Authentication
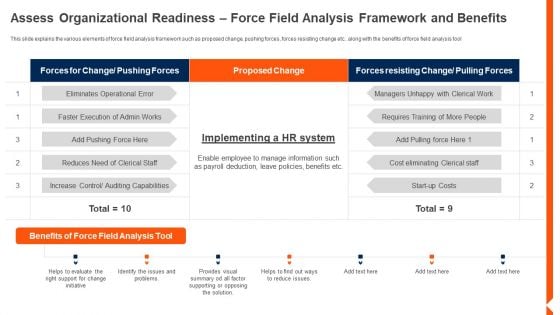
Solution Monitoring Verification Assess Organizational Readiness Force Field Analysis Slides PDF
This slide explains the various elements of force field analysis framework such as proposed change, pushing forces, forces resisting change etc.. along with the benefits of force field analysis tool Deliver and pitch your topic in the best possible manner with this solution monitoring verification assess organizational readiness force field analysis slides pdf Use them to share invaluable insights on capabilities, control, eliminates and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
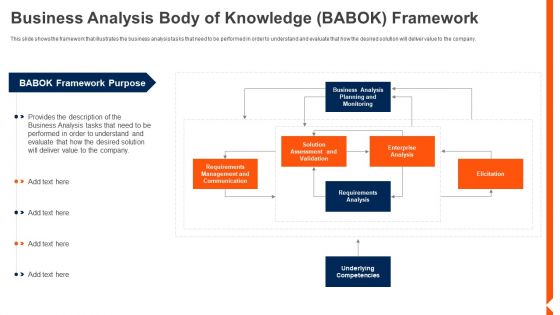
Solution Monitoring Verification Business Analysis Body Of Knowledge BABOK Download PDF
This slide shows the framework that illustrates the business analysis tasks that need to be performed in order to understand and evaluate that how the desired solution will deliver value to the company. Deliver an awe inspiring pitch with this creative solution monitoring verification business analysis body of knowledge babok download pdf bundle. Topics like performed, value, analysis, tasks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
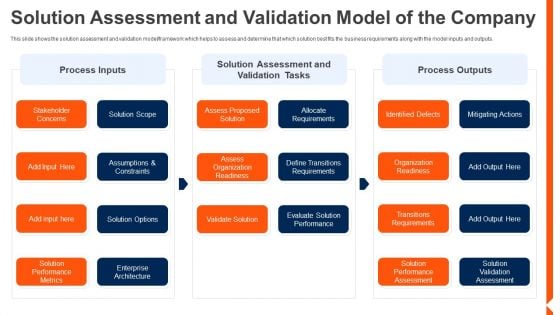
Solution Monitoring Verification Solution Assessment And Validation Model Company Elements PDF
This slide shows the solution assessment and validation model framework which helps to assess and determine that which solution best fits the business requirements along with the model inputs and outputs. Deliver an awe inspiring pitch with this creative solution monitoring verification solution assessment and validation model company elements pdf bundle. Topics like process inputs, assessment, validation tasks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
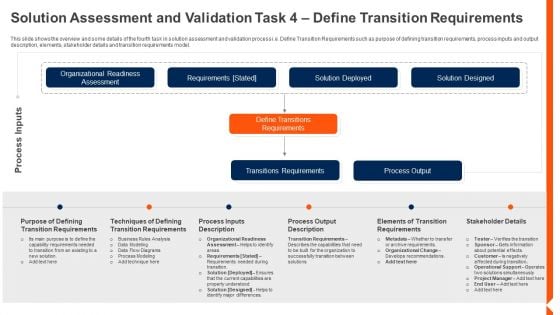
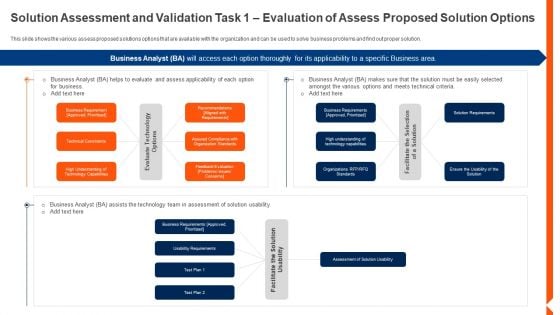
Solution Monitoring Verification Solution Assessment And Validation Task Define Pictures PDF
This slide shows the various assess proposed solutions options that are available with the organization and can be used to solve business problems and find out proper solution. Deliver an awe inspiring pitch with this creative solution monitoring verification solution assessment and validation task define pictures pdf bundle. Topics like recommendations, business, requirements can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Hotel Protection And Security Ppt PowerPoint Presentation Complete Deck With Slides
Boost your confidence and team morale with this well-structured Hotel Protection And Security Ppt PowerPoint Presentation Complete Deck With Slides. This prefabricated set gives a voice to your presentation because of its well-researched content and graphics. Our experts have added all the components very carefully, thus helping you deliver great presentations with a single click. Not only that, it contains a set of eleven slides that are designed using the right visuals, graphics, etc. Various topics can be discussed, and effective brainstorming sessions can be conducted using the wide variety of slides added in this complete deck. Apart from this, our PPT design contains clear instructions to help you restructure your presentations and create multiple variations. The color, format, design anything can be modified as deemed fit by the user. Not only this, it is available for immediate download. So, grab it now.
Business Framework Risk Protection Factors PowerPoint Presentation
A white tube with blue wire has been used to decorate this Power point diagram template slide. This PPT slide contains the concept of risk protection in any field. This PPT slide can be used for business risk related topics. Build an exclusive presentation for your business presentation.
