Balloon Celebration

Stock Offering As An Exit Alternative Strategic Acquisition By Third Party Process Timeline Diagrams PDF
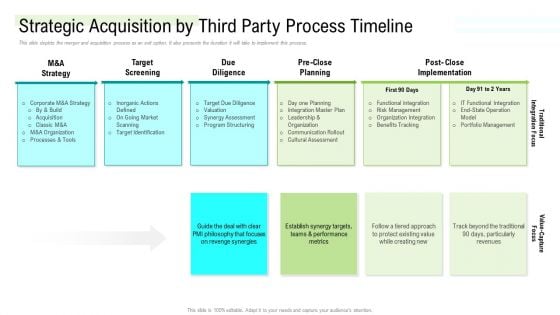
This slide depicts the merger and acquisition process as an exit option. It also presents the duration it will take to implement this process. Deliver and pitch your topic in the best possible manner with this stock offering as an exit alternative strategic acquisition by third party process timeline diagrams pdf. Use them to share invaluable insights on strategy, target, due diligence, planning, implementation and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
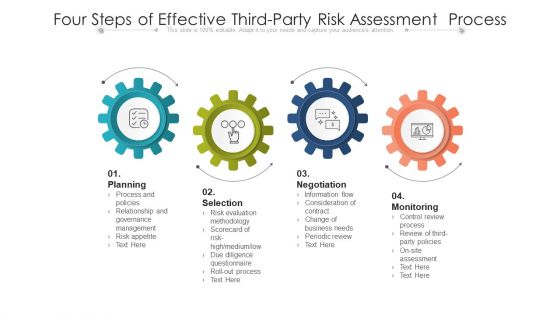
Four Steps Of Effective Third Party Risk Assessment Process Ppt PowerPoint Presentation File Information PDF
Persuade your audience using this four steps of effective third party risk assessment process ppt powerpoint presentation file information pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including planning, negotiation, monitoring. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
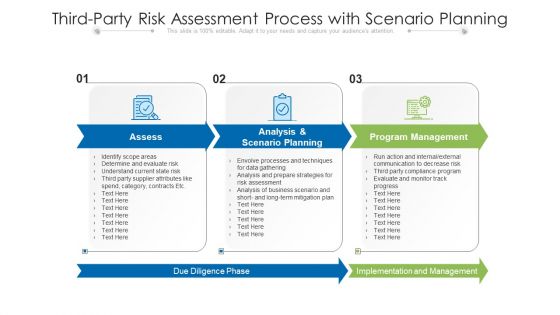
Third Party Risk Assessment Process With Scenario Planning Ppt PowerPoint Presentation Gallery Infographic Template PDF
Persuade your audience using this third party risk assessment process with scenario planning ppt powerpoint presentation gallery infographic template pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including assess, analysis and scenario planning, program management. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
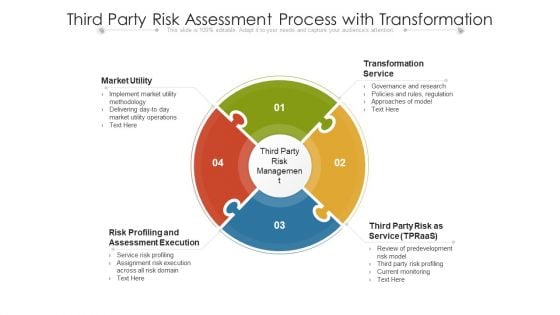
Third Party Risk Assessment Process With Transformation Ppt PowerPoint Presentation Gallery Samples PDF
Persuade your audience using this third party risk assessment process with transformation ppt powerpoint presentation gallery samples pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including market utility, transformation service, assessment execution. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
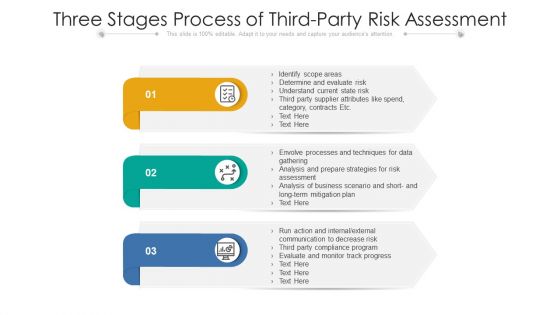
Three Stages Process Of Third Party Risk Assessment Ppt PowerPoint Presentation File Smartart PDF
Persuade your audience using this three stages process of third party risk assessment ppt powerpoint presentation file smartart pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including evaluate, business, communication. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
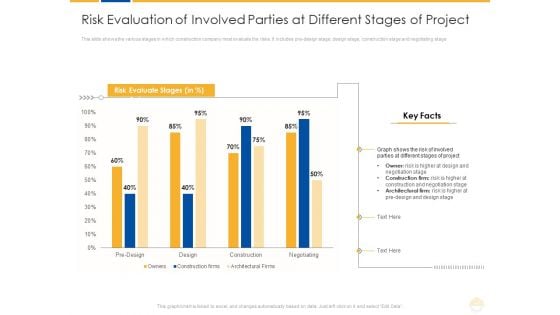
Risk Evaluation Of Involved Parties At Different Stages Of Project Ppt Outline Objects PDF
This slide shows the various stages in which construction company most evaluate the risks. It includes pre design stage, design stage, construction stage and negotiating stage. Deliver an awe inspiring pitch with this creative risk evaluation of involved parties at different stages of project ppt outline objects pdf bundle. Topics like risk, design, project can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
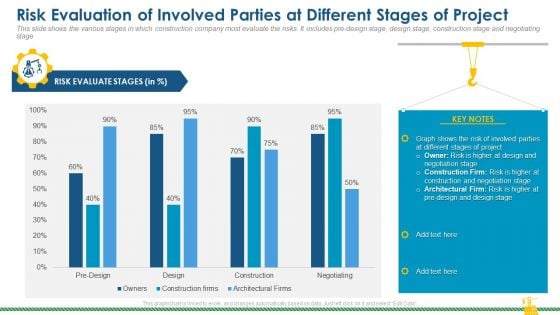
Risk Evaluation Of Involved Parties At Different Stages Of Project Formats PDF
This slide shows the various stages in which construction company most evaluate the risks. It includes pre design stage, design stage, construction stage and negotiating stage. Deliver and pitch your topic in the best possible manner with this risk evaluation of involved parties at different stages of project formats pdf. Use them to share invaluable insights on risk evaluate, project, negotiation stage and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
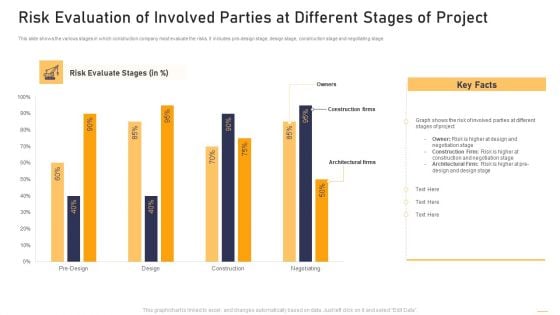
Surge In Construction Faults Lawsuits Case Competition Risk Evaluation Of Involved Parties Topics PDF
This slide shows the various stages in which construction company most evaluate the risks. It includes pre-design stage, design stage, construction stage and negotiating stage. Deliver an awe inspiring pitch with this creative surge in construction faults lawsuits case competition risk evaluation of involved parties topics pdf bundle. Topics like pre design stage, design stage, construction stage, negotiating stage can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

International Organization Standardization 270001 Understanding The Requirement Of Interested Parties Diagrams PDF
