lock

Cloud Security Threats Contract Breaches With Clients Download PDF
This slide defines the contract breaches with clients and customers that could be the biggest threat to the organizational data. Presenting Cloud Security Threats Contract Breaches With Clients Download PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Organization, Business Partners, Information Could. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
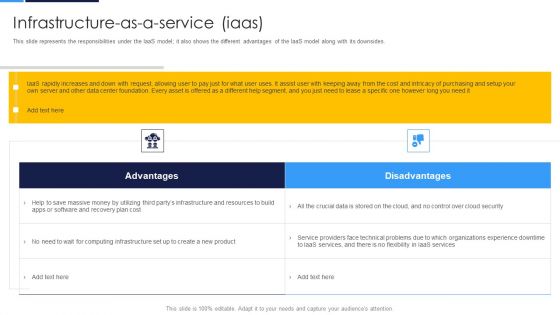
Cloud Security Assessment Infrastructure As A Ervice Iaas Diagrams PDF
This slide represents the responsibilities under the IaaS model it also shows the different advantages of the IaaS model along with its downsides.Deliver an awe inspiring pitch with this creative Cloud Security Assessment Infrastructure As A Ervice Iaas Diagrams PDF bundle. Topics like Service Providers, Computing Infrastructure, Recovery Plan can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
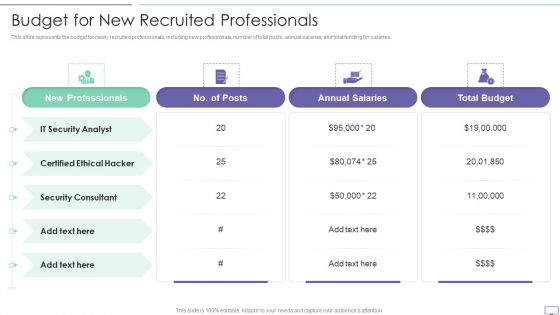
IT Security Hacker Budget For New Recruited Professionals Infographics PDF
This slide represents the budget for newly recruited professionals, including new professionals, number of total posts, annual salaries, and total funding for salaries.Deliver and pitch your topic in the best possible manner with this IT Security Hacker Budget For New Recruited Professionals Infographics PDF. Use them to share invaluable insights on New Professionals, Certified Ethical, Annual Salaries and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
IT Security Hacker Costs Of Repairing Damages Icons PDF
This slide depicts the increased additional costs caused by cyber-attacks to the organization, such as DDOS attacks, hacking of the website, email domain, and ransom money.Deliver an awe inspiring pitch with this creative IT Security Hacker Costs Of Repairing Damages Icons PDF bundle. Topics like Network Equipment, Network Accounts, Regain Access can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
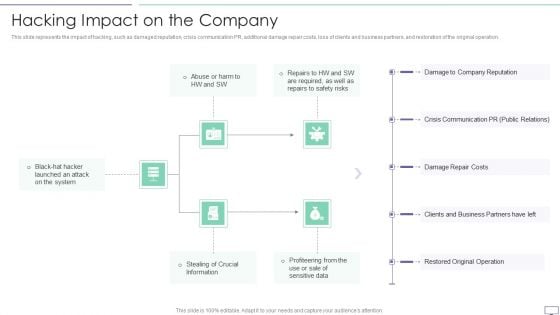
IT Security Hacker Hacking Impact On The Company Information PDF
This slide represents the impact of hacking, such as damaged reputation, crisis communication PR, additional damage repair costs, loss of clients and business partners, and restoration of the original operation. Deliver an awe inspiring pitch with this creative IT Security Hacker Hacking Impact On The Company Information PDF bundle. Topics like Company Reputation, Crisis Communication, Damage Repair can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
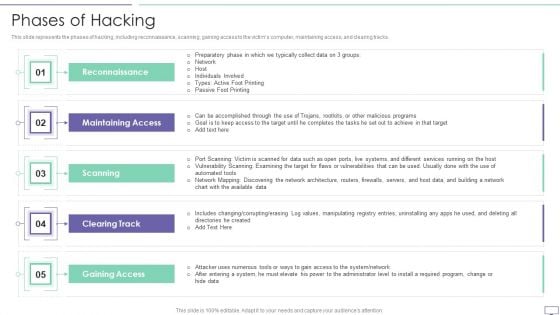
IT Security Hacker Phases Of Hacking Topics PDF
This slide represents the phases of hacking, including reconnaissance, scanning, gaining access to the victims computer, maintaining access, and clearing tracks.Deliver and pitch your topic in the best possible manner with this IT Security Hacker Phases Of Hacking Topics PDF. Use them to share invaluable insights on Maintaining Access, Reconnaissance, Gaining Access and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
