Authentication
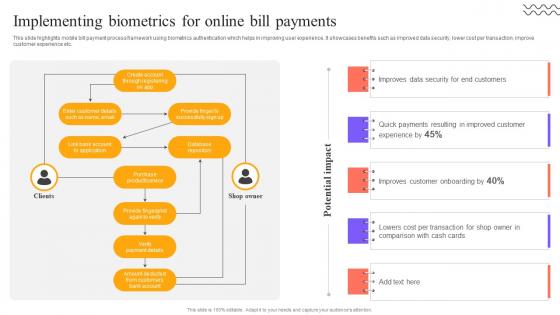
Digital Approach To Client Implementing Biometrics For Online Bill Payments
This slide highlights mobile bill payment process framework using biometrics authentication which helps in improving user experience. It showcases benefits such as improved data security, lower cost per transaction, improve customer experience etc. Take your projects to the next level with our ultimate collection of Digital Approach To Client Implementing Biometrics For Online Bill Payments. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest This slide highlights mobile bill payment process framework using biometrics authentication which helps in improving user experience. It showcases benefits such as improved data security, lower cost per transaction, improve customer experience etc.
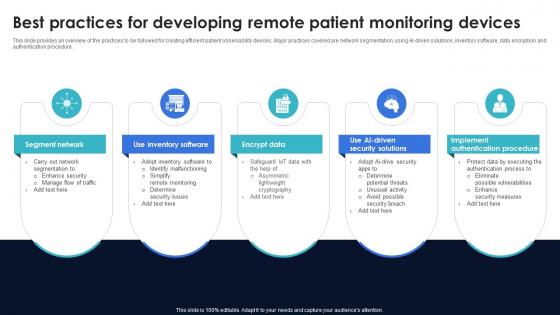
Optimization Of IoT Remote Monitoring Best Practices For Developing Remote Patient Monitoring IoT SS V
This slide provides an overview of the practices to be followed for creating efficient patient observability devices. Major practices covered are network segmentation, using AI-driven solutions, inventory software, data encryption and authentication procedure. Present like a pro with Optimization Of IoT Remote Monitoring Best Practices For Developing Remote Patient Monitoring IoT SS V. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide provides an overview of the practices to be followed for creating efficient patient observability devices. Major practices covered are network segmentation, using AI-driven solutions, inventory software, data encryption and authentication procedure.

AWS Amplify Amazon Web Services Key Features Application Areas Of Mobile Cloud Computing
The purpose of the mentioned slide is to showcase key components of AWS Amplify service provider for mobile cloud computing. It includes the backend as service, authentication and authorization, data storage and APIs, etc. Want to ace your presentation in front of a live audience Our AWS Amplify Amazon Web Services Key Features Application Areas Of Mobile Cloud Computing can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. The purpose of the mentioned slide is to showcase key components of AWS Amplify service provider for mobile cloud computing. It includes the backend as service, authentication and authorization, data storage and APIs, etc.
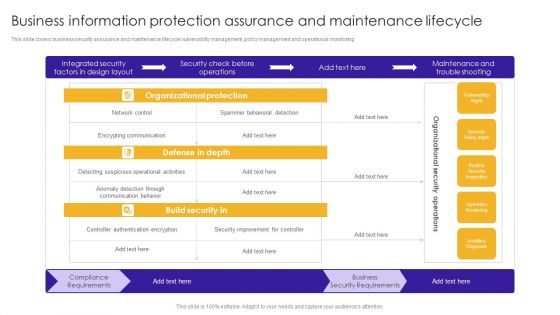
Business Information Protection Assurance And Maintenance Lifecycle Brochure PDF
This slide covers business security assurance and maintenance lifecycle vulnerability management ,policy management and operational monitoring.Showcasing this set of slides titled Business Information Protection Assurance And Maintenance Lifecycle Brochure PDF. The topics addressed in these templates are Encrypting Communication, Detecting Suspicious, Authentication Encryption. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cloud Security Best Practices Cloud Computing Security IT Ppt Portfolio Master Slide PDF
This slide defines the best practices of cloud security, including understanding cloud utilization and risk, protection of cloud, and responding to cloud protection issues. Deliver an awe inspiring pitch with this creative cloud security best practices cloud computing security it ppt portfolio master slide pdf bundle. Topics like cloud protection, cloud utilization and risk, authentication process, security policies can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
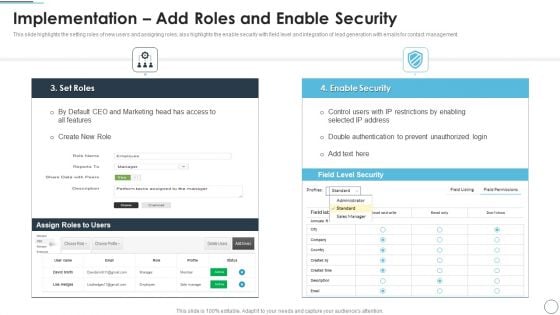
CRM Solutions Implementation Strategy Implementation Add Roles And Enable Security Information PDF
This slide highlights the setting roles of new users and assigning roles, also highlights the enable security with field level and integration of lead generation with emails for contact management.Deliver an awe inspiring pitch with this creative CRM Solutions Implementation Strategy Implementation Add Roles And Enable Security Information PDF bundle. Topics like Restrictions By Enabling, Prevent Unauthorized, Double Authentication can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Cyber Security Administration In Organization Addressing Indicators Associated To Insider Cyber Threats Themes PDF
This slide provides details regarding indicators associated to insider threats in terms of traits, demeanor and goals, etc. Deliver and pitch your topic in the best possible manner with this cyber security administration in organization addressing indicators associated to insider cyber threats themes pdf. Use them to share invaluable insights on unauthorized, privileged, measures, authentication and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Intelligent Infrastructure Tracking Intelligence Infrastructure Activities Dashboard Template PDF
