Threat
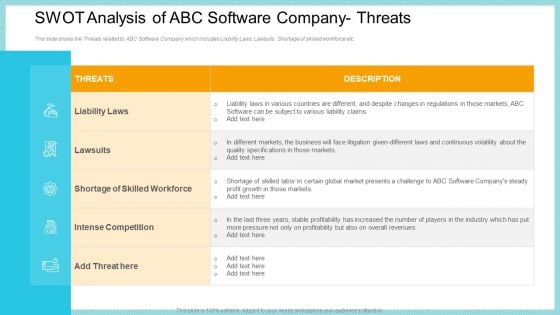
SWOT Analysis Of ABC Software Company Threats Structure PDF
This slide shows the Threats related to ABC Software Company which includes Liability Laws, Lawsuits, Shortage of skilled workforce etc. Presenting swot analysis of abc software company threats structure pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like revenues, profitability, quality. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Agenda Of How To Intensify Project Threats Portrait PDF
This is a agenda of how to intensify project threats portrait pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like agenda of how to intensify project threats. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
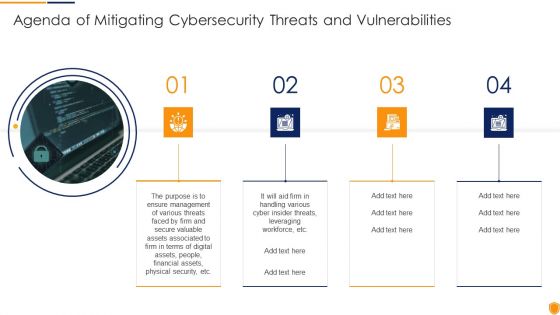
Agenda Of Mitigating Cybersecurity Threats And Vulnerabilities Guidelines PDF
Presenting agenda of mitigating cybersecurity threats and vulnerabilities guidelines pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like agenda of mitigating cybersecurity threats and vulnerabilities. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Mitigating Cybersecurity Threats And Vulnerabilities Addressing Indicators Associated Icons PDF
This slide provides details regarding indicators associated to insider threats in terms of traits, demeanor and goals, etc. Presenting mitigating cybersecurity threats and vulnerabilities addressing indicators associated icons pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like user accounts, authentication levels, data exfiltration. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Table Of Contents Mitigating Cybersecurity Threats And Vulnerabilities Portrait PDF
Presenting table of contents mitigating cybersecurity threats and vulnerabilities portrait pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like current scenario assessment, secure digital assets, physical security, natural calamity threats. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
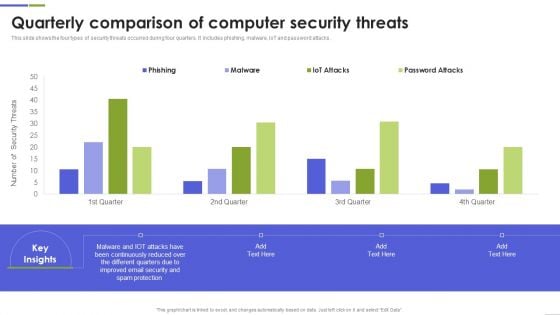
Quarterly Comparison Of Computer Security Threats Mockup PDF
This slide shows the four types of security threats occurred during four quarters. It includes phishing, malware, IoT and password attacks. Pitch your topic with ease and precision using this Quarterly Comparison Of Computer Security Threats Mockup PDF This layout presents information on Continuously Reduced, Different Quarters, Spam Protection It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
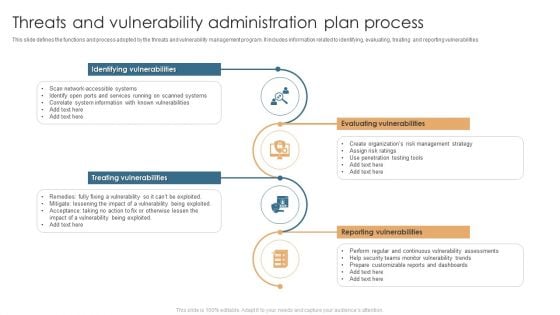
Threats And Vulnerability Administration Plan Process Guidelines PDF
This slide defines the functions and process adopted by the threats and vulnerability management program. It includes information related to identifying, evaluating, treating and reporting vulnerabilities. Presenting Threats And Vulnerability Administration Plan Process Guidelines PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Evaluating Vulnerabilities, Reporting Vulnerabilities, Treating Vulnerabilities, Identifying Vulnerabilities. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Threats And Vulnerability Administration Plan Requirement Icon Pictures PDF
Persuade your audience using this Threats And Vulnerability Administration Plan Requirement Icon Pictures PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Threats And Vulnerability, Administration Plan, Requirement Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
