Transportation Safety
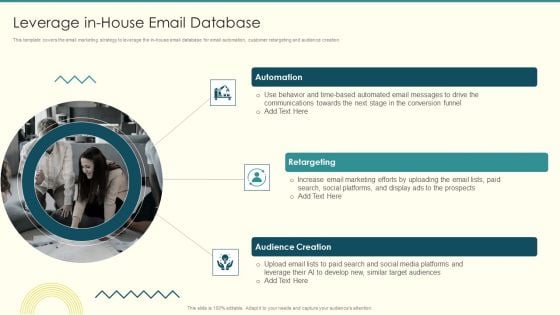
Security And Performance Digital Marketing Leverage Inhouse Email Database Introduction PDF
This template covers the email marketing strategy to leverage the in house email database for email automation, customer retargeting and audience creation. Presenting Security And Performance Digital Marketing Leverage Inhouse Email Database Introduction PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Communications Towards, Automated Messages, Social Platforms. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security And Performance Digital Marketing Optimize Onpage SEO Include ALT Tags For Images Infographics PDF
This template covers search engine optimization guidelines for images. It also depicts that Alt Attributes must be added at backend of the images to assists search engine crawlers in indexing. This is a Security And Performance Digital Marketing Optimize Onpage SEO Include ALT Tags For Images Infographics PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Context Descriptions, Search Engine, Assisting Indexing. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security And Performance Digital Marketing Optimize Onpage SEO Include Title Tag And Meta Descriptions Formats PDF
This template covers search engine optimization guidelines to optimal title length for title tag and to write meta description displayed on the SERPs . Presenting Security And Performance Digital Marketing Optimize Onpage SEO Include Title Tag And Meta Descriptions Formats PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Currently Limited, Typically Displays, Guidelines. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
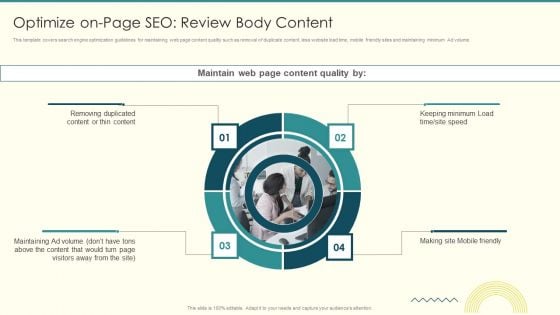
Security And Performance Digital Marketing Optimize Onpage SEO Review Body Content Pictures PDF
This template covers search engine optimization guidelines for maintaining web page content quality such as removal of duplicate content, less website load time, mobile friendly sites and maintaining minimum Ad volume. .This is a Security And Performance Digital Marketing Optimize Onpage SEO Review Body Content Pictures PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Removing Duplicated, Keeping Minimum, Maintaining Volume. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
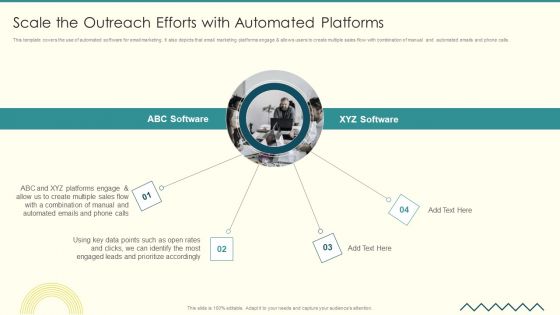
Security And Performance Digital Marketing Scale The Outreach Efforts With Automated Platforms Graphics PDF
This template covers the use of automated software for email marketing. It also depicts that email marketing platforms engage allows users to create multiple sales flow with combination of manual and automated emails and phone calls.Presenting Security And Performance Digital Marketing Scale The Outreach Efforts With Automated Platforms Graphics PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Combination Manual, Leads Prioritize, Identify Most. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security And Performance Digital Marketing Structure Of Facebook Campaigns Clipart PDF
This template depicts that Facebook Ads needs three parts to run such as a campaign, ad set, and ad. All these parts are called campaign structure and help run ads the way the company wants and reach the right prospects.his is a Security And Performance Digital Marketing Structure Of Facebook Campaigns Clipart PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Powerful Consisting, Features Campaigns, Define Creative. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
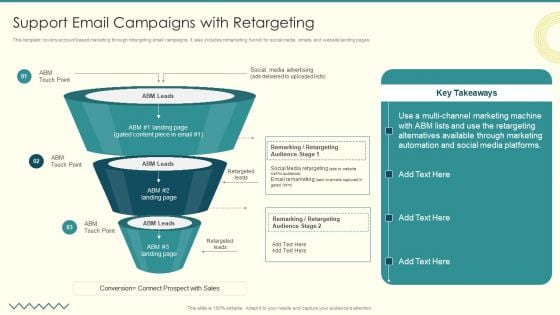
Security And Performance Digital Marketing Support Email Campaigns With Retargeting Elements PDF
This template covers account based marketing through retargeting email campaigns. It also includes remarketing funnel for social media, emails and website landing pages.Presenting Security And Performance Digital Marketing Support Email Campaigns With Retargeting Elements PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Alternatives Available, Remarking Retargeting, Media Advertising. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
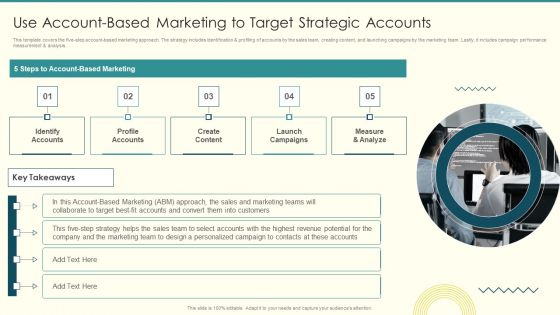
Security And Performance Digital Marketing Use Accountbased Marketing To Target Strategic Accounts Topics PDF
This template covers the five-step account-based marketing approach. The strategy includes identification profiling of accounts by the sales team, creating content, and launching campaigns by the marketing team. Lastly, it includes campaign performance measurement analysis. This is a Security And Performance Digital Marketing Use Accountbased Marketing To Target Strategic Accounts Topics PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Personalized Campaign, Revenue Potential, Launch Campaigns. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
