Authentication

IT Protection Cyber Security Cyber Threat Ppt PowerPoint Presentation Complete Deck
Presenting this set of slides with name it protection cyber security cyber threat ppt powerpoint presentation complete deck. The topics discussed in these slides are network protection, cyber security, cyber threat, laptop protected, security breach. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
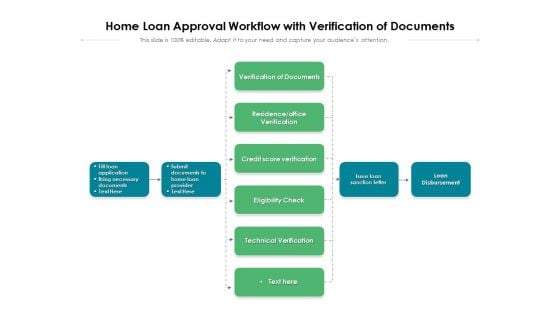
Home Loan Approval Workflow With Verification Of Documents Ppt PowerPoint Presentation Ideas Files PDF
Presenting home loan approval workflow with verification of documents ppt powerpoint presentation ideas files pdf to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including verification of documents, residence office verification, credit score verification, eligibility check, technical verification, issue loan, sanction letter, loan disbursement. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Data Encryption Method In Application Security Testing Ppt Powerpoint Formats
This slide discusses the introduction of encryption in application security for protection of specific fields in an application. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Data Encryption Method In Application Security Testing Ppt Powerpoint Formats to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide discusses the introduction of encryption in application security for protection of specific fields in an application.
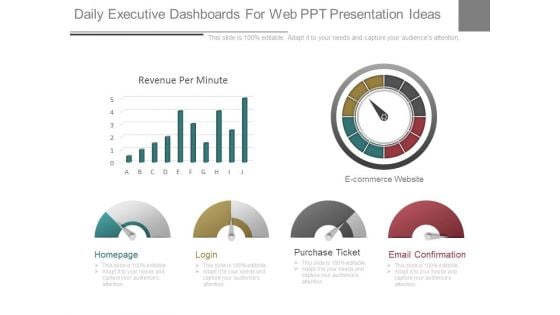
Daily Executive Dashboards For Web Ppt Presentation Ideas
This is a daily executive dashboards for web ppt presentation ideas. This is a six stage process. The stages in this process are homepage, login, purchase ticket, email confirmation, ecommerce website, revenue per minute.
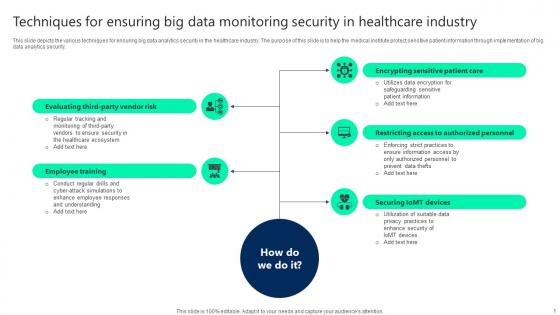
Techniques For Ensuring Big Data Monitoring Security In Healthcare Industry Infographics pdf
This slide depicts the various techniques for ensuring big data analytics security in the healthcare industry. The purpose of this slide is to help the medical institute protect sensitive patient information through implementation of big data analytics security. Pitch your topic with ease and precision using this Techniques For Ensuring Big Data Monitoring Security In Healthcare Industry Infographics pdf. This layout presents information on Employee Training, Securing Iomt Devices, Restricting Access. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide depicts the various techniques for ensuring big data analytics security in the healthcare industry. The purpose of this slide is to help the medical institute protect sensitive patient information through implementation of big data analytics security.
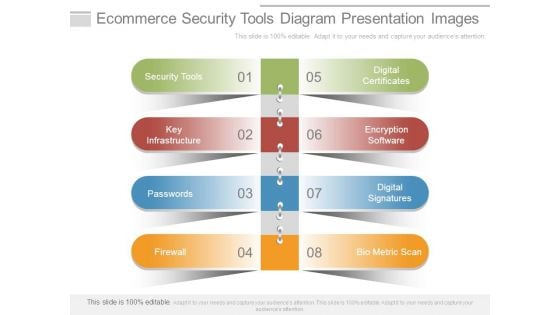
Ecommerce Security Tools Diagram Presentation Images
This is a ecommerce security tools diagram presentation images. This is a eight stage process. The stages in this process are security tools, key infrastructure, passwords, firewall, digital certificates, encryption software, digital signatures, bio metric scan.