Mentioned slide displays various requirements of internal as well as external stakeholders of the organization. Internal stakeholders covered in the slide are board of directors and employee. Deliver and pitch your topic in the best possible manner with this international organization standardization 270001 understanding the requirement of interested parties diagrams pdf. Use them to share invaluable insights on customers, employees, board of directors and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
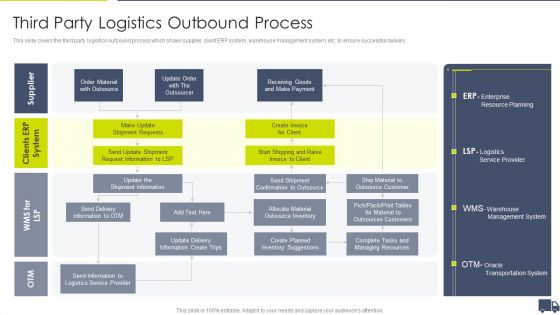
Enhancing Logistics Customer Service Third Party Logistics Outbound Process Topics PDF
This is a Enhancing Logistics Customer Service Third Party Logistics Outbound Process Topics PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Clients ERP System, Supplier Order Material, Send Delivery Information. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Vendor Management To Handle Purchase Third Party Vendor Risk Management Framework Clipart PDF
This is a Vendor Management To Handle Purchase Third Party Vendor Risk Management Framework Clipart PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Helping Organization, Preonboarding Stage, Implemented Vendor. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
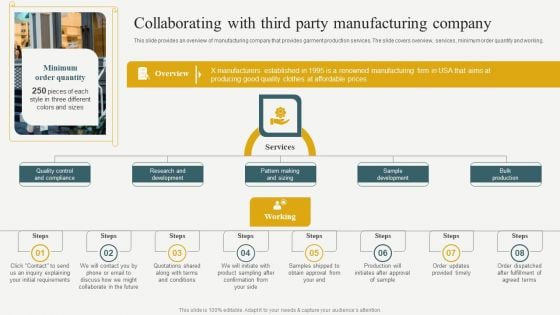
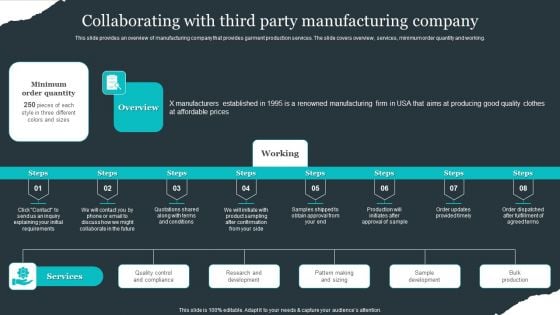
Evaluating Financial Position Of E Commerce Company Collaborating With Third Party Manufacturing Company Designs PDF
This slide provides an overview of manufacturing company that provides garment production services. The slide covers overview, services, minimum order quantity and working. There are so many reasons you need a Evaluating Financial Position Of E Commerce Company Collaborating With Third Party Manufacturing Company Designs PDF. The first reason is you cannot spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
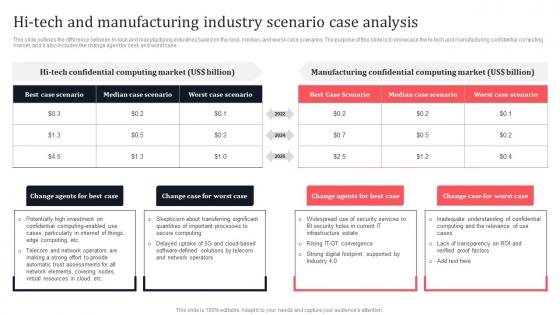
Hi Tech And Manufacturing Industry Scenario Case Analysis Secure Multi Party Graphics Pdf
This slide outlines the difference between hi-tech and manufacturing industries based on the best, median, and worst-case scenarios. The purpose of this slide is to showcase the hi-tech and manufacturing confidential computing market, and it also includes the change agent for best, and worst case. Presenting this PowerPoint presentation, titled Hi Tech And Manufacturing Industry Scenario Case Analysis Secure Multi Party Graphics Pdf with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Hi Tech And Manufacturing Industry Scenario Case Analysis Secure Multi Party Graphics Pdf Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Hi Tech And Manufacturing Industry Scenario Case Analysis Secure Multi Party Graphics Pdf that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide outlines the difference between hi-tech and manufacturing industries based on the best, median, and worst-case scenarios. The purpose of this slide is to showcase the hi-tech and manufacturing confidential computing market, and it also includes the change agent for best, and worst case.
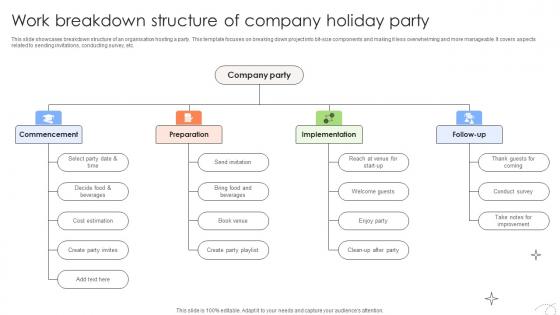
Executing And Monitoring Project Work Breakdown Structure Of Company Holiday Party PM SS V
This slide showcases breakdown structure of an organisation hosting a party. This template focuses on breaking down project into bit-size components and making it less overwhelming and more manageable. It covers aspects related to sending invitations, conducting survey, etc. Do you know about Slidesgeeks Executing And Monitoring Project Work Breakdown Structure Of Company Holiday Party PM SS V These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide showcases breakdown structure of an organisation hosting a party. This template focuses on breaking down project into bit-size components and making it less overwhelming and more manageable. It covers aspects related to sending invitations, conducting survey, etc.
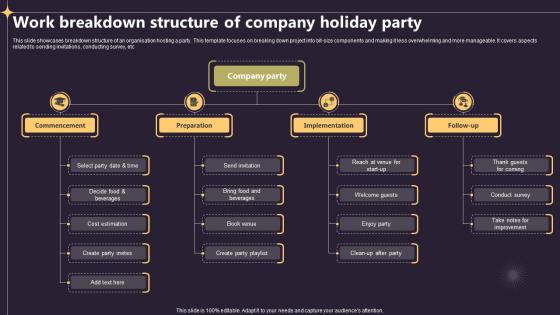
Closing A Project By Fulfilling Work Breakdown Structure Of Company Holiday Party PM SS V
This slide showcases breakdown structure of an organisation hosting a party. This template focuses on breaking down project into bit-size components and making it less overwhelming and more manageable. It covers aspects related to sending invitations, conducting survey, etc. This Closing A Project By Fulfilling Work Breakdown Structure Of Company Holiday Party PM SS V from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide showcases breakdown structure of an organisation hosting a party. This template focuses on breaking down project into bit-size components and making it less overwhelming and more manageable. It covers aspects related to sending invitations, conducting survey, etc.

