Authentication

Smart Phone Data Safety Application With Protection Shield Ppt Gallery Outfit PDF
Persuade your audience using this smart phone data safety application with protection shield ppt gallery outfit pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including smart phone data transfer via secured network image. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Enhanced Protection Corporate Event Administration Contingency Plan For Threat Handling Icons PDF
This slide portrays information contingency plan for handling threats with the help of technical equipment that assist contingency solution and considerations. Deliver an awe inspiring pitch with this creative enhanced protection corporate event administration contingency plan for threat handling icons pdf bundle. Topics like contingency considerations, mainframe systems, security, implementation, technologies integration can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Enhanced Protection Corporate Event Administration Essential Roles And Responsibilities Involved In Secops Guidelines PDF
This slide portrays information regarding the roles and responsibilities, qualification associated to staff available at Tier1, 2, 3, and 4 level at SOC structure. Deliver and pitch your topic in the best possible manner with this enhanced protection corporate event administration essential roles and responsibilities involved in secops guidelines pdf. Use them to share invaluable insights on security engineers, business, communication skills, management, training and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
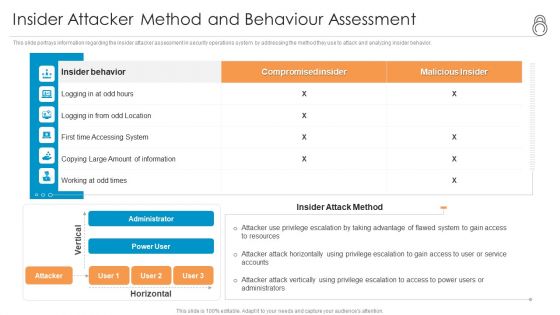
Enhanced Protection Corporate Event Administration Insider Attacker Method And Behaviour Assessment Topics PDF
This slide portrays information regarding the insider attacker assessment in security operations system by addressing the method they use to attack and analyzing insider behavior. Deliver and pitch your topic in the best possible manner with this enhanced protection corporate event administration insider attacker method and behaviour assessment topics pdf. Use them to share invaluable insights on insider attacker method and behaviour assessment and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
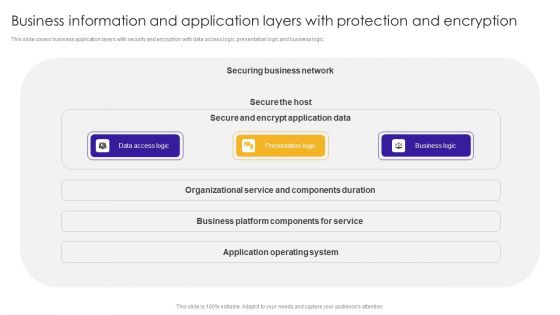
Business Information And Application Layers With Protection And Encryption Brochure PDF
This slide covers business application layers with security and encryption with data access logic, presentation logic and business logic.Pitch your topic with ease and precision using this Business Information And Application Layers With Protection And Encryption Brochure PDF. This layout presents information on Organizational Service, Components Duration, Operating System. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
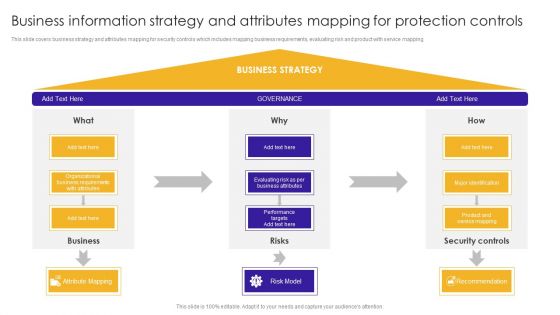
Business Information Strategy And Attributes Mapping For Protection Controls Portrait PDF
This slide covers business strategy and attributes mapping for security controls which includes mapping business requirements, evaluating risk and product with service mapping. Showcasing this set of slides titled Business Information Strategy And Attributes Mapping For Protection Controls Portrait PDF. The topics addressed in these templates are Major Identification, Service Mapping, Recommendation. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
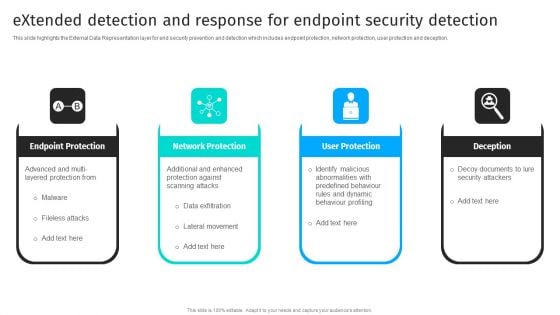
Extended Detection And Response For Endpoint Security Detection Information PDF
