Vulnerability Management
Vulnerability Assessment Steps Ppt PowerPoint Presentation Model Icon Cpb
Presenting this set of slides with name vulnerability assessment steps ppt powerpoint presentation model icon cpb. This is an editable Powerpoint six stages graphic that deals with topics like vulnerability assessment steps to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Mobile App Vulnerability Testing Ppt PowerPoint Presentation Ideas Infographics Cpb
Presenting this set of slides with name mobile app vulnerability testing ppt powerpoint presentation ideas infographics cpb. This is an editable Powerpoint four stages graphic that deals with topics like mobile app vulnerability testing to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Vulnerability Remediation Tracking Ppt PowerPoint Presentation Model Ideas Cpb
Presenting this set of slides with name vulnerability remediation tracking ppt powerpoint presentation model ideas cpb. This is an editable Powerpoint five stages graphic that deals with topics like vulnerability remediation tracking to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Vulnerability Scanning Network Ppt PowerPoint Presentation Infographics Skills Cpb
Presenting this set of slides with name vulnerability scanning network ppt powerpoint presentation infographics skills cpb. This is an editable Powerpoint three stages graphic that deals with topics like vulnerability scanning network to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
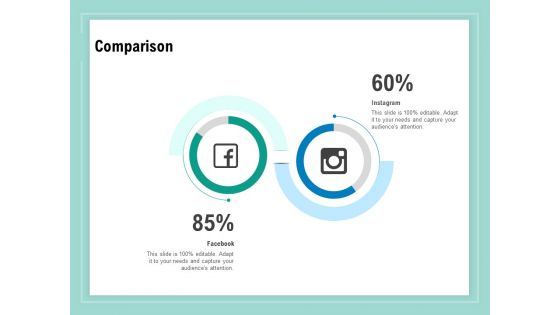
Vulnerability Assessment Methodology Comparison Ppt Show Clipart Images PDF
Presenting this set of slides with name vulnerability assessment methodology comparison ppt show clipart images pdf. This is a two stage process. The stages in this process are comparison. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
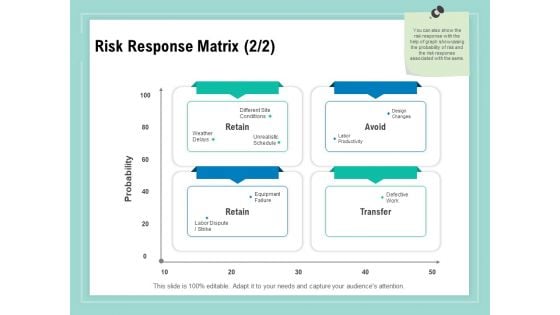
Vulnerability Assessment Methodology Risk Response Matrix Ppt Diagram Ppt PDF
Presenting this set of slides with name vulnerability assessment methodology risk response matrix ppt diagram ppt pdf. This is a four stage process. The stages in this process are retain, avoid, transfer. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
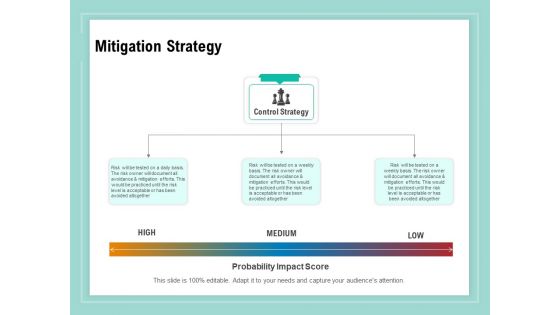
Vulnerability Assessment Methodology Mitigation Strategy Ppt Infographic Template Examples PDF
Presenting this set of slides with name vulnerability assessment methodology mitigation strategy ppt infographic template examples pdf. This is a three stage process. The stages in this process are high, medium, low. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
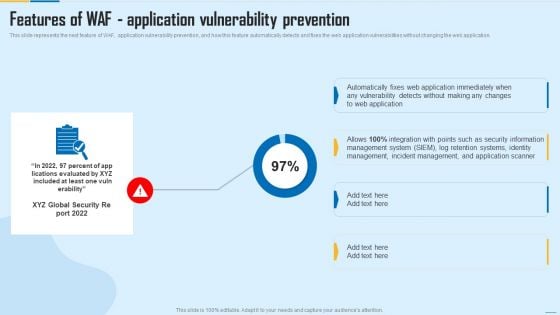
Features Of WAF Application Vulnerability Prevention WAF Platform Designs PDF
This slide represents the next feature of WAF, application vulnerability prevention, and how this feature automatically detects and fixes the web application vulnerabilities without changing the web application. Deliver and pitch your topic in the best possible manner with this Features Of WAF Application Vulnerability Prevention WAF Platform Designs PDF. Use them to share invaluable insights on Management System, Incident Management, Security Information and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Vulnerability Handling Process Flowchart For It Organization Download Pdf
This slide represents procedure to handle and resolve vulnerability in an IT company. It includes various stages, such as identifying, evaluating, remediating, verifying, and reporting. Showcasing this set of slides titled Vulnerability Handling Process Flowchart For It Organization Download Pdf. The topics addressed in these templates are Identify, Evaluate, Remediate. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide represents procedure to handle and resolve vulnerability in an IT company. It includes various stages, such as identifying, evaluating, remediating, verifying, and reporting.