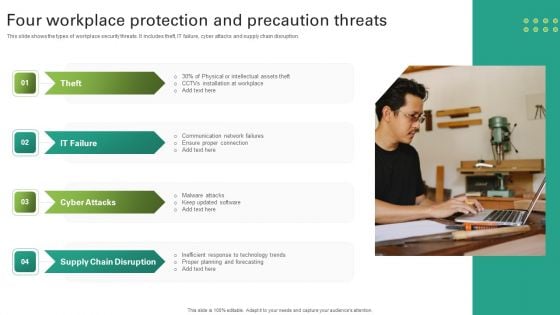
Four Workplace Protection And Precaution Threats Template PDF
This slide shows the types of workplace security threats. It includes theft, IT failure, cyber attacks and supply chain disruption. Presenting Four Workplace Protection And Precaution Threats Template PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Theft, It Failure, Cyber Attacks. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Threats Affecting Infra Cyber Security In Market Icons PDF
The following slide showcases threats in infrastructure security which can cause electrical blackouts, breaches of national secrets, etc. It presents information related to phishing, ransomware, botnets, etc. Presenting Threats Affecting Infra Cyber Security In Market Icons PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Phishing, Ransomware, Botnets. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Major Threats That Creates Obstacles In Firm Growth Ideas PDF
This slide provides information regarding SWOT analysis technique utilized by Amazon to evaluate its competitive positioning. The slide highlighting threats faced by Amazon causing potential issues in terms of data and online privacy risk, aggressive pricing strategies, etc. Are you searching for a Major Threats That Creates Obstacles In Firm Growth Ideas PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Major Threats That Creates Obstacles In Firm Growth Ideas PDF from Slidegeeks today.

Major Threats That Creates Obstacles In Firm Growth Guidelines PDF
This slide provides information regarding SWOT analysis technique utilized by Amazon to evaluate its competitive positioning. The slide highlighting threats faced by Amazon causing potential issues in terms of data and online privacy risk, aggressive pricing strategies, etc. Are you searching for a Major Threats That Creates Obstacles In Firm Growth Guidelines PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Major Threats That Creates Obstacles In Firm Growth Guidelines PDF from Slidegeeks today.
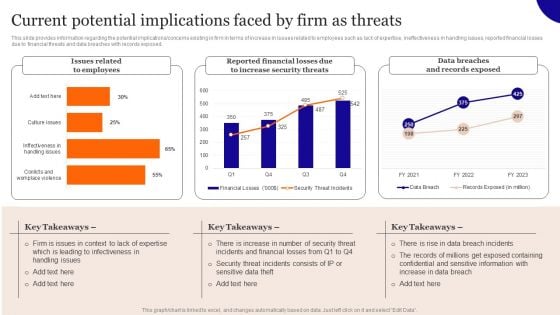
Current Potential Implications Faced By Firm As Threats Download PDF
This slide provides information regarding the potential implications or concerns existing in firm in terms of increase in issues related to employees such as lack of expertise, ineffectiveness in handling issues, reported financial losses due to financial threats and data breaches with records exposed. Create an editable Current Potential Implications Faced By Firm As Threats Download PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Current Potential Implications Faced By Firm As Threats Download PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
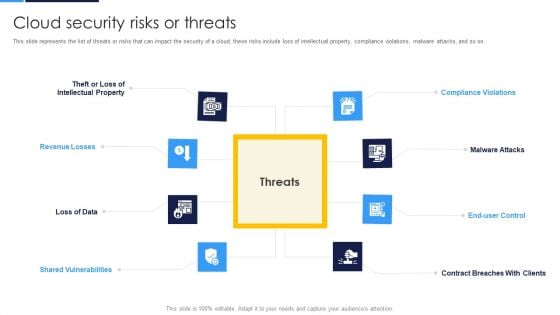
Cloud Security Assessment Cloud Security Risks Or Threats Topics PDF
This slide represents the list of threats or risks that can impact the security of a cloud these risks include loss of intellectual property, compliance violations, malware attacks, and so on.Presenting Cloud Security Assessment Cloud Security Risks Or Threats Topics PDF to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like Revenue Losses, Shared Vulnerabilities, Compliance Violations In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
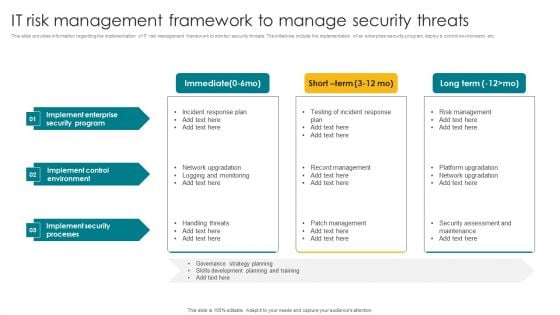
IT Risk Management Framework To Manage Security Threats Template PDF