Mobile Text Message For Birthday Greetings Ppt PowerPoint Presentation Portfolio Outfit PDF
Presenting mobile text message for birthday greetings ppt powerpoint presentation portfolio outfit pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including mobile text message for birthday greetings. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
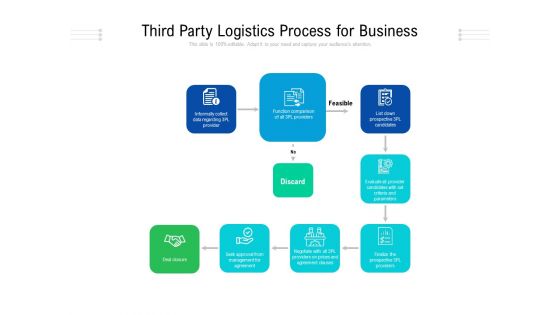
Third Party Logistics Process For Business Ppt PowerPoint Presentation Outline Themes PDF
Persuade your audience using this third party logistics process for business ppt powerpoint presentation outline themes pdf. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including deal closure, informally collect data regarding 3pl provider, function comparison of all 3pl providers, feasible, list down prospective 3pl candidates, discard, seek approval from management for agreement. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
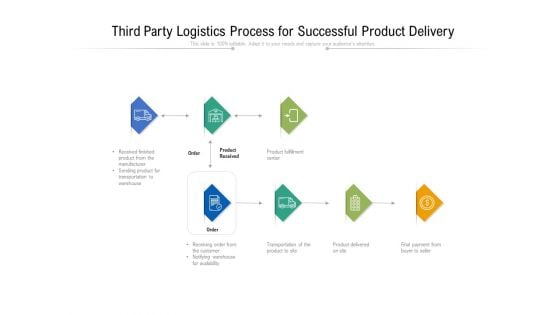
Third Party Logistics Process For Successful Product Delivery Ppt PowerPoint Presentation Layouts Elements PDF
Persuade your audience using this third party logistics process for successful product delivery ppt powerpoint presentation layouts elements pdf. This PPT design covers seven stages, thus making it a great tool to use. It also caters to a variety of topics including product fulfillment center, receiving order from the customer, product delivered on site, final payment from buyer to seller, received finished product from the manufacturer. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
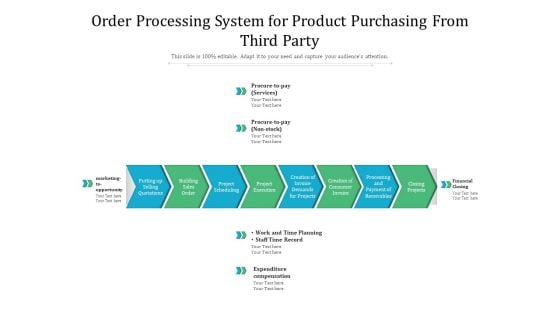
Order Processing System For Product Purchasing From Third Party Ppt PowerPoint Presentation Ideas Example PDF
Presenting order processing system for product purchasing from third party ppt powerpoint presentation ideas example pdf to dispense important information. This template comprises eight stages. It also presents valuable insights into the topics including putting up selling quotations, building sales order, project scheduling, project execution, creation of invoice demands for projects, creation of consumer invoice, processing and payment of receivables, closing projects. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Management Acquisition As Exit Strategy Ownership Transfer Strategic Acquisition By Third Party Process Timeline Rules PDF
This slide depicts the merger and acquisition process as an exit option. It also presents the duration it will take to implement this process. This is a management acquisition as exit strategy ownership transfer strategic acquisition by third party process timeline rules pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like market, organization, strategy, plan, performance. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
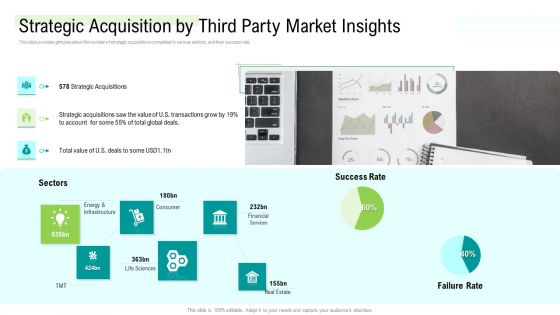
Management Acquisition As Exit Strategy Ownership Transfer Strategic Acquisition By Third Party Market Insights Ideas PDF
This slide provides glimpse about the number of strategic acquisitions completed in various sectors, and their success rate. This is a management acquisition as exit strategy ownership transfer strategic acquisition by third party market insights ideas pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like strategic, value, global, success rate, financial services. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
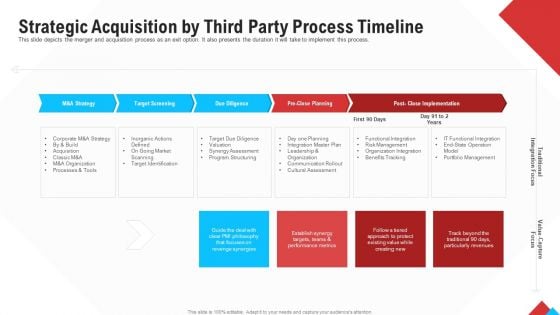
Reform Endgame Strategic Acquisition By Third Party Process Timeline Pictures PDF
This slide depicts the merger and acquisition process as an exit option. It also presents the duration it will take to implement this process. This is a reform endgame strategic acquisition by third party process timeline pictures pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like m and a strategy, target screening, due diligence, pre close planning, post close implementation. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
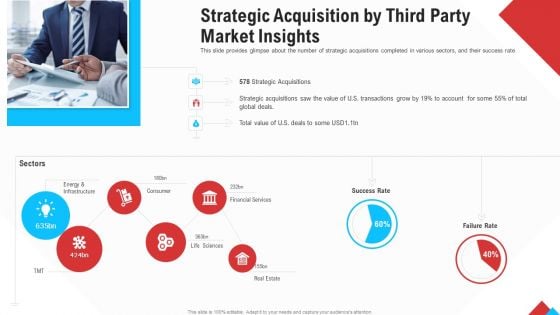
Reform Endgame Strategic Acquisition By Third Party Market Insights Brochure PDF
This slide provides glimpse about the number of strategic acquisitions completed in various sectors, and their success rate. This is a reform endgame strategic acquisition by third party market insights brochure pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like infrastructure, consumer, financial services, success rate, failure rate. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
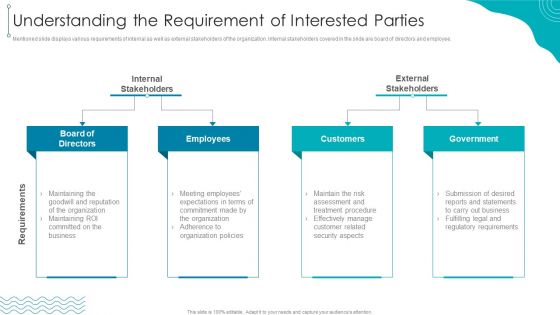
ISO 27001 Organizational Qualifying Procedure Understanding The Requirement Of Interested Parties Sample PDF
Mentioned slide displays various requirements of internal as well as external stakeholders of the organization. Internal stakeholders covered in the slide are board of directors and employee.This is a ISO 27001 Organizational Qualifying Procedure Understanding The Requirement Of Interested Parties Sample PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Internal Stakeholders, External Stakeholders, Reputation Organization. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
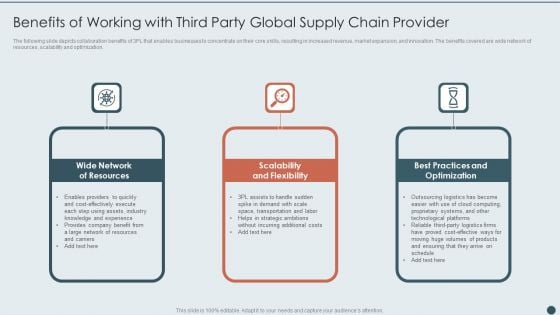
Benefits Of Working With Third Party Global Supply Chain Provider Download PDF