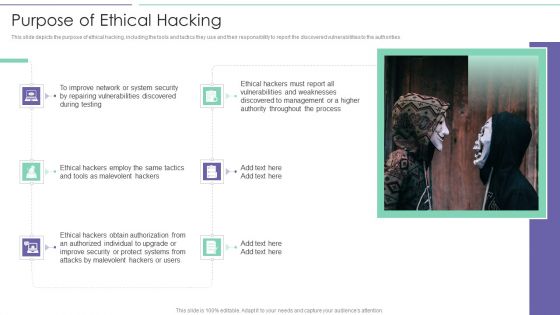
IT Security Hacker Purpose Of Ethical Hacking Slides PDF
This slide depicts the purpose of ethical hacking, including the tools and tactics they use and their responsibility to report the discovered vulnerabilities to the authorities.Deliver and pitch your topic in the best possible manner with this IT Security Hacker Purpose Of Ethical Hacking Slides PDF. Use them to share invaluable insights on Vulnerabilities Discovered, Malevolent Hackers, Malevolent Hackers and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
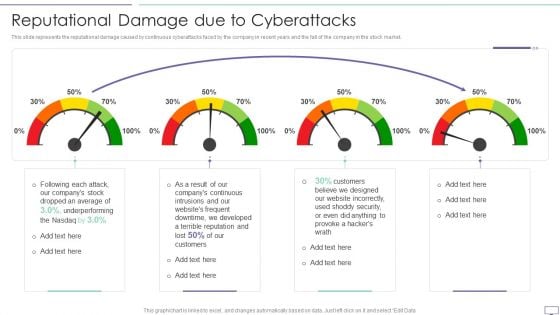
IT Security Hacker Reputational Damage Due To Cyberattacks Guidelines PDF
This slide represents the reputational damage caused by continuous cyberattacks faced by the company in recent years and the fall of the company in the stock market.Deliver and pitch your topic in the best possible manner with this IT Security Hacker Reputational Damage Due To Cyberattacks Guidelines PDF. Use them to share invaluable insights on Website Incorrectly, Underperforming, Dropped An Average and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Table Of Contents For IT Security Hacker Background PDF
This is a Table Of Contents For IT Security Hacker Background PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Current Situation, Impact Of Hacking, Repairing Damages. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Service Agreement For Securing More Clients Brochure PDF
Purpose of this slide is to show service agreement that will assist service managers in gaining the attention on new clients. Sections covered in the agreement are parties, invoices, list of service and signature.Deliver an awe inspiring pitch with this creative Service Agreement For Securing More Clients Brochure PDF bundle. Topics like Agreement Is Entered, Services Provide, Term Of Agreement can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
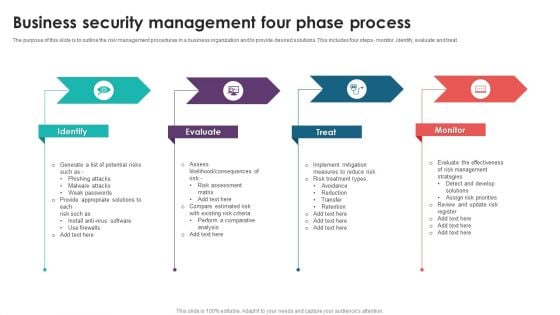
Business Security Management Four Phase Process Topics PDF
The purpose of this slide is to outline the risk management procedures in a business organization and to provide desired solutions. This includes four steps- monitor, identify, evaluate and treat. Presenting Business Security Management Four Phase Process Topics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Identify, Evaluate, Treat, Monitor. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Table Of Contents Cyber Security Automation Framework Ideas PDF
If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Table Of Contents Cyber Security Automation Framework Ideas PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.

