lock
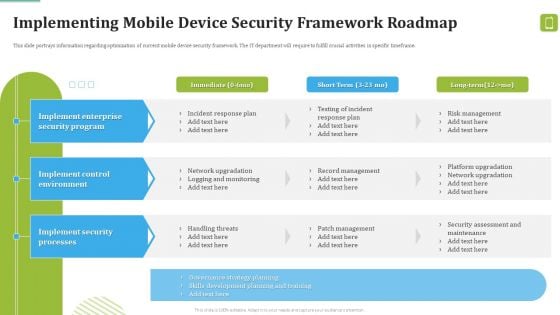
MDM Strategies At Office Implementing Mobile Device Security Framework Roadmap Rules PDF
This slide portrays information regarding optimization of current mobile device security framework. The IT department will require to fulfill crucial activities in specific timeframe. Deliver an awe inspiring pitch with this creative MDM Strategies At Office Implementing Mobile Device Security Framework Roadmap Rules PDF bundle. Topics like Implement Enterprise, Security Program, Implement Control can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

CRM System Deployment Plan Implementation Steps Enable Data Security Designs PDF
This slide covers two ways of enabling data security in CRM systems. It includes options such as IP restrictions and two-factor authentication. Deliver and pitch your topic in the best possible manner with this CRM System Deployment Plan Implementation Steps Enable Data Security Designs PDF. Use them to share invaluable insights on Security And Compliance, SAML Authentication, Data Subject Requests and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
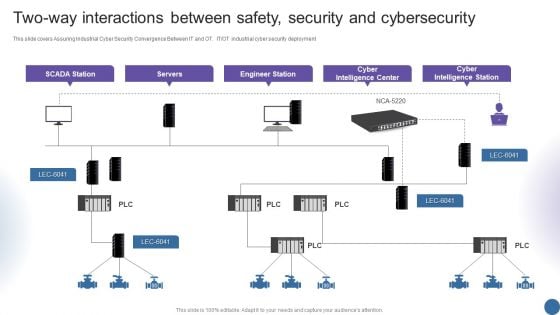
Two Way Interactions Between Safety Security And Cybersecurity Managing Organizational Transformation Summary PDF
This slide covers Assuring Industrial Cyber Security Convergence Between IT and OT. IT OT industrial cyber security deployment. Deliver an awe inspiring pitch with this creative Two Way Interactions Between Safety Security And Cybersecurity Managing Organizational Transformation Summary PDF bundle. Topics like Servers, Engineer Station, Intelligence Center can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
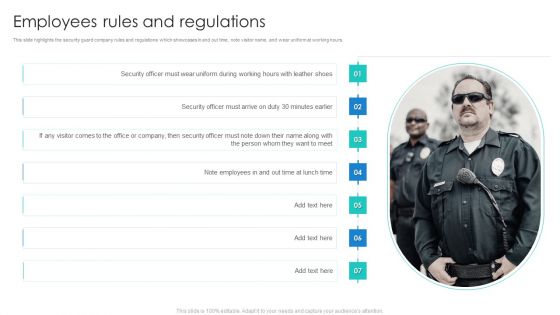
Manpower Corporate Security Business Profile Employees Rules And Regulations Formats PDF
This slide highlights the security guard company rules and regulations which showcases In and out time, note visitor name, and wear uniform at working hours. Deliver an awe inspiring pitch with this creative Manpower Corporate Security Business Profile Employees Rules And Regulations Formats PDF bundle. Topics like Security, Employees Rules And Regulations can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Agenda IT Security Automation Tools Integration Ppt Summary Design Templates PDF
This is a Agenda IT Security Automation Tools Integration Ppt Summary Design Templates PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like IT Environment, Security Processes, Security Automation. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Automation Tools Integration Table Of Contents Ppt Ideas Graphic Tips PDF
This is a IT Security Automation Tools Integration Table Of Contents Ppt Ideas Graphic Tips PDF template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Ineffective Security System, Security Automation, Architecture And Importance. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
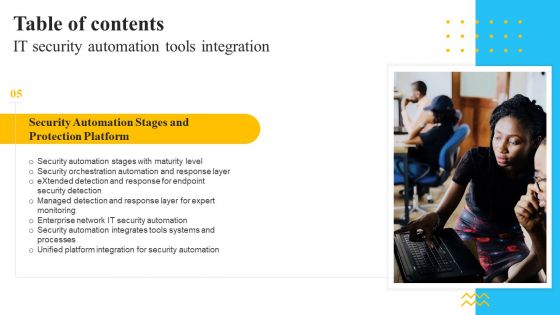
Table Of Contents IT Security Automation Tools Integration Ppt Gallery Aids PDF
Presenting Table Of Contents IT Security Automation Tools Integration Ppt Gallery Aids PDF to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like Security Automation Stages, Protection Platform, Security Orchestration. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
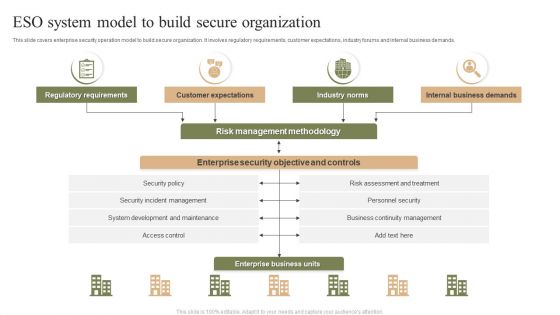
ESO System Model To Build Secure Organization Ppt PowerPoint Presentation File Layout PDF
This slide covers enterprise security operation model to build secure organization. It involves regulatory requirements, customer expectations, industry forums and internal business demands. Showcasing this set of slides titled ESO System Model To Build Secure Organization Ppt PowerPoint Presentation File Layout PDF. The topics addressed in these templates are Customer Expectations, Industry Norms, Internal Business Demands. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Quarterly Comparison Of Security For Cloud Based Systems Threats Infographics PDF
This slide shows the various types of cloud security threats occurred during four quarters. It includes phishing, malware, IoT and password attacks. Pitch your topic with ease and precision using this Quarterly Comparison Of Security For Cloud Based Systems Threats Infographics PDF. This layout presents information on Quarterly Comparison Of Security, Cloud Based Systems Threats. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