This slide portrays information regarding tracking essential activities in intelligence infrastructure dashboard in terms of IT operations, security, business analytics, internet of things, etc. Deliver and pitch your topic in the best possible manner with this Intelligent Infrastructure Tracking Intelligence Infrastructure Activities Dashboard Template PDF. Use them to share invaluable insights on Application Delivery, IT Operations, Authentication and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
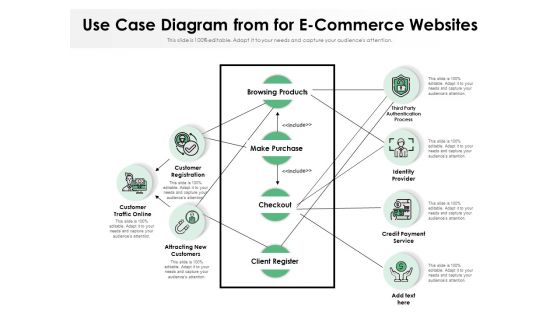
Business Case Flow Chart For Online Purchasing Process Ppt PowerPoint Presentation Infographics Display PDF
Presenting business case flow chart for online purchasing process ppt powerpoint presentation infographics display pdf to dispense important information. This template comprises seven stages. It also presents valuable insights into the topics including customer traffic online, customer registration, attracting new customers, browsing products, make purchase, checkout, client register, credit payment service, identity provider, third party authentication process. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
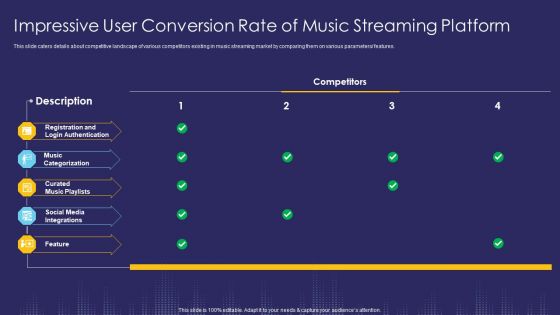
Impressive User Conversion Rate Of Music Streaming Platform Feature Ppt Model Slide Download PDF
This slide caters details about competitive landscape of various competitors existing in music streaming market by comparing them on various parameters or features. Deliver an awe inspiring pitch with this creative impressive user conversion rate of music streaming platform feature ppt model slide download pdf bundle. Topics like social media, authentication can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Mitigating Cybersecurity Threats And Vulnerabilities Addressing Indicators Associated Icons PDF
This slide provides details regarding indicators associated to insider threats in terms of traits, demeanor and goals, etc. Presenting mitigating cybersecurity threats and vulnerabilities addressing indicators associated icons pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like user accounts, authentication levels, data exfiltration. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
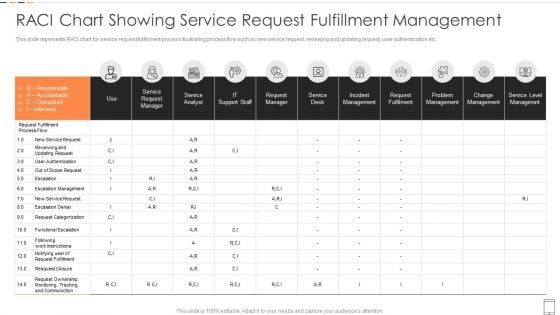
RACI Chart Showing Service Request Fulfillment Management Introduction PDF
This slide represents RACI chart for service request fulfillment process illustrating process flow such as new service request, reviewing and updating request, user authentication etc.Pitch your topic with ease and precision using this RACI Chart Showing Service Request Fulfillment Management Introduction PDF This layout presents information on Incident Management, Request Fulfilment, Problem Management It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
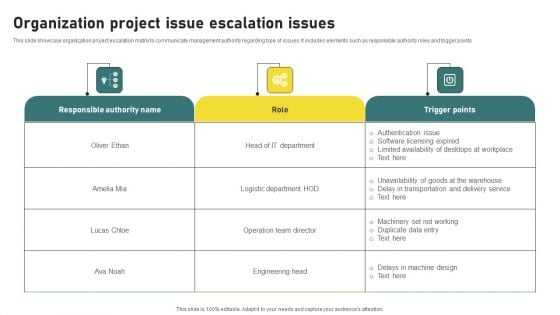
Organization Project Issue Escalation Issues Slides PDF
This slide showcase organization project escalation matrix to communicate management authority regarding type of issues. It includes elements such as responsible authority roles and trigger points. Pitch your topic with ease and precision using this Organization Project Issue Escalation Issues Slides PDF. This layout presents information on Operation Team Director, Authentication Issue. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
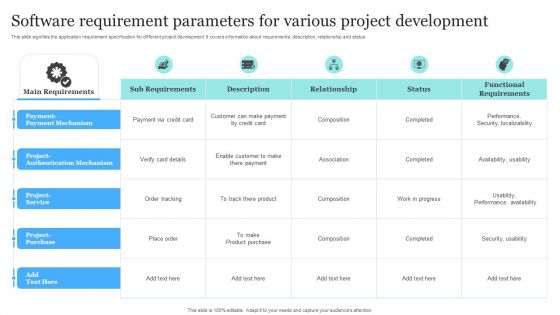
Software Requirement Parameters For Various Project Development Introduction PDF
This slide signifies the application requirement specification for different project development. It covers information about requirements, description, relationship and status. Pitch your topic with ease and precision using this Software Requirement Parameters For Various Project Development Introduction PDF. This layout presents information on Payment Payment Mechanism, Project Authentication Mechanism, Project Service, Project Purchase. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Bestinformation Technology Security And Data Security Practices Slides PDF
The following slide highlights the best practices to protect the business from security threats. It includes activities such as installing and upgrading protective software, adopting strong password policy, applying multi-layer authentication etc. Persuade your audience using this Bestinformation Technology Security And Data Security Practices Slides PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Adopt Strong Password Policy, Make Regular Backups, Resource Information. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
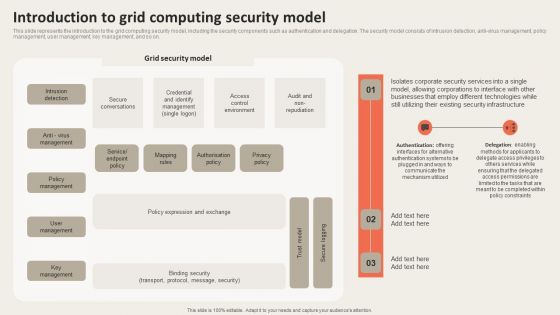
Grid Computing Applications Introduction To Grid Computing Security Model Rules PDF
This slide represents the introduction to the grid computing security model, including the security components such as authentication and delegation. The security model consists of intrusion detection, anti-virus management, policy management, user management, key management, and so on. Make sure to capture your audiences attention in your business displays with our gratis customizable Grid Computing Applications Introduction To Grid Computing Security Model Rules PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
