Vulnerability Scanning

Vulnerability Scanning Practices Ppt PowerPoint Presentation Outline Designs Cpb
Presenting this set of slides with name vulnerability scanning practices ppt powerpoint presentation outline designs cpb. This is an editable Powerpoint four stages graphic that deals with topics like vulnerability scanning practices to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Vulnerability Scanning Network Ppt PowerPoint Presentation Infographics Skills Cpb
Presenting this set of slides with name vulnerability scanning network ppt powerpoint presentation infographics skills cpb. This is an editable Powerpoint three stages graphic that deals with topics like vulnerability scanning network to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Vulnerability Scanning Process Ppt PowerPoint Presentation Icon Gridlines Cpb Pdf
Presenting this set of slides with name vulnerability scanning process ppt powerpoint presentation icon gridlines cpb pdf. This is an editable Powerpoint one stages graphic that deals with topics like vulnerability scanning process to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Comparative Analysis Of Vulnerability Scanning Application Security Testing
This slide showcases the difference between vulnerability scanning and penetration testing based on aspects such as nature, purpose, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Comparative Analysis Of Vulnerability Scanning Application Security Testing and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide showcases the difference between vulnerability scanning and penetration testing based on aspects such as nature, purpose, etc.

Security Testing Types Vulnerability Scanning Application Security Testing
This slide outlines the overview of vulnerability scanning in security testing for application security. Do you know about Slidesgeeks Security Testing Types Vulnerability Scanning Application Security Testing These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide outlines the overview of vulnerability scanning in security testing for application security.

Tools For Vulnerability Scanning In Security Testing Application Security Testing
This slide highlights the tools used for vulnerability scanning in security testing in application security which include Acunetix, Akto, etc. Retrieve professionally designed Tools For Vulnerability Scanning In Security Testing Application Security Testing to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide highlights the tools used for vulnerability scanning in security testing in application security which include Acunetix, Akto, etc.
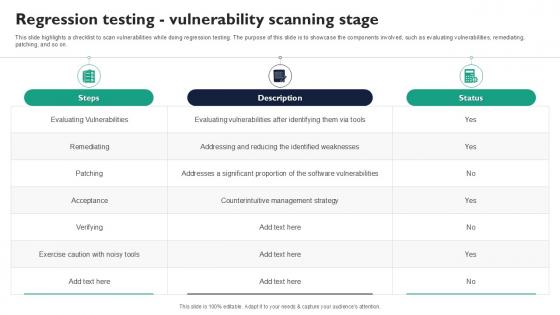
Regression Testing Vulnerability Scanning Stage Corrective Regression Testing Ppt Example
This slide highlights a checklist to scan vulnerabilities while doing regression testing. The purpose of this slide is to showcase the components involved, such as evaluating vulnerabilities, remediating, patching, and so on. Boost your pitch with our creative Regression Testing Vulnerability Scanning Stage Corrective Regression Testing Ppt Example. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide highlights a checklist to scan vulnerabilities while doing regression testing. The purpose of this slide is to showcase the components involved, such as evaluating vulnerabilities, remediating, patching, and so on.