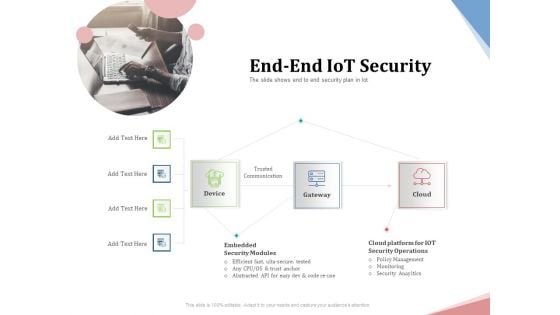
Machine To Machine Communication Outline End End Iot Security Ppt Visual Aids Styles PDF
The slide shows end to end security plan in Iot. This is a machine to machine communication outline end end iot security ppt visual aids styles pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like trusted, communication, gateway, cloud, device, embedded security modules, cloud platform for iot security operations. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Intelligence Framework For Application Consumption Growing Cyber Security Issues Ppt File Shapes PDF
The slide provides the major cyber security issues Unprecedented Attacks, Cyber Espionage, and Data Theft along with the split of total information security incidents by the type of incident. Presenting cloud intelligence framework for application consumption growing cyber security issues ppt file shapes pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like mobile devices, security plans, organizations, cloud technologies, loss or theft of equipment. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Companys Data Safety Recognition Security Awareness Tracking Kpis Culture Mockup PDF
This slide covers the key performance for security awareness training including compliance, security culture and incident reduction. This is a companys data safety recognition security awareness tracking kpis culture mockup pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like compliance, incident reduction, security culture. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
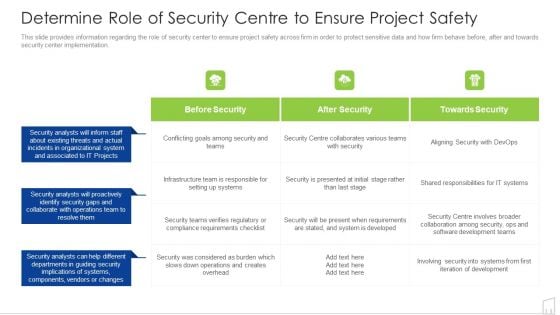
Determine Role Of Security Centre To Ensure Project Safety Ppt Professional Example PDF
This slide provides information regarding the role of security center to ensure project safety across firm in order to protect sensitive data and how firm behave before, after and towards security center implementation. Deliver an awe inspiring pitch with this creative determine role of security centre to ensure project safety ppt professional example pdf bundle. Topics like security, system, developed, requirements, teams can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Management Plan Steps In Detail Adopting Access Controls Download PDF
This slide provides information about the fifth step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. Adopting Access Controls. Deliver an awe inspiring pitch with this creative security management plan steps in detail adopting access controls download pdf bundle. Topics like logical access controls, control implementation costs, physical access controls can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
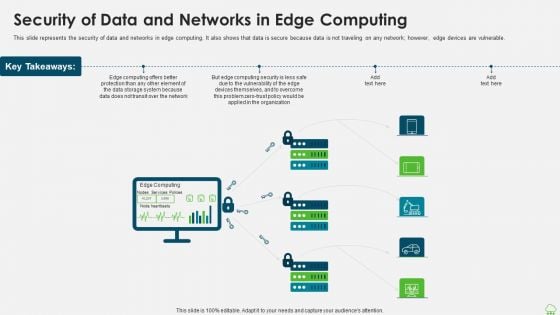
Distributed Computing IT Security Of Data And Networks In Edge Computing Themes PDF
This slide represents the security of data and networks in edge computing. It also shows that data is secure because data is not traveling on any network however, edge devices are vulnerable. Presenting distributed computing it security of data and networks in edge computing themes pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like organization, data storage, computing security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

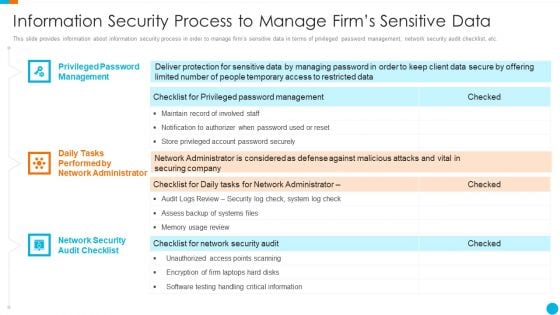
Major Techniques For Project Safety IT Information Security Process To Manage Firms Sensitive Data Designs PDF
This slide provides information about information security process in order to manage firms sensitive data in terms of privileged password management, network security audit checklist, etc. Deliver and pitch your topic in the best possible manner with this major techniques for project safety it information security process to manage firms sensitive data designs pdf. Use them to share invaluable insights on privileged password management, daily tasks performed by network administrator, network security audit checklist and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Upgrading Total Project Safety IT Information Security Process To Manage Firms Sensitive Data Structure PDF
