Business Security
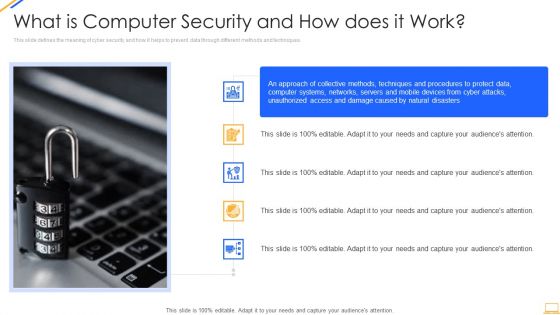
Desktop Security Management What Is Computer Security And How Does It Work Template PDF
This slide defines the meaning of cyber security and how it helps to prevent data through different methods and techniques. Deliver an awe inspiring pitch with this creative desktop security management what is computer security and how does it work template pdf bundle. Topics like networks, systems, protect data can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Email Security Encryption And Data Loss Prevention Your Investment For E Mail Security Proposal Diagrams PDF
This Slide shows the detailed investment of your client into various security softwares. Deliver an awe-inspiring pitch with this creative email security encryption and data loss prevention your investment for e mail security proposal diagrams pdf bundle. Topics like product, free version, starting price, frequency, per user can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Building Trust With IoT Security Overall Impact Of IoT Security Breaches Incidents IoT SS V
This slide includes IoT security breaches impact on an organisations operational capabilities, hindering the ability to function properly. It includes impacts such as financial burden, operations disruptions, and reputational damage. Create an editable Building Trust With IoT Security Overall Impact Of IoT Security Breaches Incidents IoT SS V that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Building Trust With IoT Security Overall Impact Of IoT Security Breaches Incidents IoT SS V is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide includes IoT security breaches impact on an organisations operational capabilities, hindering the ability to function properly. It includes impacts such as financial burden, operations disruptions, and reputational damage.
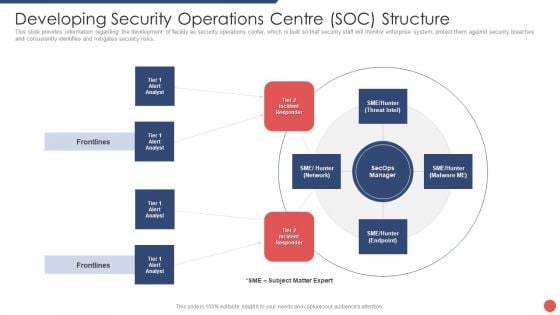
Security Functioning Centre Developing Security Operations Centre SOC Structure Guidelines PDF
This slide provides information regarding the development of facility as security operations center, which is built so that security staff will monitor enterprise system, protect them against security breaches and consistently identifies and mitigates security risks. Deliver and pitch your topic in the best possible manner with this security functioning centre developing security operations centre soc structure guidelines pdf. Use them to share invaluable insights on incident responder, analyst, network and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
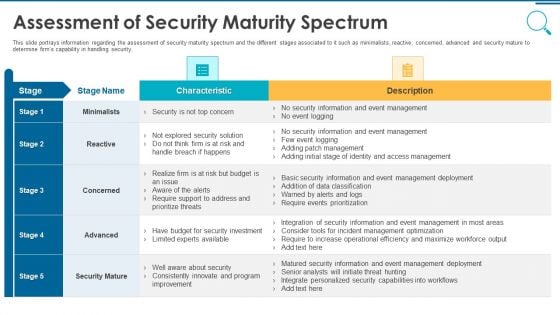
Information And Technology Security Operations Assessment Of Security Maturity Spectrum Template PDF
This slide portrays information regarding the assessment of security maturity spectrum and the different stages associated to it such as minimalists, reactive, concerned, advanced and security mature to determine firms capability in handling security. Deliver an awe inspiring pitch with this creative information and technology security operations assessment of security maturity spectrum template pdf bundle. Topics like minimalists, reactive, concerned, advanced, security mature can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
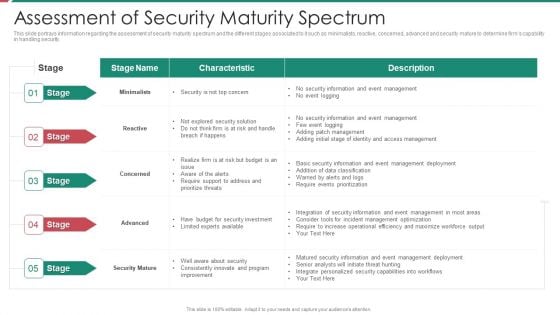
Security And Process Integration Assessment Of Security Maturity Spectrum Slides PDF
This slide portrays information regarding the assessment of security maturity spectrum and the different stages associated to it such as minimalists, reactive, concerned, advanced and security mature to determine firms capability in handling security. Deliver an awe inspiring pitch with this creative security and process integration assessment of security maturity spectrum slides pdf bundle. Topics like minimalists, reactive, concerned, advanced, security mature can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
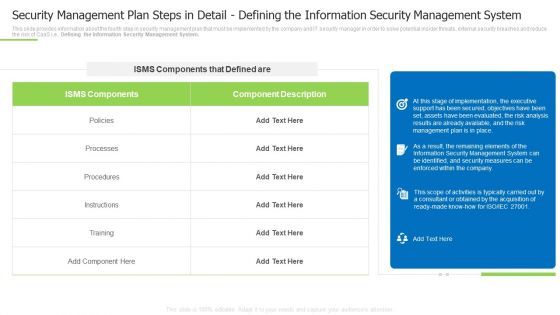
Security Management Plan Steps In Detail Defining The Information Security Management System Summary PDF