Grid Computing For High Performance Solutions Introduction To Grid Computing Security Model Icons PDF
This slide represents the introduction to the grid computing security model, including the security components such as authentication and delegation. The security model consists of intrusion detection, anti-virus management, policy management, user management, key management, and so on. There are so many reasons you need a Grid Computing For High Performance Solutions Introduction To Grid Computing Security Model Icons PDF. The first reason is you cannot spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Aspects Of Information System Access Control Security Auditing Diagrams PDF
The following slide highlights the aspects of information system access control security audit illustrating key headings which incudes data access control, authentication privacy, user identity, user management, password management, network access control, and login Presenting Aspects Of Information System Access Control Security Auditing Diagrams PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including User Management, Data Access Control, Network Access Control. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
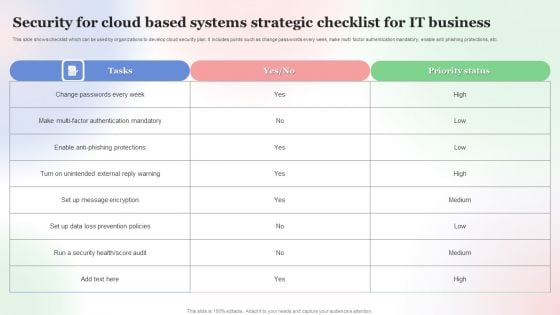
Security For Cloud Based Systems Strategic Checklist For IT Business Background PDF
This slide shows checklist which can be used by organizations to develop cloud security plan. It includes points such as change passwords every week, make multi factor authentication mandatory, enable anti phishing protections, etc. Pitch your topic with ease and precision using this Security For Cloud Based Systems Strategic Checklist For IT Business Background PDF. This layout presents information on Security For Cloud Based, Systems Strategic Checklist, For IT Business. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Monthly IT Security Awareness Training Program Timeline Ppt Model Demonstration PDF
This slide covers monthly cybersecurity awareness training program timeline. It involves activities such as passwords training, phishing exercise, remote access testing and conduct internal tabletop exercises. Showcasing this set of slides titled Monthly IT Security Awareness Training Program Timeline Ppt Model Demonstration PDF. The topics addressed in these templates are Authentication And Passwords, Conduct Phishing Exercise, Remote Access Testing. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
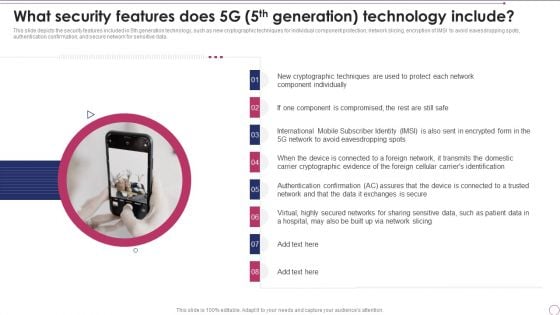
1G To 5G Wireless Communication System IT What Security Features Does 5G 5Th Generation Technology Include Professional PDF
This slide depicts the security features included in 5th generation technology, such as new cryptographic techniques for individual component protection, network slicing, encryption of IMSI to avoid eavesdropping spots, authentication confirmation, and secure network for sensitive data. Presenting 1G To 5G Wireless Communication System IT What Security Features Does 5G 5Th Generation Technology Include Professional PDF to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like Cryptographic Evidence, Domestic, Via Network Slicing. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Security Threats Compliance Violations Demonstration PDF
This slide depicts the value of compliance violations threat of cloud security in a business and how fast an organization can switch to a non compliance state. This is a Cloud Security Threats Compliance Violations Demonstration PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Businesses, Organizations, Authentication Procedures. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Internet Security Threats Management Framework Icons PDF
This slide exhibits data breach risk management model. It includes major evaluation criteria such as- does the management has two unique credentials to perform administer activities, does the multifactor authentication is enabled for administrative access etc. Showcasing this set of slides titled internet security threats management framework icons pdf. The topics addressed in these templates are asset, control topic, evaluation questions, response, threat. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
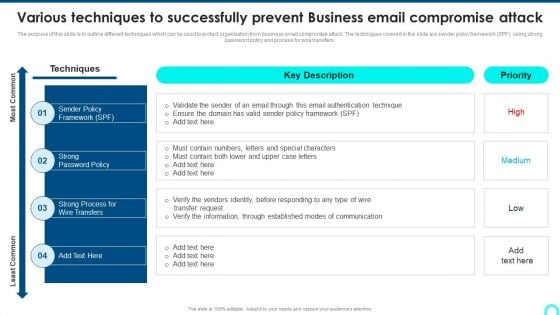
Various Techniques To Successfully Prevent Business Email Compromise Attack Sample PDF
The purpose of this slide is to outline different techniques which can be used to protect organization from business email compromise attack. The techniques covered in the slide are sender policy framework SPF, using strong password policy and process for wire transfers. Deliver and pitch your topic in the best possible manner with this Various Techniques To Successfully Prevent Business Email Compromise Attack Sample PDF. Use them to share invaluable insights on Through Established, Authentication Technique, Through Established and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