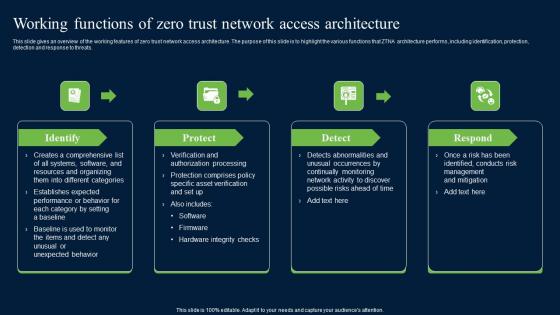
Working Functions Of Zero Trust Network Access Security Infographics Pdf
This slide gives an overview of the working features of zero trust network access architecture. The purpose of this slide is to highlight the various functions that ZTNA architecture performs, including identification, protection, detection and response to threats. Create an editable Working Functions Of Zero Trust Network Access Security Infographics Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Working Functions Of Zero Trust Network Access Security Infographics Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide gives an overview of the working features of zero trust network access architecture. The purpose of this slide is to highlight the various functions that ZTNA architecture performs, including identification, protection, detection and response to threats.
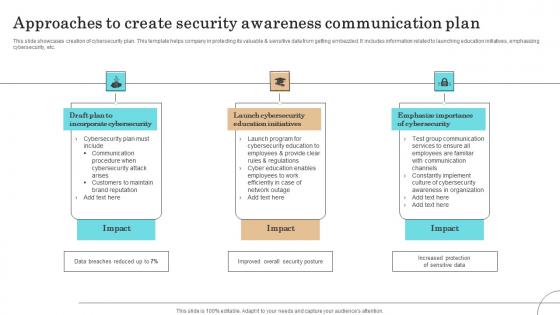
Approaches To Create Security Awareness Communication Plan Professional Pdf
This slide showcases creation of cybersecurity plan. This template helps company in protecting its valuable sensitive data from getting embezzled. It includes information related to launching education initiatives, emphasizing cybersecurity, etc.Showcasing this set of slides titled Approaches To Create Security Awareness Communication Plan Professional Pdf The topics addressed in these templates are Incorporate Cybersecurity, Launch Cybersecurity, Education Initiatives All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcases creation of cybersecurity plan. This template helps company in protecting its valuable sensitive data from getting embezzled. It includes information related to launching education initiatives, emphasizing cybersecurity, etc.
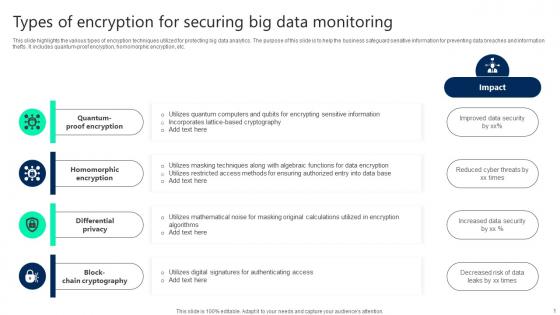
Types Of Encryption For Securing Big Data Monitoring Topics pdf
This slide highlights the various types of encryption techniques utilized for protecting big data analytics. The purpose of this slide is to help the business safeguard sensitive information for preventing data breaches and information thefts. It includes quantum-proof encryption, homomorphic encryption, etc. Showcasing this set of slides titled Types Of Encryption For Securing Big Data Monitoring Topics pdf. The topics addressed in these templates are Quantum Proof Encryption, Homomorphic Encryption, Differential Privacy. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide highlights the various types of encryption techniques utilized for protecting big data analytics. The purpose of this slide is to help the business safeguard sensitive information for preventing data breaches and information thefts. It includes quantum-proof encryption, homomorphic encryption, etc.
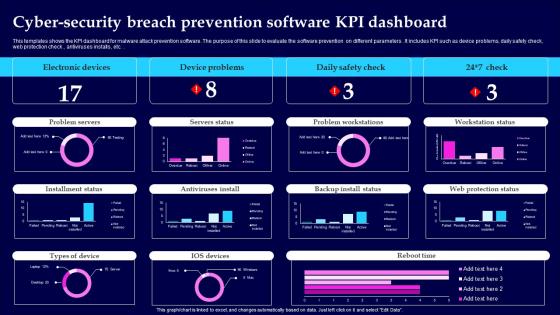
Cyber Security Breach Prevention Software KPI Dashboard Information Pdf
This templates shows the KPI dashboard for malware attack prevention software. The purpose of this slide to evaluate the software prevention on different parameters. It includes KPI such as device problems, daily safety check, web protection check, antiviruses installs , etc. Showcasing this set of slides titled Cyber Security Breach Prevention Software KPI Dashboard Information Pdf The topics addressed in these templates are Electronic Devices, Device Problems, Daily Safety Check All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This templates shows the KPI dashboard for malware attack prevention software. The purpose of this slide to evaluate the software prevention on different parameters. It includes KPI such as device problems, daily safety check, web protection check, antiviruses installs , etc.
