Waf
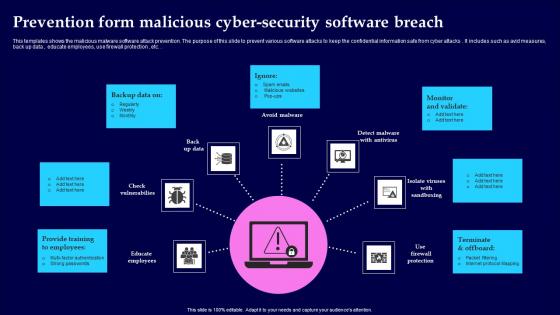
Prevention Form Malicious Cyber Security Software Breach Portrait Pdf
This templates shows the malicious malware software attack prevention. The purpose of this slide to prevent various software attacks to keep the confidential information safe from cyber attacks. It includes such as avid measures, back up data , educate employees, use firewall protection , etc. Showcasing this set of slides titled Prevention Form Malicious Cyber Security Software Breach Portrait Pdf The topics addressed in these templates are Provide Training, Monitor And Validate, Terminate And Offboard All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This templates shows the malicious malware software attack prevention. The purpose of this slide to prevent various software attacks to keep the confidential information safe from cyber attacks. It includes such as avid measures, back up data , educate employees, use firewall protection , etc.

Architecture Of Citrix Secure Web Gateway Proxy Solution Web Threat Protection System
This slide represents the Secure Web Gateway solution provided by Citrix. The purpose of this slide is to demonstrate the architecture of Citrixs SWG solution. The key components included are users, firewall, internet, logstream, SWG appliance, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Architecture Of Citrix Secure Web Gateway Proxy Solution Web Threat Protection System for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide represents the Secure Web Gateway solution provided by Citrix. The purpose of this slide is to demonstrate the architecture of Citrixs SWG solution. The key components included are users, firewall, internet, logstream, SWG appliance, etc.

A52 Zero Trust Network Access System Use Cases
This slide outlines multiple use cases of zero-trust network access systems. The purpose of this slide is to showcase the main use cases of the ZTNA model, which are replacing VPN and MPLS connections, internal firewall replacement, securing remote access to private apps, limiting user access, and so on. There are so many reasons you need a A52 Zero Trust Network Access System Use Cases. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide outlines multiple use cases of zero-trust network access systems. The purpose of this slide is to showcase the main use cases of the ZTNA model, which are replacing VPN and MPLS connections, internal firewall replacement, securing remote access to private apps, limiting user access, and so on.

IoT Device Management Fundamentals IoT Architecture For Connected Medical Devices IoT Ss V
This slide covers IoT embedded architecture to monitor and analyse connected devices performance. It includes key components such as connected medical sensor, gateway, firewall, data processor, data lake, data analytics, etc. The IoT Device Management Fundamentals IoT Architecture For Connected Medical Devices IoT SS V is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide covers IoT embedded architecture to monitor and analyse connected devices performance. It includes key components such as connected medical sensor, gateway, firewall, data processor, data lake, data analytics, etc.

Tool Driven User Replacement Architecture Stress Testing For Robust Ppt Example
The purpose of this slide is to highlight the architecture of load testing it includes components such as load tool, internet, firewall, load balancer, database, etc. The Tool Driven User Replacement Architecture Stress Testing For Robust Ppt Example is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. The purpose of this slide is to highlight the architecture of load testing it includes components such as load tool, internet, firewall, load balancer, database, etc.

About Us For Our Intelligent Intrusion Prevention System Ppt Template
This slide gives an overview of the firewall solutions provider company. It includes the total number of clients, employees, successful projects, partnerships and collaborations with industry leading organizations, and history.Find a pre designed and impeccable About Us For Our Intelligent Intrusion Prevention System Ppt Template. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide gives an overview of the firewall solutions provider company. It includes the total number of clients, employees, successful projects, partnerships and collaborations with industry leading organizations, and history.
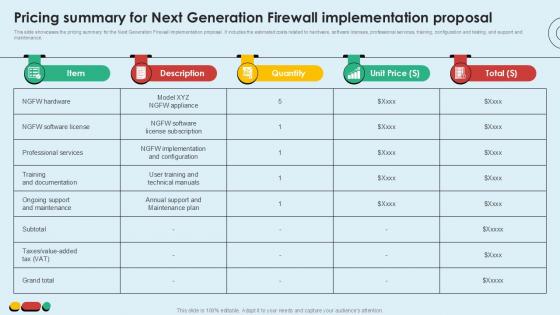
Pricing Summary For Next Generation Intelligent Intrusion Prevention System Ppt Sample
This slide showcases the pricing summary for the Next Generation Firewall implementation proposal. It includes the estimated costs related to hardware, software licenses, professional services, training, configuration and testing, and support and maintenance.Find highly impressive Pricing Summary For Next Generation Intelligent Intrusion Prevention System Ppt Sample on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Pricing Summary For Next Generation Intelligent Intrusion Prevention System Ppt Sample for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide showcases the pricing summary for the Next Generation Firewall implementation proposal. It includes the estimated costs related to hardware, software licenses, professional services, training, configuration and testing, and support and maintenance.
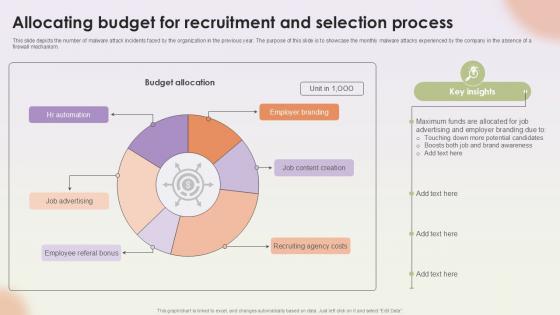
Allocating Budget For Recruitment Workforce Procurement And Aptitude Evaluation Ppt Slides
This slide depicts the number of malware attack incidents faced by the organization in the previous year. The purpose of this slide is to showcase the monthly malware attacks experienced by the company in the absence of a firewall mechanism. Boost your pitch with our creative Allocating Budget For Recruitment Workforce Procurement And Aptitude Evaluation Ppt Slides. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide depicts the number of malware attack incidents faced by the organization in the previous year. The purpose of this slide is to showcase the monthly malware attacks experienced by the company in the absence of a firewall mechanism.