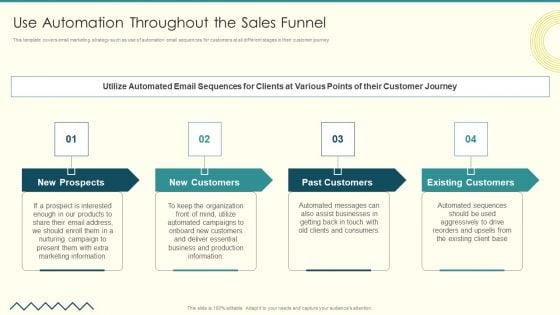
Security And Performance Digital Marketing Use Automation Throughout The Sales Funnel Structure PDF
This template covers email marketing strategy such as use of automation email sequences for customers at all different stages in their customer journey . Presenting Security And Performance Digital Marketing Use Automation Throughout The Sales Funnel Structure PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Past Customers, Existing Customers, Assist Businesses. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security And Performance Digital Marketing Use Existing Email Lists To Launch Retargeting Campaigns Clipart PDF
This template depicts that by uploading existing email lists to Google, Facebook, and LinkedIn, user may target those customers with display advertising or create fresh unique lookalike audiences. This is a Security And Performance Digital Marketing Use Existing Email Lists To Launch Retargeting Campaigns Clipart PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Lookalike Audience, Retargeted Advertising, Lookalike Retargeting. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
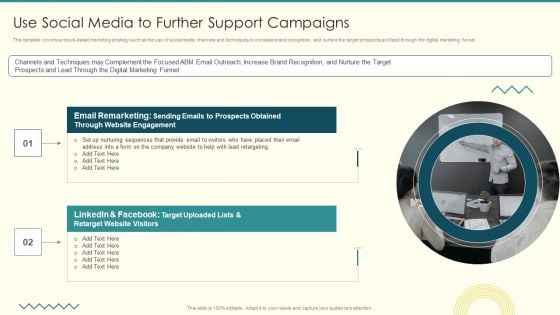
Security And Performance Digital Marketing Use Social Media To Further Support Campaigns Clipart PDF
This template covers account-based marketing strategy such as the use of social media channels and techniques to increase brand recognition, and nurture the target prospects and lead through the digital marketing funnel.This is a Security And Performance Digital Marketing Use Social Media To Further Support Campaigns Clipart PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Prospects Obtained, Nurturing Sequences, Channels Techniques. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security And Performance Digital Marketing Use Top Of Funnel Content In Cold Calling Campaigns Template PDF
This template covers the cold calling email campaign strategy. It also depicts that TOFU should include introductory content focusing on brand, MOFU should include useful information about brand and, BOFU should include social proofs.Presenting Security And Performance Digital Marketing Use Top Of Funnel Content In Cold Calling Campaigns Template PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Sample Reports, Testimonials, Landing Pages. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Professional Data Certification Program Certified Information Systems Security Professional CISSP Details Portrait PDF
This slide covers CISSP certification details such as what is the CISSP, how to become certified, how to prepare for CISSP and why to get CISSP certifications. This is a IT Professional Data Certification Program Certified Information Systems Security Professional CISSP Details Portrait PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Organization, Customers, Access Management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
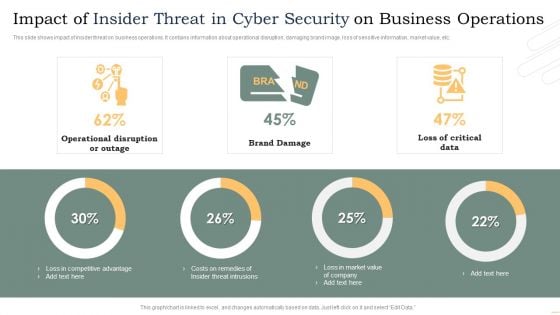
Impact Of Insider Threat In Cyber Security On Business Operations Microsoft PDF
This slide shows impact of insider threat on business operations. It contains information about operational disruption, damaging brand image, loss of sensitive information, market value, etc. Pitch your topic with ease and precision using this Impact Of Insider Threat In Cyber Security On Business Operations Microsoft PDF. This layout presents information on Operational Disruption Or Outage, Brand Damage, Loss Critical Data. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
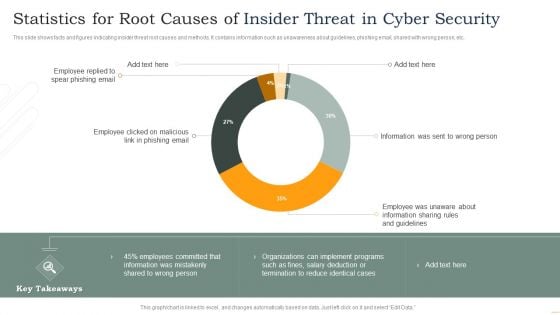
Statistics For Root Causes Of Insider Threat In Cyber Security Inspiration PDF
This slide shows facts and figures indicating insider threat root causes and methods. It contains information such as unawareness about guidelines, phishing email, shared with wrong person, etc. Showcasing this set of slides titled Statistics For Root Causes Of Insider Threat In Cyber Security Inspiration PDF. The topics addressed in these templates are Employee Replied, Spear Phishing Email, Employee Clicked, Phishing Email. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
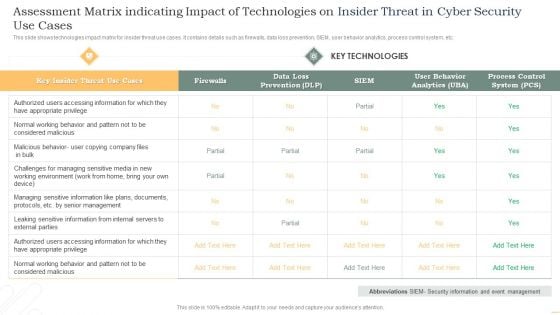
Assessment Matrix Indicating Impact Of Technologies On Insider Threat In Cyber Security Use Cases Themes PDF
This slide shows technologies impact matrix for insider threat use cases. It contains details such as firewalls, data loss prevention, SIEM, user behavior analytics, process control system, etc. Showcasing this set of slides titled Assessment Matrix Indicating Impact Of Technologies On Insider Threat In Cyber Security Use Cases Themes PDF. The topics addressed in these templates are Key Insider, Threat, Use Cases, Key Technologies. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
