Business Security

Security Training Program Frameworks Contd Hacking Prevention Awareness Training For IT Security Background PDF
This slide outlines the criteria, describes possible positions that could be subject to instruction, instruction information sources, and metrics to assess training success in those control areas. Deliver an awe inspiring pitch with this creative security training program frameworks contd hacking prevention awareness training for it security background pdf bundle. Topics like management, implement, security policy, monitor can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

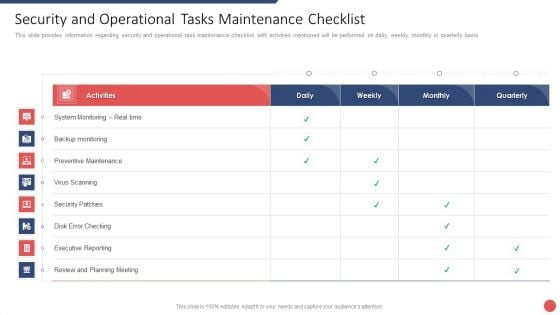
Information And Technology Security Operations Security And Operational Tasks Maintenance Checklist Pictures PDF
This slide provides information regarding security and operational task maintenance checklist with activities mentioned will be performed on daily, weekly, monthly or quarterly basis. Deliver and pitch your topic in the best possible manner with this information and technology security operations security and operational tasks maintenance checklist pictures pdf. Use them to share invaluable insights on system monitoring, executive reporting, planning meeting, preventive maintenance and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
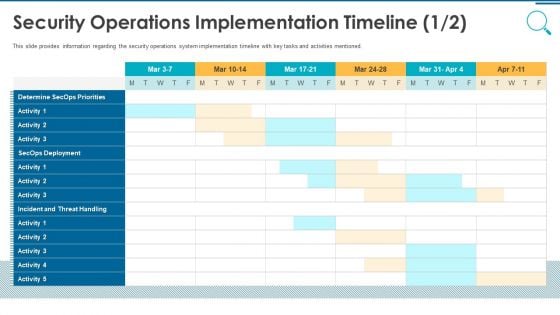
Information And Technology Security Operations Security Operations Implementation Timeline Activity Professional PDF
This slide provides information regarding the security operations system implementation timeline with key tasks and activities mentioned. Deliver an awe inspiring pitch with this creative information and technology security operations security operations implementation timeline activity professional pdf bundle. Topics like determine secops priorities, secops deployment, incident and threat handling can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
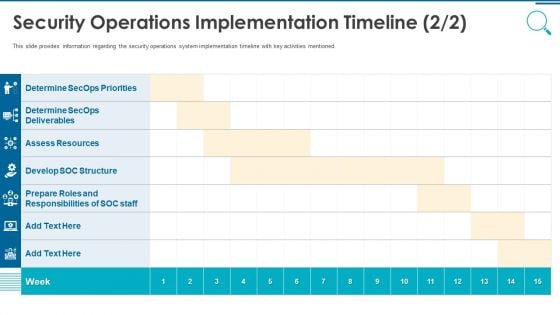
Information And Technology Security Operations Security Operations Implementation Timeline Staff Template PDF
This slide provides information regarding the security operations system implementation timeline with key activities mentioned. Deliver and pitch your topic in the best possible manner with this information and technology security operations security operations implementation timeline staff template pdf. Use them to share invaluable insights on assess resources, develop soc structure, determine secops deliverables and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
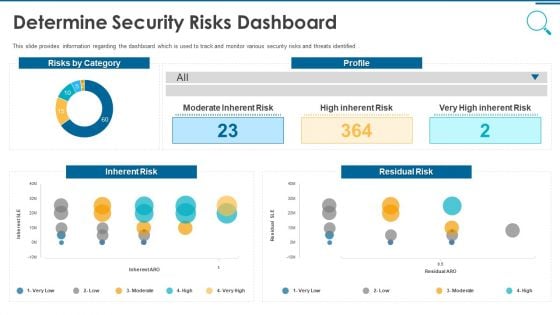
Information And Technology Security Operations Determine Security Risks Dashboard Themes PDF
This slide provides information regarding the dashboard which is used to track and monitor various security risks and threats identified. Deliver and pitch your topic in the best possible manner with this information and technology security operations determine security risks dashboard themes pdf. Use them to share invaluable insights on moderate inherent risk, high inherent risk, very high inherent risk and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Organizational Security Solutions Security And Operational Tasks Maintenance Checklist Pictures PDF
