Business Security
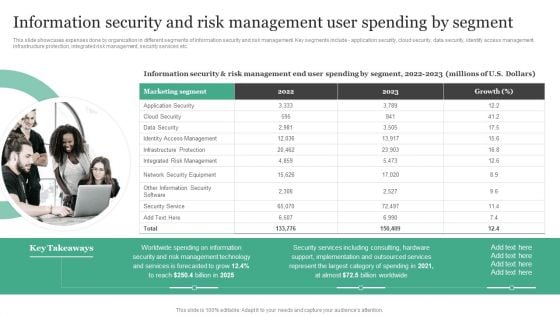
Information Security And Risk Management User Spending By Segment Information Security Risk Administration Slides PDF
This slide showcases expenses done by organization in different segments of information security and risk management. Key segments include - application security, cloud security, data security, identify access management, infrastructure protection, integrated risk management, security services etc.Make sure to capture your audiences attention in your business displays with our gratis customizable Information Security And Risk Management User Spending By Segment Information Security Risk Administration Slides PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Security And Surveillance Company Profile Security Company Case Study Demonstration PDF
This slide highlights the case study of security company which includes key problems such as theft, fire breakout with integrated solution and business value delivered. Presenting Security And Surveillance Company Profile Security Company Case Study Demonstration PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Client Problem, Integrated Solution, Business Value. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
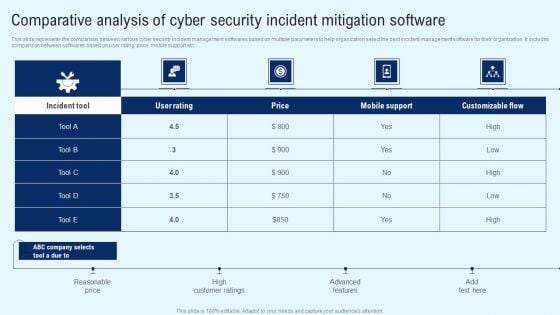
Implementing Cyber Security Incident Comparative Analysis Of Cyber Security Background PDF
This slide represents the comparison between various cyber security incident management softwares based on multiple parameters to help organization select the best incident management software for their organization. It includes comparison between softwares based on user rating, price, mobile support etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Implementing Cyber Security Incident Comparative Analysis Of Cyber Security Background PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
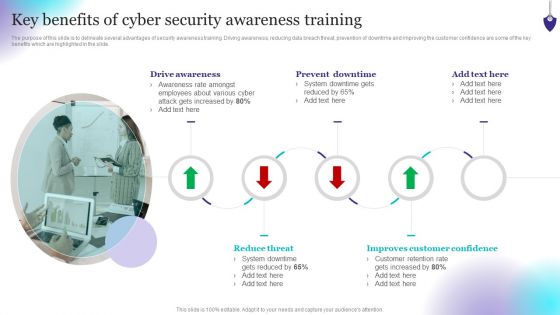
Organizing Security Awareness Key Benefits Of Cyber Security Awareness Training Rules PDF
The purpose of this slide is to delineate several advantages of security awareness training. Driving awareness, reducing data breach threat, prevention of downtime and improving the customer confidence are some of the key benefits which are highlighted in the slide. Make sure to capture your audiences attention in your business displays with our gratis customizable Organizing Security Awareness Key Benefits Of Cyber Security Awareness Training Rules PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
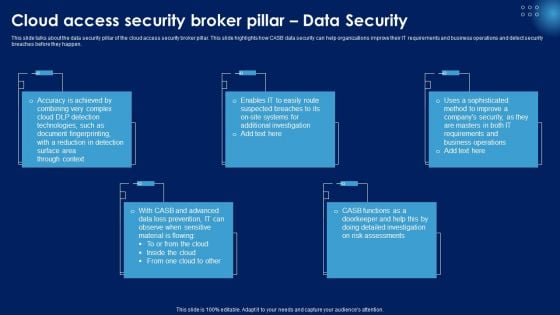
Cloud Access Security Broker Pillar Data Security Ppt PowerPoint Presentation File Model PDF
This slide talks about the data security pillar of the cloud access security broker pillar. This slide highlights how CASB data security can help organizations improve their IT requirements and business operations and detect security breaches before they happen. Slidegeeks is here to make your presentations a breeze with Cloud Access Security Broker Pillar Data Security Ppt PowerPoint Presentation File Model PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
