Zero Trust

Zero Trust Exchange Overview And Benefits Zero Trust Network Access
This slide provides an overview of zero trust exchange and its benefits. The purpose of this slide is to highlight the key advantages of zero trust exchange to businesses including enhancing user experience, reducing internet attacks and later threat movement, lowering costs and complexity, and so on. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Zero Trust Exchange Overview And Benefits Zero Trust Network Access and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide provides an overview of zero trust exchange and its benefits. The purpose of this slide is to highlight the key advantages of zero trust exchange to businesses including enhancing user experience, reducing internet attacks and later threat movement, lowering costs and complexity, and so on.

Zero Trust Model Key Points To Choose Zero Trust Solution
This slide highlights the main criteria while choosing the right zero trust solution for the organization. The purpose of this slide is to showcase the key points the businesses should keep in mind while selecting the ZTNA vendor. The main points include vendor support, zero trust technology type, and so on. Explore a selection of the finest Zero Trust Model Key Points To Choose Zero Trust Solution here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Zero Trust Model Key Points To Choose Zero Trust Solution to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide highlights the main criteria while choosing the right zero trust solution for the organization. The purpose of this slide is to showcase the key points the businesses should keep in mind while selecting the ZTNA vendor. The main points include vendor support, zero trust technology type, and so on.

Zero Trust Model Benefits Of Zero Trust Network Access ZTNA
This slide represents the benefits of zero trust network access, a component of SASE technology. The purpose of this slide is to demonstrate the multiple benefits of ZTNA to businesses and users. It also caters to the security benefits such as increased control and visibility, invisible infrastructure, and simple app segmentation. Get a simple yet stunning designed Zero Trust Model Benefits Of Zero Trust Network Access ZTNA. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Zero Trust Model Benefits Of Zero Trust Network Access ZTNA can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide represents the benefits of zero trust network access, a component of SASE technology. The purpose of this slide is to demonstrate the multiple benefits of ZTNA to businesses and users. It also caters to the security benefits such as increased control and visibility, invisible infrastructure, and simple app segmentation.

Zero Trust Model Zero Trust Exchange Overview And Benefits
This slide provides an overview of zero trust exchange and its benefits. The purpose of this slide is to highlight the key advantages of zero trust exchange to businesses including enhancing user experience, reducing internet attacks and later threat movement, lowering costs and complexity, and so on. This modern and well-arranged Zero Trust Model Zero Trust Exchange Overview And Benefits provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide provides an overview of zero trust exchange and its benefits. The purpose of this slide is to highlight the key advantages of zero trust exchange to businesses including enhancing user experience, reducing internet attacks and later threat movement, lowering costs and complexity, and so on.

Zero Trust Model Zero Trust Network Access Architectural Models
This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption. This Zero Trust Model Zero Trust Network Access Architectural Models is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Zero Trust Model Zero Trust Network Access Architectural Models features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption.

Zero Trust Model Zero Trust Network Access ZTNA Introduction
This slide represents the overview of zero trust network access, including its, benefits and principles. The purpose of this slide is to demonstrate the overview, principles and benefits of ZTNA. The primary benefits include seamless user experience, effortless scale, no need for legacy applications, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Zero Trust Model Zero Trust Network Access ZTNA Introduction to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Zero Trust Model Zero Trust Network Access ZTNA Introduction. This slide represents the overview of zero trust network access, including its, benefits and principles. The purpose of this slide is to demonstrate the overview, principles and benefits of ZTNA. The primary benefits include seamless user experience, effortless scale, no need for legacy applications, etc.

Zero Trust Model Endpoint Initiated Zero Trust Network Topology Model
This slide describes the overview of the endpoint-initiated zero trust network topology model of ZTNA deployment. The purpose of this slide is to showcase the conceptual model of the approach along with its benefits and drawbacks. The model components include the end-user device, SDP controller, gateway, and directory. Make sure to capture your audiences attention in your business displays with our gratis customizable Zero Trust Model Endpoint Initiated Zero Trust Network Topology Model. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide describes the overview of the endpoint-initiated zero trust network topology model of ZTNA deployment. The purpose of this slide is to showcase the conceptual model of the approach along with its benefits and drawbacks. The model components include the end-user device, SDP controller, gateway, and directory.
Zero Trust Model Zero Trust Network Access Performance Tracking
This slide represents the performance tracking dashboard for zero trust network access. The purpose of this slide is to showcase the level of request modes, connected users, daily usage of the network, security rating, device risk and threat flow. The Zero Trust Model Zero Trust Network Access Performance Tracking is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide represents the performance tracking dashboard for zero trust network access. The purpose of this slide is to showcase the level of request modes, connected users, daily usage of the network, security rating, device risk and threat flow.

Zero Trust Model Working Functions Of Zero Trust Network Access
This slide gives an overview of the working features of zero trust network access architecture. The purpose of this slide is to highlight the various functions that ZTNA architecture performs, including identification, protection, detection and response to threats. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Zero Trust Model Working Functions Of Zero Trust Network Access was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Zero Trust Model Working Functions Of Zero Trust Network Access. This slide gives an overview of the working features of zero trust network access architecture. The purpose of this slide is to highlight the various functions that ZTNA architecture performs, including identification, protection, detection and response to threats.