Framework Of IT Security Awareness Training Program Information PDF
This slide covers framework of cybersecurity awareness training program. It involves five steps such as analyse, plan, deploy, measure and optimize. Presenting Framework Of IT Security Awareness Training Program Information PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Analyze, Plan, Deploy, Measure, Optimize. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
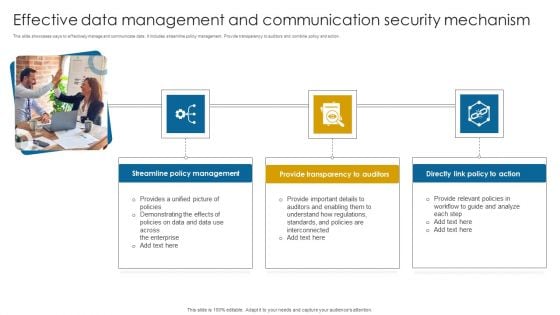
Effective Data Management And Communication Security Mechanism Themes PDF
This slide showcases ways to effectively manage and communicate data. It includes streamline policy management. Provide transparency to auditors and combine policy and action. Presenting Effective Data Management And Communication Security Mechanism Themes PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Streamline Policy Management, Provide Transparency, Directly Action. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
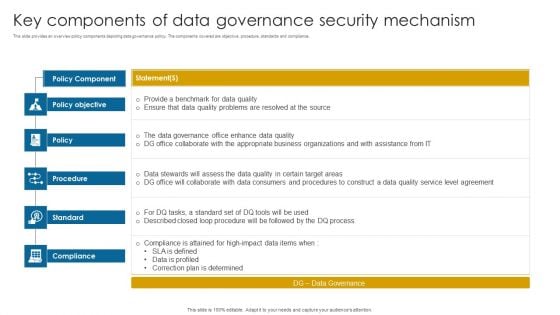
Key Components Of Data Governance Security Mechanism Information PDF
This slide provides an overview policy components depicting data governance policy. The components covered are objective, procedure, standards and compliance.Pitch your topic with ease and precision using this Key Components Of Data Governance Security Mechanism Information PDF. This layout presents information on Data Governance, Compliance Attained, Correction Determined. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
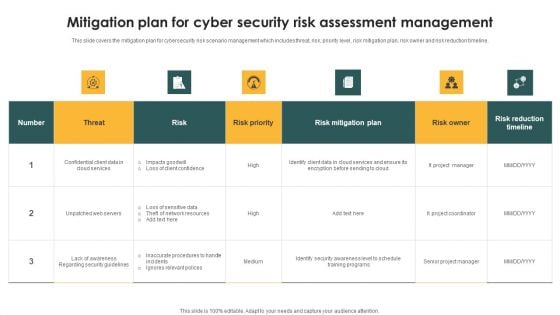
Mitigation Plan For Cyber Security Risk Assessment Management Sample PDF
This slide covers the mitigation plan for cybersecurity risk scenario management which includes threat, risk, priority level, risk mitigation plan, risk owner and risk reduction timeline. Showcasing this set of slides titled Mitigation Plan For Cyber Security Risk Assessment Management Sample PDF. The topics addressed in these templates are Threat, Risk, Risk Priority. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Agenda Security Automation To Analyze And Mitigate Cyberthreats Brochure PDF
Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Agenda Security Automation To Analyze And Mitigate Cyberthreats Brochure PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
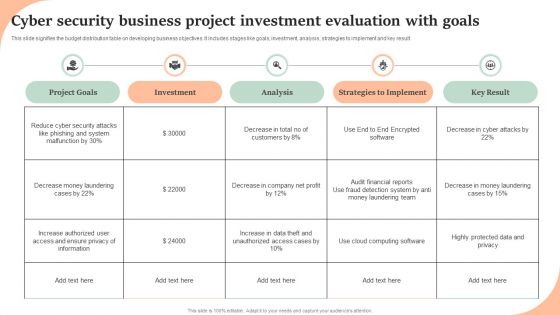
Cyber Security Business Project Investment Evaluation With Goals Structure PDF
This slide signifies the budget distribution table on developing business objectives. It includes stages like goals, investment, analysis, strategies to implement and key result. Showcasing this set of slides titled Cyber Security Business Project Investment Evaluation With Goals Structure PDF. The topics addressed in these templates are Project Goals, Investment, Analysis, Strategies To Implement, Key Result. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Information Technology Security Risk Assessment Framework Demonstration PDF
The following slide highlights the structure to identify best practices to fix risk tolerances. It constitutes of activities such as identify, protect, detect, respond and recover. Presenting Information Technology Security Risk Assessment Framework Demonstration PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Protect, Detect, Respond. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Information Systems Security And Risk Management Plan Quotes Guidelines PDF
From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Information Systems Security And Risk Management Plan Quotes Guidelines PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
IT Security Risk Management And Incident Management Dashboard Icons PDF
This slide displays dashboard to help company in designing initiatives to mitigate cybersecurity risks. It includes kpis such as incident management, patches, compliance, vulnerabilities, etc. Showcasing this set of slides titled IT Security Risk Management And Incident Management Dashboard Icons PDF. The topics addressed in these templates are Compliance, Patches, Incident Management, Vulnerabilities Management, Cybersecurity Initiatives. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