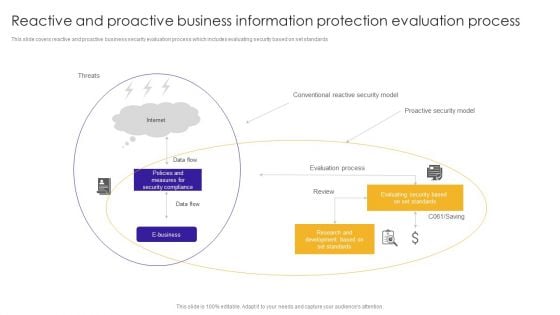
Reactive And Proactive Business Information Protection Evaluation Process Sample PDF
This slide covers reactive and proactive business security evaluation process which includes evaluating security based on set standards. Persuade your audience using this Reactive And Proactive Business Information Protection Evaluation Process Sample PDF. This PPT design covers one stage, thus making it a great tool to use. It also caters to a variety of topics including Conventional Reactive, Proactive Security, Evaluation Process. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
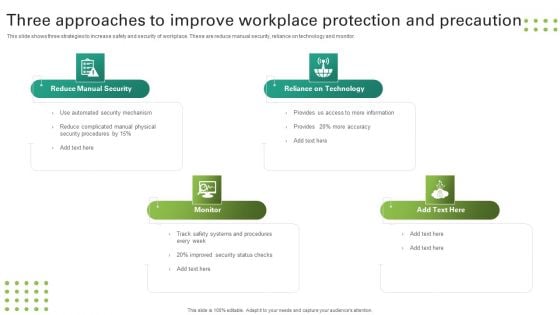
Three Approaches To Improve Workplace Protection And Precaution Background PDF
This slide shows three strategies to increase safety and security of workplace. These are reduce manual security, reliance on technology and monitor. Persuade your audience using this Three Approaches To Improve Workplace Protection And Precaution Background PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Reduce Manual Security, Reliance On Technology, Monitor. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
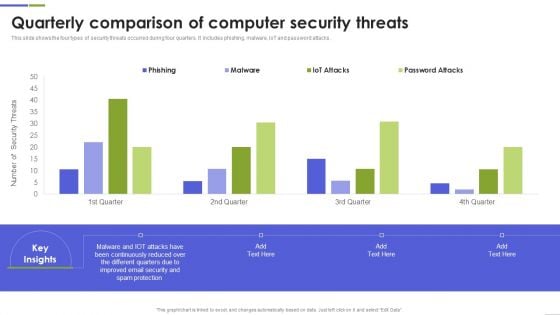
Quarterly Comparison Of Computer Security Threats Mockup PDF
This slide shows the four types of security threats occurred during four quarters. It includes phishing, malware, IoT and password attacks. Pitch your topic with ease and precision using this Quarterly Comparison Of Computer Security Threats Mockup PDF This layout presents information on Continuously Reduced, Different Quarters, Spam Protection It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
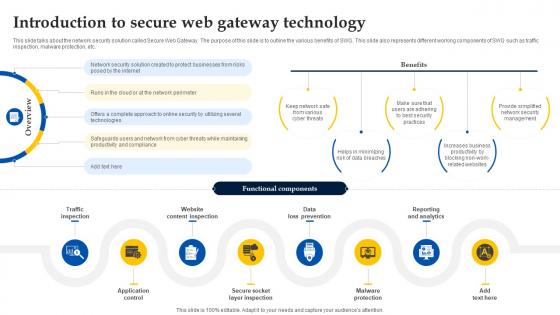
Web Access Control Solution Introduction To Secure Web Gateway Technology
This slide talks about the network security solution called Secure Web Gateway. The purpose of this slide is to outline the various benefits of SWG. This slide also represents different working components of SWG such as traffic inspection, malware protection, etc. Retrieve professionally designed Web Access Control Solution Introduction To Secure Web Gateway Technology to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide talks about the network security solution called Secure Web Gateway. The purpose of this slide is to outline the various benefits of SWG. This slide also represents different working components of SWG such as traffic inspection, malware protection, etc.

Winning Strategies To Improve Organization Data Security Pictures PDF
The following slide highlights a winning strategy to avoid data security breach in the organization. Businesses can protect the confidential data by following strategies such as security audit, establishing strong password, back up sensitive data, and improve cyber-security. Presenting Winning Strategies To Improve Organization Data Security Pictures PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Security Audit, Establish Strong, Sensitive Data. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Solution Monitoring Verification Description Of BABOK Areas Solution Assessment Brochure PDF
This slide shows the description of a BABOK Business Analysis Body of Knowledge area i.e. solution assessment and validation whose main purpose is to assess and determine that which solution best fits the business requirements along with elements and techniques at each stage. Presenting solution monitoring verification description of babok areas solution assessment brochure pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like proposed, requirements, organizational. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
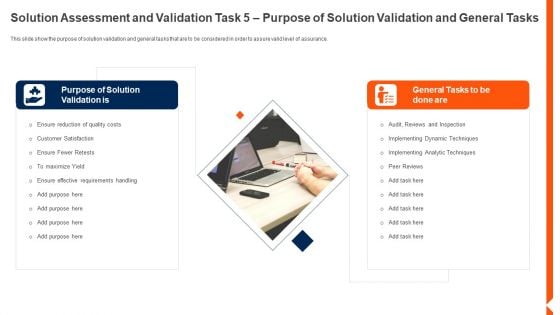
Solution Monitoring Verification Solution Assessment And Validation Validation General Background PDF
This slide show the purpose of solution validation and general tasks that are to be considered in order to assure valid level of assurance. Presenting solution monitoring verification solution assessment and validation validation general background pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like purpose, solution, requirements. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
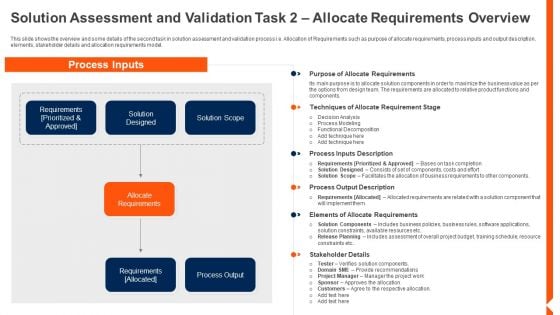
Solution Monitoring Verification Solution Assessment And Validation Task Allocate Portrait PDF
This slide shows the overview and some details of the second task in solution assessment and validation process i.e. Allocation of Requirements such as purpose of allocate requirements, process inputs and output description, elements, stakeholder details and allocation requirements model. Deliver an awe inspiring pitch with this creative solution monitoring verification solution assessment and validation task allocate portrait pdf bundle. Topics like allocate requirements, techniques, process, description can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Solution Monitoring Verification Solution Assessment And Validation Task Assess Sample PDF