Vulnerability Scanning With Integration And Reporting Ppt PowerPoint Presentation Pictures Clipart Images PDF
Presenting this set of slides with name vulnerability scanning with integration and reporting ppt powerpoint presentation pictures clipart images pdf. This is a one stage process. The stages in this process are patch inventory, patch catalogue, patch installation, patch integration, reporting. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Security Software Integration Pci Vulnerability Scan In Powerpoint And Google Slides Cpb
Introducing our well designed Security Software Integration Pci Vulnerability Scan In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Security Software Integration Pci Vulnerability Scan. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Security Software Integration Pci Vulnerability Scan In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Company Vulnerability Administration Conduct Vulnerability Assessment Activities Elements PDF
This is a company vulnerability administration conduct vulnerability assessment activities elements pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like execute vulnerability scans, execute vulnerability assessments, personnel should possess the skills to appropriately execute the tasks defined, individuals need to be trained to use the specific tools, techniques, and methodologies . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
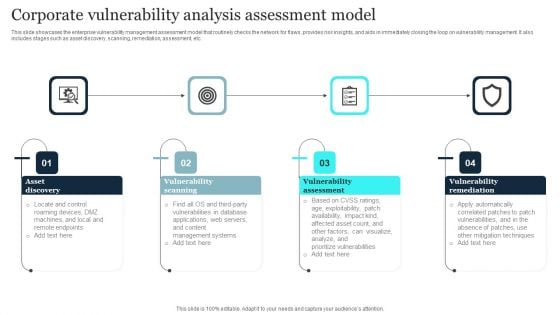
Corporate Vulnerability Analysis Assessment Model Elements PDF
This slide showcases the enterprise vulnerability management assessment model that routinely checks the network for flaws, provides risk insights, and aids in immediately closing the loop on vulnerability management. It also includes stages such as asset discovery, scanning, remediation, assessment, etc. Presenting Corporate Vulnerability Analysis Assessment Model Elements PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Vulnerability Assessment, Vulnerability Scanning, Asset Discovery. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
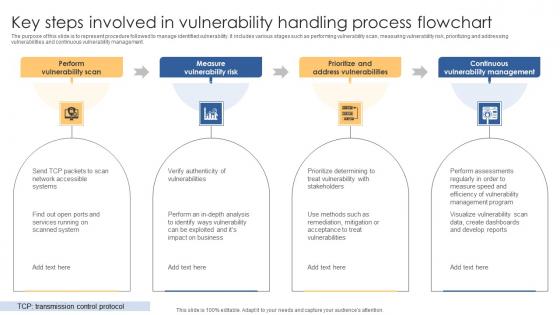
Key Steps Involved In Vulnerability Handling Process Flowchart Summary Pdf
The purpose of this slide is to represent procedure followed to manage identified vulnerability. It includes various stages such as performing vulnerability scan, measuring vulnerability risk, prioritizing and addressing vulnerabilities and continuous vulnerability management. Showcasing this set of slides titled Key Steps Involved In Vulnerability Handling Process Flowchart Summary Pdf. The topics addressed in these templates are Perform Vulnerability Scan, Measure Vulnerability Risk, Prioritize Address Vulnerabilities. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. The purpose of this slide is to represent procedure followed to manage identified vulnerability. It includes various stages such as performing vulnerability scan, measuring vulnerability risk, prioritizing and addressing vulnerabilities and continuous vulnerability management.
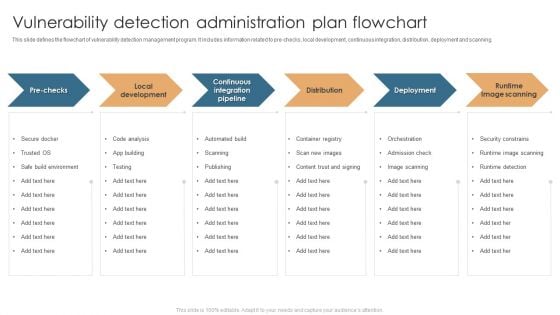
Vulnerability Detection Administration Plan Flowchart Sample PDF
This slide defines the flowchart of vulnerability detection management program. It includes information related to pre-checks, local development, continuous integration, distribution, deployment and scanning. Presenting Vulnerability Detection Administration Plan Flowchart Sample PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Local Development, Deployment, Runtime Image Scanning, Distribution. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
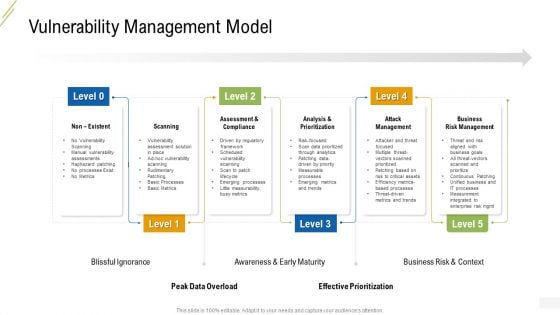
Company Vulnerability Administration Vulnerability Management Model Infographics PDF
This is a company vulnerability administration vulnerability management model infographics pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like assessment and compliance, analysis and prioritization, attack management, business risk management, scanning. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
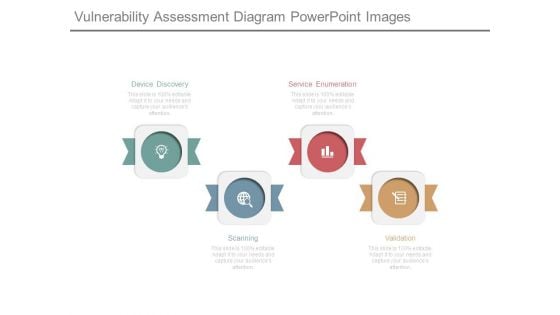
Vulnerability Assessment Diagram Powerpoint Images
This is a vulnerability assessment diagram powerpoint images. This is a four stage process. The stages in this process are device discovery, scanning, service enumeration, validation.