ITIL Strategy Service Excellence Client Standards Checklist Contd Ppt PowerPoint Presentation Styles Example PDF
Presenting this set of slides with name itil strategy service excellence client standards checklist contd ppt powerpoint presentation styles example pdf. This is a one stage process. The stages in this process are genuine anti spam solution, vendor supported server, licensed firewall between internal, secured encryption, wireless data traffic, environment, high speed internet access. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
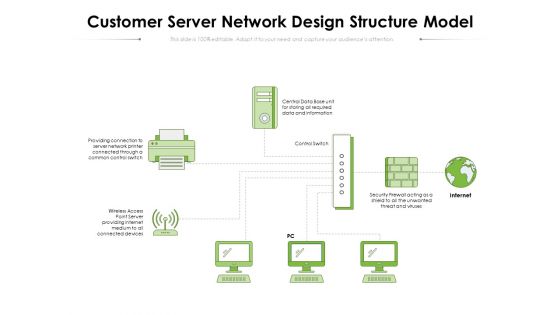
Customer Server Network Design Structure Model Ppt PowerPoint Presentation Gallery Graphics PDF
Presenting this set of slides with name customer server network design structure model ppt powerpoint presentation gallery graphics pdf. This is a one stage process. The stages in this process are central data base, data and information, internet, control switch, providing connection to server, common control switch, wireless access point server, providing internet medium, security firewall acting, threat and viruses. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
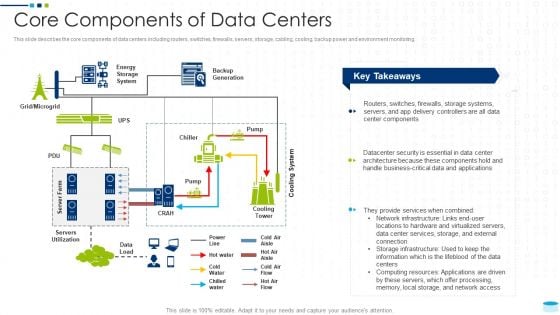
Data Center Infrastructure Management IT Core Components Of Data Centers Rules PDF
This slide describes the core components of data centers including routers, switches, firewalls, servers, storage, cabling, cooling, backup power and environment monitoring. Deliver and pitch your topic in the best possible manner with this data center infrastructure management it core components of data centers rules pdf. Use them to share invaluable insights on servers utilization, server farm, energy storage system, backup generation and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
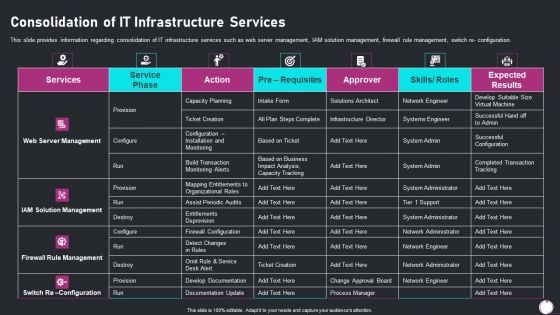
Information Technology Transformation Playbook Consolidation Of IT Infrastructure Services Graphics PDF
This slide provides information regarding consolidation of IT infrastructure services such as web server management, IAM solution management, firewall rule management, switch re- configuration. Deliver an awe inspiring pitch with this creative information technology transformation playbook consolidation of it infrastructure services graphics pdf bundle. Topics like consolidation of it infrastructure services can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Reverse Proxy Server IT Anonymous Proxy Server And Its Architecture Ppt Infographic Template Icon PDF
The following slide showcases the anonymous proxy server, how it hides the users identity and how it helps users access the restricted data by avoiding firewall settings. Deliver an awe inspiring pitch with this creative reverse proxy server it anonymous proxy server and its architecture ppt infographic template icon pdf bundle. Topics like proxy server, access restricted recreational, pornographic can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
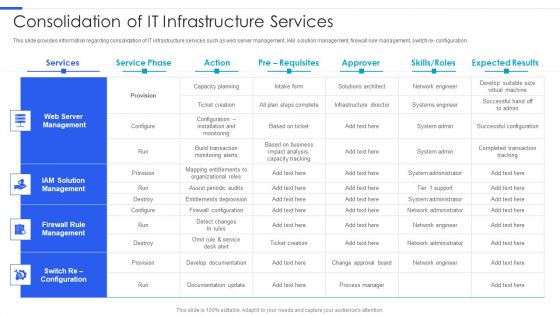
Playbook For Managing Information Consolidation Of IT Infrastructure Services Download PDF
This slide provides information regarding consolidation of IT infrastructure services such as web server management, IAM solution management, firewall rule management, switch re- configuration. Deliver an awe inspiring pitch with this creative Playbook For Managing Information Consolidation Of IT Infrastructure Services Download PDF bundle. Topics like Web Server Management, IAM Solution Management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
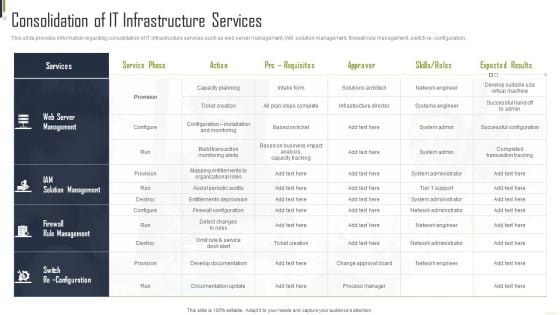
Consolidation Of IT Infrastructure Services Playbook For Information Inspiration PDF
This slide provides information regarding consolidation of IT infrastructure services such as web server management, IAM solution management, firewall rule management, switch re- configuration. Deliver and pitch your topic in the best possible manner with this Consolidation Of IT Infrastructure Services Playbook For Information Inspiration PDF. Use them to share invaluable insights on Solution Management, Rule Management, Successful Configuration and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
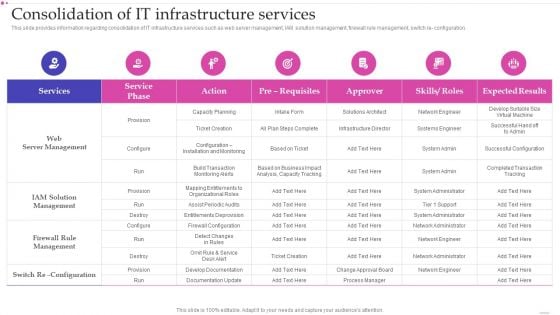
Optimizing IT Infrastructure Playbook Consolidation Of IT Infrastructure Services Structure PDF