This slide provides information regarding the implementation of IT risk management framework to monitor security threats. The initiatives include the implementation of an enterprise security program, deploy a control environment, etc. The IT Risk Management Framework To Manage Security Threats Template PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Mitigating Cybersecurity Threats And Vulnerabilities Addressing Various Ways Template PDF
This slide provides details regarding various ways to handle insider cyber threats in terms of periodic risk assessment, end user informing, etc. This is a mitigating cybersecurity threats and vulnerabilities addressing various ways template pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like periodic risk assessment, networks and individuals, inform end user. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
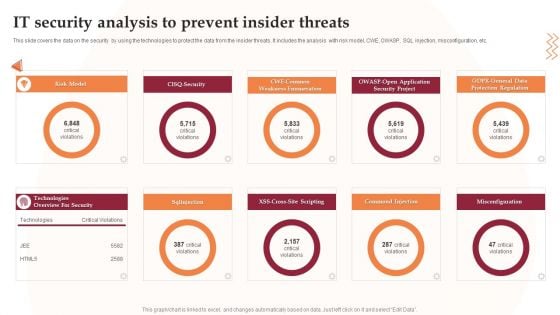
IT Security Analysis To Prevent Insider Threats Infographics PDF
This slide covers the data on the security by using the technologies to protect the data from the insider threats. It includes the analysis with risk model, CWE, OWASP, SQL injection, misconfiguration, etc. Presenting IT Security Analysis To Prevent Insider Threats Infographics PDF to dispense important information. This template comprises nine stages. It also presents valuable insights into the topics including Security Project, Application, Risk Model. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
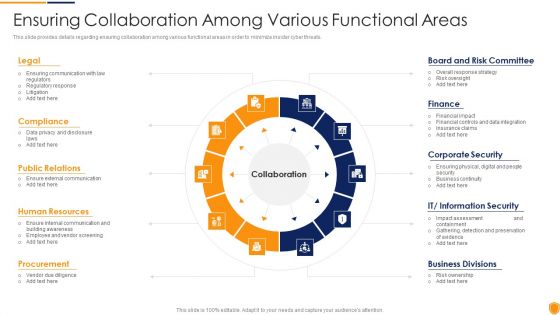
Mitigating Cybersecurity Threats And Vulnerabilities Ensuring Collaboration Among Elements PDF
This slide provides details regarding ensuring collaboration among various functional areas in order to minimize insider cyber threats. Presenting mitigating cybersecurity threats and vulnerabilities ensuring collaboration among elements pdf to provide visual cues and insights. Share and navigate important information on ten stages that need your due attention. This template can be used to pitch topics like compliance, public relations, human resources, procurement, board and risk committee. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
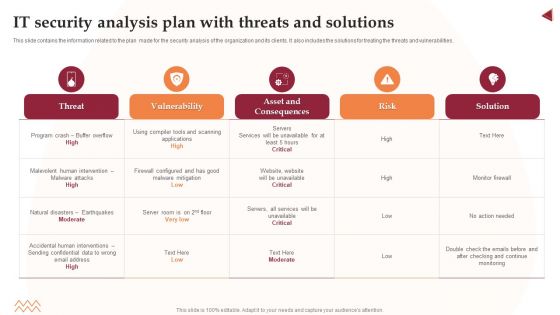
IT Security Analysis Plan With Threats And Solutions Infographics PDF
This slide contains the information related to the plan made for the security analysis of the organization and its clients. It also includes the solutions for treating the threats and vulnerabilities. Showcasing this set of slides titled IT Security Analysis Plan With Threats And Solutions Infographics PDF. The topics addressed in these templates are Risk, Applications, Services. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
SWOT Analysis Of ABC Software Company Threats Icons PDF
This slide shows the Threats related to ABC Software Company which includes Liability Laws, Lawsuits, Shortage of skilled workforce etc. Presenting swot analysis of abc software company threats icons pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like liability laws, intense competition, shortage of skilled workforce. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Process For Responding To Internet Security Threats Template PDF