Database Vulnerability Handling Process Flowchart Icon Guidelines Pdf
Pitch your topic with ease and precision using this Database Vulnerability Handling Process Flowchart Icon Guidelines Pdf. This layout presents information on Database Vulnerability, Handling Process Flowchart Icon. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our Database Vulnerability Handling Process Flowchart Icon Guidelines Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Information System Vulnerability Handling Process Flowchart Icon Designs Pdf
Pitch your topic with ease and precision using this Information System Vulnerability Handling Process Flowchart Icon Designs Pdf. This layout presents information on Information System Vulnerability, Handling Process Flowchart Icon. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our Information System Vulnerability Handling Process Flowchart Icon Designs Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Vulnerability Assessment Companies Ppt PowerPoint Presentation Outline Graphics Design Cpb
This is a vulnerability assessment companies ppt powerpoint presentation outline graphics design cpb. This is a five stage process. The stages in this process are vulnerability assessment companies.

Enterprise Vulnerability Assessment Ppt PowerPoint Presentation Layouts Graphics Template Cpb
This is a enterprise vulnerability assessment ppt powerpoint presentation layouts graphics template cpb. This is a one stage process. The stages in this process are enterprise vulnerability assessment.

Nessus Vulnerability Report In Powerpoint And Google Slides Cpb
Introducing our well designed Nessus Vulnerability Report In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Nessus Vulnerability Report. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Nessus Vulnerability Report In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Steps To Perform Vulnerability Analysis For Network Security Pictures Pdf
This slide showcase vulnerability assessment process that help organization to identify security vulnerabilities in network system and prioritize them to plan mitigation action plan. It includes steps such as identifying, scanning, identify type of scan, configure scan etc.Showcasing this set of slides titled Steps To Perform Vulnerability Analysis For Network Security Pictures Pdf The topics addressed in these templates are Evaluate Possible Risk, Interpret Scan Results, Create Mitigation Plan All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcase vulnerability assessment process that help organization to identify security vulnerabilities in network system and prioritize them to plan mitigation action plan. It includes steps such as identifying, scanning, identify type of scan, configure scan etc.
Vulnerability Reporting Tool In Powerpoint And Google Slides Cpb
Presenting our innovatively-designed set of slides titled Vulnerability Reporting Tool In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Vulnerability Reporting Tool that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well-structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Vulnerability Reporting Tool In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Food Ingredient Adulteration Vulnerability Prevention Strategy Information Pdf
This slide provide information about food ingredient fraud vulnerability mitigation plan to protect organization image. It includes elements such as facility security, building security and security assessments Showcasing this set of slides titled Food Ingredient Adulteration Vulnerability Prevention Strategy Information Pdf. The topics addressed in these templates are Security Assessments, Building Security, Facility Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide provide information about food ingredient fraud vulnerability mitigation plan to protect organization image. It includes elements such as facility security, building security and security assessments
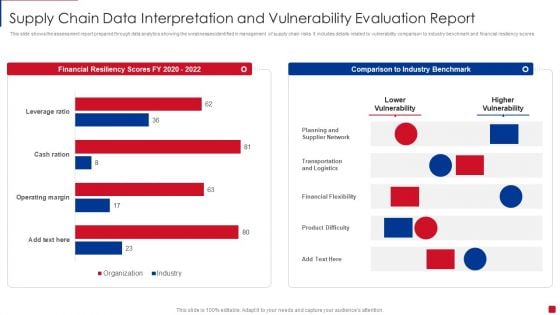
Supply Chain Data Interpretation And Vulnerability Evaluation Report Pictures PDF