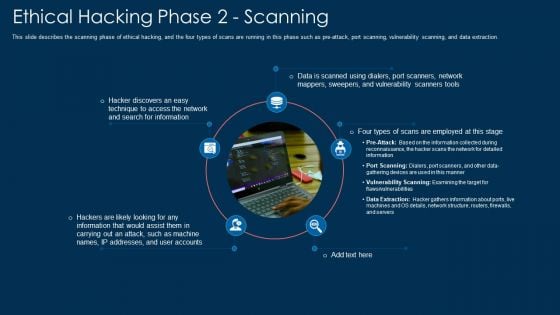
Ethical Hacking Phase 2 Scanning Ppt Infographic Template Design Templates PDF
This slide describes the scanning phase of ethical hacking, and the four types of scans are running in this phase such as pre-attack, port scanning, vulnerability scanning, and data extraction. This is a ethical hacking phase 2 scanning ppt infographic template design templates pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like information, network, technique. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Regression Testing Vulnerability Automated Regression Testing And Achieving PPT Template
This slide highlights a checklist to scan vulnerabilities while doing regression testing. The purpose of this slide is to showcase the components involved, such as evaluating vulnerabilities, remediating, patching, and so on. This Regression Testing Vulnerability Automated Regression Testing And Achieving PPT Template is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Regression Testing Vulnerability Automated Regression Testing And Achieving PPT Template features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide highlights a checklist to scan vulnerabilities while doing regression testing. The purpose of this slide is to showcase the components involved, such as evaluating vulnerabilities, remediating, patching, and so on.
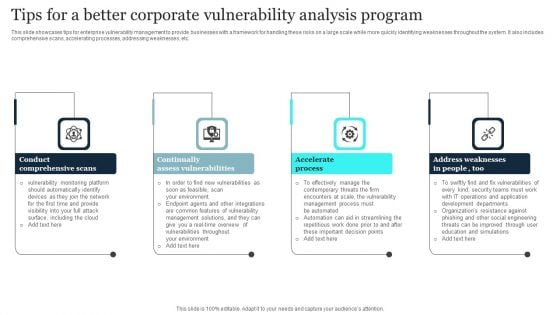
Tips For A Better Corporate Vulnerability Analysis Program Mockup PDF
This slide showcases tips for enterprise vulnerability management to provide businesses with a framework for handling these risks on a large scale while more quickly identifying weaknesses throughout the system. It also includes comprehensive scans, accelerating processes, addressing weaknesses, etc. Presenting Tips For A Better Corporate Vulnerability Analysis Program Mockup PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Continually Assess Vulnerabilities, Conduct Comprehensive Scan, Accelerate Process. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
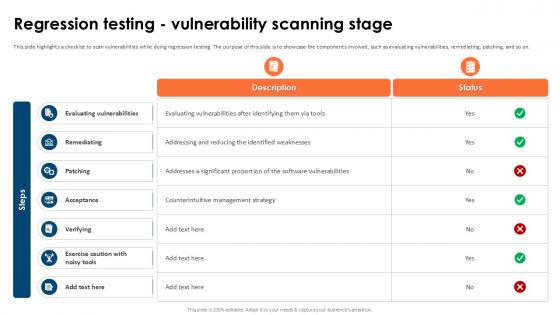
Regression Testing Vulnerability Partial Regression Testing For A Best PPT Example
This slide highlights a checklist to scan vulnerabilities while doing regression testing. The purpose of this slide is to showcase the components involved, such as evaluating vulnerabilities, remediating, patching, and so on. This Regression Testing Vulnerability Partial Regression Testing For A Best PPT Example is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Regression Testing Vulnerability Partial Regression Testing For A Best PPT Example features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide highlights a checklist to scan vulnerabilities while doing regression testing. The purpose of this slide is to showcase the components involved, such as evaluating vulnerabilities, remediating, patching, and so on.

