lock

Securing Market Leadership Through Competitive Excellence Pros And Cons Of Red Ocean Strategy Microsoft PDF
The following slide exhibits the advantages and disadvantages of red ocean strategy. The advantages mentioned in the slide are no need to create new marketplace, high demand of products and services etc. The disadvantages are difficult to survive in the existing market, no extraordinary profits etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Securing Market Leadership Through Competitive Excellence Pros And Cons Of Red Ocean Strategy Microsoft PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Securing Market Leadership Through Competitive Excellence Pros And Cons Of Red Ocean Strategy Microsoft PDF today and make your presentation stand out from the rest.
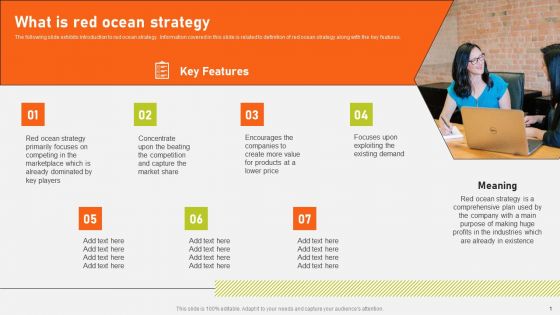
Securing Market Leadership Through Competitive Excellence What Is Red Ocean Strategy Formats PDF
The following slide exhibits introduction to red ocean strategy. Information covered in this slide is related to definition of red ocean strategy along with the key features. Find highly impressive Securing Market Leadership Through Competitive Excellence What Is Red Ocean Strategy Formats PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Securing Market Leadership Through Competitive Excellence What Is Red Ocean Strategy Formats PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.
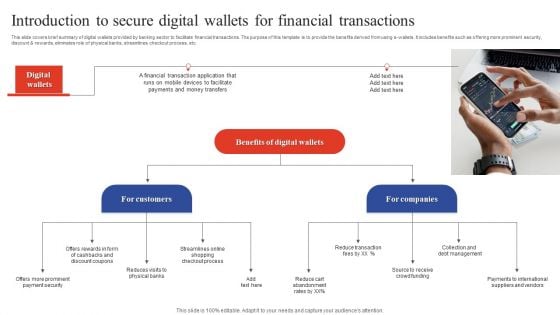
Deployment Of Omnichannel Banking Solutions Introduction To Secure Digital Wallets For Financial Transactions Template PDF
This slide covers brief summary of digital wallets provided by banking sector to facilitate financial transactions. The purpose of this template is to provide the benefits derived from using e-wallets. It includes benefits such as offering more prominent security, discount and rewards, eliminates role of physical banks, streamlines checkout process, etc. Retrieve professionally designed Deployment Of Omnichannel Banking Solutions Introduction To Secure Digital Wallets For Financial Transactions Template PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
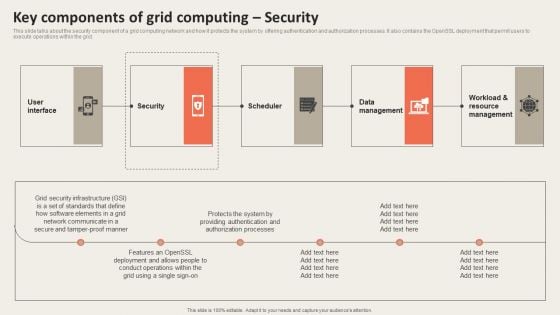
Grid Computing Applications Key Components Of Grid Computing Security Guidelines PDF
This slide talks about the security component of a grid computing network and how it protects the system by offering authentication and authorization processes. It also contains the OpenSSL deployment that permit users to execute operations within the grid. This modern and well arranged Grid Computing Applications Key Components Of Grid Computing Security Guidelines PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
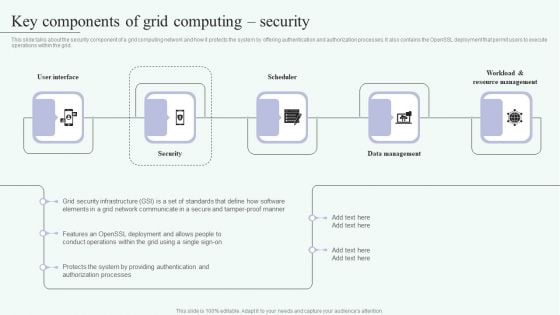
Grid Computing For High Performance Solutions Key Components Of Grid Computing Security Clipart PDF
This slide talks about the security component of a grid computing network and how it protects the system by offering authentication and authorization processes. It also contains the OpenSSL deployment that permit users to execute operations within the grid. Welcome to our selection of the Grid Computing For High Performance Solutions Key Components Of Grid Computing Security Clipart PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.