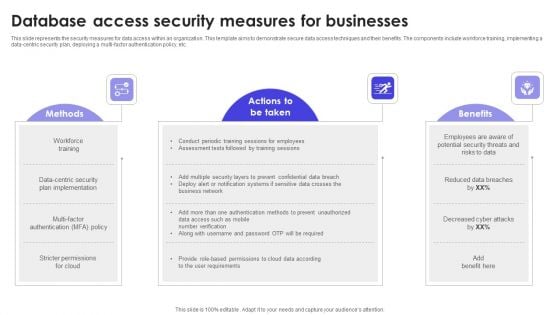
Database Access Security Measures For Businesses Portrait PDF
This slide represents the security measures for data access within an organization. This template aims to demonstrate secure data access techniques and their benefits. The components include workforce training, implementing a data-centric security plan, deploying a multi-factor authentication policy, etc. Pitch your topic with ease and precision using this Database Access Security Measures For Businesses Portrait PDF. This layout presents information on Methods, Benefits, Actions. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
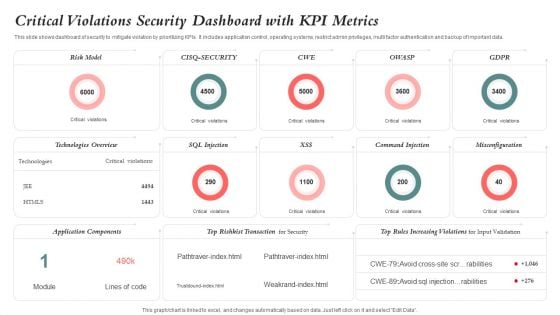
Critical Violations Security Dashboard With KPI Metrics Graphics PDF
This slide shows dashboard of security to mitigate violation by prioritizing KPIs. It includes application control, operating systems, restrict admin privileges, multi factor authentication and backup of important data. Showcasing this set of slides titled Critical Violations Security Dashboard With KPI Metrics Graphics PDF. The topics addressed in these templates are Risk Model, Application Components, Technologies Overview. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
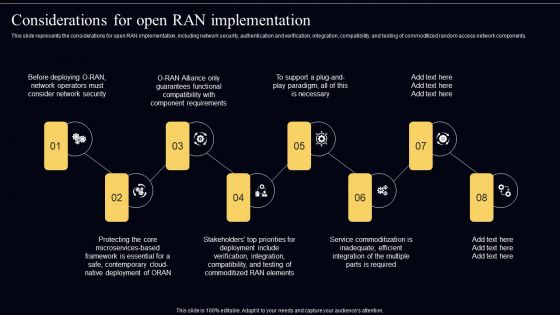
Open Radio Access Network IT Considerations For Open RAN Implementation Topics PDF
This slide represents the considerations for open RAN implementation, including network security, authentication and verification, integration, compatibility, and testing of commoditized random access network components. Boost your pitch with our creative Open Radio Access Network IT Considerations For Open RAN Implementation Topics PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
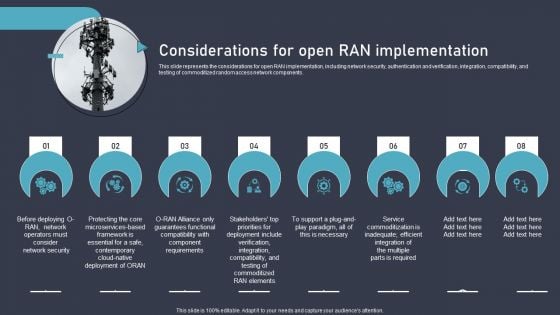
O RAN Architecture Considerations For Open Ran Implementation Brochure PDF
This slide represents the considerations for open RAN implementation, including network security, authentication and verification, integration, compatibility, and testing of commoditized random access network components. Create an editable O RAN Architecture Considerations For Open Ran Implementation Brochure PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre-designed presentation templates help save time. O RAN Architecture Considerations For Open Ran Implementation Brochure PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Cyber Exploitation IT Email Prevention Guidelines For Employees Formats PDF
This slide depicts the email prevention guidelines for employees, including spam filters and multi-factor authentication for email login credentials. Presenting cyber exploitation it email prevention guidelines for employees formats pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like usage of a spam filter, usage of mfa. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
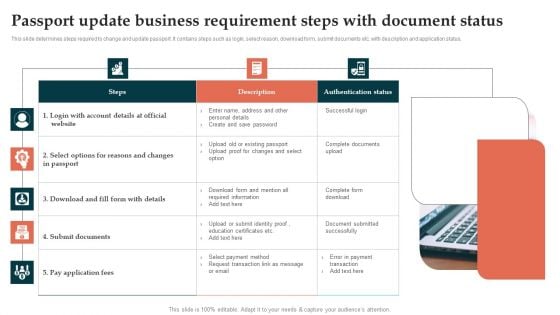
Passport Update Business Requirement Steps With Document Status Pictures PDF
This slide determines steps required to change and update passport. It contains steps such as login, select reason, download form, submit documents etc. with description and application status. Persuade your audience using this Passport Update Business Requirement Steps With Document Status Pictures PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Steps, Description, Authentication Status . Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
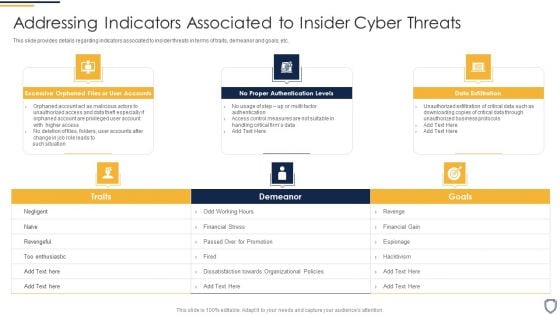
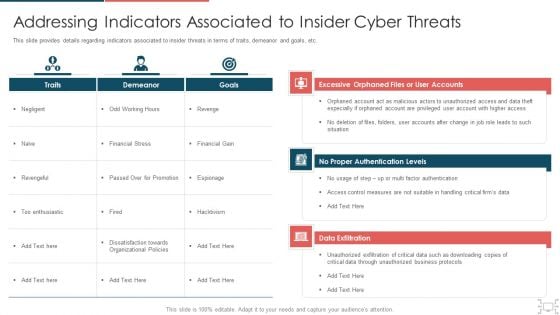
Corporate Security And Risk Management Addressing Indicators Associated To Insider Cyber Threats Topics PDF
This slide provides details regarding indicators associated to insider threats in terms of traits, demeanor and goals, etc. This is a corporate security and risk management addressing indicators associated to insider cyber threats topics pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like excessive orphaned files or user accounts, no proper authentication levels, data exfiltration . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
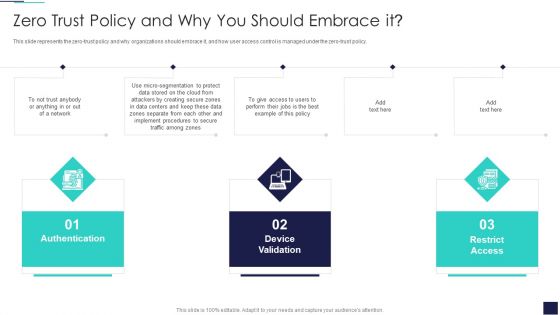
Cloud Information Security Zero Trust Policy And Why You Should Embrace IT Ppt File Outfit PDF
This slide represents the zero-trust policy and why organizations should embrace it, and how user access control is managed under the zero-trust policy. This is a Cloud Information Security Zero Trust Policy And Why You Should Embrace IT Ppt File Outfit PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Authentication Device, Validation Network, Restrict Access. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
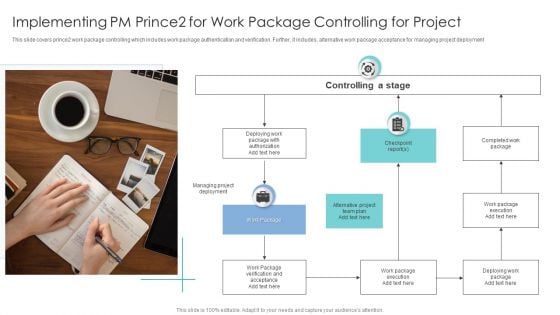
Implementing PM Prince2 For Work Package Controlling For Project Elements PDF