This slide provides information regarding consolidation of IT infrastructure services such as web server management, IAM solution management, firewall rule management, switch re configuration.Deliver an awe inspiring pitch with this creative Optimizing IT Infrastructure Playbook Consolidation Of IT Infrastructure Services Structure PDF bundle. Topics like Installation Monitoring, Rule Management, Documentation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
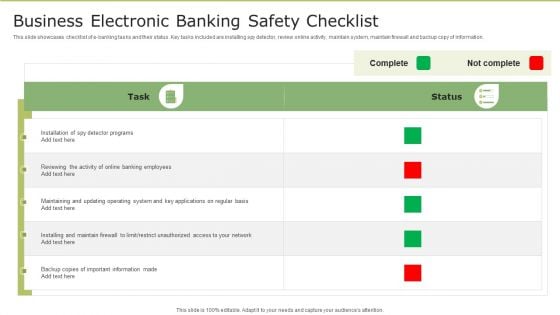
Business Electronic Banking Safety Checklist Introduction PDF
This slide showcases checklist of e banking tasks and their status. Key tasks included are installing spy detector, review online activity, maintain system, maintain firewall and backup copy of information. Showcasing this set of slides titled Business Electronic Banking Safety Checklist Introduction PDF. The topics addressed in these templates are Key Applications, Operating System, Network. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
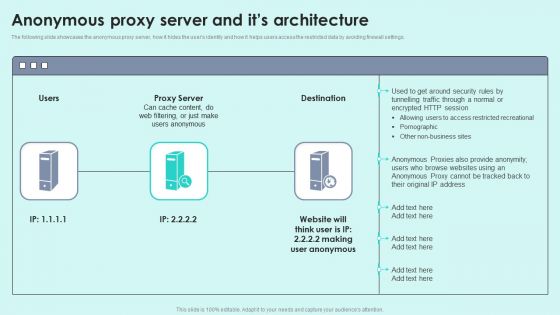
Anonymous Proxy Server And Its Architecture Reverse Proxy For Load Balancing Slides PDF
The following slide showcases the anonymous proxy server, how it hides the users identity and how it helps users access the restricted data by avoiding firewall settings.Deliver and pitch your topic in the best possible manner with this Anonymous Proxy Server And Its Architecture Reverse Proxy For Load Balancing Slides PDF. Use them to share invaluable insights on Restricted Recreational, Tunnelling Traffic, Anonymous Proxy and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Secure Proxy Connection To Content Server Reverse Proxy For Load Balancing Designs PDF
This slide describes the secure proxy connection to the content server and how data is transmitted over the connection securely via data encryption. Deliver an awe inspiring pitch with this creative Secure Proxy Connection To Content Server Reverse Proxy For Load Balancing Designs PDF bundle. Topics like Servers Outside, Encrypted Secure, Outside Firewall can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
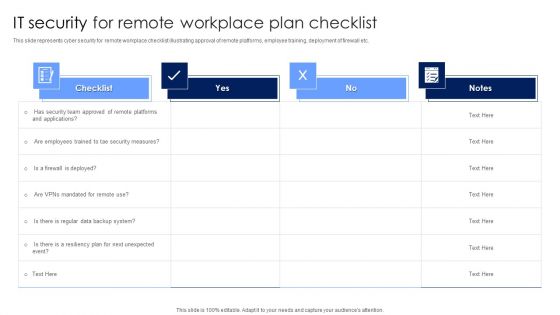
IT Security For Remote Workplace Plan Checklist Introduction PDF
This slide represents cyber security for remote workplace checklist illustrating approval of remote platforms, employee training, deployment of firewall etc. Pitch your topic with ease and precision using this IT Security For Remote Workplace Plan Checklist Introduction PDF. This layout presents information on Security Measures, Employees, Team. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
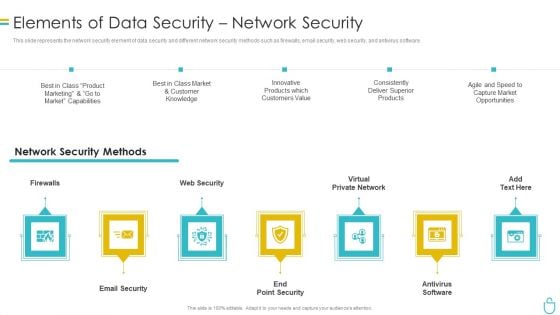
Information Security Elements Of Data Security Network Security Ppt Visual Aids Infographics PDF
This slide represents the network security element of data security and different network security methods such as firewalls, email security, web security, and antivirus software. Presenting information security elements of data security network security ppt visual aids infographics pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like customer, market, product, opportunities, network. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
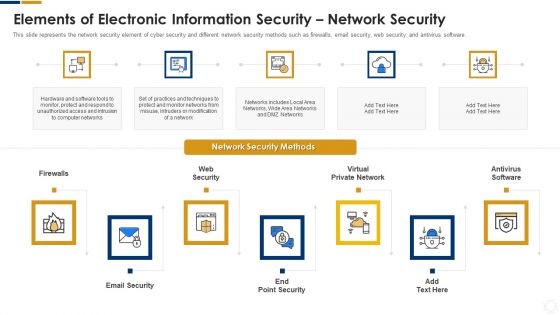
Cybersecurity Elements Of Electronic Information Security Network Security Ppt Ideas Skills PDF
This slide represents the network security element of cyber security and different network security methods such as firewalls, email security, web security, and antivirus software. This is a cybersecurity elements of electronic information security network security ppt ideas skills pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like email security, web security, virtual private network, antivirus software. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
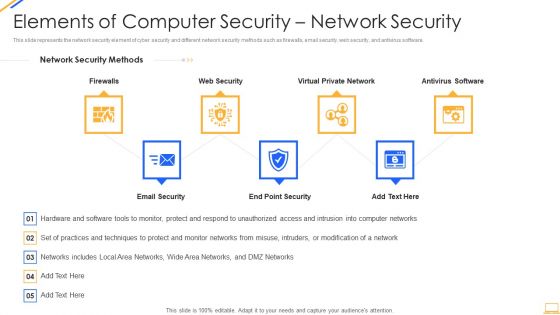
Desktop Security Management Elements Of Computer Security Network Security Infographics PDF
This slide represents the network security element of cyber security and different network security methods such as firewalls, email security, web security, and antivirus software. Presenting desktop security management elements of computer security network security infographics pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like network, security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