This slide highlights the External Data Representation layer for end security prevention and detection which includes endpoint protection, network protection, user protection and deception.There are so many reasons you need a Extended Detection And Response For Endpoint Security Detection Information PDF. The first reason is you can notspend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
Framework For Improving Critical Infra Cyber Security Icons PDF
The following slide exhibits framework for protection, resilience of infrastructure and other sectors important to national security. It presents information related to protection, responding, etc. Showcasing this set of slides titled Framework For Improving Critical Infra Cyber Security Icons PDF. The topics addressed in these templates are Identify, Protect, Detect. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
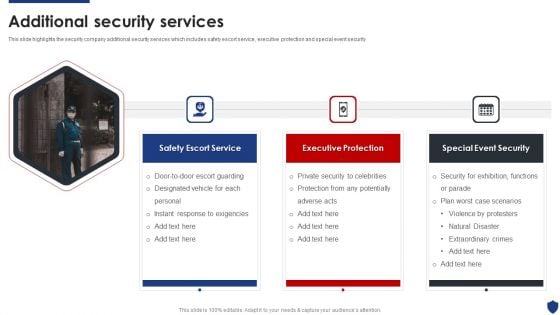
Security Officer Service Company Profile Additional Security Services Ppt PowerPoint Presentation Gallery Introduction PDF
This slide highlights the security company additional security services which includes safety escort service, executive protection and special event security. Presenting Security Officer Service Company Profile Additional Security Services Ppt PowerPoint Presentation Gallery Introduction PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Safety Escort Service, Executive Protection, Special Event Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
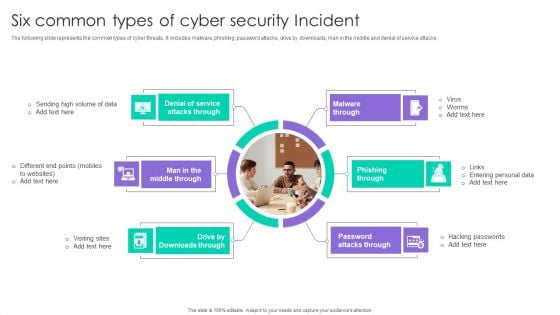
Six Common Types Of Cyber Security Incident Ppt Slides Graphics Tutorials PDF
The following slide represents the common types of cyber threats. It includes malware, phishing, password attacks, drive by downloads, man in the middle and denial of service attacks. Persuade your audience using this Six Common Types Of Cyber Security Incident Ppt Slides Graphics Tutorials PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Malware Through, Phishing Through, Password Attacks Through. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Ensuring Checklist For Mobile Security Deployment Mobile Device Security Management Pictures PDF
This slide provides information regarding mobile device security deployment checklist in terms of device security, protection against malicious codes. Deliver and pitch your topic in the best possible manner with this Ensuring Checklist For Mobile Security Deployment Mobile Device Security Management Pictures PDF. Use them to share invaluable insights on Remotely Locking, Protection Against, Malicious Codes and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

IT Security Automation Tools Integration Extended Detection And Response For Endpoint Elements PDF
This slide highlights the External Data Representation layer for end security prevention and detection which includes endpoint protection, network protection, user protection and deception. This is a IT Security Automation Tools Integration Extended Detection And Response For Endpoint Elements PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Endpoint Protection, Network Protection, User Protection, Deception. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
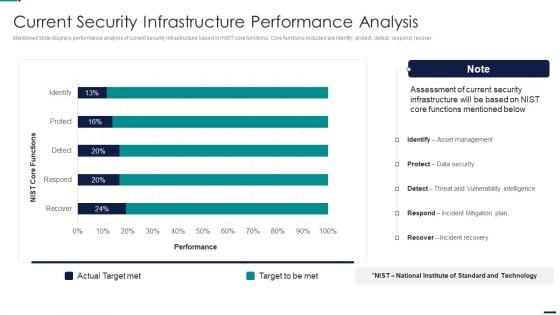
Risk Management Model For Data Security Current Security Infrastructure Performance Analysis Pictures PDF
Mentioned slide displays performance analysis of current security infrastructure based on NIST core functions. Core functions included are identify, protect, detect, respond, recover. Deliver and pitch your topic in the best possible manner with this Risk Management Model For Data Security Current Security Infrastructure Performance Analysis Pictures PDF. Use them to share invaluable insights on Identify, Protect, Detect, Respond, Recover and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