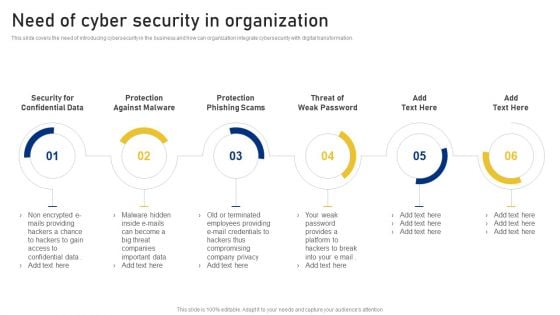
Reshaping Business In Digital Need Of Cyber Security In Organization Sample PDF
This slide covers the need of introducing cybersecurity in the business and how can organization integrate cybersecurity with digital transformation. This is a Reshaping Business In Digital Need Of Cyber Security In Organization Sample PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Protection Against Malware, Protection Phishing Scams, Threat Weak Password . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Determine Standard Mobile Device Management Components Mobile Device Security Management Information PDF
This slide provides information regarding essential standard mobile device management components terms of central management console, registry.This is a Determine Standard Mobile Device Management Components Mobile Device Security Management Information PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Management Console, Create Virtual, Synchronization Among. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
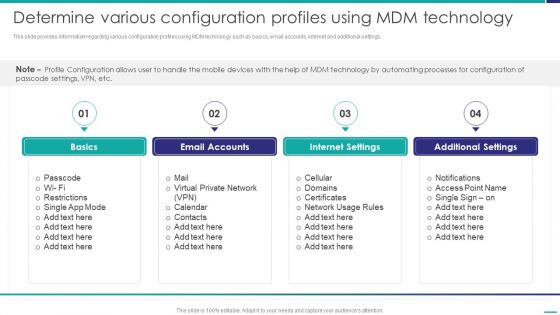
Determine Various Configuration Profiles Using MDM Technology Mobile Device Security Management Infographics PDF
This slide provides information regarding various configuration profiles using MDM technology such as basics, email accounts, internet and additional settings. Presenting Determine Various Configuration Profiles Using MDM Technology Mobile Device Security Management Infographics PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Restrictions, Internet Settings, Additional Settings. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Determine Various Mobile Device Management Deployment Methods Mobile Device Security Management Summary PDF
This slide provides information regarding various mobile device management deployment methods such as device enrollment program, configurator, user initiated through URL that can be selected by vendor based on requirement. This is a Determine Various Mobile Device Management Deployment Methods Mobile Device Security Management Summary PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Enrollment Program, Configurator, Automatic Enrollment. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Ensuring Mobile Device Compliance And Policy Enforcement Mobile Device Security Management Slides PDF
This slide provides information regarding mobile device compliance and policy enforcement with automated device setup, dynamic workflows and policies, etc.Presenting Ensuring Mobile Device Compliance And Policy Enforcement Mobile Device Security Management Slides PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Automated Device, Enforcement Automation, Device Compliance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
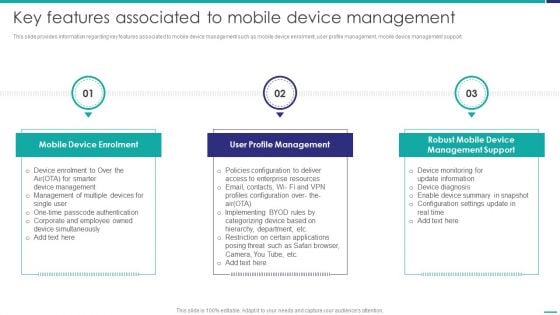
Key Features Associated To Mobile Device Management Mobile Device Security Management Mockup PDF
This slide provides information regarding key features associated to mobile device management such as mobile device enrolment, user profile management, mobile device management support. This is a Key Features Associated To Mobile Device Management Mobile Device Security Management Mockup PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Device Enrolment, Profile Management, Management Support. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Mobile Device Management Assistance To Mobile Device Security Management Professional PDF
This slide provides information regarding mobile device management technology assistance to employees and to IT department associated to firm. This is a Mobile Device Management Assistance To Mobile Device Security Management Professional PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Reducing Connection, Rendering Appropriate, Remote Configuration. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
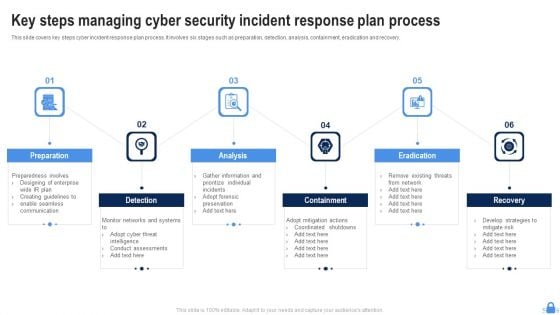
Key Steps Managing Cyber Security Incident Response Plan Process Portrait PDF
This slide covers key steps cyber incident response plan process. It involves six stages such as preparation, detection, analysis, containment, eradication and recovery. Persuade your audience using this Key Steps Managing Cyber Security Incident Response Plan Process Portrait PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Preparation, Detection, Analysis, Eradication. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Table Of Contents IT Security Automation Systems Guide Layer Clipart PDF
Welcome to our selection of the Table Of Contents IT Security Automation Systems Guide Layer Clipart PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.