Impact Of Implementing Cyber Security Incident Management On Organization Icons PDF
This slide represents the comparison between current and past scenario to analyze the impact of cyber security incident management on business operations. It includes analysis of KPIs such engagement, satisfaction, turnover rate etc. Present like a pro with Impact Of Implementing Cyber Security Incident Management On Organization Icons PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
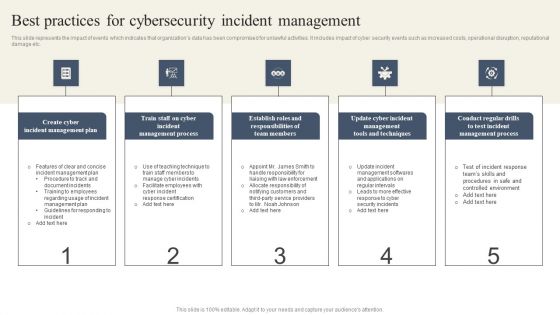
CYBER Security Breache Response Strategy Best Practices For Cybersecurity Incident Management Ideas PDF
This slide represents the impact of events which indicates that organizations data has been compromised for unlawful activities. It includes impact of cyber security events such as increased costs, operational disruption, reputational damage etc. Boost your pitch with our creative CYBER Security Breache Response Strategy Best Practices For Cybersecurity Incident Management Ideas PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
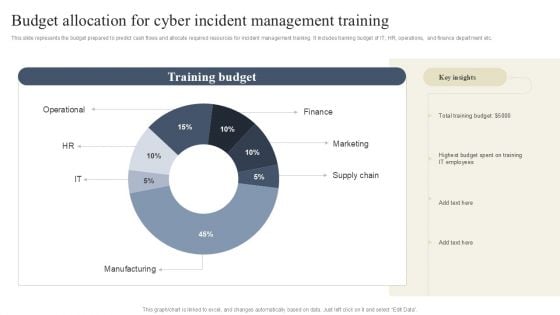
CYBER Security Breache Response Strategy Budget Allocation For Cyber Incident Management Training Topics PDF
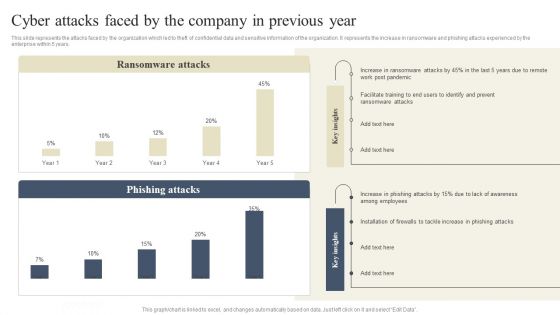
CYBER Security Breache Response Strategy Cyber Attacks Faced By The Company In Previous Year Information PDF
This slide represents the attacks faced by the organization which led to theft of confidential data and sensitive information of the organization. It represents the increase in ransomware and phishing attacks experienced by the enterprise within 5 years. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give CYBER Security Breache Response Strategy Cyber Attacks Faced By The Company In Previous Year Information PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable CYBER Security Breache Response Strategy Cyber Attacks Faced By The Company In Previous Year Information PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
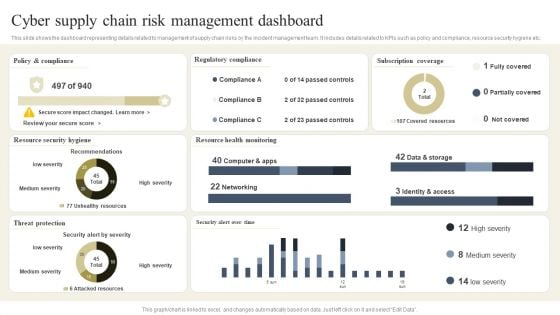
CYBER Security Breache Response Strategy Cyber Supply Chain Risk Management Dashboard Inspiration PDF
This slide shows the dashboard representing details related to management of supply chain risks by the incident management team. It includes details related to KPIs such as policy and compliance, resource security hygiene etc. The CYBER Security Breache Response Strategy Cyber Supply Chain Risk Management Dashboard Inspiration PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
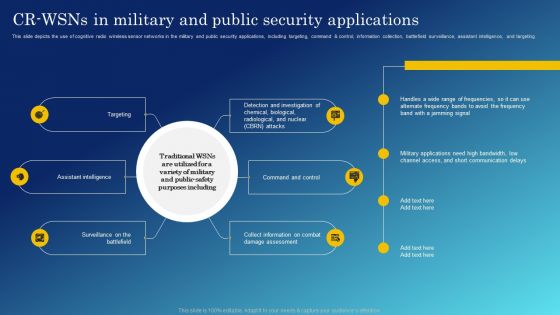
Cognitive Sensing Innovation CR Wsns In Military And Public Security Applications Inspiration PDF
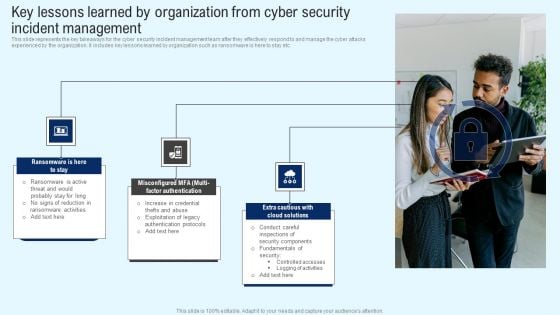
Implementing Cyber Security Incident Key Lessons Learned By Organization From Cyber Inspiration PDF
This slide represents the key takeaways for the cyber security incident management team after they effectively respond to and manage the cyber attacks experienced by the organization. It includes key lessons learned by organization such as ransomware is here to stay etc. Present like a pro with Implementing Cyber Security Incident Key Lessons Learned By Organization From Cyber Inspiration PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
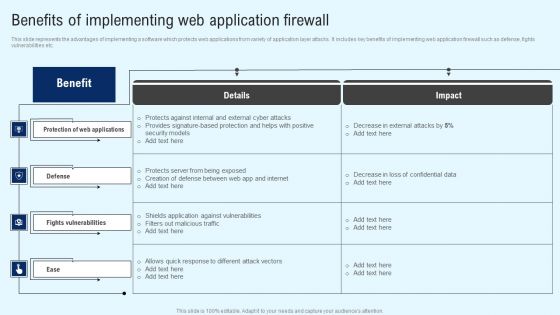
Implementing Cyber Security Incident Benefits Of Implementing Web Application Designs PDF
This slide represents the advantages of implementing a software which protects web applications from variety of application layer attacks. It includes key benefits of implementing web application firewall such as defense, fights vulnerabilities etc. If you are looking for a format to display your unique thoughts, then the professionally designed Implementing Cyber Security Incident Benefits Of Implementing Web Application Designs PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Implementing Cyber Security Incident Benefits Of Implementing Web Application Designs PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Implementing Cyber Security Incident Best Practices For Cybersecurity Incident Guidelines PDF
This slide represents the best practices to be adopted by the organizations which aim to minimize impact of cyber security incidents on business operations and prevent them from happening again. It includes best practices such as create cyber incident management plan etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Implementing Cyber Security Incident Best Practices For Cybersecurity Incident Guidelines PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
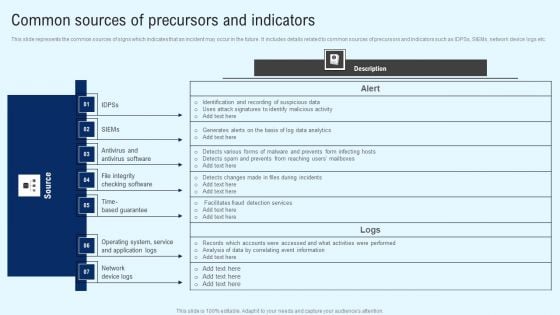
Implementing Cyber Security Incident Common Sources Of Precursors And Indicators Inspiration PDF
This slide represents the common sources of signs which indicates that an incident may occur in the future. It includes details related to common sources of precursors and indicators such as IDPSs, SIEMs, network device logs etc. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Implementing Cyber Security Incident Common Sources Of Precursors And Indicators Inspiration PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Implementing Cyber Security Incident Common Sources Of Precursors And Indicators Inspiration PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.