Zero Trust Model Zero Trust Network Access Architecture Workflow
This slide outlines the workflow of zero trust network access architecture. The purpose of this slide is to showcase the various steps of the ZTNA model workflow, including user authentication, grant access, monitoring of user sessions, and threat response. Explore a selection of the finest Zero Trust Model Zero Trust Network Access Architecture Workflow here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Zero Trust Model Zero Trust Network Access Architecture Workflow to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide outlines the workflow of zero trust network access architecture. The purpose of this slide is to showcase the various steps of the ZTNA model workflow, including user authentication, grant access, monitoring of user sessions, and threat response.

Zero Trust Model Technologies Used In Zero Trust Network Access
This slide represents the techniques used in the zero-trust network access model. The purpose of this slide is to showcase the multiple technologies used in the ZTNA model, including their functions and the network protection they offer. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Zero Trust Model Technologies Used In Zero Trust Network Access. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Zero Trust Model Technologies Used In Zero Trust Network Access today and make your presentation stand out from the rest This slide represents the techniques used in the zero-trust network access model. The purpose of this slide is to showcase the multiple technologies used in the ZTNA model, including their functions and the network protection they offer.
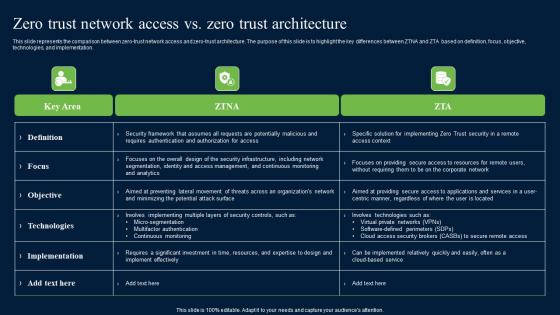
Zero Trust Network Access Vs Zero Trust Architecture Diagrams Pdf
This slide represents the comparison between zero-trust network access and zero-trust architecture. The purpose of this slide is to highlight the key differences between ZTNA and ZTA based on definition, focus, objective, technologies, and implementation. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Zero Trust Network Access Vs Zero Trust Architecture Diagrams Pdf can be your best option for delivering a presentation. Represent everything in detail using Zero Trust Network Access Vs Zero Trust Architecture Diagrams Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide represents the comparison between zero-trust network access and zero-trust architecture. The purpose of this slide is to highlight the key differences between ZTNA and ZTA based on definition, focus, objective, technologies, and implementation.

Zero Trust Model Timeline To Implement Zero Trust Network Access
This slide showcases the timeline for implementing the ZTNA security model. This slide highlights the various steps organizations will take while deploying the ZTNA system, forming a dedicated team, choosing zero-trust implementation on-ramp, assessing the environment and so on. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Zero Trust Model Timeline To Implement Zero Trust Network Access can be your best option for delivering a presentation. Represent everything in detail using Zero Trust Model Timeline To Implement Zero Trust Network Access and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide showcases the timeline for implementing the ZTNA security model. This slide highlights the various steps organizations will take while deploying the ZTNA system, forming a dedicated team, choosing zero-trust implementation on-ramp, assessing the environment and so on.

Zero Trust Model Zero Trust Network Access System Use Cases
This slide outlines multiple use cases of zero-trust network access systems. The purpose of this slide is to showcase the main use cases of the ZTNA model, which are replacing VPN and MPLS connections, internal firewall replacement, securing remote access to private apps, limiting user access, and so on. Are you searching for a Zero Trust Model Zero Trust Network Access System Use Cases that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Zero Trust Model Zero Trust Network Access System Use Cases from Slidegeeks today. This slide outlines multiple use cases of zero-trust network access systems. The purpose of this slide is to showcase the main use cases of the ZTNA model, which are replacing VPN and MPLS connections, internal firewall replacement, securing remote access to private apps, limiting user access, and so on.

Zero Trust Network Access Vs Zero Trust Architecture Inspiration PDF
This slide represents the comparison between zero-trust network access and zero-trust architecture. The purpose of this slide is to highlight the key differences between ZTNA and ZTA based on definition, focus, objective, technologies, and implementation. Want to ace your presentation in front of a live audience Our Zero Trust Network Access Vs Zero Trust Architecture Inspiration PDF can help you do that by engaging all the users towards you.. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.

Zero Trust Model Top Zero Trust Network Access Software Solutions
This slide illustrates the top software solution for zero-trust network access. The purpose of this slide is to showcase the prominent tools for ZTNA implementation, including Okta identity-driven security, ping identity, Google BeyondCorp, Twingate, Permiter 81 and so on. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Zero Trust Model Top Zero Trust Network Access Software Solutions and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide illustrates the top software solution for zero-trust network access. The purpose of this slide is to showcase the prominent tools for ZTNA implementation, including Okta identity-driven security, ping identity, Google BeyondCorp, Twingate, Permiter 81 and so on.