This slide exhibits process for responding to security data breach. It includes multiple steps such as- analyzing the current damage, keeping record how much damage is caused and so on. Pitch your topic with ease and precision using this process for responding to internet security threats template pdf. This layout presents information on process for responding to internet security threats. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
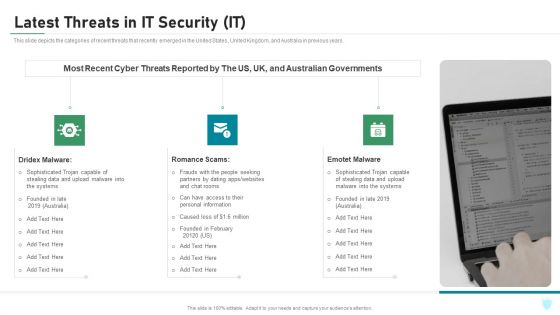
Latest Threats In IT Security IT Ppt Gallery Elements PDF
This slide depicts the categories of recent threats that recently emerged in the United States, United Kingdom, and Australia in previous years. Presenting latest threats in it security it ppt gallery elements pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like dridex malware, romance scams, emotet malware. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
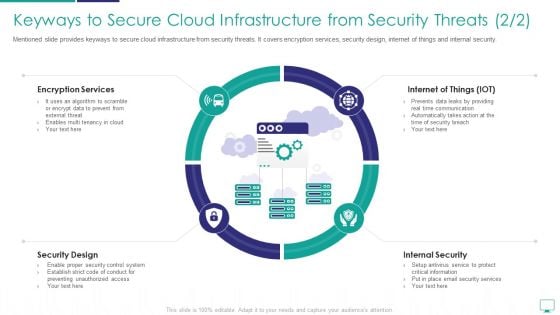
Keyways To Secure Cloud Infrastructure From Security Threats Formats PDF
Mentioned slide provides keyways to secure cloud infrastructure from security threats. It covers encryption services, security design, internet of things and internal security.This is a keyways to secure cloud infrastructure from security threats formats pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like encryption services, internet of things, security design. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Desktop Security Management Latest Threats In Computer Security Inspiration PDF
This slide depicts the categories of recent threats that recently emerged in the United States, United Kingdom, and Australia in previous years. Presenting desktop security management latest threats in computer security inspiration pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like financial, information, systems. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
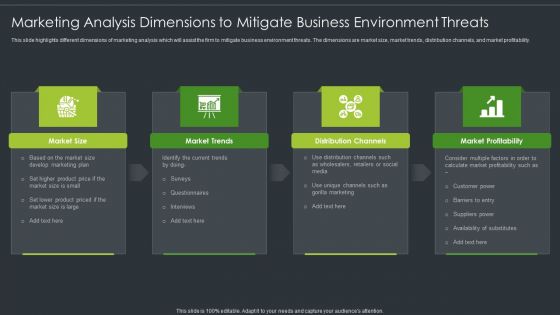
Marketing Analysis Dimensions To Mitigate Business Environment Threats Clipart PDF
This slide highlights different dimensions of marketing analysis which will assist the firm to mitigate business environment threats. The dimensions are market size, market trends, distribution channels, and market profitability. Persuade your audience using this Marketing Analysis Dimensions To Mitigate Business Environment Threats Clipart PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Market Size, Market Trends, Distribution Channels. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
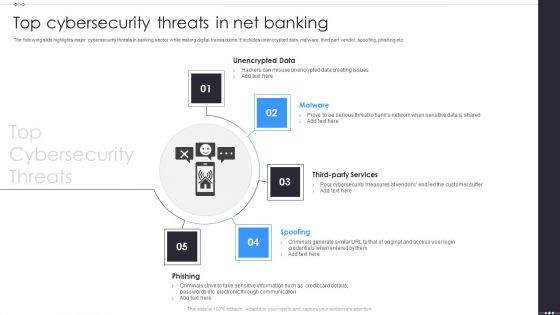
Top Cybersecurity Threats In Net Banking Download PDF
The following slide highlights major cybersecurity threats in banking sector while making digital transactions. It includes unencrypted data, malware, third part vendor, spoofing, phishing etc. Persuade your audience using this Top Cybersecurity Threats In Net Banking Download PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Unencrypted Data, Spoofing, Phishing. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Keyways To Secure Cloud Infrastructure From Security Threats Inspiration PDF
Mentioned slide provides keyways to secure cloud infrastructure from security threats. It covers encryption services, security design, internet of things and internal security.Presenting Keyways To Secure Cloud Infrastructure From Security Threats Inspiration PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Encryption Services, Internal Security, Security Design. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Business Threats Mitigation Icon Ppt PowerPoint Presentation Show Portrait