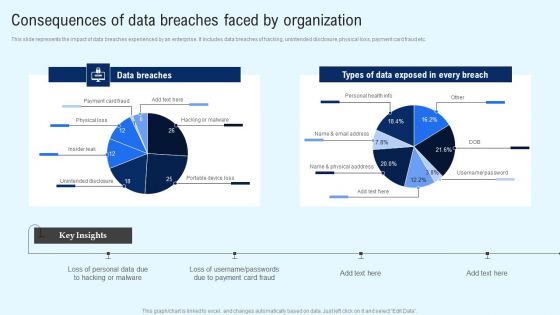
Implementing Cyber Security Incident Consequences Of Data Breaches Faced By Organization Infographics PDF
This slide represents the impact of data breaches experienced by an enterprise. It includes data breaches of hacking, unintended disclosure, physical loss, payment card fraud etc. Create an editable Implementing Cyber Security Incident Consequences Of Data Breaches Faced By Organization Infographics PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre designed presentation templates help save time. Implementing Cyber Security Incident Consequences Of Data Breaches Faced By Organization Infographics PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
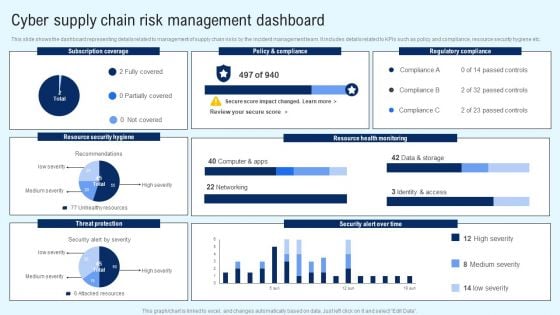
Implementing Cyber Security Incident Cyber Supply Chain Risk Dashboard Download PDF
This slide shows the dashboard representing details related to management of supply chain risks by the incident management team. It includes details related to KPIs such as policy and compliance, resource security hygiene etc. Slidegeeks is here to make your presentations a breeze with Implementing Cyber Security Incident Cyber Supply Chain Risk Dashboard Download PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
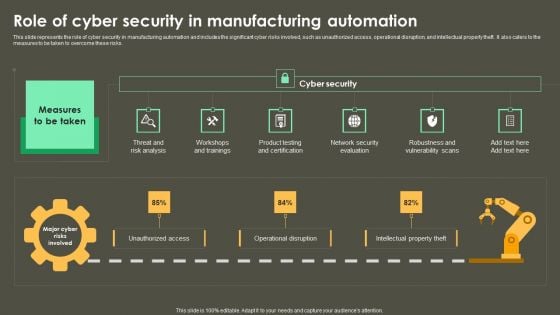
Iot Integration In Manufacturing Role Of Cyber Security In Manufacturing Automation Elements PDF
This slide represents the role of cyber security in manufacturing automation and includes the significant cyber risks involved, such as unauthorized access, operational disruption, and intellectual property theft. It also caters to the measures to be taken to overcome these risks. This modern and well-arranged Iot Integration In Manufacturing Role Of Cyber Security In Manufacturing Automation Elements PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
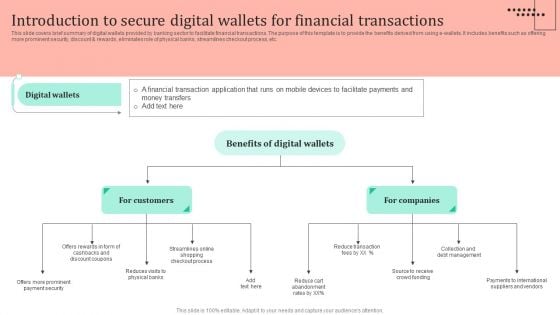
Omnichannel Strategy Implementation For Banking Solutions Introduction To Secure Digital Wallets For Financial Pictures PDF
This slide covers brief summary of digital wallets provided by banking sector to facilitate financial transactions. The purpose of this template is to provide the benefits derived from using e wallets. It includes benefits such as offering more prominent security, discount and rewards, eliminates role of physical banks, streamlines checkout process, etc. Welcome to our selection of the Omnichannel Strategy Implementation For Banking Solutions Introduction To Secure Digital Wallets For Financial Pictures PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.