This slide covers prince2 work package controlling which includes work package authentication and verification. Further, it includes, alternative work package acceptance for managing project deployment. This is a Implementing PM Prince2 For Work Package Controlling For Project Elements PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Team Plan, Work Package Execution, Managing Project Deployment. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Solutions To Overcome Various Personal Banking Relationship Challenges Structure PDF
This slide signifies the solutions to overcome various banking relationship challenges. It covers information about challenges like security breach, regulatory compliance and changing business model with implemented strategies to overcome.Presenting Solutions To Overcome Various Personal Banking Relationship Challenges Structure PDF to dispense important information. This template comprises one stage. It also presents valuable insights into the topics including Regulatory Compliance, Changing Business, Authentication System. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
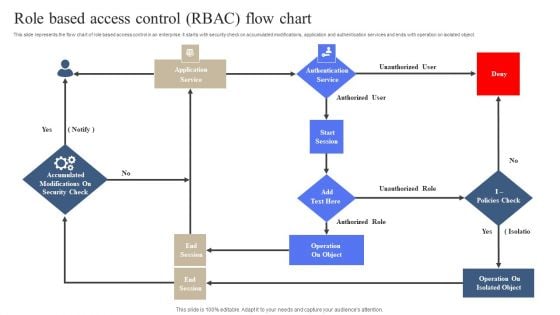
Role Based Access Control RBAC Flow Chart Slides PDF
This slide represents the flow chart of role based access control in an enterprise. It starts with security check on accumulated modifications, application and authentication services and ends with operation on isolated object. Persuade your audience using this Role Based Access Control RBAC Flow Chart Slides PDF. This PPT design covers One stage, thus making it a great tool to use. It also caters to a variety of topics including Operation On Object, Operation On Isolated Object. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Key Metrics To Manage Cyber Risk With Application Control Ppt PowerPoint Presentation Pictures Slide PDF
This slide covers cyber risk measure dashboard. It also includes application control, patch application, patch operating system, restrict admin privileges, disable untrusted Microsoft office macros, user application hardening, multi factor authentication and daily backup of important data. Pitch your topic with ease and precision using this key metrics to manage cyber risk with application control ppt powerpoint presentation pictures slide pdf. This layout presents information on disable untrusted microsoft office macros, application control, patch operating systems. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
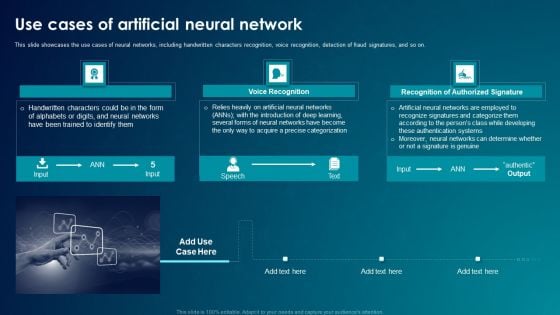
ANN System Use Cases Of Artificial Neural Network Pictures PDF
This slide showcases the use cases of neural networks, including handwritten characters recognition, voice recognition, detection of fraud signatures, and so on. This is a ANN System Use Cases Of Artificial Neural Network Pictures PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Neural Networks, Acquire, Authentication Systems. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
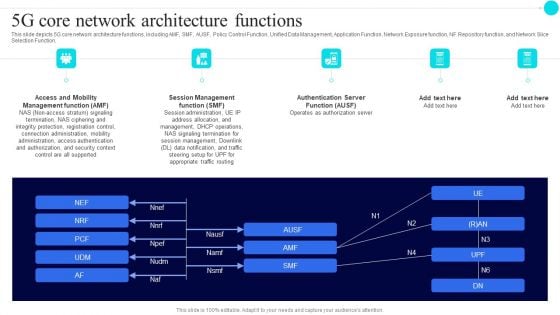
5G Core Network Architecture Functions 5G Functional Architecture Background PDF
This slide depicts 5G core network architecture functions, including AMF, SMF, AUSF, Policy Control Function, Unified Data Management, Application Function, Network Exposure function, NF Repository function, and Network Slice Selection Function.Presenting 5G Core Network Architecture Functions 5G Functional Architecture Background PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like session management, authentication server, management function. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
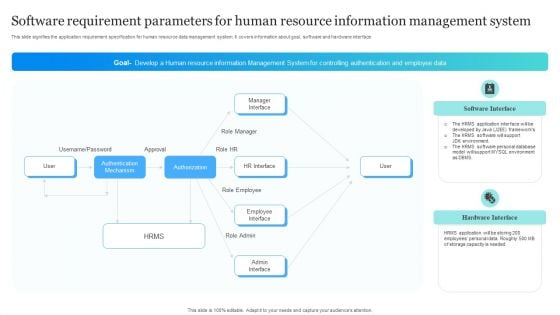
Software Requirement Parameters For Human Resource Information Management System Brochure PDF
This slide signifies the application requirement specification for human resource data management system. It covers information about goal, software and hardware interface. Persuade your audience using this Software Requirement Parameters For Human Resource Information Management System Brochure PDF. This PPT design covers two stages, thus making it a great tool to use. It also caters to a variety of topics including Authorization, Employee Interface, Manager Interface, Authentication Mechanism. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
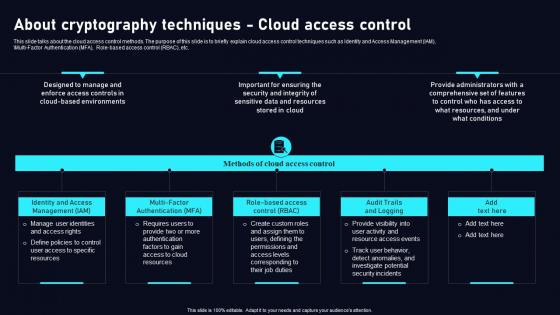
About Cryptography Techniques Cloud Data Security Using Cryptography Background Pdf
This slide talks about the cloud access control methods. The purpose of this slide is to briefly explain cloud access control techniques such as Identity and Access Management IAM, Multi Factor Authentication MFA, Role based access control RBAC, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than About Cryptography Techniques Cloud Data Security Using Cryptography Background Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab About Cryptography Techniques Cloud Data Security Using Cryptography Background Pdf today and make your presentation stand out from the rest This slide talks about the cloud access control methods. The purpose of this slide is to briefly explain cloud access control techniques such as Identity and Access Management IAM, Multi Factor Authentication MFA, Role based access control RBAC, etc.
