Authentication

Red And White Arrows In Round Shape PowerPoint Templates Ppt Backgrounds For Slides 1212
We present our Red And White Arrows In Round Shape PowerPoint Templates PPT Backgrounds For Slides 1212.Download our Business PowerPoint Templates because watch the excitement levels rise as they realise their worth. Use our Computer PowerPoint Templates because this PPt Enlighten others on your team with your views. Use our Success PowerPoint Templates because the choices you make today will determine the future growth of your enterprise. Download our Circle charts PowerPoint Templates because there is a very good saying that prevention is better than cure, either way you have a store of knowledge for sure. Use our Arrows PowerPoint Templates because it outlines the process with this innovative graphic to authenticate your plan of achieving the goal of added value/profit.Use these PowerPoint slides for presentations relating to Copyspace empty arrow round frame, business, arrows, computer, circle charts, success. The prominent colors used in the PowerPoint template are Red, White, Black. Use our Red And White Arrows In Round Shape PowerPoint Templates PPT Backgrounds For Slides 1212 are Classic. Presenters tell us our circle PowerPoint templates and PPT Slides are Magnificent. People tell us our Red And White Arrows In Round Shape PowerPoint Templates PPT Backgrounds For Slides 1212 are designed to make your presentations professional. You can be sure our computer PowerPoint templates and PPT Slides are Multicolored. Professionals tell us our Red And White Arrows In Round Shape PowerPoint Templates PPT Backgrounds For Slides 1212 are Cheerful. Professionals tell us our round PowerPoint templates and PPT Slides are Bright. You are almost fanatic about good work. Fan the enthusiasm of your audience with our Red And White Arrows In Round Shape PowerPoint Templates Ppt Backgrounds For Slides 1212.

New Years Eve Party Celebrations PowerPoint Templates Ppt Backgrounds For Slides 1212
We present our New Years Eve Party Celebrations PowerPoint Templates PPT Backgrounds For Slides 1212.Use our New year PowerPoint Templates because another year is coming to a close. Present our Christmas PowerPoint Templates because you can Spread the powerful message of Christianity to your congregation or community. Use our Festival PowerPoint Templates because it outlines the process with this innovative graphic to authenticate your plan of achieving the goal of added value/profit. Download and present our Holidays PowerPoint Templates because there is a very good saying that prevention is better than cure, either way you have a store of knowledge for sure. Use our Success PowerPoint Templates because our cleverly selected background hues are guaranteed to achieve this aim.Use these PowerPoint slides for presentations relating to New Years Eve Party Celebrations, new year, success, christmas, holidays, festival. The prominent colors used in the PowerPoint template are Pink, Green, Red. The feedback we get is that our New Years Eve Party Celebrations PowerPoint Templates PPT Backgrounds For Slides 1212 are Handsome. Customers tell us our christmas PowerPoint templates and PPT Slides are Youthful. PowerPoint presentation experts tell us our New Years Eve Party Celebrations PowerPoint Templates PPT Backgrounds For Slides 1212 are Endearing. You can be sure our Eve PowerPoint templates and PPT Slides are Appealing. We assure you our New Years Eve Party Celebrations PowerPoint Templates PPT Backgrounds For Slides 1212 are Attractive. The feedback we get is that our Eve PowerPoint templates and PPT Slides are Playful. Ensure your customers stay faithful to you. Capture their confidence with our New Years Eve Party Celebrations PowerPoint Templates Ppt Backgrounds For Slides 1212.
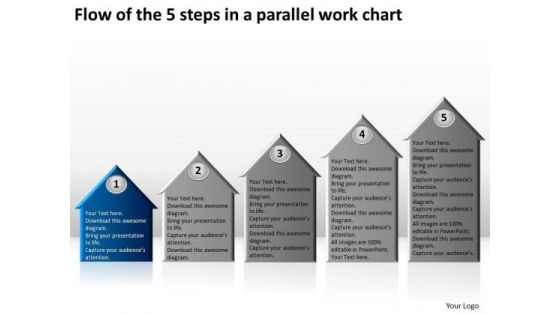
Flow Of The 5 Steps In A Parallel Work Chart Business Plan Proposal PowerPoint Templates
We present our flow of the 5 steps in a parallel work chart business plan proposal PowerPoint templates.Present our Business PowerPoint Templates because this layout helps you to bring some important aspects of your business process to the notice of all concerned. Streamline the flow of information across the board. Download and present our Marketing PowerPoint Templates because it outlines the process with this innovative graphic to authenticate your plan of achieving the goal of added value/profit. Present our Process and Flows PowerPoint Templates because Our PowerPoint Templates and Slides ensures Effective communication. They help you put across your views with precision and clarity. Download our Arrows PowerPoint Templates because you can outline your targets to your team. Use our Shapes PowerPoint Templates because visual appeal is a priority for us.Use these PowerPoint slides for presentations relating to Arrows, business, chart, commerce, concept, conceptual, design, direction, graph, graphic, green, icon, idea, illustration, model, moving, planning, process, red, strategy, success, theoretical, up, vector. The prominent colors used in the PowerPoint template are Blue, White, Gray. Use our flow of the 5 steps in a parallel work chart business plan proposal PowerPoint templates have awesome images to get your point across. Customers tell us our direction PowerPoint templates and PPT Slides are Bright. You can be sure our flow of the 5 steps in a parallel work chart business plan proposal PowerPoint templates are Bold. The feedback we get is that our commerce PowerPoint templates and PPT Slides are Royal. You can be sure our flow of the 5 steps in a parallel work chart business plan proposal PowerPoint templates are Tasteful. People tell us our graph PowerPoint templates and PPT Slides provide great value for your money. Be assured of finding the best projection to highlight your words. Face your audience with our Flow Of The 5 Steps In A Parallel Work Chart Business Plan Proposal PowerPoint Templates. You will come out on top.

Security In IoT Payment For Digital Wallet In Depth Guide To Digital Wallets Fin SS V
The following slide highlights the security measures for IoT and digital wallet that ensure secure data transfer from one device to another. Key components are security credentials, device authentication, and consumer authentication. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Security In IoT Payment For Digital Wallet In Depth Guide To Digital Wallets Fin SS V template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Security In IoT Payment For Digital Wallet In Depth Guide To Digital Wallets Fin SS V that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers The following slide highlights the security measures for IoT and digital wallet that ensure secure data transfer from one device to another. Key components are security credentials, device authentication, and consumer authentication.