Presenting this set of slides with name business threats mitigation icon ppt powerpoint presentation show portrait. This is a one stage process. The stages in this process are hazard symbol, risk icon, risk management icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
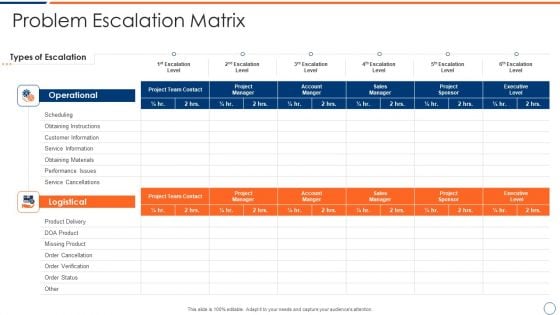
How To Intensify Project Threats Problem Escalation Matrix Formats PDF
Deliver and pitch your topic in the best possible manner with this how to intensify project threats problem escalation matrix formats pdf. Use them to share invaluable insights on operational, logistical and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
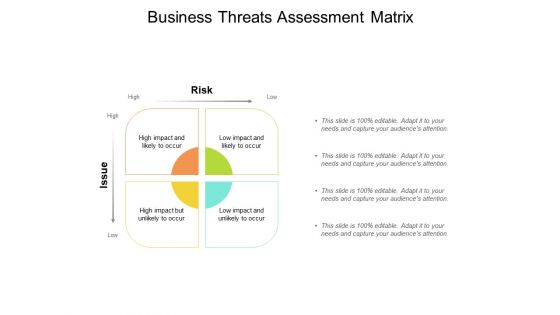
Business Threats Assessment Matrix Ppt PowerPoint Presentation Inspiration Clipart Images
Presenting this set of slides with name business threats assessment matrix ppt powerpoint presentation inspiration clipart images. This is a four stage process. The stages in this process are issue and risk, project management, opportunity management. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Icons Slide For How To Intensify Project Threats Elements PDF
Download our innovative and attention grabbing icons slide for how to intensify project threats elements pdf template. The set of slides exhibit completely customizable icons. These icons can be incorporated into any business presentation. So download it immediately to clearly communicate with your clientele.

How To Intensify Project Threats Post It Notes Clipart PDF
Presenting how to intensify project threats post it notes clipart pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like post it notes. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
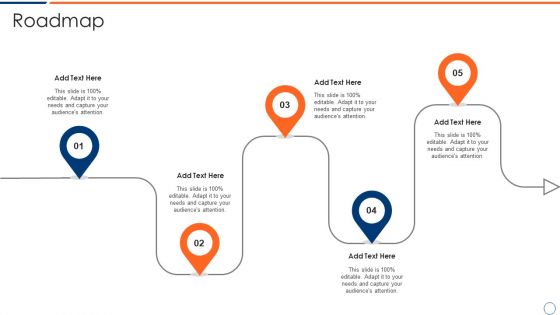
How To Intensify Project Threats Roadmap Slides PDF
Presenting how to intensify project threats roadmap slides pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like roadmap. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
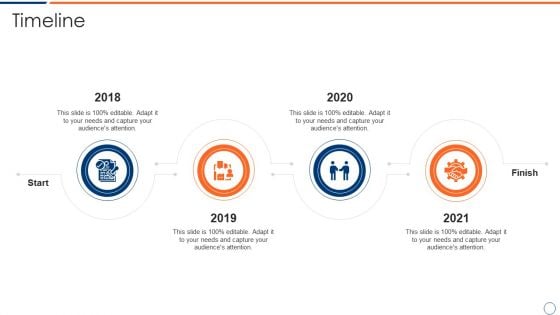
How To Intensify Project Threats Timeline Themes PDF
This is a how to intensify project threats timeline themes pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like timeline, 2018 to 2021. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Icons Slide For Mitigating Cybersecurity Threats And Vulnerabilities Microsoft PDF
Introducing our well designed icons slide for mitigating cybersecurity threats and vulnerabilities microsoft pdf set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.

Mitigating Cybersecurity Threats And Vulnerabilities Incident Reporting Dashboard Demonstration PDF
The firm will track the various incidents issues faced and resolved in the firm. Deliver an awe inspiring pitch with this creative mitigating cybersecurity threats and vulnerabilities incident reporting dashboard demonstration pdf bundle. Topics like incident reporting dashboard can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Icons Slide For IT Threats Response Playbook Download PDF
Download our innovative and attention grabbing Icons Slide For IT Threats Response Playbook Download PDF template. The set of slides exhibit completely customizable icons. These icons can be incorporated into any business presentation. So download it immediately to clearly communicate with your clientele.