This slide provides information regarding security and operational task maintenance checklist with activities mentioned will be performed on daily, weekly, monthly or quarterly basis. Deliver and pitch your topic in the best possible manner with this organizational security solutions security and operational tasks maintenance checklist pictures pdf. Use them to share invaluable insights on system monitoring, executive reporting, planning meeting, preventive maintenance and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Security Functioning Centre Security And Operational Tasks Maintenance Checklist Inspiration PDF
This slide provides information regarding security and operational task maintenance checklist with activities mentioned will be performed on daily, weekly, monthly or quarterly basis. Deliver and pitch your topic in the best possible manner with this security functioning centre security and operational tasks maintenance checklist inspiration pdf. Use them to share invaluable insights on executive reporting, review and planning meeting, system monitoring and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
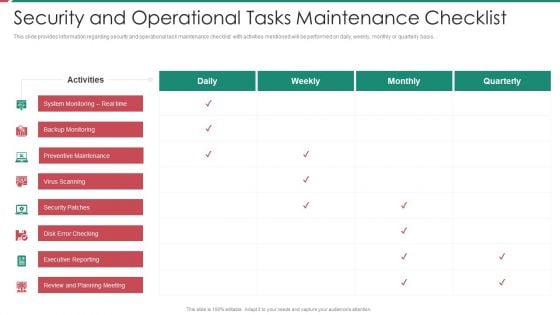
Security And Process Integration Security And Operational Tasks Maintenance Checklist Diagrams PDF
This slide provides information regarding security and operational task maintenance checklist with activities mentioned will be performed on daily, weekly, monthly or quarterly basis. Deliver and pitch your topic in the best possible manner with this security and process integration security and operational tasks maintenance checklist diagrams pdf. Use them to share invaluable insights on system monitoring, executive reporting, planning meeting, preventive maintenance and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
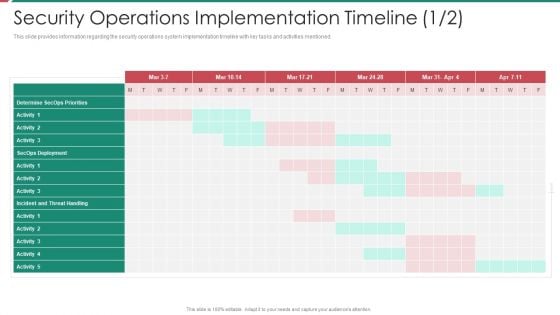
Security And Process Integration Security Operations Implementation Timeline Activity Inspiration PDF
This slide provides information regarding the security operations system implementation timeline with key tasks and activities mentioned. Deliver an awe inspiring pitch with this creative security and process integration security operations implementation timeline activity inspiration pdf bundle. Topics like determine secops priorities, secops deployment, incident and threat handling can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
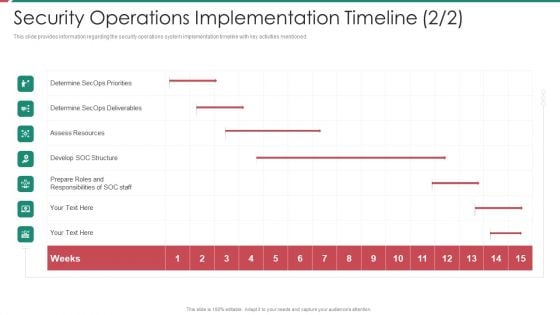
Security And Process Integration Security Operations Implementation Timeline Staff Ideas PDF
This slide provides information regarding the security operations system implementation timeline with key activities mentioned. Deliver and pitch your topic in the best possible manner with this security and process integration security operations implementation timeline staff ideas pdf. Use them to share invaluable insights on assess resources, develop soc structure, determine secops deliverables and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
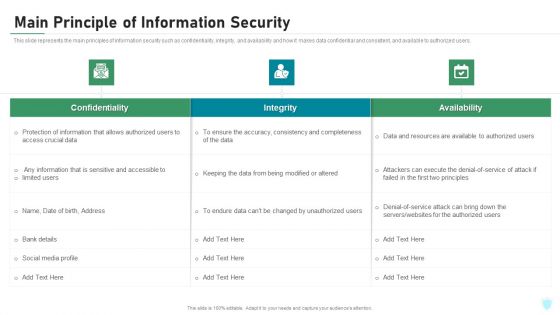
IT Security IT Main Principle Of Information Security Ppt Show Example Topics PDF