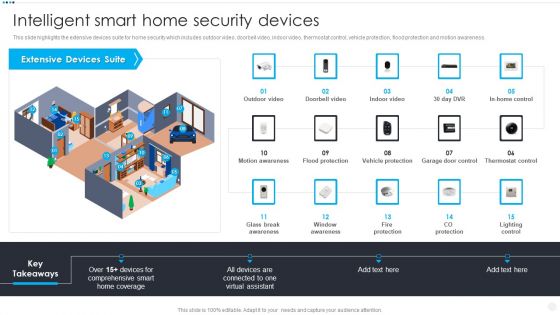
Smart Home Security Solutions Company Profile Intelligent Smart Home Security Devices Inspiration PDF
This slide highlights the extensive devices suite for home security which includes outdoor video, doorbell video, indoor video, thermostat control, vehicle protection, flood protection and motion awareness. Deliver an awe inspiring pitch with this creative Smart Home Security Solutions Company Profile Intelligent Smart Home Security Devices Inspiration PDF bundle. Topics like Extensive Devices Suite, Comprehensive Smart Home, Glass Break Awareness can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
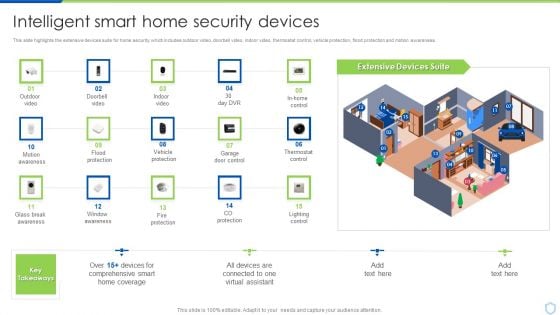
Security And Surveillance Company Profile Intelligent Smart Home Security Devices Brochure PDF
This slide highlights the extensive devices suite for home security which includes outdoor video, doorbell video, indoor video, thermostat control, vehicle protection, flood protection and motion awareness. Deliver an awe inspiring pitch with this creative Security And Surveillance Company Profile Intelligent Smart Home Security Devices Brochure PDF bundle. Topics like Awareness Campaign, Empower And Educate, Empowering Lives can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
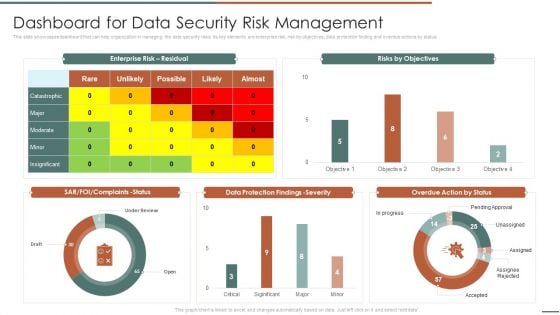
Information Security Risk Evaluation Dashboard For Data Security Risk Management Template PDF
This slide showcases dashboard that can help organization in managing the data security risks. Its key elements are enterprise risk, risk by objectives, data protection finding and overdue actions by status.Deliver an awe inspiring pitch with this creative Information Security Risk Evaluation Dashboard For Data Security Risk Management Template PDF bundle. Topics like Complaints Status, Protection Findings, Overdue Action can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
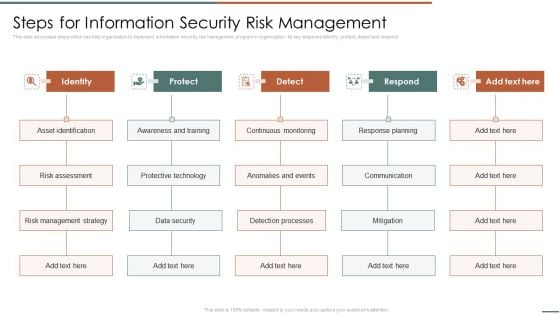
Information Security Risk Evaluation Steps For Information Security Risk Management Themes PDF
This slide showcase steps which can help organization to implement information security risk management program in organization. Its key steps are identify, protect, detect and respond.Deliver an awe inspiring pitch with this creative Information Security Risk Evaluation Steps For Information Security Risk Management Themes PDF bundle. Topics like Awareness And Training, Protective Technology, Risk Assessment can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
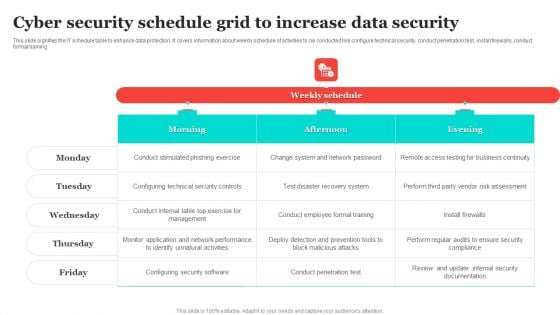
Cyber Security Schedule Grid To Increase Data Security Structure PDF
This slide signifies the IT schedule table to enhance data protection. It covers information about weekly schedule of activities to be conducted like configure technical security, conduct penetration test, install firewalls, conduct formal training. Pitch your topic with ease and precision using this Cyber Security Schedule Grid To Increase Data Security Structure PDF. This layout presents information on Recovery System, Vendor Risk Assessment, Configuring Security Software. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Online Help Internet PowerPoint Template 0910
3d illustration of a large red and white lifesaver sitting on top of an open laptop computer on a black reflective surface Operate efficiently with our Online Help Internet PowerPoint Template 0910. Download without worries with our money back guaranteee.