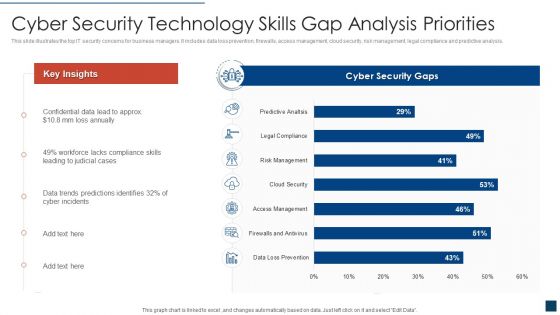
Cyber Security Technology Skills Gap Analysis Priorities Clipart PDF
This slide illustrates the top IT security concerns for business managers. It includes data loss prevention, firewalls, access management, cloud security, risk management, legal compliance and predictive analysis. Showcasing this set of slides titled cyber security technology skills gap analysis priorities clipart pdf. The topics addressed in these templates are cyber security technology skills gap analysis priorities. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Elements Of Information Technology Security Information Technology Security Ppt Inspiration Icons PDF
This slide represents the network security element of network security and different network security methods such as firewalls, email security, web security, and antivirus software. Presenting elements of information technology security information technology security ppt inspiration icons pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like network security methods, tools, techniques, respond. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
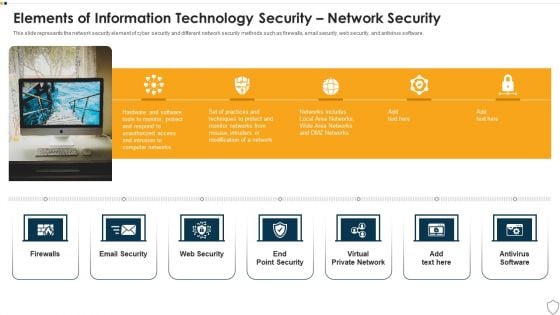
IT Security Elements Of Information Technology Security Network Security Ppt Pictures Graphics PDF
This slide represents the network security element of cyber security and different network security methods such as firewalls, email security, web security, and antivirus software. Presenting it security elements of information technology security network security ppt pictures graphics pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like web security, end point security, virtual private network, email security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
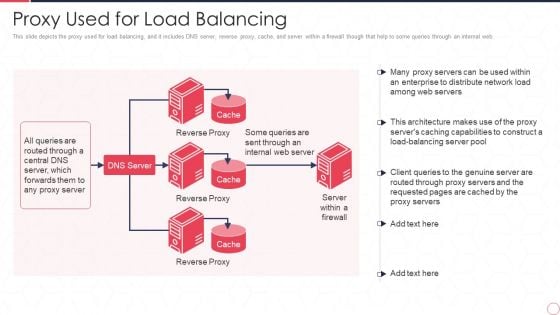
Reverse Proxy Server IT Proxy Used For Load Balancing Ppt Show Design Inspiration PDF
This slide depicts the proxy used for load balancing, and it includes DNS server, reverse proxy, cache, and server within a firewall though that help to some queries through an internal web. Presenting reverse proxy server it proxy used for load balancing ppt show design inspiration pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like reverse proxy, dns server, cache. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
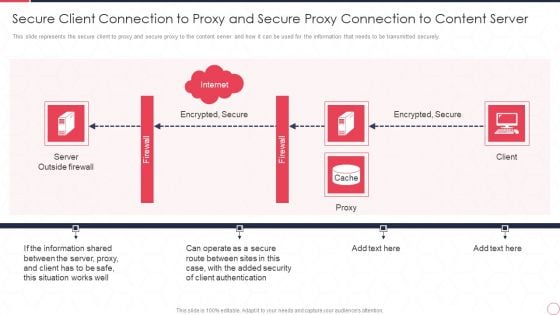
Reverse Proxy Server IT Secure Client Connection To Proxy And Secure Proxy Connection Ppt Infographic Template Design Inspiration PDF
This slide represents the secure client to proxy and secure proxy to the content server and how it can be used for the information that needs to be transmitted securely. This is a reverse proxy server it secure client connection to proxy and secure proxy connection ppt infographic template design inspiration pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like server outside firewall, encrypted, secure, proxy, client. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
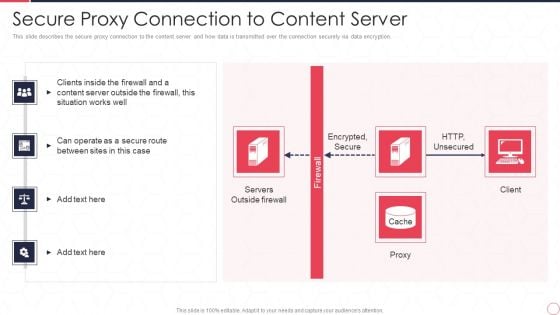
Reverse Proxy Server IT Secure Proxy Connection To Content Server Ppt Gallery Brochure PDF
This slide describes the secure proxy connection to the content server and how data is transmitted over the connection securely via data encryption. Presenting reverse proxy server it secure proxy connection to content server ppt gallery brochure pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like encrypted, secure, http, unsecured, servers, outside firewall, proxy, client. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

5 Key Practices To Prevent Cyber Phishing Scams And Attacks Graphics PDF
Mentioned slide showcases best practices which can be implemented to prevent cyber phishing. The practices are recognizing hyperlinks attached in an email, backup system copies, secure robust HTTPs connections, installing a firewall and using anti spam tools. Presenting 5 key practices to prevent cyber phishing scams and attacks graphics pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including secure, device, reduced. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cybersecurity Risk Administration Plan Setting Scenario For Security Control Topics PDF