Cybersecurity Operations Cybersecops Challenges And Solutions Of Security Operations Graphics PDF
This slide outlines the key challenges and solutions of security operations centers. The purpose of this slide is to highlight the problems faced by SOC teams and methods to overcome those problems. The main challenges include talent gaps, sophisticated attackers, increased data and network traffic, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Cybersecurity Operations Cybersecops Challenges And Solutions Of Security Operations Graphics PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Table Of Contents For Comprehensive Guide For Ensuring IT Infrastructure Security Slides PDF
If you are looking for a format to display your unique thoughts, then the professionally designed Table Of Contents For Comprehensive Guide For Ensuring IT Infrastructure Security Slides PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Table Of Contents For Comprehensive Guide For Ensuring IT Infrastructure Security Slides PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
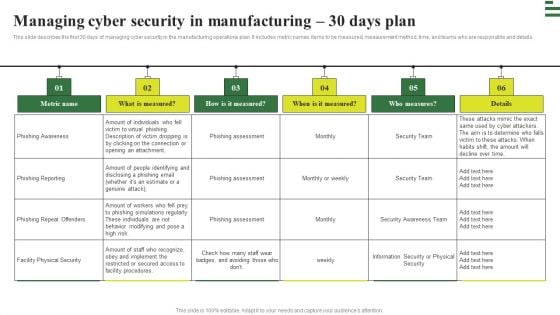
Transforming Manufacturing With Automation Managing Cyber Security 30 Days Plan Download PDF
This slide describes the first 30 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Transforming Manufacturing With Automation Managing Cyber Security 30 Days Plan Download PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Transforming Manufacturing With Automation Managing Cyber Security 60 Days Plan Structure PDF
This slide represents the next 60 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. This modern and well arranged Transforming Manufacturing With Automation Managing Cyber Security 60 Days Plan Structure PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Cloud Access Security Broker Pillar Compliance Ppt PowerPoint Presentation File Layouts PDF
This slide gives an overview of the compliance pillar of cloud access security broker. The purpose of this slide is to showcase how compliance is a vital factor for an organization migrating its data and systems to the cloud. Compliance can help industries such as healthcare, retail, and financial services. Present like a pro with Cloud Access Security Broker Pillar Compliance Ppt PowerPoint Presentation File Layouts PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
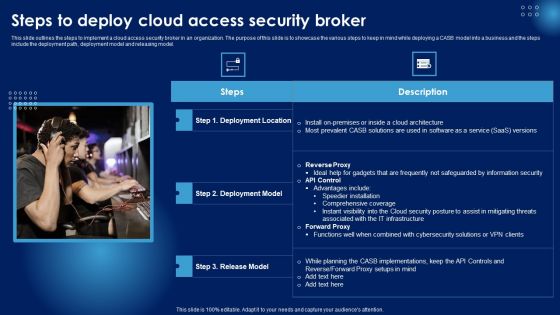
Steps To Deploy Cloud Access Security Broker Ppt PowerPoint Presentation Diagram Images PDF
This slide outlines the steps to implement a cloud access security broker in an organization. The purpose of this slide is to showcase the various steps to keep in mind while deploying a CASB model into a business and the steps include the deployment path, deployment model and releasing model. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Steps To Deploy Cloud Access Security Broker Ppt PowerPoint Presentation Diagram Images PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
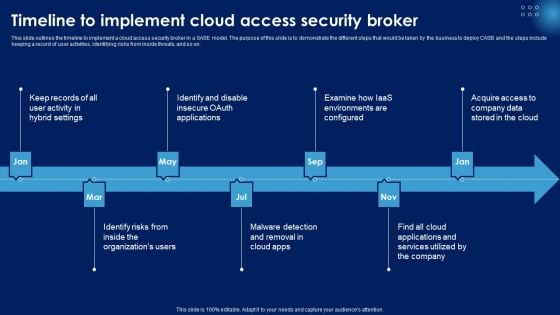
Timeline To Implement Cloud Access Security Broker Ppt PowerPoint Presentation File Styles PDF
This slide outlines the timeline to implement a cloud access security broker in a SASE model. The purpose of this slide is to demonstrate the different steps that would be taken by the business to deploy CASB and the steps include keeping a record of user activities, identifying risks from inside threats, and so on. Slidegeeks is here to make your presentations a breeze with Timeline To Implement Cloud Access Security Broker Ppt PowerPoint Presentation File Styles PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Blockchain Security Solutions Deployment Blockchain Hashing SHA 256 Algorithm Formats PDF
This slide talks about the hashing SHA-256 algorithm used in blockchain technology, including its properties. The purpose of this slide is to give an overview of hashing and its properties, such as collision resistance, deterministic, quick, and irreversible. Create an editable Blockchain Security Solutions Deployment Blockchain Hashing SHA 256 Algorithm Formats PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Blockchain Security Solutions Deployment Blockchain Hashing SHA 256 Algorithm Formats PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Blockchain Security Solutions Deployment How Blockchain Prevents Fraud And Data Theft Themes PDF
This slide describes the different methods used by blockchain technology to prevent data from fraud and stealing. The purpose of this slide is to showcase the various techniques and technologies used in blockchain technology to prevent fraud and data theft. Get a simple yet stunning designed Blockchain Security Solutions Deployment How Blockchain Prevents Fraud And Data Theft Themes PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Blockchain Security Solutions Deployment How Blockchain Prevents Fraud And Data Theft Themes PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
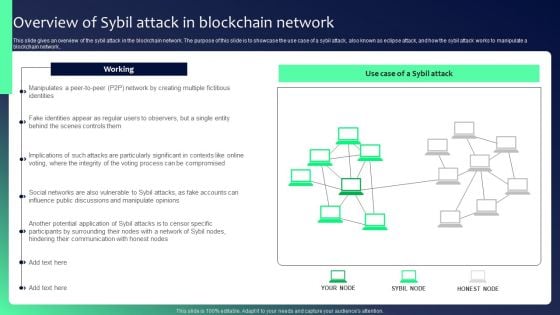
Blockchain Security Solutions Deployment Overview Of Sybil Attack In Blockchain Summary PDF