IT Security Risk Management Process For Organization Template PDF
This slide displays flow diagram to illustrate cybersecurity risk management process to ensure continuous monitoring. It includes components such as threats, vulnerabilities, impacts, intelligence, etc. Showcasing this set of slides titled IT Security Risk Management Process For Organization Template PDF. The topics addressed in these templates are Organization, Cyber Intelligence, Continuous Monitoring, Vulnerabilities. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
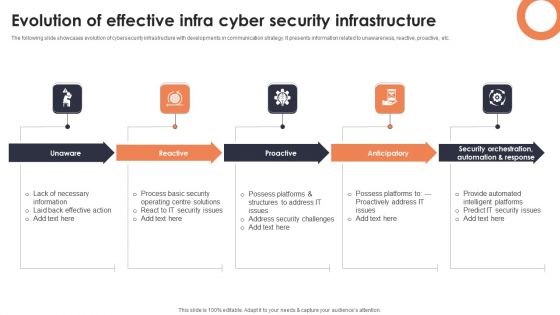
Evolution Of Effective Infra Cyber Security Infrastructure Infographics PDF
The following slide showcases evolution of cybersecurity infrastructure with developments in communication strategy. It presents information related to unawareness, reactive, proactive, etc. Presenting Evolution Of Effective Infra Cyber Security Infrastructure Infographics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Unaware, Reactive, Proactive. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
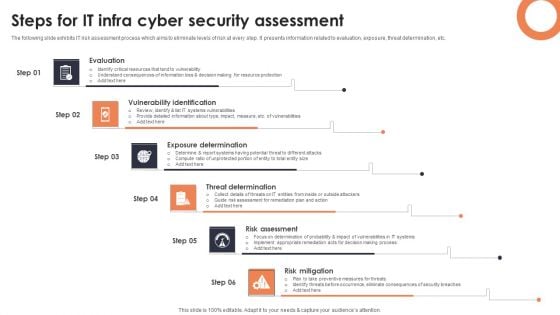
Steps For IT Infra Cyber Security Assessment Background PDF
The following slide exhibits IT risk assessment process which aims to eliminate levels of risk at every step. It presents information related to evaluation, exposure, threat determination, etc. Presenting Steps For IT Infra Cyber Security Assessment Background PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Evaluation, Vulnerability Identification, Exposure Determination. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Timeframe For Incident Management In Security Centre Portrait PDF
This slide provides information regarding entire duration of incident handling process which occur in various phases. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Timeframe For Incident Management In Security Centre Portrait PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.
Security Software Company Investor Funding Pitch Deck Quotes Background PDF
This Security Software Company Investor Funding Pitch Deck Quotes Background PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The product features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today
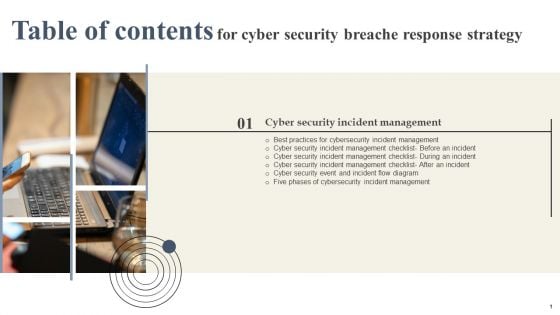
Cyber Security Breache Response Strategy Table Of Contents Summary PDF
Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Cyber Security Breache Response Strategy Table Of Contents Summary PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
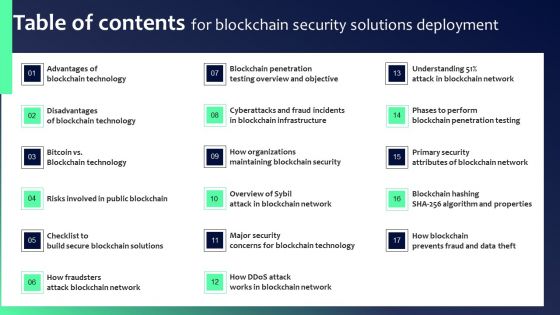
Table Of Contents For Blockchain Security Solutions Deployment Ideas PDF
Slidegeeks has constructed Table Of Contents For Blockchain Security Solutions Deployment Ideas PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.
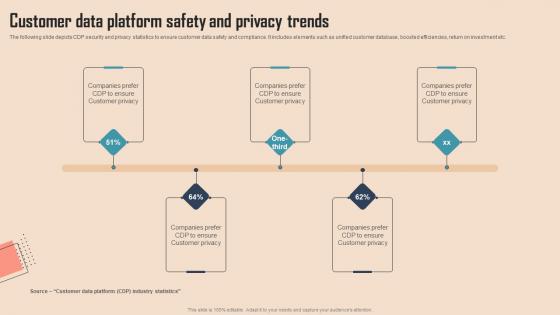
Customer Data Platform Safety And Comprehensive CDP Guide For Promoters Brochure Pdf
The following slide depicts CDP security and privacy statistics to ensure customer data safety and compliance. It includes elements such as unified customer database, boosted efficiencies, return on investment etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Customer Data Platform Safety And Comprehensive CDP Guide For Promoters Brochure Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. The following slide depicts CDP security and privacy statistics to ensure customer data safety and compliance. It includes elements such as unified customer database, boosted efficiencies, return on investment etc.
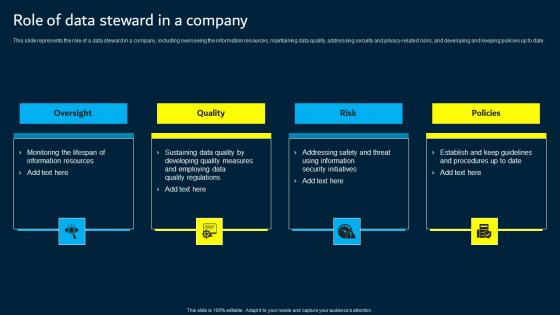
Role Of Data Steward In A Company Data Custodianship Brochure Pdf
This slide represents the role of a data steward in a company, including overseeing the information resources, maintaining data quality, addressing security and privacy related risks, and developing and keeping policies up to date. Retrieve professionally designed Role Of Data Steward In A Company Data Custodianship Brochure Pdf to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide represents the role of a data steward in a company, including overseeing the information resources, maintaining data quality, addressing security and privacy related risks, and developing and keeping policies up to date.
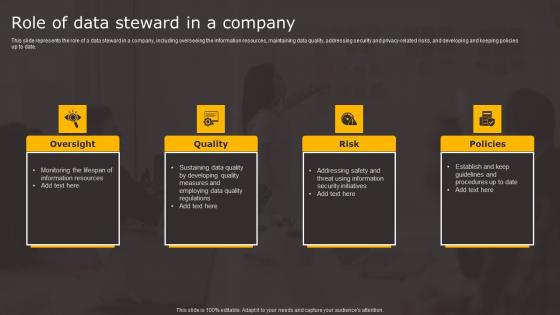
Data Stewardship In Business Processes Role Of Data Steward In A Company Background Pdf
This slide represents the role of a data steward in a company, including overseeing the information resources, maintaining data quality, addressing security and privacy related risks, and developing and keeping policies up to date. Make sure to capture your audiences attention in your business displays with our gratis customizable Data Stewardship In Business Processes Role Of Data Steward In A Company Background Pdf. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide represents the role of a data steward in a company, including overseeing the information resources, maintaining data quality, addressing security and privacy related risks, and developing and keeping policies up to date.