Internet Of Things Advantages With Enhanced Data Protection Ppt PowerPoint Presentation File Background Designs PDF
Presenting internet of things advantages with enhanced data protection ppt powerpoint presentation file background designs pdf to dispense important information. This template comprises eight stages. It also presents valuable insights into the topics including system scalability, data protection, encrypted authentication. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Eight Steps Infographics To Improve Cyber Security Icons PDF
Persuade your audience using this eight steps infographics to improve cyber security icons pdf. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including threats, knowledge, monitoring, authentication, protection. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
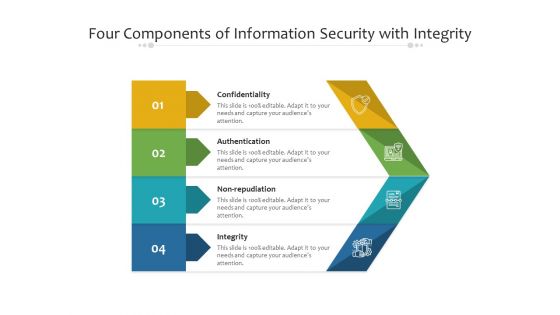
Four Components Of Information Security With Integrity Ppt PowerPoint Presentation File Gallery PDF
Presenting four components of information security with integrity ppt powerpoint presentation file gallery pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including confidentiality, authentication, integrity. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
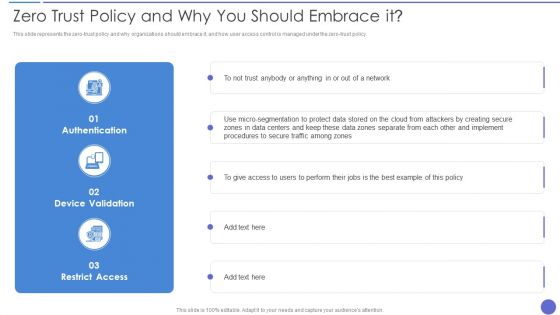
Cloud Data Security Zero Trust Policy And Why You Should Embrace It Microsoft PDF
Deliver an awe inspiring pitch with this creative Cloud Data Security Zero Trust Policy And Why You Should Embrace It Microsoft PDF bundle. Topics like Authentication, Device Validation, Restrict Access can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
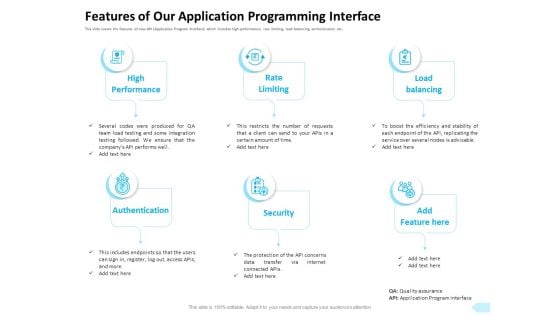
API Integration Software Development Features Of Our Application Programming Interface Graphics PDF
Presenting this set of slides with name api integration software development features of our application programming interface graphics pdf. This is a six stage process. The stages in this process are high performance, rate limiting, load balancing, authentication, security, feature. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

