Threats Actors
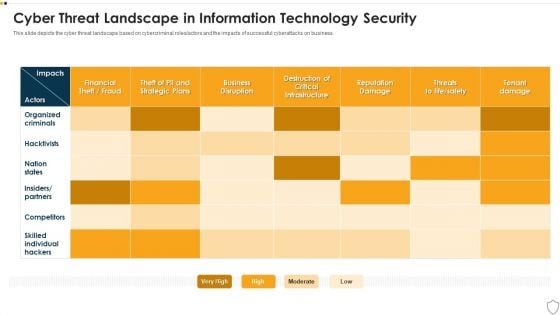
IT Security Cyber Threat Landscape In Information Technology Security Download PDF
This slide depicts the cyber threat landscape based on cybercriminal roles or actors and the impacts of successful cyberattacks on business. Deliver and pitch your topic in the best possible manner with this it security cyber threat landscape in information technology security download pdf. Use them to share invaluable insights on business, competitors, reputation damage, organized criminals and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
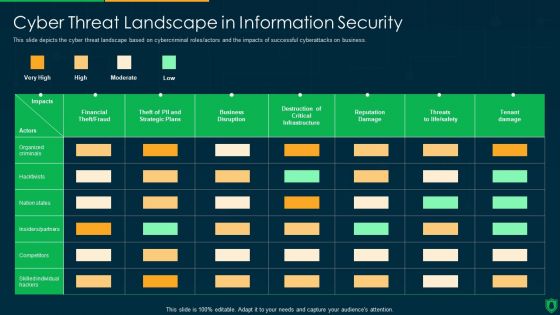
Info Security Cyber Threat Landscape In Information Security Ppt PowerPoint Presentation File Slides PDF
This slide depicts the cyber threat landscape based on cybercriminal roles or actors and the impacts of successful cyberattacks on business. Deliver and pitch your topic in the best possible manner with this info security cyber threat landscape in information security ppt powerpoint presentation file slides pdf. Use them to share invaluable insights on business disruption, financial theft, fraud, reputation damage, tenant damage and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
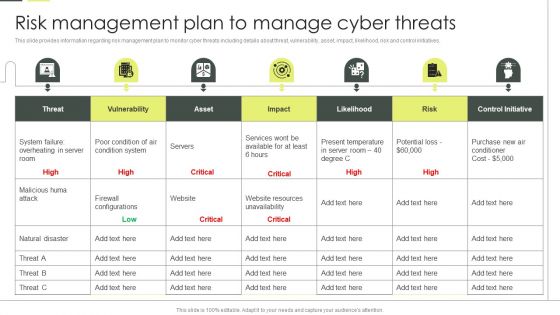
Building An IT Strategy Plan For Business Expansion Risk Management Plan To Manage Cyber Threats Professional PDF
This slide provides information regarding risk management plan to monitor cyber threats including details about threat, vulnerability, asset, impact, likelihood, risk and control initiatives. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Building An IT Strategy Plan For Business Expansion Risk Management Plan To Manage Cyber Threats Professional PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Building An IT Strategy Plan For Business Expansion Risk Management Plan To Manage Cyber Threats Professional PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.