Eye With Code Technology PowerPoint Templates And PowerPoint Backgrounds 0311
Microsoft PowerPoint Template and Background with eye viewing digital information represented by ones and zeros Double your growth with our Eye With Code Technology PowerPoint Templates And PowerPoint Backgrounds 0311. Download without worries with our money back guaranteee.

Data Fraud Business PowerPoint Templates And PowerPoint Backgrounds 0511
Microsoft PowerPoint Template and Background with a magnifying glass over computer data background Launch your campaign with our Data Fraud Business PowerPoint Templates And PowerPoint Backgrounds 0511. Make sure your presentation gets the attention it deserves.

Data Fraud Business PowerPoint Themes And PowerPoint Slides 0511
Microsoft PowerPoint Theme and Slide with a magnifying glass over computer data Slide Exhort your team with our Data Fraud Business PowerPoint Themes And PowerPoint Slides 0511. Urge them on to go one better.

Eye With Code Technology PowerPoint Themes And PowerPoint Slides 0311
Microsoft PowerPoint Theme and Slide with eye viewing digital information represented by ones and zeros Evoke dormant ambitions with our Eye With Code Technology PowerPoint Themes And PowerPoint Slides 0311. Encourage desires to develop anew.
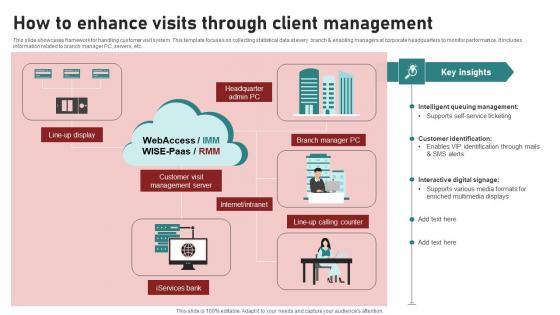
How To Enhance Visits Through Client Management Ppt Sample pdf
This slide showcases framework for handling customer visit system. This template focuses on collecting statistical data at every branch and enabling managers at corporate headquarters to monitor performance. It includes information related to branch manager PC, servers, etc. Showcasing this set of slides titled How To Enhance Visits Through Client Management Ppt Sample pdf. The topics addressed in these templates are Branch Manager PC, Services Bank, Customer Visit Management. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcases framework for handling customer visit system. This template focuses on collecting statistical data at every branch and enabling managers at corporate headquarters to monitor performance. It includes information related to branch manager PC, servers, etc.
Infrastructure As A Service Cloud Computing Strategy Icon Elements Pdf
Pitch your topic with ease and precision using this Infrastructure As A Service Cloud Computing Strategy Icon Elements Pdf. This layout presents information on Infrastructure As Service, Cloud Computing Strategy, Icon. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our Infrastructure As A Service Cloud Computing Strategy Icon Elements Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
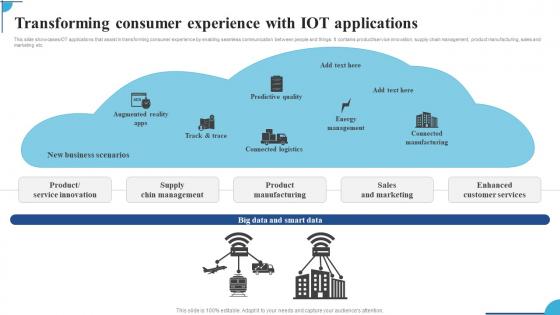
Transforming Consumer Experience With IOT Applications Ppt Slides Pictures Pdf
This slide showcases IOT applications that assist in transforming consumer experience by enabling seamless communication between people and things. It contains product service innovation,supply chain management,product manufacturing,sales and marketing etc. Showcasing this set of slides titled Transforming Consumer Experience With IOT Applications Ppt Slides Pictures Pdf. The topics addressed in these templates are Supply Chin Management,Product Manufacturing,Sales And Marketing. All the content presented in this PPT design is completely editable. Download it and make adjustments in color,background,font etc. as per your unique business setting. This slide showcases IOT applications that assist in transforming consumer experience by enabling seamless communication between people and things. It contains product service innovation,supply chain management,product manufacturing,sales and marketing etc.