API Management For Building Software Applications Features Of Our Application Programming Interface Ideas PDF
Presenting this set of slides with name api management for building software applications features of our application programming interface ideas pdf. This is a six stage process. The stages in this process are high performance, load balancing, security, rate limiting, authentication. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
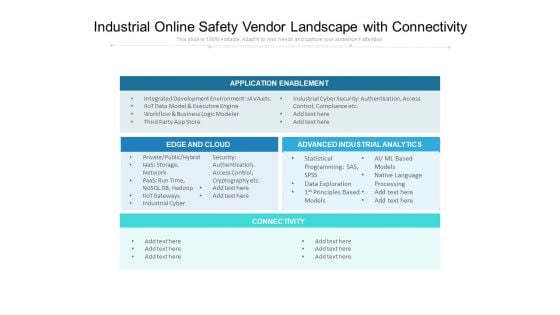
Industrial Online Safety Vendor Landscape With Connectivity Ppt PowerPoint Presentation Infographic Template Graphics Download PDF
Showcasing this set of slides titled industrial online safety vendor landscape with connectivity ppt powerpoint presentation infographic template graphics download pdf. The topics addressed in these templates are network, security,authentication, access control, cryptography, processing, business, analytics. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Data Processing Cloud Services Icon Infographics PDF
Pitch your topic with ease and precision using this Data Processing Cloud Services Icon Infographics PDF. This layout presents information on Security Compliance, Monitor Visibility, Authentication. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
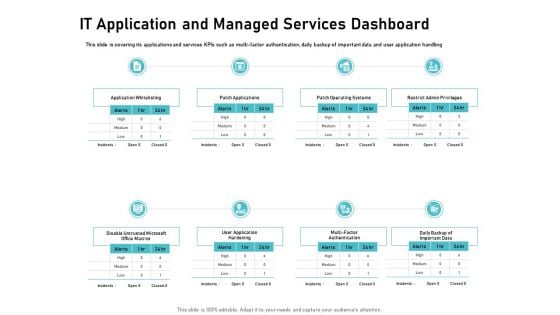
IT Support And Monitoring Services Pricing IT Application And Managed Services Dashboard Rules PDF
Presenting this set of slides with name it support and monitoring services pricing it application and managed services dashboard rules pdf. The topics discussed in these slides are authentication, application whitelisting, operating systems, privileges. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
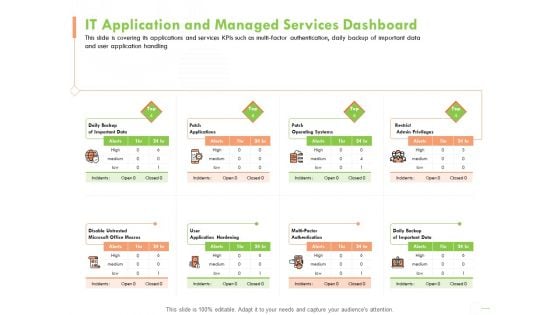
Welfare Work Value IT Application And Managed Services Dashboard Ppt Inspiration Styles PDF
Presenting this set of slides with name welfare work value it application and managed services dashboard ppt inspiration styles pdf. The topics discussed in these slides are application hardening, authentication, data, operating systems. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
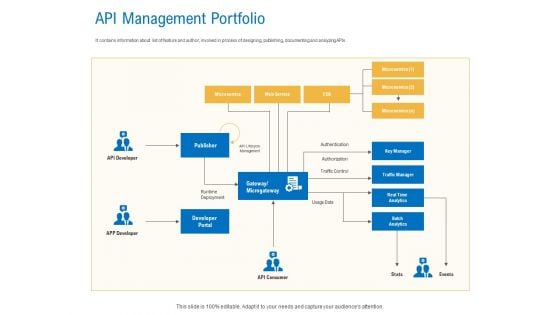
Digital Businesses Ecosystems API Management Portfolio Demonstration PDF
Deliver an awe inspiring pitch with this creative digital businesses ecosystems api management portfolio demonstration pdf bundle. Topics like service, analytics, microservice, authentication, traffic control can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
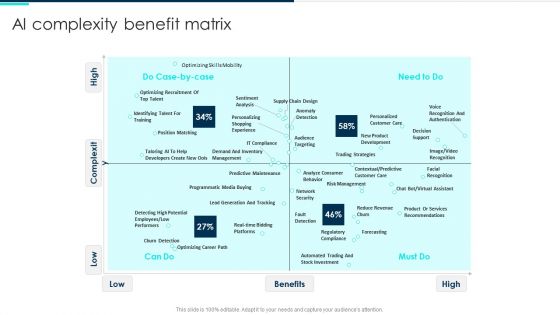
Ai Complexity Benefit Matrix Deploying Artificial Intelligence In Business Information PDF
Deliver an awe inspiring pitch with this creative Ai Complexity Benefit Matrix Deploying Artificial Intelligence In Business Information PDF bundle. Topics like Optimizing Recruitment, Recognition Authentication, Automated Trading can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Resource Optimization Plan For Implementing It Project Diagrams PDF
Showcasing this set of slides titled Resource Optimization Plan For Implementing It Project Diagrams PDF. The topics addressed in these templates are Presentation Preparation, Implement Authentication, Database Structure. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Measures Taken For Data Protection In Cloud Globally Ethical Dimensions Of Datafication Clipart Pdf
This slide represents the measures taken for data protection in the cloud worldwide, covering multi-factor authentication, cloud backup, encryption, employee training, auditing of user activity, review of access rights, data classification, and removing sensitive data from the cloud. Take your projects to the next level with our ultimate collection of Measures Taken For Data Protection In Cloud Globally Ethical Dimensions Of Datafication Clipart Pdf Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they well make your projects stand out from the rest. This slide represents the measures taken for data protection in the cloud worldwide, covering multi-factor authentication, cloud backup, encryption, employee training, auditing of user activity, review of access rights, data classification, and removing sensitive data from the cloud.
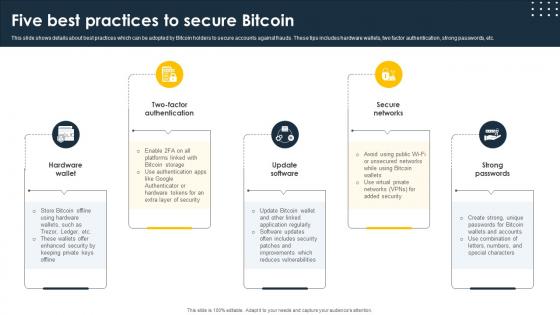
Complete Beginners Guide Five Best Practices To Secure Bitcoin Fin SS V
This slide shows details about best practices which can be adopted by Bitcoin holders to secure accounts against frauds. These tips includes hardware wallets, two factor authentication, strong passwords, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Complete Beginners Guide Five Best Practices To Secure Bitcoin Fin SS V template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Complete Beginners Guide Five Best Practices To Secure Bitcoin Fin SS V that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide shows details about best practices which can be adopted by Bitcoin holders to secure accounts against frauds. These tips includes hardware wallets, two factor authentication, strong passwords, etc.

Five Best Practices To Secure Everything About Bitcoin PPT Template Fin SS V
This slide shows details about best practices which can be adopted by Bitcoin holders to secure accounts against frauds. These tips includes hardware wallets, two factor authentication, strong passwords, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Five Best Practices To Secure Everything About Bitcoin PPT Template Fin SS V to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide shows details about best practices which can be adopted by Bitcoin holders to secure accounts against frauds. These tips includes hardware wallets, two factor authentication, strong passwords, etc.
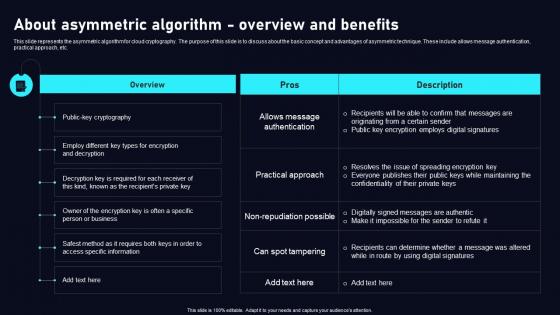
About Asymmetric Algorithm Cloud Data Security Using Cryptography Brochure Pdf
This slide represents the asymmetric algorithm for cloud cryptography. The purpose of this slide is to discuss about the basic concept and advantages of asymmetric technique. These include allows message authentication, practical approach, etc. Get a simple yet stunning designed About Asymmetric Algorithm Cloud Data Security Using Cryptography Brochure Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit About Asymmetric Algorithm Cloud Data Security Using Cryptography Brochure Pdf can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide represents the asymmetric algorithm for cloud cryptography. The purpose of this slide is to discuss about the basic concept and advantages of asymmetric technique. These include allows message authentication, practical approach, etc.
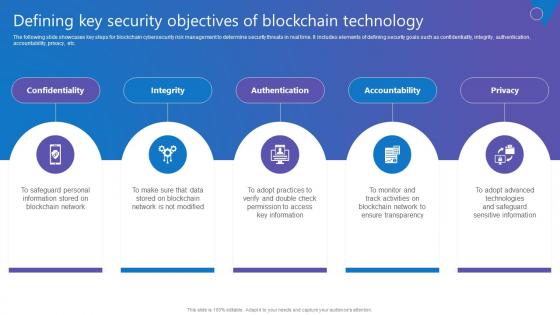
Defining Key Security Objectives Comprehensive Guide To Blockchain Digital Security Rules Pdf
The following slide showcases key steps for blockchain cybersecurity risk management to determine security threats in real time. It includes elements of defining security goals such as confidentiality, integrity, authentication, accountability, privacy, etc. Want to ace your presentation in front of a live audience Our Defining Key Security Objectives Comprehensive Guide To Blockchain Digital Security Rules Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use. The following slide showcases key steps for blockchain cybersecurity risk management to determine security threats in real time. It includes elements of defining security goals such as confidentiality, integrity, authentication, accountability, privacy, etc.