Healthcare Information Technology Transforming Medicare Services Using Health Guidelines Pdf
This slide covers healthcare information technology trends to ensure effective transformation of health services. It involves key trends such as internet of medical things, cognitive automation and cyber security and data privacy. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Healthcare Information Technology Transforming Medicare Services Using Health Guidelines Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Healthcare Information Technology Transforming Medicare Services Using Health Guidelines Pdf today and make your presentation stand out from the rest This slide covers healthcare information technology trends to ensure effective transformation of health services. It involves key trends such as internet of medical things, cognitive automation and cyber security and data privacy.
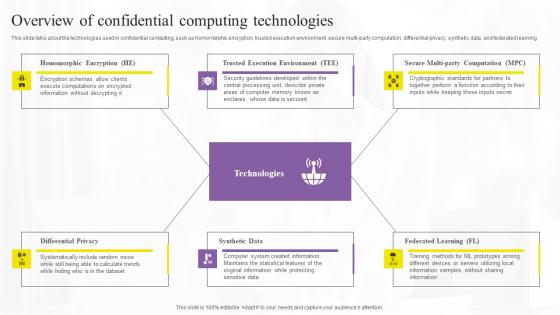
Overview Of Confidential Computing Technologies Elements Pdf
This slide talks about the technologies used in confidential computing, such as homomorphic encryption, trusted execution environment, secure multi-party computation, differential privacy, synthetic data, and federated learning. The Overview Of Confidential Computing Technologies Elements Pdf is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide talks about the technologies used in confidential computing, such as homomorphic encryption, trusted execution environment, secure multi-party computation, differential privacy, synthetic data, and federated learning.
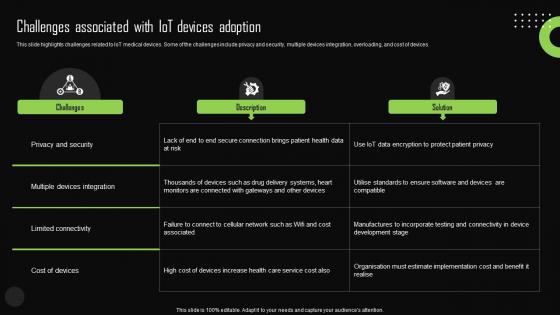
Challenges Associated With Iot Devices Adoption Iot Device Management Slides Pdf
This slide highlights challenges related to IoT medical devices. Some of the challenges include privacy and security, multiple devices integration, overloading, and cost of devices. Slidegeeks is here to make your presentations a breeze with Challenges Associated With Iot Devices Adoption Iot Device Management Slides Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide highlights challenges related to IoT medical devices. Some of the challenges include privacy and security, multiple devices integration, overloading, and cost of devices.
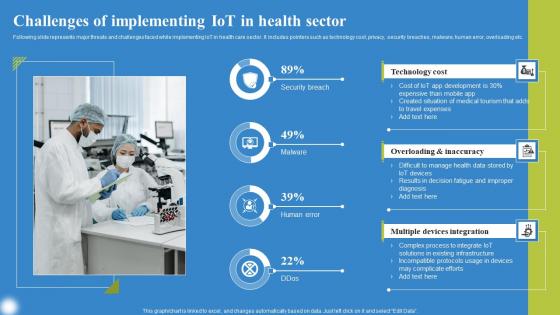
Challenges Of Implementing IoT Deploying IoT Solutions For Enhanced Healthcare Background Pdf
Following slide represents major threats and challenges faced while implementing IoT in health care sector. It includes pointers such as technology cost, privacy, security breaches, malware, human error, overloading etc. Retrieve professionally designed Challenges Of Implementing IoT Deploying IoT Solutions For Enhanced Healthcare Background Pdf to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. Following slide represents major threats and challenges faced while implementing IoT in health care sector. It includes pointers such as technology cost, privacy, security breaches, malware, human error, overloading etc.
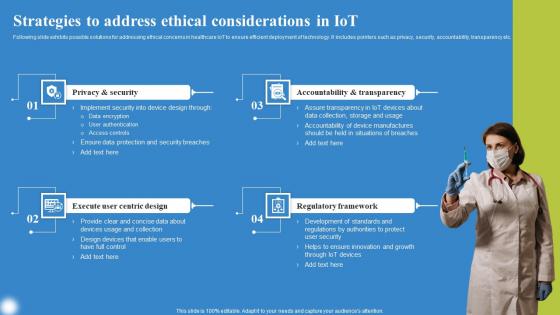
Strategies To Address Ethical Deploying IoT Solutions For Enhanced Healthcare Background Pdf
Following slide exhibits possible solutions for addressing ethical concerns in healthcare IoT to ensure efficient deployment of technology. It includes pointers such as privacy, security, accountability, transparency etc. Want to ace your presentation in front of a live audience Our Strategies To Address Ethical Deploying IoT Solutions For Enhanced Healthcare Background Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use. Following slide exhibits possible solutions for addressing ethical concerns in healthcare IoT to ensure efficient deployment of technology. It includes pointers such as privacy, security, accountability, transparency etc.
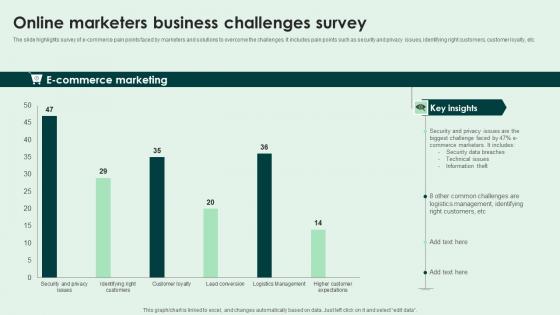
Online Marketers Business Challenges Survey Slides Pdf
The slide highlights survey of e-commerce pain points faced by marketers and solutions to overcome the challenges. It includes pain points such as security and privacy issues, identifying right customers, customer loyalty, etc. Pitch your topic with ease and precision using this Online Marketers Business Challenges Survey Slides Pdf. This layout presents information on E Commerce Marketing. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. The slide highlights survey of e-commerce pain points faced by marketers and solutions to overcome the challenges. It includes pain points such as security and privacy issues, identifying right customers, customer loyalty, etc.