This slide gives an overview of the sybil attack in the blockchain network. The purpose of this slide is to showcase the use case of a sybil attack, also known as eclipse attack, and how the sybil attack works to manipulate a blockchain network.. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Blockchain Security Solutions Deployment Overview Of Sybil Attack In Blockchain Summary PDF can be your best option for delivering a presentation. Represent everything in detail using Blockchain Security Solutions Deployment Overview Of Sybil Attack In Blockchain Summary PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
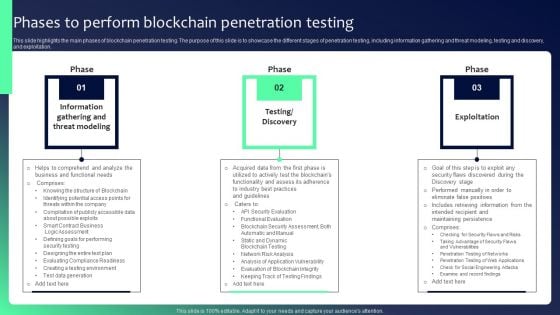
Blockchain Security Solutions Deployment Phases To Perform Blockchain Penetration Graphics PDF
This slide highlights the main phases of blockchain penetration testing. The purpose of this slide is to showcase the different stages of penetration testing, including information gathering and threat modeling, testing and discovery, and exploitation. Find highly impressive Blockchain Security Solutions Deployment Phases To Perform Blockchain Penetration Graphics PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Blockchain Security Solutions Deployment Phases To Perform Blockchain Penetration Graphics PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now

Conduct Inspection Examine Poor Workplace Safety Protocol And Security Practices Elements Pdf
This slide highlights the poor work practices at worksites which showcases defective tools usage, improper lifting, high load at extension cords with general principal for inspections. Find highly impressive Conduct Inspection Examine Poor Workplace Safety Protocol And Security Practices Elements Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Conduct Inspection Examine Poor Workplace Safety Protocol And Security Practices Elements Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide highlights the poor work practices at worksites which showcases defective tools usage, improper lifting, high load at extension cords with general principal for inspections.
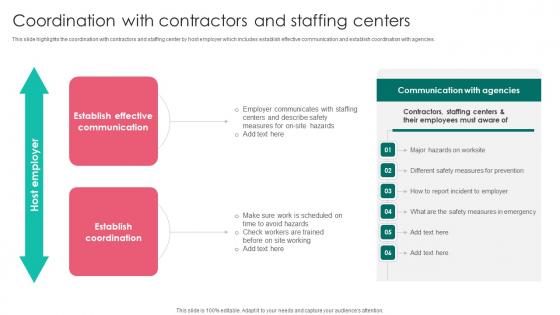
Coordination With Contractors Workplace Safety Protocol And Security Practices Ideas Pdf
This slide highlights the coordination with contractors and staffing center by host employer which includes establish effective communication and establish coordination with agencies. If you are looking for a format to display your unique thoughts, then the professionally designed Coordination With Contractors Workplace Safety Protocol And Security Practices Ideas Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Coordination With Contractors Workplace Safety Protocol And Security Practices Ideas Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide highlights the coordination with contractors and staffing center by host employer which includes establish effective communication and establish coordination with agencies.
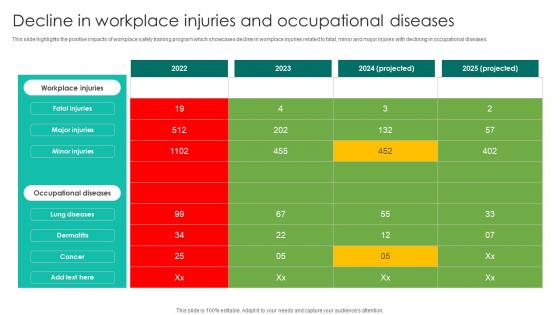
Decline In Workplace Injuries Workplace Safety Protocol And Security Practices Diagrams Pdf
This slide highlights the positive impacts of workplace safety training program which showcases decline in workplace injuries related to fatal, minor and major injures with declining in occupational diseases. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Decline In Workplace Injuries Workplace Safety Protocol And Security Practices Diagrams Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Decline In Workplace Injuries Workplace Safety Protocol And Security Practices Diagrams Pdf that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide highlights the positive impacts of workplace safety training program which showcases decline in workplace injuries related to fatal, minor and major injures with declining in occupational diseases.

Most Common Air Compressor Workplace Safety Protocol And Security Practices Microsoft Pdf
This slide highlights the common air compressor hazards which includes electrical dangers, fumes from diesel air compressor, high pressure injection and high noise form air compressor Are you searching for a Most Common Air Compressor Workplace Safety Protocol And Security Practices Microsoft Pdf that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Most Common Air Compressor Workplace Safety Protocol And Security Practices Microsoft Pdf from Slidegeeks today. This slide highlights the common air compressor hazards which includes electrical dangers, fumes from diesel air compressor, high pressure injection and high noise form air compressor
Operational Safety Guidelines Air Workplace Safety Protocol And Security Practices Icons Pdf
This slides highlights the operational safety guidelines to minimize air compressor hazards. It showcases different protective gears with pre operation, operation and post operation. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download Operational Safety Guidelines Air Workplace Safety Protocol And Security Practices Icons Pdf to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the Operational Safety Guidelines Air Workplace Safety Protocol And Security Practices Icons Pdf. This slides highlights the operational safety guidelines to minimize air compressor hazards. It showcases different protective gears with pre operation, operation and post operation.