Following slide displays security control scenario setting. It includes scenario detail, category of security controls and controls description.Presenting Cybersecurity Risk Administration Plan Setting Scenario For Security Control Topics PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Category Of Security Controls, Controls Description, Secured Firewall Configuration In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
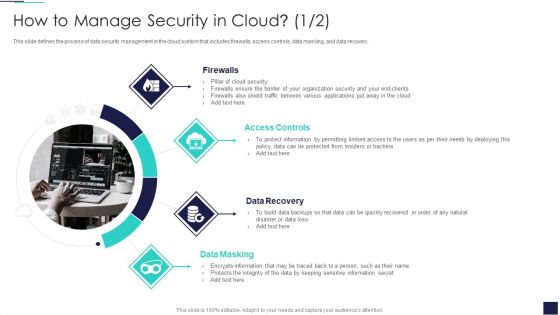
Cloud Information Security How To Manage Security In Cloud Ppt Ideas Example Topics PDF
This slide defines the process of data security management in the cloud system that includes firewalls, access controls, data masking, and data recovery. Presenting Cloud Information Security How To Manage Security In Cloud Ppt Ideas Example Topics PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Access Controls, Data Recovery, Data Masking. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
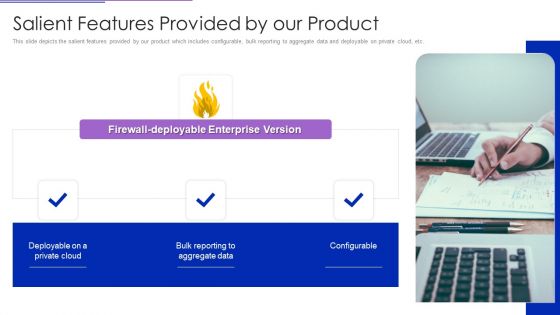
Bliss Investor Capital Raising Elevator Pitch Deck Salient Features Provided By Our Product Demonstration PDF
This slide depicts the salient features provided by our product which includes configurable, bulk reporting to aggregate data and deployable on private cloud, etc.Presenting Bliss Investor Capital Raising Elevator Pitch Deck Salient Features Provided By Our Product Demonstration PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Firewall Deployable, Enterprise Version, Aggregate Data In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Payment Card Industry Financial Regulatory Compliance Icons PDF
This slide showcases compliance of payment card industry. It includes conducting regular system tests, protecting cardholder data by encrypting and firewall, creating unique system password and maintaining security policy.Persuade your audience using this Payment Card Industry Financial Regulatory Compliance Icons PDF This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Maintaining Security, Encrypting Cardholder, Assigning A Unique Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
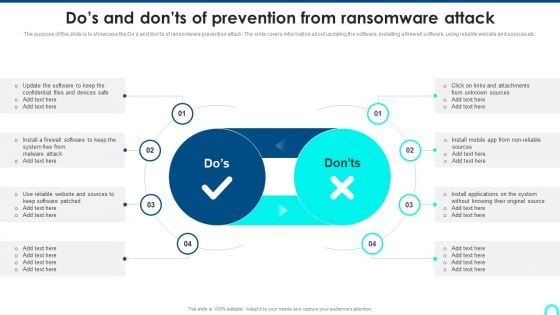
Dos And Donts Of Prevention From Ransomware Attack Summary PDF
The purpose of this slide is to showcase the Dos and donts of ransomware prevention attack. The slide covers information about updating the software, installing a firewall software, using reliable website and sources etc.Deliver and pitch your topic in the best possible manner with this Dos And Donts Of Prevention From Ransomware Attack Summary PDF. Use them to share invaluable insights on Confidential Files, Install Applications, Keep Software and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
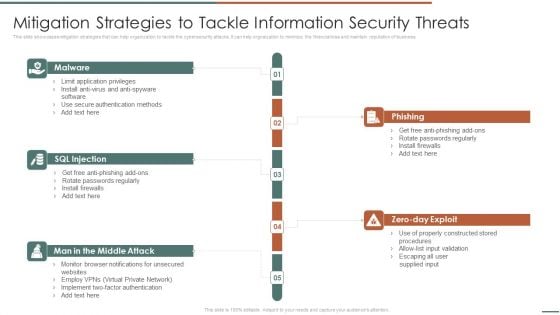
Information Security Risk Evaluation Mitigation Strategies To Tackle Information Security Threats Designs PDF
This slide showcases mitigation strategies that can help organization to tackle the cybersecurity attacks. It can help orgnaization to minimize the financial loss and maintain reputation of business.Presenting Information Security Risk Evaluation Mitigation Strategies To Tackle Information Security Threats Designs PDF to provide visual cues and insights. Share and navigate important information on fivestages that need your due attention. This template can be used to pitch topics like Phishing, Rotate Passwords, Install Firewalls. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
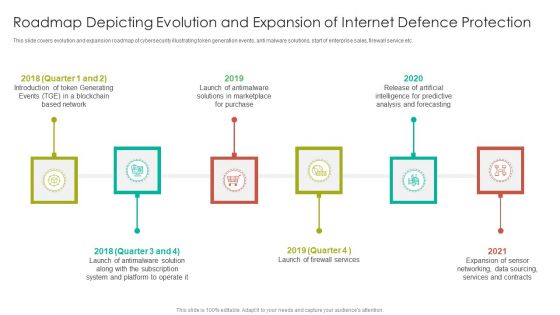
Roadmap Depicting Evolution And Expansion Of Internet Defence Protection Guidelines PDF
This slide covers evolution and expansion roadmap of cybersecurity illustrating token generation events, anti malware solutions, start of enterprise sales, firewall service etc.Persuade your audience using this Roadmap Depicting Evolution And Expansion Of Internet Defence Protection Guidelines PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Token Generating, Solutions Marketplace, Launch Antimalware. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
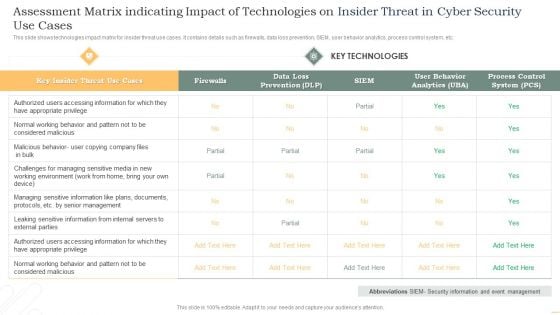
Assessment Matrix Indicating Impact Of Technologies On Insider Threat In Cyber Security Use Cases Themes PDF
This slide shows technologies impact matrix for insider threat use cases. It contains details such as firewalls, data loss prevention, SIEM, user behavior analytics, process control system, etc. Showcasing this set of slides titled Assessment Matrix Indicating Impact Of Technologies On Insider Threat In Cyber Security Use Cases Themes PDF. The topics addressed in these templates are Key Insider, Threat, Use Cases, Key Technologies. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