This slide provides information about information security process in order to manage firms sensitive data in terms of privileged password management, network security audit checklist, etc. Presenting upgrading total project safety it information security process to manage firms sensitive data structure pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like privileged password management, daily tasks performed by network administrator, network security audit checklist. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security Management Plan Steps In Detail Evaluating Information Processing Assets Template PDF
This slide provides information about the second step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. Evaluating Information Processing Assets. Deliver an awe inspiring pitch with this creative security management plan steps in detail evaluating information processing assets template pdf bundle. Topics like information, network infrastructure, services, customer information can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Management Plan Steps In Detail Risk Assessment And Analysis Introduction PDF
This slide provides information about the third step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Risk Assessment and Analysis. Deliver an awe inspiring pitch with this creative security management plan steps in detail risk assessment and analysis introduction pdf bundle. Topics like information, system, risks, measures can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Continuous Development Evaluation Plan Eliminate Cyber Attacks Current Security Monitoring Infographics PDF
This slide shows some of the current Cyber Security Monitoring Key Performance Indicators of the company prior to the measures taken by the company to mitigate security monitoring issues and implementing an advanced security monitoring plan. Deliver an awe inspiring pitch with this creative continuous development evaluation plan eliminate cyber attacks current security monitoring infographics pdf bundle. Topics like monitoring, service, parameters can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
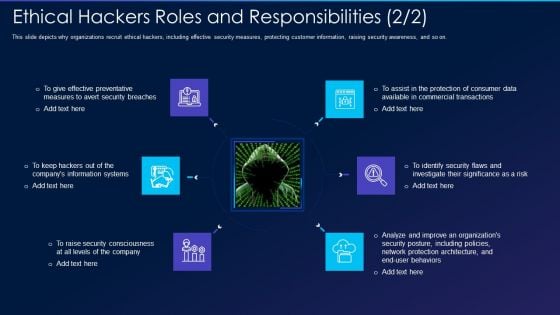
Cyber Exploitation IT Ethical Hackers Roles And Responsibilities Security Inspiration PDF
This slide depicts why organizations recruit ethical hackers, including effective security measures, protecting customer information, raising security awareness, and so on. Presenting cyber exploitation it ethical hackers roles and responsibilities security inspiration pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like security, organizations, analyze, measures. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
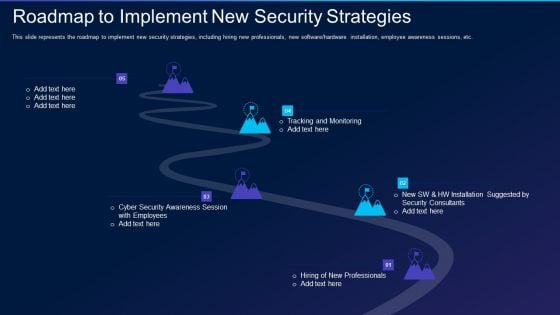
Cyber Exploitation IT Roadmap To Implement New Security Strategies Information PDF
This slide represents the roadmap to implement new security strategies, including hiring new professionals, new software or hardware installation, employee awareness sessions, etc. This is a cyber exploitation it roadmap to implement new security strategies information pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like tracking and monitoring, security consultants, cyber security awareness. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cybersecurity Managing Electronic Information Security 60 Days Plan Ppt Ideas Graphics Tutorials PDF
This slide represents the plan for 60 days after implementing the cyber security model in the organization. This slide represents the plan for 60 days after implementing the cyber security model in the organization. Deliver an awe inspiring pitch with this creative cybersecurity managing electronic information security 60 days plan ppt ideas graphics tutorials pdf bundle. Topics like measured, security, team, organization can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Techniques And Strategies To Reduce Security Management Risks Measures And Ways To Mitigate Clipart PDF
This slide provides information about the ways and measures through which the company and IT security managers can overcome the problems and issues related to Security Management.Deliver and pitch your topic in the best possible manner with this techniques and strategies to reduce security management risks measures and ways to mitigate clipart pdf Use them to share invaluable insights on potential insider threats, external security breaches, centric breaches and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Devops Engineer Capabilities Software Security Skills Ppt Slides Graphics Template PDF