Safety Guidelines Handling Power Workplace Safety Protocol And Security Practices Guidelines Pdf
This slide highlights the safety guidelines which showcases the general precautions while handling power tools to prevent accidents. It also highlights on different personal protective equipment while using tools Create an editable Safety Guidelines Handling Power Workplace Safety Protocol And Security Practices Guidelines Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Safety Guidelines Handling Power Workplace Safety Protocol And Security Practices Guidelines Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide highlights the safety guidelines which showcases the general precautions while handling power tools to prevent accidents. It also highlights on different personal protective equipment while using tools
Worker Participation To Eliminate Safety Workplace Safety Protocol And Security Practices Icons Pdf
This slide highlights the worker participation to remove safety risks which includes motivate workers for participation, report safety concerns, provide information access to workers and eliminate participation barrier. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Worker Participation To Eliminate Safety Workplace Safety Protocol And Security Practices Icons Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Worker Participation To Eliminate Safety Workplace Safety Protocol And Security Practices Icons Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide highlights the worker participation to remove safety risks which includes motivate workers for participation, report safety concerns, provide information access to workers and eliminate participation barrier.
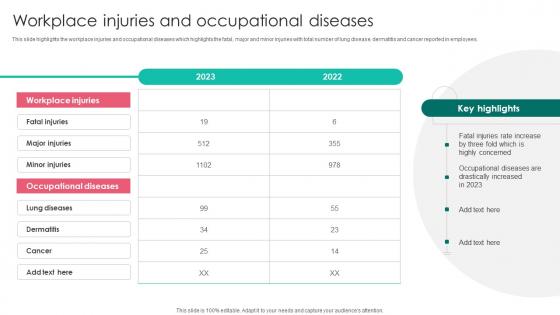
Workplace Injuries And Occupational Workplace Safety Protocol And Security Practices Download Pdf
This slide highlights the workplace injuries and occupational diseases which highlights the fatal, major and minor injuries with total number of lung disease, dermatitis and cancer reported in employees. Get a simple yet stunning designed Workplace Injuries And Occupational Workplace Safety Protocol And Security Practices Download Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Workplace Injuries And Occupational Workplace Safety Protocol And Security Practices Download Pdf can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide highlights the workplace injuries and occupational diseases which highlights the fatal, major and minor injuries with total number of lung disease, dermatitis and cancer reported in employees.
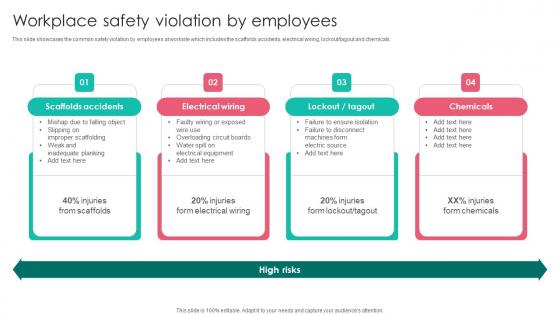
Workplace Safety Violation By Employees Workplace Safety Protocol And Security Practices Demonstration Pdf
This slide showcases the common safety violation by employees at worksite which includes the scaffolds accidents, electrical wiring, lockout tagout and chemicals. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Workplace Safety Violation By Employees Workplace Safety Protocol And Security Practices Demonstration Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Workplace Safety Violation By Employees Workplace Safety Protocol And Security Practices Demonstration Pdf today and make your presentation stand out from the rest This slide showcases the common safety violation by employees at worksite which includes the scaffolds accidents, electrical wiring, lockout tagout and chemicals.

Methods To Identify Crypto Comprehensive Guide To Blockchain Digital Security Template Pdf
The following slide illustrates various methods to determine blockchain phishing attack and safeguard confidential information. It includes elements such as copycatting, spellings, ambiguous links, using public email ID, disordered content etc. This Methods To Identify Crypto Comprehensive Guide To Blockchain Digital Security Template Pdf is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Methods To Identify Crypto Comprehensive Guide To Blockchain Digital Security Template Pdf features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today The following slide illustrates various methods to determine blockchain phishing attack and safeguard confidential information. It includes elements such as copycatting, spellings, ambiguous links, using public email ID, disordered content etc.

Table Of Contents For Comprehensive Guide To Blockchain Digital Security Risk Management Download Pdf
Boost your pitch with our creative Table Of Contents For Comprehensive Guide To Blockchain Digital Security Risk Management Download Pdf. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. Our Table Of Contents For Comprehensive Guide To Blockchain Digital Security Risk Management Download Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
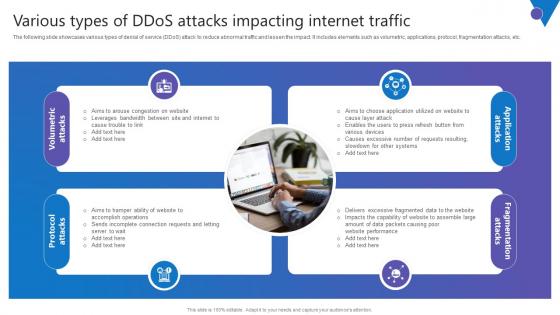
Various Types Of DDoS Attacks Comprehensive Guide To Blockchain Digital Security Introduction Pdf
The following slide showcases various types of denial of service DDoS attack to reduce abnormal traffic and lessen the impact. It includes elements such as volumetric, applications, protocol, fragmentation attacks, etc. Get a simple yet stunning designed Various Types Of DDoS Attacks Comprehensive Guide To Blockchain Digital Security Introduction Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Various Types Of DDoS Attacks Comprehensive Guide To Blockchain Digital Security Introduction Pdf can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. The following slide showcases various types of denial of service DDoS attack to reduce abnormal traffic and lessen the impact. It includes elements such as volumetric, applications, protocol, fragmentation attacks, etc.

Table Of Contents Exploring Investment Opportunities With Security Token Offerings Graphics Pdf
Do you know about Slidesgeeks Table Of Contents Exploring Investment Opportunities With Security Token Offerings Graphics Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. Our Table Of Contents Exploring Investment Opportunities With Security Token Offerings Graphics Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Top Tenets Of Zero Trust Network Access Model Zero Trust Network Security Graphics Pdf
This graph chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Top Tenets Of Zero Trust Network Access Model Zero Trust Network Security Graphics Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Top Tenets Of Zero Trust Network Access Model Zero Trust Network Security Graphics Pdf today and make your presentation stand out from the rest This graph chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data.