Action Steps To Tackle Edge Analytics Challenges Template Pdf
This slide covers the challenges of edge analytics in business formal language. The purpose of this template is to provide a concise overview of the challenges that organizations may face when adopting edge analytics, including data security, data privacy, latency, cost, and fragmentation.Showcasing this set of slides titled Action Steps To Tackle Edge Analytics Challenges Template Pdf The topics addressed in these templates are Processing Power Bandwidth, Integrate Manage, Promote Interoperability All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide covers the challenges of edge analytics in business formal language. The purpose of this template is to provide a concise overview of the challenges that organizations may face when adopting edge analytics, including data security, data privacy, latency, cost, and fragmentation.

Comparative Analysis Of Top Content Management Developing And Creating Digital Content Strategy SS V
The following slide highlights comparison of multiple content management software to select the best alternative. It includes elements such as automatic notification, easy navigations, ensuring privacy, security, offering customization etc. There are so many reasons you need a Comparative Analysis Of Top Content Management Developing And Creating Digital Content Strategy SS V. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. The following slide highlights comparison of multiple content management software to select the best alternative. It includes elements such as automatic notification, easy navigations, ensuring privacy, security, offering customization etc.

Optimization Of IoT Remote Monitoring Major Challenges Faced In IoT Healthcare System IoT SS V
This slide provides an overview of the major issues faced by the IoT healthcare industry. Major problems covered are data security and privacy, integration of multiple devices and data overload. Find highly impressive Optimization Of IoT Remote Monitoring Major Challenges Faced In IoT Healthcare System IoT SS V on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Optimization Of IoT Remote Monitoring Major Challenges Faced In IoT Healthcare System IoT SS V for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide provides an overview of the major issues faced by the IoT healthcare industry. Major problems covered are data security and privacy, integration of multiple devices and data overload.

Addressing Solutions For Erp Integration Challenges Erp And Digital Transformation For Maximizing DT SS V
This slide presents solutions to address various issues regarding enterprise integration in digital transformation. It includes resistance to change, data integration and quality issues, vendor selection and compatibility, inadequate talent and training, security and data privacy concerns, legacy systems and technical debt, and user adoption and training.Find a pre-designed and impeccable Addressing Solutions For Erp Integration Challenges Erp And Digital Transformation For Maximizing DT SS V. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide presents solutions to address various issues regarding enterprise integration in digital transformation. It includes resistance to change, data integration and quality issues, vendor selection and compatibility, inadequate talent and training, security and data privacy concerns, legacy systems and technical debt, and user adoption and training.
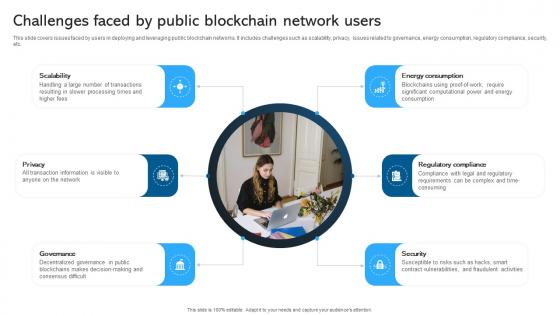
Comprehensive Manual Challenges Faced By Public Blockchain Network Users BCT SS V
This slide covers issues faced by users in deploying and leveraging public blockchain networks. It includes challenges such as scalability, privacy, issues related to governance, energy consumption, regulatory compliance, security, etc. Boost your pitch with our creative Comprehensive Manual Challenges Faced By Public Blockchain Network Users BCT SS V. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide covers issues faced by users in deploying and leveraging public blockchain networks. It includes challenges such as scalability, privacy, issues related to governance, energy consumption, regulatory compliance, security, etc.
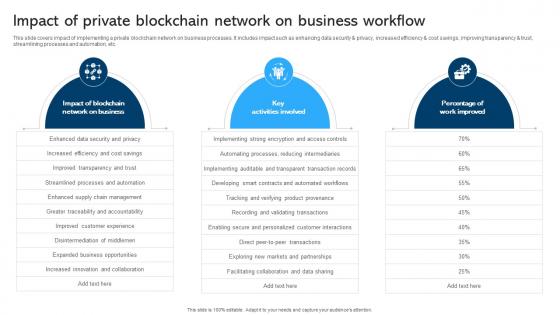
Comprehensive Manual For Blockchain Impact Of Private Blockchain Network BCT SS V
This slide covers impact of implementing a private blockchain network on business processes. It includes impact such as enhancing data security and privacy, increased efficiency and cost savings, improving transparency and trust, streamlining processes and automation, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Comprehensive Manual For Blockchain Impact Of Private Blockchain Network BCT SS V. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide covers impact of implementing a private blockchain network on business processes. It includes impact such as enhancing data security and privacy, increased efficiency and cost savings, improving transparency and trust, streamlining processes and automation, etc.

Why Invest With Us Digital Payment Platform Pitch Deck
This slide mentions the various reasons why potential investors should be investing with the company. Key reasons strong product offering, ROI for investors, security and privacy, AI integrated technology, investment option, growing user base. Explore a selection of the finest Why Invest With Us Digital Payment Platform Pitch Deck here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Why Invest With Us Digital Payment Platform Pitch Deck to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide mentions the various reasons why potential investors should be investing with the company. Key reasons strong product offering, ROI for investors, security and privacy, AI integrated technology, investment option, growing user base.
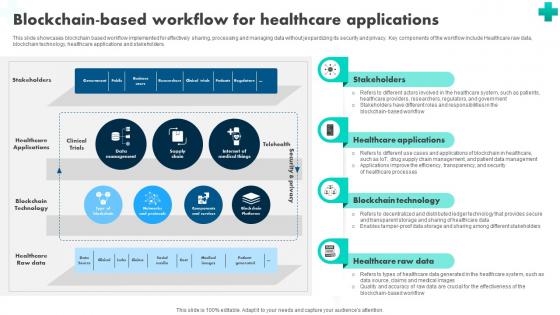
A56 How Blockchain Is Reshaping Blockchain Based Workflow For Healthcare BCT SS V
This slide showcases blockchain based workflow implemented for effectively sharing, processing and managing data without jeopardizing its security and privacy. Key components of the workflow include Healthcare raw data, blockchain technology, healthcare applications and stakeholders. Want to ace your presentation in front of a live audience Our A56 How Blockchain Is Reshaping Blockchain Based Workflow For Healthcare BCT SS V can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide showcases blockchain based workflow implemented for effectively sharing, processing and managing data without jeopardizing its security and privacy. Key components of the workflow include Healthcare raw data, blockchain technology, healthcare applications and stakeholders.