This slide provides the glimpse about the software security skills such as security training, code analysis, change management, compliance monitoring, threat investigation, vulnerability management, etc. This is a devops engineer capabilities software security skills ppt slides graphics template pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like vulnerability management, threat investigation, compliance monitoring, security training, code analysis. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Our Strategies To Secure Network Load Balancer Ppt Outline Topics PDF
This slide represents the strategies to secure the network load balancer by protecting servers at the physical level, controlling network traffic, security app features, and more. Presenting our strategies to secure network load balancer ppt outline topics pdf to provide visual cues and insights. Share and navigate important information on nine stages that need your due attention. This template can be used to pitch topics like our strategies to secure network load balancer. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
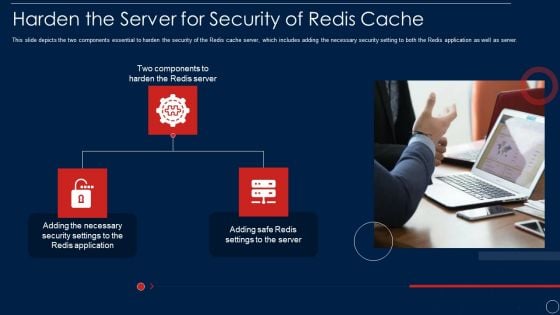
Redis Cache Data Structure IT Harden The Server For Security Of Redis Cache Template PDF
This slide depicts the two components essential to harden the security of the Redis cache server, which includes adding the necessary security setting to both the Redis application as well as server. This is a redis cache data structure it harden the server for security of redis cache template pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like harden the server for security of redis cache. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
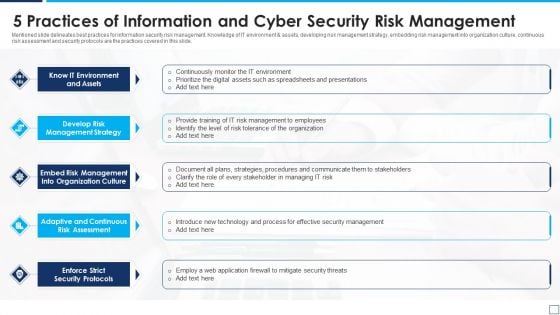
5 Practices Of Information And Cyber Security Risk Management Graphics PDF
Mentioned slide delineates best practices for information security risk management. Knowledge of IT environment and assets, developing risk management strategy, embedding risk management into organization culture, continuous risk assessment and security protocols are the practices covered in this slide. Presenting 5 practices of information and cyber security risk management graphics pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including know it environment and assets, develop risk management strategy, enforce strict security protocols. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
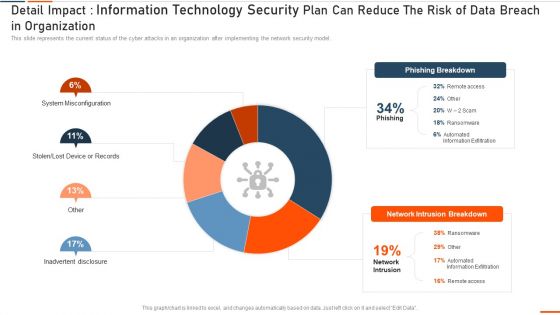
Detail Impact Information Technology Security Plan Can Reduce Ppt Show Slide Download PDF
This slide represents the current status of the cyber attacks in an organization after implementing the network security model. Deliver an awe inspiring pitch with this creative it security detail impact detail impact information technology security plan can reduce ppt show slide download pdf bundle. Topics like detail impact information technology security plan can reduce the risk of data breach in organization can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
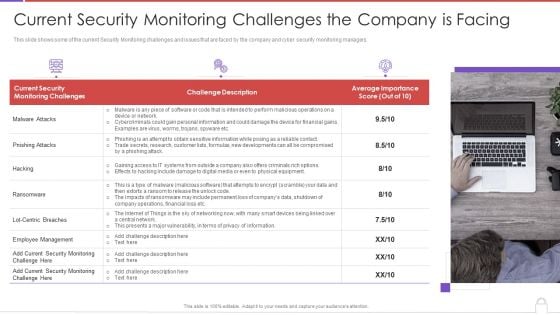
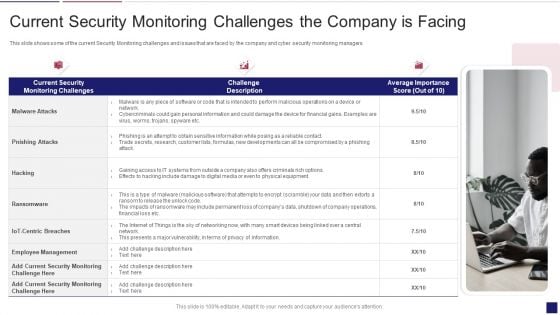
Methods To Develop Advanced Current Security Monitoring Challenges The Company Is Facing Professional PDF
This slide shows some of the current Security Monitoring challenges and issues that are faced by the company and cyber security monitoring managers. This is a methods to develop advanced current security monitoring challenges the company is facing professional pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like current security, monitoring challenges, challenge description, average importance score. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Structure PDF
This slide provides information about some of the best security monitoring tools that are available with the security monitoring manager and what tool is selected by the security monitoring manager based on tool implementation costs, tool implementation time etc. Deliver and pitch your topic in the best possible manner with this modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring structure pdf. Use them to share invaluable insights on cybersecurity monitoring tools to be implemented and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Data Safety Initiatives Key Security Controls To Be Addressed In The Program Summary PDF
