Authentication
Detailed Analysis To Understand Global Security Industry PPT PowerPoint IR SS V
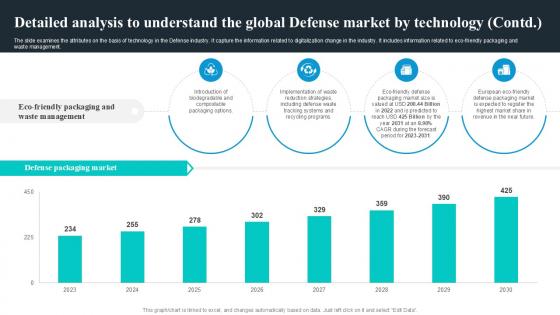
The slide examines the attributes on the basis of technology in the Defense industry. It capture the information related to digitalization change in the industry. It includes information related to eco-friendly packaging and waste management. Present like a pro with Detailed Analysis To Understand Global Security Industry PPT PowerPoint IR SS V. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. The slide examines the attributes on the basis of technology in the Defense industry. It capture the information related to digitalization change in the industry. It includes information related to eco-friendly packaging and waste management.

Gartners Magic Quadrant For Understanding Global Security Industry PPT PowerPoint IR SS V
The slide provides a diagrammatic representation of positioning and evaluation of various Defense organizations based on their completeness of vision and the ability to execute. The matrix includes challengers, visionaries, leaders and niche players. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Gartners Magic Quadrant For Understanding Global Security Industry PPT PowerPoint IR SS V and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates The slide provides a diagrammatic representation of positioning and evaluation of various Defense organizations based on their completeness of vision and the ability to execute. The matrix includes challengers, visionaries, leaders and niche players.
Key Industry Considerations And Report Global Security Industry PPT PowerPoint IR SS V
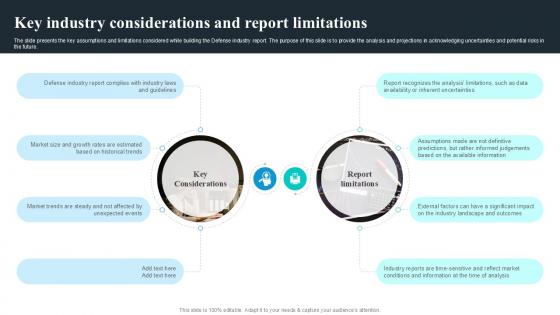
The slide covers the segmentation analysis in the Defense industry report. It includes attributes related to technology, type of product, services, distribution channel, geographical analysis, and key market player profile. The slide presents the key assumptions and limitations considered while building the Defense industry report. The purpose of this slide is to provide the analysis and projections in acknowledging uncertainties and potential risks in the future. Make sure to capture your audiences attention in your business displays with our gratis customizable Key Industry Considerations And Report Global Security Industry PPT PowerPoint IR SS V. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. The slide covers the segmentation analysis in the Defense industry report. It includes attributes related to technology, type of product, services, distribution channel, geographical analysis, and key market player profile.
About Non Fungible Tokenization In Crypto Currency Securing Your Data Ppt Slide
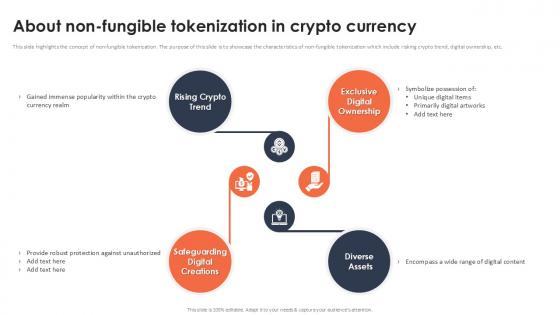
This slide highlights the concept of non-fungible tokenization. The purpose of this slide is to showcase the characteristics of non-fungible tokenization which include risking crypto trend, digital ownership, etc. Boost your pitch with our creative About Non Fungible Tokenization In Crypto Currency Securing Your Data Ppt Slide Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide highlights the concept of non-fungible tokenization. The purpose of this slide is to showcase the characteristics of non-fungible tokenization which include risking crypto trend, digital ownership, etc.

Evolution Of Tokenization From Ancient Times To Modern Era Securing Your Data Ppt Powerpoint
This slide outlines the history of tokenization. The purpose of this slide is to showcase the years of evolution such as 1970s digital tokenization, data compliance in 2001, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Evolution Of Tokenization From Ancient Times To Modern Era Securing Your Data Ppt Powerpoint These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide outlines the history of tokenization. The purpose of this slide is to showcase the years of evolution such as 1970s digital tokenization, data compliance in 2001, etc.
Governance And Risk Management In Cloud Based Systems Securing Your Data Ppt Example
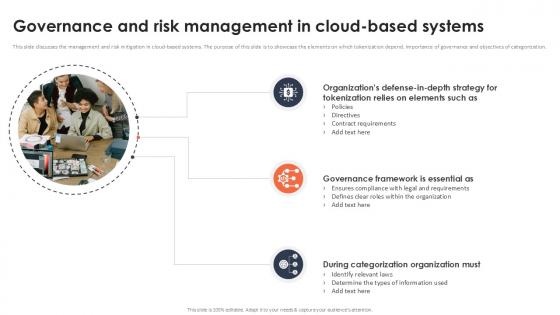
This slide discusses the management and risk mitigation in cloud-based systems. The purpose of this slide is to showcase the elements on which tokenization depend, importance of governance and objectives of categorization. This modern and well-arranged Governance And Risk Management In Cloud Based Systems Securing Your Data Ppt Example provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide discusses the management and risk mitigation in cloud-based systems. The purpose of this slide is to showcase the elements on which tokenization depend, importance of governance and objectives of categorization.

Key Applications And Use Cases Of Tokenization Securing Your Data Ppt Powerpoint
This slide discusses various application fields of tokenization. The purpose of this slide is to highlight the areas of application which include mobile wallet services, online retail platforms, etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Key Applications And Use Cases Of Tokenization Securing Your Data Ppt Powerpoint from Slidegeeks and deliver a wonderful presentation. This slide discusses various application fields of tokenization. The purpose of this slide is to highlight the areas of application which include mobile wallet services, online retail platforms, etc.
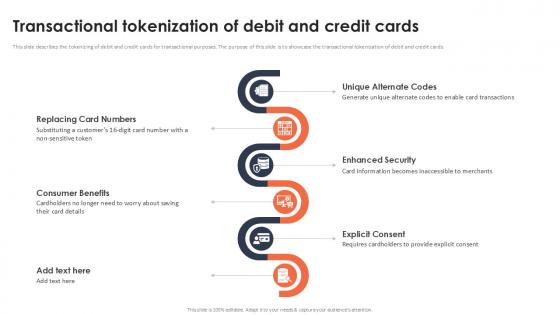
Transactional Tokenization Of Debit And Credit Cards Securing Your Data Ppt Slide
This slide describes the tokenizing of debit and credit cards for transactional purposes. The purpose of this slide is to showcase the transactional tokenization of debit and credit cards. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Transactional Tokenization Of Debit And Credit Cards Securing Your Data Ppt Slide and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide describes the tokenizing of debit and credit cards for transactional purposes. The purpose of this slide is to showcase the transactional tokenization of debit and credit cards.