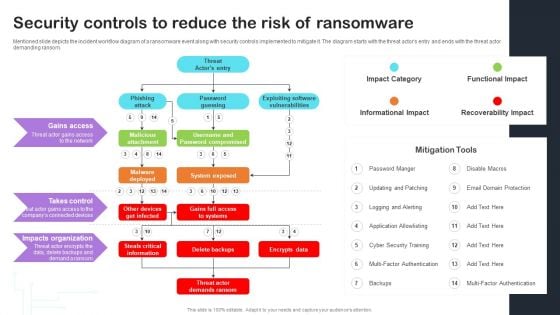
Security Controls To Reduce The Risk Improving Cybersecurity With Incident Pictures PDF
Mentioned slide depicts the incident workflow diagram of a ransomware event along with security controls implemented to mitigate it. The diagram starts with the threat actors entry and ends with the threat actor demanding ransom.Are you searching for a Security Controls To Reduce The Risk Improving Cybersecurity With Incident Pictures PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you ve put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Security Controls To Reduce The Risk Improving Cybersecurity With Incident Pictures PDF from Slidegeeks today.
Cyber Risks And Incident Response Playbook Security Controls To Reduce The Risk Of Ransomware Themes PDF
Mentioned slide depicts the incident workflow diagram of a ransomware event along with security controls implemented to mitigate it. The diagram starts with the threat actors entry and ends with the threat actor demanding ransom. Take your projects to the next level with our ultimate collection of Cyber Risks And Incident Response Playbook Security Controls To Reduce The Risk Of Ransomware Themes PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors theyll make your projects stand out from the rest.
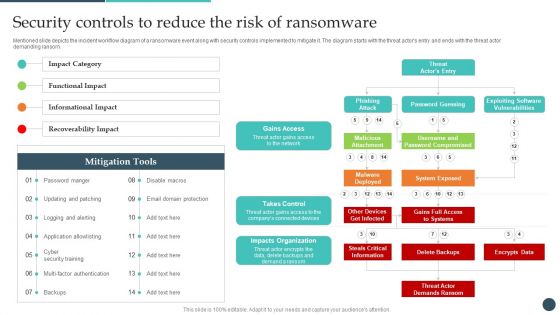
Safety Breach Response Playbook Security Controls To Reduce The Risk Topics PDF
Mentioned slide depicts the incident workflow diagram of a ransomware event along with security controls implemented to mitigate it. The diagram starts with the threat actors entry and ends with the threat actor demanding ransom. Presenting this PowerPoint presentation, titled Safety Breach Response Playbook Security Controls To Reduce The Risk Topics PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Safety Breach Response Playbook Security Controls To Reduce The Risk Topics PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Safety Breach Response Playbook Security Controls To Reduce The Risk Topics PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.
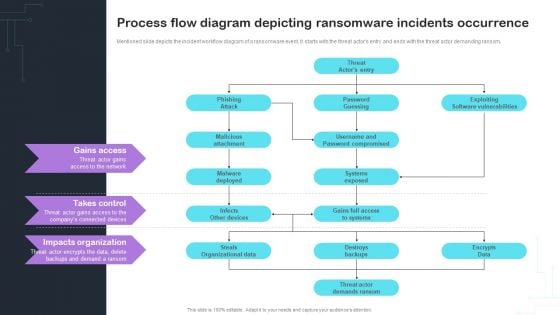
Cyber Risks And Incident Response Playbook Process Flow Diagram Depicting Ransomware Incidents Occurrence Structure PDF
Mentioned slide depicts the incident workflow diagram of a ransomware event. It starts with the threat actors entry and ends with the threat actor demanding ransom. Slidegeeks has constructed Cyber Risks And Incident Response Playbook Process Flow Diagram Depicting Ransomware Incidents Occurrence Structure PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.
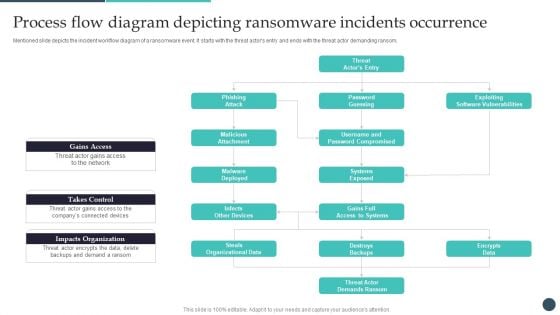
Safety Breach Response Playbook Process Flow Diagram Depicting Ransomware Ideas PDF
Mentioned slide depicts the incident workflow diagram of a ransomware event. It starts with the threat actors entry and ends with the threat actor demanding ransom. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Safety Breach Response Playbook Process Flow Diagram Depicting Ransomware Ideas PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Safety Breach Response Playbook Process Flow Diagram Depicting Ransomware Ideas PDF today and make your presentation stand out from the rest.
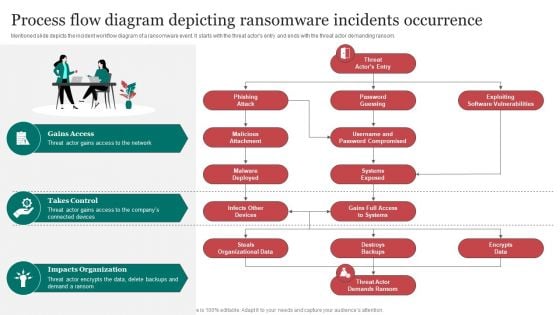
Process Flow Diagram Depicting Ransomware Incidents Occurrence Infographics PDF
Mentioned slide depicts the incident workflow diagram of a ransomware event. It starts with the threat actors entry and ends with the threat actor demanding ransom.Explore a selection of the finest Process Flow Diagram Depicting Ransomware Incidents Occurrence Infographics PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Process Flow Diagram Depicting Ransomware Incidents Occurrence Infographics PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Key Factors Data Security For A Business Ppt PowerPoint Presentation Styles Layouts PDF
Persuade your audience using this key factors data security for a business ppt powerpoint presentation styles layouts pdf. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including risks related to lack of visibility, risks related to human actions, key threat actors of the data risk. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
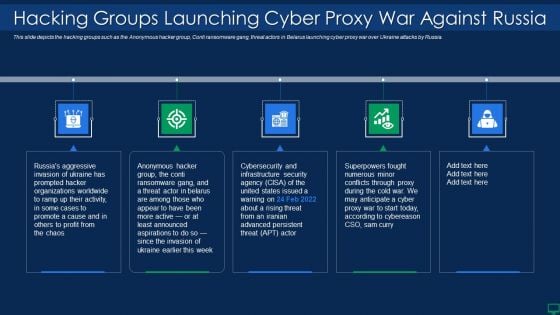
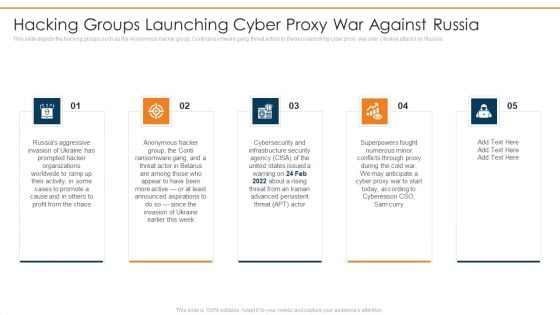
Russian Cyber Attacks On Ukraine IT Hacking Groups Launching Cyber Rules PDF
This slide depicts the hacking groups such as the Anonymous hacker group, Conti ransomware gang, threat actors in Belarus launching cyber proxy war over Ukraine attacks by Russia. Presenting russian cyber attacks on ukraine it hacking groups launching cyber rules pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like organizations, security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Data Wiper Spyware Attack Hacking Groups Launching Cyber Proxy War Against Russia Portrait PDF
This slide depicts the hacking groups such as the Anonymous hacker group, Conti ransomware gang, threat actors in Belarus launching cyber proxy war over Ukraine attacks by Russia.This is a data wiper spyware attack hacking groups launching cyber proxy war against russia portrait pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like infrastructure security, superpowers fought, conflicts through proxy You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Blockchain Platform For Industries Threat Detection Process Flow Topics PDF
This slide showcases industrial blockchain risk identification process flow. It provides information about designer, blockchain, bad actor, manufacturer, software, fingerprint, etc. Pitch your topic with ease and precision using this Blockchain Platform For Industries Threat Detection Process Flow Topics PDF. This layout presents information on Blockchain, Designer, Manufacturer. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
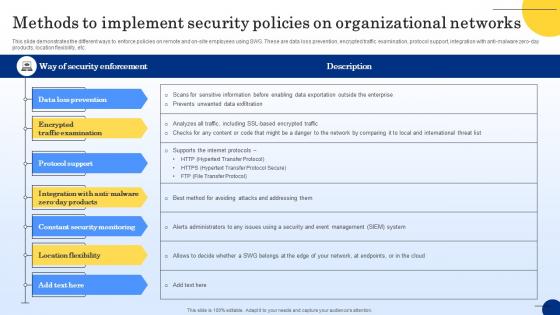
Methods To Implement Security Policies On Web Threat Protection System
This slide demonstrates the different ways to enforce policies on remote and on-site employees using SWG. These are data loss prevention, encrypted traffic examination, protocol support, integration with anti-malware zero-day products, location flexibility, etc. Are you searching for a Methods To Implement Security Policies On Web Threat Protection System that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Methods To Implement Security Policies On Web Threat Protection System from Slidegeeks today. This slide demonstrates the different ways to enforce policies on remote and on-site employees using SWG. These are data loss prevention, encrypted traffic examination, protocol support, integration with anti-malware zero-day products, location flexibility, etc.

