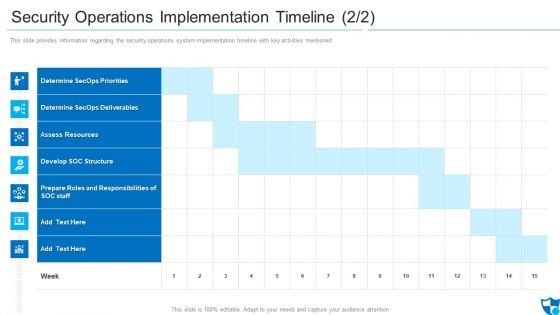
Security Operations Implementation Timeline Assess Diagrams PDF
This slide provides information regarding the security operations system implementation timeline with key activities mentioned.Deliver and pitch your topic in the best possible manner with this security operations implementation timeline assess diagrams pdf. Use them to share invaluable insights on determine secops priorities, determine secops deliverables, assess resources and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.


 Continue with Email
Continue with Email

 Home
Home


