Elliptic Curve Cryptography ECC Data Security In Cloud Computing Ppt Template
This slide talks about the Elliptic Curve Cryptography algorithm. The purpose of this slide is to elaborate the different applications of ECC algorithm. The uses of this algorithm are key agreement, mobile devices, cryptocurrency, etc. Welcome to our selection of the Elliptic Curve Cryptography ECC Data Security In Cloud Computing Ppt Template. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide talks about the Elliptic Curve Cryptography algorithm. The purpose of this slide is to elaborate the different applications of ECC algorithm. The uses of this algorithm are key agreement, mobile devices, cryptocurrency, etc.
Business Strategy Model Use Protection For Teeth Icons
Rake In The Dough With

Business Diagram Globe In Hands For Global Protection Presentation Template
This conceptual diagram is designed with graphic of globe and human hands. In this slide globe is balanced with hands which displays the concept of environment safety with human efforts. Use this slide for nature and environment safety related topics.

Five Banners For Nature And Environment Protection Powerpoint Template
This PowerPoint template has been designed with graphics of five text banners with icons. This Infographic diagram may be for nature and environment related topics. Download this impressive diagram to build unique presentations.
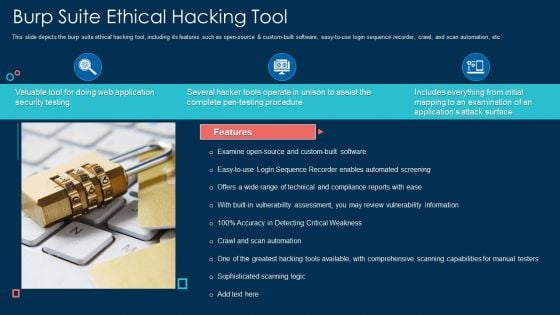
Burp Suite Ethical Hacking Tool Ppt Portfolio Skills PDF
This slide depicts the burp suite ethical hacking tool, including its features such as open source and custom built software, easy to use login sequence recorder, crawl, and scan automation, etc. Presenting burp suite ethical hacking tool ppt portfolio skills pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like security, application, information. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
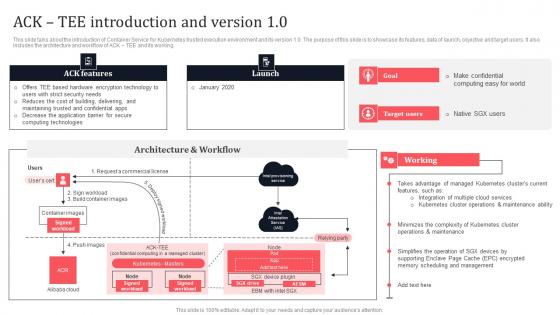
Ack Tee Introduction And Version 1 0 Secure Multi Party Slides Pdf
This slide talks about the introduction of Container Service for Kubernetes trusted execution environment and its version 1.0. The purpose of this slide is to showcase its features, data of launch, objective and target users. It also includes the architecture and workflow of ACK TEE and its working. This Ack Tee Introduction And Version 1 0 Secure Multi Party Slides Pdf from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide talks about the introduction of Container Service for Kubernetes trusted execution environment and its version 1.0. The purpose of this slide is to showcase its features, data of launch, objective and target users. It also includes the architecture and workflow of ACK TEE and its working.
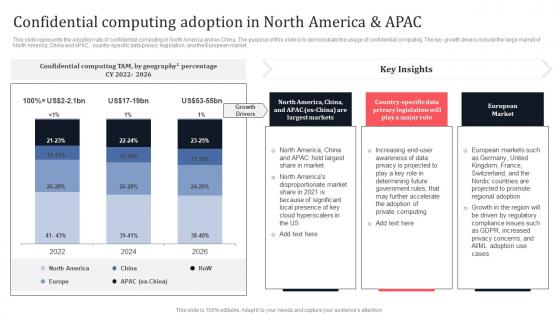
Confidential Computing Adoption In North America And APAC Secure Multi Party Brochure Pdf
This slide represents the adoption rate of confidential computing in North America and ex-China. The purpose of this slide is to demonstrate the usage of confidential computing. The key growth drivers include the large market of North America, China and APAC, country-specific data privacy legislation, and the European market. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Confidential Computing Adoption In North America And APAC Secure Multi Party Brochure Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide represents the adoption rate of confidential computing in North America and ex-China. The purpose of this slide is to demonstrate the usage of confidential computing. The key growth drivers include the large market of North America, China and APAC, country-specific data privacy legislation, and the European market.
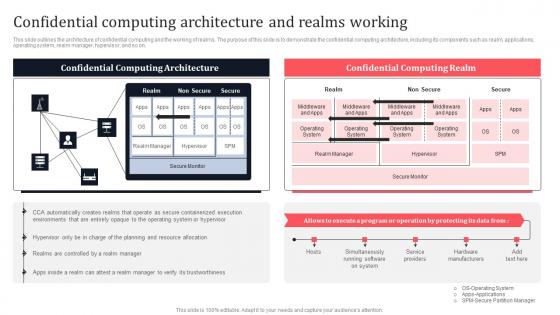
Confidential Computing Architecture And Realms Working Secure Multi Party Download Pdf
This slide outlines the architecture of confidential computing and the working of realms. The purpose of this slide is to demonstrate the confidential computing architecture, including its components such as realm, applications, operating system, realm manager, hypervisor, and so on. Slidegeeks is here to make your presentations a breeze with Confidential Computing Architecture And Realms Working Secure Multi Party Download Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first. This slide outlines the architecture of confidential computing and the working of realms. The purpose of this slide is to demonstrate the confidential computing architecture, including its components such as realm, applications, operating system, realm manager, hypervisor, and so on.
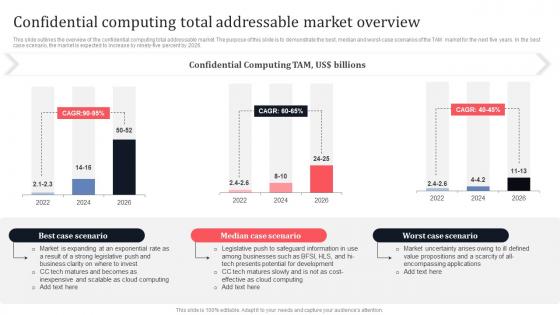
Confidential Computing Total Addressable Market Overview Secure Multi Party Download Pdf
This slide outlines the overview of the confidential computing total addressable market. The purpose of this slide is to demonstrate the best, median and worst-case scenarios of the TAM market for the next five years. In the best case scenario, the market is expected to increase by ninety-five percent by 2026. Welcome to our selection of the Confidential Computing Total Addressable Market Overview Secure Multi Party Download Pdf These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide outlines the overview of the confidential computing total addressable market. The purpose of this slide is to demonstrate the best, median and worst-case scenarios of the TAM market for the next five years. In the best case scenario, the market is expected to increase by ninety-five percent by 2026.
Inclavare Confidential Containers Architecture In Tee Secure Multi Party Icons Pdf
This slide represents the architecture of inclavare confidential containers in the TEE environment. The purpose of this slide is to showcase the various components and features of inclavare containers. The primary components include Kubelet, containerd, shim-rune, rune, PAL API, Pod and so on. This Inclavare Confidential Containers Architecture In Tee Secure Multi Party Icons Pdf from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide represents the architecture of inclavare confidential containers in the TEE environment. The purpose of this slide is to showcase the various components and features of inclavare containers. The primary components include Kubelet, containerd, shim-rune, rune, PAL API, Pod and so on.
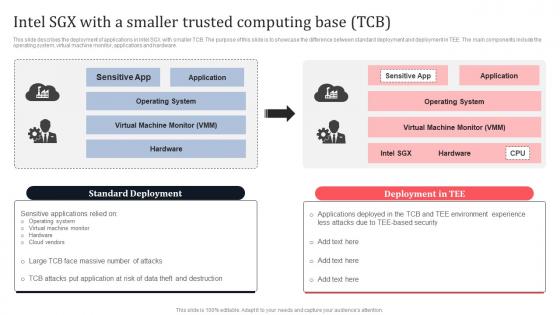
Intel SGX With A Smaller Trusted Computing Base TCB Secure Multi Party Sample Pdf