Purpose of this slide is to provide information about key security controls that are to be addressed in companys information security program. Security controls covered are user application hardening, daily backups and patch applications. Deliver an awe inspiring pitch with this creative data safety initiatives key security controls to be addressed in the program summary pdf bundle. Topics like prevents attacks, limits extent of attacks, data recovery can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
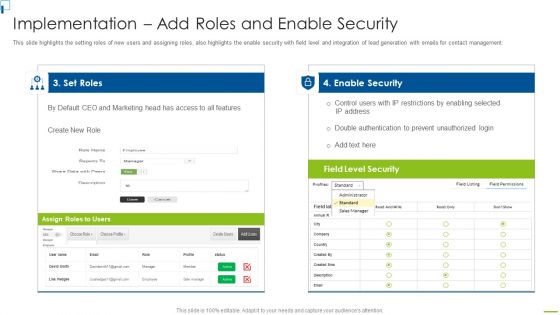
Designing And Deployment Implementation Add Roles And Enable Security Sample PDF
This slide highlights the setting roles of new users and assigning roles, also highlights the enable security with field level and integration of lead generation with emails for contact management. Deliver and pitch your topic in the best possible manner with this designing and deployment implementation add roles and enable security sample pdf. Use them to share invaluable insights on set roles, enable security, assign roles to users, field level security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
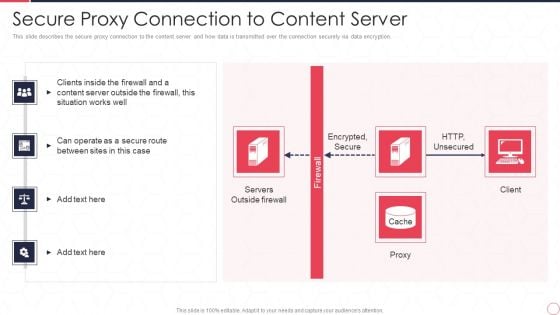
Reverse Proxy Server IT Secure Proxy Connection To Content Server Ppt Gallery Brochure PDF
This slide describes the secure proxy connection to the content server and how data is transmitted over the connection securely via data encryption. Presenting reverse proxy server it secure proxy connection to content server ppt gallery brochure pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like encrypted, secure, http, unsecured, servers, outside firewall, proxy, client. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Security Kpis To Measure Phishing Scams And Attacks Topics PDF
Mentioned slide showcases 5 cyber security KPI which can be used by organization to measure phishing attacks. The KPIs mentioned in the slide are intrusion attempts, security incidents, mean time to detect MTTD, etc. Showcasing this set of slides titled cyber security kpis to measure phishing scams and attacks topics pdf. The topics addressed in these templates are cyber security kpis to measure phishing scams and attacks. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Risk Management Model For Data Security Roles And Responsibilities For Managing Information Professional PDF
Following slide demonstrates various roles and responsibilities for information security management. Responsibilities covered are security policy development, asset classification and security framework development. This is a Risk Management Model For Data Security Roles And Responsibilities For Managing Information Professional PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Role, Position, Responsibility, Chief Information Officer, Information Management Manager. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
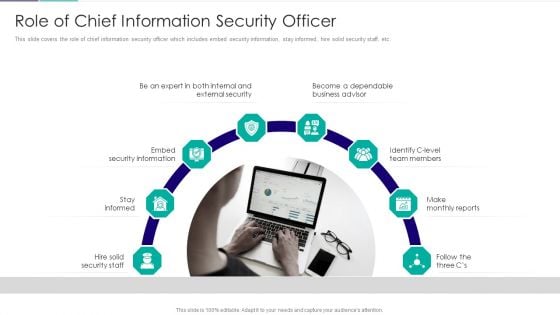
Role Of Technical Competence In Organizational Role Of Chief Information Security Officer Introduction PDF
This slide covers the role of chief information security officer which includes embed security information, stay informed, hire solid security staff, etc.This is a Role Of Technical Competence In Organizational Role Of Chief Information Security Officer Introduction PDF template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Become A Dependable, Identify C Level Team Members, Make Monthly Reports You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
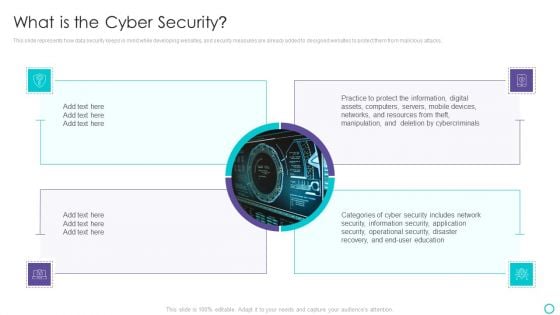
Website Designing And Development Service What Is The Cyber Security Diagrams PDF
This slide represents how data security keeps in mind while developing websites, and security measures are already added to designed websites to protect them from malicious attacks.Presenting Website Designing And Development Service What Is The Cyber Security Diagrams PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Practice To Protect, Information Digital, Operational Security In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Website Designing And Development Service Security Web Development Technique Themes PDF
This slide represents the security development and how developers act as ethical hackers to prevent malicious attacks and reveal their vulnerabilities.This is a Website Designing And Development Service Security Web Development Technique Themes PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Network Security, Content Security, Loopholes Or Shortcomings You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Smart Home Security Solutions Company Profile Company Journey From 2010 To 2022 Introduction PDF