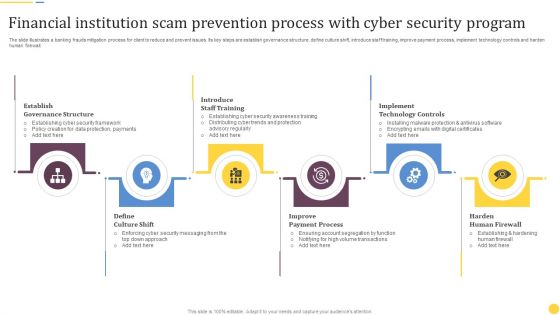
Financial Institution Scam Prevention Process With Cyber Security Program Rules PDF
The slide illustrates a banking frauds mitigation process for client to reduce and prevent issues. Its key steps are establish governance structure, define culture shift, introduce staff training, improve payment process, implement technology controls and harden human firewall. Presenting Financial Institution Scam Prevention Process With Cyber Security Program Rules PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Establish Governance Structure, Introduce Staff Training, Implement Technology Controls. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
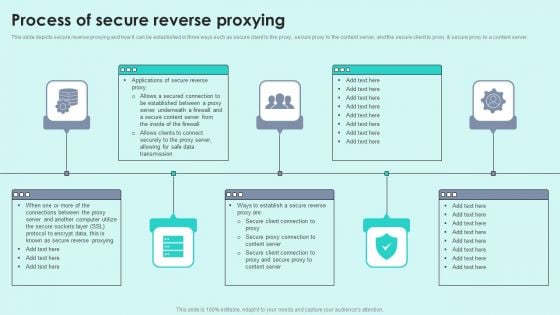
Process Of Secure Reverse Proxying Reverse Proxy For Load Balancing Microsoft PDF
This slide depicts secure reverse proxying and how it can be established in three ways such as secure client to the proxy, secure proxy to the content server, and the secure client to proxy secure proxy to a content server.This is a Process Of Secure Reverse Proxying Reverse Proxy For Load Balancing Microsoft PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Secured Connection, Established Between, Underneath Firewall. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Proxy Used For Load Balancing Reverse Proxy For Load Balancing Icons PDF
This slide depicts the proxy used for load balancing, and it includes DNS server, reverse proxy, cache, and server within a firewall though that help to some queries through an internal web.Deliver an awe inspiring pitch with this creative Proxy Used For Load Balancing Reverse Proxy For Load Balancing Icons PDF bundle. Topics like Reverse Proxy, Distribute Network, Capabilities Construct, Servers Requested can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Corporate Based Software Quality Assurance Matrix Icons PDF
This slide covers quality assurance matrix to test software application. It includes categories such as specification, features, corporate needs, technical requirements comprising of SSL certification, firewall, VPN servers, etc., along with competitor analysis and direction of movement with relationships. Pitch your topic with ease and precision using this Corporate Based Software Quality Assurance Matrix Icons PDF. This layout presents information on Competitor Analysis, Target, Requirements. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
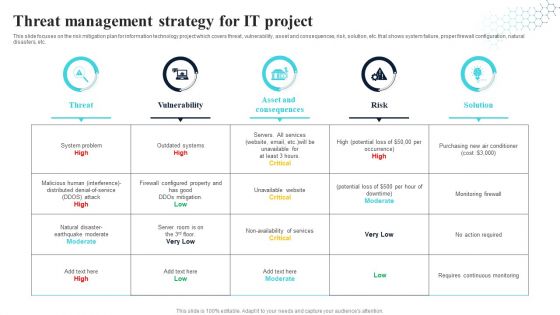
Threat Management Strategy For It Project Themes PDF
This slide focuses on the risk mitigation plan for information technology project which covers threat, vulnerability, asset and consequences, risk, solution, etc. that shows system failure, proper firewall configuration, natural disasters, etc. Pitch your topic with ease and precision using this Threat Management Strategy For It Project Themes PDF. This layout presents information on Vulnerability, Asset And Consequences, Risk. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
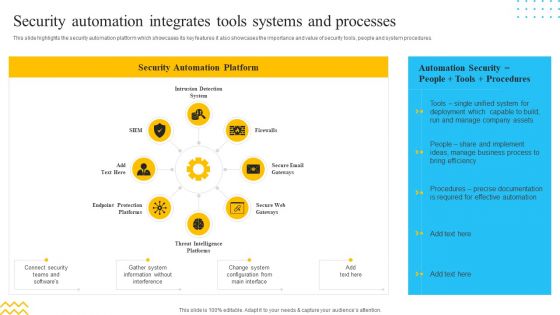
IT Security Automation Tools Integration Security Automation Integrates Tools Systems Summary PDF
This slide highlights the security automation platform which showcases its key features it also showcases the importance and value of security tools, people and system procedures. This is a IT Security Automation Tools Integration Security Automation Integrates Tools Systems Summary PDF template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Intrusion Detection System, Firewalls, Secure Email Gateways. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
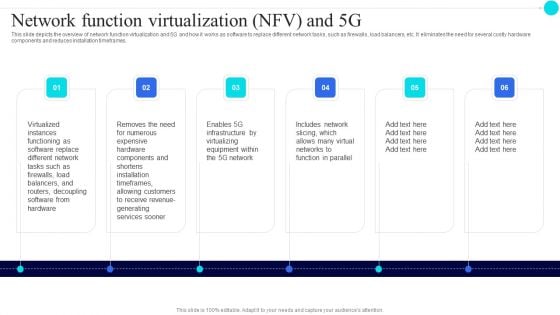
Network Function Virtualization Nfv And 5G 5G Functional Architecture Clipart PDF
This slide depicts the overview of network function virtualization and 5G and how it works as software to replace different network tasks, such as firewalls, load balancers, etc. It eliminates the need for several costly hardware components and reduces installation timeframes.Presenting Network Function Virtualization Nfv And 5G 5G Functional Architecture Clipart PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Allowing Customers, Expensive Hardware, Function Parallel. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