This slide describes the deployment of applications in Intel SGX with smaller TCB. The purpose of this slide is to showcase the difference between standard deployment and deployment in TEE. The main components include the operating system, virtual machine monitor, applications and hardware. Take your projects to the next level with our ultimate collection of Intel SGX With A Smaller Trusted Computing Base TCB Secure Multi Party Sample Pdf Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they well make your projects stand out from the rest. This slide describes the deployment of applications in Intel SGX with smaller TCB. The purpose of this slide is to showcase the difference between standard deployment and deployment in TEE. The main components include the operating system, virtual machine monitor, applications and hardware.
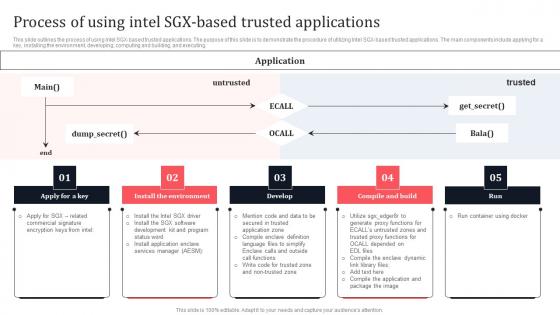
Process Of Using Intel SGX Based Trusted Applications Secure Multi Party Structure Pdf
This slide outlines the process of using Intel SGX-based trusted applications. The purpose of this slide is to demonstrate the procedure of utilizing Intel SGX-based trusted applications. The main components include applying for a key, installing the environment, developing, computing and building, and executing. Present like a pro with Process Of Using Intel SGX Based Trusted Applications Secure Multi Party Structure Pdf Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide outlines the process of using Intel SGX-based trusted applications. The purpose of this slide is to demonstrate the procedure of utilizing Intel SGX-based trusted applications. The main components include applying for a key, installing the environment, developing, computing and building, and executing.
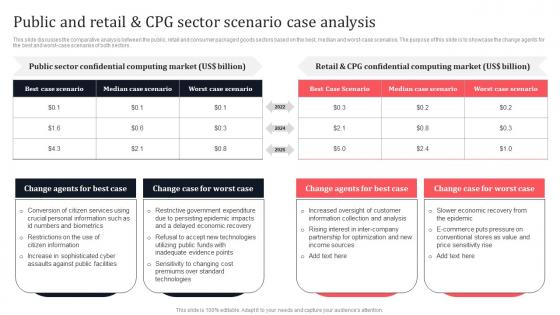
Public And Retail And CPG Sector Scenario Case Analysis Secure Multi Party Portrait Pdf
This slide discusses the comparative analysis between the public, retail and consumer packaged goods sectors based on the best, median and worst-case scenarios. The purpose of this slide is to showcase the change agents for the best and worst-case scenarios of both sectors. Slidegeeks is here to make your presentations a breeze with Public And Retail And CPG Sector Scenario Case Analysis Secure Multi Party Portrait Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first. This slide discusses the comparative analysis between the public, retail and consumer packaged goods sectors based on the best, median and worst-case scenarios. The purpose of this slide is to showcase the change agents for the best and worst-case scenarios of both sectors.
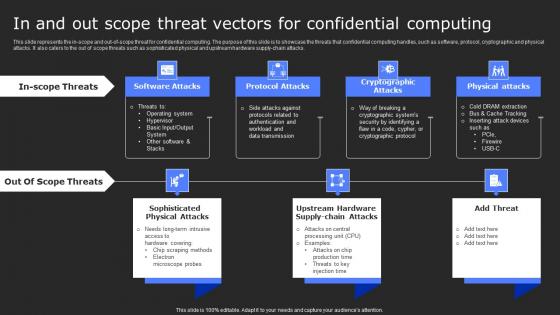
In And Out Scope Threat Vectors For Confidential Secure Computing Framework Inspiration Pdf
This slide represents the in-scope and out-of-scope threat for confidential computing. The purpose of this slide is to showcase the threats that confidential computing handles, such as software, protocol, cryptographic and physical attacks. It also caters to the out of scope threats such as sophisticated physical and upstream hardware supply-chain attacks. Take your projects to the next level with our ultimate collection of In And Out Scope Threat Vectors For Confidential Secure Computing Framework Inspiration Pdf. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest This slide represents the in-scope and out-of-scope threat for confidential computing. The purpose of this slide is to showcase the threats that confidential computing handles, such as software, protocol, cryptographic and physical attacks. It also caters to the out of scope threats such as sophisticated physical and upstream hardware supply-chain attacks.
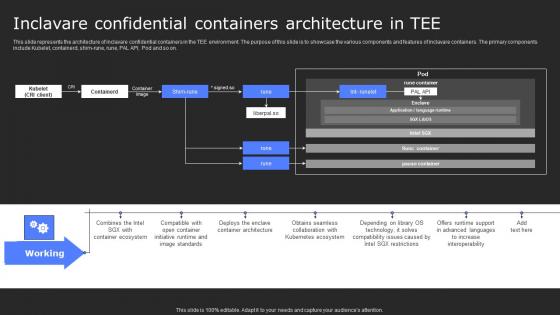
Inclavare Confidential Containers Architecture In Tee Secure Computing Framework Infographics Pdf
This slide represents the architecture of inclavare confidential containers in the TEE environment. The purpose of this slide is to showcase the various components and features of inclavare containers. The primary components include Kubelet, containerd, shim-rune, rune, PAL API, Pod and so on. Do you know about Slidesgeeks Inclavare Confidential Containers Architecture In Tee Secure Computing Framework Infographics Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide represents the architecture of inclavare confidential containers in the TEE environment. The purpose of this slide is to showcase the various components and features of inclavare containers. The primary components include Kubelet, containerd, shim-rune, rune, PAL API, Pod and so on.
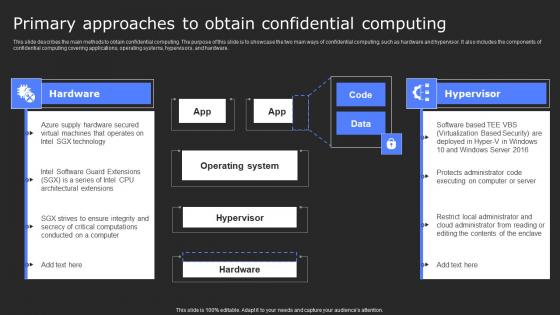
Primary Approaches To Obtain Confidential Computing Secure Computing Framework Graphics Pdf
This slide describes the main methods to obtain confidential computing. The purpose of this slide is to showcase the two main ways of confidential computing, such as hardware and hypervisor. It also includes the components of confidential computing covering applications, operating systems, hypervisors, and hardware. Slidegeeks is here to make your presentations a breeze with Primary Approaches To Obtain Confidential Computing Secure Computing Framework Graphics Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide describes the main methods to obtain confidential computing. The purpose of this slide is to showcase the two main ways of confidential computing, such as hardware and hypervisor. It also includes the components of confidential computing covering applications, operating systems, hypervisors, and hardware.
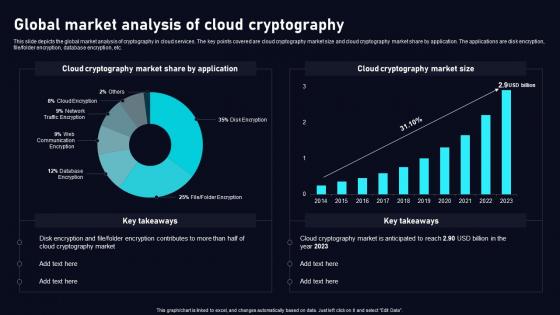
Global Market Analysis Of Cloud Data Security Using Cryptography Portrait Pdf
This slide depicts the global market analysis of cryptography in cloud services. The key points covered are cloud cryptography market size and cloud cryptography market share by application. The applications are disk encryption, file folder encryption, database encryption, etc. Do you know about Slidesgeeks Global Market Analysis Of Cloud Data Security Using Cryptography Portrait Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide depicts the global market analysis of cryptography in cloud services. The key points covered are cloud cryptography market size and cloud cryptography market share by application. The applications are disk encryption, file folder encryption, database encryption, etc.
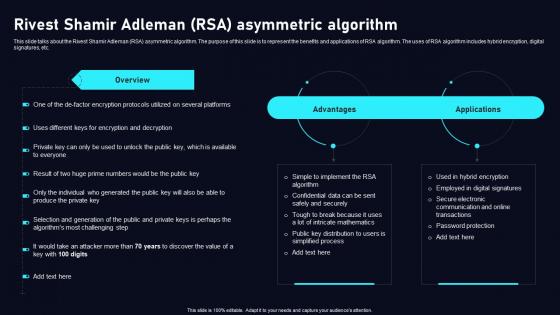
Rivest Shamir Adleman RSA Asymmetric Cloud Data Security Using Cryptography Slides Pdf
This slide talks about the Rivest Shamir Adleman RSA asymmetric algorithm. The purpose of this slide is to represent the benefits and applications of RSA algorithm. The uses of RSA algorithm includes hybrid encryption, digital signatures, etc. Slidegeeks is here to make your presentations a breeze with Rivest Shamir Adleman RSA Asymmetric Cloud Data Security Using Cryptography Slides Pdf With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide talks about the Rivest Shamir Adleman RSA asymmetric algorithm. The purpose of this slide is to represent the benefits and applications of RSA algorithm. The uses of RSA algorithm includes hybrid encryption, digital signatures, etc.