This slide provides information about the fourth step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Defining the Information Security Management System. Deliver and pitch your topic in the best possible manner with this security management plan steps in detail defining the information security management system summary pdf Use them to share invaluable insights on instructions, processes, implementation, the executive and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Techniques And Strategies To Reduce Security Management Risks Security Detail Risk Assessment And Analysis Template PDF
This slide provides information about the third step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Risk Assessment and Analysis. Deliver and pitch your topic in the best possible manner with this techniques and strategies to reduce security management risks security detail risk assessment and analysis template pdf Use them to share invaluable insights on security breach, perform a threat, several measures and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Estimated Security Monitoring Guidelines PDF
This slide shows the estimated Cyber Security Monitoring Key Performance Indicators of the company after implementing an advanced security monitoring plan, adopting security monitoring best practices and implementing Cybersecurity Monitoring Tool Cain and Abel. Deliver and pitch your topic in the best possible manner with this modern security observation plan to eradicate cybersecurity risk and data breach estimated security monitoring guidelines pdf. Use them to share invaluable insights on estimated security monitoring key performance indicators and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
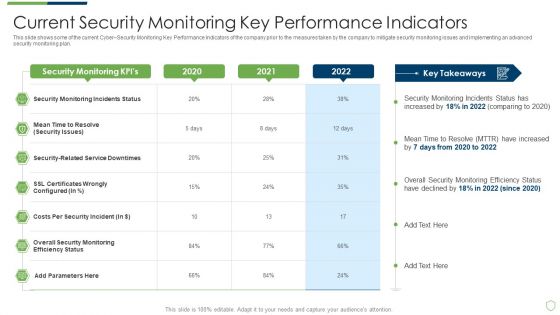
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Current Security Monitoring Pictures PDF
This slide shows some of the current Cyber Security Monitoring Key Performance Indicators of the company prior to the measures taken by the company to mitigate security monitoring issues and implementing an advanced security monitoring plan. Deliver and pitch your topic in the best possible manner with this modern security observation plan to eradicate cybersecurity risk and data breach current security monitoring pictures pdf. Use them to share invaluable insights on current security monitoring key performance indicators and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Security Real Estate Finance PowerPoint Templates And PowerPoint Themes 0912
Security Real Estate Finance PowerPoint Templates And PowerPoint Themes Presentations-Microsoft Powerpoint Templates and Background with us money locked in a padlock with keys-Security Real Estate Finance PowerPoint Templates And PowerPoint Themes PresentationsThis PPT can be used for presentations relating to-Us money locked in a padlock with keys, security, money, finance, business, real estate Put your ideas out to flower. Our Security Real Estate Finance PowerPoint Templates And PowerPoint Themes 0912 will get them to bloom.
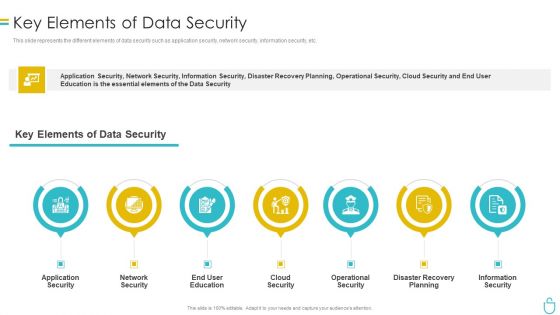
Information Security Key Elements Of Data Security Ppt Pictures Show PDF
This slide represents the different elements of data security such as application security, network security, information security, etc. Presenting information security key elements of data security ppt pictures show pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like network security, application security, cloud security, operational security, information security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
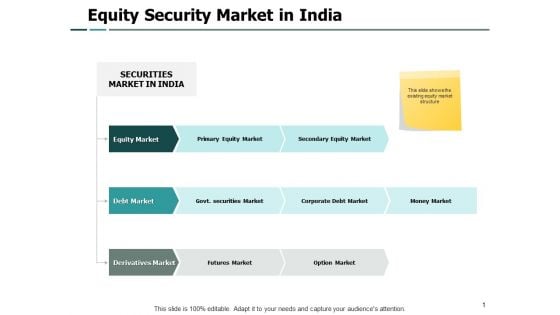
Equity Security Market In India Security Ppt PowerPoint Presentation Model Portfolio
Presenting this set of slides with name equity security market in india security ppt powerpoint presentation model portfolio. The topics discussed in these slides are marketing, business, management, planning, strategy. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
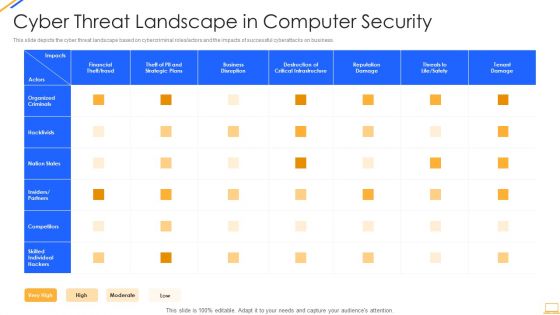
Desktop Security Management Cyber Threat Landscape In Computer Security Ideas PDF