This slide shows the overview and some details of the first task in solution assessment and validation process i.e. Assess Proposed Solution such as purpose of assessed proposed solution, process inputs and output description, elements, stakeholder details and assess proposed solution model. Deliver and pitch your topic in the best possible manner with this solution monitoring verification solution assessment and validation task assess sample pdf. Use them to share invaluable insights on techniques, purpose, process and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

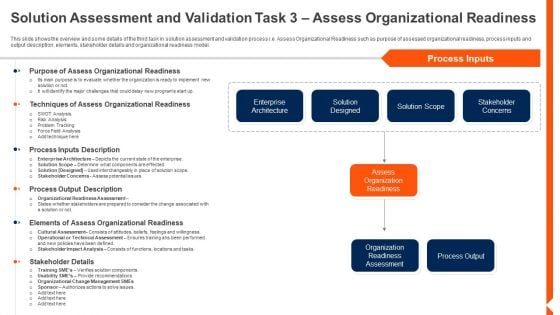
Solution Monitoring Verification Solution Assessment And Validation Task Evaluating Graphics PDF
This slide shows the overview and some details of the third task in solution assessment and validation process i.e. Assess Organizational Readiness such as purpose of assessed organizational readiness, process inputs and output description, elements, stakeholder details and organizational readiness model. Deliver and pitch your topic in the best possible manner with this solution monitoring verification solution assessment and validation task evaluating graphics pdf. Use them to share invaluable insights on organization, enterprise, stakeholder concerns and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Solution Monitoring Verification Solution Assessment And Validation Task Options Graphics PDF
This slide shows the overview and some details of the fourth task in solution assessment and validation process i.e. Define Transition Requirements such as purpose of defining transition requirements, process inputs and output description, elements, stakeholder details and transition requirements model. Deliver an awe inspiring pitch with this creative solution monitoring verification solution assessment and validation task options graphics pdf bundle. Topics like techniques, requirements, process can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
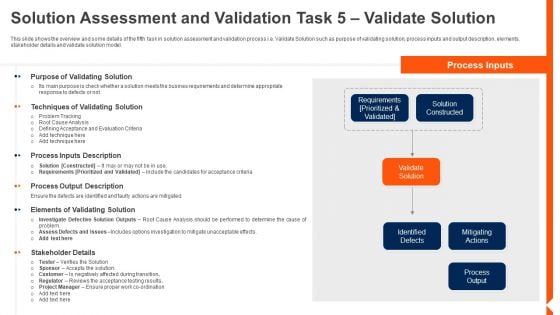
Solution Monitoring Verification Solution Assessment And Validation Task Validate Solution Brochure PDF
This slide shows the overview and some details of the sixth and the last task in solution assessment and validation process i.e. Evaluating Solution Performance such as purpose of evaluating solution performance , process inputs and output description, elements, stakeholder details and evaluating solution performance model. Deliver and pitch your topic in the best possible manner with this solution monitoring verification solution assessment and validation task validate solution brochure pdf. Use them to share invaluable insights on performance, purpose, techniques and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
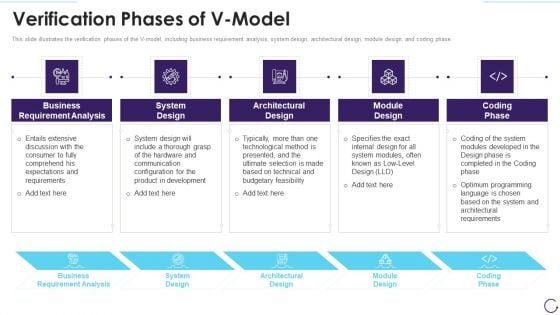
Application Development Life Cycle Verification Phases Of V Model Inspiration PDF
This slide illustrates the verification phases of the V model, including business requirement analysis, system design, architectural design, module design, and coding phase. Presenting application development life cycle validation phases of v model introduction pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like pros of rapid application development model. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
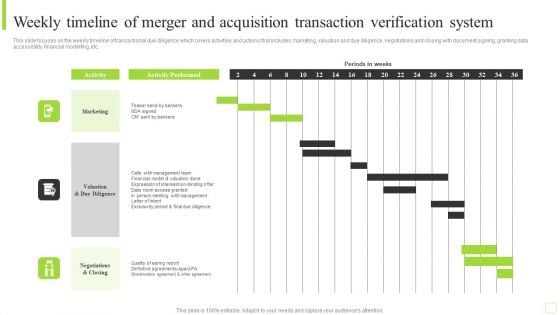
Weekly Timeline Of Merger And Acquisition Transaction Verification System Brochure PDF
This slide focuses on the weekly timeline of transactional due diligence which covers activities and actions that includes marketing, valuation and due diligence, negotiations and closing with document signing, granting data accessibility, financial modelling, etc. Pitch your topic with ease and precision using this Weekly Timeline Of Merger And Acquisition Transaction Verification System Brochure PDF. This layout presents information on Marketing, Management Team, Financial Model. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
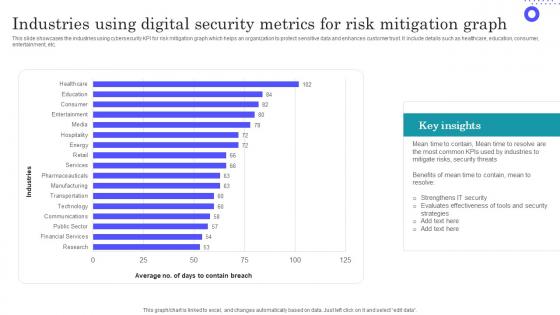
Industries Using Digital Security Metrics For Risk Mitigation Graph Inspiration Pdf
Showcasing this set of slides titled Industries Using Digital Security Metrics For Risk Mitigation Graph Inspiration Pdf The topics addressed in these templates are Evaluates Effectiveness, Most Common, Key Insights All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcases the industries using cybersecurity KPI for risk mitigation graph which helps an organization to protect sensitive data and enhances customer trust. It include details such as healthcare, education, consumer, entertainment, etc.