The following slide depicts collaboration benefits of 3PL that enables businesses to concentrate on their core skills, resulting in increased revenue, market expansion, and innovation. The benefits covered are wide network of resources, scalability and optimization. Presenting Benefits Of Working With Third Party Global Supply Chain Provider Download PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Wide Network Of Resources, Scalability And Flexibility, Best Practices And Optimization. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
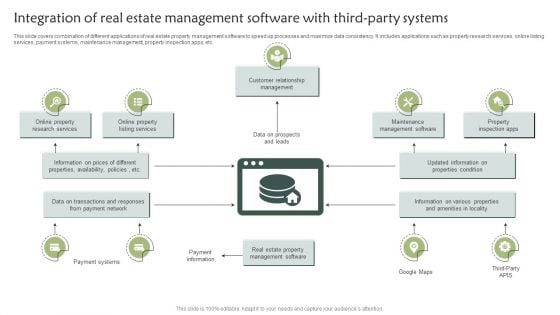
Integration Of Real Estate Management Software With Third Party Systems Guidelines PDF
This slide covers combination of different applications of real estate property management software to speed up processes and maximize data consistency. It includes applications such as property research services, online listing services, payment systems, maintenance management, property inspection apps, etc. Pitch your topic with ease and precision using this Integration Of Real Estate Management Software With Third Party Systems Guidelines PDF. This layout presents information on Customer Relationship Management, Maintenance Management Software, Payment Information. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Retail Apparel Online Collaborating With Third Party Manufacturing Company Mockup PDF
This slide provides an overview of manufacturing company that provides garment production services. The slide covers overview, services, minimum order quantity and working. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Retail Apparel Online Collaborating With Third Party Manufacturing Company Mockup PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

E Commerce Clothing Business Strategy Collaborating With Third Party Manufacturing Company Structure PDF
This slide provides an overview of manufacturing company that provides garment production services. The slide covers overview, services, minimum order quantity and working.From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. E Commerce Clothing Business Strategy Collaborating With Third Party Manufacturing Company Structure PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
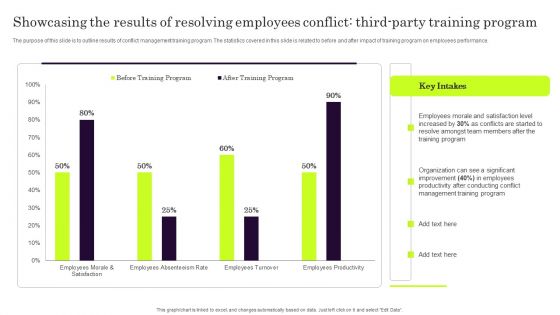
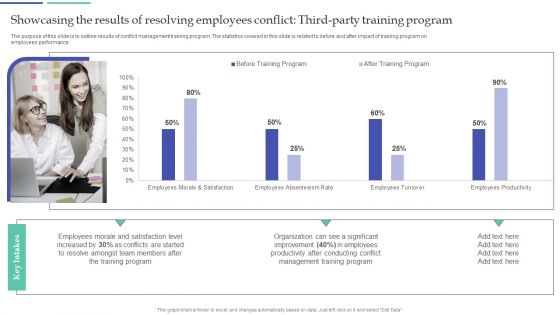
Showcasing The Results Of Resolving Employees Conflict Third Party Training Program Diagrams PDF
The purpose of this slide is to outline results of conflict management training program. The statistics covered in this slide is related to before and after impact of training program on employees performance. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Showcasing The Results Of Resolving Employees Conflict Third Party Training Program Diagrams PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
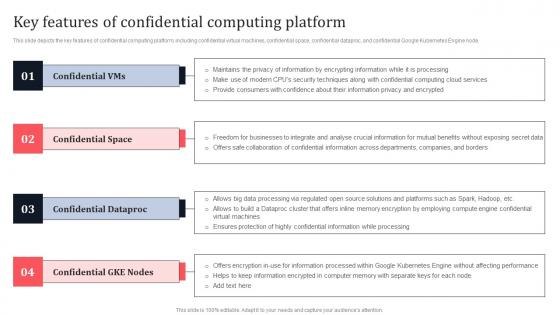
Key Features Of Confidential Computing Platform Secure Multi Party Background Pdf
This slide depicts the key features of confidential computing platform, including confidential virtual machines, confidential space, confidential dataproc, and confidential Google Kubernetes Engine node. Find a pre-designed and impeccable Key Features Of Confidential Computing Platform Secure Multi Party Background Pdf The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide depicts the key features of confidential computing platform, including confidential virtual machines, confidential space, confidential dataproc, and confidential Google Kubernetes Engine node.
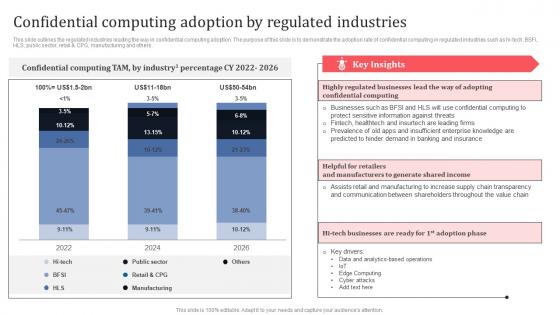
Confidential Computing Adoption By Regulated Industries Secure Multi Party Professional Pdf
This slide outlines the regulated industries leading the way in confidential computing adoption. The purpose of this slide is to demonstrate the adoption rate of confidential computing in regulated industries such as hi-tech, BSFI, HLS, public sector, retail and CPG, manufacturing and others. Get a simple yet stunning designed Confidential Computing Adoption By Regulated Industries Secure Multi Party Professional Pdf It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Confidential Computing Adoption By Regulated Industries Secure Multi Party Professional Pdf can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide outlines the regulated industries leading the way in confidential computing adoption. The purpose of this slide is to demonstrate the adoption rate of confidential computing in regulated industries such as hi-tech, BSFI, HLS, public sector, retail and CPG, manufacturing and others.
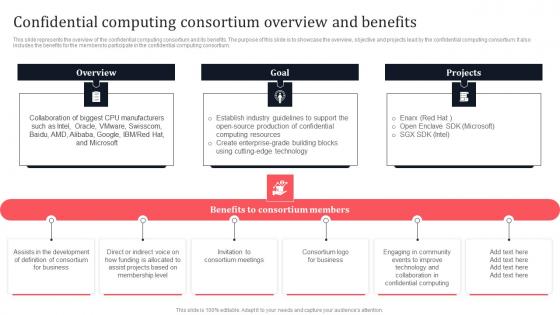
Confidential Computing Consortium Overview And Benefits Secure Multi Party Demonstration Pdf
This slide represents the overview of the confidential computing consortium and its benefits. The purpose of this slide is to showcase the overview, objective and projects lead by the confidential computing consortium. It also includes the benefits for the members to participate in the confidential computing consortium. If you are looking for a format to display your unique thoughts, then the professionally designed Confidential Computing Consortium Overview And Benefits Secure Multi Party Demonstration Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Confidential Computing Consortium Overview And Benefits Secure Multi Party Demonstration Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide represents the overview of the confidential computing consortium and its benefits. The purpose of this slide is to showcase the overview, objective and projects lead by the confidential computing consortium. It also includes the benefits for the members to participate in the confidential computing consortium.