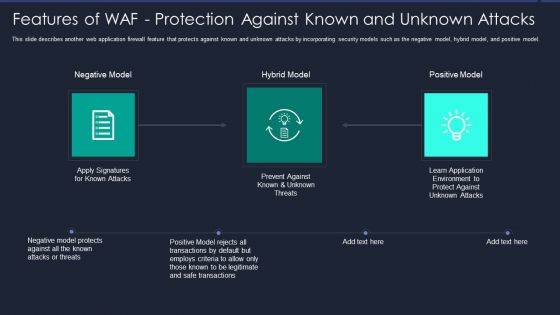
Web App Firewall Services IT Features Of WAF Protection Against Known Clipart PDF
This slide describes another web application firewall feature that protects against known and unknown attacks by incorporating security models such as the negative model, hybrid model, and positive model. Presenting web app firewall services it features of waf protection against known clipart pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like negative model, hybrid model, positive model. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Features Of WAF Protection Against Known And Unknown Attacks WAF Platform Inspiration PDF
This slide describes another web application firewall feature that protects against known and unknown attacks by incorporating security models such as the negative model, hybrid model, and positive model. Presenting Features Of WAF Protection Against Known And Unknown Attacks WAF Platform Inspiration PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Hybrid Model, Negative Model, Positive Model. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Protection Incident And Privacy Analysis With KPI Dashboard Ideas PDF
The following slide highlights some kpas of cyber security incidents to evaluate and monitor threats. It includes elements such as open incidents, warnings by severity, average response time, warnings pending for inspection etc. Showcasing this set of slides titled Cyber Protection Incident And Privacy Analysis With KPI Dashboard Ideas PDF. The topics addressed in these templates are Cyber Protection Incident, Privacy Analysis, KPI Dashboard. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Desktop Security Management Complete Computer Security Implementation Checklist Demonstration PDF
This slide depicts the cyber security checklist and measures an organization should take to protect data and company assets from cyber attacks or natural disasters. Presenting desktop security management complete computer security implementation checklist demonstration pdf to provide visual cues and insights. Share and navigate important information on twelve stages that need your due attention. This template can be used to pitch topics like technology, systems, organizations, information. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Security Assessment Cloud Security Threats Malware Attacks Inspiration PDF
This slide represents the malware threat of cloud security and how it can affect data stored on the cloud, further leading to company loss.This is a Cloud Security Assessment Cloud Security Threats Malware Attacks Inspiration PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Cloud Administrations, Information Exfiltration, Protection Frameworks. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Cloud Security Assessment Cloud Security Threats Shared Vulnerabilities Icons PDF
This slide describes how organizations and providers share vulnerabilities of a system, so each party must take precautions to protect data.This is a Cloud Security Assessment Cloud Security Threats Shared Vulnerabilities Icons PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Standards, Authorization Restrictions, Providers Already. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Secure Files Security PowerPoint Presentation Slides C
Microsoft PowerPoint Slides and Backgrounds with illustration of a lock place dinfront of and open file folder Do not leave it all up to fate. Fashion your destiny with our Secure Files Security PowerPoint Presentation Slides C.
Secure Files Security PowerPoint Presentation Slides Cc
Microsoft PowerPoint Slides and Backgrounds with illustration of a lock place dinfront of and open file folder Achieve strong & sustainable quality gains with our Secure Files Security PowerPoint Presentation Slides Cc. They will make you look good.

Secure Files Security PowerPoint Presentation Slides F
Microsoft PowerPoint Slides and Backgrounds with illustration of a lock place dinfront of and open file folder Give your thoughts an exclusive feel. Our Secure Files Security PowerPoint Presentation Slides F will give them a distinctive touch.

Secure Files Security PowerPoint Presentation Slides R
Microsoft PowerPoint Slides and Backgrounds with illustration of a lock place dinfront of and open file folder Your ideas will raise the stocks. Gain equity with our Secure Files Security PowerPoint Presentation Slides R.

Secure Files Security PowerPoint Presentation Slides S
Microsoft PowerPoint Slides and Backgrounds with illustration of a lock place dinfront of and open file folder Give a fillip to your campaign. Give it a fitting finale with our Secure Files Security PowerPoint Presentation Slides S.