Zero Trust Network Access Overview Of Zero Trust Solution Categories
This slide represents the overview of zero-trust solution categories, including MFA, SSO, identity and access management, zero-trust network access and secure access service edge. The purpose of this slide is to give an overview of zero-trust technologies and their benefits. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Zero Trust Network Access Overview Of Zero Trust Solution Categories for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide represents the overview of zero-trust solution categories, including MFA, SSO, identity and access management, zero-trust network access and secure access service edge. The purpose of this slide is to give an overview of zero-trust technologies and their benefits.

Zero Trust Model Working Of Zero Trust Network Access Model
This slide outlines the working of zero trust network access. The purpose of this slide is to demonstrate the workflow of ZTNA, including the principles shared by all ZTNA architectures. The principles include no use of MPLS, hiding the IP addresses, securing devices, IDP and SSO platform, and so on. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Zero Trust Model Working Of Zero Trust Network Access Model to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide outlines the working of zero trust network access. The purpose of this slide is to demonstrate the workflow of ZTNA, including the principles shared by all ZTNA architectures. The principles include no use of MPLS, hiding the IP addresses, securing devices, IDP and SSO platform, and so on.

Zero Trust Model Zero Trust Network Access Architecture Overview
This slide gives an overview of zero trust network access architecture. The purpose of this slide is to showcase the ZTNA architecture and its benefits, covering granting safe and fast access, protecting reliable remote access, protecting sensitive data and apps, stopping insider threats, and so on. Welcome to our selection of the Zero Trust Model Zero Trust Network Access Architecture Overview. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide gives an overview of zero trust network access architecture. The purpose of this slide is to showcase the ZTNA architecture and its benefits, covering granting safe and fast access, protecting reliable remote access, protecting sensitive data and apps, stopping insider threats, and so on.

Zero Trust Model Zero Trust Network Access User Flow Overview
This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office. Retrieve professionally designed Zero Trust Model Zero Trust Network Access User Flow Overview to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office.

Zero Trust Model Logical Components Of Zero Trust Architecture
This slide describes the core logical components of the zero-trust network architecture model. The purpose of this slide is to showcase the various architectural parts and functions of logical elements, such as the policy engine, policy administrator, and policy environment point. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Zero Trust Model Logical Components Of Zero Trust Architecture from Slidegeeks and deliver a wonderful presentation. This slide describes the core logical components of the zero-trust network architecture model. The purpose of this slide is to showcase the various architectural parts and functions of logical elements, such as the policy engine, policy administrator, and policy environment point.

Zero Trust Model Service Initiated Zero Trust Network Topology Model
This slide provides an overview of service initiated zero-trust network topology model. The purpose of this slide is to showcase its architecture, benefits, and disadvantages. The architectural components include a user device, controller, broker proxy, and connector. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Zero Trust Model Service Initiated Zero Trust Network Topology Model for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide provides an overview of service initiated zero-trust network topology model. The purpose of this slide is to showcase its architecture, benefits, and disadvantages. The architectural components include a user device, controller, broker proxy, and connector.

Zero Trust Network Access Logical Components Of Zero Trust Architecture
This slide describes the core logical components of the zero-trust network architecture model. The purpose of this slide is to showcase the various architectural parts and functions of logical elements, such as the policy engine, policy administrator, and policy environment point. Take your projects to the next level with our ultimate collection of Zero Trust Network Access Logical Components Of Zero Trust Architecture. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest This slide describes the core logical components of the zero-trust network architecture model. The purpose of this slide is to showcase the various architectural parts and functions of logical elements, such as the policy engine, policy administrator, and policy environment point.

Zero Trust Model Before Vs After Zero Trust Network Access
This slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Zero Trust Model Before Vs After Zero Trust Network Access a try. Our experts have put a lot of knowledge and effort into creating this impeccable Zero Trust Model Before Vs After Zero Trust Network Access. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems.

Zero Trust Model External Components Of Zero Trust Network Architecture
This slide gives an overview of external elements of zero trust network architecture. The purpose of this slide is to showcase the various external components and their working, covering CDM systems, industry compliance, threat intelligence, activity logs, data access policy, and so on. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Zero Trust Model External Components Of Zero Trust Network Architecture to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide gives an overview of external elements of zero trust network architecture. The purpose of this slide is to showcase the various external components and their working, covering CDM systems, industry compliance, threat intelligence, activity logs, data access policy, and so on.

Zero Trust Model Zero Trust Network Access Implementation Challenges
This slide outlines the main challenges of ZTNA implementation. The purpose of this slide is to highlight the primary challenges that organizations face while deploying ZTNA. The challenges include continual management and maintenance, low productivity, security risks, and so on. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Zero Trust Model Zero Trust Network Access Implementation Challenges from Slidegeeks and deliver a wonderful presentation. This slide outlines the main challenges of ZTNA implementation. The purpose of this slide is to highlight the primary challenges that organizations face while deploying ZTNA. The challenges include continual management and maintenance, low productivity, security risks, and so on.