How Blockchain Is Reshaping HIPAA Compliance In Blockchain Based Healthcare BCT SS V
This slide mentions how compliance with Health Insurance Portability and Accountability Act HIPAA helps in ensuring patient data privacy. It includes secured storage of health data, control over data access, data integrity and interoperability. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download How Blockchain Is Reshaping HIPAA Compliance In Blockchain Based Healthcare BCT SS V from Slidegeeks and deliver a wonderful presentation. This slide mentions how compliance with Health Insurance Portability and Accountability Act HIPAA helps in ensuring patient data privacy. It includes secured storage of health data, control over data access, data integrity and interoperability.

Deployment Of Cloud Project Management Model Strategies For Success In Digital
This slide showcases deployment of cloud project management model. It provides information about public, private, hybrid, setup, data security, data control, privacy, scalability, integration, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Deployment Of Cloud Project Management Model Strategies For Success In Digital. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Deployment Of Cloud Project Management Model Strategies For Success In Digital today and make your presentation stand out from the rest This slide showcases deployment of cloud project management model. It provides information about public, private, hybrid, setup, data security, data control, privacy, scalability, integration, etc.

The Digital Project Managers Deployment Of Cloud Project Management Model
This slide showcases deployment of cloud project management model. It provides information about public, private, hybrid, setup, data security, data control, privacy, scalability, integration, etc. If you are looking for a format to display your unique thoughts, then the professionally designed The Digital Project Managers Deployment Of Cloud Project Management Model is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download The Digital Project Managers Deployment Of Cloud Project Management Model and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide showcases deployment of cloud project management model. It provides information about public, private, hybrid, setup, data security, data control, privacy, scalability, integration, etc.
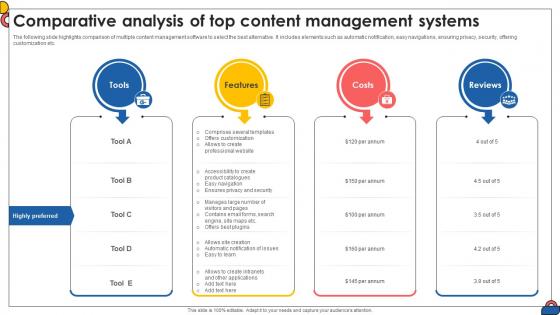
Comparative Analysis Of Top Content Management Comprehensive Guide To Implement Strategy SS V
The following slide highlights comparison of multiple content management software to select the best alternative. It includes elements such as automatic notification, easy navigations, ensuring privacy, security, offering customization etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Comparative Analysis Of Top Content Management Comprehensive Guide To Implement Strategy SS V a try. Our experts have put a lot of knowledge and effort into creating this impeccable Comparative Analysis Of Top Content Management Comprehensive Guide To Implement Strategy SS V. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today The following slide highlights comparison of multiple content management software to select the best alternative. It includes elements such as automatic notification, easy navigations, ensuring privacy, security, offering customization etc.

Deployment Of Cloud Project Management Model Digital Transformation In Project Management
This slide showcases deployment of cloud project management model. It provides information about public, private, hybrid, setup, data security, data control, privacy, scalability, integration, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Deployment Of Cloud Project Management Model Digital Transformation In Project Management. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Deployment Of Cloud Project Management Model Digital Transformation In Project Management today and make your presentation stand out from the rest This slide showcases deployment of cloud project management model. It provides information about public, private, hybrid, setup, data security, data control, privacy, scalability, integration, etc.

Growth Restraints Of Product Analytics Market Driving Business Success Integrating Product
This slide outlines major growth restraints that may hinder increased use of product analytics to boost sales. It covers arguments such as privacy and security issues, data integration from silos and lack of skilled professionals Welcome to our selection of the Growth Restraints Of Product Analytics Market Driving Business Success Integrating Product. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide outlines major growth restraints that may hinder increased use of product analytics to boost sales. It covers arguments such as privacy and security issues, data integration from silos and lack of skilled professionals

Digital Project Management Strategies Deployment Of Cloud Project Management Model
This slide showcases deployment of cloud project management model. It provides information about public, private, hybrid, setup, data security, data control, privacy, scalability, integration, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Digital Project Management Strategies Deployment Of Cloud Project Management Model. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Digital Project Management Strategies Deployment Of Cloud Project Management Model today and make your presentation stand out from the rest This slide showcases deployment of cloud project management model. It provides information about public, private, hybrid, setup, data security, data control, privacy, scalability, integration, etc.
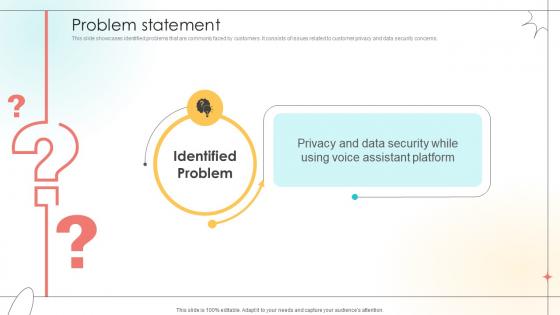
Problem Statement Open Source Solution Investor Funding Elevator Pitch Deck
This slide showcases identified problems that are commonly faced by customers. It consists of issues related to customer privacy and data security concerns. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Problem Statement Open Source Solution Investor Funding Elevator Pitch Deck was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Problem Statement Open Source Solution Investor Funding Elevator Pitch Deck. This slide showcases identified problems that are commonly faced by customers. It consists of issues related to customer privacy and data security concerns.