Industry Wise Market Segmentation Of SWG Web Threat Protection System
This slide demonstrates the contribution of different industries in growth of Secure Web Gateway market. The purpose of this slide is to represent the industry wise market share of different sectors such as BFSI, IT and telecom, retail and e-Commerce, etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Industry Wise Market Segmentation Of SWG Web Threat Protection System was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Industry Wise Market Segmentation Of SWG Web Threat Protection System This slide demonstrates the contribution of different industries in growth of Secure Web Gateway market. The purpose of this slide is to represent the industry wise market share of different sectors such as BFSI, IT and telecom, retail and e-Commerce, etc.
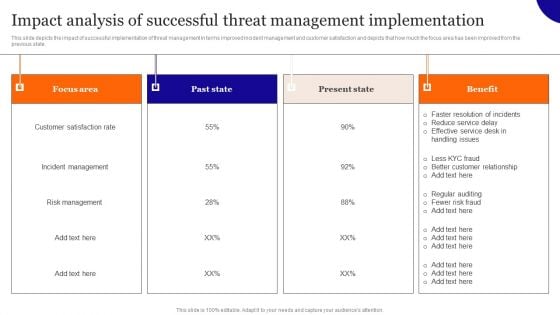
Impact Analysis Of Successful Threat Management Implementation Background PDF
This slide depicts the impact of successful implementation of threat management in terms improved incident management and customer satisfaction and depicts that how much the focus area has been improved from the previous state. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Impact Analysis Of Successful Threat Management Implementation Background PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Impact Analysis Of Successful Threat Management Implementation Background PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers
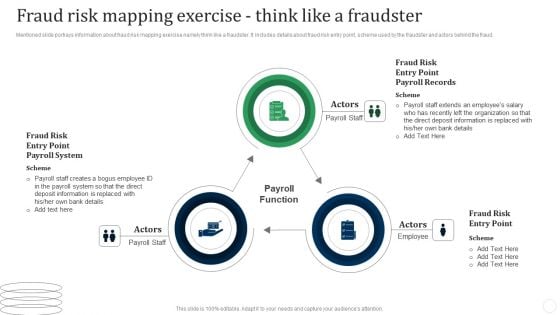
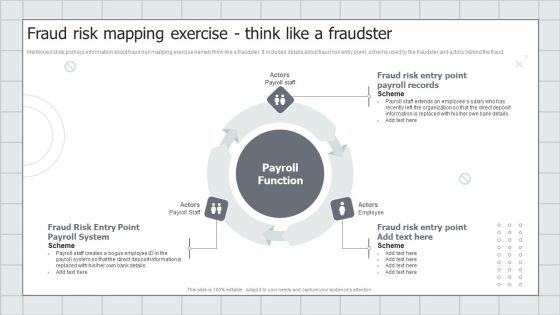
Fraud Risk Mapping Exercise Think Like A Fraudster Fraud Threat Administration Guide Rules PDF
Mentioned slide portrays information about fraud risk mapping exercise namely think like a fraudster. It includes details about fraud risk entry point, scheme used by the fraudster and actors behind the fraud.Presenting Fraud Risk Mapping Exercise Think Like A Fraudster Fraud Threat Administration Guide Rules PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Deposit Information, Staff Creates, Payroll Function. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
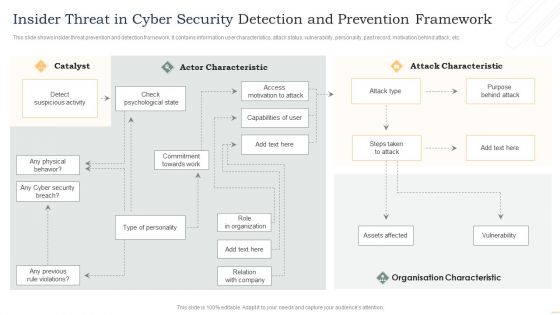
Insider Threat In Cyber Security Detection And Prevention Framework Information PDF
This slide shows insider threat prevention and detection framework. It contains information user characteristics, attack status, vulnerability, personality, past record, motivation behind attack, etc. Presenting Insider Threat In Cyber Security Detection And Prevention Framework Information PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Actor Characteristic, Attack Characteristic, Organisation Characteristic. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Series Of Cyber Security Attacks Against Ukraine 2022 Hacking Groups Launching Cyber Proxy War Against Russia Icons PDF
This slide depicts the hacking groups such as the anonymous hacker group, conti ransomware gang, threat actors in belarus launching cyber proxy war over ukraine attacks by russia. Find highly impressive Series Of Cyber Security Attacks Against Ukraine 2022 Hacking Groups Launching Cyber Proxy War Against Russia Icons PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Series Of Cyber Security Attacks Against Ukraine 2022 Hacking Groups Launching Cyber Proxy War Against Russia Icons PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.
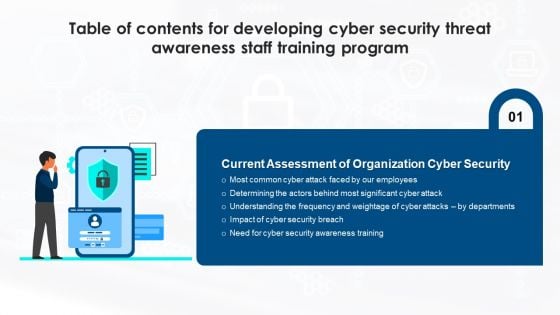
Table Of Contents For Developing Cyber Security Threat Awareness Staff Training Program Slide Microsoft PDF
Deliver and pitch your topic in the best possible manner with this Table Of Contents For Developing Cyber Security Threat Awareness Staff Training Program Slide Microsoft PDF. Use them to share invaluable insights on Current Assessment, Determining Actors, Understanding Frequency and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
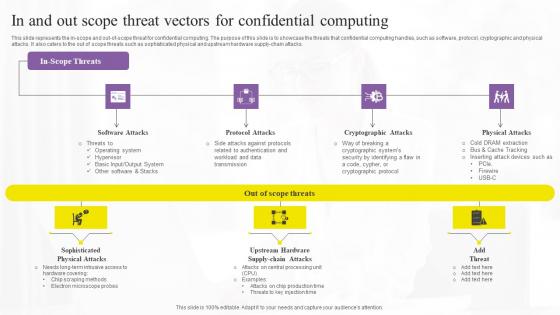
In And Out Scope Threat Vectors For Confidential Computing Technologies Infographics Pdf
This slide represents the in-scope and out-of-scope threat for confidential computing. The purpose of this slide is to showcase the threats that confidential computing handles, such as software, protocol, cryptographic and physical attacks. It also caters to the out of scope threats such as sophisticated physical and upstream hardware supply-chain attacks. Are you searching for a In And Out Scope Threat Vectors For Confidential Computing Technologies Infographics Pdf that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download In And Out Scope Threat Vectors For Confidential Computing Technologies Infographics Pdf from Slidegeeks today. This slide represents the in-scope and out-of-scope threat for confidential computing. The purpose of this slide is to showcase the threats that confidential computing handles, such as software, protocol, cryptographic and physical attacks. It also caters to the out of scope threats such as sophisticated physical and upstream hardware supply-chain attacks.