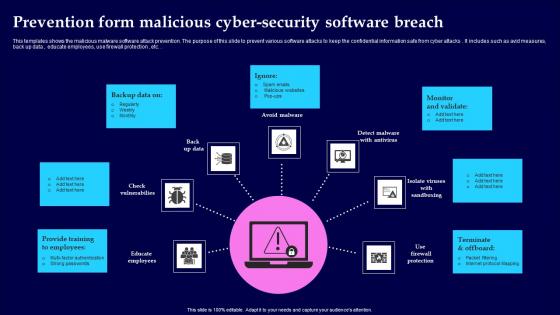
Prevention Form Malicious Cyber Security Software Breach Portrait Pdf
This templates shows the malicious malware software attack prevention. The purpose of this slide to prevent various software attacks to keep the confidential information safe from cyber attacks. It includes such as avid measures, back up data , educate employees, use firewall protection , etc. Showcasing this set of slides titled Prevention Form Malicious Cyber Security Software Breach Portrait Pdf The topics addressed in these templates are Provide Training, Monitor And Validate, Terminate And Offboard All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This templates shows the malicious malware software attack prevention. The purpose of this slide to prevent various software attacks to keep the confidential information safe from cyber attacks. It includes such as avid measures, back up data , educate employees, use firewall protection , etc.
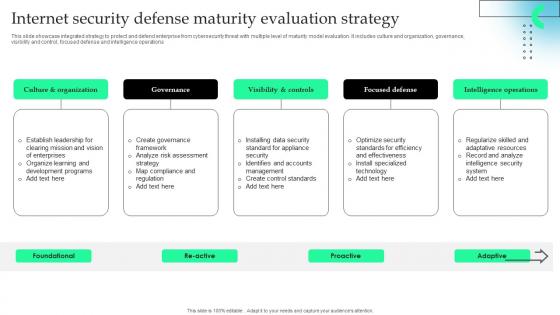
Internet Security Defense Maturity Evaluation Strategy Information Pdf
This slide showcase integrated strategy to protect and defend enterprise from cybersecurity threat with multiple level of maturity model evaluation. It includes culture and organization, governance, visibility and control, focused defense and intelligence operations.Pitch your topic with ease and precision using this Internet Security Defense Maturity Evaluation Strategy Information Pdf This layout presents information on Visibility Controls, Focused Defense, Intelligence Operations It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide showcase integrated strategy to protect and defend enterprise from cybersecurity threat with multiple level of maturity model evaluation. It includes culture and organization, governance, visibility and control, focused defense and intelligence operations.
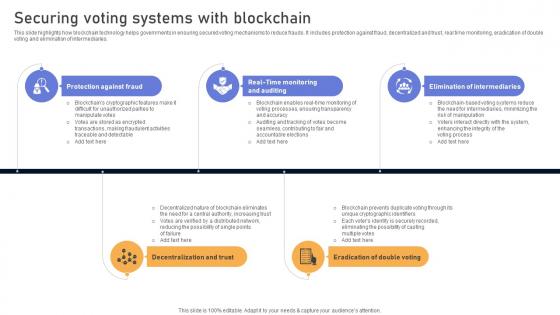
Comprehensive Look At Blockchain Securing Voting Systems With Blockchain BCT SS V
This slide highlights how blockchain technology helps governments in ensuring secured voting mechanisms to reduce frauds. It includes protection against fraud, decentralized and trust, real time monitoring, eradication of double voting and elimination of intermediaries. Get a simple yet stunning designed Comprehensive Look At Blockchain Securing Voting Systems With Blockchain BCT SS V. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Comprehensive Look At Blockchain Securing Voting Systems With Blockchain BCT SS V can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide highlights how blockchain technology helps governments in ensuring secured voting mechanisms to reduce frauds. It includes protection against fraud, decentralized and trust, real time monitoring, eradication of double voting and elimination of intermediaries.
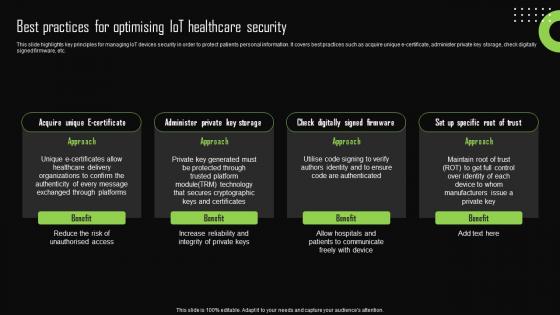
Best Practices For Optimising Iot Healthcare Security Iot Device Management Professional Pdf
This slide highlights key principles for managing IoT devices security in order to protect patients personal information. It covers best practices such as acquire unique e-certificate, administer private key storage, check digitally signed firmware, etc. There are so many reasons you need a Best Practices For Optimising Iot Healthcare Security Iot Device Management Professional Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide highlights key principles for managing IoT devices security in order to protect patients personal information. It covers best practices such as acquire unique e-certificate, administer private key storage, check digitally signed firmware, etc.