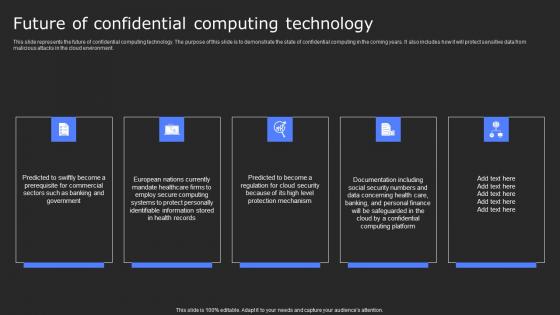
Future Of Confidential Computing Technology Secure Computing Framework Ideas Pdf
This slide represents the future of confidential computing technology. The purpose of this slide is to demonstrate the state of confidential computing in the coming years. It also includes how it will protect sensitive data from malicious attacks in the cloud environment. Presenting this PowerPoint presentation, titled Future Of Confidential Computing Technology Secure Computing Framework Ideas Pdf, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Future Of Confidential Computing Technology Secure Computing Framework Ideas Pdf. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Future Of Confidential Computing Technology Secure Computing Framework Ideas Pdf that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide represents the future of confidential computing technology. The purpose of this slide is to demonstrate the state of confidential computing in the coming years. It also includes how it will protect sensitive data from malicious attacks in the cloud environment.

Best Practices For Cyber Safety At Job Safety Infographics PDF
This slide covers the best practices for cyber safety at workplace which includes protecting the data, using strong password protection, connecting to the secure wi-fi, investing in security systems, etc. Presenting best practices for cyber safety at job safety infographics pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including protecting data, connect to secure wi fi, invest in security systems, strong password protection. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
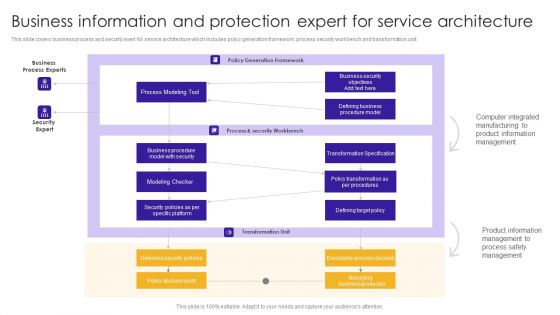
Business Information And Protection Expert For Service Architecture Demonstration PDF
This slide covers business process and security exert for service architecture which includes policy generation framework, process security workbench and transformation unit.Showcasing this set of slides titled Business Information And Protection Expert For Service Architecture Demonstration PDF. The topics addressed in these templates are Business Process, Computer Integrated, Product Information. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
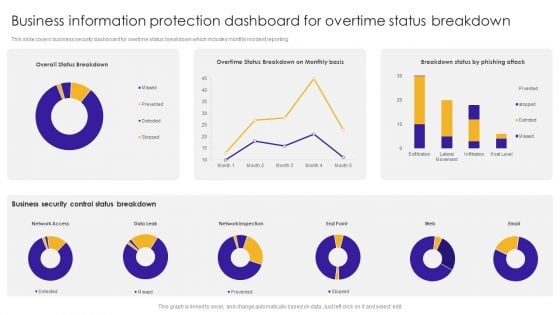
Business Information Protection Dashboard For Overtime Status Breakdown Introduction PDF
This slide covers business security dashboard for overtime status breakdown which includes monthly incident reporting.Pitch your topic with ease and precision using this Business Information Protection Dashboard For Overtime Status Breakdown Introduction PDF. This layout presents information on Business Security, Control Status Breakdown, Network Inspection. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
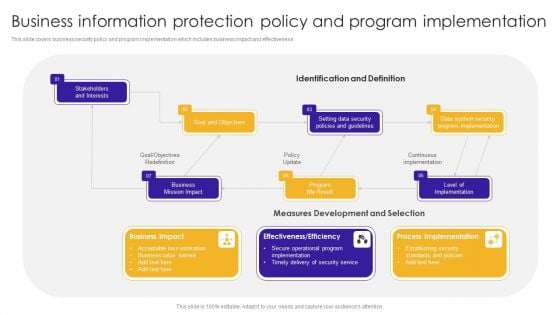
Business Information Protection Policy And Program Implementation Brochure PDF
This slide covers business security policy and program implementation which includes business impact and effectiveness.Showcasing this set of slides titled Business Information Protection Policy And Program Implementation Brochure PDF. The topics addressed in these templates are Acceptable Loss, Business Value Earned, Secure Operational. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
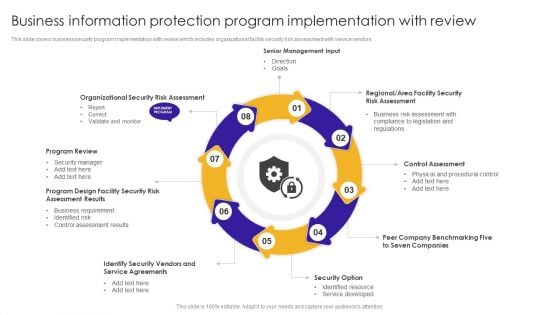
Business Information Protection Program Implementation With Review Information PDF
This slide covers business security program implementation with review which includes organizational facility security risk assessment with service vendors.Persuade your audience using this Business Information Protection Program Implementation With Review Information PDF. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including Program Review, Assessment Results, Business Requirement. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
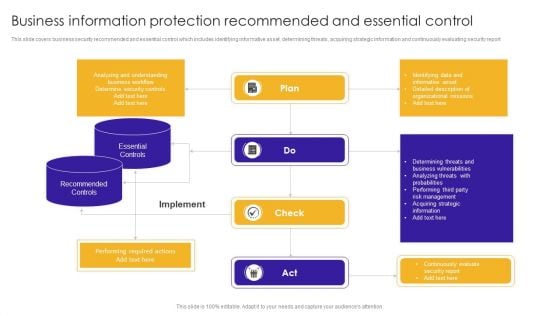
Business Information Protection Recommended And Essential Control Background PDF
This slide covers business security recommended and essential control which includes identifying informative asset, determining threats, acquiring strategic information and continuously evaluating security report. Showcasing this set of slides titled Business Information Protection Recommended And Essential Control Background PDF. The topics addressed in these templates are Determining Threats, Business Vulnerabilities, Risk Management. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
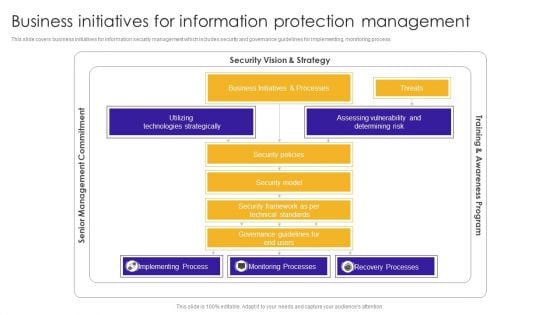
Business Initiatives For Information Protection Management Designs PDF
This slide covers business initiatives for information security management which includes security and governance guidelines for implementing, monitoring process. Pitch your topic with ease and precision using this Business Initiatives For Information Protection Management Designs PDF. This layout presents information on Technologies Strategically, Assessing Vulnerability, Implementing Process. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
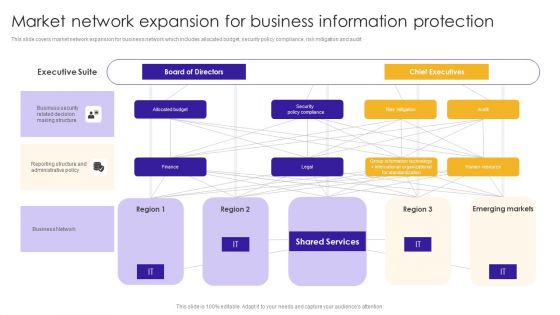