Identify Threat And Vulnerabilities Within Information System Ppt PowerPoint Presentation File Example PDF
The following slide highlights threats and vulnerabilities within companys information system to prevent adverse impact and severity. It includes elements such as unclear storage mechanism, inappropriate structure to privilege access, no framework to monitor user behavior etc. Are you searching for a Identify Threat And Vulnerabilities Within Information System Ppt PowerPoint Presentation File Example PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal. With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Identify Threat And Vulnerabilities Within Information System Ppt PowerPoint Presentation File Example PDF from Slidegeeks today.

Impact Of Secure Web Gateway On Application Security Web Threat Protection System
This slide represents the various factors which showcase the improvement of application security after adopting SWG. The parameters discussed are enhanced protection against web-based attacks, content filtering, policy enforcement, Data Loss Prevention, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Impact Of Secure Web Gateway On Application Security Web Threat Protection System template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Impact Of Secure Web Gateway On Application Security Web Threat Protection System that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide represents the various factors which showcase the improvement of application security after adopting SWG. The parameters discussed are enhanced protection against web-based attacks, content filtering, policy enforcement, Data Loss Prevention, etc.
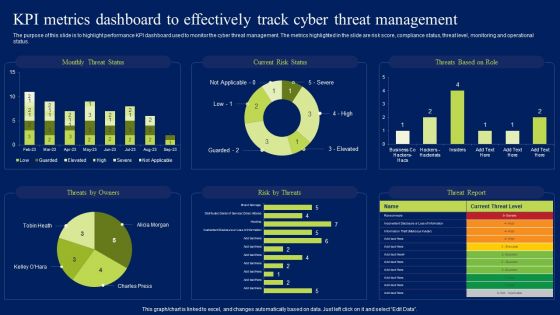
Kpi Metrics Dashboard To Effectively Track Cyber Threat Management Ppt Styles Guide PDF
The purpose of this slide is to highlight performance KPI dashboard used to monitor the cyber threat management. The metrics highlighted in the slide are risk score, compliance status, threat level, monitoring and operational status. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Kpi Metrics Dashboard To Effectively Track Cyber Threat Management Ppt Styles Guide PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Kpi Metrics Dashboard To Effectively Track Cyber Threat Management Ppt Styles Guide PDF.

IT Vulnerabilities With Threat Source And Action Organizations Risk Management And IT Security Download PDF
The following slide highlights the information technology vulnerabilities which includes the thread source from terminated employees and unauthorized users and threat action. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our IT Vulnerabilities With Threat Source And Action Organizations Risk Management And IT Security Download PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into IT Vulnerabilities With Threat Source And Action Organizations Risk Management And IT Security Download PDF.

IT Security Automation Systems Guide Time To Fix Security Threat With Manual Testing Topics PDF
This slide highlights the time to fix the security threat and error with manual testing in bar graph format. It covers key takeaways which explains how much percent of error are fixed in 1 to 3 hour, 3 to 6 hour and working day etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our IT Security Automation Systems Guide Time To Fix Security Threat With Manual Testing Topics PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into IT Security Automation Systems Guide Time To Fix Security Threat With Manual Testing Topics PDF
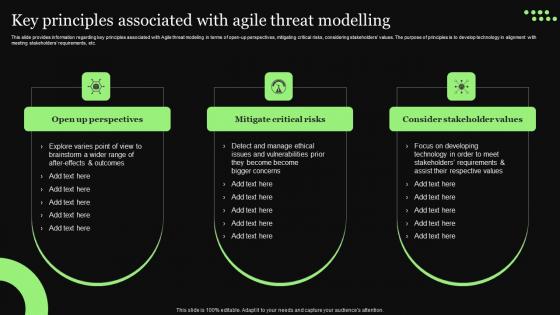
Ethical Technology Utilization Key Principles Associated With Agile Threat Modelling Ideas Pdf
This slide provides information regarding key principles associated with Agile threat modeling in terms of open up perspectives, mitigating critical risks, considering stakeholders values. The purpose of principles is to develop technology in alignment with meeting stakeholders requirements, etc. Are you searching for a Ethical Technology Utilization Key Principles Associated With Agile Threat Modelling Ideas Pdf that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Ethical Technology Utilization Key Principles Associated With Agile Threat Modelling Ideas Pdf from Slidegeeks today. This slide provides information regarding key principles associated with Agile threat modeling in terms of open up perspectives, mitigating critical risks, considering stakeholders values. The purpose of principles is to develop technology in alignment with meeting stakeholders requirements, etc.
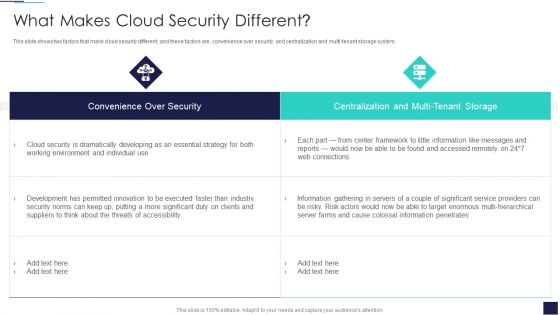
Cloud Information Security What Makes Cloud Security Different Ppt Inspiration Styles PDF
This slide shows two factors that make cloud security different, and these factors are, convenience over security, and centralization and multi-tenant storage system. Deliver an awe inspiring pitch with this creative Cloud Information Security What Makes Cloud Security Different Ppt Inspiration Styles PDF bundle. Topics like Cloud Security, Threats Accessibility, Risk Actors can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Overview Of Key Insights On Data Theft In Health Care Sector Demonstration PDF
This slide covers findings for loss of data in health and medical sector. It includes data patterns, motives behind data theft, percentage of data compromised, etc. Showcasing this set of slides titled Overview Of Key Insights On Data Theft In Health Care Sector Demonstration PDF. The topics addressed in these templates are Top Threat Patterns, Actor Motives, Data Compromised. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
SWOT Analysis Successful Rebranding Guide Icons PDF
Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward SWOT Analysis Successful Rebranding Guide Icons PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Swot Analysis Successful Rebranding Guide Icons PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.