This slide shows the assessment report prepared through data analytics showing the weaknesses identified in management of supply chain risks. It includes details related to vulnerability comparison to industry benchmark and financial resiliency scores Showcasing this set of slides titled Supply Chain Data Interpretation And Vulnerability Evaluation Report Pictures PDF. The topics addressed in these templates are Planning And Supplier Network, Transportation And Logistics, Financial Flexibility. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Agenda Of Enhancing Cyber Safety With Vulnerability Administratio Professional PDF
This is a agenda of enhancing cyber safety with vulnerability administratio professional pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security intelligence, log management and compliance, provides security services. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
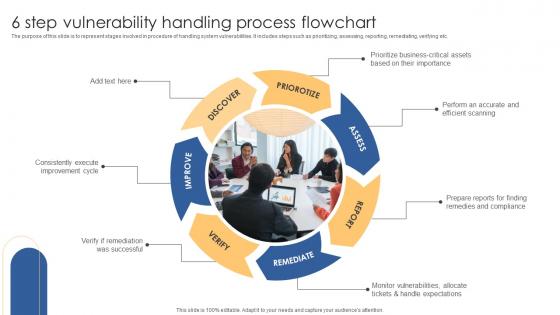
6 Step Vulnerability Handling Process Flowchart Download Pdf
The purpose of this slide is to represent stages involved in procedure of handling system vulnerabilities. It includes steps such as prioritizing, assessing, reporting, remediating, verifying etc. Showcasing this set of slides titled 6 Step Vulnerability Handling Process Flowchart Download Pdf. The topics addressed in these templates are Priorotize, Assess, Discover. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. The purpose of this slide is to represent stages involved in procedure of handling system vulnerabilities. It includes steps such as prioritizing, assessing, reporting, remediating, verifying etc.
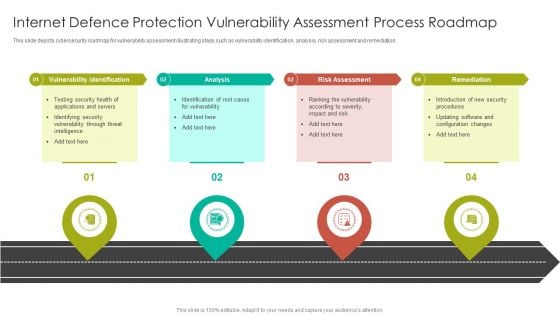
Internet Defence Protection Vulnerability Assessment Process Roadmap Graphics PDF
This slide depicts cybersecurity roadmap for vulnerability assessment illustrating steps such as vulnerability identification, analysis, risk assessment and remediation.Presenting Internet Defence Protection Vulnerability Assessment Process Roadmap Graphics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Vulnerability Identification, Risk Assessment, Remediation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
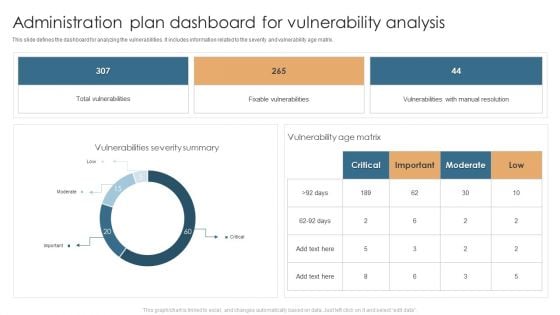
Administration Plan Dashboard For Vulnerability Analysis Microsoft PDF
This slide defines the dashboard for analyzing the vulnerabilities. It includes information related to the severity and vulnerability age matrix. Showcasing this set of slides titled Administration Plan Dashboard For Vulnerability Analysis Microsoft PDF. The topics addressed in these templates are Total Vulnerabilities, Fixable Vulnerabilitie, Vulnerability Age Matrix. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cybersecurity Risk Administration Plan Defining Vulnerability Rating Introduction PDF
Following slide defines the vulnerability ranking set by the firm. It includes information about vulnerability ranking, criteria and its description.Deliver and pitch your topic in the best possible manner with this Cybersecurity Risk Administration Plan Defining Vulnerability Rating Introduction PDF Use them to share invaluable insights on Organization Is Not Capable, Resisting The Occurrence Of Attack, Drawback Is Identified and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Food Adulteration Prevention Strategy Development To Remove Vulnerability Designs Pdf
This slide provide information about procedure to formulate food fraud mitigation plan to remove vulnerability. It includes elements such as pre-screening, vulnerability assessment, impact assessment, overall risk assessment etc. Showcasing this set of slides titled Food Adulteration Prevention Strategy Development To Remove Vulnerability Designs Pdf. The topics addressed in these templates are Vulnerability Assessment, Risk Assessment, Control Plan. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide provide information about procedure to formulate food fraud mitigation plan to remove vulnerability. It includes elements such as pre-screening, vulnerability assessment, impact assessment, overall risk assessment etc.