Steps To Perform Vulnerability Analysis For Network Security Pictures Pdf
This slide showcase vulnerability assessment process that help organization to identify security vulnerabilities in network system and prioritize them to plan mitigation action plan. It includes steps such as identifying, scanning, identify type of scan, configure scan etc.Showcasing this set of slides titled Steps To Perform Vulnerability Analysis For Network Security Pictures Pdf The topics addressed in these templates are Evaluate Possible Risk, Interpret Scan Results, Create Mitigation Plan All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcase vulnerability assessment process that help organization to identify security vulnerabilities in network system and prioritize them to plan mitigation action plan. It includes steps such as identifying, scanning, identify type of scan, configure scan etc.
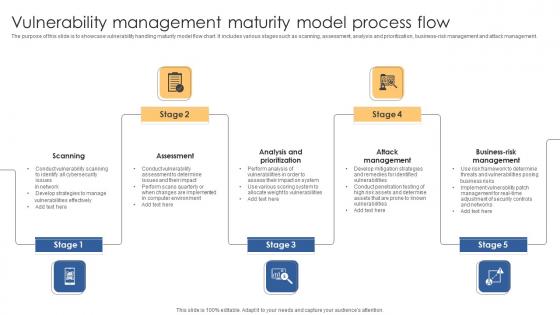
Vulnerability Management Maturity Model Process Flow Microsoft Pdf
The purpose of this slide is to showcase vulnerability handling maturity model flow chart. It includes various stages such as scanning, assessment, analysis and prioritization, business-risk management and attack management. Pitch your topic with ease and precision using this Vulnerability Management Maturity Model Process Flow Microsoft Pdf. This layout presents information on Scanning, Assessment, Analysis Prioritization. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. The purpose of this slide is to showcase vulnerability handling maturity model flow chart. It includes various stages such as scanning, assessment, analysis and prioritization, business-risk management and attack management.
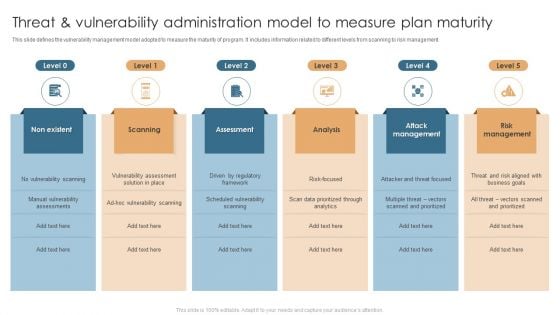
Threat And Vulnerability Administration Model To Measure Plan Maturity Structure PDF
This slide defines the vulnerability management model adopted to measure the maturity of program. It includes information related to different levels from scanning to risk management. Persuade your audience using this Threat And Vulnerability Administration Model To Measure Plan Maturity Structure PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Non Existent, Scanning, Assessment, Analysis, Attack Management. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
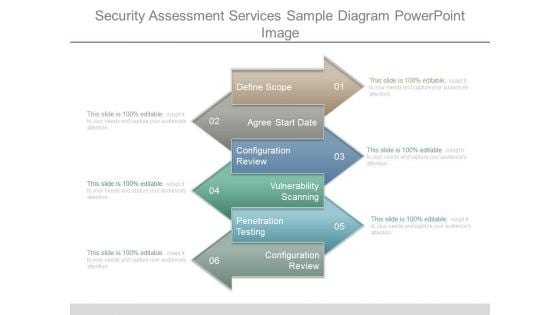
Security Assessment Services Sample Diagram Powerpoint Image
This is a security assessment services sample diagram powerpoint image. This is a six stage process. The stages in this process are define scope, agree start date, configuration review, vulnerability scanning, penetration testing, configuration review.