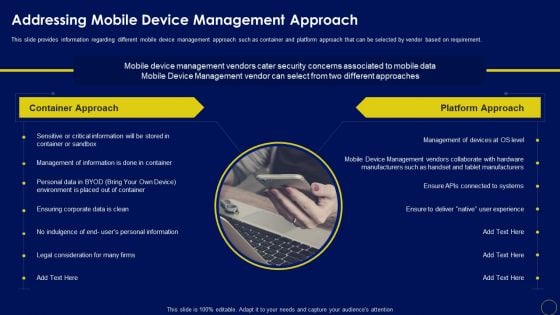
Addressing Mobile Device Management Business Mobile Device Security Management Download PDF
This slide provides information regarding different mobile device management approach such as container and platform approach that can be selected by vendor based on requirement. This modern and well-arranged Addressing Mobile Device Management Business Mobile Device Security Management Download PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Addressing Timeframe For Incident Management At Business Mobile Device Security Management Sample PDF
This slide provides information regarding entire duration of incident handling process which occur in various phases.Welcome to our selection of the Addressing Timeframe For Incident Management At Business Mobile Device Security Management Sample PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 precent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.
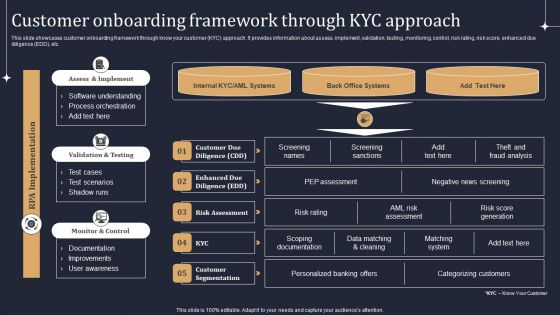
KYC Transaction Monitoring System Business Security Customer Onboarding Framework Introduction PDF
Welcome to our selection of the KYC Transaction Monitoring System Business Security Customer Onboarding Framework Introduction PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.
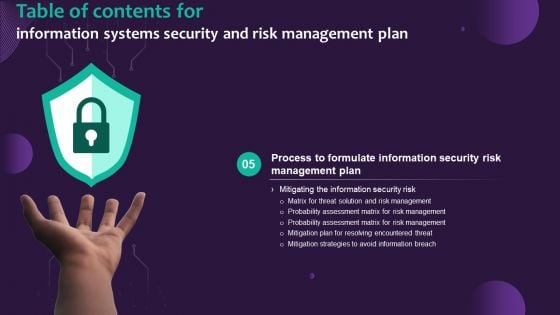
Information Systems Security And Risk Management Plan For Table Of Contents Mockup PDF
Welcome to our selection of the Information Systems Security And Risk Management Plan For Table Of Contents Mockup PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Way To Overcome Security Monitoring Themes PDF
This slide provides information about the way that the company and security monitoring manager must choose in order to solve the challenge problem related to Malware Attacks and other potential security monitoring challenges. The solution is to set up an advanced Cybersecurity Monitoring Plan in place with the help of a set series of steps mentioned in the slide. This is a continuous development evaluation plan eliminate cyber attacks way to overcome security monitoring themes pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like monitoring, systems, management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
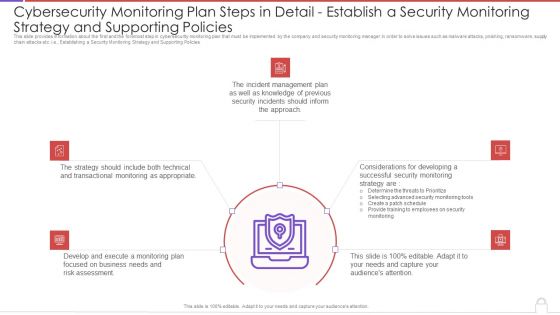
Cybersecurity Monitoring Plan Steps In Detail Establish A Security Monitoring Strategy And Pictures PDF
This slide provides information about the first and the foremost step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e., Establishing a Security Monitoring Strategy and Supporting Policies. This is a cybersecurity monitoring plan steps in detail establish a security monitoring strategy and pictures pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like incident management, transactional monitoring, monitoring plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
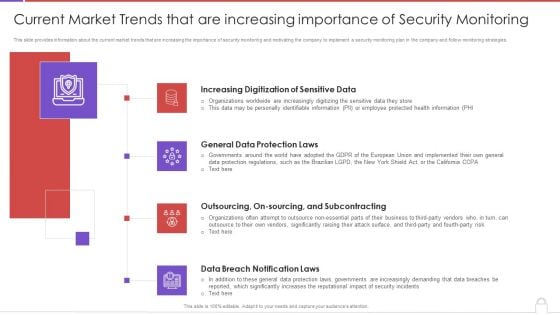
Methods To Develop Current Market Trends That Are Increasing Importance Of Security Portrait PDF
This slide provides information about the current market trends that are increasing the importance of security monitoring and motivating the company to implement a security monitoring plan in the company and follow monitoring strategies. This is a methods to develop current market trends that are increasing importance of security portrait pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like increasing digitization sensitive data, general data protection laws, outsourcing, on sourcing, and subcontracting, data breach notification laws. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