This slide highlights the security company timeline which showcases company started operation in 2010, add smart home services in 2012, acquired bluestone security in 2013. Presenting Smart Home Security Solutions Company Profile Company Journey From 2010 To 2022 Introduction PDF to provide visual cues and insights. Share and navigate important information on ten stages that need your due attention. This template can be used to pitch topics like Smart Home Services, Acquired Bluestone Security, System Product Catalogue, Launched Different CCTV, 2010 To 2022. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Smart Home Security Solutions Company Profile Executive Leadership And Management Team Themes PDF
This slide highlights the security company leadership and management team which includes president and CEO, executive vice president of finance, EVP home security, chief administration officer. This is a Smart Home Security Solutions Company Profile Executive Leadership And Management Team Themes PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Executive Leadership Management, Team Business Security, Financial Management Services. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Security Management Roadmap With Program Maturity And Cost Ppt PowerPoint Presentation File Graphic Tips PDF
This slide covers quarterly cyber security planning roadmap by management to reduce risk with program maturity and cost .It consist secure , defend, contain, manage and anticipate. Persuade your audience using this Cyber Security Management Roadmap With Program Maturity And Cost Ppt PowerPoint Presentation File Graphic Tips PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Cyber Security Management, Level Risk Reduction. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
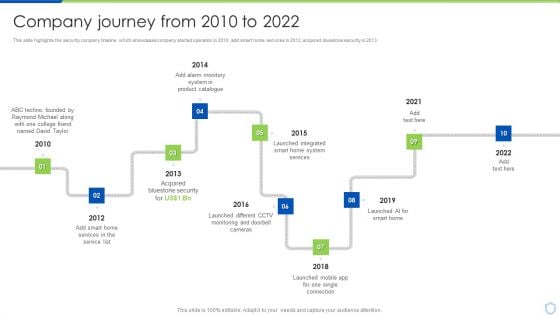
Security And Surveillance Company Profile Company Journey From 2010 To 2022 Pictures PDF
This slide highlights the security company timeline which showcases company started operation in 2010, add smart home services in 2012, acquired bluestone security in 2013. This is a Security And Surveillance Company Profile Company Journey From 2010 To 2022 Pictures PDF template with various stages. Focus and dispense information on ten stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Raymond Michael, Product Catalogue, Bluestone Security . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Camera System Company Profile Executive Leadership And Management Team Designs PDF
This slide highlights the security company leadership and management team which includes president CEO, executive vice president of finance, EVP home security, chief administration officer. This is a Security Camera System Company Profile Executive Leadership And Management Team Designs PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Business Security, Southern University, Management Services. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Hacker Ethical Hacker And Why We Need Ethical Hacker Guidelines PDF
This slide depicts the reasons to describe the need for ethical hacking, including identification and correction of security flaws, aid in development quality control, and evaluation of the companys security regulatory compliance.Presenting IT Security Hacker Ethical Hacker And Why We Need Ethical Hacker Guidelines PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Systems, Applications, Correcting Security, Regulatory Compliance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Security Hacker Techniques To Keep Our Website Protected Guidelines PDF
This slide represents the techniques to protect our website from hacking and cyber attacks, including enhanced access controls, increased network security, installation of security software, etc.This is a IT Security Hacker Techniques To Keep Our Website Protected Guidelines PDF template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Software, Enhance Access, Update Everything. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Impact Saas Cloud Security Practices In Business Growth Ppt PowerPoint Presentation Gallery Elements PDF