Anti Scam Playbook Fraud Risk Mapping Exercise Think Like A Fraudster Rules PDF
Mentioned slide portrays information about fraud risk mapping exercise namely think like a fraudster. It includes details about fraud risk entry point, scheme used by the fraudster and actors behind the fraud. Presenting Anti Scam Playbook Fraud Risk Mapping Exercise Think Like A Fraudster Rules PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like System, Risk, Information, Organization. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
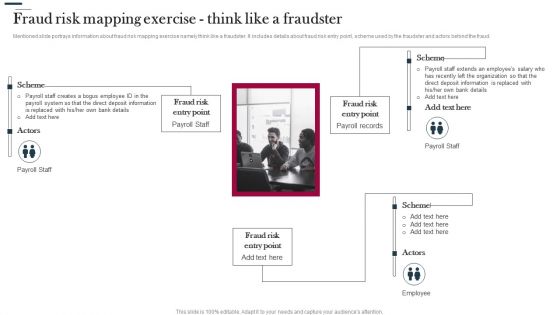
Various Strategies To Prevent Business Fraud Risk Mapping Exercise Think Like A Fraudster Summary PDF
Mentioned slide portrays information about fraud risk mapping exercise namely think like a fraudster. It includes details about fraud risk entry point, scheme used by the fraudster and actors behind the fraud. This is a Various Strategies To Prevent Business Fraud Risk Mapping Exercise Think Like A Fraudster Summary PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Fraud Risk, Entry Point, Payroll System. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
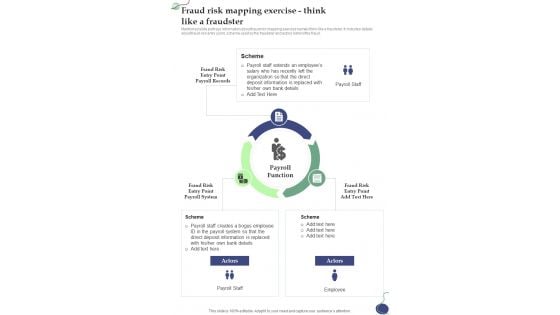
Fraud Risk Mapping Exercise Think Like A Fraudster One Pager Sample Example Document
Mentioned slide portrays information about fraud risk mapping exercise namely think like a fraudster. It includes details about fraud risk entry point, scheme used by the fraudster and actors behind the fraud. Presenting you an exemplary Fraud Risk Mapping Exercise Think Like A Fraudster One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Fraud Risk Mapping Exercise Think Like A Fraudster One Pager Sample Example Document brilliant piece now.
Fraud Avoidance Playbook Fraud Risk Mapping Exercise Think Like A Fraudster Structure PDF
Mentioned slide portrays information about fraud risk mapping exercise namely think like a fraudster. It includes details about fraud risk entry point, scheme used by the fraudster and actors behind the fraud. This is a Fraud Avoidance Playbook Fraud Risk Mapping Exercise Think Like A Fraudster Structure PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Payroll Function, Payroll System, Information. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Purpose Of Scam Inquiry And Response Playbook Demonstration PDF

SWOT Analysis Of Fitness Centers In Gym And Fitness Business Industry Ideas PDF
This slide shows the analysis of strengths, weakness, opportunities and threats of a gym and fitness center. It includes strengths such as ideal gym location, affordable prices and threats such as strong competitors etc. Persuade your audience using this SWOT Analysis Of Fitness Centers In Gym And Fitness Business Industry Ideas PDF. This PPT design covers Four stages, thus making it a great tool to use. It also caters to a variety of topics including Good Reputation Among Clients, Lack Of Effective Advertisement, Make Improvements . Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
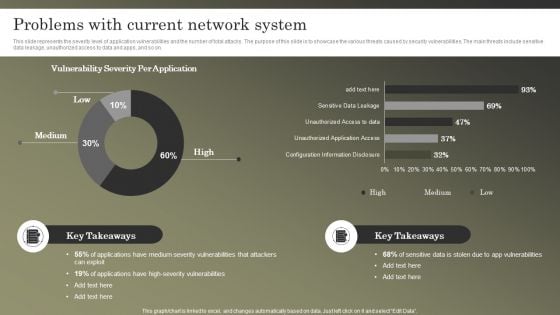
Cybersecurity Operations Cybersecops Problems With Current Network System Formats PDF
This slide represents the severity level of application vulnerabilities and the number of total attacks. The purpose of this slide is to showcase the various threats caused by security vulnerabilities. The main threats include sensitive data leakage, unauthorized access to data and apps, and so on. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Cybersecurity Operations Cybersecops Problems With Current Network System Formats PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Cybersecurity Operations Cybersecops Problems With Current Network System Formats PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.