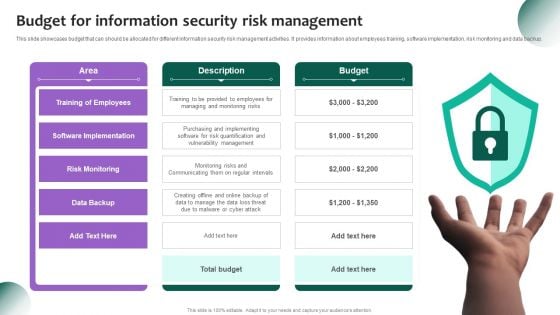
Information Systems Security And Risk Management Plan Budget For Information Security Risk Management Guidelines PDF
This slide showcases most common information attacks faced by organization. It includes - malware, phishing, man in the middle attack, SQL injection, zero day exploit and DNS attack. Make sure to capture your audiences attention in your business displays with our gratis customizable Information Systems Security And Risk Management Plan Budget For Information Security Risk Management Guidelines PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
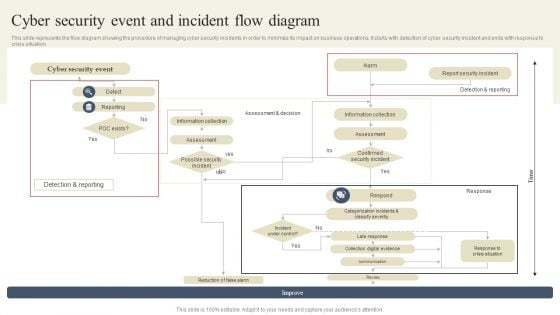
CYBER Security Breache Response Strategy Cyber Security Event And Incident Flow Diagram Sample PDF
This slide represents the flow diagram showing the procedure of managing cyber security incidents in order to minimize its impact on business operations. It starts with detection of cyber security incident and ends with response to crisis situation. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. CYBER Security Breache Response Strategy Cyber Security Event And Incident Flow Diagram Sample PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Data Breach Prevention Recognition IT Infrastructure Security Budget Rules PDF
This slide covers the budget to improve Cyber threat detection rates, reduce downtime due to network unavailability and keeping business secure against cyber attacks. Deliver and pitch your topic in the best possible manner with this data breach prevention recognition it infrastructure security budget rules pdf. Use them to share invaluable insights on it infrastructure security budget and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
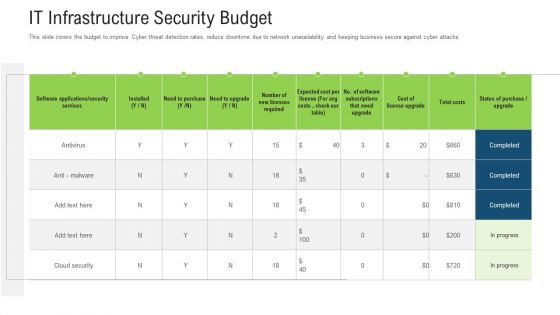
It Infrastructure Security Budget Ppt Outline Mockup PDF
This slide covers the budget to improve Cyber threat detection rates, reduce downtime due to network unavailability and keeping business secure against cyber attacks Deliver and pitch your topic in the best possible manner with this it infrastructure security budget ppt outline mockup pdf. Use them to share invaluable insights on services, software, cost and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
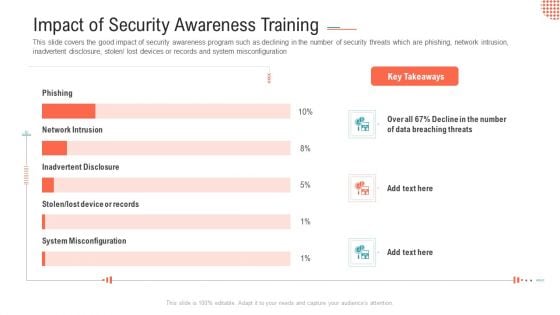
Impact Of Security Awareness Training Ppt Pictures Design Templates PDF
This slide covers the budget to improve Cyber threat detection rates, reduce downtime due to network unavailability and keeping business secure against cyber attacks Deliver and pitch your topic in the best possible manner with this impact of security awareness training ppt pictures design templates pdf. Use them to share invaluable insights on phishing breakdown, network intrusion breakdown, system misconfiguration and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Private Knowledge Security PowerPoint Template 1110
3d illustration of a large brass key inserted into a human brain on a gray reflective surface Fresh concepts are ever evolving. Help the audience absorb them with our Private Knowledge Security PowerPoint Template 1110.