IoT Device Management Fundamentals Challenges Associated With IoT Devices Adoption IoT Ss V
This slide highlights challenges related to IoT medical devices. Some of the challenges include privacy and security, multiple devices integration, overloading, and cost of devices. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than IoT Device Management Fundamentals Challenges Associated With IoT Devices Adoption IoT SS V. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab IoT Device Management Fundamentals Challenges Associated With IoT Devices Adoption IoT SS V today and make your presentation stand out from the rest This slide highlights challenges related to IoT medical devices. Some of the challenges include privacy and security, multiple devices integration, overloading, and cost of devices.
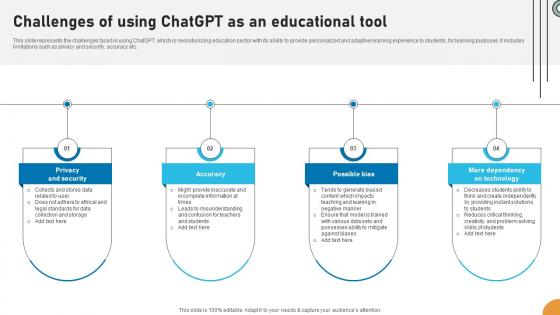
Challenges Of Using ChatGPT As An Applications Of ChatGPT In Education ChatGPT SS V
This slide represents the challenges faced in using ChatGPT, which is revolutionizing education sector with its ability to provide personalized and adaptive learning experience to students, for learning purposes. It includes limitations such as privacy and security, accuracy etc. Want to ace your presentation in front of a live audience Our Challenges Of Using ChatGPT As An Applications Of ChatGPT In Education ChatGPT SS V can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide represents the challenges faced in using ChatGPT, which is revolutionizing education sector with its ability to provide personalized and adaptive learning experience to students, for learning purposes. It includes limitations such as privacy and security, accuracy etc.
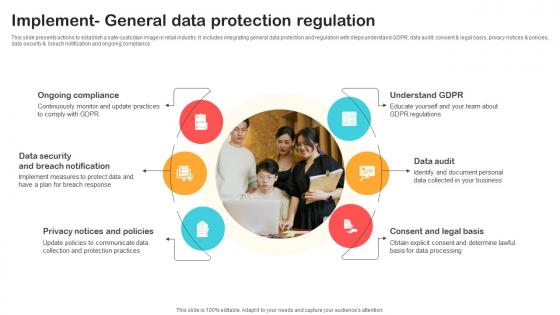
Implement General Data Protection Regulation Optimizing Retail Operations With Digital DT SS V
This slide presents actions to establish a safe-custodian image in retail industry. It includes integrating general data protection and regulation with steps understand GDPR, data audit, consent and legal basis, privacy notices and policies, data security and breach notification and ongoing compliance. Find a pre-designed and impeccable Implement General Data Protection Regulation Optimizing Retail Operations With Digital DT SS V. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide presents actions to establish a safe-custodian image in retail industry. It includes integrating general data protection and regulation with steps understand GDPR, data audit, consent and legal basis, privacy notices and policies, data security and breach notification and ongoing compliance.

Comprehensive Look At Blockchain Challenges Of Blockchain Integration BCT SS V
This slide mentions the various challenges faced in integrating blockchain technology in cybersecurity and their corresponding benefits of integration. Key challenges evaluated include scalability, interoperability, privacy, regulatory and security risks. Find highly impressive Comprehensive Look At Blockchain Challenges Of Blockchain Integration BCT SS V on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Comprehensive Look At Blockchain Challenges Of Blockchain Integration BCT SS V for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide mentions the various challenges faced in integrating blockchain technology in cybersecurity and their corresponding benefits of integration. Key challenges evaluated include scalability, interoperability, privacy, regulatory and security risks.

IoT Solutions For Oil IoT Implementation Challenges In Oil And Gas Industry IoT SS V
This slide discusses internet of things implementation challenges with solutions to ensure successful implementation. It includes challenges such as data security and privacy, integration issues, data overload, scalability and maintenance, etc. Explore a selection of the finest IoT Solutions For Oil IoT Implementation Challenges In Oil And Gas Industry IoT SS V here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our IoT Solutions For Oil IoT Implementation Challenges In Oil And Gas Industry IoT SS V to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide discusses internet of things implementation challenges with solutions to ensure successful implementation. It includes challenges such as data security and privacy, integration issues, data overload, scalability and maintenance, etc.
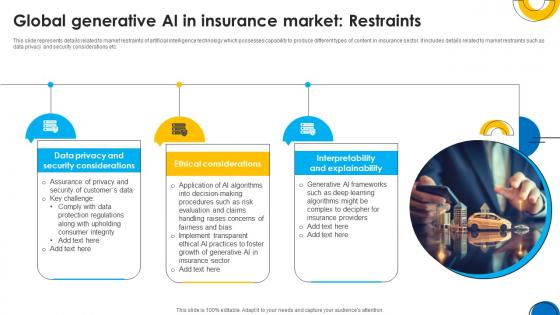
A101 Implementing ChatGpt In Insurance Global Generative Ai In Insurance ChatGpt SS V
This slide represents details related to market restraints of artificial intelligence technology which possesses capability to produce different types of content in insurance sector. It includes details related to market restraints such as data privacy and security considerations etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate A101 Implementing ChatGpt In Insurance Global Generative Ai In Insurance ChatGpt SS V for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide represents details related to market restraints of artificial intelligence technology which possesses capability to produce different types of content in insurance sector. It includes details related to market restraints such as data privacy and security considerations etc.

Implement General Data Protection Regulation DT SS V
This slide presents actions to establish a safe-custodian image in retail industry. It includes integrating general data protection and regulation with steps understand GDPR, data audit, consent and legal basis, privacy notices and policies, data security and breach notification and ongoing compliance. Find a pre-designed and impeccable Implement General Data Protection Regulation DT SS V. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide presents actions to establish a safe-custodian image in retail industry. It includes integrating general data protection and regulation with steps understand GDPR, data audit, consent and legal basis, privacy notices and policies, data security and breach notification and ongoing compliance.


 Continue with Email
Continue with Email

 Home
Home


