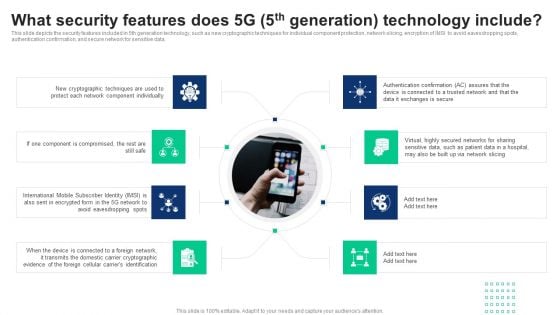
1G To 5G Cellular What Security Features Does 5G 5Th Generation Technology Include Information PDF
This slide depicts the security features included in 5th generation technology, such as new cryptographic techniques for individual component protection, network slicing, encryption of IMSI to avoid eavesdropping spots, authentication confirmation, and secure network for sensitive data. Welcome to our selection of the 1G To 5G Cellular What Security Features Does 5G 5Th Generation Technology Include Information PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.
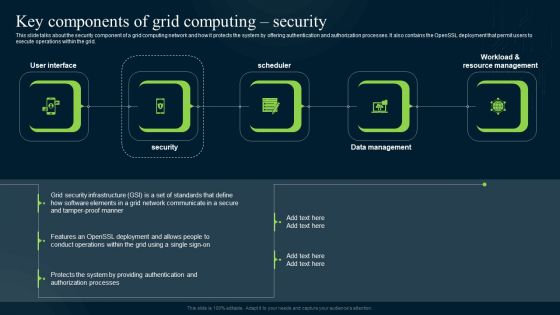
Grid Computing Infrastructure Key Components Of Grid Computing Security Information PDF
This slide talks about the security component of a grid computing network and how it protects the system by offering authentication and authorization processes. It also contains the OpenSSL deployment that permit users to execute operations within the grid. Explore a selection of the finest Grid Computing Infrastructure Key Components Of Grid Computing Security Information PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Grid Computing Infrastructure Key Components Of Grid Computing Security Information PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
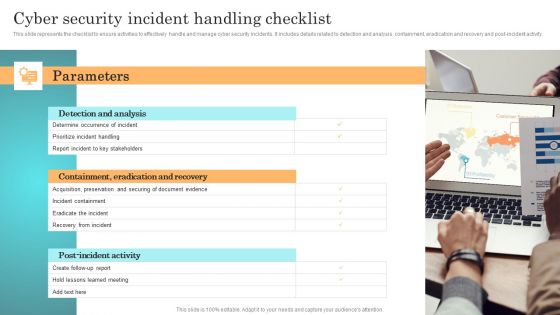
Incident Response Techniques Deployement Cyber Security Incident Handling Checklist Infographics PDF
This slide represents the checklist to ensure activities to effectively handle and manage cyber security incidents. It includes details related to detection and analysis, containment, eradication and recovery and post-incident activity. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Incident Response Techniques Deployement Cyber Security Incident Communication Strategy Brochure PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Incident Response Techniques Deployement Cyber Security Incident Communication Strategy Brochure PDF
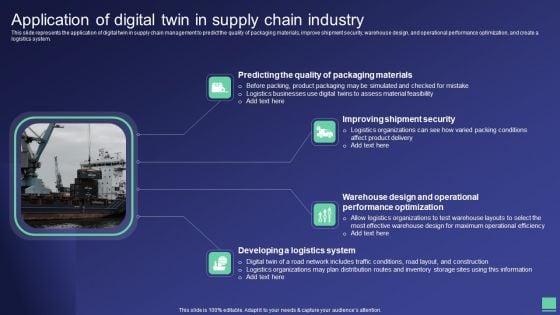
Digital Twin Tech IT Application Of Digital Twin In Supply Chain Industry Information PDF
This slide represents the application of digital twin in supply chain management to predict the quality of packaging materials, improve shipment security, warehouse design, and operational performance optimization, and create a logistics system. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Digital Twin Tech IT Application Of Digital Twin In Supply Chain Industry Information PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Deploying AI To Enhance Digital Twin Technology Supply Chain Management Rules PDF
This slide represents the application of digital twin in supply chain management to predict the quality of packaging materials, improve shipment security, warehouse design, and operational performance optimization, and create a logistics system. Find highly impressive Deploying AI To Enhance Digital Twin Technology Supply Chain Management Rules PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Deploying AI To Enhance Digital Twin Technology Supply Chain Management Rules PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.