Technical Evaluation Chart Powerpoint Slides Templates
This is a technical evaluation chart powerpoint slides templates. This is a four stage process. The stages in this process are vulnerability scanning, penetration testing, configuration review, code review.
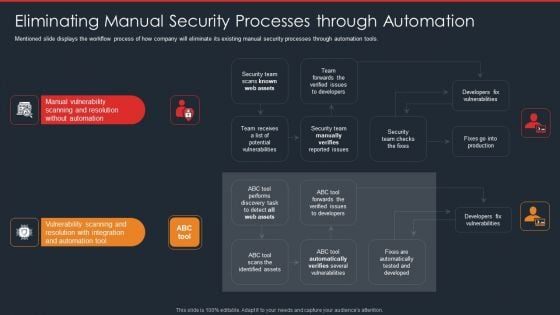
Data Safety Initiatives Eliminating Manual Security Processes Through Automation Topics PDF
Mentioned slide displays the workflow process of how company will eliminate its existing manual security processes through automation tools. This is a data safety initiatives eliminating manual security processes through automation topics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like manual vulnerability, scanning and resolution, vulnerability scanning, team. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Enterprise Workforce Software Development Roadmap Microsoft PDF
This slide shows extended team software development timeline. It provides information about cyber security, front end, back end, coding, integration, feasibility, vulnerability, backup, etc. Pitch your topic with ease and precision using this Enterprise Workforce Software Development Roadmap Microsoft PDF. This layout presents information on Extended Cyber, Security Team, Vulnerability Scan, Feasibility Analysis. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
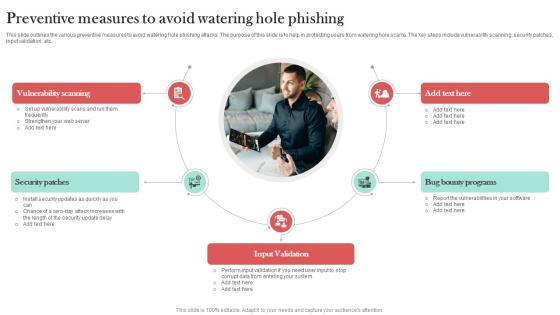
Preventive Measures To Avoid Watering Man In The Middle Phishing IT
This slide outlines the various preventive measures to avoid watering hole phishing attacks. The purpose of this slide is to help in protecting users from watering hole scams. The key steps include vulnerability scanning, security patches, input validation, etc. Present like a pro with Preventive Measures To Avoid Watering Man In The Middle Phishing IT. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide outlines the various preventive measures to avoid watering hole phishing attacks. The purpose of this slide is to help in protecting users from watering hole scams. The key steps include vulnerability scanning, security patches, input validation, etc.