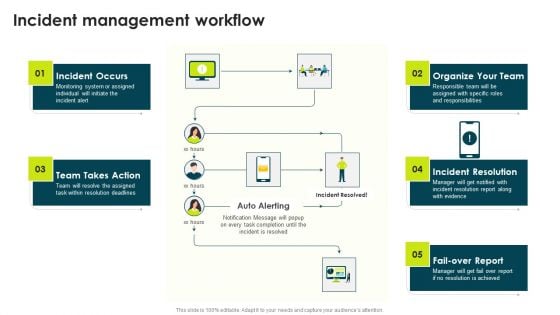
IT Threats Response Playbook Incident Management Workflow Themes PDF
Deliver an awe inspiring pitch with this creative IT Threats Response Playbook Incident Management Workflow Themes PDF bundle. Topics like Incident Occurs, Incident Resolution, Resolution Achieved can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
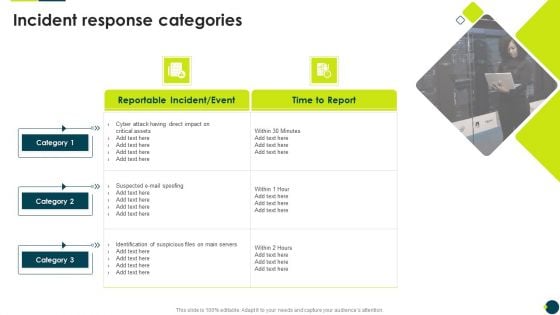
IT Threats Response Playbook Incident Response Categories Rules PDF
Deliver and pitch your topic in the best possible manner with this IT Threats Response Playbook Incident Response Categories Rules PDF. Use them to share invaluable insights on Identification Suspicious, Direct Impact, Time To Report and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

IT Threats Response Playbook SWOT Analysis Professional PDF
This is a IT Threats Response Playbook SWOT Analysis Professional PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Strengths, Weaknesses, Opportunities. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Table Of Contents For IT Threats Response Playbook Clipart PDF
Deliver and pitch your topic in the best possible manner with this Table Of Contents For IT Threats Response Playbook Clipart PDF. Use them to share invaluable insights on Security Incidents, Figures And Statistics, Ransom Payment and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Risk Management Plan To Mitigate Threats Icons PDF
This slide shows the risk management plan for retailers which includes status, description, probability, impact in terms of scope, quality, schedule and cost with mitigation actions, contingency funds and time, etc. Are you searching for a Risk Management Plan To Mitigate Threats Icons PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Risk Management Plan To Mitigate Threats Icons PDF from Slidegeeks today.

Risk Management Plan To Mitigate Threats Pictures PDF
This slide shows the risk management plan for retailers which includes status, description, probability, impact in terms of scope, quality, schedule and cost with mitigation actions, contingency funds and time, etc. Are you searching for a Risk Management Plan To Mitigate Threats Pictures PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Risk Management Plan To Mitigate Threats Pictures PDF from Slidegeeks today.
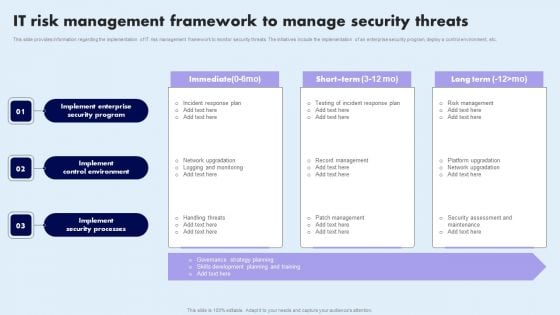
IT Risk Management Framework To Manage Security Threats Summary PDF
This slide provides information regarding the implementation of IT risk management framework to monitor security threats. The initiatives include the implementation of an enterprise security program, deploy a control environment, etc. Retrieve professionally designed IT Risk Management Framework To Manage Security Threats Summary PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
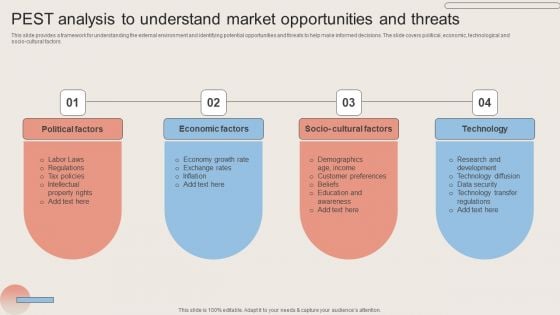
PEST Analysis To Understand Market Opportunities And Threats Mockup PDF
This slide provides a framework for understanding the external environment and identifying potential opportunities and threats to help make informed decisions. The slide covers political, economic, technological and socio cultural factors. Present like a pro with PEST Analysis To Understand Market Opportunities And Threats Mockup PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
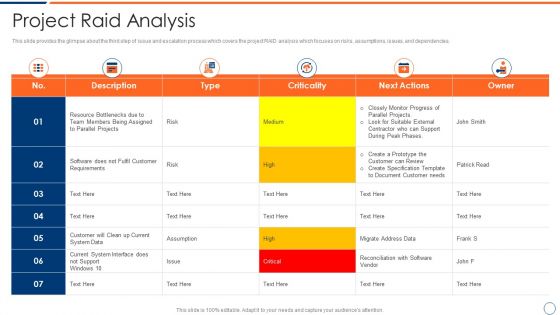
How To Intensify Project Threats Project Raid Analysis Pictures PDF