Website Security Management Strategic Plan Step By Step Guide Slides PDF
Following slide outlines website security action plan to assure safety from external threats and cyber crimes. It include steps such as strong passwords, new configurations, mitigate DDOS, safety from SQL, hide website version etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Website Security Management Strategic Plan Step By Step Guide Slides PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Website Security Management Strategic Plan Step By Step Guide Slides PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers Following slide outlines website security action plan to assure safety from external threats and cyber crimes. It include steps such as strong passwords, new configurations, mitigate DDOS, safety from SQL, hide website version etc.
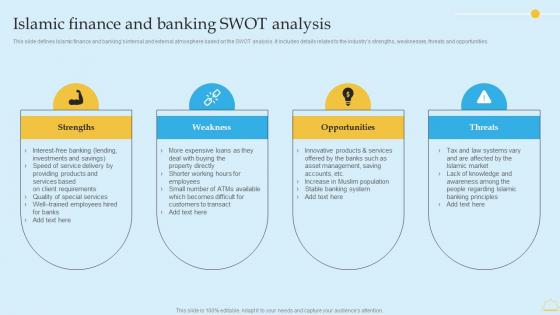
Islamic Finance And Banking SWOT Analysis In Depth Analysis Of Islamic Banking Information PDF
This slide defines Islamic finance and bankings internal and external atmosphere based on the SWOT analysis. It includes details related to the industrys strengths, weaknesses, threats and opportunities. Are you searching for a Islamic Finance And Banking SWOT Analysis In Depth Analysis Of Islamic Banking Information PDF that is uncluttered, straightforward, and original It is easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, it is perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Islamic Finance And Banking SWOT Analysis In Depth Analysis Of Islamic Banking Information PDF from Slidegeeks today. This slide defines Islamic finance and bankings internal and external atmosphere based on the SWOT analysis. It includes details related to the industrys strengths, weaknesses, threats and opportunities.
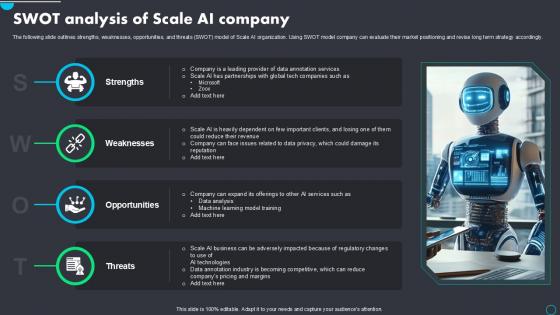
SWOT Analysis Of Scale AI Company Implementing Scale AI PPT Presentation AI SS V
The following slide outlines strengths, weaknesses, opportunities, and threats SWOT model of Scale AI organization. Using SWOT model company can evaluate their market positioning and revise long term strategy accordingly. Are you searching for a SWOT Analysis Of Scale AI Company Implementing Scale AI PPT Presentation AI SS V that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download SWOT Analysis Of Scale AI Company Implementing Scale AI PPT Presentation AI SS V from Slidegeeks today. The following slide outlines strengths, weaknesses, opportunities, and threats SWOT model of Scale AI organization. Using SWOT model company can evaluate their market positioning and revise long term strategy accordingly.
SWOT Analysis Of The Company Ppt Icon Graphics Design PDF
This slide shows companys strategic planning technique strengths, weaknesses, opportunities, and threats related to the business. Are you searching for a SWOT Analysis Of The Company Ppt Icon Graphics Design PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download SWOT Analysis Of The Company Ppt Icon Graphics Design PDF from Slidegeeks today.

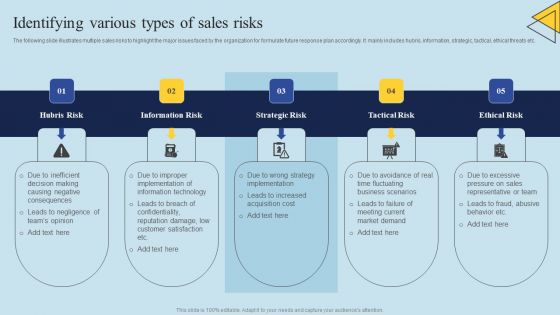
Assessing Sales Risks Identifying Various Types Of Sales Risks Brochure PDF
The following slide illustrates multiple sales risks to highlight the major issues faced by the organization for formulate future response plan accordingly. It mainly includes hubris, information, strategic, tactical, ethical threats etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Assessing Sales Risks Identifying Various Types Of Sales Risks Brochure PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Assessing Sales Risks Identifying Various Types Of Sales Risks Brochure PDF. The following slide illustrates multiple sales risks to highlight the major issues faced by the organization for formulate future response plan accordingly. It mainly includes hubris, information, strategic, tactical, ethical threats etc.

Comprehensive Swot Analysis Group Tour Operator Business Plan Go To Market Strategy Background Pdf
The purpose of this slide is to identify the industry strengths, weaknesses, opportunities, and threats related to the business. It guides the agency to build on what it does well, address what theyre lacking, seize new openings, and minimize risks. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Comprehensive Swot Analysis Group Tour Operator Business Plan Go To Market Strategy Background Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Comprehensive Swot Analysis Group Tour Operator Business Plan Go To Market Strategy Background Pdf that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers The purpose of this slide is to identify the industry strengths, weaknesses, opportunities, and threats related to the business. It guides the agency to build on what it does well, address what theyre lacking, seize new openings, and minimize risks.