This slide depicts the cyber threat landscape based on cybercriminal roles or actors and the impacts of successful cyberattacks on business. Deliver and pitch your topic in the best possible manner with this desktop security management cyber threat landscape in computer security ideas pdf. Use them to share invaluable insights on business disruption, strategic plans, financial, reputation damage and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
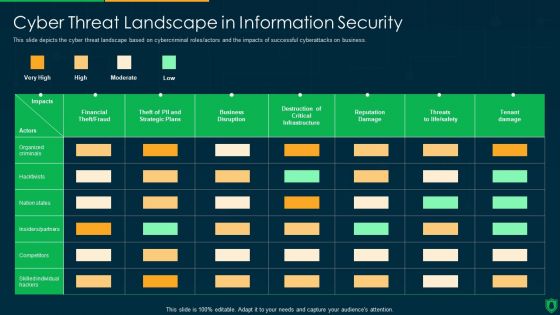
Info Security Cyber Threat Landscape In Information Security Ppt PowerPoint Presentation File Slides PDF
This slide depicts the cyber threat landscape based on cybercriminal roles or actors and the impacts of successful cyberattacks on business. Deliver and pitch your topic in the best possible manner with this info security cyber threat landscape in information security ppt powerpoint presentation file slides pdf. Use them to share invaluable insights on business disruption, financial theft, fraud, reputation damage, tenant damage and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
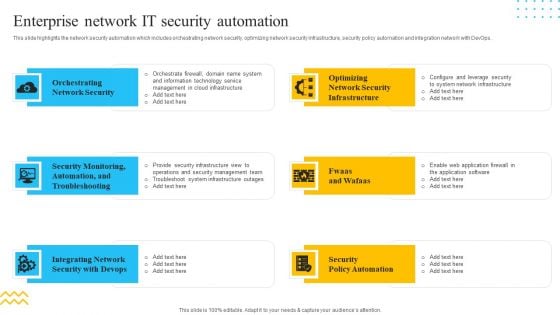
IT Security Automation Tools Integration Enterprise Network IT Security Automation Download PDF
This slide highlights the network security automation which includes orchestrating network security, optimizing network security infrastructure, security policy automation and integration network with DevOps. This is a IT Security Automation Tools Integration Enterprise Network IT Security Automation Download PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Orchestrating Network Security, Integrating Network, Security Policy Automation. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
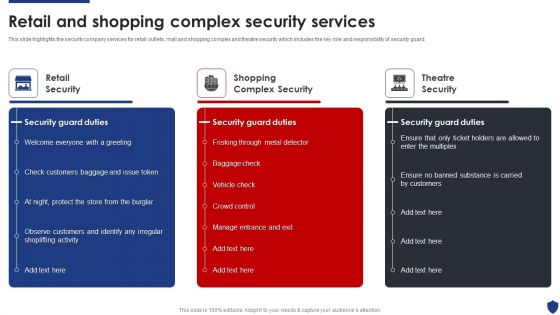
Security Officer Service Company Profile Retail And Shopping Complex Security Services Summary PDF
This slide highlights the security company services for retail outlets, mall and shopping complex and theatre security which includes the key role and responsibility of security guard. This is a Security Officer Service Company Profile Retail And Shopping Complex Security Services Summary PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Retail Security, Shopping Complex Security, Theatre Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Information Security Essential Pillars Of Cloud Security Ppt File Elements PDF
This slide shows the four essential pillars of cloud security, namely visibility and consistency, process-based security, network security, and identity security. This is a Cloud Information Security Essential Pillars Of Cloud Security Ppt File Elements PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Network Security, Identity Security, Visibility Consistency. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
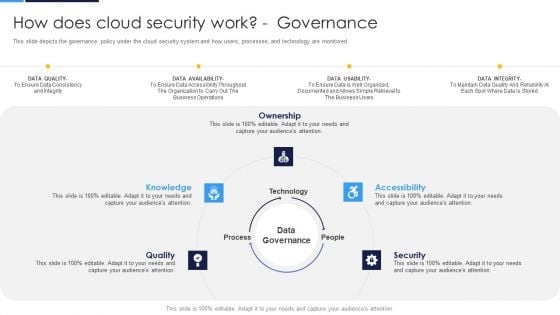
Cloud Security Assessment How Does Cloud Security Work Governance Sample PDF
This slide represents the data security under the cloud security work process, and it also shows the various factors that cover data security.This is a Cloud Security Assessment How Does Cloud Security Work Governance Sample PDF template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Physical Security, Internet Security, Endpoint Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
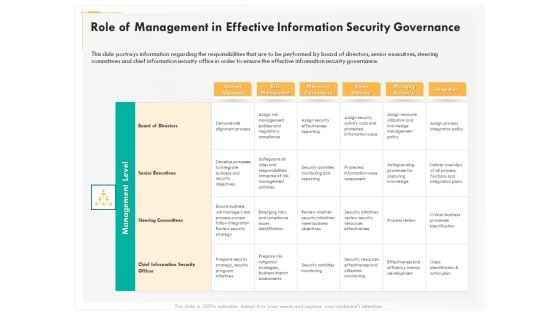
Computer Security Incident Handling Role Of Management In Effective Information Security Governance Portrait PDF
Presenting this set of slides with name computer security incident handling role of management in effective information security governance portrait pdf. The topics discussed in these slides are strategic alignment, risk management, measuring performance, value delivery, managing resource, integration. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cloud Security Best Practices Cloud Computing Security IT Ppt Portfolio Master Slide PDF
This slide defines the best practices of cloud security, including understanding cloud utilization and risk, protection of cloud, and responding to cloud protection issues. Deliver an awe inspiring pitch with this creative cloud security best practices cloud computing security it ppt portfolio master slide pdf bundle. Topics like cloud protection, cloud utilization and risk, authentication process, security policies can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Ensuring Checklist For Mobile Security Deployment Mobile Device Security Management Pictures PDF