This slide provides the glimpse about the third step of issue and escalation process which covers the project RAID analysis which focuses on risks, assumptions, issues, and dependencies. Deliver and pitch your topic in the best possible manner with this how to intensify project threats project raid analysis pictures pdf. Use them to share invaluable insights on description, type, criticality, next actions, owner and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
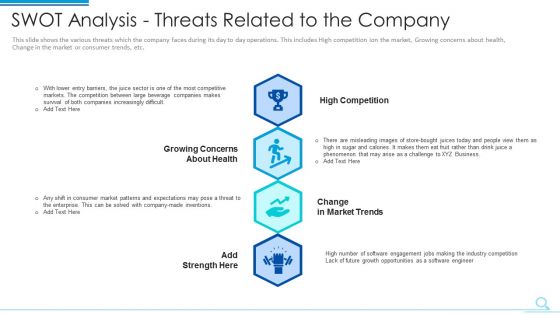
Swot Analysis Threats Related To The Company Template PDF
Presenting swot analysis threats related to the company template pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like high competition, growing concerns about health, change in market trends. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
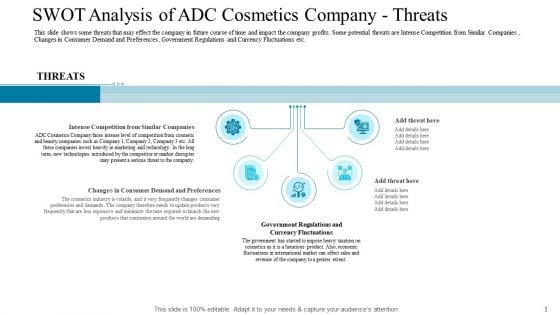
SWOT Analysis Of ADC Cosmetics Company Threats Download PDF
Presenting swot analysis of adc cosmetics company threats download pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like intense competition from similar companies, changes in consumer demand and preferences , government regulations and currency fluctuations. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Stages For Minimizing Internet Security Threats Ideas PDF
Following slide exhibits steps for minimizing security and data breach. It includes major steps such as- malware protection and monitoring, source code assessment etc. Pitch your topic with ease and precision using this stages for minimizing internet security threats ideas pdf. This layout presents information on infrastructure management, cyber analysis, vulnerability management. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
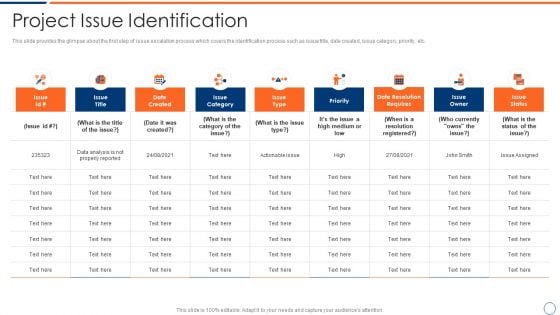
How To Intensify Project Threats Project Issue Identification Information PDF
This slide provides the glimpse about the first step of issue escalation process which covers the identification process such as issue title, date created, issue category, priority, etc. Deliver and pitch your topic in the best possible manner with this how to intensify project threats project issue identification information pdf. Use them to share invaluable insights on issue title, date created, issue category, priority and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Mitigating Cybersecurity Threats And Vulnerabilities Addressing Critical Business Information PDF
This slide provides details regarding business functions recovery as firm needs to retrieve the crucial information based on priorities in various departments and time taken to retrieve the information. Deliver an awe inspiring pitch with this creative mitigating cybersecurity threats and vulnerabilities addressing critical business information pdf bundle. Topics like addressing critical business functions recovery priorities can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user

Mitigating Cybersecurity Threats And Vulnerabilities Evaluating Financial Practices Themes PDF
The firm can track the financial performance by looking the financial practices it follows in order to avoid any early signs of financial distress. Deliver an awe inspiring pitch with this creative mitigating cybersecurity threats and vulnerabilities evaluating financial practices themes pdf bundle. Topics like evaluating financial practices in firm can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Mitigating Cybersecurity Threats And Vulnerabilities Financial Performance Tracking Designs PDF