Icons Slide For Company Vulnerability Administration Template PDF
Help your business to create an attention grabbing presentation using our icons slide for company vulnerability administration template pdf set of slides. The slide contains innovative icons that can be flexibly edited. Choose this icons slide for company vulnerability administration template pdf template to create a satisfactory experience for your customers. Go ahead and click the download button.
Icon For Vulnerability Administration Software Plan Topics PDF
Presenting Icon For Vulnerability Administration Software Plan Topics PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Icon For Vulnerability, Administration Software, Plan. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Vulnerability Rating For Risk Identification Cybersecurity Risk Assessment Structure PDF
This slide showcases table for allocating vulnerability rating to different class of information assets. Its shows information about severity, vulnerability score and description. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Vulnerability Rating For Risk Identification Cybersecurity Risk Assessment Structure PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
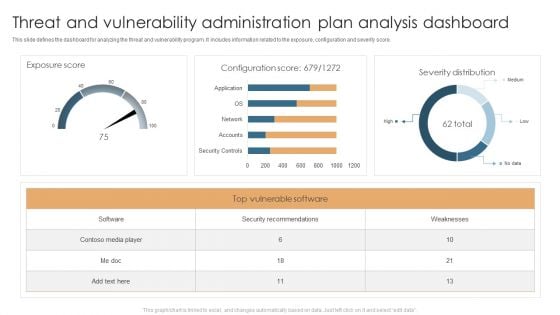
Threat And Vulnerability Administration Plan Analysis Dashboard Slides PDF
This slide defines the dashboard for analyzing the threat and vulnerability program. It includes information related to the exposure, configuration and severity score. Showcasing this set of slides titled Threat And Vulnerability Administration Plan Analysis Dashboard Slides PDF. The topics addressed in these templates are Exposure Score, Configuration Score, Severity Distribution. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Company Vulnerability Administration Develop A Plan Revision Process Information PDF
Presenting company vulnerability administration develop a plan revision process information pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like determine if changes have occurred, review the changes, update toolset if necessary, update sources of vulnerability information. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Threats And Vulnerability Administration Plan Requirement Icon Pictures PDF
Persuade your audience using this Threats And Vulnerability Administration Plan Requirement Icon Pictures PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Threats And Vulnerability, Administration Plan, Requirement Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Company Vulnerability Administration Analyze Root Causes Sample Professional PDF
Presenting company vulnerability administration analyze root causes sample pdf professional pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like perform root cause analysis, develop corrective actions to address root cause, update the vulnerability repository, monitor effect of corrective actions. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
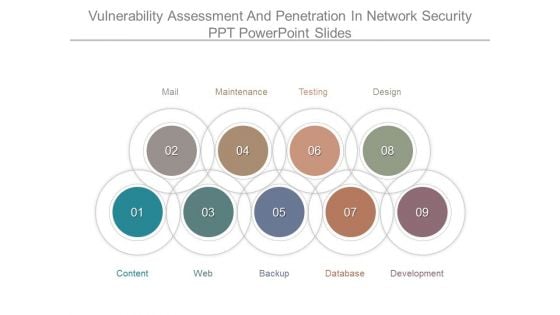
Vulnerability Assessment And Penetration In Network Security Ppt Powerpoint Slides
This is a vulnerability assessment and penetration in network security ppt powerpoint slides. This is a nine stage process. The stages in this process are mail, maintenance, testing, design, development, database, backup, web, content.