Comprehensive Swot Analysis Of House Flipping Business Real Estate Renovation Slides Pdf
The purpose of this slide is to identify the industry strengths, weaknesses, opportunities, and threats related to the business. It guides the company to build on what it does well, address what theyre lacking, seize new openings, and minimize risks. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Comprehensive Swot Analysis Of House Flipping Business Real Estate Renovation Slides Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Comprehensive Swot Analysis Of House Flipping Business Real Estate Renovation Slides Pdf that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers. The purpose of this slide is to identify the industry strengths, weaknesses, opportunities, and threats related to the business. It guides the company to build on what it does well, address what theyre lacking, seize new openings, and minimize risks.
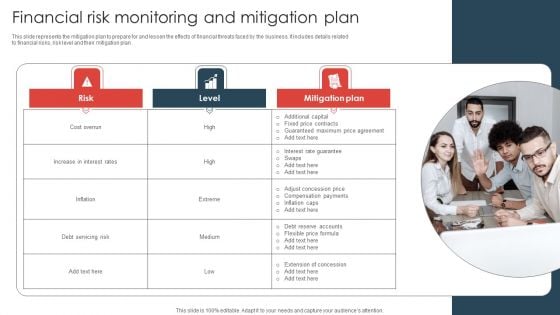
Strategic Risk Management Plan Financial Risk Monitoring And Mitigation Plan Formats PDF
This slide represents the mitigation plan to prepare for and lessen the effects of financial threats faced by the business. It includes details related to financial risks, risk level and their mitigation plan.Are you searching for a Strategic Risk Management Plan Financial Risk Monitoring And Mitigation Plan Formats PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you ve put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Strategic Risk Management Plan Financial Risk Monitoring And Mitigation Plan Formats PDF from Slidegeeks today.
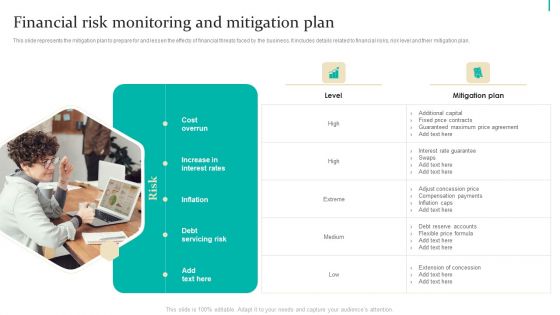
Enterprise Risk Management Financial Risk Monitoring And Mitigation Plan Microsoft PDF
This slide represents the mitigation plan to prepare for and lessen the effects of financial threats faced by the business. It includes details related to financial risks, risk level and their mitigation plan. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Enterprise Risk Management Financial Risk Monitoring And Mitigation Plan Microsoft PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Enterprise Risk Management Financial Risk Monitoring And Mitigation Plan Microsoft PDF.
Determining Risks In Sales Administration Procedure Identifying Various Types Of Sales Risks Guidelines PDF
The following slide illustrates multiple sales risks to highlight the major issues faced by the organization for formulate future response plan accordingly. It mainly includes hubris, information, strategic, tactical, ethical threats etc. Are you searching for a Determining Risks In Sales Administration Procedure Identifying Various Types Of Sales Risks Guidelines PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal. With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Determining Risks In Sales Administration Procedure Identifying Various Types Of Sales Risks Guidelines PDF from Slidegeeks today.
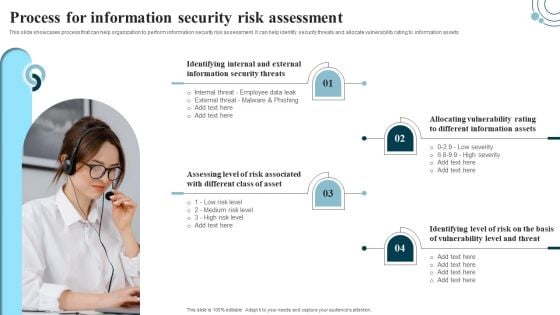
Developing IT Security Strategy Process For Information Security Risk Assessment Graphics PDF
This slide showcases process that can help organization to perform information security risk assessment. It can help identify security threats and allocate vulnerability rating to information assets. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Developing IT Security Strategy Process For Information Security Risk Assessment Graphics PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Developing IT Security Strategy Process For Information Security Risk Assessment Graphics PDF.

International Design And Architecture Firm SWOT Analysis Ppt Professional File Formats PDF
This slide highlights the SWOT analysis of the architecture company which includes strengths as 30 years of practice experience, weakness as External financing required, threats as high competition. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our International Design And Architecture Firm SWOT Analysis Ppt Professional File Formats PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into International Design And Architecture Firm SWOT Analysis Ppt Professional File Formats PDF.

SWOT Analysis Web Design And Development Company Profile Information PDF
his slide focuses on strengths, weakness, opportunities and threats to evaluate competitive position of our web design company which includes diverse services, global presence, projected market growth, etc Are you searching for a SWOT Analysis Web Design And Development Company Profile Information PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort youve put in, this template is ideal. With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download SWOT Analysis Web Design And Development Company Profile Information PDF from Slidegeeks today.
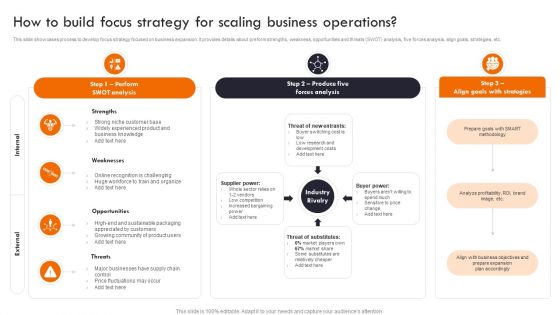
Gaining Competitive Edge How To Build Focus Strategy For Scaling Business Operations Structure PDF
This slide showcases process to develop focus strategy focused on business expansion. It provides details about preform strengths, weakness, opportunities and threats SWOT analysis, five forces analysis, align goals, strategies, etc. Are you searching for a Gaining Competitive Edge How To Build Focus Strategy For Scaling Business Operations Structure PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort youve put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Gaining Competitive Edge How To Build Focus Strategy For Scaling Business Operations Structure PDF from Slidegeeks today.