Visionary Guide To Blockchain Securing Voting Systems With Blockchain BCT SS V
This slide highlights how blockchain technology helps governments in ensuring secured voting mechanisms to reduce frauds. It includes protection against fraud, decentralized and trust, real time monitoring, eradication of double voting and elimination of intermediaries. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Visionary Guide To Blockchain Securing Voting Systems With Blockchain BCT SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide highlights how blockchain technology helps governments in ensuring secured voting mechanisms to reduce frauds. It includes protection against fraud, decentralized and trust, real time monitoring, eradication of double voting and elimination of intermediaries.
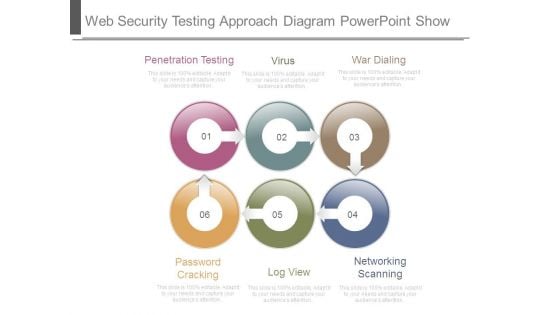
Web Security Testing Approach Diagram Powerpoint Show
This is a web security testing approach diagram powerpoint show. This is a six stage process. The stages in this process are penetration testing, virus, war dialing, password cracking, log view, networking scanning.
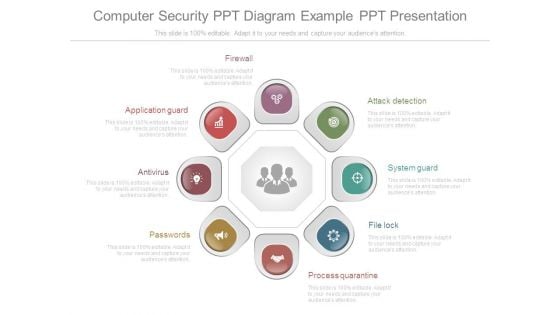
Computer Security Ppt Diagram Example Ppt Presentation
This is a computer security ppt diagram example ppt presentation. This is a eight stage process. The stages in this process are application guard, antivirus, passwords, firewall, attack detection, system guard, file lock, process quarantine.
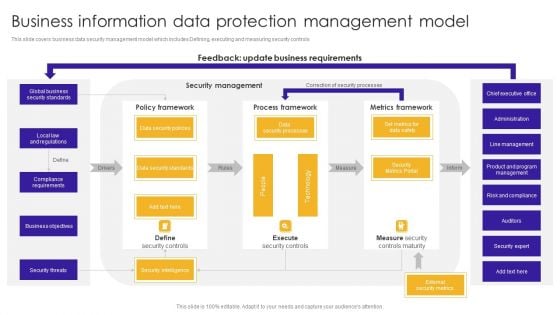
Business Information Data Protection Management Model Structure PDF
This slide covers business data security management model which includes Defining, executing and measuring security controls.Pitch your topic with ease and precision using this Business Information Data Protection Management Model Structure PDF. This layout presents information on Compliance Requirements, Security Standards, Controls Maturity. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
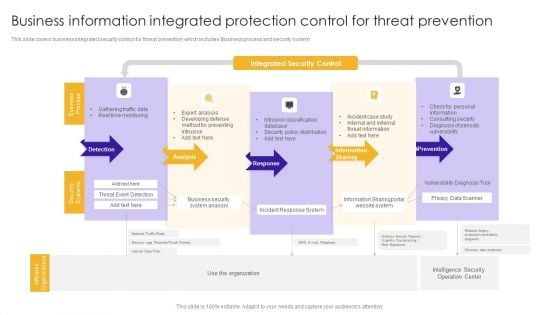
Business Information Integrated Protection Control For Threat Prevention Graphics PDF
This slide covers business integrated security control for threat prevention which includes Business process and security system.Pitch your topic with ease and precision using this Business Information Integrated Protection Control For Threat Prevention Graphics PDF. This layout presents information on Incident Response, Security Policy Distribution, Threat Information. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
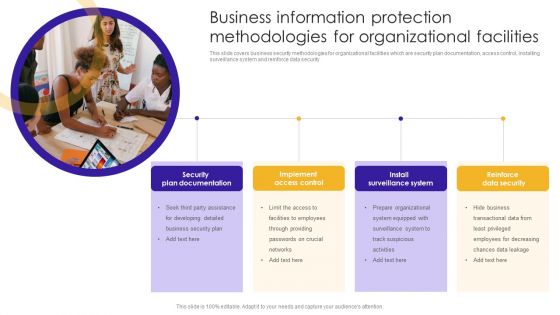
Business Information Protection Methodologies For Organizational Facilities Demonstration PDF
This slide covers business security methodologies for organizational facilities which are security plan documentation, access control, installing surveillance system and reinforce data security.Presenting Business Information Protection Methodologies For Organizational Facilities Demonstration PDF to dispense important information. This template comprises one stage. It also presents valuable insights into the topics including Plan Documentation, Implement Access, Surveillance System. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
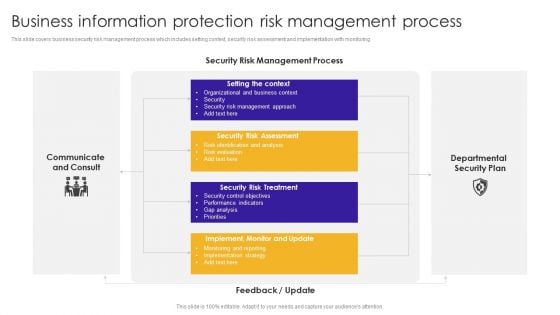
Business Information Protection Risk Management Process Structure PDF
This slide covers business security risk management process which includes setting context, security risk assessment and implementation with monitoring. Pitch your topic with ease and precision using this Business Information Protection Risk Management Process Structure PDF. This layout presents information on Organizational Business, Security Risk Assessment, Performance Indicators. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
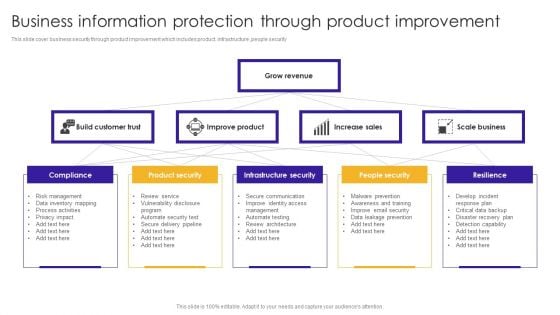
Business Information Protection Through Product Improvement Infographics PDF
This slide cover business security through product improvement which includes product, infrastructure ,people security. Pitch your topic with ease and precision using this Business Information Protection Through Product Improvement Infographics PDF. This layout presents information on Improve Product, Scale Business, Infrastructure Security. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
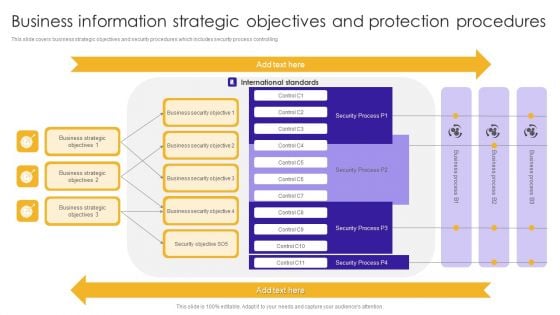
Business Information Strategic Objectives And Protection Procedures Portrait PDF