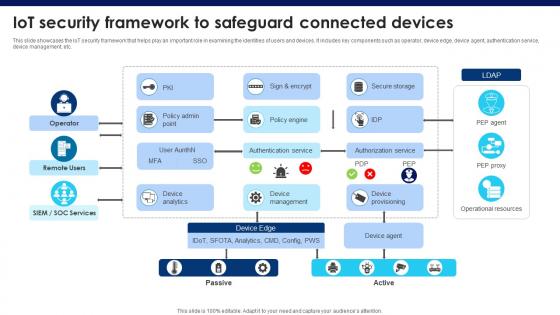
Building Trust With IoT Security IoT Security Framework To Safeguard Connected Devices IoT SS V
This slide showcases the IoT security framework that helps play an important role in examining the identities of users and devices. It includes key components such as operator, device edge, device agent, authentication service, device management, etc. This Building Trust With IoT Security IoT Security Framework To Safeguard Connected Devices IoT SS V from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide showcases the IoT security framework that helps play an important role in examining the identities of users and devices. It includes key components such as operator, device edge, device agent, authentication service, device management, etc.

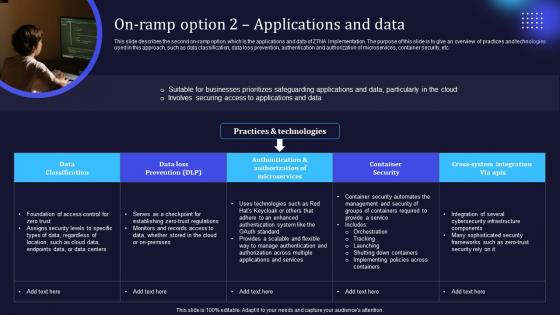
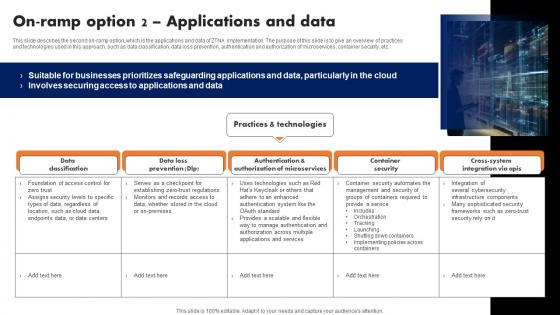
On Ramp Option 2 Applications And Data Zero Trust Network Security Sample Pdf
This slide describes the second on-ramp option, which is the applications and data of ZTNA implementation. The purpose of this slide is to give an overview of practices and technologies used in this approach, such as data classification, data loss prevention, authentication and authorization of microservices, container security, etc. The On Ramp Option 2 Applications And Data Zero Trust Network Security Sample Pdf is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide describes the second on-ramp option, which is the applications and data of ZTNA implementation. The purpose of this slide is to give an overview of practices and technologies used in this approach, such as data classification, data loss prevention, authentication and authorization of microservices, container security, etc.
Zero Trust Model On Ramp Option 2 Applications And Data
This slide describes the second on-ramp option, which is the applications and data of ZTNA implementation. The purpose of this slide is to give an overview of practices and technologies used in this approach, such as data classification, data loss prevention, authentication and authorization of microservices, container security, etc. Slidegeeks has constructed Zero Trust Model On Ramp Option 2 Applications And Data after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide describes the second on-ramp option, which is the applications and data of ZTNA implementation. The purpose of this slide is to give an overview of practices and technologies used in this approach, such as data classification, data loss prevention, authentication and authorization of microservices, container security, etc.
On Ramp Option 2 Applications And Data Software Defined Perimeter SDP
This slide describes the second on-ramp option, which is the applications and data of ZTNA implementation. The purpose of this slide is to give an overview of practices and technologies used in this approach, such as data classification, data loss prevention, authentication and authorization of microservices, container security, etc. The On Ramp Option 2 Applications And Data Software Defined Perimeter SDP is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide describes the second on-ramp option, which is the applications and data of ZTNA implementation. The purpose of this slide is to give an overview of practices and technologies used in this approach, such as data classification, data loss prevention, authentication and authorization of microservices, container security, etc.

On Ramp Option 2 Applications And Data Zero Trust Network Access
This slide describes the second on-ramp option, which is the applications and data of ZTNA implementation. The purpose of this slide is to give an overview of practices and technologies used in this approach, such as data classification, data loss prevention, authentication and authorization of microservices, container security, etc. Slidegeeks is here to make your presentations a breeze with On Ramp Option 2 Applications And Data Zero Trust Network Access With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide describes the second on-ramp option, which is the applications and data of ZTNA implementation. The purpose of this slide is to give an overview of practices and technologies used in this approach, such as data classification, data loss prevention, authentication and authorization of microservices, container security, etc.
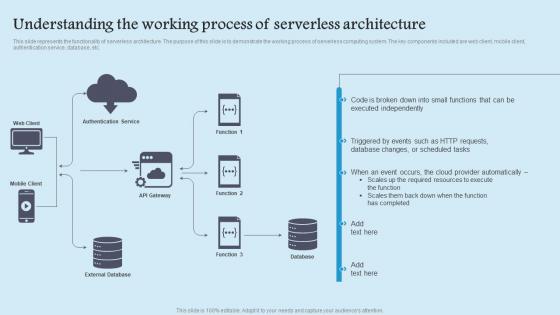
Understanding Working Process Role Serverless Computing Modern Technology Ideas Pdf
This slide represents the functionality of serverless architecture. The purpose of this slide is to demonstrate the working process of serverless computing system. The key components included are web client, mobile client, authentication service, database, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Understanding Working Process Role Serverless Computing Modern Technology Ideas Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Understanding Working Process Role Serverless Computing Modern Technology Ideas Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide represents the functionality of serverless architecture. The purpose of this slide is to demonstrate the working process of serverless computing system. The key components included are web client, mobile client, authentication service, database, etc.