This slide represents the main principles of information security such as confidentiality, integrity, and availability and how it makes data confidential and consistent, and available to authorized users. Deliver an awe inspiring pitch with this creative it security it main principle of information security ppt show example topics pdf bundle. Topics like confidentiality, integrity, availability can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
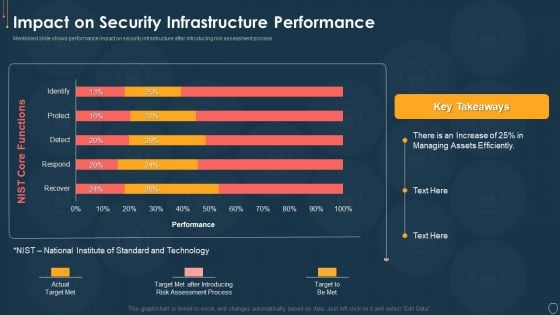
Cyber Security Risk Management Plan Impact On Security Infrastructure Performance Microsoft PDF
Mentioned slide shows performance impact on security infrastructure after introducing risk assessment process. Deliver and pitch your topic in the best possible manner with this cyber security risk management plan impact on security infrastructure performance microsoft pdf. Use them to share invaluable insights on efficiently, process, target, technology and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Security Risk Management Plan Information Security Risk Management Dashboard Sample PDF
Following slide covers information security risk management dashboard. It include KPIs such as risk analysis progress, percent risk, response progress for risks and number of risks encountered. Deliver an awe inspiring pitch with this creative cyber security risk management plan information security risk management dashboard sample pdf bundle. Topics like vulnerabilities, entities, action plan, risk analysis can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Information Security Compliance Dashboard Of Data Security Ppt Icon Vector PDF
This slide depicts the data security compliance report on how data and hardware are monitored in different categories such as standard, regulation, and asset type control. Deliver an awe inspiring pitch with this creative information security compliance dashboard of data security ppt icon vector pdf bundle. Topics like asset type control, control issues by standard, control issues by regulation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Information Security Data Security Awareness Training For Staff Ppt Visual Aids Pictures PDF
This slide represents the data security awareness training program for staff, including the name of the participants and what modules would be covered under training daily. Deliver and pitch your topic in the best possible manner with this information security data security awareness training for staff ppt visual aids pictures pdf. Use them to share invaluable insights on project managers, developers, senior executives, planning and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
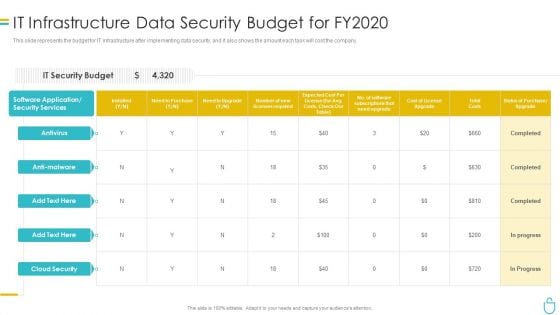
Information Security It Infrastructure Data Security Budget For FY2020 Ppt Inspiration File Formats PDF
This slide represents the budget for IT infrastructure after implementing data security, and it also shows the amount each task will cost the company. Deliver and pitch your topic in the best possible manner with this information security it infrastructure data security budget for fy2020 ppt inspiration file formats pdf. Use them to share invaluable insights on costs, need to purchase, required, application and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