How To Configure Firewall As A Service Fwaas Network Security Diagrams Pdf
This slide talks about the steps of configuring Firewall-as-a-Service. The purpose of this slide is to illustrate how FWaaS packages can be installed and configured. The key steps explained in this slide are enable FWaaS and configure FWaaS. Welcome to our selection of the How To Configure Firewall As A Service Fwaas Network Security Diagrams Pdf. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today This slide talks about the steps of configuring Firewall-as-a-Service. The purpose of this slide is to illustrate how FWaaS packages can be installed and configured. The key steps explained in this slide are enable FWaaS and configure FWaaS.

Building Trust With IoT Security Case Study 1 Enhancing Operational Technology By Integrating IoT SS V
This slide includes a case study of the company providing operational digital safety solutions integrating Cisco technology to enhance visibility at scale. It includes elements such as objectives of company , solutions implemented, and results. Slidegeeks is here to make your presentations a breeze with Building Trust With IoT Security Case Study 1 Enhancing Operational Technology By Integrating IoT SS V With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide includes a case study of the company providing operational digital safety solutions integrating Cisco technology to enhance visibility at scale. It includes elements such as objectives of company , solutions implemented, and results.

Global Data Security Industry Report Blueprint Of The Global Cybersecurity Industry Report IR SS V
The slide shows the overview of the cybersecurity industry report. It sets the stage for subsequent content by introducing the key topics covered in the report to capture the readers attention. It covers a detailed scope, research methodology, and objectives. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Global Data Security Industry Report Blueprint Of The Global Cybersecurity Industry Report IR SS V for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. The slide shows the overview of the cybersecurity industry report. It sets the stage for subsequent content by introducing the key topics covered in the report to capture the readers attention. It covers a detailed scope, research methodology, and objectives.