Pillars Of Cloud Security Identity Security Cloud Computing Security IT Ppt Model Slides PDF
This slide depicts the identity security pillar of cloud security. It also shows how it could be beneficial to protect data from loss. This is a pillars of cloud security identity security cloud computing security it ppt model slides pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like pillars of cloud security identity security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Pillars Of Cloud Security Network Security Cloud Computing Security IT Ppt Summary Guidelines PDF
This slide defines the network security pillar of cloud security and what precautions are taken to protect networks from attacks. Presenting pillars of cloud security network security cloud computing security it ppt summary guidelines pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like performing, traffic security, micro segmentation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Information Security Pillars Of Cloud Security Network Security Ppt Inspiration Layouts PDF
This slide defines the network security pillar of cloud security and what precautions are taken to protect networks from attacks. Presenting Cloud Information Security Pillars Of Cloud Security Network Security Ppt Inspiration Layouts PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Premises Conditions, Micro Segmentation, Cloud Based Information. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Security Assessment Pillars Of Cloud Security Identity Security Clipart PDF
This slide depicts the identity security pillar of cloud security. It also shows how it could be beneficial to protect data from loss.This is a Cloud Security Assessment Pillars Of Cloud Security Identity Security Clipart PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Devices To Accomplish, Service Permissions, Information Applications You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
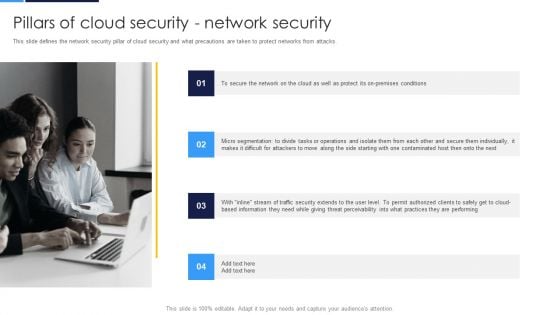
Cloud Security Assessment Pillars Of Cloud Security Network Security Mockup PDF
This slide defines the network security pillar of cloud security and what precautions are taken to protect networks from attacks.Presenting Cloud Security Assessment Pillars Of Cloud Security Network Security Mockup PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Premises Conditions, Difficult For Attackers, Them Individually In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Enhanced Protection Corporate Event Administration Budget For Effective Secops System Management Sample PDF
Firm has prepared the budget for managing security operational system management. It also provides information about the software used and the duration required for implementation. Deliver and pitch your topic in the best possible manner with this enhanced protection corporate event administration budget for effective secops system management sample pdf. Use them to share invaluable insights on functional area, software, implement duration, cost of implementation and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Enhanced Protection Corporate Event Administration Various Metrics To Measure Secops System Performance Ideas PDF
This slide portrays information regarding the various metrics that considered in order to assess SecOps system performance such as mean time to detection, mean time to resolution, total cases per month, etc. Presenting enhanced protection corporate event administration various metrics to measure secops system performance ideas pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like security, analyst, escalation, management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
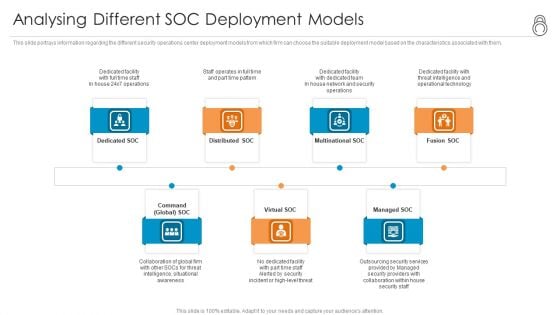
Enhanced Protection Corporate Event Administration Analysing Different SOC Deployment Models Information PDF
This slide portrays information regarding the different security operations center deployment models from which firm can choose the suitable deployment model based on the characteristics associated to the. This is a enhanced protection corporate event administration analysing different soc deployment models information pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like multinational soc, distributed soc, dedicated soc, command global soc, virtual soc. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
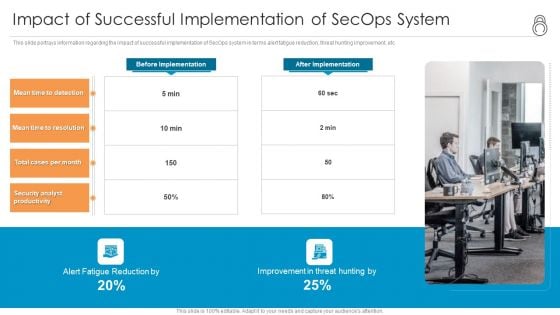
Enhanced Protection Corporate Event Administration Impact Of Successful Implementation Of Secops System Graphics PDF
This slide portrays information regarding the impact of successful implementation of SecOps system in terms alert fatigue reduction, threat hunting improvement, etc. Presenting enhanced protection corporate event administration impact of successful implementation of secops system graphics pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like security, analyst, improvement, reduction. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
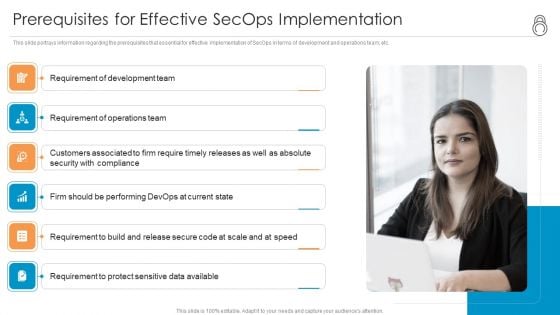
Enhanced Protection Corporate Event Administration Prerequisites For Effective Secops Implementation Inspiration PDF
This slide portrays information regarding the prerequisites that essential for effective implementation of SecOps in terms of development and operations team, etc. This is a enhanced protection corporate event administration prerequisites for effective secops implementation inspiration pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like development, data available, security with compliance, operations team. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
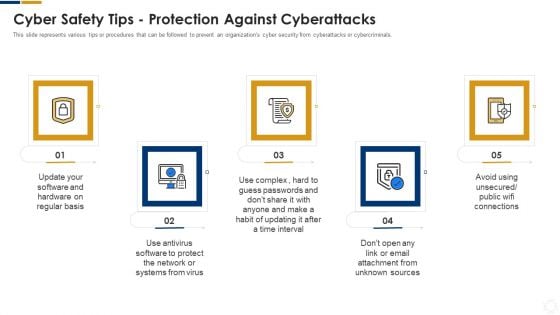