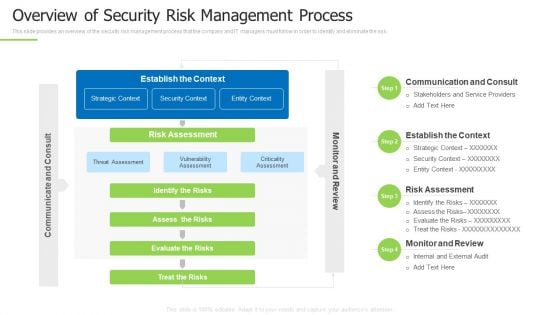
Techniques And Strategies To Reduce Security Management Risks Overview Of Security Risk Background PDF
This slide provides an overview of the security risk management process that the company and IT managers must follow in order to identify and eliminate the risk. Deliver an awe inspiring pitch with this creative techniques and strategies to reduce security management risks overview of security risk background pdf bundle. Topics like identify the risks, strategic context, vulnerability assessment can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Desktop Security Management Computer Security Awareness Training For Staff Template PDF
This slide represents the cybersecurity awareness training program for staff, including the name of the participants and what modules would be covered under training daily. Deliver an awe inspiring pitch with this creative desktop security management computer security awareness training for staff template pdf bundle. Topics like project managers, developers, senior executives, security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
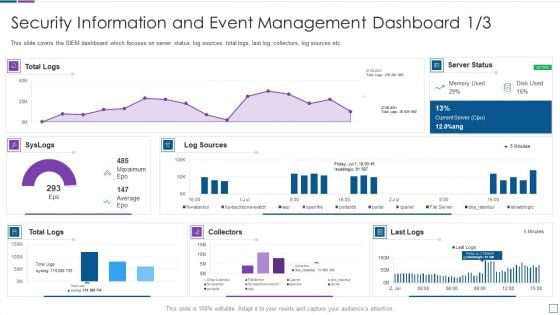
Real Time Assessment Of Security Threats Security Information And Event Management Microsoft PDF
This slide covers the SIEM dashboard which focuses on server status, log sources, total logs, last log, collectors, log sources etc. Deliver and pitch your topic in the best possible manner with this real time assessment of security threats security information and event management microsoft pdf. Use them to share invaluable insights on security information and event management dashboard and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
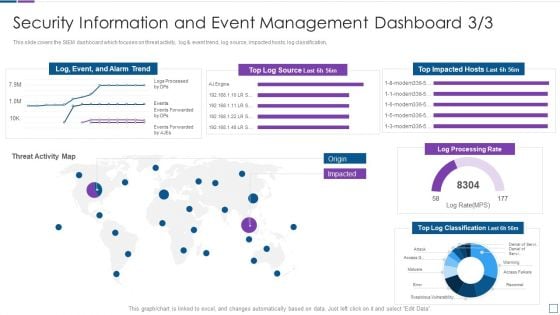
Security Information And Event Management Real Time Assessment Of Security Threats Template PDF
This slide covers the SIEM dashboard which focuses on threat activity, log and event trend, log source, impacted hosts, log classification. Deliver an awe inspiring pitch with this creative security information and event management real time assessment of security threats template pdf bundle. Topics like security information and event management dashboard can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
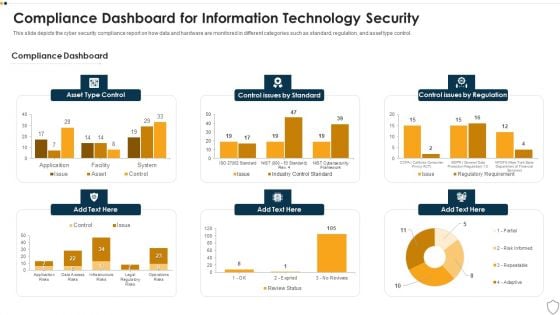
IT Security Compliance Dashboard For Information Technology Security Ppt Slides Brochure PDF
This slide depicts the cyber security compliance report on how data and hardware are monitored in different categories such as standard, regulation, and asset type control. Deliver an awe inspiring pitch with this creative it security compliance dashboard for information technology security ppt slides brochure pdf bundle. Topics like asset type control, control issues by standard, control issues by regulation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
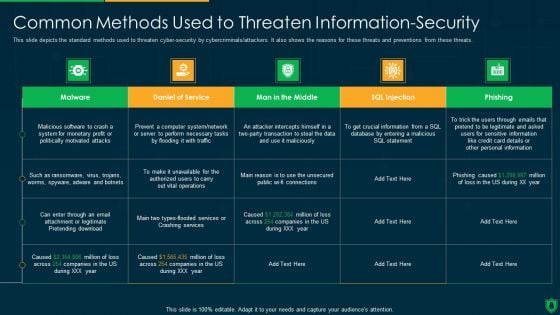
Info Security Common Methods Used To Threaten Information Security Ppt PowerPoint Presentation Gallery Clipart Images PDF