Global Data Security Industry Report Porters Framework Detailed Five Forces Analysis For Cybersecurity IR SS V
The slide highlights Porters framework and its implications in the cybersecurity industry. Evaluating the five forces can assist businesses in anticipating changes in the competition, influencing the evolution of industry structure, and finding more beneficial strategic positions. It covers the threat of new entrants and substitutes, competitive rivalry, and the bargaining power of suppliers and buyers. Welcome to our selection of the Global Data Security Industry Report Porters Framework Detailed Five Forces Analysis For Cybersecurity IR SS V. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. The slide highlights Porters framework and its implications in the cybersecurity industry. Evaluating the five forces can assist businesses in anticipating changes in the competition, influencing the evolution of industry structure, and finding more beneficial strategic positions. It covers the threat of new entrants and substitutes, competitive rivalry, and the bargaining power of suppliers and buyers.
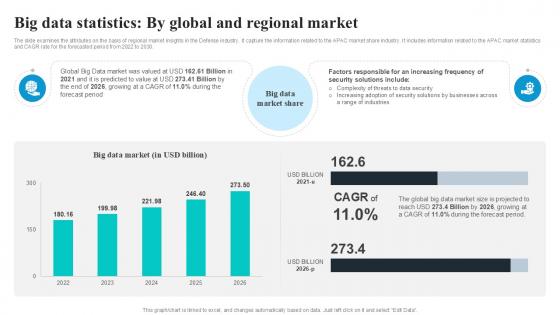
Big Data Statistics By Global Security Industry PPT Sample IR SS V
The slide examines the attributes on the basis of regional market insights in the Defense industry. It capture the information related to the APAC market share industry. It includes information related to the APAC market statistics and CAGR rate for the forecasted period from 2022 to 2030. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Big Data Statistics By Global Security Industry PPT Sample IR SS V for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. The slide examines the attributes on the basis of regional market insights in the Defense industry. It capture the information related to the APAC market share industry. It includes information related to the APAC market statistics and CAGR rate for the forecasted period from 2022 to 2030.
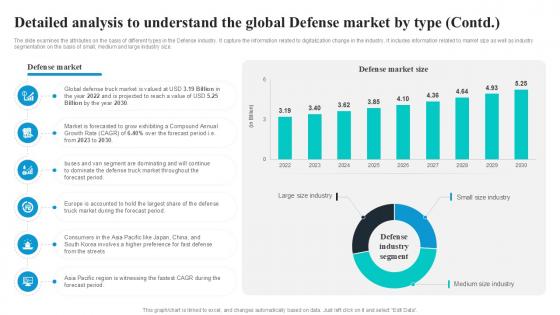
Detailed Analysis To Understand The Global Global Security Industry PPT PowerPoint IR SS V
The slide examines the attributes on the basis of different types in the Defense industry. It capture the information related to digitalization change in the industry. It includes information related to market size as well as industry segmentation on the basis of small, medium and large industry size. Slidegeeks is here to make your presentations a breeze with Detailed Analysis To Understand The Global Global Security Industry PPT PowerPoint IR SS V With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first The slide examines the attributes on the basis of different types in the Defense industry. It capture the information related to digitalization change in the industry. It includes information related to market size as well as industry segmentation on the basis of small, medium and large industry size.
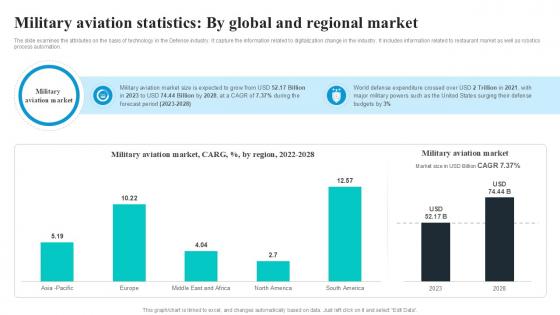
Military Aviation Statistics By Global Security Industry PPT PowerPoint IR SS V
The slide examines the attributes on the basis of technology in the Defense industry. It capture the information related to digitalization change in the industry. It includes information related to restaurant market as well as robotics process automation. Welcome to our selection of the Military Aviation Statistics By Global Security Industry PPT PowerPoint IR SS V. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. The slide examines the attributes on the basis of technology in the Defense industry. It capture the information related to digitalization change in the industry. It includes information related to restaurant market as well as robotics process automation.

Porters Framework Analysis To Global Security Industry PPT PowerPoint IR SS V
The slide highlights the porters framework analysis of Defense industry. The main purpose of this side is to evaluating and assessing the impact of external and internal factors on Defense market. It further helps in mitigating the potential risks. Key components include threat of new entrants, bargaining power, supplier power, threat of substitute, competitive rivalry. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Porters Framework Analysis To Global Security Industry PPT PowerPoint IR SS V from Slidegeeks and deliver a wonderful presentation. The slide highlights the porters framework analysis of Defense industry. The main purpose of this side is to evaluating and assessing the impact of external and internal factors on Defense market. It further helps in mitigating the potential risks. Key components include threat of new entrants, bargaining power, supplier power, threat of substitute, competitive rivalry.

Prospects And Growth Potential In Global Security Industry PPT Sample IR SS V
This slide highlights the different prospects responsible for growth of Defense market. The purpose of this slide is to cover different prospects related to growth of the industry. It covers digital and technological transformation, sustainable and climate concerns, product development innovation, and data-driven decision making. The Prospects And Growth Potential In Global Security Industry PPT Sample IR SS V is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide highlights the different prospects responsible for growth of Defense market. The purpose of this slide is to cover different prospects related to growth of the industry. It covers digital and technological transformation, sustainable and climate concerns, product development innovation, and data-driven decision making.
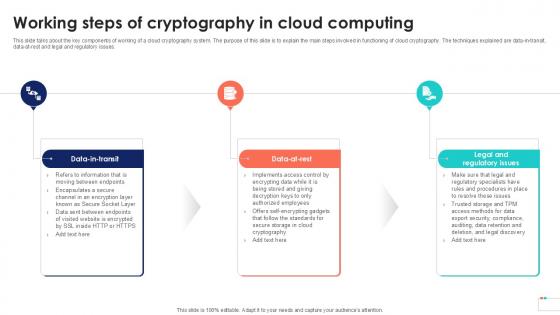
Working Steps Of Cryptography Data Security In Cloud Computing Ppt Slide
This slide talks about the key components of working of a cloud cryptography system. The purpose of this slide is to explain the main steps involved in functioning of cloud cryptography. The techniques explained are data-in-transit, data-at-rest and legal and regulatory issues. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Working Steps Of Cryptography Data Security In Cloud Computing Ppt Slide to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide talks about the key components of working of a cloud cryptography system. The purpose of this slide is to explain the main steps involved in functioning of cloud cryptography. The techniques explained are data-in-transit, data-at-rest and legal and regulatory issues.