Typical Cause Application Vulnerability Ppt PowerPoint Presentation Ideas Slides Cpb
Presenting this set of slides with name typical cause application vulnerability ppt powerpoint presentation ideas slides cpb. This is an editable Powerpoint five stages graphic that deals with topics like typical cause application vulnerability to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Web Vulnerability Assessment Ppt PowerPoint Presentation Layouts Slides Cpb
Presenting this set of slides with name web vulnerability assessment ppt powerpoint presentation layouts slides cpb. This is an editable Powerpoint five stages graphic that deals with topics like web vulnerability assessment to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Features Of WAF Application Vulnerability Prevention Formats PDF
This slide represents the next feature of WAF, application vulnerability prevention, and how this feature automatically detects and fixes the web application vulnerabilities without changing the web application. Make sure to capture your audiences attention in your business displays with our gratis customizable Features Of WAF Application Vulnerability Prevention Formats PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
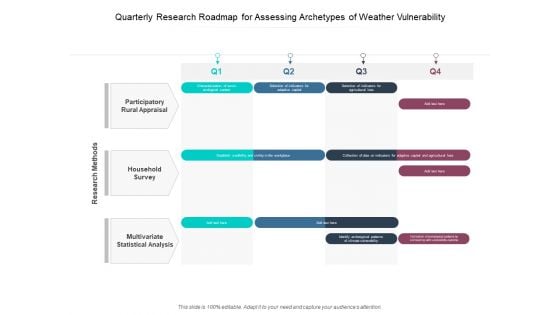
Quarterly Research Roadmap For Assessing Archetypes Of Weather Vulnerability Formats
We present our quarterly research roadmap for assessing archetypes of weather vulnerability formats. This PowerPoint layout is easy-to-edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well-researched quarterly research roadmap for assessing archetypes of weather vulnerability formats in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
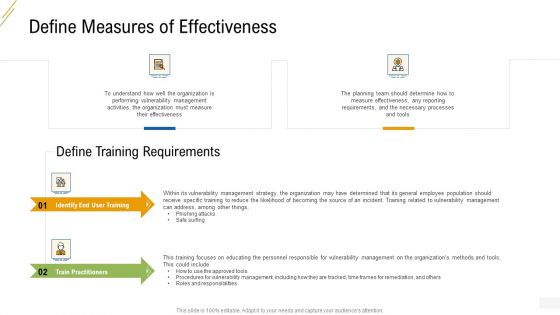
Company Vulnerability Administration Define Measures Of Effectiveness Sample PDF
Deliver an awe inspiring pitch with this creative company vulnerability administration define measures of effectiveness sample pdf bundle. Topics like define training requirements, identify end user training, train practitioners can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Vulnerability Assessment Methodology Circular Diagram Ppt Icon Summary PDF
Presenting this set of slides with name vulnerability assessment methodology circular diagram ppt icon summary pdf. This is a six stage process. The stages in this process are circular diagram. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Vulnerability Assessment Methodology Risk Response Plan Ppt Pictures PDF
Presenting this set of slides with name vulnerability assessment methodology risk response plan ppt pictures pdf. This is a eight stage process. The stages in this process are exploit, enhance, share, accept, avoid, mitigate, transfer. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
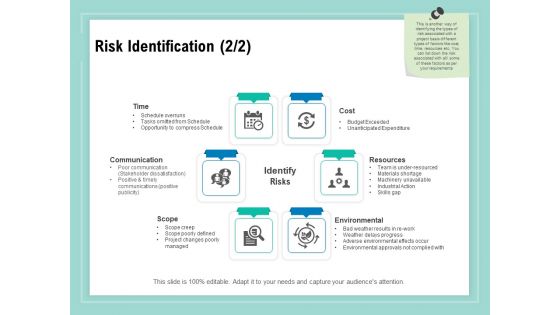
Vulnerability Assessment Methodology Risk Identification Cost Ppt Professional Display PDF
Presenting this set of slides with name vulnerability assessment methodology risk identification cost ppt professional display pdf. This is a six stage process. The stages in this process are cost, resources, environmental, scope, communication, time. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Five Techniques Of Vulnerability Testing Ppt PowerPoint Presentation Model Icon
Presenting this set of slides with name five techniques of vulnerability testing ppt powerpoint presentation model icon. This is a five stage process. The stages in this process are Penetration Testing, Internal Testing, Gaining access. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Vulnerability Assessment Methodology Linear Diagram Ppt Icon Graphics PDF
Presenting this set of slides with name vulnerability assessment methodology linear diagram ppt icon graphics pdf. This is a four stage process. The stages in this process are linear diagram. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Vulnerability Assessment Methodology Roadmap Ppt Layouts Deck PDF