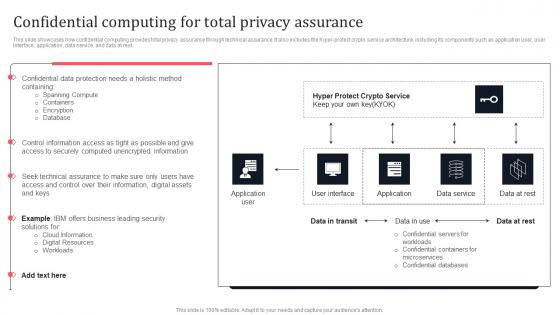
Confidential Computing For Total Privacy Assurance Secure Multi Party Brochure Pdf
This slide showcases how confidential computing provides total privacy assurance through technical assurance. It also includes the hyper-protect crypto service architecture, including its components such as application user, user interface, application, data service, and data at rest. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Confidential Computing For Total Privacy Assurance Secure Multi Party Brochure Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Confidential Computing For Total Privacy Assurance Secure Multi Party Brochure Pdf that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers. This slide showcases how confidential computing provides total privacy assurance through technical assurance. It also includes the hyper-protect crypto service architecture, including its components such as application user, user interface, application, data service, and data at rest.
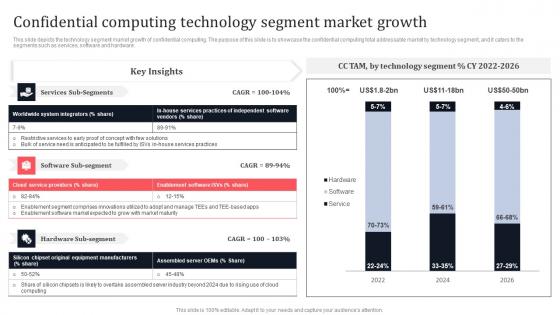
Confidential Computing Technology Segment Market Growth Secure Multi Party Guidelines Pdf
This slide depicts the technology segment market growth of confidential computing. The purpose of this slide is to showcase the confidential computing total addressable market by technology segment, and it caters to the segments such as services, software and hardware. This Confidential Computing Technology Segment Market Growth Secure Multi Party Guidelines Pdf is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Confidential Computing Technology Segment Market Growth Secure Multi Party Guidelines Pdf features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide depicts the technology segment market growth of confidential computing. The purpose of this slide is to showcase the confidential computing total addressable market by technology segment, and it caters to the segments such as services, software and hardware.
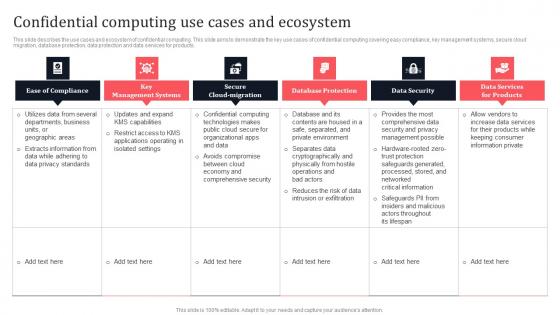
Confidential Computing Use Cases And Ecosystem Secure Multi Party Mockup Pdf
This slide describes the use cases and ecosystem of confidential computing. This slide aims to demonstrate the key use cases of confidential computing covering easy compliance, key management systems, secure cloud migration, database protection, data protection and data services for products. Explore a selection of the finest Confidential Computing Use Cases And Ecosystem Secure Multi Party Mockup Pdf here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Confidential Computing Use Cases And Ecosystem Secure Multi Party Mockup Pdf to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide describes the use cases and ecosystem of confidential computing. This slide aims to demonstrate the key use cases of confidential computing covering easy compliance, key management systems, secure cloud migration, database protection, data protection and data services for products.
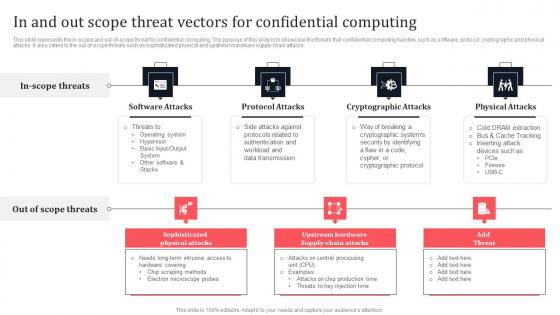
In And Out Scope Threat Vectors For Confidential Computing Secure Multi Party Elements Pdf
This slide represents the in-scope and out-of-scope threat for confidential computing. The purpose of this slide is to showcase the threats that confidential computing handles, such as software, protocol, cryptographic and physical attacks. It also caters to the out of scope threats such as sophisticated physical and upstream hardware supply-chain attacks. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download In And Out Scope Threat Vectors For Confidential Computing Secure Multi Party Elements Pdf to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the In And Out Scope Threat Vectors For Confidential Computing Secure Multi Party Elements Pdf This slide represents the in-scope and out-of-scope threat for confidential computing. The purpose of this slide is to showcase the threats that confidential computing handles, such as software, protocol, cryptographic and physical attacks. It also caters to the out of scope threats such as sophisticated physical and upstream hardware supply-chain attacks.
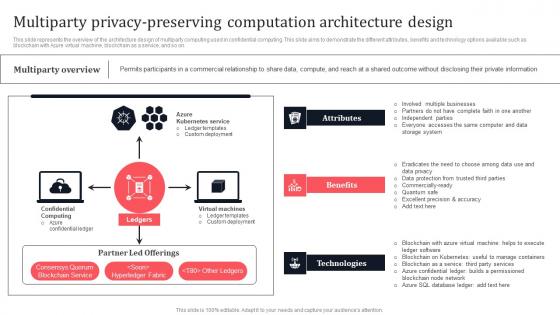
Multiparty Privacy Preserving Computation Architecture Design Secure Multi Party Demonstration Pdf
This slide represents the overview of the architecture design of multiparty computing used in confidential computing. This slide aims to demonstrate the different attributes, benefits and technology options available such as blockchain with Azure virtual machine, blockchain as a service, and so on. Create an editable Multiparty Privacy Preserving Computation Architecture Design Secure Multi Party Demonstration Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Multiparty Privacy Preserving Computation Architecture Design Secure Multi Party Demonstration Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide represents the overview of the architecture design of multiparty computing used in confidential computing. This slide aims to demonstrate the different attributes, benefits and technology options available such as blockchain with Azure virtual machine, blockchain as a service, and so on.
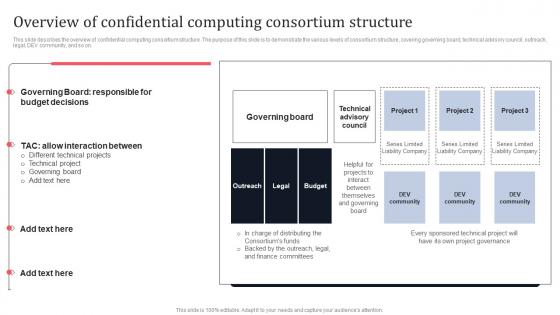
Overview Of Confidential Computing Consortium Structure Secure Multi Party Formats Pdf
This slide describes the overview of confidential computing consortium structure. The purpose of this slide is to demonstrate the various levels of consortium structure, covering governing board, technical advisory council, outreach, legal, DEV community, and so on. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Overview Of Confidential Computing Consortium Structure Secure Multi Party Formats Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Overview Of Confidential Computing Consortium Structure Secure Multi Party Formats Pdf You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today. This slide describes the overview of confidential computing consortium structure. The purpose of this slide is to demonstrate the various levels of consortium structure, covering governing board, technical advisory council, outreach, legal, DEV community, and so on.