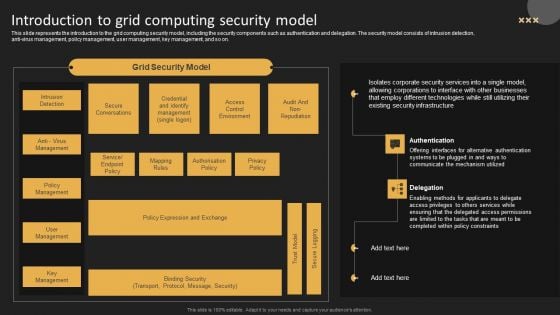
Introduction To Grid Computing Security Model Template PDF
This slide represents the introduction to the grid computing security model, including the security components such as authentication and delegation. The security model consists of intrusion detection, anti virus management, policy management, user management, key management, and so on. Get a simple yet stunning designed Introduction To Grid Computing Security Model Template PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Introduction To Grid Computing Security Model Template PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
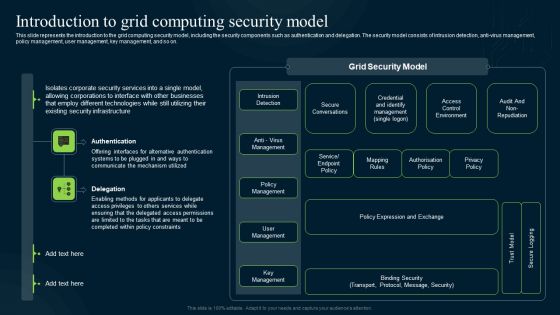
Grid Computing Infrastructure Introduction To Grid Computing Security Model Background PDF
This slide represents the introduction to the grid computing security model, including the security components such as authentication and delegation. The security model consists of intrusion detection, anti-virus management, policy management, user management, key management, and so on. This modern and well-arranged Grid Computing Infrastructure Introduction To Grid Computing Security Model Background PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
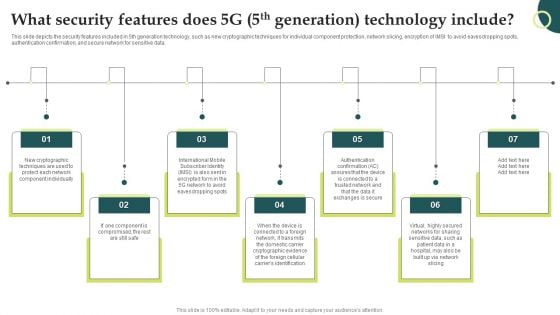
Evolution Of Wireless Technologies What Security Features Does 5G 5Th Generation Portrait PDF
This slide depicts the security features included in 5th generation technology, such as new cryptographic techniques for individual component protection, network slicing, encryption of IMSI to avoid eavesdropping spots, authentication confirmation, and secure network for sensitive data. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Evolution Of Wireless Technologies What Security Features Does 5G 5Th Generation Portrait PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Evolution Of Wireless Technologies What Security Features Does 5G 5Th Generation Portrait PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
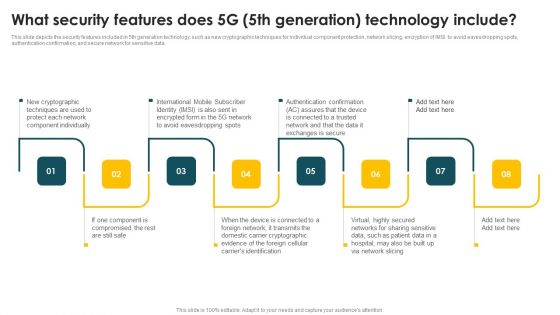
Mobile Phone Generations 1G To 5G What Security Features Does 5G 5Th Generation Designs PDF
This slide depicts the security features included in 5th generation technology, such as new cryptographic techniques for individual component protection, network slicing, encryption of IMSI to avoid eavesdropping spots, authentication confirmation, and secure network for sensitive data. Explore a selection of the finest Mobile Phone Generations 1G To 5G What Security Features Does 5G 5Th Generation Designs PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Mobile Phone Generations 1G To 5G What Security Features Does 5G 5Th Generation Designs PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
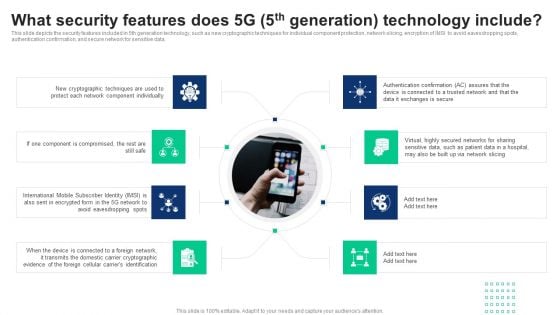
1G To 5G Cellular What Security Features Does 5G 5Th Generation Technology Include Information PDF
This slide depicts the security features included in 5th generation technology, such as new cryptographic techniques for individual component protection, network slicing, encryption of IMSI to avoid eavesdropping spots, authentication confirmation, and secure network for sensitive data. Welcome to our selection of the 1G To 5G Cellular What Security Features Does 5G 5Th Generation Technology Include Information PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.
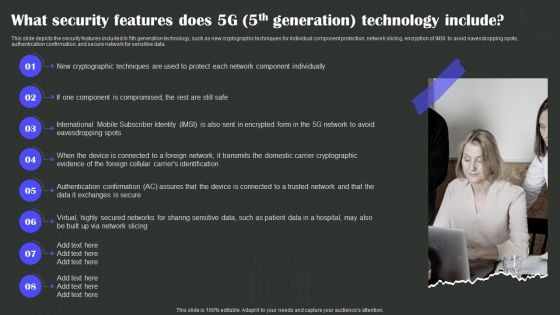
What Security Features Does 5G 5Th Generation Technology Include Wireless Technology Transformation Mockup PDF
This slide depicts the security features included in 5th generation technology, such as new cryptographic techniques for individual component protection, network slicing, encryption of IMSI to avoid eavesdropping spots, authentication confirmation, and secure network for sensitive data. Present like a pro with What Security Features Does 5G 5Th Generation Technology Include Wireless Technology Transformation Mockup PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
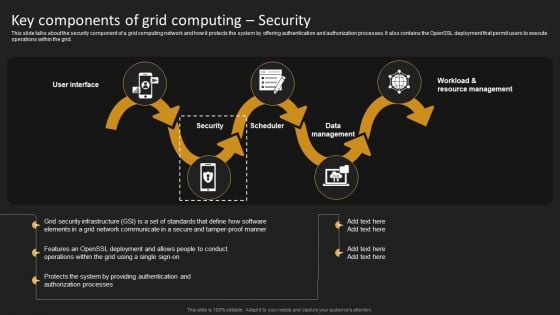
Key Components Of Grid Computing Security Structure PDF
This slide talks about the security component of a grid computing network and how it protects the system by offering authentication and authorization processes. It also contains the OpenSSL deployment that permit users to execute operations within the grid. Welcome to our selection of the Key Components Of Grid Computing Security Structure PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.