Key Security PowerPoint Backgrounds And Templates 1210
Microsoft PowerPoint Template and Background with Photo of a Vintage Key With Dramatic Lighting Our Key Security PowerPoint Backgrounds And Templates 1210 offer many amenities. They facilitate any excercise you undertake.

Cloud Information Security Cloud Security Threats Compliance Violations Ppt Slides Aids PDF
This slide depicts the value of compliance violations threat of cloud security in a business and how fast an organization can switch to a non-compliance state. This is a Cloud Information Security Cloud Security Threats Compliance Violations Ppt Slides Aids PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Risks Organizations, Data Business, Serious Repercussions. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Credit Card Security PowerPoint Template 1110
Security: Closeup of brass padlock on credit card. Lecture teams with our Credit Card Security PowerPoint Template 1110. Download without worries with our money back guaranteee.
Datacenter Services Network Security Ppt Sample
This is a datacenter services network security ppt sample. This is a five stage process. The stages in this process are arrow, business, marketing.
Security Service Management Architecture Ppt Slides
This is a security service management architecture ppt slides. This is a five stage process. The stages in this process are architecture, business, communication.
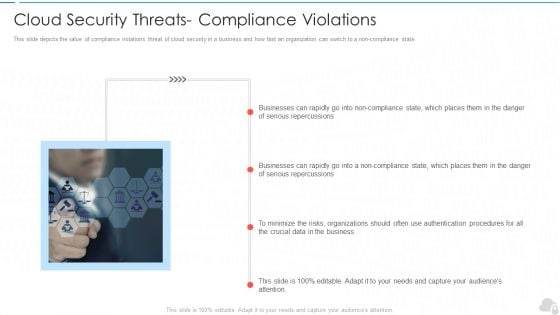
Cloud Security Threats Compliance Violations Cloud Computing Security IT Ppt Layouts Slide Portrait PDF
This slide depicts the value of compliance violations threat of cloud security in a business and how fast an organization can switch to a non-compliance state. This is a cloud security threats compliance violations cloud computing security it ppt layouts slide portrait pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like businesses, organizations, serious repercussions. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Finance Security Money PowerPoint Template 0610
Stack of Money with a Lock and Key - Financial Security Concept Observe growth with our Finance Security Money PowerPoint Template 0610. Download without worries with our money back guaranteee.
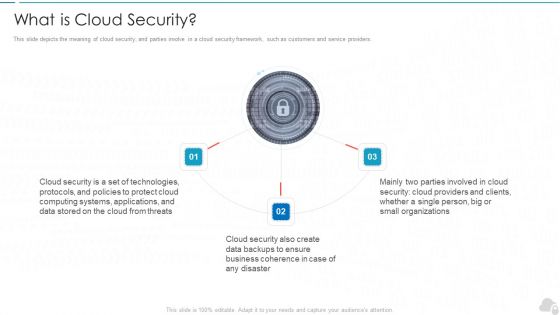
What Is Cloud Security Cloud Computing Security IT Ppt File Graphics PDF
This slide depicts the meaning of cloud security, and parties involve in a cloud security framework, such as customers and service providers. Presenting what is cloud security cloud computing security it ppt file graphics pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like cloud security, technologies, protocols, business, organizations. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Corporate Security And Risk Management Icons PDF
This is a corporate security and risk management corporate security and risk management icons pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like corporate security and risk management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Save Money Security PowerPoint Template 0810
lock your rate, save your money, cut your expenses Relieve anxiety with our Save Money Security PowerPoint Template 0810. Your thoughts will flow smoothly with ease.