This slide covers business strategic objectives and security procedures which includes security process controlling.Pitch your topic with ease and precision using this Business Information Strategic Objectives And Protection Procedures Portrait PDF. This layout presents information on Business Security, Business Strategic, International Standards. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Security For Network Protection From Unauthorized Access Vector Icon Ppt PowerPoint Presentation File Summary PDF
Presenting this set of slides with name security for network protection from unauthorized access vector icon ppt powerpoint presentation file summary pdf. This is a three stage process. The stages in this process are security for network protection from unauthorized access vector icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Security Protection With Firewall Vector Icon Ppt PowerPoint Presentation File Graphic Images PDF
Presenting this set of slides with name security protection with firewall vector icon ppt powerpoint presentation file graphic images pdf. The topics discussed in these slide is security protection with firewall vector icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Fire Protection Device On Wall For Security Ppt PowerPoint Presentation Gallery File Formats PDF
Presenting this set of slides with name fire protection device on wall for security ppt powerpoint presentation gallery file formats pdf. The topics discussed in these slide is fire protection device on wall for security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Cloud Data Protection And Security Vector Icon Ppt PowerPoint Presentation File Aids PDF
Presenting cloud data protection and security vector icon ppt powerpoint presentation file aids pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including cloud data protection and security vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Data Privacy Security And Protection Vector Icon Ppt PowerPoint Presentation File Graphic Tips PDF
Presenting data privacy security and protection vector icon ppt powerpoint presentation file graphic tips pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including data privacy security and protection vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Computer Protected With Security System From Online Threat Ppt PowerPoint Presentation File Example Topics PDF
Presenting computer protected with security system from online threat ppt powerpoint presentation file example topics pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including computer protected with security system from online threat. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Health Protection Plan For Secured Life Vector Icon Ppt PowerPoint Presentation Slides Examples PDF
Pitch your topic with ease and precision using this health protection plan for secured life vector icon ppt powerpoint presentation slides examples pdf. This layout presents information on health protection plan for secured life vector icon. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Internet Security Firewall Protection Vector Icon Ppt PowerPoint Presentation Pictures Smartart PDF
Presenting internet security firewall protection vector icon ppt powerpoint presentation pictures smartart pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including internet security firewall protection vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Protection Vector Showing Secured Bitcoin With Dollar Symbol Ppt PowerPoint Presentation Infographic Template Icon PDF
Showcasing this set of slides titled protection vector showing secured bitcoin with dollar symbol ppt powerpoint presentation infographic template icon pdf. The topics addressed in these templates are protection vector showing secured bitcoin with dollar symbol. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
IT Security Protection For PC Vector Icon Ppt PowerPoint Presentation File Guide PDF
Presenting it security protection for pc vector icon ppt powerpoint presentation file guide pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including it security protection for pc vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Person Using Smart Phone With Security Protection Ppt Portfolio Templates PDF
Presenting person using smart phone with security protection ppt portfolio templates pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including person using smart phone with security protection. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Smart Phone With Various Security Features For Data Protection Ppt Outline Gallery PDF