Web App Firewall Services IT Features Of WAF Protection Against The OWASP Vulnerabilities Graphics PDF
This slide represents one of WAFs features that is protection against the top 10 open web application security project vulnerabilities such as injection, XSS, XXE, and so on. This is a web app firewall services it features of waf protection against the owasp vulnerabilities graphics pdf template with various stages. Focus and dispense information on ten stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like management, data exposure, security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
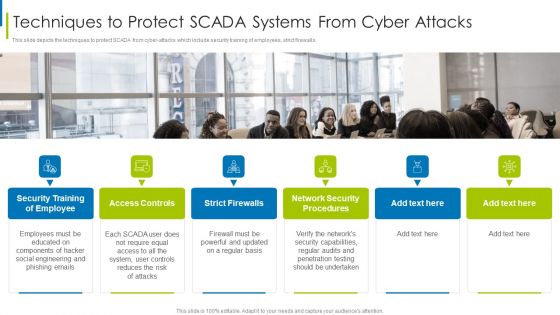
Cyber Terrorism Assault Techniques To Protect SCADA Systems From Cyber Attacks Demonstration PDF
This slide depicts the techniques to protect SCADA from cyber-attacks which include security training of employees, strict firewalls.Presenting cyber terrorism assault techniques to protect scada systems from cyber attacks demonstration pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like access controls, strict firewalls, network security procedures In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
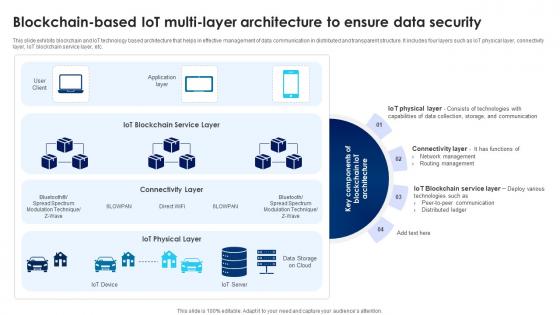
Building Trust With IoT Security Blockchain Based IoT Multi Layer Architecture To Ensure Data IoT SS V
This slide exhibits blockchain and IoT technology based architecture that helps in effective management of data communication in distributed and transparent structure. It includes four layers such as IoT physical layer, connectivity layer, IoT blockchain service layer, etc. Get a simple yet stunning designed Building Trust With IoT Security Blockchain Based IoT Multi Layer Architecture To Ensure Data IoT SS V. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Building Trust With IoT Security Blockchain Based IoT Multi Layer Architecture To Ensure Data IoT SS V can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide exhibits blockchain and IoT technology based architecture that helps in effective management of data communication in distributed and transparent structure. It includes four layers such as IoT physical layer, connectivity layer, IoT blockchain service layer, etc.
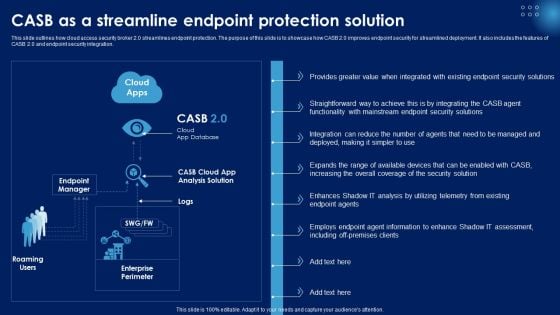
CASB As A Streamline Endpoint Protection Solution Ppt PowerPoint Presentation File Layouts PDF
This slide outlines how cloud access security broker 2.0 streamlines endpoint protection. The purpose of this slide is to showcase how CASB 2.0 improves endpoint security for streamlined deployment. It also includes the features of CASB 2.0 and endpoint security integration. Take your projects to the next level with our ultimate collection of CASB As A Streamline Endpoint Protection Solution Ppt PowerPoint Presentation File Layouts PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest.

Pillars Of Cloud Security Network Security Rules PDF
This slide defines the network security pillar of cloud security and what precautions are taken to protect networks from attacks. This is a Pillars Of Cloud Security Network Security Rules PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Secure, Network, Information. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
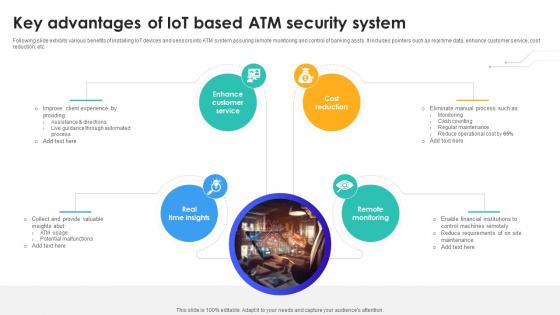
Key Advantages Of IoT Based Atm Security System IoT In Banking For Digital Future IoT SS V
Following slide exhibits various benefits of installing IoT devices and sensors into ATM system assuring remote monitoring and control of banking assts. It includes pointers such as real time data, enhance customer service, cost reduction, etc. This modern and well-arranged Key Advantages Of IoT Based Atm Security System IoT In Banking For Digital Future IoT SS V provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. Following slide exhibits various benefits of installing IoT devices and sensors into ATM system assuring remote monitoring and control of banking assts. It includes pointers such as real time data, enhance customer service, cost reduction, etc.