Cybersecurity Cyber Safety Tips Protection Against Cyberattacks Ppt Styles Gallery PDF
This slide represents various tips or procedures that can be followed to prevent an organizations cyber security from cyberattacks or cybercriminals. This is a cybersecurity cyber safety tips protection against cyberattacks ppt styles gallery pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like systems, network. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Major Reasons To Manage Online Protection And Privacy Issues Template PDF
The following slide highlights the major causes to administer digital security and privacy concerns. It includes activities such as setting credibility with users, optimizing social media presence, improving marketing efforts etc. Persuade your audience using this Major Reasons To Manage Online Protection And Privacy Issues Template PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Set Credibility With Users, Optimize Social Media Presence, To Reduce Damage Expenses. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Checklist To Ensure Asset Protection From Improving Cybersecurity With Incident Download PDF
Following slide displays checklist having security control measures that can be used by members to ensure the safety of companys assets from any insider threat.Present like a pro with Checklist To Ensure Asset Protection From Improving Cybersecurity With Incident Download PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Cyber Risks And Incident Response Playbook Checklist To Ensure Asset Protection From Internal Threats Structure PDF
Following slide displays checklist having security control measures that can be used by members to ensure the safety of companys assets from any insider threat. Present like a pro with Cyber Risks And Incident Response Playbook Checklist To Ensure Asset Protection From Internal Threats Structure PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether youre in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Cybersecurity Online Risk Assessment Process To Enhance Data Protection Introduction PDF
The purpose of this slide is to represent a process for cybersecurity digital risk assessment to analyze business threats. It includes various stages such as classifying information assets, evaluating risks, examining risk, observing and reviewing effectiveness and implementing security controls. Presenting Cybersecurity Online Risk Assessment Process To Enhance Data Protection Introduction PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Classify Information Assets, Evaluate Risk, Examine Risk. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Home Security Concept PowerPoint Templates And PowerPoint Themes 1012
Home Security Concept PowerPoint Templates And PowerPoint Themes 1012-Develop competitive advantage with our above template which contains a diagram of house made of colorful books on lifeline. It Imitates crisis, education, help, house, insurance, investment, learning, literature, protection, real estate agency, success and support. Our stunning image makes your presentations professional showing that you care about even the smallest details. Create captivating presentations to deliver comparative and weighted arguments.-Home Security Concept PowerPoint Templates And PowerPoint Themes 1012-This PowerPoint template can be used for presentations relating to-Home security concept, architecture, real estate, construction, security, finance Advance your career with our Home Security Concept PowerPoint Templates And PowerPoint Themes 1012. Download without worries with our money back guaranteee.
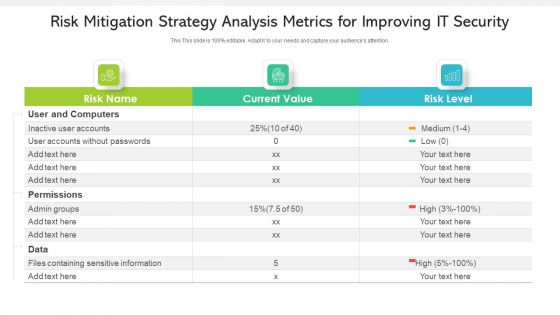
Risk Mitigation Strategy Analysis Metrics For Improving IT Security Ppt PowerPoint Presentation Gallery Gridlines PDF
Showcasing this set of slides titled risk mitigation strategy analysis metrics for improving it security ppt powerpoint presentation gallery gridlines pdf. The topics addressed in these templates are inactive user accounts, accounts without passwords, permissions. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
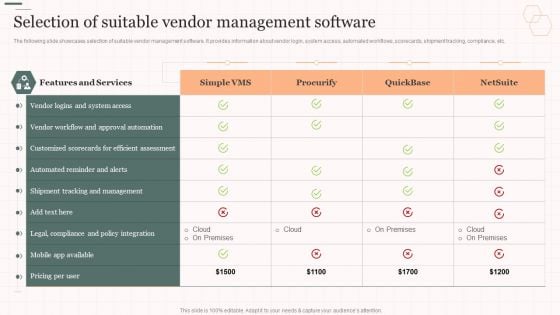
Selection Of Suitable Vendor Management Software Vendor Management Strategies Guidelines PDF
The following slide showcases selection of suitable vendor management software. It provides information about vendor login, system access, automated workflows, scorecards, shipment tracking, compliance, etc. Deliver an awe inspiring pitch with this creative Selection Of Suitable Vendor Management Software Vendor Management Strategies Guidelines PDF bundle. Topics like Approval Automation, Shipment Tracking, Legal Compliance can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Currency Umbrella Security PowerPoint Templates And PowerPoint Themes 1012
Currency Umbrella Security PowerPoint Templates And PowerPoint Themes 1012-The euro is the currency used by the Institutions of the European Union and is the official currency of the Eurozone. This Template shows the currency Euro under the Umbrella which signifies the increasing rate of Euro from 2010 to 2012. Stable ideas are the building blocks of a successful structure. Lay down the fundamentals to build upon. Take it up to a higher level with your thoughts. -Currency Umbrella Security PowerPoint Templates And PowerPoint Themes 1012-This PowerPoint template can be used for presentations relating to-Currency protected by umbrella, security, business, money, shapes, metaphor Start accelerating revenue growth with our Currency Umbrella Security PowerPoint Templates And PowerPoint Themes 1012. They will make you look good.