Presenting this set of slides with name vulnerability assessment methodology roadmap ppt layouts deck pdf. This is a five stage process. The stages in this process are roadmap. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Vulnerability Assessment Methodology Target Ppt Infographic Template Templates PDF
Presenting this set of slides with name vulnerability assessment methodology target ppt infographic template templates pdf. This is a four stage process. The stages in this process are target. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Vulnerability Assessment Methodology Thank You Ppt Infographic Template Designs PDF
Presenting this set of slides with name vulnerability assessment methodology thank you ppt infographic template designs pdf. This is a one stage process. The stages in this process are thank you. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Vulnerability Assessment Methodology Timeline Ppt File Demonstration PDF
Presenting this set of slides with name vulnerability assessment methodology timeline ppt file demonstration pdf. This is a four stage process. The stages in this process are timeline, 2020. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Vulnerability Assessment Methodology Venn Diagram Ppt Portfolio Clipart PDF
Presenting this set of slides with name vulnerability assessment methodology venn diagram ppt portfolio clipart pdf. This is a five stage process. The stages in this process are venn diagram. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Company Vulnerability Administration Resource The Activities Pictures PDF
This is a company vulnerability administration resource the activities pictures pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like determine stakeholder resource responsibility, determine a budget, these actions may cause disruptions to the normal business operation of their unit. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
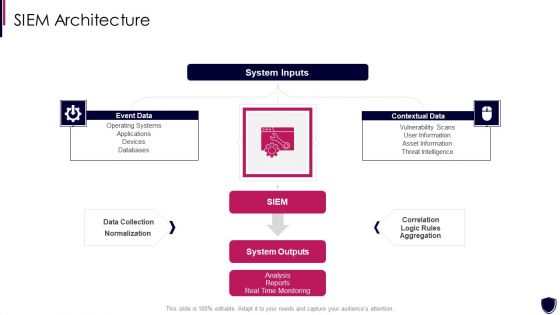
Enhancing Cyber Safety With Vulnerability Administration SIEM Architecture Information PDF
Presenting enhancing cyber safety with vulnerability administration siem architecture information pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like event data, contextual data, system inputs, system outputs, data collection. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Company Vulnerability Administration Define The Roles And Responsibilities Designs PDF
This is a company vulnerability administration define the roles and responsibilities designs pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like monitoring roles, remediation roles, authorization roles. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Enhancing Cyber Safety With Vulnerability Administration SIEM Integrations Inspiration PDF
This is a enhancing cyber safety with vulnerability administration siem integrations inspiration pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security events, network logs, applications and devices, it infrastructure. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Company Vulnerability Administration Collect And Analyze Program Information Demonstration PDF
Presenting company vulnerability administration collect and analyze program information demonstration pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like collect all pertinent work products, policies, and guidance, analyze the measures of effectiveness, analyze the collected products versus the measures of effectiveness, determine the risk of not meeting the measures of effectiveness. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Company Vulnerability Administration Improve The Capability Professional PDF