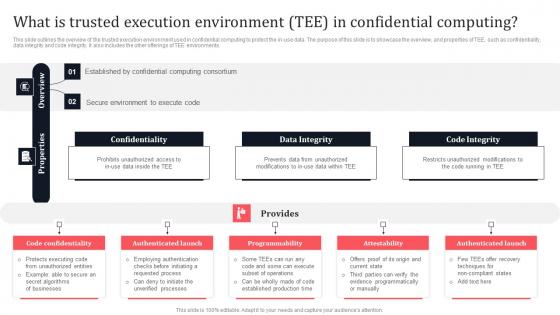
What Is Trusted Execution Environment Tee In Confidential Secure Multi Party Slides Pdf
This slide outlines the overview of the trusted execution environment used in confidential computing to protect the in-use data. The purpose of this slide is to showcase the overview, and properties of TEE, such as confidentiality, data integrity and code integrity. It also includes the other offerings of TEE environments. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our What Is Trusted Execution Environment Tee In Confidential Secure Multi Party Slides Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into What Is Trusted Execution Environment Tee In Confidential Secure Multi Party Slides Pdf This slide outlines the overview of the trusted execution environment used in confidential computing to protect the in-use data. The purpose of this slide is to showcase the overview, and properties of TEE, such as confidentiality, data integrity and code integrity. It also includes the other offerings of TEE environments.
Resolving Team Disputes In Organization Showcasing The Results Of Resolving Employees Conflict Third Party Graphics PDF
The purpose of this slide is to outline the results of resolving workplace conflicts after developing in house strategy. Reduction in stress level, increase in trust level, improved work performance and increase in employee retention rate are the major benefits which are mentioned in the slide. Boost your pitch with our creative Resolving Team Disputes In Organization Showcasing The Results Of Resolving Employees Conflict Third Party Graphics PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you don not have to invest time in any additional work. Just grab the template now and use them.
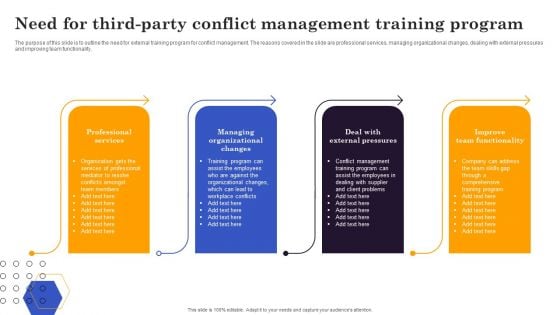
Conflict Resolution Method Need For Third Party Conflict Management Training Program Microsoft PDF
The purpose of this slide is to outline the need for external training program for conflict management. The reasons covered in the slide are professional services, managing organizational changes, dealing with external pressures and improving team functionality. Slidegeeks is here to make your presentations a breeze with Conflict Resolution Method Need For Third Party Conflict Management Training Program Microsoft PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
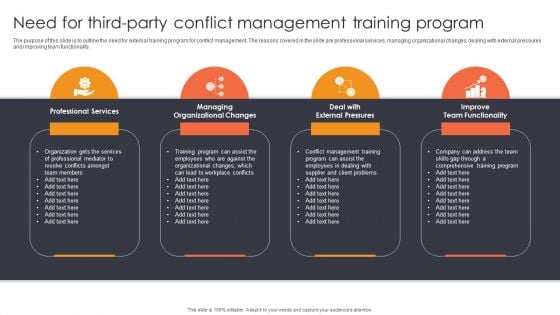
Need For Third Party Conflict Management Training Program Ppt Gallery Portfolio PDF
The purpose of this slide is to outline the need for external training program for conflict management. The reasons covered in the slide are professional services, managing organizational changes, dealing with external pressures and improving team functionality. The Need For Third Party Conflict Management Training Program Ppt Gallery Portfolio PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
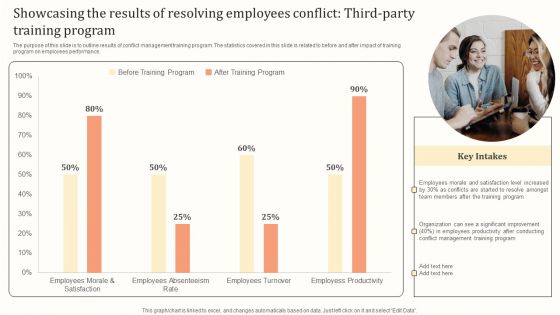
Showcasing The Results Of Resolving Employees Conflict Third Party Training Program Structure PDF
The purpose of this slide is to outline results of conflict management training program. The statistics covered in this slide is related to before and after impact of training program on employees performance. Do you know about Slidesgeeks Showcasing The Results Of Resolving Employees Conflict Third Party Training Program Structure PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
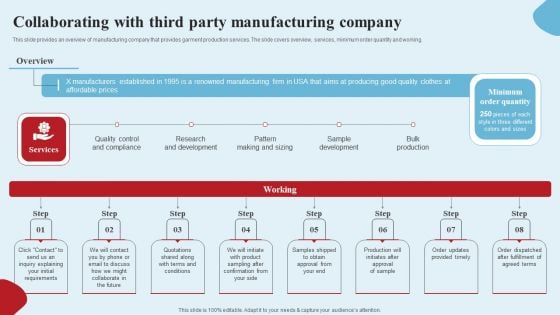
Apparel Ecommerce Business Strategy Collaborating With Third Party Manufacturing Company Pictures PDF
This slide provides an overview of manufacturing company that provides garment production services. The slide covers overview, services, minimum order quantity and working. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Apparel Ecommerce Business Strategy Collaborating With Third Party Manufacturing Company Pictures PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Budget For Implementing Confidential Computing Architecture Secure Multi Party Brochure Pdf
This slide describes the implementation cost of confidential computing, including required tools, hardware and software costs, and other expenditures. The purpose of this slide is to showcase the estimated cost, actual cost and variance. Find a pre-designed and impeccable Budget For Implementing Confidential Computing Architecture Secure Multi Party Brochure Pdf The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide describes the implementation cost of confidential computing, including required tools, hardware and software costs, and other expenditures. The purpose of this slide is to showcase the estimated cost, actual cost and variance.
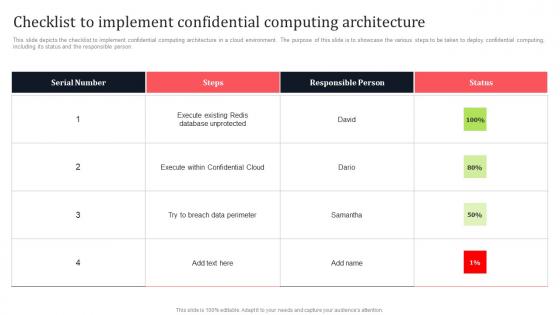
Checklist To Implement Confidential Computing Architecture Secure Multi Party Guidelines Pdf
This slide depicts the checklist to implement confidential computing architecture in a cloud environment. The purpose of this slide is to showcase the various steps to be taken to deploy confidential computing, including its status and the responsible person. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Checklist To Implement Confidential Computing Architecture Secure Multi Party Guidelines Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide depicts the checklist to implement confidential computing architecture in a cloud environment. The purpose of this slide is to showcase the various steps to be taken to deploy confidential computing, including its status and the responsible person.