Market Network Expansion For Business Information Protection Sample PDF
This slide covers market network expansion for business network which includes allocated budget, security policy compliance, risk mitigation and audit. Showcasing this set of slides titled Market Network Expansion For Business Information Protection Sample PDF. The topics addressed in these templates are Business Security, Related Decision, Making Structure. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
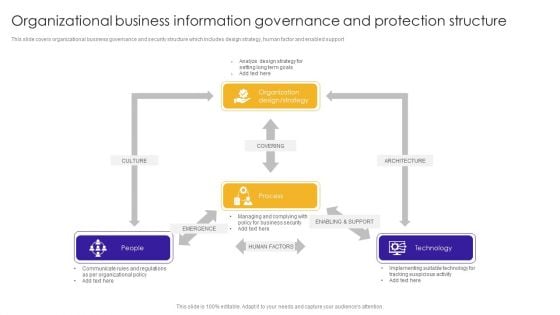
Organizational Business Information Governance And Protection Structure Guidelines PDF
This slide covers organizational business governance and security structure which includes design strategy, human factor and enabled support. Showcasing this set of slides titled Organizational Business Information Governance And Protection Structure Guidelines PDF. The topics addressed in these templates are Communicate Rules, Organizational Policy, Business Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
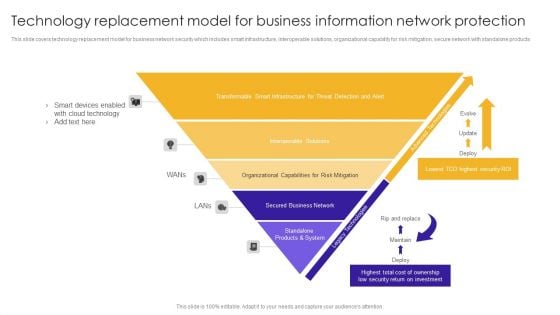
Technology Replacement Model For Business Information Network Protection Structure PDF
This slide covers technology replacement model for business network security which includes smart infrastructure, interoperable solutions, organizational capability for risk mitigation, secure network with standalone products.Showcasing this set of slides titled Technology Replacement Model For Business Information Network Protection Structure PDF. The topics addressed in these templates are Smart Devices, Cloud Technology, Transformable Smart. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Cyber Protection And Precaution Tracking Dashboard Designs PDF
This slide shows the dashboard of cyber safety and security of an organization. It includes risk level, compliance status, tracking and security budget. Showcasing this set of slides titled Cyber Protection And Precaution Tracking Dashboard Designs PDF. The topics addressed in these templates are Risk, Compliance Status, Risk Level. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Solution Monitoring Verification Role Of Business Analyst In Solution Assessment Sample PDF
This slide show the roles and responsibilities of a Business Analyst BA in the process of Solution Assessment and Validation such as developing alternative solutions, promoting the selection of a solution, evaluating the various technology options, monitoring the QA process, communicating the solution impacts to the stakeholders etc. This is a solution monitoring verification role of business analyst in solution assessment sample pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like develop, technology, consideration. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Protection Ppt PowerPoint Presentation Complete With Slides
Improve your presentation delivery using this Protection Ppt PowerPoint Presentation Complete With Slides. Support your business vision and objectives using this well-structured PPT deck. This template offers a great starting point for delivering beautifully designed presentations on the topic of your choice. Comprising twenty three this professionally designed template is all you need to host discussion and meetings with collaborators. Each slide is self-explanatory and equipped with high-quality graphics that can be adjusted to your needs. Therefore, you will face no difficulty in portraying your desired content using this PPT slideshow. This PowerPoint slideshow contains every important element that you need for a great pitch. It is not only editable but also available for immediate download and utilization. The color, font size, background, shapes everything can be modified to create your unique presentation layout. Therefore, download it now.
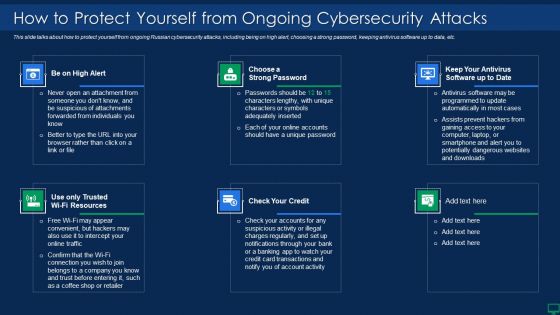
Russian Cyber Attacks On Ukraine IT How To Protect Yourself Summary PDF
This slide talks about how to protect yourself from ongoing Russian cybersecurity attacks, including being on high alert, choosing a strong password, keeping antivirus software up to data, etc. Presenting russian cyber attacks on ukraine it how to protect yourself summary pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like resources, account, potentially. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Future Of Confidential Computing Technology Secure Multi Party Rules Pdf
This slide represents the future of confidential computing technology. The purpose of this slide is to demonstrate the state of confidential computing in the coming years. It also includes how it will protect sensitive data from malicious attacks in the cloud environment. Slidegeeks has constructed Future Of Confidential Computing Technology Secure Multi Party Rules Pdf after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide represents the future of confidential computing technology. The purpose of this slide is to demonstrate the state of confidential computing in the coming years. It also includes how it will protect sensitive data from malicious attacks in the cloud environment.