Success Key Security PowerPoint Template 0510
key to success 3d Develop plans with our Success Key Security PowerPoint Template 0510. Download without worries with our money back guaranteee.

Time Bomb Security PowerPoint Template 0910
time bomb with dynamite and timer on the computer chip Enthuse your audience with our Time Bomb Security PowerPoint Template 0910. You will come out on top.

Protect Your Money Security PowerPoint Template 1110
protect your credit card with new device. isolated. with path Fight fires with our Protect Your Money Security PowerPoint Template 1110. Try us out and see what a difference our templates make.

Accessing The Data Security PowerPoint Template 1010
3d illustration of a large brass key and lock protruding from a simple pie chart Help develop a solution with our Accessing The Data Security PowerPoint Template 1010. Just download, type and present.

Unlock Your Potential Security PowerPoint Template 1110
A safe lock dial with the words Unlock Your Potential on it Our Unlock Your Potential Security PowerPoint Template 1110 ensure your credentials are established. Your abilities will be acknowledged by all.
Private Database Security PowerPoint Icon C
Microsoft PowerPoint Template and Background with white and black keep out sign protruding out of an open drawer of a gray file cabinet Chase dreams with our Private Database Security PowerPoint Icon C. You will come out on top.

Copy Right Security PowerPoint Template 1110
3d illustration of a brass metallic key and keyring sitting in front of a large chrome metallic copyright symbol on a dark gray reflective surface Our Copy Right Security PowerPoint Template 1110 give expression to your drive. They emit the essence of your determination.
Private Database Security PowerPoint Icon Cc
Microsoft PowerPoint Template and Background with white and black keep out sign protruding out of an open drawer of a gray file cabinet Correct wrongs with our Private Database Security PowerPoint Icon Cc. Download without worries with our money back guaranteee.
Private Database Security PowerPoint Icon F
Microsoft PowerPoint Template and Background with white and black keep out sign protruding out of an open drawer of a gray file cabinet Acquire the endorsement of the audience. The use of our Private Database Security PowerPoint Icon F will go in your favour.
Private Database Security PowerPoint Icon R
Microsoft PowerPoint Template and Background with white and black keep out sign protruding out of an open drawer of a gray file cabinet Aim for the skies with our Private Database Security PowerPoint Icon R. You will come out on top.
Private Database Security PowerPoint Icon S
Microsoft PowerPoint Template and Background with white and black keep out sign protruding out of an open drawer of a gray file cabinet Our Private Database Security PowerPoint Icon S have fantastic ability. They will have an astounding effect on the audience.