This slide depicts the standard methods used to threaten cyber-security by cybercriminals or attackers. It also shows the reasons for these threats and preventions from these threats. Deliver an awe inspiring pitch with this creative info security common methods used to threaten information security ppt powerpoint presentation gallery clipart images pdf bundle. Topics like personal information, phishing caused, sql statement can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
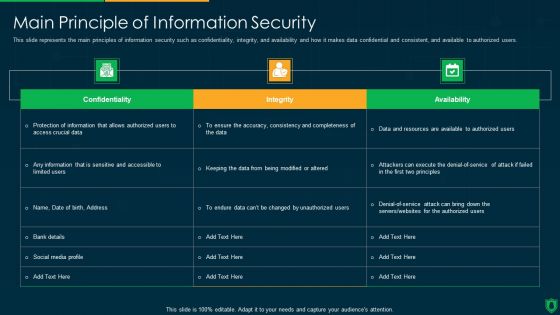
Info Security Main Principle Of Information Security Ppt PowerPoint Presentation File Background Designs PDF
This slide represents the main principles of information security such as confidentiality, integrity, and availability and how it makes data confidential and consistent, and available to authorized users. Deliver an awe inspiring pitch with this creative info security main principle of information security ppt powerpoint presentation file background designs pdf bundle. Topics like integrity, confidentiality, availability, data can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Risk Management Model For Data Security Information Security Risk Assessment Worksheet Infographics PDF
This slide illustrates information security risk assessment worksheet. Risk covered are monetary loss, reputation loss and loss of customer confidence. Deliver and pitch your topic in the best possible manner with this Risk Management Model For Data Security Information Security Risk Assessment Worksheet Infographics PDF. Use them to share invaluable insights on Facilities And Equipment, Software Application, At Personnel Level, Monetary Loss, Risk and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
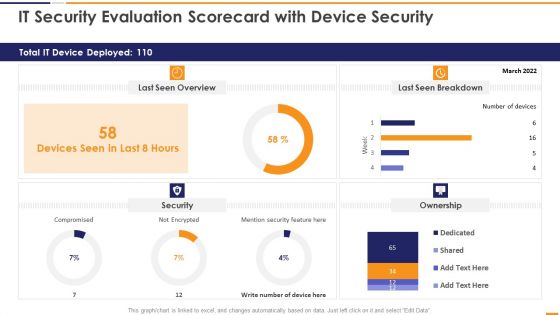
IT Security Evaluation Scorecard With Device Security Ppt Slides Good PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver an awe inspiring pitch with this creative IT Security Evaluation Scorecard With Device Security Ppt Slides Good PDF bundle. Topics like Total IT Device, Last Seen Overview, Last Seen Breakdown, Mention Security Feature can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
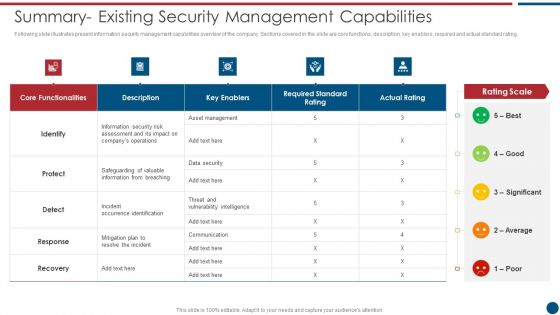
Risk Based Procedures To IT Security Summary Existing Security Management Capabilities Topics PDF
Following slide illustrates present information security management capabilities overview of the company. Sections covered in the slide are core functions, description, key enablers, required and actual standard rating. Deliver an awe inspiring pitch with this creative Risk Based Procedures To IT Security Summary Existing Security Management Capabilities Topics PDF bundle. Topics like Asset Management, Key Enablers, Communication Plan can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
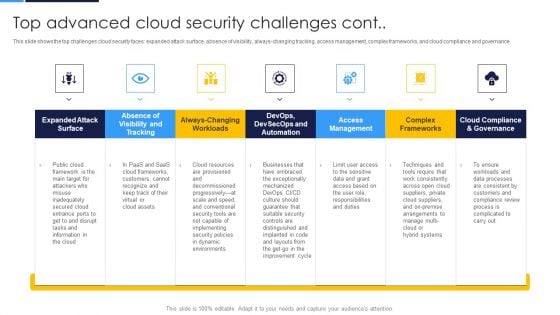
Cloud Security Assessment Top Advanced Cloud Security Challenges Cont Information PDF
This slide shows the top challenges cloud security faces expanded attack surface, absence of visibility, always-changing tracking, access management, complex frameworks, and cloud compliance and governance. Deliver and pitch your topic in the best possible manner with this Cloud Security Assessment Top Advanced Cloud Security Challenges Cont Information PDF. Use them to share invaluable insights on Dynamic Environments, Resources Are Provisioned, Access Management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