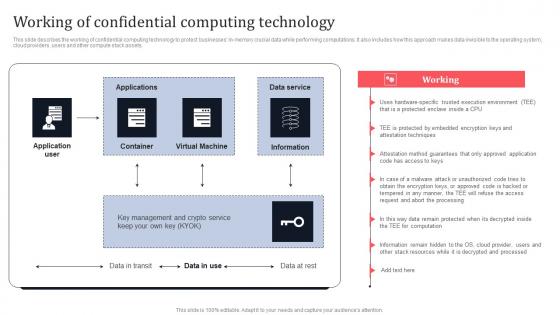
Working Of Confidential Computing Technology Secure Multi Party Information Pdf
This slide describes the working of confidential computing technology to protect businesses in-memory crucial data while performing computations. It also includes how this approach makes data invisible to the operating system, cloud providers, users and other compute stack assets. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Working Of Confidential Computing Technology Secure Multi Party Information Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide describes the working of confidential computing technology to protect businesses in-memory crucial data while performing computations. It also includes how this approach makes data invisible to the operating system, cloud providers, users and other compute stack assets.
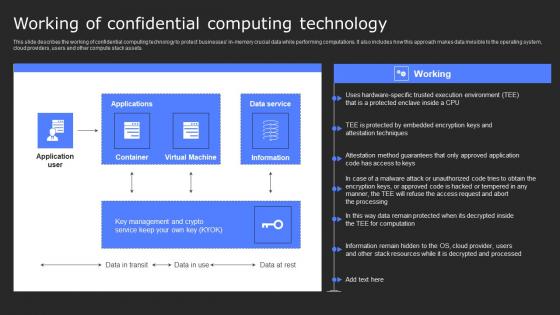
Working Of Confidential Computing Technology Secure Computing Framework Diagrams Pdf
This slide describes the working of confidential computing technology to protect businesses in-memory crucial data while performing computations. It also includes how this approach makes data invisible to the operating system, cloud providers, users and other compute stack assets. Slidegeeks is here to make your presentations a breeze with Working Of Confidential Computing Technology Secure Computing Framework Diagrams Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide describes the working of confidential computing technology to protect businesses in-memory crucial data while performing computations. It also includes how this approach makes data invisible to the operating system, cloud providers, users and other compute stack assets.
Evil Criminal Robbing PowerPoint Icon R
Microsoft PowerPoint Template and Background with man evil criminal robbing a business man Be atypical with our Evil Criminal Robbing PowerPoint Icon R. Sometimes it's better not to confirm.
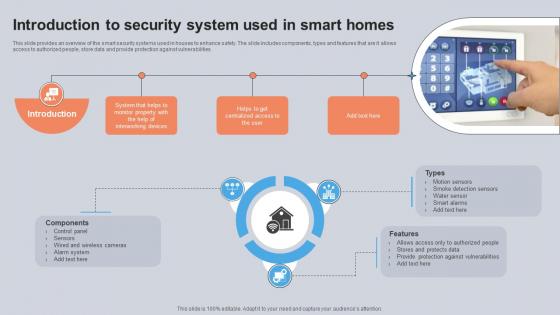
Introduction To Security System Used In Smart Homes Utilizing Smart Appliances IoT SS V
This slide provides an overview of the smart security systems used in houses to enhance safety. The slide includes components, types and features that are it allows access to authorized people, store data and provide protection against vulnerabilities. Create an editable Introduction To Security System Used In Smart Homes Utilizing Smart Appliances IoT SS V that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Introduction To Security System Used In Smart Homes Utilizing Smart Appliances IoT SS V is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide provides an overview of the smart security systems used in houses to enhance safety. The slide includes components, types and features that are it allows access to authorized people, store data and provide protection against vulnerabilities.
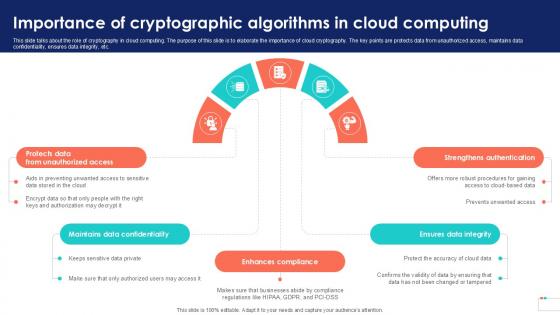
Importance Of Cryptographic Algorithms Data Security In Cloud Computing Ppt Presentation
This slide talks about the role of cryptography in cloud computing. The purpose of this slide is to elaborate the importance of cloud cryptography. The key points are protects data from unauthorized access, maintains data confidentiality, ensures data integrity, etc. Presenting this PowerPoint presentation, titled Importance Of Cryptographic Algorithms Data Security In Cloud Computing Ppt Presentation, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Importance Of Cryptographic Algorithms Data Security In Cloud Computing Ppt Presentation. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Importance Of Cryptographic Algorithms Data Security In Cloud Computing Ppt Presentation that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide talks about the role of cryptography in cloud computing. The purpose of this slide is to elaborate the importance of cloud cryptography. The key points are protects data from unauthorized access, maintains data confidentiality, ensures data integrity, etc.
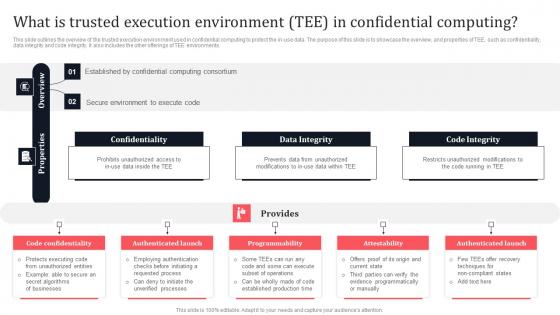
What Is Trusted Execution Environment Tee In Confidential Secure Multi Party Slides Pdf
This slide outlines the overview of the trusted execution environment used in confidential computing to protect the in-use data. The purpose of this slide is to showcase the overview, and properties of TEE, such as confidentiality, data integrity and code integrity. It also includes the other offerings of TEE environments. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our What Is Trusted Execution Environment Tee In Confidential Secure Multi Party Slides Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into What Is Trusted Execution Environment Tee In Confidential Secure Multi Party Slides Pdf This slide outlines the overview of the trusted execution environment used in confidential computing to protect the in-use data. The purpose of this slide is to showcase the overview, and properties of TEE, such as confidentiality, data integrity and code integrity. It also includes the other offerings of TEE environments.