This slide presents the dashboard which will help firm in tracking the fiscal performance. This dashboard displays revenues and expenses trends and payment received analysis. Deliver and pitch your topic in the best possible manner with this mitigating cybersecurity threats and vulnerabilities financial performance tracking designs pdf. Use them to share invaluable insights on receivables analysis, revenue and expense trends and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Mitigating Cybersecurity Threats And Vulnerabilities Table Of Contents Infographics PDF
Presenting mitigating cybersecurity threats and vulnerabilities table of contents infographics pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like leveraging workforce, budget assessment, dashboard, impact assessment. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Mitigating Cybersecurity Threats And Vulnerabilities Technological Assessment Sample PDF
This slide provides details regarding present management capabilities assessment based on several parameters such as incidents and service requests handling rate, service failure rate, customer satisfaction score, etc. Deliver an awe inspiring pitch with this creative mitigating cybersecurity threats and vulnerabilities technological assessment sample pdf bundle. Topics like Industry Standard, Firms Standard, Client Onboarding, Service Failure Rate can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
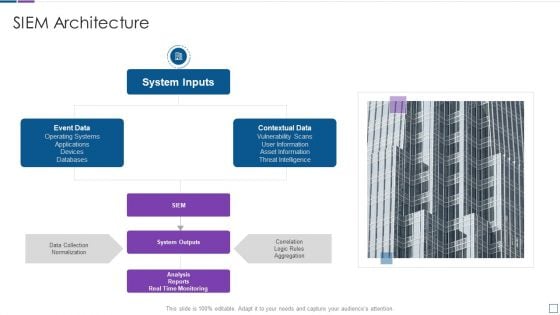
Real Time Assessment Of Security Threats SIEM Architecture Sample PDF
This is a real time assessment of security threats siem architecture sample pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like system inputs, event data, contextual data, system outputs. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
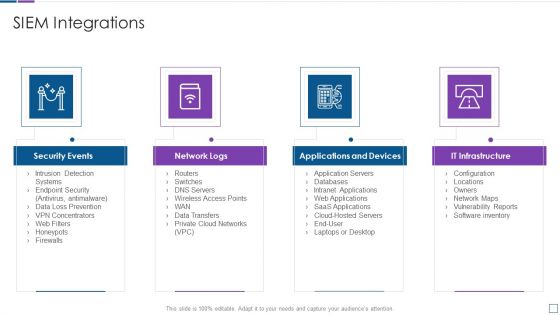
Real Time Assessment Of Security Threats SIEM Integrations Slides PDF
Presenting real time assessment of security threats siem integrations slides pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like security events, network logs, applications and devices, it infrastructure. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Purpose Of IT Threats Response Playbook Professional PDF
This is a Purpose Of IT Threats Response Playbook Professional PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Standardized Cybersecurity, Future Security, Appropriate Manner. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Data Governance Threats Management Process Ppt Icon Templates PDF
This slide covers governance approach process to manage data risk. It includes steps such as identify risks, develop policies, execute control, monitor and report on control outputs. Presenting Data Governance Threats Management Process Ppt Icon Templates PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Identify Risk, Develop Policy, Develop Control, Execute Control. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
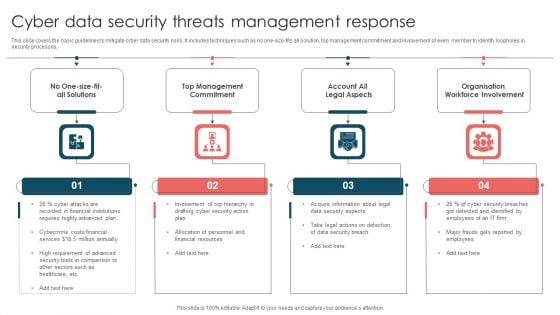
Cyber Data Security Threats Management Response Ppt Summary Skills PDF
This slide covers the basic guidelines to mitigate cyber data security risks. It includes techniques such as no one-size-fits all solution, top management commitment and involvement of every member to identify loopholes in security processes. Presenting Cyber Data Security Threats Management Response Ppt Summary Skills PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Organisation Workforce Involvement, Account Legal Aspects, Top Management Commitment. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

 Home
Home