Zero Trust Model Checklist To Build Zero Trust Network Access
This slide outlines the checklist to develop a zero-trust network access architecture. The purpose of this slide is to define the various measures organizations should take while building a ZTNA architecture. The measures include knowing the architecture, creating a strong device identity, and so on. Slidegeeks is here to make your presentations a breeze with Zero Trust Model Checklist To Build Zero Trust Network Access With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide outlines the checklist to develop a zero-trust network access architecture. The purpose of this slide is to define the various measures organizations should take while building a ZTNA architecture. The measures include knowing the architecture, creating a strong device identity, and so on.

Zero Trust Model Overview Of Zero Trust Solution Categories
This slide represents the overview of zero-trust solution categories, including MFA, SSO, identity and access management, zero-trust network access and secure access service edge. The purpose of this slide is to give an overview of zero-trust technologies and their benefits. This Zero Trust Model Overview Of Zero Trust Solution Categories from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide represents the overview of zero-trust solution categories, including MFA, SSO, identity and access management, zero-trust network access and secure access service edge. The purpose of this slide is to give an overview of zero-trust technologies and their benefits.

Zero Trust Model Zero Trust Network Access Vs Zero Trust Architecture
This slide represents the comparison between zero-trust network access and zero-trust architecture. The purpose of this slide is to highlight the key differences between ZTNA and ZTA based on definition, focus, objective, technologies, and implementation. Presenting this PowerPoint presentation, titled Zero Trust Model Zero Trust Network Access Vs Zero Trust Architecture, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Zero Trust Model Zero Trust Network Access Vs Zero Trust Architecture. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Zero Trust Model Zero Trust Network Access Vs Zero Trust Architecture that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide represents the comparison between zero-trust network access and zero-trust architecture. The purpose of this slide is to highlight the key differences between ZTNA and ZTA based on definition, focus, objective, technologies, and implementation.

Zero Trust Model Main Pillars Of Zero Network Trust Access
This slide outlines the critical pillars of the zero network trust access model. The purpose of this slide is to showcase the primary pillars of ZTNA, including users, devices, networks, infrastructure, applications, data, visibility and analytics, and orchestration and automation. The Zero Trust Model Main Pillars Of Zero Network Trust Access is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide outlines the critical pillars of the zero network trust access model. The purpose of this slide is to showcase the primary pillars of ZTNA, including users, devices, networks, infrastructure, applications, data, visibility and analytics, and orchestration and automation.

A48 Zero Trust Network Access Architectural Models
This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption. Boost your pitch with our creative A48 Zero Trust Network Access Architectural Models. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption.
Zero Trust Network Access Performance Tracking Dashboard
This slide represents the performance tracking dashboard for zero trust network access. The purpose of this slide is to showcase the level of request modes, connected users, daily usage of the network, security rating, device risk and threat flow. Want to ace your presentation in front of a live audience Our Zero Trust Network Access Performance Tracking Dashboard can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide represents the performance tracking dashboard for zero trust network access. The purpose of this slide is to showcase the level of request modes, connected users, daily usage of the network, security rating, device risk and threat flow.

A50 Zero Trust Network Access Architecture Workflow
This slide outlines the workflow of zero trust network access architecture. The purpose of this slide is to showcase the various steps of the ZTNA model workflow, including user authentication, grant access, monitoring of user sessions, and threat response. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate A50 Zero Trust Network Access Architecture Workflow for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide outlines the workflow of zero trust network access architecture. The purpose of this slide is to showcase the various steps of the ZTNA model workflow, including user authentication, grant access, monitoring of user sessions, and threat response.

A49 Zero Trust Network Access Architecture Overview
This slide gives an overview of zero trust network access architecture. The purpose of this slide is to showcase the ZTNA architecture and its benefits, covering granting safe and fast access, protecting reliable remote access, protecting sensitive data and apps, stopping insider threats, and so on. Create an editable A49 Zero Trust Network Access Architecture Overview that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. A49 Zero Trust Network Access Architecture Overview is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide gives an overview of zero trust network access architecture. The purpose of this slide is to showcase the ZTNA architecture and its benefits, covering granting safe and fast access, protecting reliable remote access, protecting sensitive data and apps, stopping insider threats, and so on.

Zero Trust Model Microsegmentation Overview And Working
This slide outlines the overview and working of the micro-segmentation concept of cybersecurity. The purpose of this slide is to showcase how micro-segmentation divides the network components into smaller segments, all the way down to workloads. Are you searching for a Zero Trust Model Microsegmentation Overview And Working that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Zero Trust Model Microsegmentation Overview And Working from Slidegeeks today. This slide outlines the overview and working of the micro-segmentation concept of cybersecurity. The purpose of this slide is to showcase how micro-segmentation divides the network components into smaller segments, all the way down to workloads.