The following slide showcases the impact of software as a service SaaS security in developing business. It includes key elements such as scalability, security, customization, maintenance, availability, IT cost etc. Showcasing this set of slides titled Impact Saas Cloud Security Practices In Business Growth Ppt PowerPoint Presentation Gallery Elements PDF. The topics addressed in these templates are Scalability, Security, Customization, Maintenance. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Major Saas Cloud Security Challenges For IT Department Ppt PowerPoint Presentation Gallery Design Templates PDF
The following slide highlights some SaaS security challenges faced by IT team to plan mitigation actions. It mainly includes file security, insider threat, privilege access etc. Presenting Major Saas Cloud Security Challenges For It Department Ppt PowerPoint Presentation Gallery Design Templates PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including File Security, Insider Threat, Imposing Minimum, Privilege Access. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
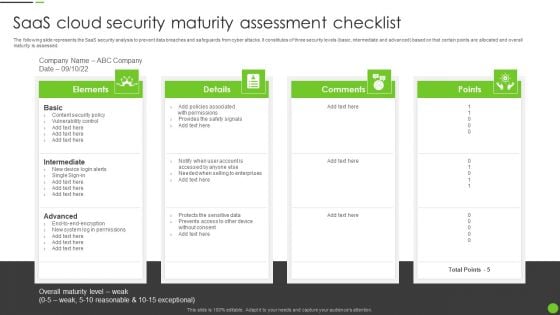
Saas Cloud Security Maturity Assessment Checklist Ppt PowerPoint Presentation File Portfolio PDF
The following slide represents the SaaS security analysis to prevent data breaches and safeguards from cyber attacks. It constitutes of three security levels basic, intermediate and advanced based on that certain points are allocated and overall maturity is assessed. Persuade your audience using this Saas Cloud Security Maturity Assessment Checklist Ppt PowerPoint Presentation File Portfolio PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Intermediate, Advanced, Content Security Policy. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
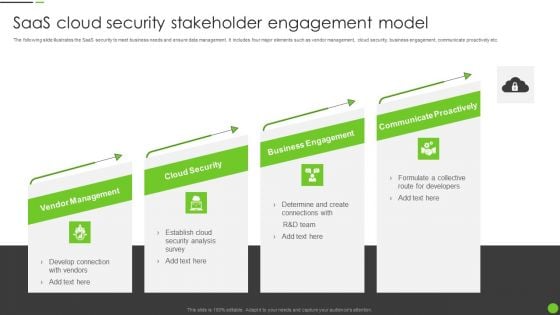
Saas Cloud Security Stakeholder Engagement Model Ppt PowerPoint Presentation Gallery Design Ideas PDF
The following slide illustrates the SaaS security to meet business needs and ensure data management. It includes four major elements such as vendor management, cloud security, business engagement, communicate proactively etc. Presenting Saas Cloud Security Stakeholder Engagement Model Ppt PowerPoint Presentation Gallery Design Ideas PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Vendor Management, Cloud Security, Business Engagement, Communicate Proactively. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
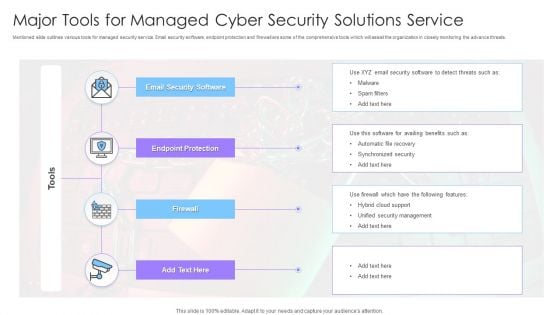
Major Tools For Managed Cyber Security Solutions Service Ppt Infographics Graphics Tutorials PDF
Mentioned slide outlines various tools for managed security service. Email security software, endpoint protection and firewall are some of the comprehensive tools which will assist the organization in closely monitoring the advance threats. Showcasing this set of slides titled Major Tools For Managed Cyber Security Solutions Service Ppt Infographics Graphics Tutorials PDF. The topics addressed in these templates are Endpoint Protection, Firewall, Email Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
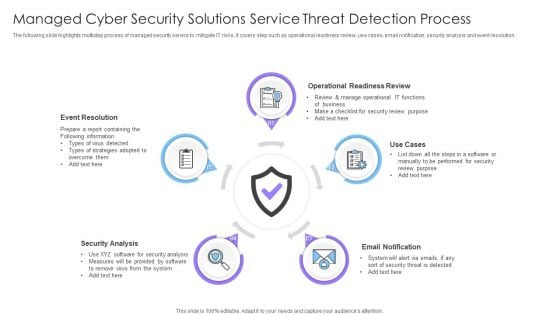
Managed Cyber Security Solutions Service Threat Detection Process Ppt Portfolio Pictures PDF
The following slide highlights multistep process of managed security service to mitigate IT risks. It covers step such as operational readiness review, use cases, email notification, security analysis and event resolution. Presenting Managed Cyber Security Solutions Service Threat Detection Process Ppt Portfolio Pictures PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Event Resolution, Security Analysis, Use Cases, Operational Readiness Review. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Multiple Types Of Managed Cyber Security Solutions Services Ppt Styles Layout Ideas PDF
This slide exhibits the different types of managed security services such as risk management, virtual CISO and security awareness education. It also provides information about the multiple offerings of each service. Persuade your audience using this Multiple Types Of Managed Cyber Security Solutions Services Ppt Styles Layout Ideas PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Risk Management, Offerings, Security Awareness Education, Virtual CISO. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
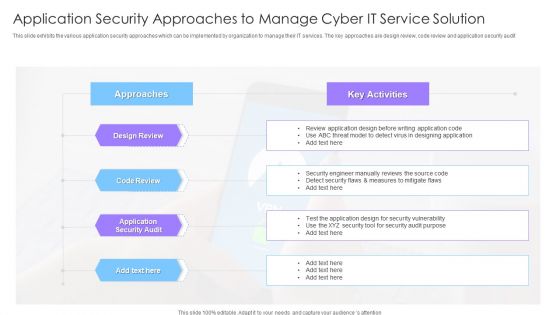