This slide provides information regarding mobile device security deployment checklist in terms of device security, protection against malicious codes. Deliver and pitch your topic in the best possible manner with this Ensuring Checklist For Mobile Security Deployment Mobile Device Security Management Pictures PDF. Use them to share invaluable insights on Remotely Locking, Protection Against, Malicious Codes and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cloud Information Security Hybrid Cloud Security Solutions Ppt Infographics Professional PDF
This slide describes the hybrid cloud security solutions, which include categorization of services and redundancy. Deliver an awe inspiring pitch with this creative Cloud Information Security Hybrid Cloud Security Solutions Ppt Infographics Professional PDF bundle. Topics like Categorization Services, Enable Organizations, Security Properly can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
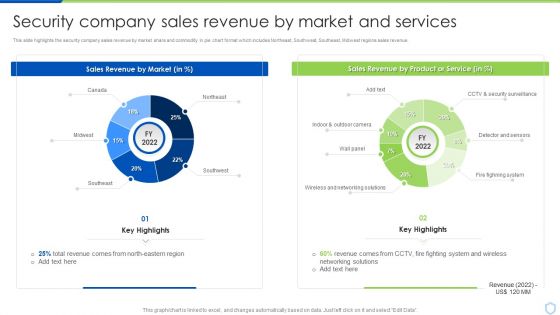
Security And Surveillance Company Profile Security Company Sales Revenue Clipart PDF
This slide highlights the security company sales revenue by market share and commodity in pie chart format which includes Northeast, Southwest, Southeast, Midwest regions sales revenue.Deliver an awe inspiring pitch with this creative Security And Surveillance Company Profile Security Company Sales Revenue Clipart PDF bundle. Topics like Sales Revenue, Security Surveillance, Networking Solutions can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security And Surveillance Company Profile Security Company Strategic Partnerships Graphics PDF
This slide highlights the strategic partnership of the security company. It covers the major services such as voice control, mobile security application, and CCTV installation.Deliver and pitch your topic in the best possible manner with this Security And Surveillance Company Profile Security Company Strategic Partnerships Graphics PDF. Use them to share invaluable insights on Technology Partner, Installation Centres, Partnership Type and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Developing Firm Security Strategy Plan Effective Security Management At Workplace Structure PDF
This slide portrays information regarding how firm is successful in handling security issues or events and is able in reducing the occurrence of events. Deliver and pitch your topic in the best possible manner with this developing firm security strategy plan effective security management at workplace structure pdf. Use them to share invaluable insights on effective security management at workplace and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Cyber Security Risk Management Plan Current Security Infrastructure Performance Analysis Icons PDF
Mentioned slide displays performance analysis of current security infrastructure based on NIST core functions. Core functions included are identify, protect, detect, respond, recover. Deliver an awe inspiring pitch with this creative cyber security risk management plan current security infrastructure performance analysis icons pdf bundle. Topics like technology, target, plan, vulnerability intelligence, security infrastructure can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
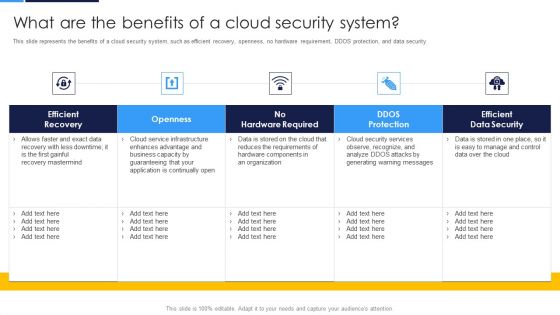
Cloud Security Assessment What Are The Benefits Of A Cloud Security System Information PDF
This slide represents the benefits of a cloud security system, such as efficient recovery, openness, no hardware requirement, DDOS protection, and data security.Deliver and pitch your topic in the best possible manner with this Cloud Security Assessment What Are The Benefits Of A Cloud Security System Information PDF. Use them to share invaluable insights on Efficient Recovery, Hardware Required, Efficient Data and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
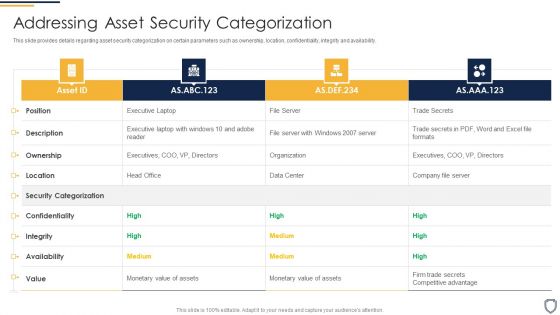