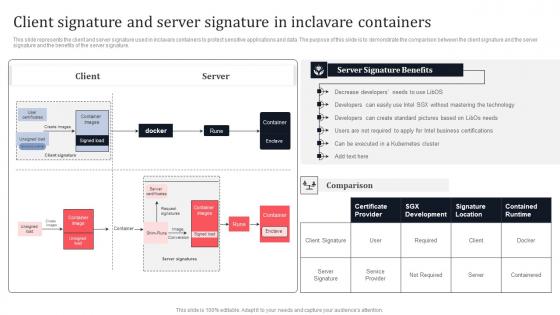
Client Signature And Server Signature In Inclavare Containers Secure Multi Party Mockup Pdf
This slide represents the client and server signature used in inclavare containers to protect sensitive applications and data. The purpose of this slide is to demonstrate the comparison between the client signature and the server signature and the benefits of the server signature. Want to ace your presentation in front of a live audience Our Client Signature And Server Signature In Inclavare Containers Secure Multi Party Mockup Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide represents the client and server signature used in inclavare containers to protect sensitive applications and data. The purpose of this slide is to demonstrate the comparison between the client signature and the server signature and the benefits of the server signature.
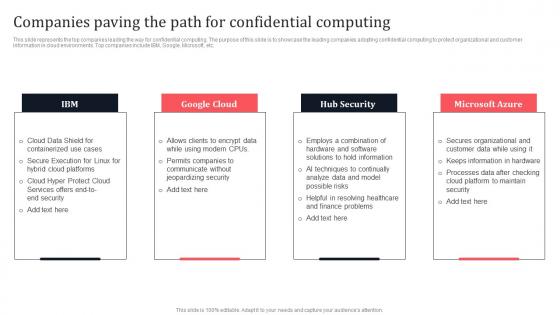
Companies Paving The Path For Confidential Computing Secure Multi Party Elements Pdf
This slide represents the top companies leading the way for confidential computing. The purpose of this slide is to showcase the leading companies adopting confidential computing to protect organizational and customer information in cloud environments. Top companies include IBM, Google, Microsoft, etc. There are so many reasons you need a Companies Paving The Path For Confidential Computing Secure Multi Party Elements Pdf The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide represents the top companies leading the way for confidential computing. The purpose of this slide is to showcase the leading companies adopting confidential computing to protect organizational and customer information in cloud environments. Top companies include IBM, Google, Microsoft, etc.
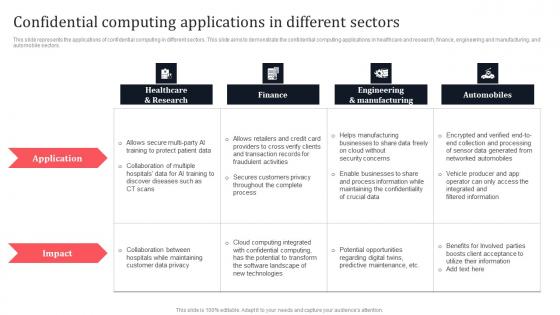
Confidential Computing Applications In Different Sectors Secure Multi Party Slides Pdf
This slide represents the applications of confidential computing in different sectors. This slide aims to demonstrate the confidential computing applications in healthcare and research, finance, engineering and manufacturing, and automobile sectors. Present like a pro with Confidential Computing Applications In Different Sectors Secure Multi Party Slides Pdf Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide represents the applications of confidential computing in different sectors. This slide aims to demonstrate the confidential computing applications in healthcare and research, finance, engineering and manufacturing, and automobile sectors.
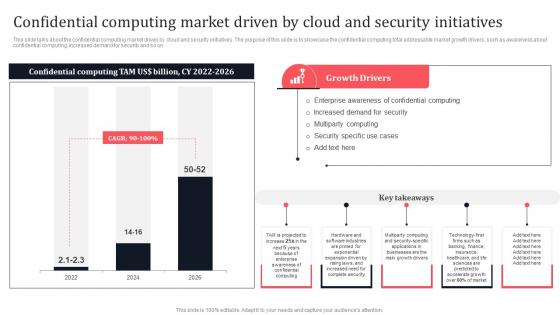
Confidential Computing Market Driven By Cloud And Security Secure Multi Party Microsoft Pdf
This slide talks about the confidential computing market driven by cloud and security initiatives. The purpose of this slide is to showcase the confidential computing total addressable market growth drivers, such as awareness about confidential computing, increased demand for security and so on. Make sure to capture your audiences attention in your business displays with our gratis customizable Confidential Computing Market Driven By Cloud And Security Secure Multi Party Microsoft Pdf These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide talks about the confidential computing market driven by cloud and security initiatives. The purpose of this slide is to showcase the confidential computing total addressable market growth drivers, such as awareness about confidential computing, increased demand for security and so on.
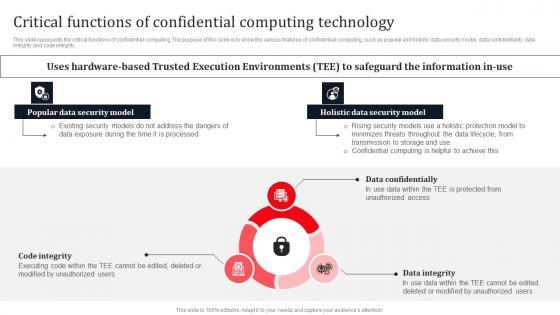
Critical Functions Of Confidential Computing Technology Secure Multi Party Information Pdf
This slide represents the critical functions of confidential computing. The purpose of this slide is to show the various features of confidential computing, such as popular and holistic data security model, data confidentiality, data integrity and code integrity. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Critical Functions Of Confidential Computing Technology Secure Multi Party Information Pdf from Slidegeeks and deliver a wonderful presentation. This slide represents the critical functions of confidential computing. The purpose of this slide is to show the various features of confidential computing, such as popular and holistic data security model, data confidentiality, data integrity and code integrity.
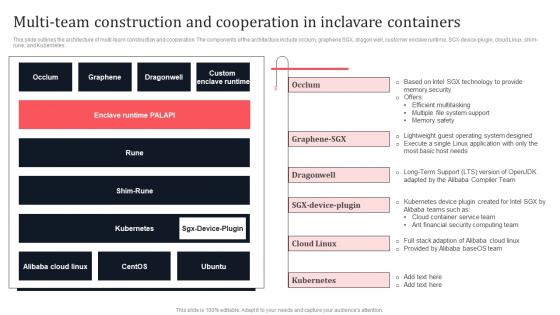
Multi Team Construction And Cooperation In Inclavare Containers Secure Multi Party Pictures Pdf
This slide outlines the architecture of multi-team construction and cooperation. The components of the architecture include occlum, graphene SGX, dragon well, customer enclave runtime, SGX-device-plugin, cloud Linux, shim-rune, and Kubernetes. Boost your pitch with our creative Multi Team Construction And Cooperation In Inclavare Containers Secure Multi Party Pictures Pdf Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide outlines the architecture of multi-team construction and cooperation. The components of the architecture include occlum, graphene SGX, dragon well, customer enclave runtime, SGX-device-plugin, cloud Linux, shim-rune, and Kubernetes.

Need For Confidential Computing In Cloud Environment Secure Multi Party Sample Pdf
This slide depicts the need for confidential computing in a cloud environment and by showcasing the security concerns with early data processing system and confidential computing solutions to overcome those problems. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Need For Confidential Computing In Cloud Environment Secure Multi Party Sample Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide depicts the need for confidential computing in a cloud environment and by showcasing the security concerns with early data processing system and confidential computing solutions to overcome those problems.