Presenting smart phone with various security features for data protection ppt outline gallery pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including smart phone with various security features for data protection. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Network Protection With Firewall Security System Ppt PowerPoint Presentation File Pictures PDF
Presenting network protection with firewall security system ppt powerpoint presentation file pictures pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including network protection with firewall security system. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Security For Cloud Based Systems Icon For Data Protection Themes PDF
Showcasing this set of slides titled Security For Cloud Based Systems Icon For Data Protection Themes PDF. The topics addressed in these templates are Security For Cloud, Based Systems Icon, For Data Protection . All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Bring Your Own Device Security Policies For Device Protection Icon Designs PDF
Presenting Bring Your Own Device Security Policies For Device Protection Icon Designs PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Bring Your Own, Device Security Policies, Device Protection. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
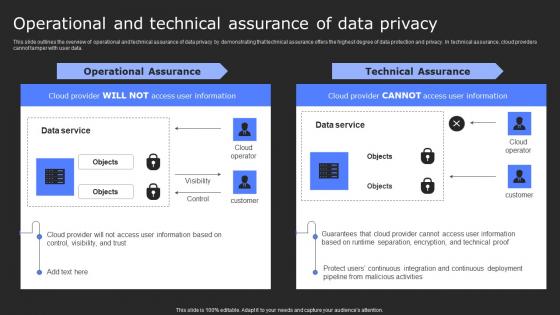
Operational And Technical Assurance Of Data Privacy Secure Computing Framework Mockup Pdf
This slide outlines the overview of operational and technical assurance of data privacy by demonstrating that technical assurance offers the highest degree of data protection and privacy. In technical assurance, cloud providers cannot tamper with user data. Get a simple yet stunning designed Operational And Technical Assurance Of Data Privacy Secure Computing Framework Mockup Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Operational And Technical Assurance Of Data Privacy Secure Computing Framework Mockup Pdf can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide outlines the overview of operational and technical assurance of data privacy by demonstrating that technical assurance offers the highest degree of data protection and privacy. In technical assurance, cloud providers cannot tamper with user data.
Protection Working Management Chart Powerpoint Slide Inspiration
This is a protection working management chart powerpoint slide inspiration. This is a six stage process. The stages in this process are protection, organization, human, employee benefits, business protection, technology.

Protect Money Future PowerPoint Template 0610
Protection of money. Isolated 3D image on white background Crunch the data with our Protect Money Future PowerPoint Template 0610. Derive accurate conclusions with your ideas.
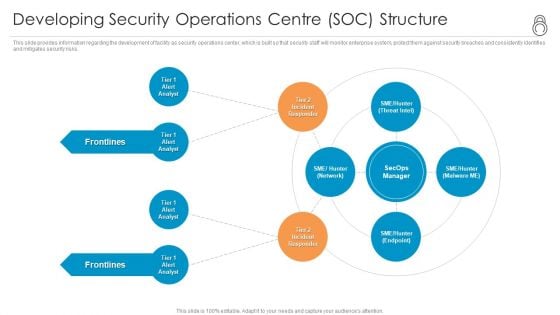
Enhanced Protection Corporate Event Administration Developing Security Operations Centre SOC Structure Formats PDF
This slide provides information regarding the development of facility as security operations center, which is built so that security staff will monitor enterprise system, protect them against security breaches and consistently identifies and mitigates security risks. Presenting enhanced protection corporate event administration developing security operations centre soc structure formats pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like developing security operations centre soc structure. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
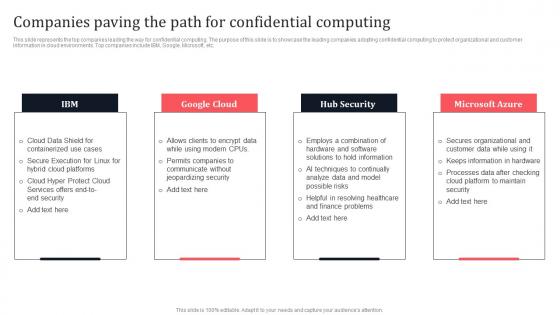
Companies Paving The Path For Confidential Computing Secure Multi Party Elements Pdf
This slide represents the top companies leading the way for confidential computing. The purpose of this slide is to showcase the leading companies adopting confidential computing to protect organizational and customer information in cloud environments. Top companies include IBM, Google, Microsoft, etc. There are so many reasons you need a Companies Paving The Path For Confidential Computing Secure Multi Party Elements Pdf The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide represents the top companies leading the way for confidential computing. The purpose of this slide is to showcase the leading companies adopting confidential computing to protect organizational and customer information in cloud environments. Top companies include IBM, Google, Microsoft, etc.