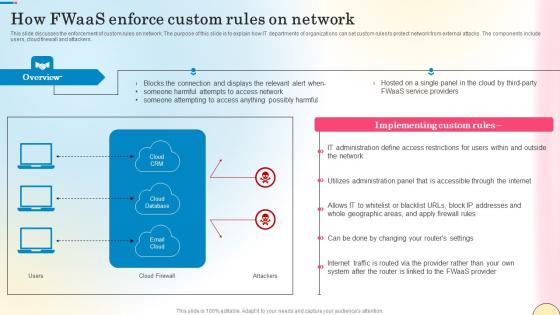
How Fwaas Enforce Custom Rules On Network Network Security Professional Pdf
This slide discusses the enforcement of custom rules on network. The purpose of this slide is to explain how IT departments of organizations can set custom rules to protect network from external attacks. The components include users, cloud firewall and attackers. This How Fwaas Enforce Custom Rules On Network Network Security Professional Pdf is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The How Fwaas Enforce Custom Rules On Network Network Security Professional Pdf features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide discusses the enforcement of custom rules on network. The purpose of this slide is to explain how IT departments of organizations can set custom rules to protect network from external attacks. The components include users, cloud firewall and attackers.
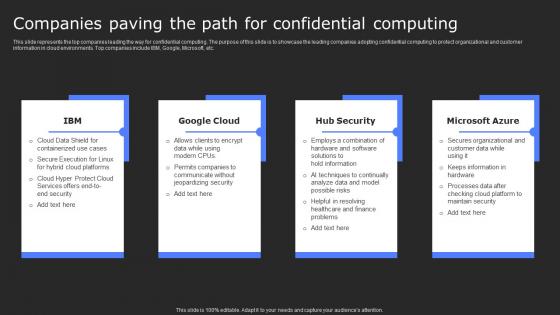
Companies Paving The Path For Confidential Secure Computing Framework Download Pdf
This slide represents the top companies leading the way for confidential computing. The purpose of this slide is to showcase the leading companies adopting confidential computing to protect organizational and customer information in cloud environments. Top companies include IBM, Google, Microsoft, etc. Present like a pro with Companies Paving The Path For Confidential Secure Computing Framework Download Pdf Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide represents the top companies leading the way for confidential computing. The purpose of this slide is to showcase the leading companies adopting confidential computing to protect organizational and customer information in cloud environments. Top companies include IBM, Google, Microsoft, etc.

What Is Trusted Execution Environment Tee In Secure Computing Framework Mockup Pdf
This slide outlines the overview of the trusted execution environment used in confidential computing to protect the in-use data. The purpose of this slide is to showcase the overview, and properties of TEE, such as confidentiality, data integrity and code integrity. It also includes the other offerings of TEE environments. Present like a pro with What Is Trusted Execution Environment Tee In Secure Computing Framework Mockup Pdf Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide outlines the overview of the trusted execution environment used in confidential computing to protect the in-use data. The purpose of this slide is to showcase the overview, and properties of TEE, such as confidentiality, data integrity and code integrity. It also includes the other offerings of TEE environments.

Global Data Security Industry Report Emerging Threat Trends In Cybersecurity Industry IR SS V
The slide presents the latest threat trends in the global cybersecurity industry. The purpose of the slide is to raise awareness about the evolving landscape of cyber threats, which is crucial for individuals and organizations to stay protected. It covers threat such as automotive hacking, cloud services attacks, social engineering attacks, 5g network threats, and ransomware attacks. Slidegeeks is here to make your presentations a breeze with Global Data Security Industry Report Emerging Threat Trends In Cybersecurity Industry IR SS V With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first The slide presents the latest threat trends in the global cybersecurity industry. The purpose of the slide is to raise awareness about the evolving landscape of cyber threats, which is crucial for individuals and organizations to stay protected. It covers threat such as automotive hacking, cloud services attacks, social engineering attacks, 5g network threats, and ransomware attacks.
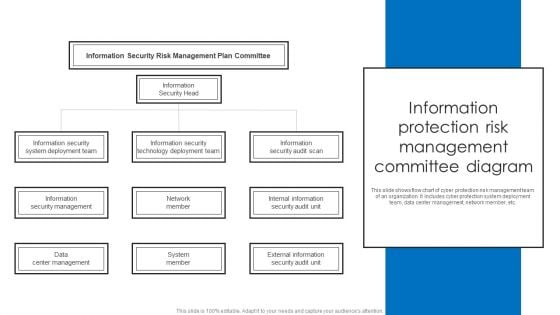
Information Protection Risk Management Committee Diagram Information PDF
This slide shows flow chart of cyber protection risk management team of an organization. It includes cyber protection system deployment team, data center management, network member, etc. Persuade your audience using this Information Protection Risk Management Committee Diagram Information PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Information Security Head, Information Security Audit Scan, Network Member. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Organizational Design Methodologies Powerpoint Guide
This is a organizational design methodologies powerpoint guide. This is a five stage process. The stages in this process are requirements, design, implementation, verification, maintenance.
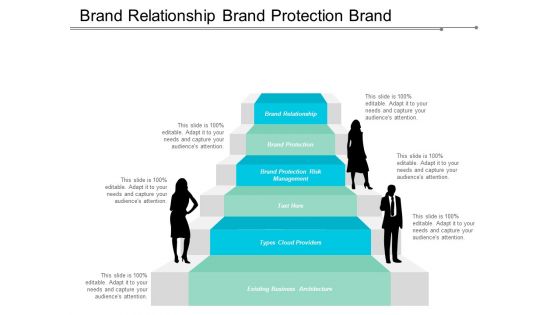
Brand Relationship Brand Protection Brand Protection Risk Management Ppt PowerPoint Presentation Ideas Layout
This is a brand relationship brand protection brand protection risk management ppt powerpoint presentation ideas layout. This is a six stage process. The stages in this process are brand relationship, brand protection, brand protection risk management.