About Cryptography Overview Cloud Data Security Using Cryptography Designs Pdf
This slide talks about the concept of cryptography to secure the information sent to the recipient. The purpose of this slide is to represent the various principles of cryptography such as confidentiality, integrity, authentication, etc. Slidegeeks is here to make your presentations a breeze with About Cryptography Overview Cloud Data Security Using Cryptography Designs Pdf With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide talks about the concept of cryptography to secure the information sent to the recipient. The purpose of this slide is to represent the various principles of cryptography such as confidentiality, integrity, authentication, etc.
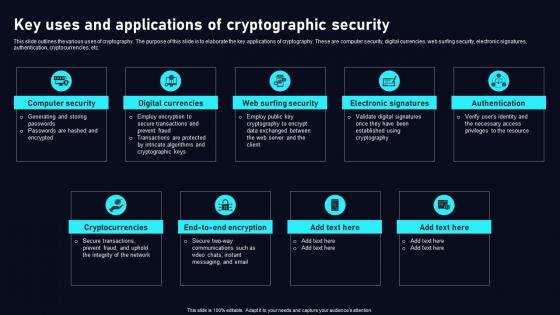
Key Uses And Applications Cryptographic Cloud Data Security Using Cryptography Sample Pdf
This slide outlines the various uses of cryptography. The purpose of this slide is to elaborate the key applications of cryptography. These are computer security, digital currencies, web surfing security, electronic signatures, authentication, cryptocurrencies, etc. Want to ace your presentation in front of a live audience Our Key Uses And Applications Cryptographic Cloud Data Security Using Cryptography Sample Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use. This slide outlines the various uses of cryptography. The purpose of this slide is to elaborate the key applications of cryptography. These are computer security, digital currencies, web surfing security, electronic signatures, authentication, cryptocurrencies, etc.
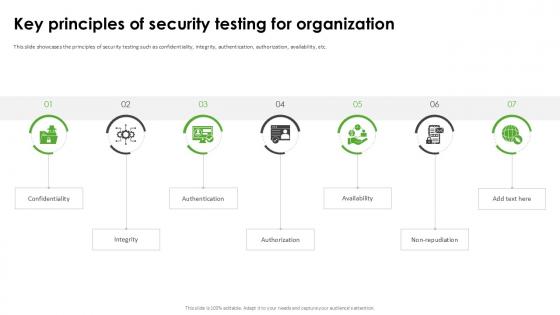
Key Principles Of Security Testing Harnessing The World Of Ethical Ppt Example
This slide showcases the principles of security testing such as confidentiality, integrity, authentication, authorization, availability, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Key Principles Of Security Testing Harnessing The World Of Ethical Ppt Example template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Key Principles Of Security Testing Harnessing The World Of Ethical Ppt Example that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide showcases the principles of security testing such as confidentiality, integrity, authentication, authorization, availability, etc.
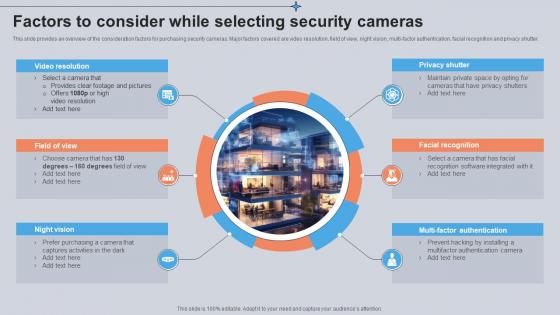
Factors To Consider While Selecting Security Cameras Utilizing Smart Appliances IoT SS V
This slide provides an overview of the consideration factors for purchasing security cameras. Major factors covered are video resolution, field of view, night vision, multi-factor authentication, facial recognition and privacy shutter. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Factors To Consider While Selecting Security Cameras Utilizing Smart Appliances IoT SS V to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide provides an overview of the consideration factors for purchasing security cameras. Major factors covered are video resolution, field of view, night vision, multi-factor authentication, facial recognition and privacy shutter.

About Cryptography Overview And Key Data Security In Cloud Computing Ppt Example
This slide talks about the concept of cryptography to secure the information sent to the recipient. The purpose of this slide is to represent the various principles of cryptography such as confidentiality, integrity, authentication, etc. Want to ace your presentation in front of a live audience Our About Cryptography Overview And Key Data Security In Cloud Computing Ppt Example can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide talks about the concept of cryptography to secure the information sent to the recipient. The purpose of this slide is to represent the various principles of cryptography such as confidentiality, integrity, authentication, etc.

Methods Used By Asymmetric Algorithm Data Security In Cloud Computing Ppt Powerpoint
This slide talks about the various applications of asymmetric algorithm in cloud cryptography. The purpose of this slide is to explain how this technique can help in providing security in cloud computing. These are authentication, encryption, key management and digital signatures. Boost your pitch with our creative Methods Used By Asymmetric Algorithm Data Security In Cloud Computing Ppt Powerpoint. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide talks about the various applications of asymmetric algorithm in cloud cryptography. The purpose of this slide is to explain how this technique can help in providing security in cloud computing. These are authentication, encryption, key management and digital signatures.
Main Features For Robust Application Security Testing Ppt Powerpoint Icons
This slide outlines the key characteristics of application security which include authentication, authorization, encryption, logging, etc. Are you searching for a Main Features For Robust Application Security Testing Ppt Powerpoint Icons that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Main Features For Robust Application Security Testing Ppt Powerpoint Icons from Slidegeeks today. This slide outlines the key characteristics of application security which include authentication, authorization, encryption, logging, etc.

Mastering Blockchain Wallets Best Practices To Enhance Mobile Wallet Security BCT SS V
This slide covers guidelines for users to improve the security of their mobile wallets. The purpose of this template is to provide tips such as adding two factor authentication, using secure Wifi connections, storing passwords in way preventing theft, installing mobile applications from trusted sources, etc. along with security and compliance measures by E-wallets providers. There are so many reasons you need a Mastering Blockchain Wallets Best Practices To Enhance Mobile Wallet Security BCT SS V. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide covers guidelines for users to improve the security of their mobile wallets. The purpose of this template is to provide tips such as adding two factor authentication, using secure Wifi connections, storing passwords in way preventing theft, installing mobile applications from trusted sources, etc. along with security and compliance measures by E-wallets providers.