Table Of Contents Monitoring Digital Assets To Enhance Cyber Security Slides Pdf
Present like a pro with Table Of Contents Monitoring Digital Assets To Enhance Cyber Security Slides Pdf Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. Our Table Of Contents Monitoring Digital Assets To Enhance Cyber Security Slides Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
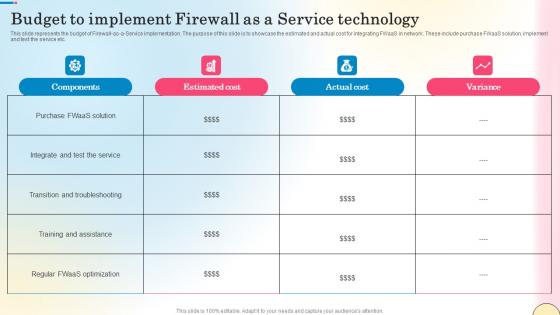
Budget To Implement Firewall As A Service Technology Network Security Diagrams Pdf
This slide represents the budget of Firewall-as-a-Service implementation. The purpose of this slide is to showcase the estimated and actual cost for integrating FWaaS in network. These include purchase FWaaS solution, implement and test the service etc. Get a simple yet stunning designed Budget To Implement Firewall As A Service Technology Network Security Diagrams Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Budget To Implement Firewall As A Service Technology Network Security Diagrams Pdf can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide represents the budget of Firewall-as-a-Service implementation. The purpose of this slide is to showcase the estimated and actual cost for integrating FWaaS in network. These include purchase FWaaS solution, implement and test the service etc.
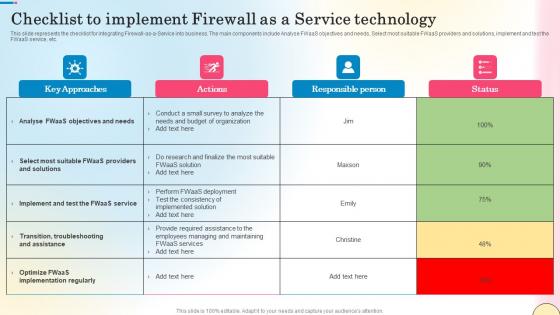
Checklist To Implement Firewall As A Service Technology Network Security Mockup Pdf
This slide represents the checklist for integrating Firewall-as-a-Service into business. The main components include Analyse FWaaS objectives and needs, Select most suitable FWaaS providers and solutions, implement and test the FWaaS service, etc. Find highly impressive Checklist To Implement Firewall As A Service Technology Network Security Mockup Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Checklist To Implement Firewall As A Service Technology Network Security Mockup Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide represents the checklist for integrating Firewall-as-a-Service into business. The main components include Analyse FWaaS objectives and needs, Select most suitable FWaaS providers and solutions, implement and test the FWaaS service, etc.
Firewall As A Service Performance Tracking Dashboard Network Security Guidelines Pdf
This slide represents the dashboard to track the performance of Firewall-as-a-Service deployed by different organizations. The purpose of this slide is to showcase the overall performance of FWaaS by demonstrating statistics of monthly threat status, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Firewall As A Service Performance Tracking Dashboard Network Security Guidelines Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Firewall As A Service Performance Tracking Dashboard Network Security Guidelines Pdf that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide represents the dashboard to track the performance of Firewall-as-a-Service deployed by different organizations. The purpose of this slide is to showcase the overall performance of FWaaS by demonstrating statistics of monthly threat status, etc.
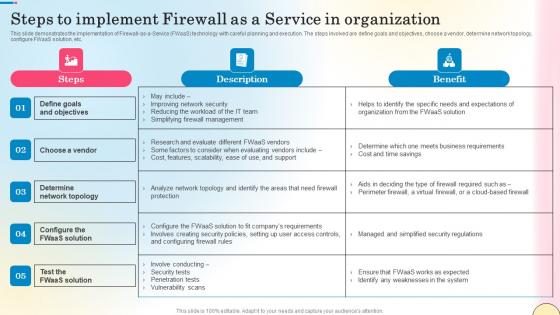
Steps To Implement Firewall As A Service In Organization Network Security Formats Pdf
This slide demonstrates the implementation of Firewall-as-a-Service FWaaS technology with careful planning and execution. The steps involved are define goals and objectives, choose a vendor, determine network topology, configure FWaaS solution, etc. Get a simple yet stunning designed Steps To Implement Firewall As A Service In Organization Network Security Formats Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Steps To Implement Firewall As A Service In Organization Network Security Formats Pdf can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide demonstrates the implementation of Firewall-as-a-Service FWaaS technology with careful planning and execution. The steps involved are define goals and objectives, choose a vendor, determine network topology, configure FWaaS solution, etc.

Comparative Analysis Of Encryption And Tokenization In Ds Securing Your Data Ppt Presentation
This slide represents the comparison of encryption and tokenization. The purpose of this slide is to highlight different components of comparison such as definition, importance, objective, and so on Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Comparative Analysis Of Encryption And Tokenization In Ds Securing Your Data Ppt Presentation With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Comparative Analysis Of Encryption And Tokenization In Ds Securing Your Data Ppt Presentation today and make your presentation stand out from the rest This slide represents the comparison of encryption and tokenization. The purpose of this slide is to highlight different components of comparison such as definition, importance, objective, and so on

Critical Challenges Of Tokenization Implementation In Ds Securing Your Data Ppt Slide
This slide highlights the disadvantages of carrying out tokenization. The purpose of this slide is to showcase the drawbacks and its implications which include increased IT complexity, limited adoption, etc. Find highly impressive Critical Challenges Of Tokenization Implementation In Ds Securing Your Data Ppt Slide on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Critical Challenges Of Tokenization Implementation In Ds Securing Your Data Ppt Slide for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide highlights the disadvantages of carrying out tokenization. The purpose of this slide is to showcase the drawbacks and its implications which include increased IT complexity, limited adoption, etc.