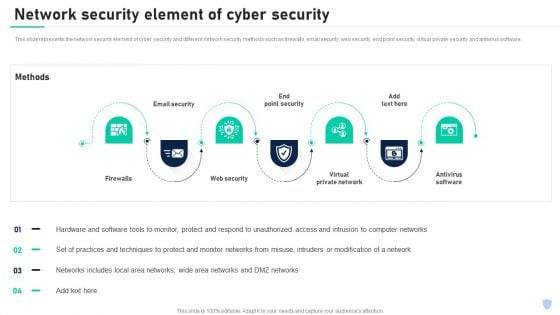
Cyber Security Components To Enhance Processes Network Security Element Of Cyber Security Ideas PDF
This slide represents the network security element of cyber security and different network security methods such as firewalls, email security, web security, end point security, virtual private security and antivirus software. There are so many reasons you need a Cyber Security Components To Enhance Processes Network Security Element Of Cyber Security Ideas PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
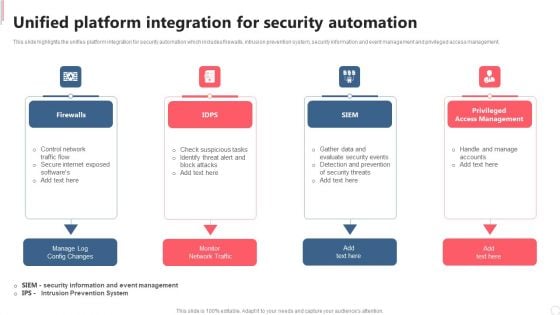
Cyber Security Automation Framework Unified Platform Integration For Security Automation Template PDF
This slide highlights the unifies platform integration for security automation which includes firewalls, intrusion prevention system, security information and event management and privileged access management. Present like a pro with Cyber Security Automation Framework Unified Platform Integration For Security Automation Template PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
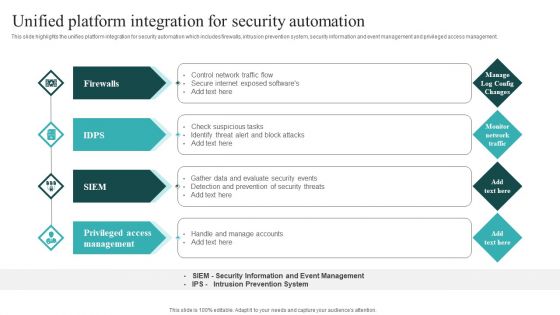
IT Security Automation Systems Guide Unified Platform Integration For Security Automation Background PDF
This slide highlights the unifies platform integration for security automation which includes firewalls, intrusion prevention system, security information and event management and privileged access management. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit IT Security Automation Systems Guide Unified Platform Integration For Security Automation Background PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.
Reverse Proxy Web Server Anonymous Proxy Server And Its Architecture Icons PDF
The following slide showcases the anonymous proxy server, how it hides the users identity and how it helps users access the restricted data by avoiding firewall settings. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Reverse Proxy Web Server Anonymous Proxy Server And Its Architecture Icons PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
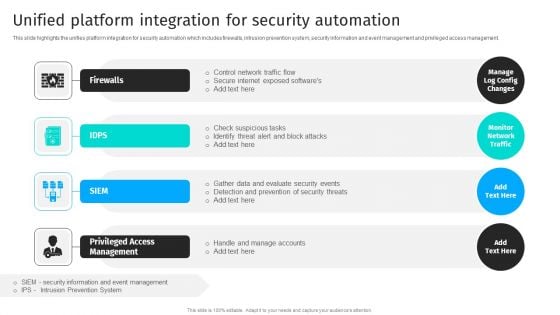
Security Automation To Analyze And Mitigate Cyberthreats Unified Platform Integration Themes PDF
This slide highlights the unifies platform integration for security automation which includes firewalls, intrusion prevention system, security information and event management and privileged access management.The Security Automation To Analyze And Mitigate Cyberthreats Unified Platform Integration Themes PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
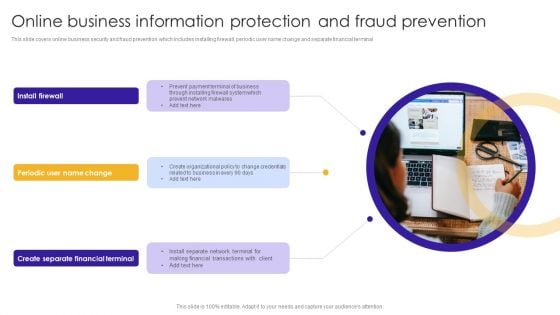
Online Business Information Protection And Fraud Prevention Topics PDF
This slide covers online business security and fraud prevention which includes installing firewall, periodic user name change and separate financial terminal. Persuade your audience using this Online Business Information Protection And Fraud Prevention Topics PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Create Separate, Financial Terminal, Prevent Network. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Competitor Analysis Grid Of Security Software Inspiration PDF
This slide provides an overview of the comparison among various software. The comparison is done on the basis of features that are antivirus, firewall, system cleansing, anti-spyware and parental control. Pitch your topic with ease and precision using this Competitor Analysis Grid Of Security Software Inspiration PDF. This layout presents information on System Cleansing, Everyday Backup Option, Anti Spyware. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
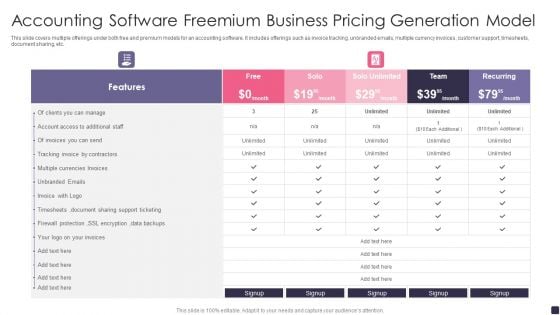
Accounting Software Freemium Business Pricing Generation Model Pictures PDF
This slide covers multiple offerings under both free and premium models for an accounting software. It includes offerings such as invoice tracking, unbranded emails, multiple currency invoices, customer support, timesheets, document sharing, etc.Showcasing this set of slides titled Accounting Software Freemium Business Pricing Generation Model Pictures PDF. The topics addressed in these templates are Tracking Invoice, Timesheets Document, Firewall Protection. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