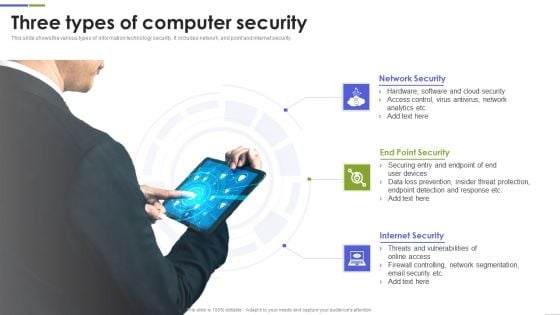
Three Types Of Computer Security Designs PDF
This slide shows the various types of information technology security. It includes network, end point and internet security. Presenting Three Types Of Computer Security Designs PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Network Security, Point Security, Internet Security This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
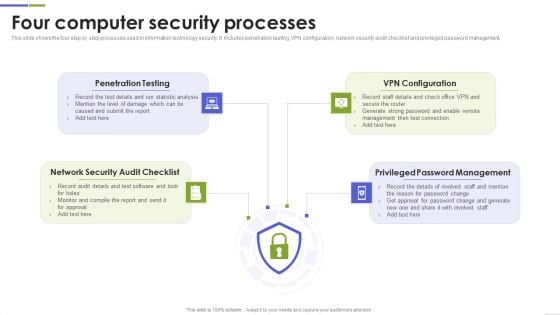
Four Computer Security Processes Portrait PDF
This slide shows the four step by step processes used in information technology security. It includes penetration testing, VPN configuration, network security audit checklist and privileged password management. Presenting Four Computer Security Processes Portrait PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Penetration Testing, Configuration, Password Management This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Computer Cyber Security Icon Infographics PDF
Presenting Computer Cyber Security Icon Infographics PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Computer Cyber, Security Icon This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
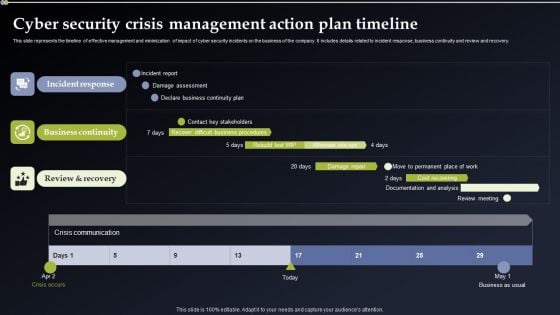
Deploying Cyber Security Incident Response Administration Cyber Security Crisis Management Action Pictures PDF
This slide represents the timeline of effective management and minimization of impact of cyber security incidents on the business of the company. It includes details related to incident response, business continuity and review and recovery. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Deploying Cyber Security Incident Response Administration Cyber Security Crisis Management Action Pictures PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Smart Home Security Solutions Company Profile Security Company Case Study Brochure PDF
This slide highlights the case study of security company which includes key problems such as theft, fire breakout with integrated solution and business value delivered. Presenting Smart Home Security Solutions Company Profile Security Company Case Study Brochure PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like High Value Brand, Client Problem Storing, Integrated Solution Warehousing, Business Value Delivered. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
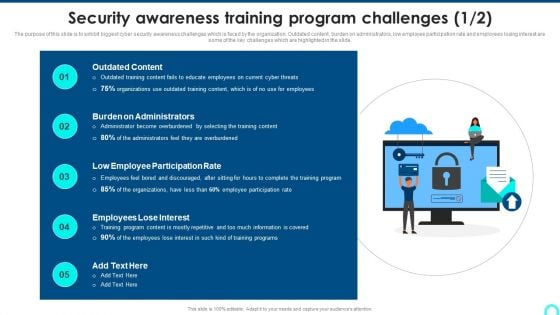
Security Awareness Training Program Challenges Rules PDF
The purpose of this slide is to exhibit biggest cyber security awareness challenges which is faced by the organization. Outdated content, burden on administrators, low employee participation rate and employees losing interest are some of the key challenges which are highlighted in the slide. Presenting Security Awareness Training Program Challenges Rules PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Outdated Content, Burden On Administrators, Employee Participation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Privacy Security Ppt PowerPoint Presentation Show Outline
Presenting this set of slides with name privacy security ppt powerpoint presentation show outline. This is a four stage process. The stages in this process are technology, marketing, planning, business, management. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Security Camera System Company Profile Security Company Case Study Clipart PDF
This slide highlights the case study of security company which includes key problems such as theft, fire breakout with integrated solution and business value delivered. This is a Security Camera System Company Profile Security Company Case Study Clipart PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Integrated Solution, Value Delivered, Client Problem. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