Application Security Approaches To Manage Cyber It Service Solution Ppt Styles Slide Portrait PDF
This slide exhibits the various application security approaches which can be implemented by organization to manage their IT services. The key approaches are design review, code review and application security audit Showcasing this set of slides titled Application Security Approaches To Manage Cyber It Service Solution Ppt Styles Slide Portrait PDF. The topics addressed in these templates are Design Review, Code Review, Approaches, Application Security Audit. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
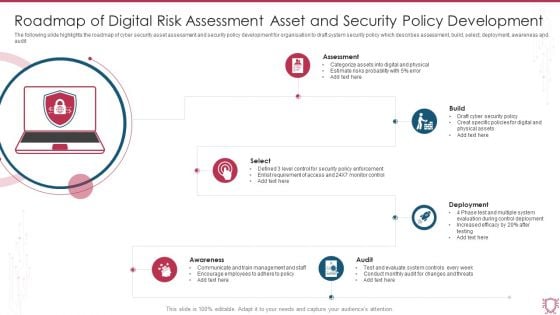
Roadmap Of Digital Risk Assessment Asset And Security Policy Development Sample PDF
The following slide highlights the roadmap of cyber security asset assessment and security policy development for organisation to draft system security policy which describes assessment, build, select, deployment, awareness and audit. Persuade your audience using this Roadmap Of Digital Risk Assessment Asset And Security Policy Development Sample PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Assessment, Build, Deployment, Select, Audit, Awareness. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
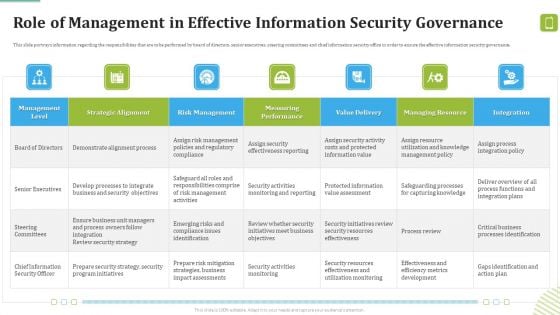
MDM Strategies At Office Role Of Management In Effective Information Security Governance Ideas PDF
This slide portrays information regarding the responsibilities that are to be performed by board of directors, senior executives, steering committees and chief information security office in order to ensure the effective information security governance. Deliver an awe inspiring pitch with this creative MDM Strategies At Office Role Of Management In Effective Information Security Governance Ideas PDF bundle. Topics like Demonstrate Alignment, Business Security, Program Initiatives can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
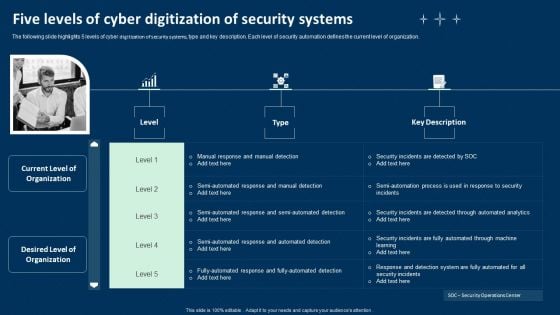
Five Levels Of Cyber Digitization Of Security Systems Ppt Infographics Graphics Tutorials PDF
The following slide highlights 5 levels of cyber digitization of security systems, type and key description. Each level of security automation defines the current level of organization. Presenting Five Levels Of Cyber Digitization Of Security Systems Ppt Infographics Graphics Tutorials PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Investigating Steps, Security Analysts, Determining Responsive Action. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Four Step Process Of Digitization Of Security Systems Ppt Icon Show PDF
The following slide highlights multistep process of digitization of security systems. The company can detect security breach after following steps such as investigating the steps of IT analyst, determining responsive action, eradication and closing the ticked. Presenting Four Step Process Of Digitization Of Security Systems Ppt Icon Show PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Investigating Steps, Security Analysts, Determining Responsive Action. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Multistep Digitization Of Security Systems Checklist Ppt Portfolio Example File PDF
The following slide highlights a comprehensive checklist for digitization of security systems. The checklist covers key points such as deciding the budget, selecting the right tools, deciding the tasks for automation etc. Presenting Multistep Digitization Of Security Systems Checklist Ppt Portfolio Example File PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Security Automation, Checklist, Security Automation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
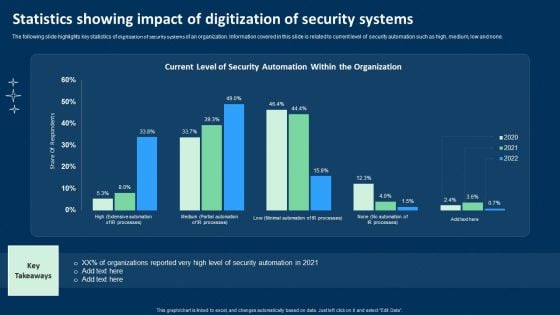
Statistics Showing Impact Of Digitization Of Security Systems Ppt Show Ideas PDF
The following slide highlights key statistics of digitization of security systems of an organization. Information covered in this slide is related to current level of security automation such as high, medium, low and none. Showcasing this set of slides titled Statistics Showing Impact Of Digitization Of Security Systems Ppt Show Ideas PDF. The topics addressed in these templates are Current Level, Security Automation, Organization. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.


 Continue with Email
Continue with Email

 Home
Home


