A51 Zero Trust Network Access Implementation Challenges
This slide outlines the main challenges of ZTNA implementation. The purpose of this slide is to highlight the primary challenges that organizations face while deploying ZTNA. The challenges include continual management and maintenance, low productivity, security risks, and so on Want to ace your presentation in front of a live audience Our A51 Zero Trust Network Access Implementation Challenges can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide outlines the main challenges of ZTNA implementation. The purpose of this slide is to highlight the primary challenges that organizations face while deploying ZTNA. The challenges include continual management and maintenance, low productivity, security risks, and so on

Zero Trust Model Step 4 And 5 Available Technology Review And Zero Trust
This slide represents the fourth and fifth steps of ZTNA deployment, which is reviewing available technology and launching primary zero trust projects. The purpose of this slide is to showcase the next steps in zero trust model implementation. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Zero Trust Model Step 4 And 5 Available Technology Review And Zero Trust will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide represents the fourth and fifth steps of ZTNA deployment, which is reviewing available technology and launching primary zero trust projects. The purpose of this slide is to showcase the next steps in zero trust model implementation.

Zero Trust Model Top Tenets Of Zero Trust Network Access Model
Find highly impressive Zero Trust Model Top Tenets Of Zero Trust Network Access Model on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Zero Trust Model Top Tenets Of Zero Trust Network Access Mode for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now Our Zero Trust Model Top Tenets Of Zero Trust Network Access Model are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Zero Trust Model Comparison Between Zero Trust Model SDP And VPN
This slide represents the comparison between the zero trust security model, software-defined perimeter, and virtual private network. The purpose of this slide is to showcase the difference as well as the relationship between three security technologies such as zero trust, SDP and VPN. Find highly impressive Zero Trust Model Comparison Between Zero Trust Model SDP And VPN on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Zero Trust Model Comparison Between Zero Trust Model SDP And VPN for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide represents the comparison between the zero trust security model, software-defined perimeter, and virtual private network. The purpose of this slide is to showcase the difference as well as the relationship between three security technologies such as zero trust, SDP and VPN.

Zero Trust Network Access Step 4 And 5 Available Technology Review And Zero Trust Initiatives Launch
This slide represents the fourth and fifth steps of ZTNA deployment, which is reviewing available technology and launching primary zero trust projects. The purpose of this slide is to showcase the next steps in zero trust model implementation. If you are looking for a format to display your unique thoughts, then the professionally designed Zero Trust Network Access Step 4 And 5 Available Technology Review And Zero Trust Initiatives Launch is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Zero Trust Network Access Step 4 And 5 Available Technology Review And Zero Trust Initiatives Launch and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide represents the fourth and fifth steps of ZTNA deployment, which is reviewing available technology and launching primary zero trust projects. The purpose of this slide is to showcase the next steps in zero trust model implementation.

Zero Trust Network Access Working Of Zero Trust Network Access Model
This slide outlines the working of zero trust network access. The purpose of this slide is to demonstrate the workflow of ZTNA, including the principles shared by all ZTNA architectures. The principles include no use of MPLS, hiding the IP addresses, securing devices, IDP and SSO platform, and so on. Presenting this PowerPoint presentation, titled Zero Trust Network Access Working Of Zero Trust Network Access Model, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Zero Trust Network Access Working Of Zero Trust Network Access Model. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Zero Trust Network Access Working Of Zero Trust Network Access Model that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide outlines the working of zero trust network access. The purpose of this slide is to demonstrate the workflow of ZTNA, including the principles shared by all ZTNA architectures. The principles include no use of MPLS, hiding the IP addresses, securing devices, IDP and SSO platform, and so on.
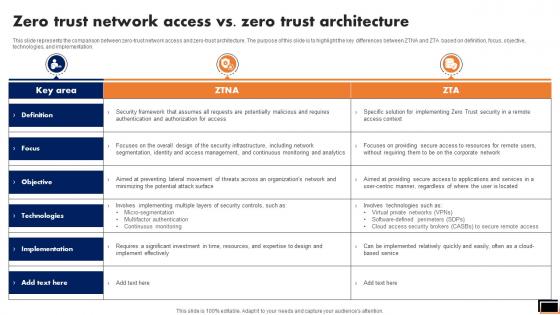
Zero Trust Network Access Vs Zero Trust Architecture Software Defined Perimeter SDP
This slide represents the comparison between zero-trust network access and zero-trust architecture. The purpose of this slide is to highlight the key differences between ZTNA and ZTA based on definition, focus, objective, technologies, and implementation. Presenting this PowerPoint presentation, titled Zero Trust Network Access Vs Zero Trust Architecture Software Defined Perimeter SDP, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Zero Trust Network Access Vs. Zero Trust Architecture Software Defined Perimeter SDP. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Zero Trust Network Access Vs. Zero Trust Architecture Software Defined Perimeter SDP that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide represents the comparison between zero-trust network access and zero-trust architecture. The purpose of this slide is to highlight the key differences between ZTNA and ZTA based on definition, focus, objective, technologies, and implementation.

Top Tenets Of Zero Trust Network Access Model Zero Trust Network Security Graphics Pdf
This graph chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Top Tenets Of Zero Trust Network Access Model Zero Trust Network Security Graphics Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Top Tenets Of Zero Trust Network Access Model Zero Trust Network Security Graphics Pdf today and make your presentation stand out from the rest This graph chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data.