Key Uses And Applications Of Data Security In Cloud Computing Ppt Slide
This slide outlines the various uses of cryptography. The purpose of this slide is to elaborate the key applications of cryptography. These are computer security, digital currencies, web surfing security, electronic signatures, authentication, cryptocurrencies, etc. Take your projects to the next level with our ultimate collection of Key Uses And Applications Of Data Security In Cloud Computing Ppt Slide. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest This slide outlines the various uses of cryptography. The purpose of this slide is to elaborate the key applications of cryptography. These are computer security, digital currencies, web surfing security, electronic signatures, authentication, cryptocurrencies, etc.
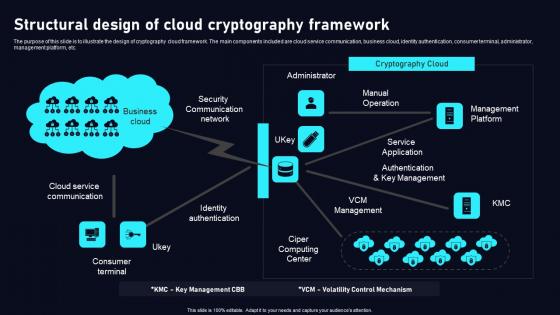
Structural Design Of Cloud Cryptography Cloud Data Security Using Cryptography Themes Pdf
The purpose of this slide is to illustrate the design of cryptography cloud framework. The main components included are cloud service communication, business cloud, identity authentication, consumer terminal, administrator, management platform, etc. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Structural Design Of Cloud Cryptography Cloud Data Security Using Cryptography Themes Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates The purpose of this slide is to illustrate the design of cryptography cloud framework. The main components included are cloud service communication, business cloud, identity authentication, consumer terminal, administrator, management platform, etc.
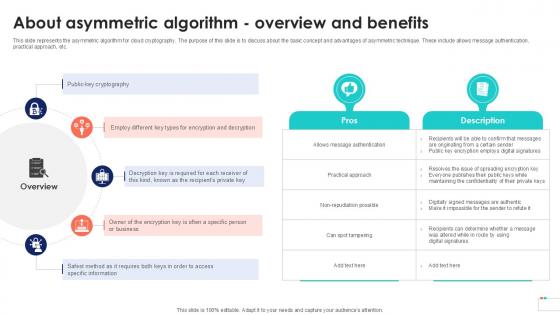
About Asymmetric Algorithm Overview Data Security In Cloud Computing Ppt Template
This slide represents the asymmetric algorithm for cloud cryptography. The purpose of this slide is to discuss about the basic concept and advantages of asymmetric technique. These include allows message authentication, practical approach, etc. Boost your pitch with our creative About Asymmetric Algorithm Overview Data Security In Cloud Computing Ppt Template. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide represents the asymmetric algorithm for cloud cryptography. The purpose of this slide is to discuss about the basic concept and advantages of asymmetric technique. These include allows message authentication, practical approach, etc.
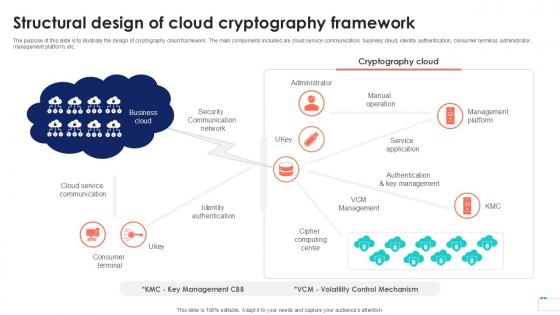
Structural Design Of Cloud Cryptography Data Security In Cloud Computing Ppt Sample
The purpose of this slide is to illustrate the design of cryptography cloud framework. The main components included are cloud service communication, business cloud, identity authentication, consumer terminal, administrator, management platform, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Structural Design Of Cloud Cryptography Data Security In Cloud Computing Ppt Sample will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. The purpose of this slide is to illustrate the design of cryptography cloud framework. The main components included are cloud service communication, business cloud, identity authentication, consumer terminal, administrator, management platform, etc.

Data Breach Prevention Strategies For Users Data Breach Prevention Sample Pdf
This slide represents the strategies to protect users from data breaches. These include use unique passwords, two-factor authentication, only submit sensitive data on HTTPS websites, software and hardware updates, encrypt hard drives, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Data Breach Prevention Strategies For Users Data Breach Prevention Sample Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide represents the strategies to protect users from data breaches. These include use unique passwords, two-factor authentication, only submit sensitive data on HTTPS websites, software and hardware updates, encrypt hard drives, etc.
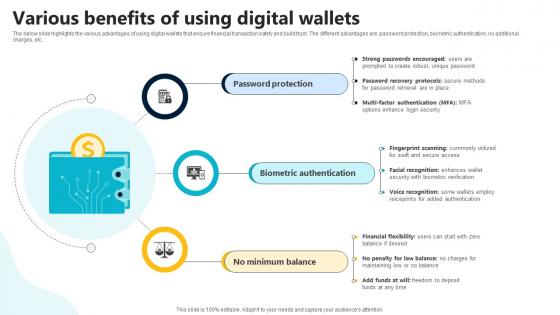
Various Benefits Of Using Digital Wallets In Depth Guide To Digital Wallets Fin SS V
The below slide highlights the various advantages of using digital wallets that ensure financial transaction safety and build trust. The different advantages are password protection, biometric authentication, no additional charges, etc. The Various Benefits Of Using Digital Wallets In Depth Guide To Digital Wallets Fin SS V is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. The below slide highlights the various advantages of using digital wallets that ensure financial transaction safety and build trust. The different advantages are password protection, biometric authentication, no additional charges, etc.

Empowering The Future Strategies To Reduce Cybersecurity Concerns In IoT SS V
This slide exhibits key cybersecurity concerns solving methods for IoT-enabled smart grid. These strategies include multiple authentication, employee training, password strength, and operating system protection. Are you searching for a Empowering The Future Strategies To Reduce Cybersecurity Concerns In IoT SS V that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Empowering The Future Strategies To Reduce Cybersecurity Concerns In IoT SS V from Slidegeeks today. This slide exhibits key cybersecurity concerns solving methods for IoT-enabled smart grid. These strategies include multiple authentication, employee training, password strength, and operating system protection.
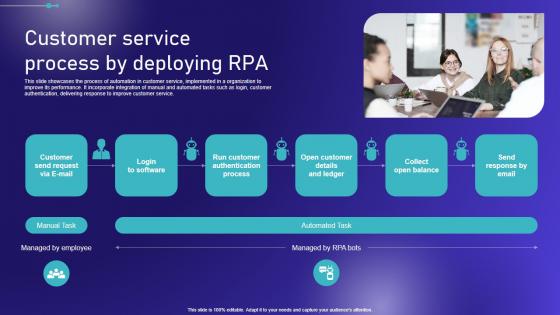
Customer Service Process By Deploying RPA Embracing Robotic Process Mockup PDF
This slide showcases the process of automation in customer service, implemented in a organization to improve its performance. It incorporate integration of manual and automated tasks such as login, customer authentication, delivering response to improve customer service. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Customer Service Process By Deploying RPA Embracing Robotic Process Mockup PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide showcases the process of automation in customer service, implemented in a organization to improve its performance. It incorporate integration of manual and automated tasks such as login, customer authentication, delivering response to improve customer service.