Pillars Of Cloud Security Identity Security Diagrams PDF
This slide depicts the identity security pillar of cloud security. It also shows how it could be beneficial to protect data from loss. Deliver an awe inspiring pitch with this creative Pillars Of Cloud Security Identity Security Diagrams PDF bundle. Topics like Service Permissions, Application, Required can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cloud Security Assessment Phase 2 Secure Your Cloud Structure PDF
This slide depicts how organizations could secure their cloud and what factors should keep under consideration while protecting the cloud.Deliver an awe inspiring pitch with this creative Cloud Security Assessment Phase 2 Secure Your Cloud Structure PDF bundle. Topics like Implement Information, Security Policies, Data Encryption can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Enhanced Protection Corporate Event Administration How Firm Handle Insider Threats Structure PDF
This slide provides information regarding how firm will handle insider threats through employee training, IT security and HR coordination, etc. This is a enhanced protection corporate event administration how firm handle insider threats structure pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like employee training, it security and hr coordination, develop threat hunting team, implement user behavioral analytics. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
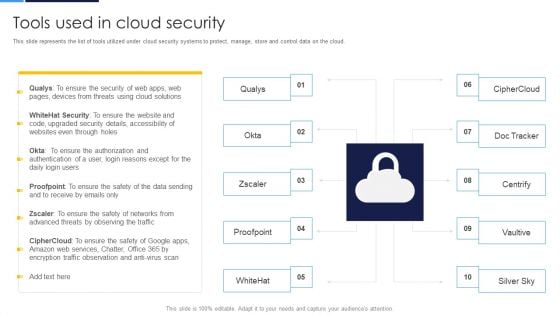
Cloud Security Assessment Tools Used In Cloud Security Designs PDF
This slide represents the list of tools utilized under cloud security systems to protect, manage, store and control data on the cloud.Deliver an awe inspiring pitch with this creative Cloud Security Assessment Tools Used In Cloud Security Designs PDF bundle. Topics like Advanced Threats, Traffic Observation, Details Accessibility can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
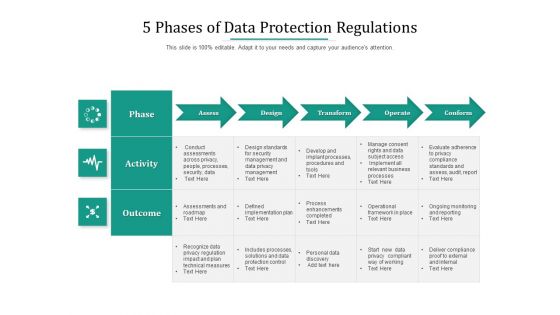
5 Phases Of Data Protection Regulations Ppt PowerPoint Presentation Summary Images PDF
Pitch your topic with ease and precision using this 5 phases of data protection regulations ppt powerpoint presentation summary images pdf. This layout presents information on business, processes, security, management, working. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
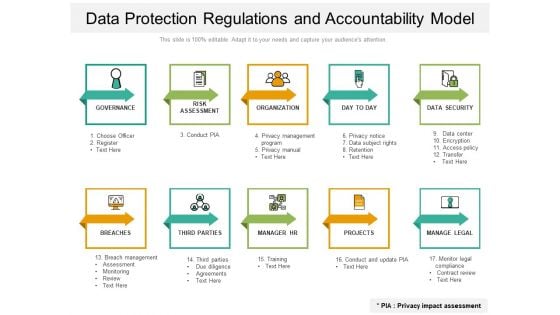
Data Protection Regulations And Accountability Model Ppt PowerPoint Presentation Styles Microsoft PDF
Presenting data protection regulations and accountability model ppt powerpoint presentation styles microsoft pdf. to dispense important information. This template comprises ten stages. It also presents valuable insights into the topics including organization, data security, manage legal, projects, manager hr, governance, risk assessment. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
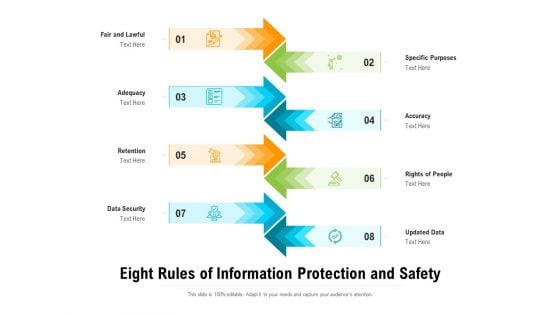
Eight Rules Of Information Protection And Safety Ppt PowerPoint Presentation Gallery Show PDF
Presenting eight rules of information protection and safety ppt powerpoint presentation gallery show pdf to dispense important information. This template comprises eight stages. It also presents valuable insights into the topics including adequacy, retention, data security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
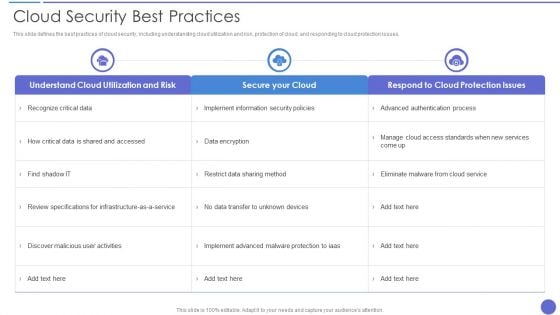
Cloud Security Best Practices Themes PDF
This slide defines the best practices of cloud security, including understanding cloud utilization and risk, protection of cloud, and responding to cloud protection issues. Deliver and pitch your topic in the best possible manner with this Cloud Security Best Practices Themes PDF. Use them to share invaluable insights on Secure Your Cloud, Data Encryption, Recognize Critical Data and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
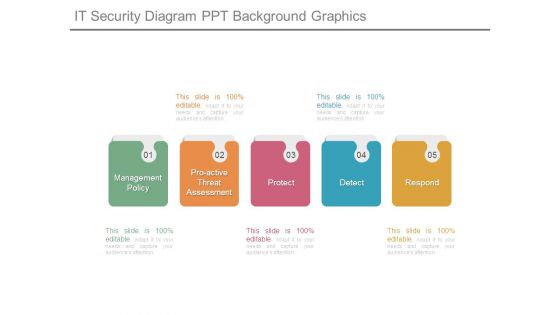
It Security Diagram Ppt Background Graphics
This is a it security diagram ppt background graphics. This is a five stage process. The stages in this process are management policy, proactive threat assessment, protect, detect, respond.
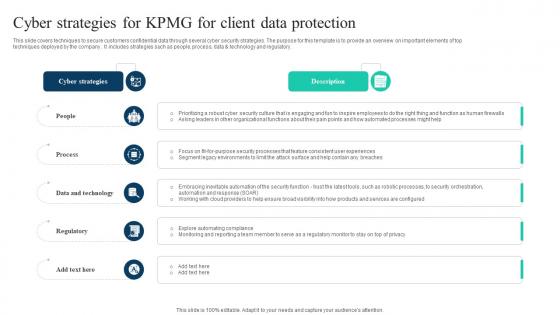
The Ultimate Guide To KPMG Cyber Strategies For KPMG For Client Data Protection Strategy SS V
This slide covers techniques to secure customers confidential data through several cyber security strategies. The purpose for this template is to provide an overview on important elements of top techniques deployed by the company . It includes strategies such as people, process, data and technology and regulatory. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward The Ultimate Guide To KPMG Cyber Strategies For KPMG For Client Data Protection Strategy SS V template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal The Ultimate Guide To KPMG Cyber Strategies For KPMG For Client Data Protection Strategy SS V that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide covers techniques to secure customers confidential data through several cyber security strategies. The purpose for this template is to provide an overview on important elements of top techniques deployed by the company . It includes strategies such as people, process, data and technology and regulatory.
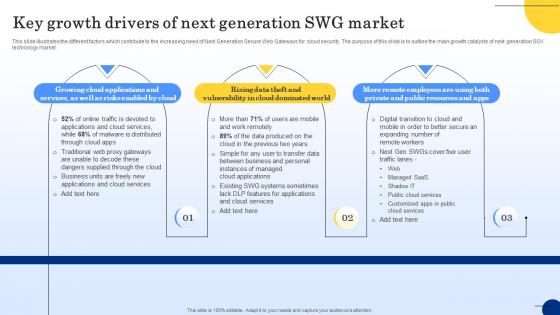
Key Growth Drivers Of Next Generation SWG Market Web Threat Protection System
This slide illustrates the different factors which contribute to the increasing need of Next Generation Secure Web Gateways for cloud security. The purpose of this slide is to outline the main growth catalysts of next generation SGV technology market. Explore a selection of the finest Key Growth Drivers Of Next Generation SWG Market Web Threat Protection System here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Key Growth Drivers Of Next Generation SWG Market Web Threat Protection System to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide illustrates the different factors which contribute to the increasing need of Next Generation Secure Web Gateways for cloud security. The purpose of this slide is to outline the main growth catalysts of next generation SGV technology market.
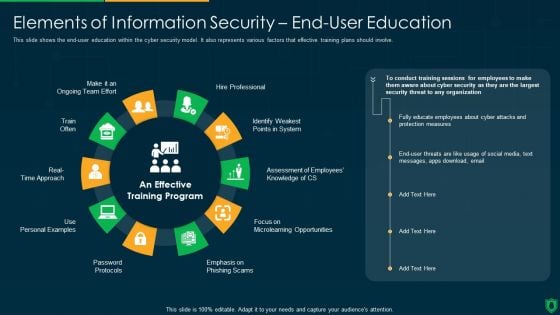
Info Security Elements Of Information Security End User Education Ppt PowerPoint Presentation File Example File PDF
This slide shows the end-user education within the cyber security model. It also represents various factors that effective training plans should involve. Presenting info security elements of information security end user education ppt powerpoint presentation file example file pdf to provide visual cues and insights. Share and navigate important information on ten stages that need your due attention. This template can be used to pitch topics like hire professional, emphasis on phishing scam, password protocols, train often. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Concept Of Locked Money Credit PowerPoint Templates And PowerPoint Themes 0912
Concept Of Locked Money Credit PowerPoint Templates And PowerPoint Themes 0912-Microsoft Powerpoint Templates and Background with protect your investments Advertise your expertise with our Concept Of Locked Money Credit PowerPoint Templates And PowerPoint Themes 0912. Establish your undeniable command over the subject.