Endpoint Initiated Zero Trust Network Topology Zero Trust Network Security Template Pdf
This slide describes the overview of the endpoint-initiated zero trust network topology model of ZTNA deployment. The purpose of this slide is to showcase the conceptual model of the approach along with its benefits and drawbacks. The model components include the end-user device, SDP controller, gateway, and directory. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Endpoint Initiated Zero Trust Network Topology Zero Trust Network Security Template Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide describes the overview of the endpoint-initiated zero trust network topology model of ZTNA deployment. The purpose of this slide is to showcase the conceptual model of the approach along with its benefits and drawbacks. The model components include the end-user device, SDP controller, gateway, and directory.
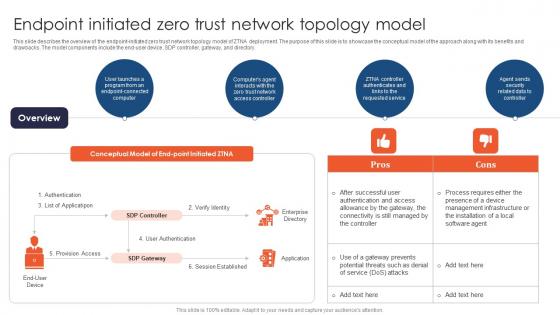
Endpoint Initiated Zero Trust Network Topology Model Zero Trust Network Access
This slide describes the overview of the endpoint-initiated zero trust network topology model of ZTNA deployment. The purpose of this slide is to showcase the conceptual model of the approach along with its benefits and drawbacks. The model components include the end-user device, SDP controller, gateway, and directory. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Endpoint Initiated Zero Trust Network Topology Model Zero Trust Network Access will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide describes the overview of the endpoint-initiated zero trust network topology model of ZTNA deployment. The purpose of this slide is to showcase the conceptual model of the approach along with its benefits and drawbacks. The model components include the end-user device, SDP controller, gateway, and directory.

Zero Trust Network Access Top Tenets Of Zero Trust Network Access Model
Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Zero Trust Network Access Top Tenets Of Zero Trust Network Access Model to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. Our Zero Trust Network Access Top Tenets Of Zero Trust Network Access Model are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Zero Trust Network Access Working Functions Of Zero Trust Network Access Architecture
This slide gives an overview of the working features of zero trust network access architecture. The purpose of this slide is to highlight the various functions that ZTNA architecture performs, including identification, protection, detection and response to threats. Slidegeeks has constructed Zero Trust Network Access Working Functions Of Zero Trust Network Access Architecture after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide gives an overview of the working features of zero trust network access architecture. The purpose of this slide is to highlight the various functions that ZTNA architecture performs, including identification, protection, detection and response to threats.

Key Points To Choose Zero Trust Solution Zero Trust Network Security Formats Pdf
This slide highlights the main criteria while choosing the right zero trust solution for the organization. The purpose of this slide is to showcase the key points the businesses should keep in mind while selecting the ZTNA vendor. The main points include vendor support, zero trust technology type, and so on. This modern and well-arranged Key Points To Choose Zero Trust Solution Zero Trust Network Security Formats Pdf provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide highlights the main criteria while choosing the right zero trust solution for the organization. The purpose of this slide is to showcase the key points the businesses should keep in mind while selecting the ZTNA vendor. The main points include vendor support, zero trust technology type, and so on.
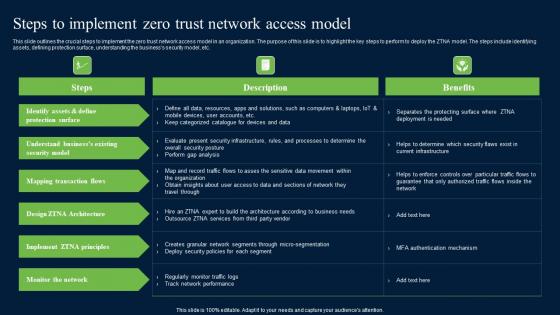
Steps To Implement Zero Trust Network Access Model Zero Trust Network Security Inspiration Pdf
This slide outlines the crucial steps to implement the zero trust network access model in an organization. The purpose of this slide is to highlight the key steps to perform to deploy the ZTNA model. The steps include identifying assets, defining protection surface, understanding the businesss security model, etc. Get a simple yet stunning designed Steps To Implement Zero Trust Network Access Model Zero Trust Network Security Inspiration Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Steps To Implement Zero Trust Network Access Model Zero Trust Network Security Inspiration Pdf can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide outlines the crucial steps to implement the zero trust network access model in an organization. The purpose of this slide is to highlight the key steps to perform to deploy the ZTNA model. The steps include identifying assets, defining protection surface, understanding the businesss security model, etc.