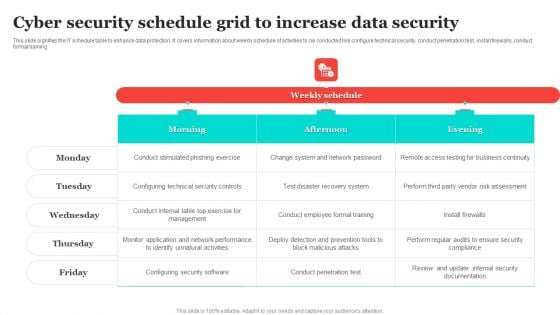
Cyber Security Schedule Grid To Increase Data Security Structure PDF
This slide signifies the IT schedule table to enhance data protection. It covers information about weekly schedule of activities to be conducted like configure technical security, conduct penetration test, install firewalls, conduct formal training. Pitch your topic with ease and precision using this Cyber Security Schedule Grid To Increase Data Security Structure PDF. This layout presents information on Recovery System, Vendor Risk Assessment, Configuring Security Software. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Artificial Intelligence Machine Learning In Information Technology Industry Icons PDF
This slide showcase how machine learning is a critical component of process automation for smarter incident management systems, efficient resource use, and the shift of IT operations from a reactive to a predictive mode. It includes supervised training, unsupervised instruction, and self learning optimization in AI learning applications. Presenting Artificial Intelligence Machine Learning In Information Technology Industry Icons PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Data Centres, Firewalls, Routers. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
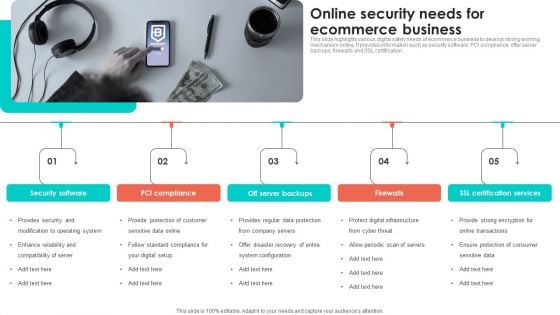
Online Security Needs For Ecommerce Business Professional PDF
This slide highlights various digital safety needs of ecommerce business to develop strong working mechanism online. It provides information such as security software, PCI compliance, offer server backups, firewalls and SSL certification. Presenting Online Security Needs For Ecommerce Business Professional PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including PCI Compliance, Off Server Backups, Security Software. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
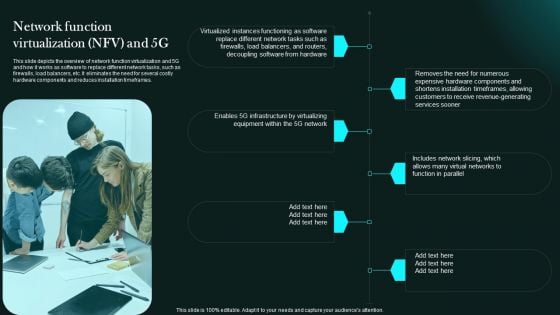
Network Function Virtualization Nfv And 5G 5G Network Functional Architecture Information PDF
This slide depicts the overview of network function virtualization and 5G and how it works as software to replace different network tasks, such as firewalls, load balancers, etc. It eliminates the need for several costly hardware components and reduces installation timeframes.Make sure to capture your audiences attention in your business displays with our gratis customizable Network Function Virtualization Nfv And 5G 5G Network Functional Architecture Information PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
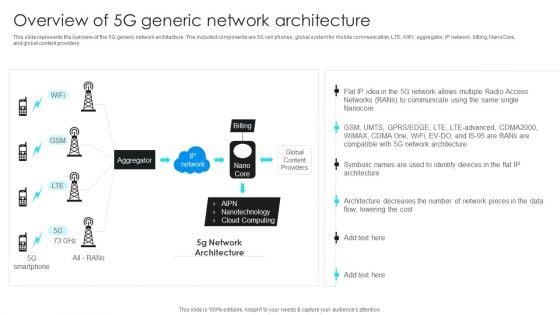
5G Network Operations Overview Of 5G Generic Network Architecture Mockup PDF
This slide depicts the overview of network function virtualization and 5G and how it works as software to replace different network tasks, such as firewalls, load balancers, etc. It eliminates the need for several costly hardware components and reduces installation timeframes. Make sure to capture your audiences attention in your business displays with our gratis customizable 5G Network Operations Overview Of 5G Generic Network Architecture Mockup PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Dos And Donts Of Prevention From Ransomware Attack Ppt Outline Designs Download PDF
The purpose of this slide is to showcase the Dos and donts of ransomware prevention attack. The slide covers information about updating the software, installing a firewall software, using reliable website and sources etc. There are so many reasons you need a Dos And Donts Of Prevention From Ransomware Attack Ppt Outline Designs Download PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
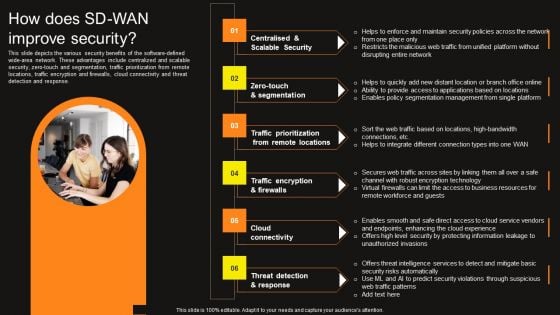
Virtual WAN Architecture How Does SD WAN Improve Security Professional PDF
This slide depicts the various security benefits of the software-defined wide-area network. These advantages include centralized and scalable security, zero-touch and segmentation, traffic prioritization from remote locations, traffic encryption and firewalls, cloud connectivity and threat detection and response. Find a pre-designed and impeccable Virtual WAN Architecture How Does SD WAN Improve Security Professional PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.


 Continue with Email
Continue with Email

 Home
Home


