Use Cases Of Biometrics In Initiating Globalization Of Banking Ppt Powerpoint
This slide showcases need of biometrics in banks. This template focuses on protecting users from generative AI attacks such as face swaps and fake account. It includes information related to customer onboarding and authentication. Take your projects to the next level with our ultimate collection of Use Cases Of Biometrics In Initiating Globalization Of Banking Ppt Powerpoint. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest This slide showcases need of biometrics in banks. This template focuses on protecting users from generative AI attacks such as face swaps and fake account. It includes information related to customer onboarding and authentication.

Beginners Guide To Commercial Addressing Cybersecurity Challenges In Commercial Fin SS V
This slide shows extensive details regarding various solutions which can be used against cyberthreats by banks. These solutions are network security, multifactor authentication, data encryption and secure communications, etc. Want to ace your presentation in front of a live audience Our Beginners Guide To Commercial Addressing Cybersecurity Challenges In Commercial Fin SS V can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide shows extensive details regarding various solutions which can be used against cyberthreats by banks. These solutions are network security, multifactor authentication, data encryption and secure communications, etc.

Addressing Cybersecurity Challenges In Complete Guide On Managing Banking Fin SS V
This slide shows extensive details regarding various solutions which can be used against cyberthreats by banks. These solutions are network security, multifactor authentication, data encryption and secure communications, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Addressing Cybersecurity Challenges In Complete Guide On Managing Banking Fin SS V for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide shows extensive details regarding various solutions which can be used against cyberthreats by banks. These solutions are network security, multifactor authentication, data encryption and secure communications, etc.
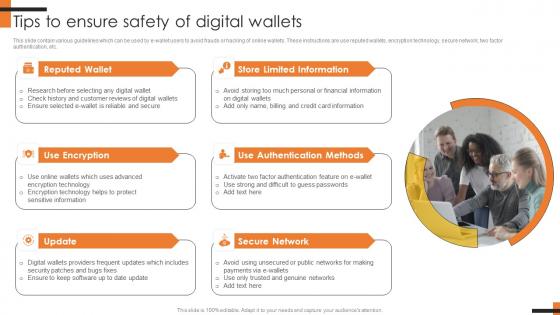
Tips To Ensure Safety Of Digital Wallets Comprehensive Smartphone Banking Information Pdf
This slide contain various guidelines which can be used by e-wallet users to avoid frauds or hacking of online wallets. These instructions are use reputed wallets, encryption technology, secure network, two factor authentication, etc.The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100Precent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Tips To Ensure Safety Of Digital Wallets Comprehensive Smartphone Banking Information Pdf from Slidegeeks and deliver a wonderful presentation. This slide contain various guidelines which can be used by e wallet users to avoid frauds or hacking of online wallets. These instructions are use reputed wallets, encryption technology, secure network, two factor authentication, etc.

Wireless Banking To Improve Tips To Ensure Safety Of Digital Wallets Fin SS V
This slide contain various guidelines which can be used by e-wallet users to avoid frauds or hacking of online wallets. These instructions are use reputed wallets, encryption technology, secure network, two factor authentication, etc. The Wireless Banking To Improve Tips To Ensure Safety Of Digital Wallets Fin SS V is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide contain various guidelines which can be used by e-wallet users to avoid frauds or hacking of online wallets. These instructions are use reputed wallets, encryption technology, secure network, two factor authentication, etc.
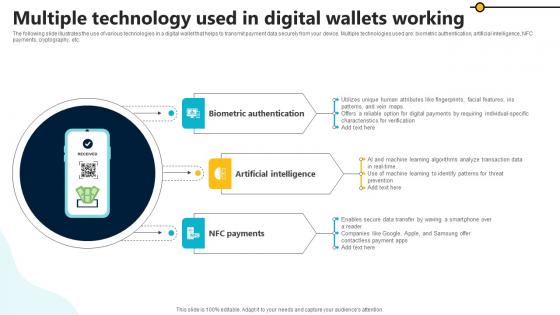
Multiple Technology Used In Digital Wallets Working In Depth Guide To Digital Wallets Fin SS V
The following slide illustrates the use of various technologies in a digital wallet that helps to transmit payment data securely from your device. Multiple technologies used are biometric authentication, artificial intelligence, NFC payments, cryptography, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Multiple Technology Used In Digital Wallets Working In Depth Guide To Digital Wallets Fin SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. The following slide illustrates the use of various technologies in a digital wallet that helps to transmit payment data securely from your device. Multiple technologies used are biometric authentication, artificial intelligence, NFC payments, cryptography, etc.

Comprehensive Look At Blockchain Use Cases Of Blockchain In Cybersecurity BCT SS V
This slide highlights various use cases of integrating blockchain technology in cybersecurity. It includes edge computing with authentication, advance confidentiality, secured private messaging, improved PKI and intact domain systems. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Comprehensive Look At Blockchain Use Cases Of Blockchain In Cybersecurity BCT SS V template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Comprehensive Look At Blockchain Use Cases Of Blockchain In Cybersecurity BCT SS V that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide highlights various use cases of integrating blockchain technology in cybersecurity. It includes edge computing with authentication, advance confidentiality, secured private messaging, improved PKI and intact domain systems.
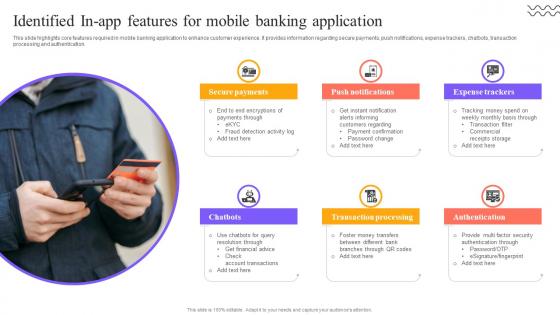
Digital Approach To Client Identified In App Features For Mobile Banking Application
This slide highlights core features required in mobile banking application to enhance customer experience. It provides information regarding secure payments, push notifications, expense trackers, chatbots, transaction processing and authentication. Are you searching for a Digital Approach To Client Identified In App Features For Mobile Banking Application that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Digital Approach To Client Identified In App Features For Mobile Banking Application from Slidegeeks today. This slide highlights core features required in mobile banking application to enhance customer experience. It provides information regarding secure payments, push notifications, expense trackers, chatbots, transaction processing and authentication.