Zero Trust Model Critical Principles Of Zero Trust Network Access Model
This slide illustrates the key principles of zero trust network access model, including their impact. The purpose of this slide is to highlight the primary principles of the ZTNA model, including least privilege access, micro-segmentation, MFA, device validation, and monitoring everything. If you are looking for a format to display your unique thoughts, then the professionally designed Zero Trust Model Critical Principles Of Zero Trust Network Access Model is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Zero Trust Model Critical Principles Of Zero Trust Network Access Model and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide illustrates the key principles of zero trust network access model, including their impact. The purpose of this slide is to highlight the primary principles of the ZTNA model, including least privilege access, micro-segmentation, MFA, device validation, and monitoring everything.

Zero Trust Network Access Comparison Between Zero Trust Model SDP And VPN
This slide represents the comparison between the zero trust security model, software-defined perimeter, and virtual private network. The purpose of this slide is to showcase the difference as well as the relationship between three security technologies such as zero trust, SDP and VPN. Welcome to our selection of the Zero Trust Network Access Comparison Between Zero Trust Model SDP And VPN. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide represents the comparison between the zero trust security model, software-defined perimeter, and virtual private network. The purpose of this slide is to showcase the difference as well as the relationship between three security technologies such as zero trust, SDP and VPN.

Zero Trust Network Access Critical Principles Of Zero Trust Network Access Model
This slide illustrates the key principles of zero trust network access model, including their impact. The purpose of this slide is to highlight the primary principles of the ZTNA model, including least privilege access, micro-segmentation, MFA, device validation, and monitoring everything. Explore a selection of the finest Zero Trust Network Access Critical Principles Of Zero Trust Network Access Model here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Zero Trust Network Access Critical Principles Of Zero Trust Network Access Model to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide illustrates the key principles of zero trust network access model, including their impact. The purpose of this slide is to highlight the primary principles of the ZTNA model, including least privilege access, micro-segmentation, MFA, device validation, and monitoring everything.

Zero Trust Network Access Key Points To Choose Zero Trust Solution
This slide highlights the main criteria while choosing the right zero trust solution for the organization. The purpose of this slide is to showcase the key points the businesses should keep in mind while selecting the ZTNA vendor. The main points include vendor support, zero trust technology type, and so on. This Zero Trust Network Access Key Points To Choose Zero Trust Solution from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide highlights the main criteria while choosing the right zero trust solution for the organization. The purpose of this slide is to showcase the key points the businesses should keep in mind while selecting the ZTNA vendor. The main points include vendor support, zero trust technology type, and so on.