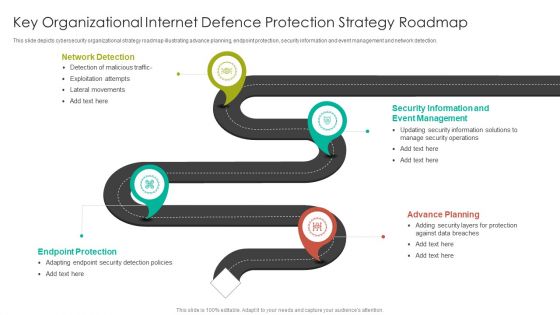
Key Organizational Internet Defence Protection Strategy Roadmap Summary PDF
This slide depicts cybersecurity organizational strategy roadmap illustrating advance planning, endpoint protection, security information and event management and network detection.Persuade your audience using this Key Organizational Internet Defence Protection Strategy Roadmap Summary PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Network Detection, Event Management, Security Information. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
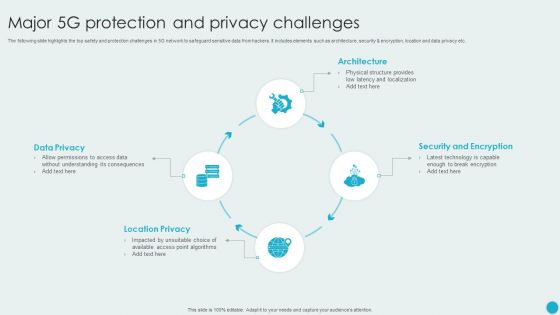
Major 5G Protection And Privacy Challenges Themes PDF
The following slide highlights the top safety and protection challenges in 5G network to safeguard sensitive data from hackers. It includes elements such as architecture, security and encryption, location and data privacy etc. Presenting Major 5G Protection And Privacy Challenges Themes PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Data Privacy, Location Privacy, Security And Encryption. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
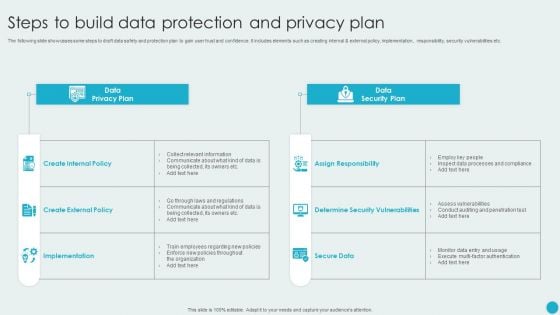
Steps To Build Data Protection And Privacy Plan Diagrams PDF
The following slide showcases some steps to draft data safety and protection plan to gain user trust and confidence. It includes elements such as creating internal and external policy, implementation, responsibility, security vulnerabilities etc. Showcasing this set of slides titled Steps To Build Data Protection And Privacy Plan Diagrams PDF. The topics addressed in these templates are Data Privacy Plan, Data Security Plan, Implementation. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Information Security Complete Data Security Implementation Checklist Ppt Icon Clipart PDF
This slide depicts the cyber security checklist and measures an organization should take to protect data and company assets from cyber attacks or natural disasters. This is a information security complete data security implementation checklist ppt icon clipart pdf template with various stages. Focus and dispense information on eleven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like strong passwords, antivirus software, frequent staff training, recovery planning, device security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Info Security Complete Information Security Implementation Checklist Ppt PowerPoint Presentation Icon Portfolio PDF
This slide depicts the cyber security checklist and measures an organization should take to protect data and company assets from cyber attacks or natural disasters. This is a info security complete information security implementation checklist ppt powerpoint presentation icon portfolio pdf template with various stages. Focus and dispense information on twelve stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like frequent, staff training, antivirus software, strong passwords, data backup, recovery planning. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Solution Monitoring And Verification Process To Meet Company Requirements Ppt PowerPoint Presentation Complete Deck With Slides
Induce strategic thinking by presenting this complete deck. Enthrall your audience by deploying this thought provoking PPT deck. It can be downloaded in both standard and widescreen aspect ratios, thus making it a complete package to use and deploy. Convey your thoughts and actions using the fourty eight slides presented in this complete deck. Additionally, feel free to alter its components like color, graphics, design, etc, to create a great first impression. Grab it now by clicking on the download button below.
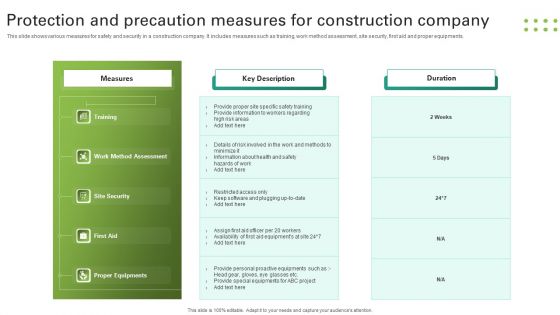
Protection And Precaution Measures For Construction Company Portrait PDF
This slide shows various measures for safety and security in a construction company. It includes measures such as training, work method assessment, site security, first aid and proper equipments. Pitch your topic with ease and precision using this Protection And Precaution Measures For Construction Company Portrait PDF. This layout presents information on Measures, Key Description, Duration. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Web Access Control Solution Reasons Behind Need For Secure Web Gateway
Find a pre-designed and impeccable Web Access Control Solution Reasons Behind Need For Secure Web Gateway. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide discusses the requirement of Secure Web Gateway in protecting organizations from various cyber crimes. The reasons behind need of Secure Web Gateway are protection against web-based threats, enforce security policies, controlled access, etc.
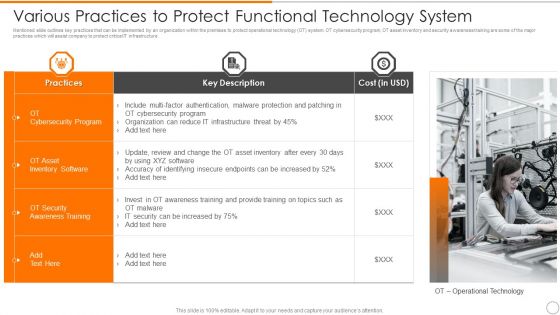
Various Practices To Protect Functional Technology System Information PDF
Showcasing this set of slides titled various practices to protect functional technology system information pdf. The topics addressed in these templates are inventory software, awareness training, security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Top Web Application Security Threats Application Security Testing
This slide discusses the vulnerabilities and security threats in web application such as SQL injection, cross-site scripting, etc. Presenting this PowerPoint presentation, titled Top Web Application Security Threats Application Security Testing, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Top Web Application Security Threats Application Security Testing. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Top Web Application Security Threats Application Security Testing that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide discusses the vulnerabilities and security threats in web application such as SQL injection, cross-site scripting, etc.


 Continue with Email
Continue with Email

 Home
Home


