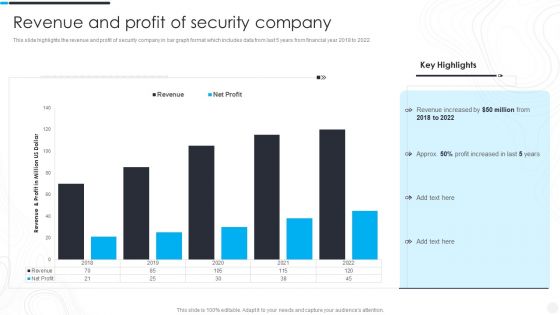
Security Camera System Company Profile Revenue And Profit Of Security Company Clipart PDF
This slide highlights the revenue and profit of security company in bar graph format which includes data from last 5 years from financial year 2018 to 2022.Deliver and pitch your topic in the best possible manner with this Security Camera System Company Profile Revenue And Profit Of Security Company Clipart PDF. Use them to share invaluable insights on Revenue Increased, Profit Increased, Key Highlights and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
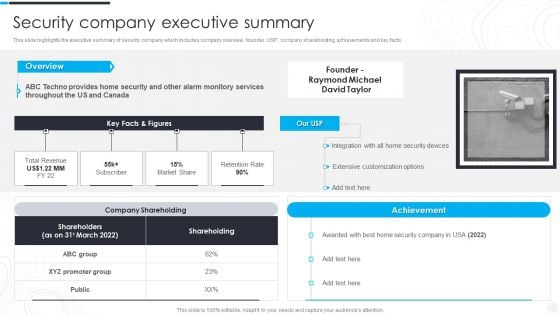
Security Camera System Company Profile Security Company Executive Summary Formats PDF
This slide highlights the executive summary of security company which includes company overview, founder, USP, company shareholding, achievements and key facts.Deliver an awe inspiring pitch with this creative Security Camera System Company Profile Security Company Executive Summary Formats PDF bundle. Topics like Company Shareholding, Customization Options, Raymond Michael can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Information Security Risk Evaluation Budget For Information Security Risk Management Diagrams PDF
This slide showcases budget that can should be allocated for different information security risk management activities. It provides information about employees training, software implementation, risk monitoring and data backup.Deliver an awe inspiring pitch with this creative Information Security Risk Evaluation Budget For Information Security Risk Management Diagrams PDF bundle. Topics like Training Of Employees, Software Implementation, Risk Monitoring can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Information Security Risk Evaluation Checklist For Information Security Risk Management Microsoft PDF
This slide showcases challenges involved in formulating risk management program for information security. It also shows solutions to tackle the challenges and impact of implementing them.Deliver an awe inspiring pitch with this creative Information Security Risk Evaluation Checklist For Information Security Risk Management Microsoft PDF bundle. Topics like Identifying Potential, Defining Mitigation, Created Sales can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
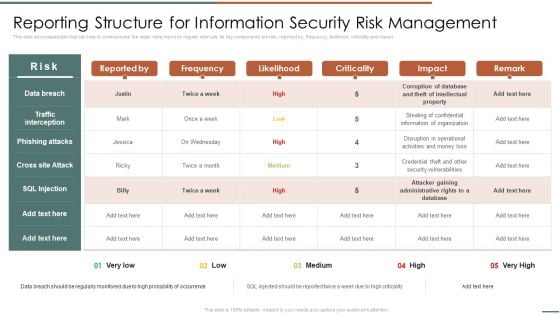
Information Security Risk Evaluation Reporting Structure For Information Security Risk Management Guidelines PDF
This slide showcases plan that can help to communicate the major risks report on regular intervals. Its key components are risk, reported by, frequency, likelihood, criticality and impact.Deliver an awe inspiring pitch with this creative Information Security Risk Evaluation Reporting Structure For Information Security Risk Management Guidelines PDF bundle. Topics like Phishing Attacks, Cross Attack, Security Vulnerabilities can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
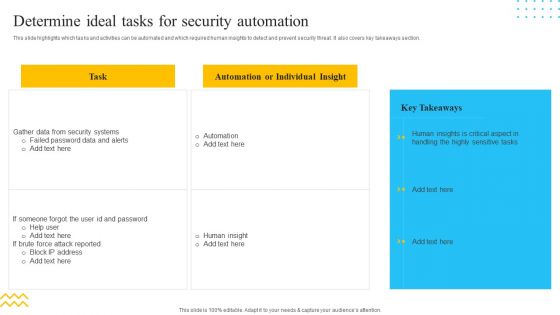
IT Security Automation Tools Integration Determine Ideal Tasks For Security Automation Template PDF