Corporate Security And Risk Management Addressing Asset Security Categorization Guidelines PDF
This slide provides details regarding asset security categorization on certain parameters such as ownership, location, confidentiality, integrity and availability. Deliver an awe inspiring pitch with this creative corporate security and risk management addressing asset security categorization guidelines pdf bundle. Topics like addressing asset security categorization can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
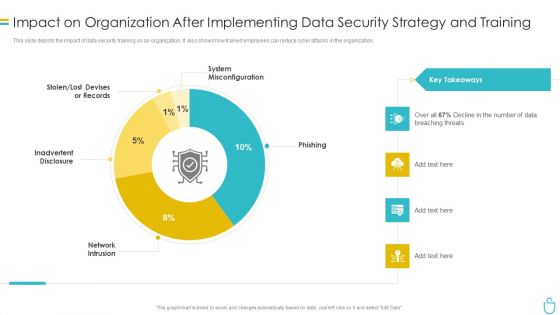
Information Security Impact On Organization After Implementing Data Security Strategy And Training Ppt Ideas Images PDF
This slide depicts the impact of data security training on an organization. It also shows how trained employees can reduce cyber attacks in the organization. Deliver and pitch your topic in the best possible manner with this information security impact on organization after implementing data security strategy and training ppt ideas images pdf. Use them to share invaluable insights on organization, data security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
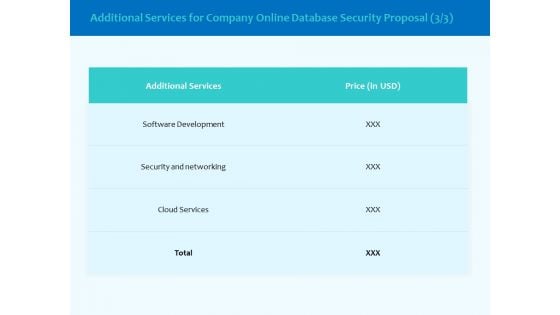
Best Data Security Software Additional Services For Company Online Database Security Proposal Pictures PDF
Presenting this set of slides with name best data security software additional services for company online database security proposal pictures pdf. The topics discussed in these slides are software development, security and networking, cloud services. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Uniformed Security Our Services For The Security Guard Services Proposal Icons PDF
Deliver and pitch your topic in the best possible manner with this uniformed security our services for the security guard services proposal icons pdf. Use them to share invaluable insights on security, monitoring, planning, corporate and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
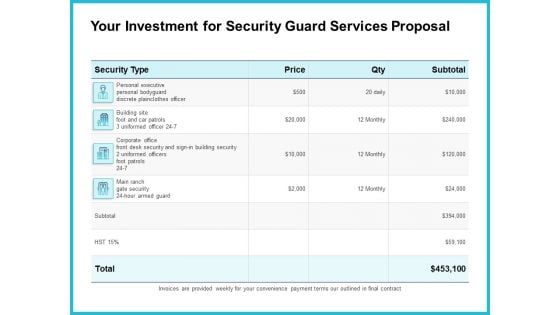
Uniformed Security Your Investment For Security Guard Services Proposal Graphics PDF
Deliver an awe inspiring pitch with this creative uniformed security your investment for security guard services proposal graphics pdf bundle. Topics like executive, security, corporate, price can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Information And Technology Security Operations Impact Of Effective Security Management Icons PDF
This slide portrays information regarding how firm is successful in handling security issues or events and is able in reducing the occurrence of events. Deliver an awe inspiring pitch with this creative information and technology security operations impact of effective security management icons pdf bundle. Topics like impact of effective security management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
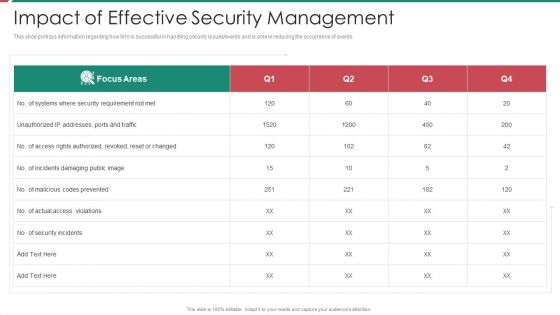
Security And Process Integration Impact Of Effective Security Management Topics PDF
This slide portrays information regarding how firm is successful in handling security issues or events and is able in reducing the occurrence of events. Deliver an awe inspiring pitch with this creative security and process integration impact of effective security management topics pdf bundle. Topics like impact of effective security management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Effective Mobile Device Security Management Mobile Device Security Management Professional PDF
This slide portrays information regarding how firm is successful in handling security issues events and is able in reducing the occurrence of events associated to mobile device. Deliver an awe inspiring pitch with this creative Effective Mobile Device Security Management Mobile Device Security Management Professional PDF bundle. Topics like Security Requirement, Authorized Revoked, Access Violations can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Uniformed Security Our Equipments Used For Security Guard Services Proposal Template PDF
Deliver an awe inspiring pitch with this creative uniformed security our equipments used for security guard services proposal template pdf bundle. Topics like surveillance technology and software, security trailers, vehicles, cameras, mobile phones can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