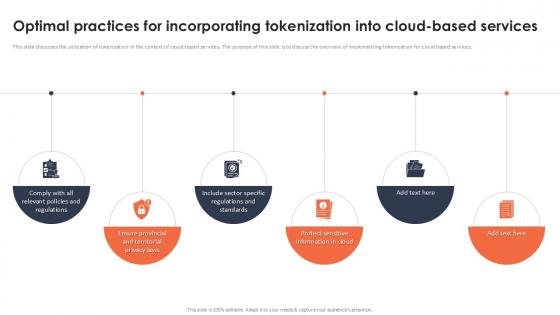
Optimal Practices For Incorporating Tokenization Into Cloud Securing Your Data Ppt Sample
This slide discusses the utilization of tokenization in the context of cloud-based services. The purpose of this slide is to discuss the overview of implementing tokenization for cloud based services. Are you searching for a Optimal Practices For Incorporating Tokenization Into Cloud Securing Your Data Ppt Sample that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Optimal Practices For Incorporating Tokenization Into Cloud Securing Your Data Ppt Sample from Slidegeeks today. This slide discusses the utilization of tokenization in the context of cloud-based services. The purpose of this slide is to discuss the overview of implementing tokenization for cloud based services.
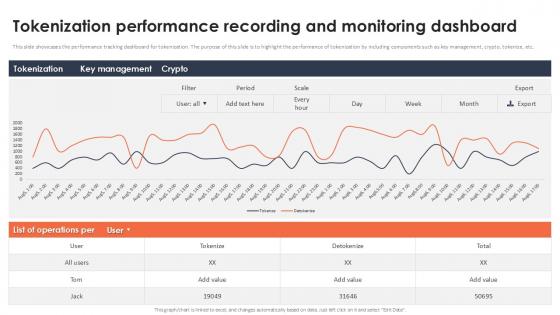
Tokenization Performance Recording And Monitoring Dashboard Securing Your Data Ppt Slide
This slide showcases the performance tracking dashboard for tokenization. The purpose of this slide is to highlight the performance of tokenization by including components such as key management, crypto, tokenize, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Tokenization Performance Recording And Monitoring Dashboard Securing Your Data Ppt Slide With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Tokenization Performance Recording And Monitoring Dashboard Securing Your Data Ppt Slide today and make your presentation stand out from the rest This slide showcases the performance tracking dashboard for tokenization. The purpose of this slide is to highlight the performance of tokenization by including components such as key management, crypto, tokenize, etc.
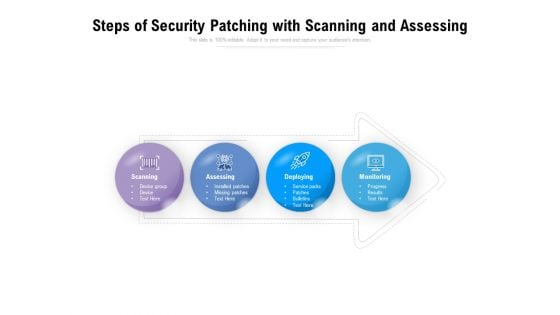
Steps Of Security Patching With Scanning And Assessing Ppt PowerPoint Presentation Slides Portrait PDF
Presenting this set of slides with name steps of security patching with scanning and assessing ppt powerpoint presentation slides portrait pdf. This is a four stage process. The stages in this process are scanning, assessing, deploying, monitoring, device group, device, installed patches, missing patches, service packs, patches, bulletins, progress, results. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Cyber Security Detection Response Ppt PowerPoint Presentation Model Infographic Template Cpb Pdf
Presenting this set of slides with name cyber security detection response ppt powerpoint presentation model infographic template cpb pdf. This is an editable Powerpoint four stages graphic that deals with topics like customer centric systems to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Data Security Financial Services Ppt PowerPoint Presentation Styles Design Templates Cpb Pdf
Presenting this set of slides with name data security financial services ppt powerpoint presentation styles design templates cpb pdf. This is an editable Powerpoint four stages graphic that deals with topics like data metrics inside application to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Data Warehouse Security Issues Ppt PowerPoint Presentation Inspiration Master Slide Cpb Pdf
Presenting this set of slides with name data warehouse security issues ppt powerpoint presentation inspiration master slide cpb pdf. This is an editable Powerpoint seven stages graphic that deals with topics like data services market data pricing analytics to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Cyber Security For Your Organization Budget For Effective Cybersecurity Management Ppt Ideas Objects PDF
Presenting this set of slides with name cyber security for your organization budget for effective cybersecurity management ppt ideas objects pdf. This is a one stage process. The stages in this process are incident management, risk management, client onboarding process, document management, information management, release management . This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Cyber Security For Your Organization Business Impact Assessment Ppt Icon Designs PDF
Presenting this set of slides with name cyber security for your organization business impact assessment ppt icon designs pdf. This is a three stage process. The stages in this process are department function, executive dexter hastings, employees, bcp representative, primary business function, strengths, weaknesses, loss impact. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security For Your Organization Table Of Contents Ppt Design Ideas PDF
Presenting this set of slides with name cyber security for your organization table of contents ppt design ideas pdf. The topics discussed in these slides are analyzing current scenario, initiating cyber risk management program, incident management, role personnel, dashboard, impact analysis, cost associated firm, cybersecurity contingency plan. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.


 Continue with Email
Continue with Email

 Home
Home


