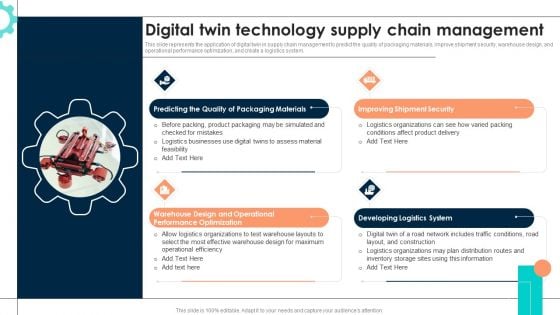
Intelligent Manufacturing Digital Twin Technology Supply Chain Management Rules PDF
This slide represents the application of digital twin in supply chain management to predict the quality of packaging materials, improve shipment security, warehouse design, and operational performance optimization, and create a logistics system. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Intelligent Manufacturing Digital Twin Technology Supply Chain Management Rules PDF can be your best option for delivering a presentation. Represent everything in detail using Intelligent Manufacturing Digital Twin Technology Supply Chain Management Rules PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
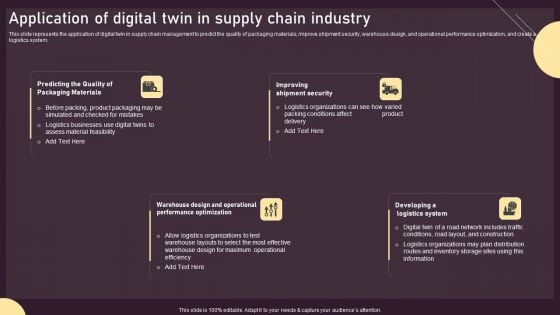
Application Of Digital Twin In Supply Chain Industry Ppt PowerPoint Presentation File Infographics PDF
This slide represents the application of digital twin in supply chain management to predict the quality of packaging materials, improve shipment security, warehouse design, and operational performance optimization, and create a logistics system. This Application Of Digital Twin In Supply Chain Industry Ppt PowerPoint Presentation File Infographics PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Application Of Digital Twin In Supply Chain Industry Ppt PowerPoint Presentation File Infographics PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today

Digital Twin Technology Supply Chain Management Template PDF
This slide represents the application of digital twin in supply chain management to predict the quality of packaging materials, improve shipment security, warehouse design, and operational performance optimization, and create a logistics system. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Digital Twin Technology Supply Chain Management Template PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Digital Twin Technology Supply Chain Management Template PDF.

Transforming Manufacturing With Automation Digital Twin Technology Download PDF
This slide represents the application of digital twin in supply chain management to predict the quality of packaging materials, improve shipment security, warehouse design, and operational performance optimization, and create a logistics system. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Transforming Manufacturing With Automation Digital Twin Technology Download PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Transforming Manufacturing With Automation Digital Twin Technology Download PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.
Enhanced Protection Corporate Event Administration Determine Focus Areas To Implement Security Operations Centre Icons PDF
This slide portrays information regarding the focus areas that are need to be addressed for effective implementation of security operations center. The focus areas are such as digital forensics and control, risk monitoring and management, etc. This is a enhanced protection corporate event administration determine focus areas to implement security operations centre icons pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like digital forensics and control, risk monitoring and management, system and network administration. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Plan Topics PDF
This slide provides information about the second step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Aligning the Incident Management Policies and Plan. This is a modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring plan topics pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity monitoring plan steps in detail aligning the incident management policies and plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Introduction PDF
This slide provides information about the fifth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Fine Tune Monitoring System. This is a modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring introduction pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity monitoring plan steps in detail fine tune monitoring system. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Matrix For Threat Solution And Risk Management Information Security Risk Administration Inspiration PDF
This slide showcases matrix that can help organization to formulate solutions for different types of information security attacks. It can help organization to mitigate the risks and safeguard information in case of any attack.Welcome to our selection of the Matrix For Threat Solution And Risk Management Information Security Risk Administration Inspiration PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 precent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.
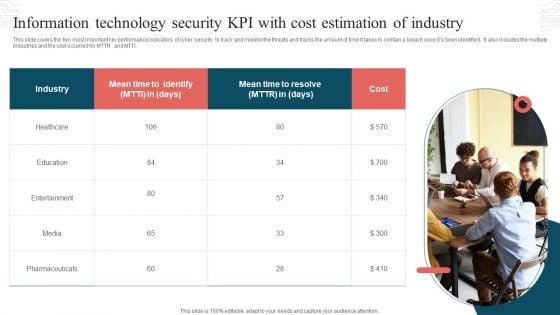
Information Technology Security KPI With Cost Estimation Of Industry Topics PDF
This slide covers the two most important key performance indicators of cyber security to track and monitor the threats and tracks the amount of time it takes to contain a breach once its been identified. It also includes the multiple industries and the cost occurred for MTTR and MTTI. Persuade your audience using this Information Technology Security KPI With Cost Estimation Of Industry Topics PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Industry, Mean Time, Cost. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
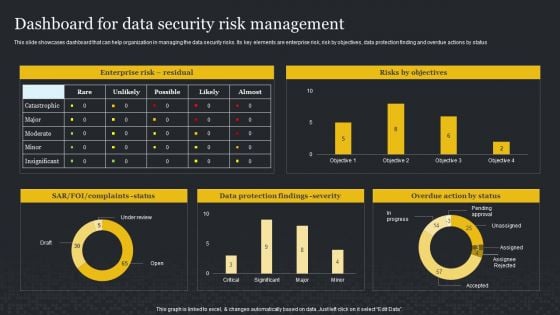
Dashboard For Data Security Risk Management Cybersecurity Risk Assessment Template PDF
This slide showcases dashboard that can help organization in managing the data security risks. Its key elements are enterprise risk, risk by objectives, data protection finding and overdue actions by status. Welcome to our selection of the Dashboard For Data Security Risk Management Cybersecurity Risk Assessment Template PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 parcent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.