This slide highlights which tasks and activities can be automated and which required human insights to detect and prevent security threat. It also covers key takeaways section. Deliver an awe inspiring pitch with this creative IT Security Automation Tools Integration Determine Ideal Tasks For Security Automation Template PDF bundle. Topics like Automation, Individual Insight, Gather Data can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
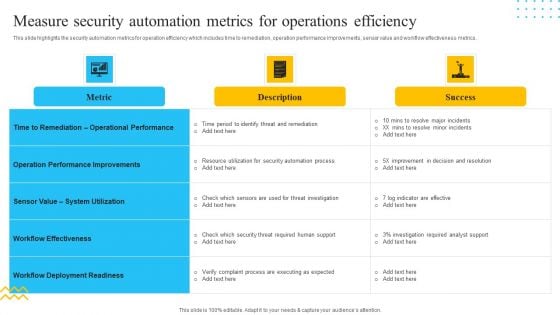
IT Security Automation Tools Integration Measure Security Automation Metrics For Operations Template PDF
This slide highlights the security automation metrics for operation efficiency which includes time to remediation, operation performance improvements, sensor value and workflow effectiveness metrics. Deliver and pitch your topic in the best possible manner with this IT Security Automation Tools Integration Measure Security Automation Metrics For Operations Template PDF. Use them to share invaluable insights on Metric, Operation Performance Improvements, Success and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
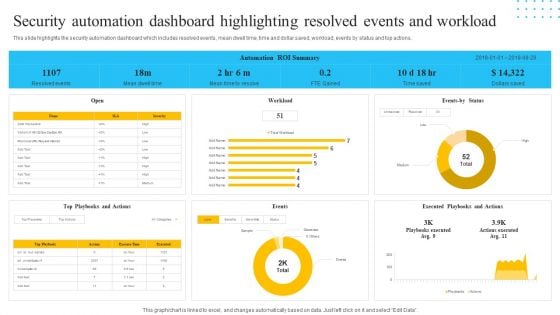
IT Security Automation Tools Integration Security Automation Dashboard Highlighting Resolved Inspiration PDF
This slide highlights the security automation dashboard which includes resolved events, mean dwell time, time and dollar saved, workload, events by status and top actions. Deliver an awe inspiring pitch with this creative IT Security Automation Tools Integration Security Automation Dashboard Highlighting Resolved Inspiration PDF bundle. Topics like Events Status, Workload, Events, Open can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
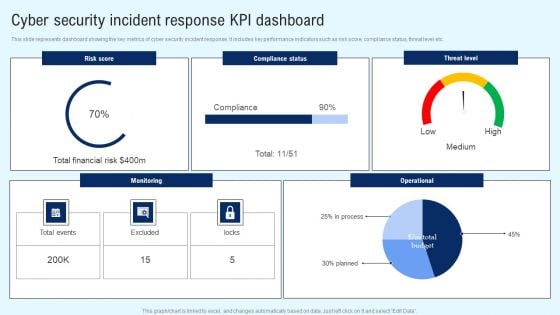
Implementing Cyber Security Incident Cyber Security Incident Response KPI Dashboard Clipart PDF
This slide represents dashboard showing the key metrics of cyber security incident response. It includes key performance indicators such as risk score, compliance status, threat level etc. There are so many reasons you need a Implementing Cyber Security Incident Cyber Security Incident Response KPI Dashboard Clipart PDF. The first reason is you cannot spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
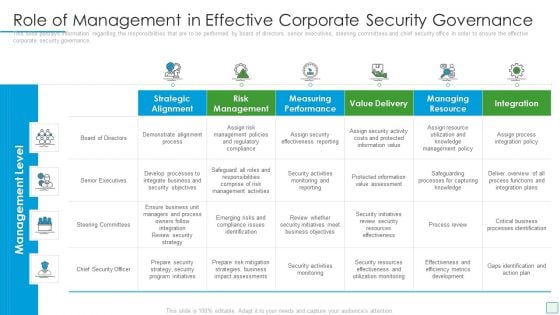
Developing Firm Security Strategy Plan Role Of Management In Effective Corporate Security Governance Slides PDF
This slide portrays information regarding the responsibilities that are to be performed by board of directors, senior executives, steering committees and chief security office in order to ensure the effective corporate security governance. Deliver an awe inspiring pitch with this creative developing firm security strategy plan role of management in effective corporate security governance slides pdf bundle. Topics like strategic alignment, risk management, measuring performance, value delivery, managing resource can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
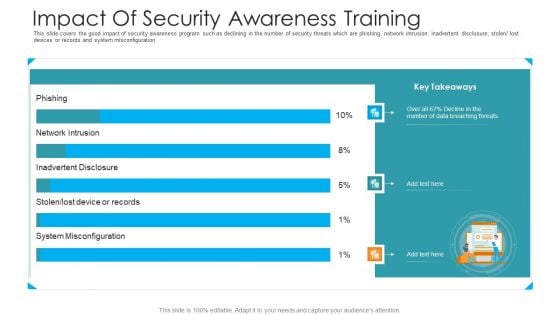
Impact Of Security Awareness Training Hacking Prevention Awareness Training For IT Security Infographics PDF