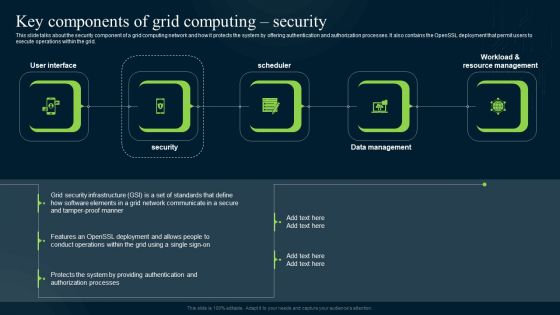
Grid Computing Infrastructure Key Components Of Grid Computing Security Information PDF
This slide talks about the security component of a grid computing network and how it protects the system by offering authentication and authorization processes. It also contains the OpenSSL deployment that permit users to execute operations within the grid. Explore a selection of the finest Grid Computing Infrastructure Key Components Of Grid Computing Security Information PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Grid Computing Infrastructure Key Components Of Grid Computing Security Information PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
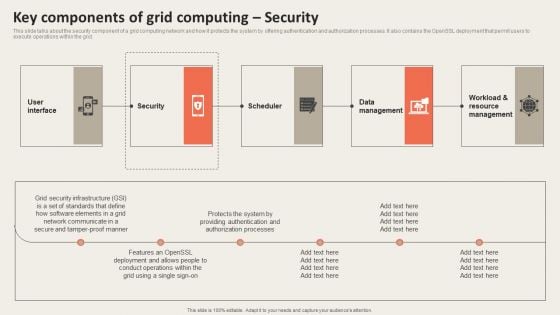
Grid Computing Applications Key Components Of Grid Computing Security Guidelines PDF
This slide talks about the security component of a grid computing network and how it protects the system by offering authentication and authorization processes. It also contains the OpenSSL deployment that permit users to execute operations within the grid. This modern and well arranged Grid Computing Applications Key Components Of Grid Computing Security Guidelines PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
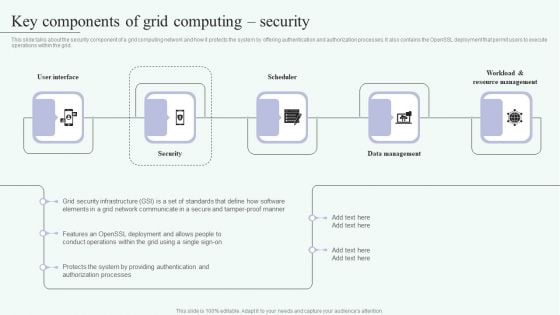
Grid Computing For High Performance Solutions Key Components Of Grid Computing Security Clipart PDF
This slide talks about the security component of a grid computing network and how it protects the system by offering authentication and authorization processes. It also contains the OpenSSL deployment that permit users to execute operations within the grid. Welcome to our selection of the Grid Computing For High Performance Solutions Key Components Of Grid Computing Security Clipart PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.
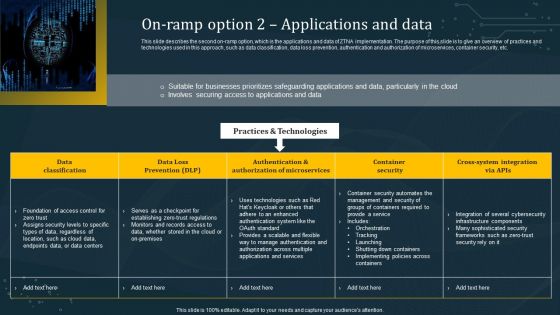
On Ramp Option 2 Applications And Data Template PDF
This slide describes the second on-ramp option, which is the applications and data of ZTNA implementation. The purpose of this slide is to give an overview of practices and technologies used in this approach, such as data classification, data loss prevention, authentication and authorization of microservices, container security, etc. Take your projects to the next level with our ultimate collection of On Ramp Option 2 Applications And Data Template PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest
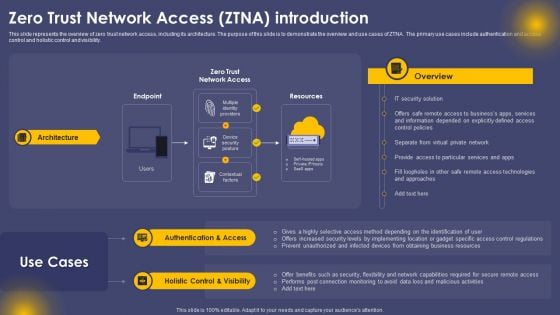
Zero Trust Network Access Ztna Introduction Ppt Slide PDF
This slide represents the overview of zero trust network access, including its architecture. The purpose of this slide is to demonstrate the overview and use cases of ZTNA. The primary use cases include authentication and access control and holistic control and visibility. Slidegeeks has constructed Zero Trust Network Access Ztna Introduction Ppt Slide PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.

Internet Marketing Qualifications Diagram Powerpoint Slides
This is a internet marketing qualifications diagram powerpoint slides. This is a three stage process. The stages in this process are innovative, authentic internet marketing, authenticity, valuable information.

Outdoor Activity Day Presentation Images
This is a outdoor activity day presentation images. This is a four stage process. The stages in this process are outdoor activity day, personal leadership challenges, authentic leadership, leadership and authenticity.


 Continue with Email
Continue with Email

 Home
Home


