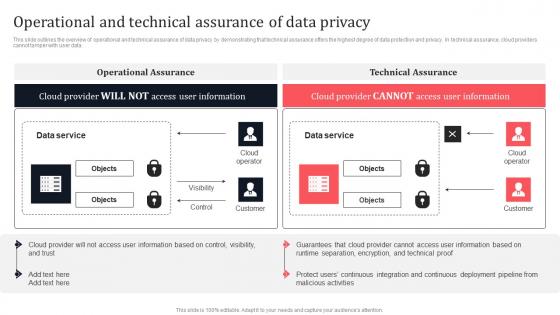
Operational And Technical Assurance Of Data Privacy Secure Multi Party Professional Pdf
This slide outlines the overview of operational and technical assurance of data privacy by demonstrating that technical assurance offers the highest degree of data protection and privacy. In technical assurance, cloud providers cannot tamper with user data. There are so many reasons you need a Operational And Technical Assurance Of Data Privacy Secure Multi Party Professional Pdf The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide outlines the overview of operational and technical assurance of data privacy by demonstrating that technical assurance offers the highest degree of data protection and privacy. In technical assurance, cloud providers cannot tamper with user data.
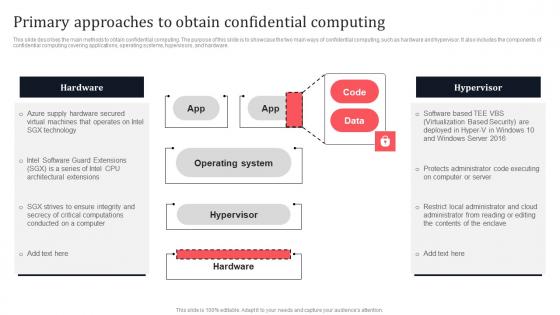
Primary Approaches To Obtain Confidential Computing Secure Multi Party Topics Pdf
This slide describes the main methods to obtain confidential computing. The purpose of this slide is to showcase the two main ways of confidential computing, such as hardware and hypervisor. It also includes the components of confidential computing covering applications, operating systems, hypervisors, and hardware. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Primary Approaches To Obtain Confidential Computing Secure Multi Party Topics Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide describes the main methods to obtain confidential computing. The purpose of this slide is to showcase the two main ways of confidential computing, such as hardware and hypervisor. It also includes the components of confidential computing covering applications, operating systems, hypervisors, and hardware.
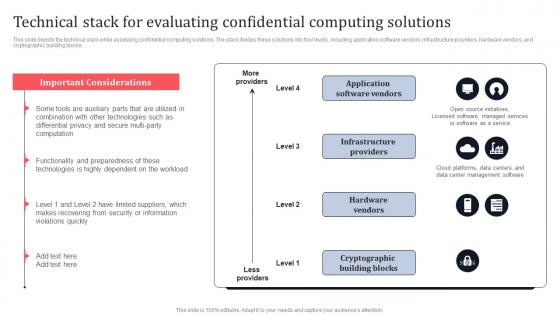
Technical Stack For Evaluating Confidential Computing Solutions Secure Multi Party Topics Pdf
This slide depicts the technical stack while assessing confidential computing solutions. The stack divides these solutions into four levels, including application software vendors, infrastructure providers, hardware vendors, and cryptographic building blocks. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Technical Stack For Evaluating Confidential Computing Solutions Secure Multi Party Topics Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide depicts the technical stack while assessing confidential computing solutions. The stack divides these solutions into four levels, including application software vendors, infrastructure providers, hardware vendors, and cryptographic building blocks.
United States Air Force Birthday Poster In National Flag Color Ppt PowerPoint Presentation Gallery Icon PDF
Showcasing this set of slides titled united states air force birthday poster in national flag color ppt powerpoint presentation gallery icon pdf. The topics addressed in these templates are united states air force birthday poster in national flag color. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
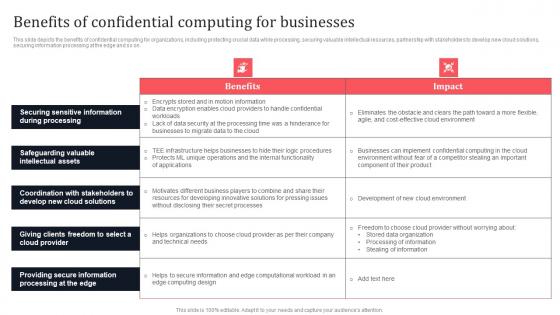
Benefits Of Confidential Computing For Businesses Secure Multi Party Ideas Pdf
This slide depicts the benefits of confidential computing for organizations, including protecting crucial data while processing, securing valuable intellectual resources, partnership with stakeholders to develop new cloud solutions, securing information processing at the edge and so on. Do you know about Slidesgeeks Benefits Of Confidential Computing For Businesses Secure Multi Party Ideas Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide depicts the benefits of confidential computing for organizations, including protecting crucial data while processing, securing valuable intellectual resources, partnership with stakeholders to develop new cloud solutions, securing information processing at the edge and so on.
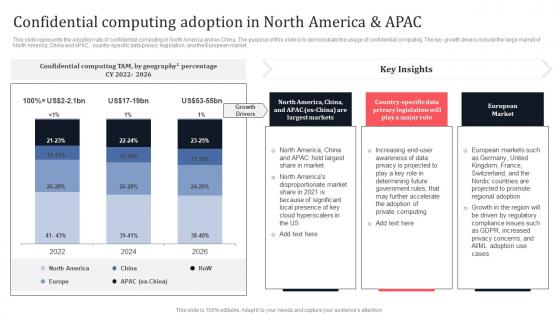
Confidential Computing Adoption In North America And APAC Secure Multi Party Brochure Pdf
This slide represents the adoption rate of confidential computing in North America and ex-China. The purpose of this slide is to demonstrate the usage of confidential computing. The key growth drivers include the large market of North America, China and APAC, country-specific data privacy legislation, and the European market. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Confidential Computing Adoption In North America And APAC Secure Multi Party Brochure Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide represents the adoption rate of confidential computing in North America and ex-China. The purpose of this slide is to demonstrate the usage of confidential computing. The key growth drivers include the large market of North America, China and APAC, country-specific data privacy legislation, and the European market.
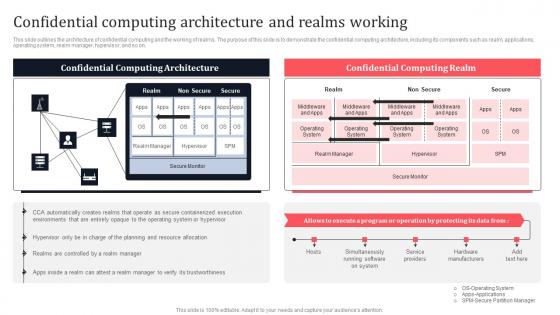
Confidential Computing Architecture And Realms Working Secure Multi Party Download Pdf
This slide outlines the architecture of confidential computing and the working of realms. The purpose of this slide is to demonstrate the confidential computing architecture, including its components such as realm, applications, operating system, realm manager, hypervisor, and so on. Slidegeeks is here to make your presentations a breeze with Confidential Computing Architecture And Realms Working Secure Multi Party Download Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first. This slide outlines the architecture of confidential computing and the working of realms. The purpose of this slide is to demonstrate the confidential computing architecture, including its components such as realm, applications, operating system, realm manager, hypervisor, and so on.


 Continue with Email
Continue with Email

 Home
Home


