Zero Trust Network Access Steps To Implement Zero Trust Network Access Model
This slide outlines the crucial steps to implement the zero trust network access model in an organization. The purpose of this slide is to highlight the key steps to perform to deploy the ZTNA model. The steps include identifying assets, defining protection surface, understanding the businesss security model, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Zero Trust Network Access Steps To Implement Zero Trust Network Access Model template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Zero Trust Network Access Steps To Implement Zero Trust Network Access Model that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide outlines the crucial steps to implement the zero trust network access model in an organization. The purpose of this slide is to highlight the key steps to perform to deploy the ZTNA model. The steps include identifying assets, defining protection surface, understanding the businesss security model, etc.
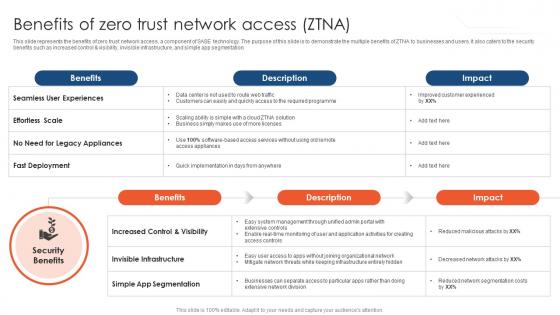
Zero Trust Network Access Benefits Of Zero Trust Network Access ZTNA
This slide represents the benefits of zero trust network access, a component of SASE technology. The purpose of this slide is to demonstrate the multiple benefits of ZTNA to businesses and users. It also caters to the security benefits such as increased control and visibility, invisible infrastructure, and simple app segmentation. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Zero Trust Network Access Benefits Of Zero Trust Network Access ZTNA template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Zero Trust Network Access Benefits Of Zero Trust Network Access ZTNA that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide represents the benefits of zero trust network access, a component of SASE technology. The purpose of this slide is to demonstrate the multiple benefits of ZTNA to businesses and users. It also caters to the security benefits such as increased control and visibility, invisible infrastructure, and simple app segmentation.
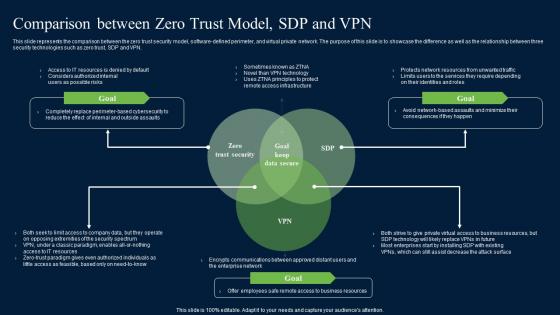
Comparison Between Zero Trust Model SDP Zero Trust Network Security Guidelines Pdf
This slide represents the comparison between the zero trust security model, software-defined perimeter, and virtual private network. The purpose of this slide is to showcase the difference as well as the relationship between three security technologies such as zero trust, SDP and VPN. Present like a pro with Comparison Between Zero Trust Model SDP Zero Trust Network Security Guidelines Pdf Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide represents the comparison between the zero trust security model, software-defined perimeter, and virtual private network. The purpose of this slide is to showcase the difference as well as the relationship between three security technologies such as zero trust, SDP and VPN.
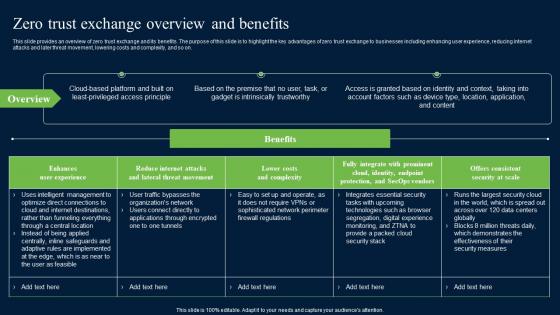
Zero Trust Exchange Overview And Benefits Zero Trust Network Security Introduction Pdf
This slide provides an overview of zero trust exchange and its benefits. The purpose of this slide is to highlight the key advantages of zero trust exchange to businesses including enhancing user experience, reducing internet attacks and later threat movement, lowering costs and complexity, and so on. Want to ace your presentation in front of a live audience Our Zero Trust Exchange Overview And Benefits Zero Trust Network Security Introduction Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide provides an overview of zero trust exchange and its benefits. The purpose of this slide is to highlight the key advantages of zero trust exchange to businesses including enhancing user experience, reducing internet attacks and later threat movement, lowering costs and complexity, and so on.
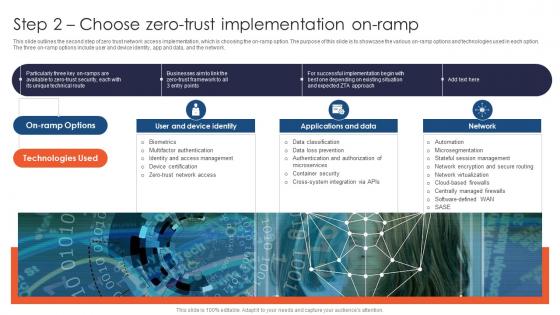
Zero Trust Network Access Step 2 Choose Zero Trust Implementation On Ramp
This slide outlines the second step of zero trust network access implementation, which is choosing the on-ramp option. The purpose of this slide is to showcase the various on-ramp options and technologies used in each option. The three on-ramp options include user and device identity, app and data, and the network. Find highly impressive Zero Trust Network Access Step 2 Choose Zero Trust Implementation On Ramp on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Zero Trust Network Access Step 2 Choose Zero Trust Implementation On Ramp for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide outlines the second step of zero trust network access implementation, which is choosing the on-ramp option. The purpose of this slide is to showcase the various on-ramp options and technologies used in each option. The three on-ramp options include user and device identity, app and data, and the network.
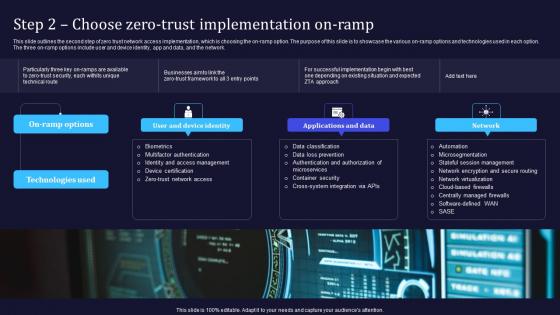
Zero Trust Model Step 2 Choose Zero Trust Implementation On Ramp
This slide outlines the second step of zero trust network access implementation, which is choosing the on-ramp option. The purpose of this slide is to showcase the various on-ramp options and technologies used in each option. The three on-ramp options include user and device identity, app and data, and the network. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Zero Trust Model Step 2 Choose Zero Trust Implementation On Ramp a try. Our experts have put a lot of knowledge and effort into creating this impeccable Zero Trust Model Step 2 Choose Zero Trust Implementation On Ramp. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide outlines the second step of zero trust network access implementation, which is choosing the on-ramp option. The purpose of this slide is to showcase the various on-ramp options and technologies used in each option. The three on-ramp options include user and device identity, app and data, and the network.

Step 1 Form A Dedicated Zero Trust Team Zero Trust Network Security Portrait Pdf
This slide represents the first step of ZTNA implementation, which is forming a dedicated zero-trust team. The purpose of this slide is to highlight the objective behind building a dedicated team and representing the domains and names of team members. Create an editable Step 1 Form A Dedicated Zero Trust Team Zero Trust Network Security Portrait Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Step 1 Form A Dedicated Zero Trust Team Zero Trust Network Security Portrait Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide represents the first step of ZTNA implementation, which is forming a dedicated zero-trust team. The purpose of this slide is to highlight the objective behind building a dedicated team and representing the domains and names of team members.


 Continue with Email
Continue with Email

 Home
Home


