Yearly Brand Promotion Plan SWOT Analysis For Successful Brand Building Ideas PDF
This slide represents SWOT analysis for brand. It assess strength, weakness, profundities and threats of a brand that enables business to study each criteria and develop strategies accordingly. Are you searching for a Yearly Brand Promotion Plan SWOT Analysis For Successful Brand Building Ideas PDF that is uncluttered, straightforward, and original. Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort youve put in, this template is ideal. With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Yearly Brand Promotion Plan SWOT Analysis For Successful Brand Building Ideas PDF from Slidegeeks today.
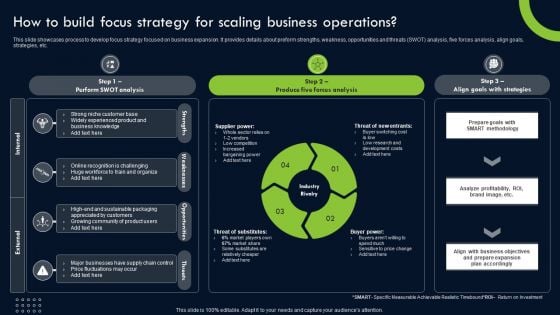
Transforming Sustainability Into Competitive How To Build Focus Strategy For Scaling Rules PDF
This slide showcases process to develop focus strategy focused on business expansion. It provides details about preform strengths, weakness, opportunities and threats SWOT analysis, five forces analysis, align goals, strategies, etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Transforming Sustainability Into Competitive How To Build Focus Strategy For Scaling Rules PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Transforming Sustainability Into Competitive How To Build Focus Strategy For Scaling Rules PDF.
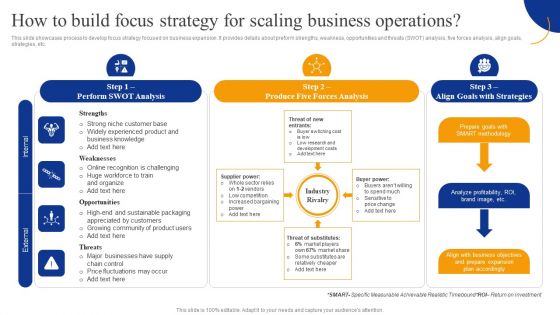
How To Build Focus Strategy For Scaling Business Operations Strategic Management For Competitive Topics PDF
This slide showcases process to develop focus strategy focused on business expansion. It provides details about preform strengths, weakness, opportunities and threats SWOT analysis, five forces analysis, align goals, strategies, etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our How To Build Focus Strategy For Scaling Business Operations Strategic Management For Competitive Topics PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into How To Build Focus Strategy For Scaling Business Operations Strategic Management For Competitive Topics PDF
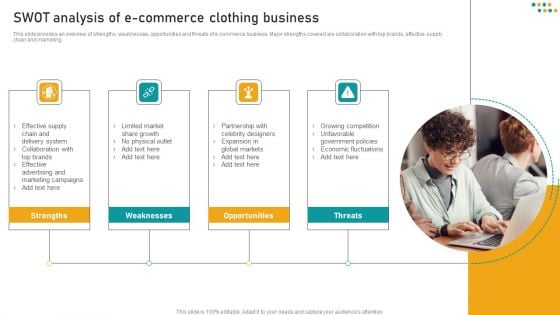
E Commerce Business SWOT Analysis Of E Commerce Clothing Business Microsoft PDF
This slide provides an overview of strengths, weaknesses, opportunities and threats of e-commerce business. Major strengths covered are collaboration with top brands, effective supply chain and marketing. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our E Commerce Business SWOT Analysis Of E Commerce Clothing Business Microsoft PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into E Commerce Business SWOT Analysis Of E Commerce Clothing Business Microsoft PDF.
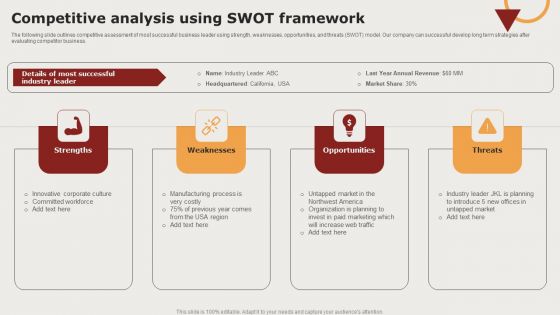
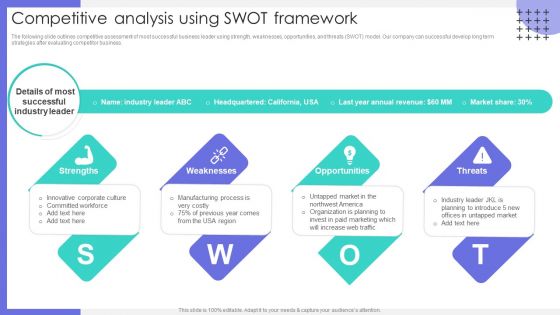
Creating Positioning Techniques For Market Research Competitive Analysis Using Swot Framework Structure Template PDF
The following slide outlines competitive assessment of most successful business leader using strength, weaknesses, opportunities, and threats SWOT model. Our company can successful develop long term strategies after evaluating competitor business. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Creating Positioning Techniques For Market Research Competitive Analysis Using Swot Framework Structure Template PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Creating Positioning Techniques For Market Research Competitive Analysis Using Swot Framework Structure Template PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.
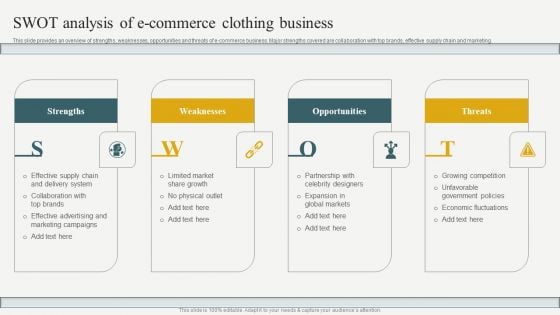
Evaluating Financial Position Of E Commerce Company SWOT Analysis Of E Commerce Clothing Business Professional PDF
This slide provides an overview of strengths, weaknesses, opportunities and threats of e-commerce business. Major strengths covered are collaboration with top brands, effective supply chain and marketing. Are you searching for a Evaluating Financial Position Of E Commerce Company SWOT Analysis Of E Commerce Clothing Business Professional PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal. With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Evaluating Financial Position Of E Commerce Company SWOT Analysis Of E Commerce Clothing Business Professional PDF from Slidegeeks today.
Cyber Attack Incident Tracking Dashboard Ppt PowerPoint Presentation File Styles PDF
The following slide depicts the number of cyber-attacks incurred during year end to monitor security trends. It includes elements such as prevented, allowed attacks, additional threats detected, number of infected hosts and malicious files etc. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Cyber Attack Incident Tracking Dashboard Ppt PowerPoint Presentation File Styles PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Cyber Attack Incident Tracking Dashboard Ppt PowerPoint Presentation File Styles PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.
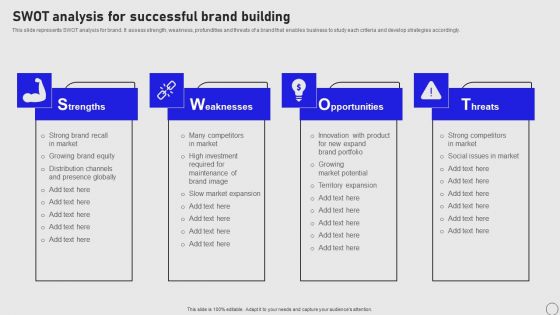
Implementing Annual Brand Marketing Strategy SWOT Analysis For Successful Brand Building Sample PDF
This slide represents SWOT analysis for brand. It assess strength, weakness, profundities and threats of a brand that enables business to study each criteria and develop strategies accordingly. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Implementing Annual Brand Marketing Strategy SWOT Analysis For Successful Brand Building Sample PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Implementing Annual Brand Marketing Strategy SWOT Analysis For Successful Brand Building Sample PDF
Competitive Analysis Using Swot Framework Ppt Backgrounds PDF


 Continue with Email
Continue with Email

 Home
Home


