The Roi Of Security Awareness Training Hacking Prevention Awareness Training For IT Security Icons PDF
This slide covers the security awareness rate of interest calculations including typical cyber risk management factor for a trained, cyber-conscious workforce. Deliver and pitch your topic in the best possible manner with this the roi of security awareness training hacking prevention awareness training for it security icons pdf. Use them to share invaluable insights on organizations, training, security, costs and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
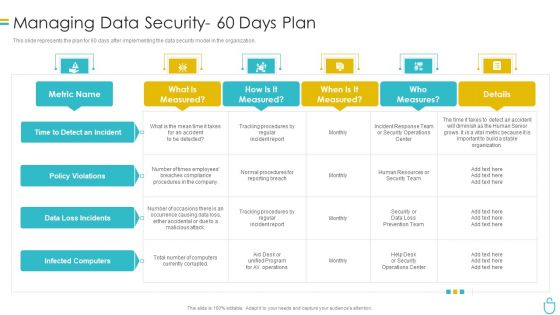
Information Security Managing Data Security 60 Days Plan Ppt Inspiration Slide Download PDF
This slide represents the plan for 60 days after implementing the data security model in the organization. Deliver and pitch your topic in the best possible manner with this information security managing data security 60 days plan ppt inspiration slide download pdf. Use them to share invaluable insights on measured, procedures, team, security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
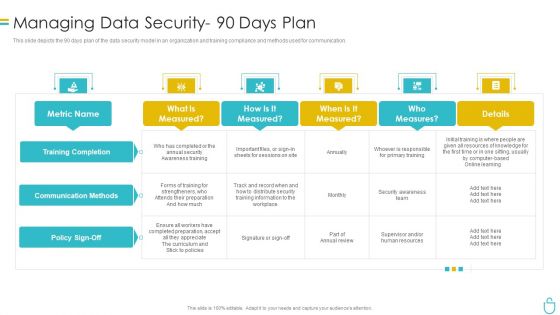
Information Security Managing Data Security 90 Days Plan Ppt Infographic Template Slides PDF
This slide depicts the 90 days plan of the data security model in an organization and training compliance and methods used for communication. Deliver an awe inspiring pitch with this creative information security managing data security 90 days plan ppt infographic template slides pdf bundle. Topics like security, measured can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
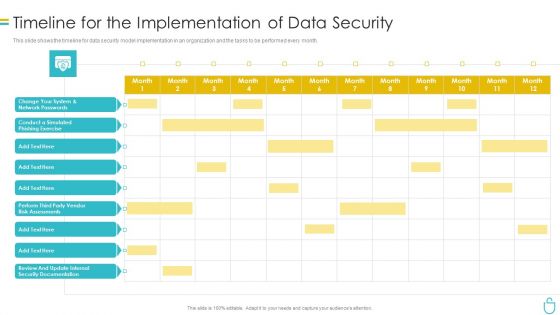
Information Security Timeline For The Implementation Of Data Security Ppt Gallery Topics PDF
This slide shows the timeline for data security model implementation in an organization and the tasks to be performed every month. Deliver and pitch your topic in the best possible manner with this information security timeline for the implementation of data security ppt gallery topics pdf. Use them to share invaluable insights on timeline for the implementation of data security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
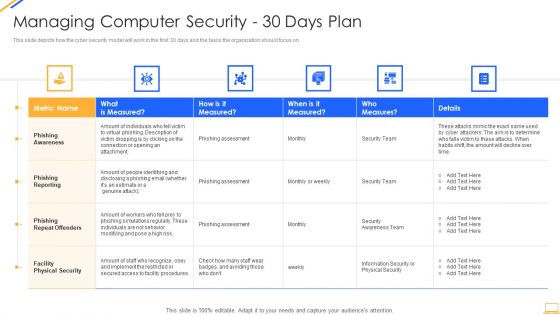
Desktop Security Management Managing Computer Security 30 Days Plan Designs PDF
This slide depicts how the cyber security model will work in the first 30 days and the tasks the organization should focus on. Deliver an awe inspiring pitch with this creative desktop security management managing computer security 30 days plan designs pdf bundle. Topics like awareness, measured, risk, security, team can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Desktop Security Management Managing Computer Security 90 Days Plan Professional PDF
This slide depicts the 90 days plan of the cyber security model in an organization and training compliance and methods used for communication. Deliver an awe inspiring pitch with this creative desktop security management managing computer security 90 days plan professional pdf bundle. Topics like awareness, security, information, resources can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
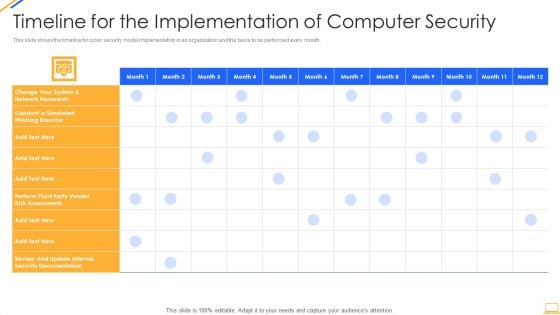
Desktop Security Management Timeline For The Implementation Of Computer Security Sample PDF
This slide shows the timeline for cyber security model implementation in an organization and the tasks to be performed every month. Deliver and pitch your topic in the best possible manner with this desktop security management timeline for the implementation of computer security sample pdf. Use them to share invaluable insights on security documentation, system and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
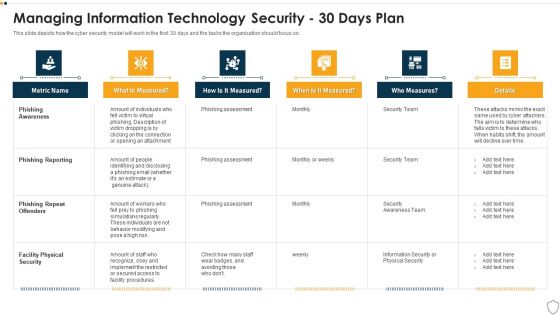
IT Security Managing Information Technology Security 30 Days Plan Themes PDF