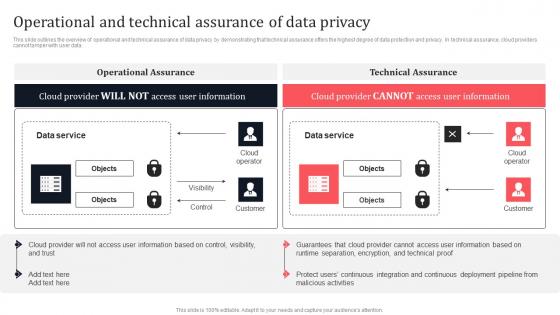
Operational And Technical Assurance Of Data Privacy Secure Multi Party Professional Pdf
This slide outlines the overview of operational and technical assurance of data privacy by demonstrating that technical assurance offers the highest degree of data protection and privacy. In technical assurance, cloud providers cannot tamper with user data. There are so many reasons you need a Operational And Technical Assurance Of Data Privacy Secure Multi Party Professional Pdf The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide outlines the overview of operational and technical assurance of data privacy by demonstrating that technical assurance offers the highest degree of data protection and privacy. In technical assurance, cloud providers cannot tamper with user data.
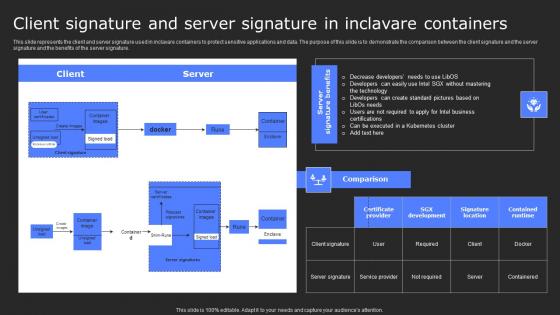
Client Signature And Server Signature In Secure Computing Framework Themes Pdf
This slide represents the client and server signature used in inclavare containers to protect sensitive applications and data. The purpose of this slide is to demonstrate the comparison between the client signature and the server signature and the benefits of the server signature. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Client Signature And Server Signature In Secure Computing Framework Themes Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide represents the client and server signature used in inclavare containers to protect sensitive applications and data. The purpose of this slide is to demonstrate the comparison between the client signature and the server signature and the benefits of the server signature.
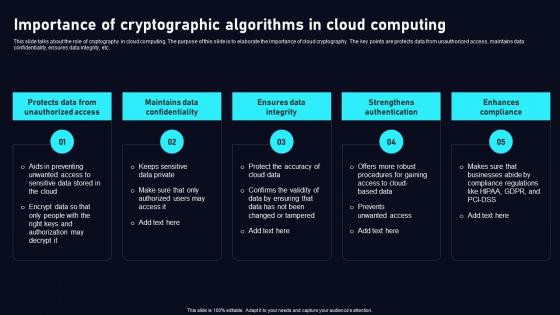
Importance Of Cryptographic Algorithms Cloud Data Security Using Cryptography Graphics Pdf
This slide talks about the role of cryptography in cloud computing. The purpose of this slide is to elaborate the importance of cloud cryptography. The key points are protects data from unauthorized access, maintains data confidentiality, ensures data integrity, etc. Boost your pitch with our creative Importance Of Cryptographic Algorithms Cloud Data Security Using Cryptography Graphics Pdf. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide talks about the role of cryptography in cloud computing. The purpose of this slide is to elaborate the importance of cloud cryptography. The key points are protects data from unauthorized access, maintains data confidentiality, ensures data integrity, etc.
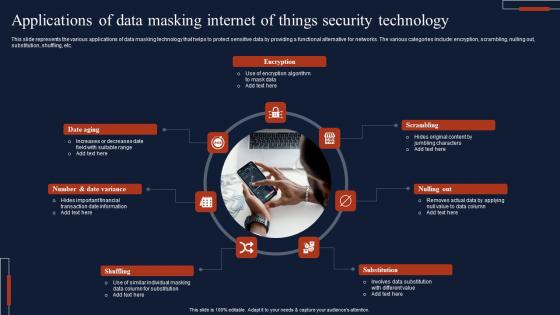
Applications Of Data Masking Internet Of Things Security Technology Topics Pdf
This slide represents the various applications of data masking technology that helps to protect sensitive data by providing a functional alternative for networks. The various categories include encryption, scrambling, nulling out, substitution, shuffling, etc. Showcasing this set of slides titled Applications Of Data Masking Internet Of Things Security Technology Topics Pdf The topics addressed in these templates are Encryption, Scrambling, Substitution, Shuffling All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide represents the various applications of data masking technology that helps to protect sensitive data by providing a functional alternative for networks. The various categories include encryption, scrambling, nulling out, substitution, shuffling, etc.