Major Techniques For Project Safety IT Information Security Process To Manage Firms Sensitive Data Designs PDF
This slide provides information about information security process in order to manage firms sensitive data in terms of privileged password management, network security audit checklist, etc. Deliver and pitch your topic in the best possible manner with this major techniques for project safety it information security process to manage firms sensitive data designs pdf. Use them to share invaluable insights on privileged password management, daily tasks performed by network administrator, network security audit checklist and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
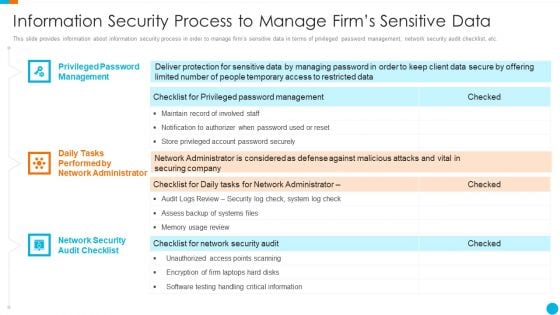
Upgrading Total Project Safety IT Information Security Process To Manage Firms Sensitive Data Structure PDF
This slide provides information about information security process in order to manage firms sensitive data in terms of privileged password management, network security audit checklist, etc. Presenting upgrading total project safety it information security process to manage firms sensitive data structure pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like privileged password management, daily tasks performed by network administrator, network security audit checklist. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
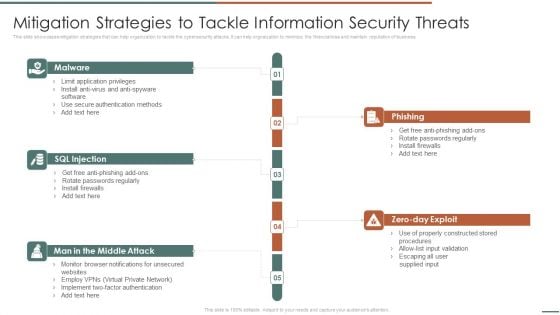
Information Security Risk Evaluation Mitigation Strategies To Tackle Information Security Threats Designs PDF
This slide showcases mitigation strategies that can help organization to tackle the cybersecurity attacks. It can help orgnaization to minimize the financial loss and maintain reputation of business.Presenting Information Security Risk Evaluation Mitigation Strategies To Tackle Information Security Threats Designs PDF to provide visual cues and insights. Share and navigate important information on fivestages that need your due attention. This template can be used to pitch topics like Phishing, Rotate Passwords, Install Firewalls. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
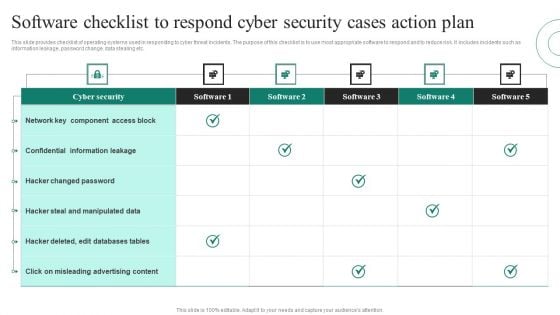
Software Checklist To Respond Cyber Security Cases Action Plan Ppt PowerPoint Presentation File Visuals PDF
This slide provides checklist of operating systems used in responding to cyber threat incidents. The purpose of this checklist is to use most appropriate software to respond and to reduce risk. It includes incidents such as information leakage, password change, data stealing etc. Pitch your topic with ease and precision using this Software Checklist To Respond Cyber Security Cases Action Plan Ppt PowerPoint Presentation File Visuals PDF. This layout presents information on Cyber Security, Confidential Information Leakage, Hacker Changed Password. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
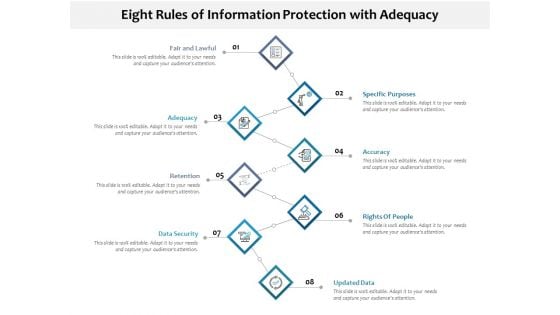
Eight Rules Of Information Protection With Adequacy Ppt PowerPoint Presentation File Format PDF
Persuade your audience using this eight rules of information protection with adequacy ppt powerpoint presentation file format pdf. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including adequacy, retention, data security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.


 Continue with Email
Continue with Email

 Home
Home


