Deploying AML Transaction Monitoring Key Members Of Financial Security Department Ideas PDF
The following slide highlights key members of financial security department . It provides information about chief financial officer CFO, compliance auditor, senior analyst, customer support manager, operations manager, etc. Welcome to our selection of the Deploying AML Transaction Monitoring Key Members Of Financial Security Department Ideas PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.
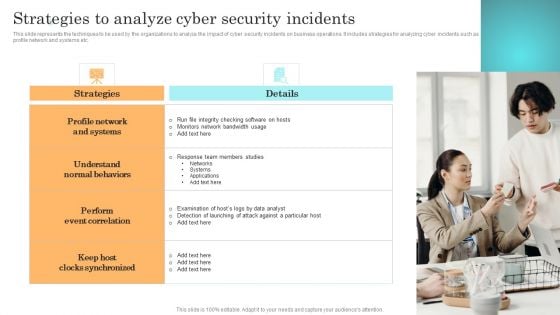
Incident Response Techniques Deployement Strategies To Analyze Cyber Security Incidents Sample PDF
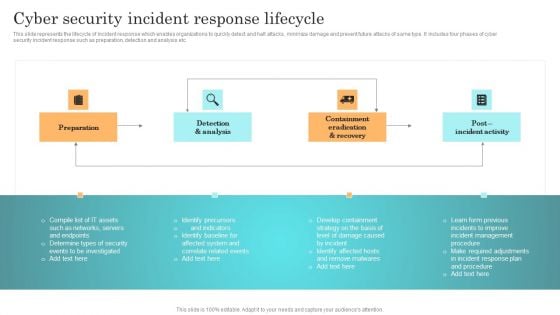
Incident Response Techniques Deployement Cyber Security Incident Response Lifecycle Template PDF
This slide represents the lifecycle of incident response which enables organizations to quickly detect and halt attacks, minimize damage and prevent future attacks of same type. It includes four phases of cyber security incident response such as preparation, detection and analysis etc. Welcome to our selection of the Incident Response Techniques Deployement Cyber Security Incident Response Lifecycle Template PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.
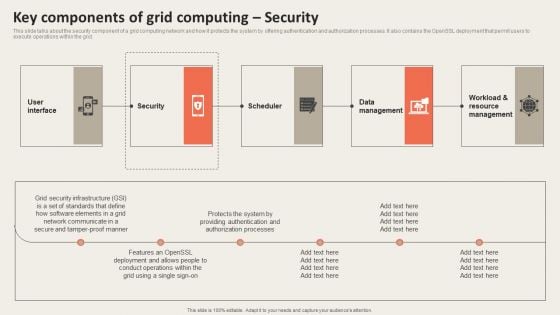
Grid Computing Applications Key Components Of Grid Computing Security Guidelines PDF
This slide talks about the security component of a grid computing network and how it protects the system by offering authentication and authorization processes. It also contains the OpenSSL deployment that permit users to execute operations within the grid. This modern and well arranged Grid Computing Applications Key Components Of Grid Computing Security Guidelines PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
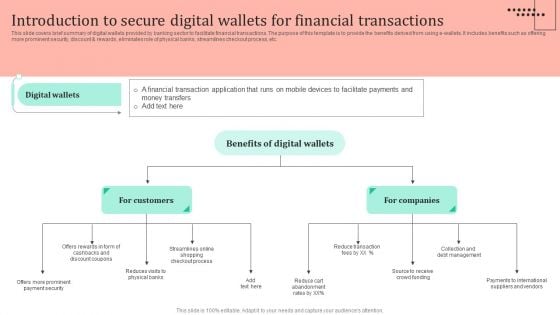
Omnichannel Strategy Implementation For Banking Solutions Introduction To Secure Digital Wallets For Financial Pictures PDF
This slide covers brief summary of digital wallets provided by banking sector to facilitate financial transactions. The purpose of this template is to provide the benefits derived from using e wallets. It includes benefits such as offering more prominent security, discount and rewards, eliminates role of physical banks, streamlines checkout process, etc. Welcome to our selection of the Omnichannel Strategy Implementation For Banking Solutions Introduction To Secure Digital Wallets For Financial Pictures PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.