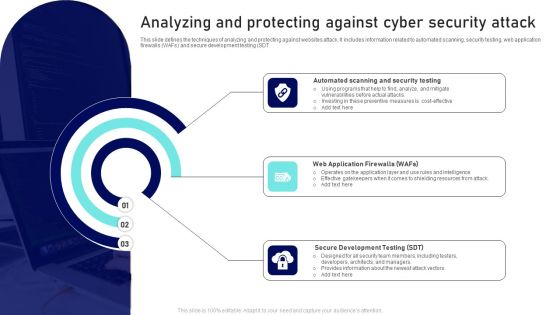
Analyzing And Protecting Against Cyber Security Attack Ppt Pictures Background Designs PDF
This slide defines the techniques of analyzing and protecting against websites attack. It includes information related to automated scanning, security testing, web application firewalls WAFs and secure development testing SDT. Presenting Analyzing And Protecting Against Cyber Security Attack Ppt Pictures Background Designs PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Web Application Firewalls, Secure Development Testing, Automated Scanning, Security Testing. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Online Security Cycle With Protect And Detect Ppt PowerPoint Presentation File Pictures PDF
Presenting this set of slides with name online security cycle with protect and detect ppt powerpoint presentation file pictures pdf. This is a four stage process. The stages in this process are react, detect, protect. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Develop Corporate Cyber Security Risk Mitigation Plan Contact Us For Organization Cyber Protection Services Portrait PDF
Deliver an awe-inspiring pitch with this creative develop corporate cyber security risk mitigation plan contact us for organization cyber protection services portrait pdf bundle. Topics like contact us, organization, cyber protection services can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Manufacturing And Production Action Plan With Effective Verification Ppt PowerPoint Presentation Layouts Icon PDF
Pitch your topic with ease and precision using this manufacturing and production action plan with effective verification ppt powerpoint presentation layouts icon pdf. This layout presents information on product, process system, root cause analysis reviewed, effectiveness verification, manufacturing production action plan with effective verification. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Suitability Standard Pmp Analysis It Project Experience Tracking For Pmp Eligibility Verification Introduction PDF
This slide provides information regarding project experience tracking for PMP eligibility verification by tracking various projects in which applicant was involved. Deliver an awe inspiring pitch with this creative suitability standard pmp analysis it project experience tracking for pmp eligibility verification introduction pdf bundle. Topics like project experience tracking for pmp eligibility verification can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Project Management Professional Assessment Process IT Project Experience Tracking For PMP Eligibility Verification Introduction PDF
This slide provides information regarding project experience tracking for PMP eligibility verification by tracking various projects in which applicant was involved. Deliver an awe inspiring pitch with this creative project management professional assessment process it project experience tracking for pmp eligibility verification introduction pdf bundle. Topics like project experience tracking for pmp eligibility verification can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Endpoint Security Protection Services Ppt PowerPoint Presentation Professional Backgrounds Cpb Pdf
Presenting this set of slides with name endpoint security protection services ppt powerpoint presentation professional backgrounds cpb pdf. This is an editable Powerpoint six stages graphic that deals with topics like endpoint security protection services to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Data Protection Security Controls Ppt PowerPoint Presentation File Designs Cpb Pdf
Presenting this set of slides with name data protection security controls ppt powerpoint presentation file designs cpb pdf. This is an editable Powerpoint five stages graphic that deals with topics like data protection security controls to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Network Protection Icon For Securing Customer Information Ppt PowerPoint Presentation Icon Pictures PDF
Persuade your audience using this network protection icon for securing customer information ppt powerpoint presentation icon pictures pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including network protection icon for securing customer information. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Smart Phone Application Protected With IT Security Software Ppt PowerPoint Presentation File Graphic Images PDF
Persuade your audience using this smart phone application protected with it security software ppt powerpoint presentation file graphic images pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including smart phone application protected with it security software. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Laptop Protection With Secured Antivirus Vector Icon Ppt PowerPoint Presentation Icon Graphics PDF
Persuade your audience using this laptop protection with secured antivirus vector icon ppt powerpoint presentation icon graphics pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including laptop protection with secured antivirus vector icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Network Security Protection Ensuring Safety From Online Threat Ppt PowerPoint Presentation Portfolio Influencers PDF
Persuade your audience using this network security protection ensuring safety from online threat ppt powerpoint presentation portfolio influencers pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including network security protection ensuring safety from online threat. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Virtual Private Network With Internet Security Firewall Protection Ppt PowerPoint Presentation File Master Slide PDF
Persuade your audience using this virtual private network with internet security firewall protection ppt powerpoint presentation file master slide pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including virtual private network with internet security firewall protection. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.


 Continue with Email
Continue with Email

 Home
Home


