This slide depicts how the cyber security model will work in the first 30 days and the tasks the organization should focus on. Deliver and pitch your topic in the best possible manner with this it security managing information technology security 30 days plan themes pdf. Use them to share invaluable insights on phishing awareness, phishing reporting, phishing repeat offenders, facility physical security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

IT Security Timeline For The Implementation Of Information Technology Security Structure PDF
This slide shows the timeline for cyber security model implementation in an organization and the tasks to be performed every month. Deliver an awe inspiring pitch with this creative it security timeline for the implementation of information technology security structure pdf bundle. Topics like timeline for the implementation of information technology security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Info Security Managing Information Security 30 Days Plan Ppt PowerPoint Presentation Icon Show PDF
This slide depicts how the cyber security model will work in the first 30 days and the tasks the organization should focus on. Deliver an awe inspiring pitch with this creative info security managing information security 30 days plan ppt powerpoint presentation icon show pdf bundle. Topics like phishing aware, phishing reporting, phishing repeat offenders, facility physical security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
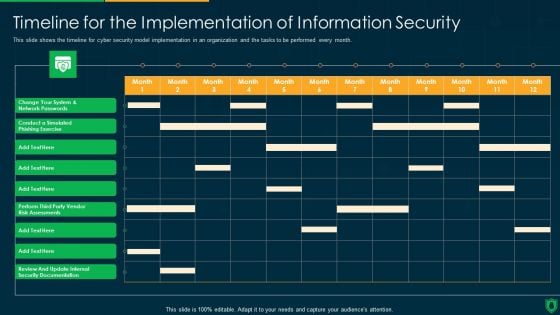
Info Security Timeline For The Implementation Of Information Security Ppt PowerPoint Presentation Diagram Templates PDF
This slide shows the timeline for cyber security model implementation in an organization and the tasks to be performed every month. Deliver an awe inspiring pitch with this creative info security timeline for the implementation of information security ppt powerpoint presentation diagram templates pdf bundle. Topics like perform third party, vendor risk assessments, review and update, internal security documentation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
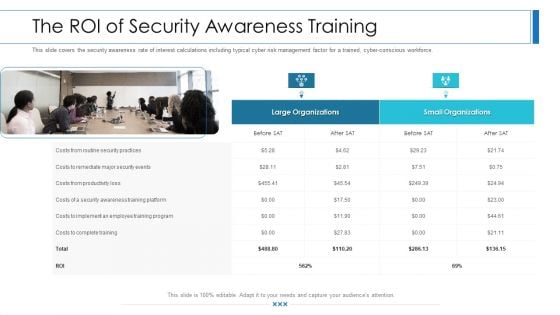
Workforce Security Realization Coaching Plan The ROI Of Security Awareness Training Pictures PDF
This slide covers the security awareness rate of interest calculations including typical cyber risk management factor for a trained, cyber-conscious workforce. Deliver and pitch your topic in the best possible manner with this workforce security realization coaching plan the roi of security awareness training pictures pdf. Use them to share invaluable insights on security awareness training and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Why Cloud Security Is Important Cloud Computing Security IT Ppt Slides Graphics Template PDF
This slide defines why cloud security is essential based on data centralization, cost, diminished control, and data reliability. Deliver and pitch your topic in the best possible manner with this why cloud security is important cloud computing security it ppt slides graphics template pdf. Use them to share invaluable insights on centralized security, cost effective, diminished administration, reliability and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Desktop Security Management It Infrastructure Computer Security Budget For Fy2022 Slides PDF
This slide represents the budget for IT infrastructure after implementing cyber security, and it also shows the amount each task will cost the company. Deliver an awe inspiring pitch with this creative desktop security management it infrastructure computer security budget for fy2022 slides pdf bundle. Topics like it infrastructure computer security budget for fy2022 can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
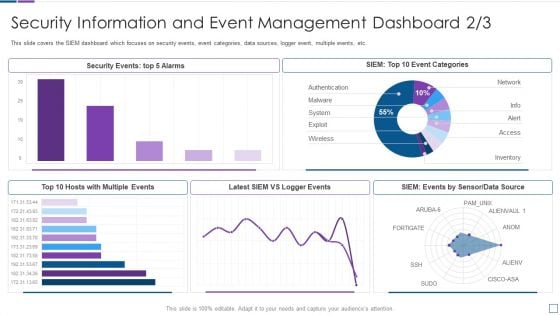
Real Time Assessment Of Security Threats Security Information And Event Management Dashboard Infographics PDF
This slide covers the SIEM dashboard which focuses on security events, event categories, data sources, logger event, multiple events, etc. Deliver an awe inspiring pitch with this creative real time assessment of security threats security information and event management dashboard infographics pdf bundle. Topics like security information and event management dashboard can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