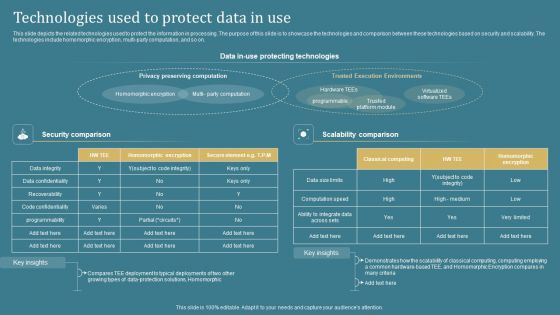
Confidential Computing System Technology Technologies Used To Protect Data In Use Inspiration PDF
This slide depicts the related technologies used to protect the information in processing. The purpose of this slide is to showcase the technologies and comparison between these technologies based on security and scalability. The technologies include homomorphic encryption, multi-party computation, and so on. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Confidential Computing System Technology Technologies Used To Protect Data In Use Inspiration PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Confidential Computing System Technology Technologies Used To Protect Data In Use Inspiration PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.
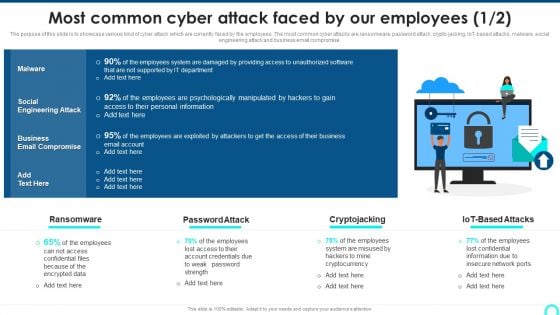
Most Common Cyber Attack Faced By Our Employees Clipart PDF
The purpose of this slide is to showcase various kind of cyber attack which are currently faced by the employees. The most common cyber attacks are ransomware, password attack, crypto jacking, IoT-based attacks, malware, social engineering attack and business email compromise. This is a Most Common Cyber Attack Faced By Our Employees Clipart PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Employees Psychologically, Personal Information, Psychologically Manipulated. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
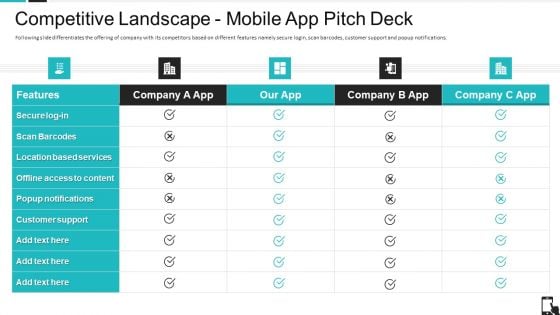
Competitive Landscape Mobile App Pitch Deck Ppt File Layout PDF
Following slide differentiates the offering of company with its competitors based on different features namely secure login, scan barcodes, customer support and popup notifications. Deliver an awe inspiring pitch with this creative competitive landscape mobile app pitch deck ppt file layout pdf bundle. Topics like secure login, scan barcodes, customer support, popup notifications, location based services, offline access to content can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Security Management Technology Framework Themes PDF
This slide provides a strategic framework for cyber security management used by organisations to implement and monitor the essential activities. Key components are to identify, protect, detect, respond and recover. Persuade your audience using this Cyber Security Management Technology Framework Themes PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Protect, Identify, Detect, Respond, Recover. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.


 Continue with Email
Continue with Email

 Home
Home


