Visionary Guide To Blockchain Use Cases Of Blockchain In Cybersecurity BCT SS V
This slide highlights various use cases of integrating blockchain technology in cybersecurity. It includes edge computing with authentication, advance confidentiality, secured private messaging, improved PKI and intact domain systems. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Visionary Guide To Blockchain Use Cases Of Blockchain In Cybersecurity BCT SS V to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide highlights various use cases of integrating blockchain technology in cybersecurity. It includes edge computing with authentication, advance confidentiality, secured private messaging, improved PKI and intact domain systems.

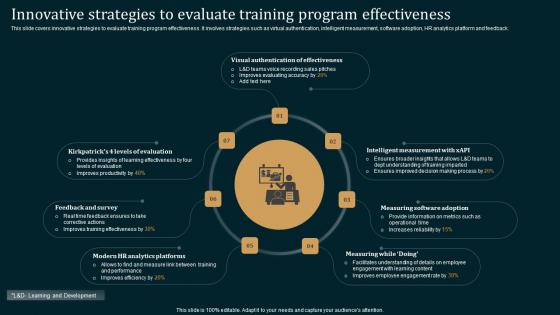
Innovative Strategies To Evaluate Training Proven Techniques For Enhancing Pictures Pdf
This slide covers innovative strategies to evaluate training program effectiveness. It involves strategies such as virtual authentication, intelligent measurement, software adoption, HR analytics platform and feedback.Get a simple yet stunning designed Innovative Strategies To Evaluate Training Proven Techniques For Enhancing Pictures Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Innovative Strategies To Evaluate Training Proven Techniques For Enhancing Pictures Pdf can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide covers innovative strategies to evaluate training program effectiveness. It involves strategies such as virtual authentication, intelligent measurement, software adoption, HR analytics platform and feedback.
Innovative Strategies To Evaluate Employee Performance Improvement Strategies Portrait Pdf
This slide covers innovative strategies to evaluate training program effectiveness. It involves strategies such as virtual authentication, intelligent measurement, software adoption, HR analytics platform and feedback. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Innovative Strategies To Evaluate Employee Performance Improvement Strategies Portrait Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide covers innovative strategies to evaluate training program effectiveness. It involves strategies such as virtual authentication, intelligent measurement, software adoption, HR analytics platform and feedback.
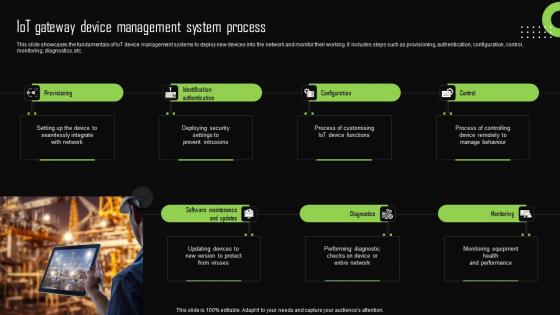
Iot Gateway Device Management System Process Iot Device Management Portrait Pdf
This slide showcases the fundamentals of IoT device management systems to deploy new devices into the network and monitor their working. It includes steps such as provisioning, authentication, configuration, control, monitoring, diagnostics, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Iot Gateway Device Management System Process Iot Device Management Portrait Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide showcases the fundamentals of IoT device management systems to deploy new devices into the network and monitor their working. It includes steps such as provisioning, authentication, configuration, control, monitoring, diagnostics, etc.

Zero Trust Network Access System Use Cases Themes Pdf
This slide outlines the workflow of zero trust network access architecture. The purpose of this slide is to showcase the various steps of the ZTNA model workflow, including user authentication, grant access, monitoring of user sessions, and threat response. Present like a pro with Zero Trust Network Access System Use Cases Themes Pdf Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide outlines the workflow of zero trust network access architecture. The purpose of this slide is to showcase the various steps of the ZTNA model workflow, including user authentication, grant access, monitoring of user sessions, and threat response.
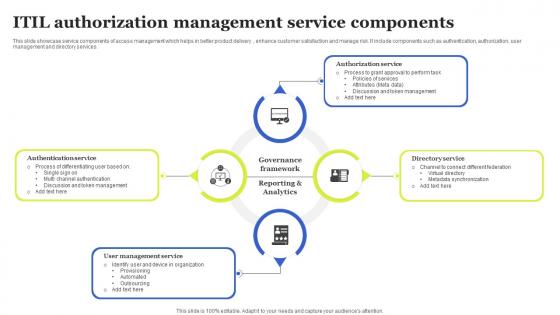
ITIL Authorization Management Service Components Introduction Pdf
This slide showcase service components of access management which helps in better product delivery , enhance customer satisfaction and manage risk. It include components such as authentication, authorization, user management and directory services. Showcasing this set of slides titled ITIL Authorization Management Service Components Introduction Pdf The topics addressed in these templates are Governance Framework, Reporting And Analytics, Directory Service All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcase service components of access management which helps in better product delivery , enhance customer satisfaction and manage risk. It include components such as authentication, authorization, user management and directory services.