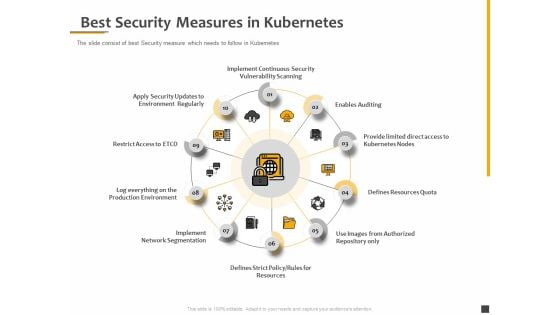
Understanding The Kubernetes Components Through Diagram Best Security Measures In Kubernetes Themes PDF
Presenting this set of slides with name understanding the kubernetes components through diagram best security measures in kubernetes themes pdf. This is a ten stage process. The stages in this process are implement continuous security vulnerability scanning, enables auditing, provide limited direct access to kubernetes nodes, defines resources quota, use images from authorized repository only, defines strict policy, rules for resources, implement network segmentation. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
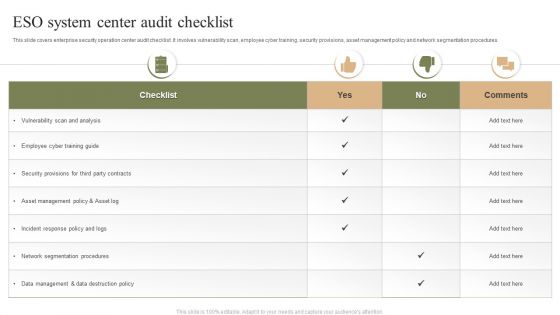
ESO System Center Audit Checklist Ppt PowerPoint Presentation Gallery Clipart Images PDF
This slide covers enterprise security operation center audit checklist. It involves vulnerability scan, employee cyber training, security provisions, asset management policy and network segmentation procedures. Showcasing this set of slides titled ESO System Center Audit Checklist Ppt PowerPoint Presentation Gallery Clipart Images PDF. The topics addressed in these templates are Checklist, Employee Cyber, Training Guide. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
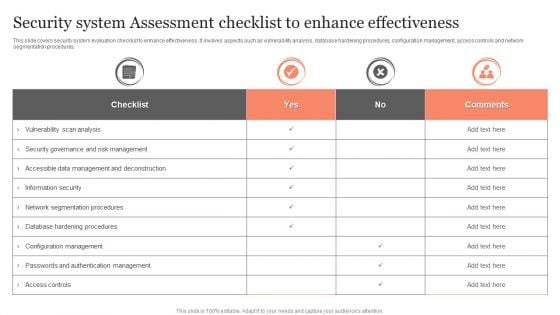
Security System Assessment Checklist To Enhance Effectiveness Ppt Visual Aids PDF
This slide covers security system evaluation checklist to enhance effectiveness. It involves aspects such as vulnerability analysis, database hardening procedures, configuration management, access controls and network segmentation procedures. Showcasing this set of slides titled Security System Assessment Checklist To Enhance Effectiveness Ppt Visual Aids PDF. The topics addressed in these templates are Checklist, Vulnerability Scan Analysis, Information Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
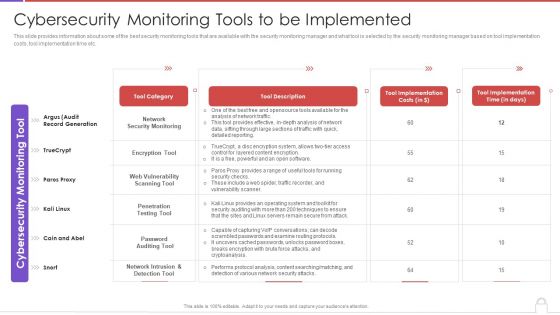
Methods To Develop Advanced Cybersecurity Monitoring Tools To Be Implemented Guidelines PDF
This slide provides information about some of the best security monitoring tools that are available with the security monitoring manager and what tool is selected by the security monitoring manager based on tool implementation costs, tool implementation time etc. Deliver an awe inspiring pitch with this creative methods to develop advanced cybersecurity monitoring tools to be implemented guidelines pdf bundle. Topics like network security monitoring, encryption tool, web vulnerability scanning tool can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
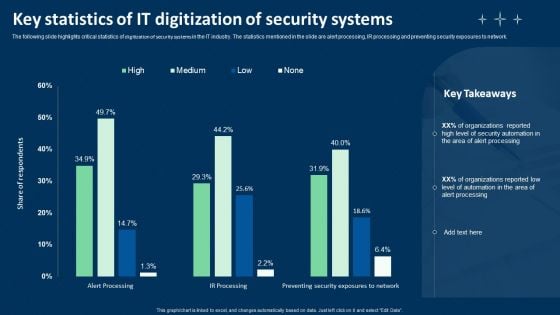
Key Statistics Of IT Digitization Of Security Systems Ppt Layouts Graphics PDF
The following slide highlights four step process of cloud digitization of security systems. The various steps are container configure management, using infrastructure as code, automating asset tagging and vulnerability scanning where security analysts should implement automation. Persuade your audience using this Key Statistics Of IT Digitization Of Security Systems Ppt Layouts Graphics PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Container Configure Management, Use Infrastructure, Code Automate Asset Tagging. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Multistep Process For Automating Cloud Security Operations Ppt Summary File Formats PDF