This is a company vulnerability administration improve the capability professional pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like if a metric of one of the measurements is negative, what does that imply about the process, how does one mitigate that deficiency what about the process must be changed to address the deficiency. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
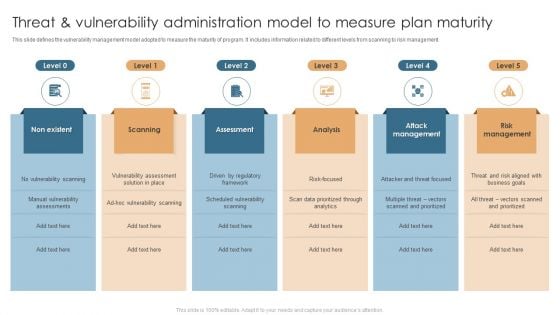
Threat And Vulnerability Administration Model To Measure Plan Maturity Structure PDF
This slide defines the vulnerability management model adopted to measure the maturity of program. It includes information related to different levels from scanning to risk management. Persuade your audience using this Threat And Vulnerability Administration Model To Measure Plan Maturity Structure PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Non Existent, Scanning, Assessment, Analysis, Attack Management. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
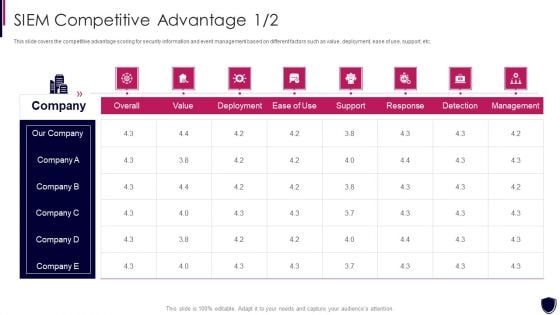
Enhancing Cyber Safety With Vulnerability Administration SIEM Competitive Advantage Designs PDF
This slide covers the competitive advantage scoring for security information and event management based on different factors such as value, deployment, ease of use, support, etc. Deliver an awe inspiring pitch with this creative enhancing cyber safety with vulnerability administration siem competitive advantage designs pdf bundle. Topics like detection, management, deployment, value can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Enhancing Cyber Safety With Vulnerability Administration Need For SIEM Software In Your Company Graphics PDF
This slide covers the need for the SIEM software which focuses on detecting incidents, compliance regulations, and incident management. This is a enhancing cyber safety with vulnerability administration need for siem software in your company graphics pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like detecting incidents, compliance with regulation, efficient incident management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
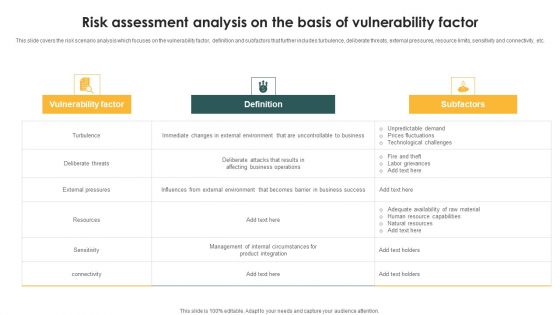
Risk Assessment Analysis On The Basis Of Vulnerability Factor Ppt PowerPoint Presentation Gallery Example Introduction PDF
This slide covers the risk scenario analysis which focuses on the vulnerability factor, definition and subfactors that further includes turbulence, deliberate threats, external pressures, resource limits, sensitivity and connectivity, etc. Showcasing this set of slides titled Risk Assessment Analysis On The Basis Of Vulnerability Factor Ppt PowerPoint Presentation Gallery Example Introduction PDF. The topics addressed in these templates are Vulnerability Factor, Definition, Subfactors, Turbulence. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Vulnerability Assessment Methodology Risk Item Tracking Ppt Professional Format Ideas PDF
Presenting this set of slides with name vulnerability assessment methodology risk item tracking ppt professional format ideas pdf. The topics discussed in these slides are risk item, monthly ranking, risk resolution. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
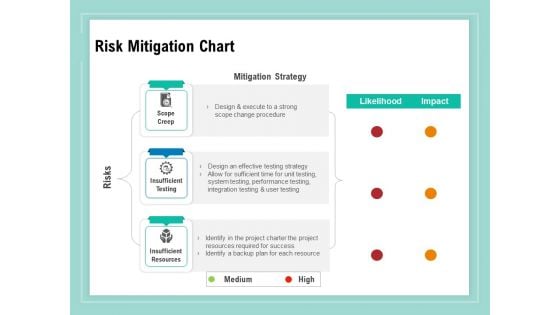
Vulnerability Assessment Methodology Risk Mitigation Chart Ppt Portfolio Background Images PDF
Presenting this set of slides with name vulnerability assessment methodology risk mitigation chart ppt portfolio background images pdf. The topics discussed in these slides are scope creep, insufficient testing, insufficient resources. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
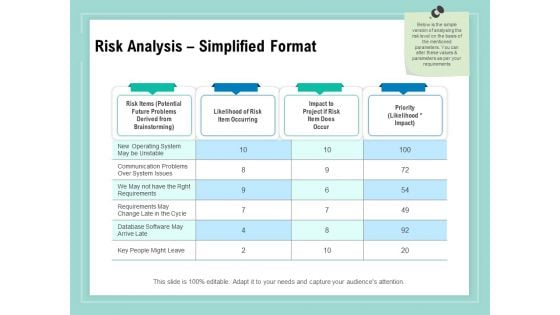
Vulnerability Assessment Methodology Risk Analysis Simplified Format Ppt Outline File Formats
Presenting this set of slides with name vulnerability assessment methodology risk analysis simplified format ppt outline file formats. The topics discussed in these slides are risk items, likelihood of risk item occurring, impact to project if risk item does occur, priority. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

 Home
Home