A50 Zero Trust Network Access Architecture Workflow
This slide outlines the workflow of zero trust network access architecture. The purpose of this slide is to showcase the various steps of the ZTNA model workflow, including user authentication, grant access, monitoring of user sessions, and threat response. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate A50 Zero Trust Network Access Architecture Workflow for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide outlines the workflow of zero trust network access architecture. The purpose of this slide is to showcase the various steps of the ZTNA model workflow, including user authentication, grant access, monitoring of user sessions, and threat response.
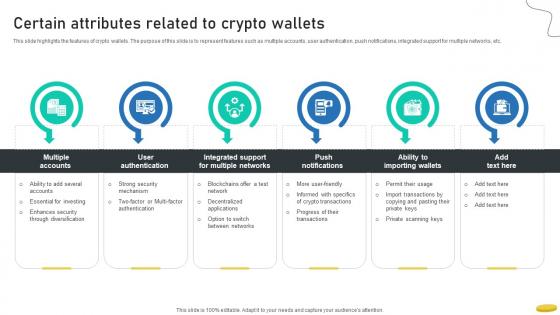
Certain Attributes Related To Crypto Wallets Cryptocurrency Management With Blockchain
This slide highlights the features of crypto wallets. The purpose of this slide is to represent features such as multiple accounts, user authentication, push notifications, integrated support for multiple networks, etc.Whether you have daily or monthly meetings, a brilliant presentation is necessary. Certain Attributes Related To Crypto Wallets Cryptocurrency Management With Blockchain can be your best option for delivering a presentation. Represent everything in detail using Certain Attributes Related To Crypto Wallets Cryptocurrency Management With Blockchain and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide highlights the features of crypto wallets. The purpose of this slide is to represent features such as multiple accounts, user authentication, push notifications, integrated support for multiple networks, etc.
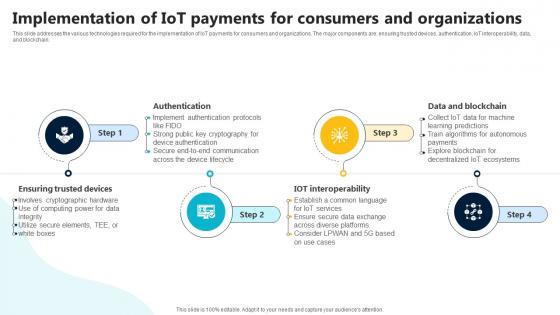
Implementation Of IoT Payments For Consumers In Depth Guide To Digital Wallets Fin SS V
This slide addresses the various technologies required for the implementation of IoT payments for consumers and organizations. The major components are ensuring trusted devices, authentication, IoT interoperability, data, and blockchain. This Implementation Of IoT Payments For Consumers In Depth Guide To Digital Wallets Fin SS V from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide addresses the various technologies required for the implementation of IoT payments for consumers and organizations. The major components are ensuring trusted devices, authentication, IoT interoperability, data, and blockchain.
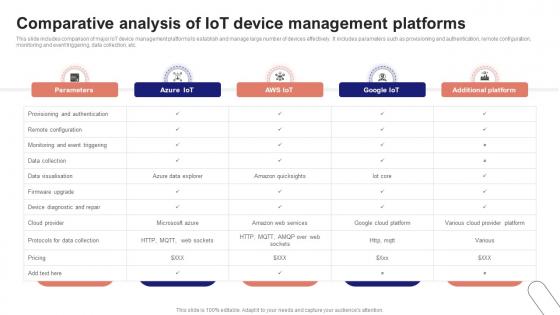
IoT Device Management Fundamentals Comparative Analysis Of IoT Device Management Platforms IoT Ss V
This slide includes comparison of major IoT device management platforms to establish and manage large number of devices effectively. It includes parameters such as provisioning and authentication, remote configuration, monitoring and event triggering, data collection, etc. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit IoT Device Management Fundamentals Comparative Analysis Of IoT Device Management Platforms IoT SS V and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide includes comparison of major IoT device management platforms to establish and manage large number of devices effectively. It includes parameters such as provisioning and authentication, remote configuration, monitoring and event triggering, data collection, etc.
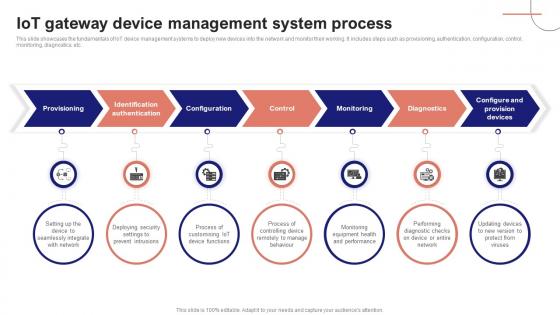
IoT Device Management Fundamentals IoT Gateway Device Management System Process IoT Ss V
This slide showcases the fundamentals of IoT device management systems to deploy new devices into the network and monitor their working. It includes steps such as provisioning, authentication, configuration, control, monitoring, diagnostics, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward IoT Device Management Fundamentals IoT Gateway Device Management System Process IoT SS V template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal IoT Device Management Fundamentals IoT Gateway Device Management System Process IoT SS V that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide showcases the fundamentals of IoT device management systems to deploy new devices into the network and monitor their working. It includes steps such as provisioning, authentication, configuration, control, monitoring, diagnostics, etc.
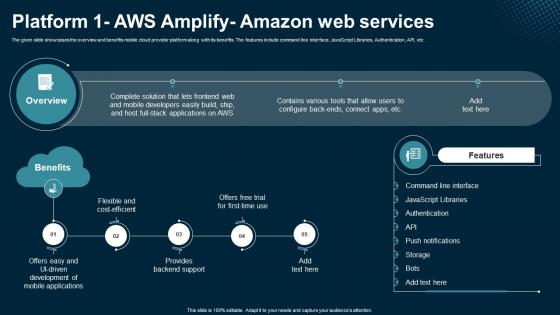
Platform 1 AWS Amplify Amazon Web Services Application Areas Of Mobile Cloud Computing
The given slide showcases the overview and benefits mobile cloud provider platform along with its benefits. The features include command line interface, JavaScript Libraries, Authentication, API, etc. The Platform 1 AWS Amplify Amazon Web Services Application Areas Of Mobile Cloud Computing is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. The given slide showcases the overview and benefits mobile cloud provider platform along with its benefits. The features include command line interface, JavaScript Libraries, Authentication, API, etc.
Securing Our Data With CRM Designing And Deployment Ppt PowerPoint Presentation Icon Example File PDF
This slide highlights the data security using CRM which incorporates IP restriction, two factor authentication, data storage, communication protection and data security. Deliver an awe inspiring pitch with this creative securing our data with crm designing and deployment ppt powerpoint presentation icon example file pdf bundle. Topics like crm data security, ip restriction, data storage and failover, communication protection can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Five Elements Of Cloud Services Security Brochure PDF
This slide includes elements of cloud computing security to assure network protection and efficient management. It contains five elements architecture, security, due diligence, authentication, monitor and visibility.Presenting Five Elements Of Cloud Services Security Brochure PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Security Coverage, Intrusion Detection, Computing Regulations. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.


 Continue with Email
Continue with Email

 Home
Home


