The following slide highlights four step process of cloud digitization of security systems. The various steps are container configure management, using infrastructure as code, automating asset tagging and vulnerability scanning where security analysts should implement automation. Persuade your audience using this Multistep Process For Automating Cloud Security Operations Ppt Summary File Formats PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Container Configure Management, Use Infrastructure Code, Automate Asset Tagging. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
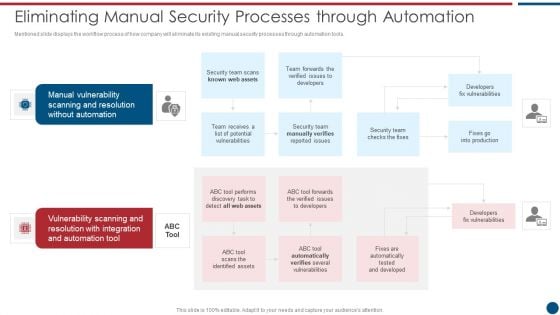
Risk Based Procedures To IT Security Eliminating Manual Security Processes Through Automation Information PDF
Mentioned slide displays the workflow process of how company will eliminate its existing manual security processes through automation tools. This is a Risk Based Procedures To IT Security Eliminating Manual Security Processes Through Automation Information PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Manual Vulnerability, Vulnerability Scanning, Automation Tool. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
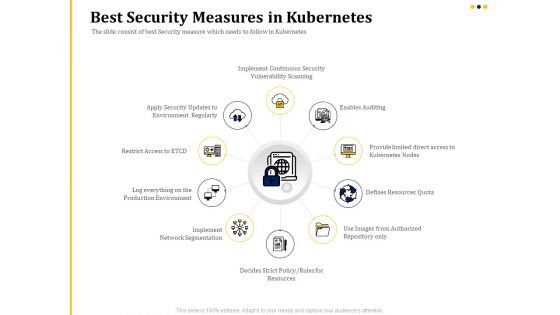
Understanding The Kubernetes Concepts And Architecture Best Security Measures In Kubernetes Ppt Outline Templates PDF
Presenting this set of slides with name understanding the kubernetes concepts and architecture best security measures in kubernetes ppt outline templates pdf. This is a ten stage process. The stages in this process are implement continuous security vulnerability scanning, enables auditing, provide limited direct access to kubernetes nodes, defines resources quota, use images from authorized repository only, defines strict policy, rules for resources, implement network segmentation. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Driving Digital Transformation Through Kubernetes And Containers Best Security Measures In Kubernetes Template PDF
Presenting this set of slides with name driving digital transformation through kubernetes and containers best security measures in kubernetes template pdf. This is a ten stage process. The stages in this process are implement continuous security vulnerability scanning, enables auditing, provide limited direct access to kubernetes nodes, defines resources quota, use images from authorized repository only, defines strict policy, rules for resources, implement network segmentation. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
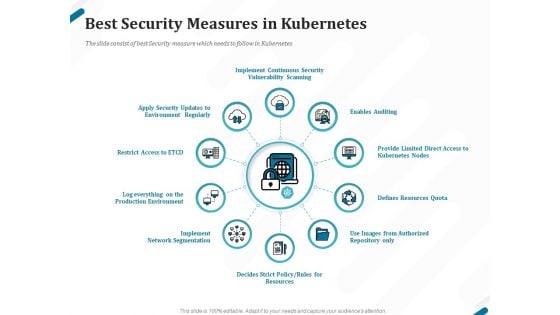
Kubernetes Containers Architecture Overview Best Security Measures In Kubernetes Ppt Pictures File Formats PDF