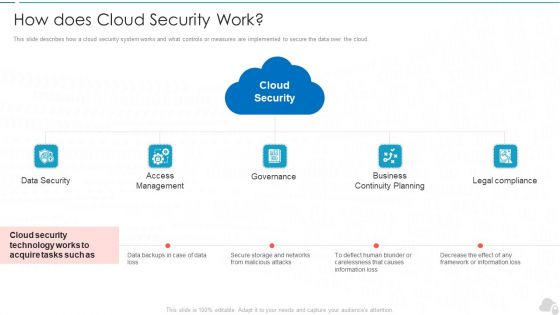
How Does Cloud Security Work Cloud Computing Security IT Ppt Show Graphics Design PDF
This slide describes how a cloud security system works and what controls or measures are implemented to secure the data over the cloud. Presenting how does cloud security work cloud computing security it ppt show graphics design pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like data security, access management, governance, business continuity planning, legal compliance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Security Automation Systems Guide Security Automation Architecture With Key Elements Inspiration PDF
This slide showcases the architecture of security automation which includes security automation logs, security admin, policy server, active directory, reputation feeds and other data sources. Make sure to capture your audiences attention in your business displays with our gratis customizable IT Security Automation Systems Guide Security Automation Architecture With Key Elements Inspiration PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
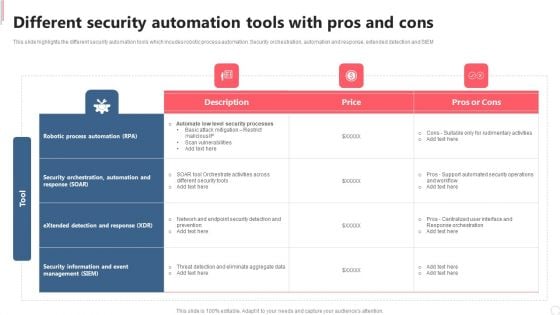
Cyber Security Automation Framework Different Security Automation Tools With Pros And Cons Clipart PDF
This slide highlights the different security automation tools which incudes robotic process automation. Security orchestration, automation and response, extended detection and SIEM. Make sure to capture your audiences attention in your business displays with our gratis customizable Cyber Security Automation Framework Different Security Automation Tools With Pros And Cons Clipart PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
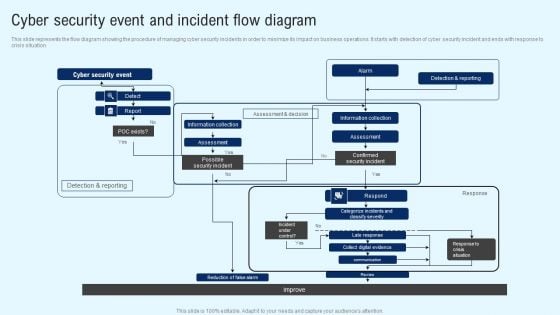
Implementing Cyber Security Incident Cyber Security Event And Incident Flow Diagram Download PDF
This slide represents the flow diagram showing the procedure of managing cyber security incidents in order to minimize its impact on business operations. It starts with detection of cyber security incident and ends with response to crisis situation. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Implementing Cyber Security Incident Cyber Security Event And Incident Flow Diagram Download PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
CYBER Security Breache Response Strategy Cyber Security Incident Response Lifecycle Icons PDF
This slide represents the lifecycle of incident response which enables organizations to quickly detect and halt attacks, minimize damage and prevent future attacks of same type. It includes four phases of cyber security incident response such as preparation, detection and analysis etc. Make sure to capture your audiences attention in your business displays with our gratis customizable CYBER Security Breache Response Strategy Cyber Security Incident Response Lifecycle Icons PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Security Risk Management Assessment Checklist Mockup PDF
This slide shows a security risk management assessment checklist with multiple categories. Deliver an awe inspiring pitch with this creative security risk management assessment checklist mockup pdf bundle. Topics like information security policy document, identification of risks from third party, reporting security threat incidents can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Security Analysis Bar Graph Ppt Slides
This is a security analysis bar chart ppt slides. This is a one stage process. The stages in this process are business, finance, marketing.