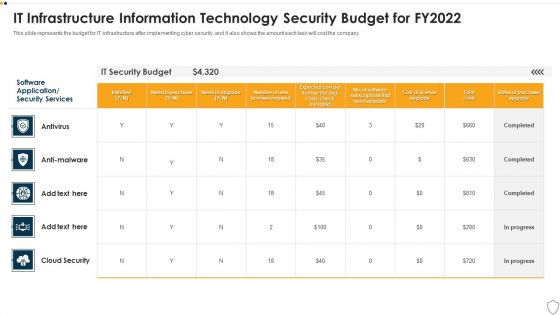
IT Security It Infrastructure Information Technology Security Budget For FY2022 Brochure PDF
This slide represents the budget for IT infrastructure after implementing cyber security, and it also shows the amount each task will cost the company. Deliver an awe inspiring pitch with this creative it security it infrastructure information technology security budget for fy2022 brochure pdf bundle. Topics like it infrastructure information technology security budget for fy2022 can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cloud Information Security Difference Between Cloud Security Solutions And Traditional Topics PDF
This slide represents the difference between cloud security solutions and traditional IT solutions based on information centers, cost, scalability, and expenses. Deliver an awe inspiring pitch with this creative Cloud Information Security Difference Between Cloud Security Solutions And Traditional Topics PDF bundle. Topics like Cloud Security, Rapidly Scalable, Diminished Opportunity can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
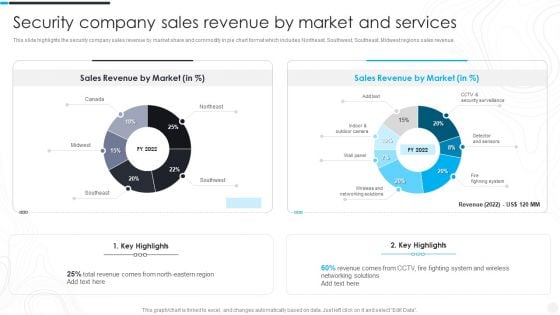
Security Camera System Company Profile Security Company Sales Revenue Template PDF
This slide highlights the security company sales revenue by market share and commodity in pie chart format which includes Northeast, Southwest, Southeast, Midwest regions sales revenue.Deliver an awe inspiring pitch with this creative Security Camera System Company Profile Security Company Sales Revenue Template PDF bundle. Topics like Detector And Sensors, Fighning System, Security Surveillance can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
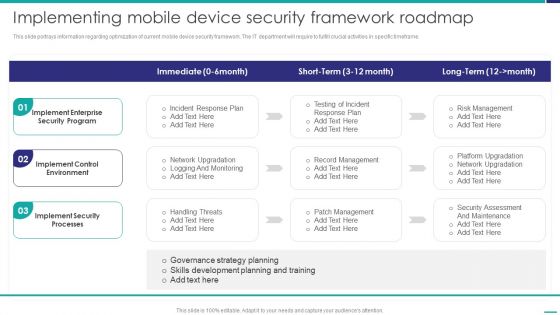
Implementing Mobile Device Security Framework Roadmap Mobile Device Security Management Infographics PDF
This slide portrays information regarding optimization of current mobile device security framework. The IT department will require to fulfill crucial activities in specific timeframe. Deliver and pitch your topic in the best possible manner with this Implementing Mobile Device Security Framework Roadmap Mobile Device Security Management Infographics PDF. Use them to share invaluable insights on Implement Enterprise, Security Program, Implement Control and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
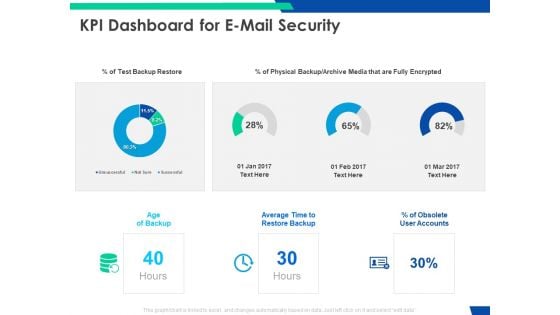
Cloud Based Email Security Market Report KPI Dashboard For E Mail Security Ppt Slides Microsoft PDF
Deliver an awe inspiring pitch with this creative cloud based email security market report kpi dashboard for e mail security ppt slides microsoft pdf bundle. Topics like kpi dashboard for e mail security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
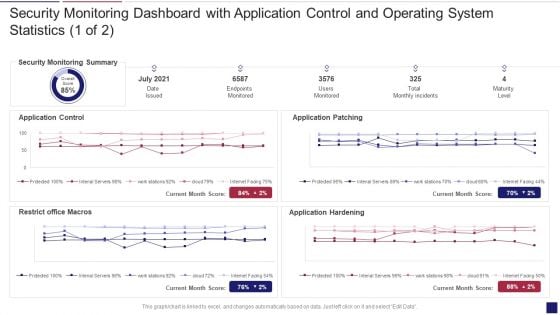
Continuous Development Evaluation Plan Eliminate Cyber Attacks Security Monitoring Dashboard Security Brochure PDF
Deliver an awe inspiring pitch with this creative continuous development evaluation plan eliminate cyber attacks security monitoring dashboard security brochure pdf bundle. Topics like security monitoring dashboard with application control and operating system statistics can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Security Monitoring Dashboard Sample PDF
Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach security monitoring dashboard sample pdf bundle. Topics like security monitoring dashboard with application control and operating system statistics can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
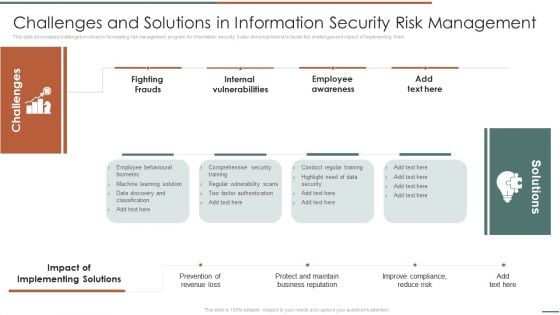
Information Security Risk Evaluation Challenges And Solutions In Information Security Risk Management Template PDF
Deliver and pitch your topic in the best possible manner with this Information Security Risk Evaluation Challenges And Solutions In Information Security Risk Management Template PDF. Use them to share invaluable insights on Internal Vulnerabilities, Employee Awareness, Comprehensive Security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.


 Continue with Email
Continue with Email

 Home
Home


