Presenting this set of slides with name kubernetes containers architecture overview best security measures in kubernetes ppt pictures file formats pdf. This is a ten stage process. The stages in this process are implement continuous security vulnerability scanning, enables auditing, provide limited direct access to kubernetes nodes, defines resources quota, use images from authorized repository only, defines strict policy, rules for resources, implement network segmentation. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
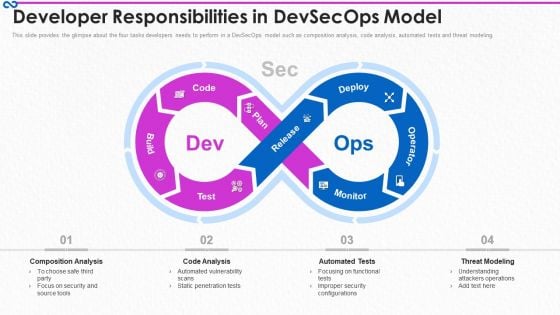
Development And Operations Procedure IT Developer Responsibilities In Devsecops Model Guidelines PDF
This slide provides the glimpse about the four tasks developers needs to perform in a DevSecOps model such as composition analysis, code analysis, automated tests and threat modeling.This is a development and operations procedure it developer responsibilities in devsecops model guidelines pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like composition analysis, automated vulnerability scans, focusing on functional tests You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Building Trust With IoT Security Deploy Tools For Continuous Device Monitoring And Diagnostics IoT SS V
This slide exhibits key activities and tools for monitoring and diagnostics of IoT device security. It includes activities such as continuous monitoring, anomaly detection, vulnerability scanning, auditing and reporting, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Building Trust With IoT Security Deploy Tools For Continuous Device Monitoring And Diagnostics IoT SS V is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Building Trust With IoT Security Deploy Tools For Continuous Device Monitoring And Diagnostics IoT SS V and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide exhibits key activities and tools for monitoring and diagnostics of IoT device security. It includes activities such as continuous monitoring, anomaly detection, vulnerability scanning, auditing and reporting, etc.
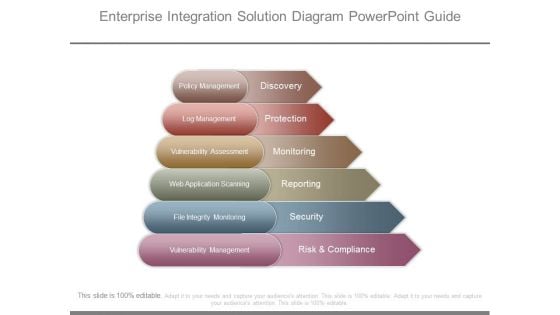
Enterprise Integration Solution Diagram Powerpoint Guide
This is a enterprise integration solution diagram powerpoint guide. This is a six stage process. The stages in this process are policy management, log management, vulnerability assessment, web application scanning, file integrity monitoring, vulnerability management, discovery, protection, monitoring, reporting, security, risk and compliance.
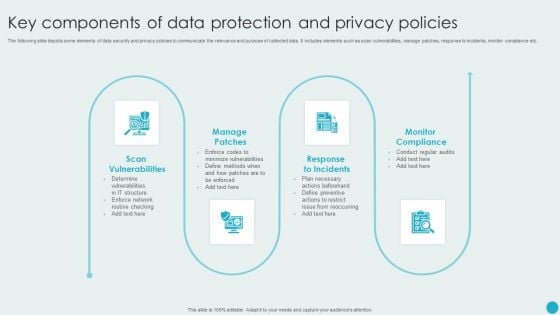
Key Components Of Data Protection And Privacy Policies Graphics PDF
The following slide depicts some elements of data security and privacy policies to communicate the relevance and purpose of collected data. It includes elements such as scan vulnerabilities, manage patches, response to incidents, monitor compliance etc. Presenting Key Components Of Data Protection And Privacy Policies Graphics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Manage Patches, Response To Incidents, Monitor Compliance. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.


 Continue with Email
Continue with Email

 Home
Home


