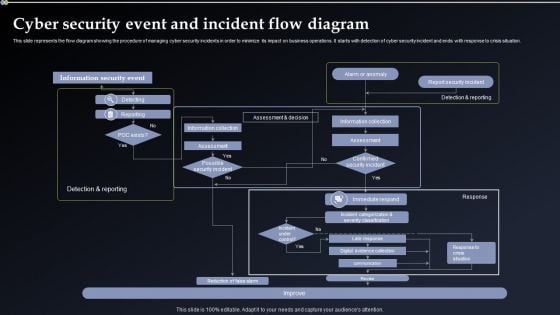
Deploying Cyber Security Incident Response Administration Cyber Security Event And Incident Portrait PDF
This slide represents the flow diagram showing the procedure of managing cyber security incidents in order to minimize its impact on business operations. It starts with detection of cyber security incident and ends with response to crisis situation. Welcome to our selection of the Deploying Cyber Security Incident Response Administration Cyber Security Event And Incident Portrait PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.

What Is Cloud Security Guidelines PDF
This slide depicts the meaning of cloud security, and parties involve in a cloud security framework, such as customers and service providers. Deliver an awe inspiring pitch with this creative What Is Cloud Security Guidelines PDF bundle. Topics like Computing Systems, Protocols, Cloud Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
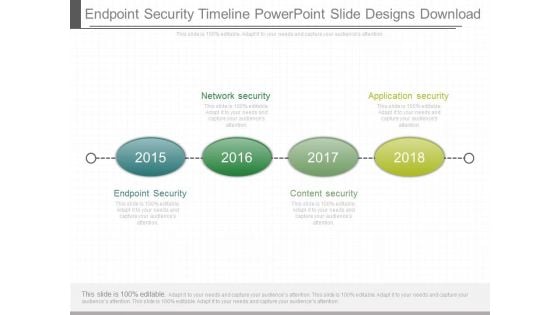
Endpoint Security Timeline Powerpoint Slide Designs Download
This is a endpoint security timeline powerpoint slide designs download. This is a four stage process. The stages in this process are network security, application security, endpoint security, content security.

Sustainable Improving Security By Green Computing Technology
This slide outlines how green computing can improve security. The purpose of this slide is to showcase the pillars of data security, security concerns and solution, and different antivirus software that can help users to protect their computers and networks. Create an editable Sustainable Improving Security By Green Computing Technology that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Sustainable Improving Security By Green Computing Technology is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide outlines how green computing can improve security. The purpose of this slide is to showcase the pillars of data security, security concerns and solution, and different antivirus software that can help users to protect their computers and networks.
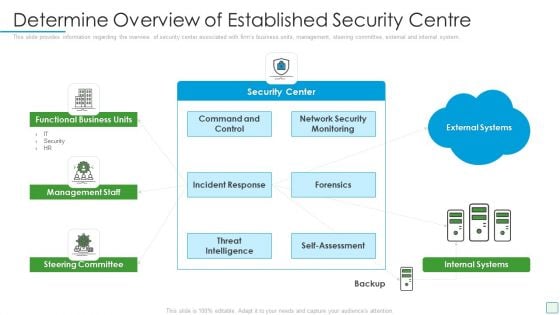
Developing Firm Security Strategy Plan Determine Overview Of Established Security Centre Download PDF
This slide provides information regarding the overview of security center associated with firms business units, management, steering committee, external and internal system. This is a developing firm security strategy plan determine overview of established security centre download pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like functional business units, management staff, steering committee, internal systems. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
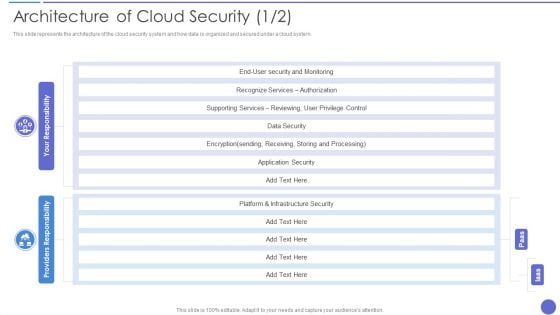
Architecture Of Cloud Security Ideas PDF
This slide represents the architecture of the cloud security system and how data is organized and secured under a cloud system. Deliver an awe inspiring pitch with this creative Architecture Of Cloud Security Ideas PDF bundle. Topics like Recognize Services, Supporting Services, Infrastructure Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Icons Slide For IT Security Designs PDF
Download our innovative and attention grabbing icons slide for it security designs pdf template. The set of slides exhibit completely customizable icons. These icons can be incorporated into any business presentation. So download it immediately to clearly communicate with your clientele.