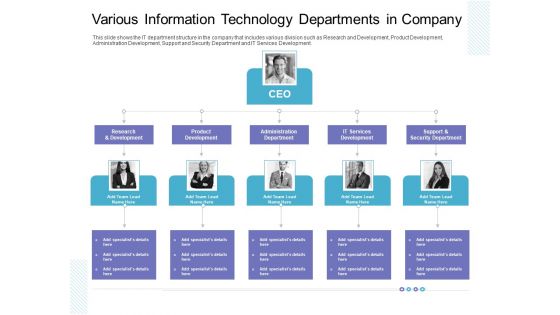
Various Information Technology Departments In Company Slides PDF
This slide shows the IT department structure in the company that includes various division such as Research and Development, Product Development, Administration Development, Support and Security Department and IT Services Development. This is a various information technology departments in company slides pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like product development, administration department, research and development, support and security department. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
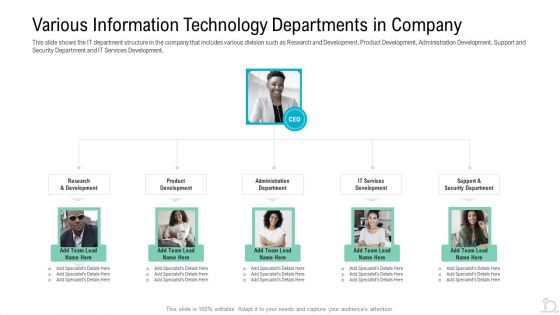
Various Information Technology Departments In Company Formats PDF
This slide shows the IT department structure in the company that includes various division such as Research and Development, Product Development, Administration Development, Support and Security Department and IT Services Development. This is a various information technology departments in company formats pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like product development, research and development, support and security department. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
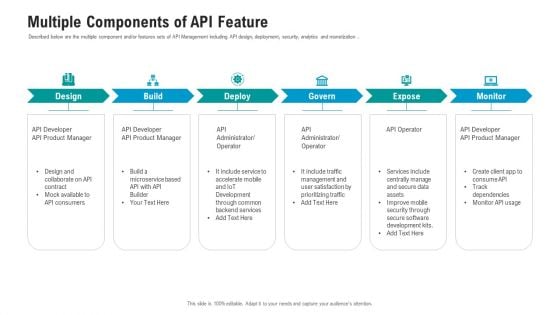
API Ecosystem Multiple Components Of API Feature Designs PDF
Described below are the multiple component and or features sets of API Management including API design, deployment, security, analytics and monetization. This is a api ecosystem multiple components of api feature designs pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like developer, consumers, service, management, security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Challenges Of Crm Implementation Along With Solutions Clipart PDF
This slide provides the glimpse about the challenges faced during CRM implementation such as data security, scope clarity, integration management, etc. along with their solutions. This is a challenges of crm implementation along with solutions clipart pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like requirements, project, implementation, security, service. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
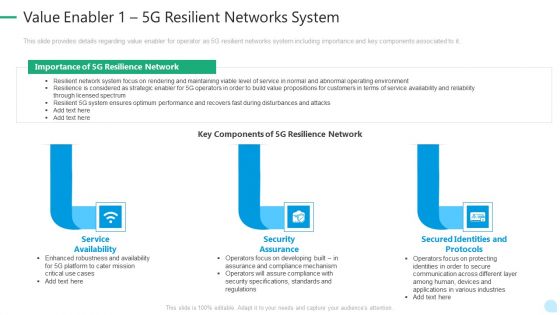
5G Network Technology Value Enabler 1 5G Resilient Networks System Ppt Layouts Diagrams PDF
This slide provides details regarding value enabler for operator as 5G resilient networks system including importance and key components associated to it. This is a 5g network technology value enabler 1 5g resilient networks system ppt layouts diagrams pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like service availability, security assurance, secured identities and protocols. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Data Center Infrastructure Management IT Types Of Data Centers Colocation Data Centers Diagrams PDF
This slide shows the one from different types of data centers that is colocation data centers that provide services to organizations, including cooling, bandwidth, and security. Presenting data center infrastructure management it types of data centers colocation data centers diagrams pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like infrastructure, maintains, security, manufactures. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
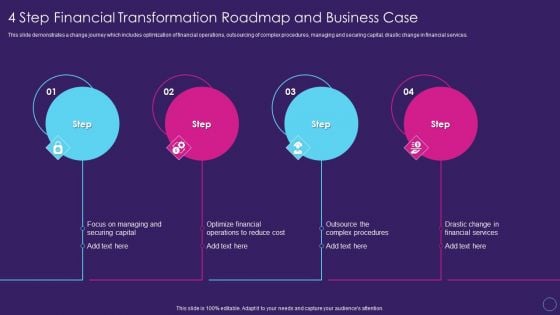
Digital Transformation Toolkit Accounting Finance 4 Step Financial Transformation Roadmap Mockup PDF
This slide demonstrates a change journey which includes optimization of financial operations, outsourcing of complex procedures, managing and securing capital, drastic change in financial services. This is a digital transformation toolkit accounting finance 4 step financial transformation roadmap mockup pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like managing, securing, operations, financial, procedures. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
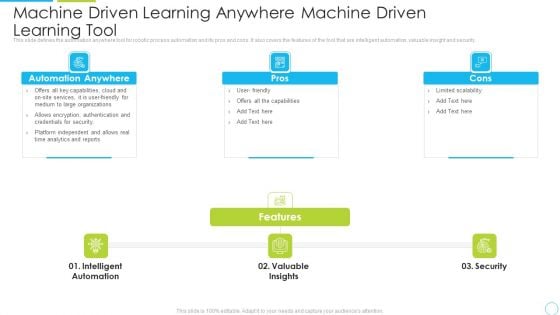
Machine Driven Learning Anywhere Machine Driven Learning Tool Ppt Layouts Samples PDF
This slide defines the automation anywhere tool for robotic process automation and its pros and cons. It also covers the features of the tool that are intelligent automation, valuable insight and security. Presenting machine driven learning anywhere machine driven learning tool ppt layouts samples pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like services, organizations, security, analytics. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.


 Continue with Email
Continue with Email

 Home
Home


