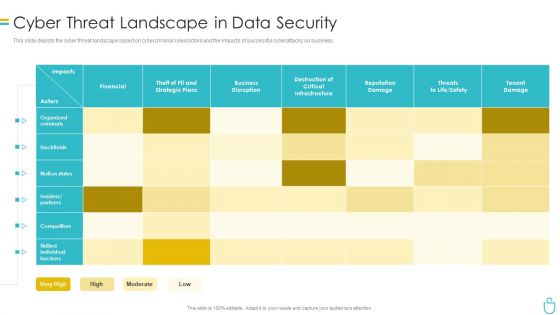
Information Security Cyber Threat Landscape In Data Security Ppt Layouts Brochure PDF
This slide depicts the cyber threat landscape based on cybercriminal roles or actors and the impacts of successful cyberattacks on business. Deliver an awe inspiring pitch with this creative information security cyber threat landscape in data security ppt layouts brochure pdf bundle. Topics like organized criminals, financial, business disruption, reputation damage can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
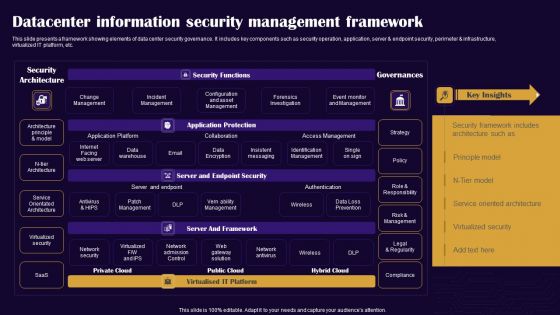
Datacenter Information Security Management Framework Professional PDF
This slide presents a framework showing elements of data center security governance. It includes key components such as security operation, application, server and endpoint security, perimeter and infrastructure, virtualized IT platform, etc. Pitch your topic with ease and precision using this Datacenter Information Security Management Framework Professional PDF. This layout presents information on Security Architecture, Security Functions, Governances. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Defense And National Security Powerpoint Slide Background
This is a defense and national security powerpoint slide background. This is a five stage process. The stages in this process are defense and national security, homeland security, intelligence operations, law enforcement, international affairs and commerce.
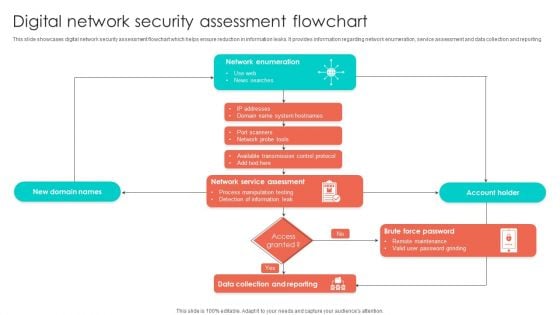
Digital Network Security Assessment Flowchart Structure PDF
This slide showcases digital network security assessment flowchart which helps ensure reduction in information leaks. It provides information regarding network enumeration, service assessment and data collection and reporting. Showcasing this set of slides titled Digital Network Security Assessment Flowchart Structure PDF. The topics addressed in these templates are Account Holder, Information Leak, Network Service Assessment. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Timeline For Implementing Efficient Application Security Testing
This slide outlines the different steps performed while deploying application security, including planning phase, requirement gathering, etc. Are you searching for a Timeline For Implementing Efficient Application Security Testing that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Timeline For Implementing Efficient Application Security Testing from Slidegeeks today. This slide outlines the different steps performed while deploying application security, including planning phase, requirement gathering, etc.
Enterprise Security Strategy Sample Diagram Ppt Design
This is a enterprise security strategy sample diagram ppt design. This is a five stage process. The stages in this process are security strategy, governance, drivers, compliance, capability.


 Continue with Email
Continue with Email

 Home
Home


