This slide covers the good impact of security awareness program such as declining in the number of security threats which are phishing, network intrusion, inadvertent disclosure, stolen or lost devices or records and system misconfiguration. Deliver an awe inspiring pitch with this creative impact of security awareness training hacking prevention awareness training for it security infographics pdf bundle. Topics like system misconfiguration, network intrusion breakdown, phishing breakdown can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Information And Technology Security Operations Selecting Suitable Security Incident Management Software Diagrams PDF
This slide will help firm in selecting the suitable automated incident management software which will handle existing security and privacy issues and predict upcoming incidents. The firm will choose effective software with features such as automated workflows, centralized platform, etc. Deliver an awe inspiring pitch with this creative information and technology security operations selecting suitable security incident management software diagrams pdf bundle. Topics like security incident forms, access rights, automated workflows, centralized platform can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
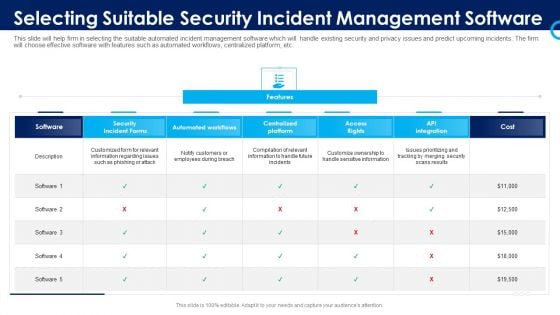
Organizational Security Solutions Selecting Suitable Security Incident Management Software Pictures PDF
This slide will help firm in selecting the suitable automated incident management software which will handle existing security and privacy issues and predict upcoming incidents. The firm will choose effective software with features such as automated workflows, centralized platform, etc. Deliver an awe inspiring pitch with this creative organizational security solutions selecting suitable security incident management software pictures pdf bundle. Topics like security incident forms, access rights, automated workflows, centralized platform can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
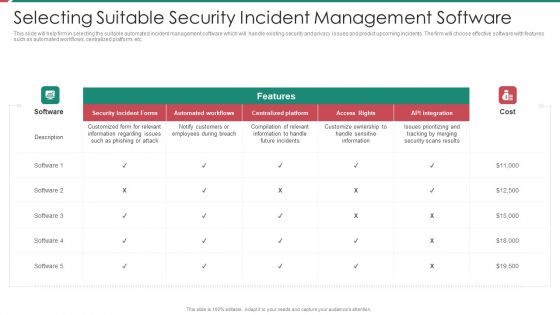
Security And Process Integration Selecting Suitable Security Incident Management Software Brochure PDF
This slide will help firm in selecting the suitable automated incident management software which will handle existing security and privacy issues and predict upcoming incidents. The firm will choose effective software with features such as automated workflows, centralized platform, etc. Deliver an awe inspiring pitch with this creative security and process integration selecting suitable security incident management software brochure pdf bundle. Topics like security incident forms, access rights, automated workflows, centralized platform can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
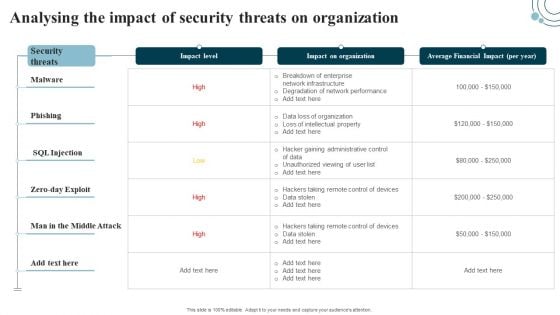
Developing IT Security Strategy Analysing The Impact Of Security Threats On Organization Ideas PDF
Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Developing IT Security Strategy Analysing The Impact Of Security Threats On Organization Ideas PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Developing IT Security Strategy Analysing The Impact Of Security Threats On Organization Ideas PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers
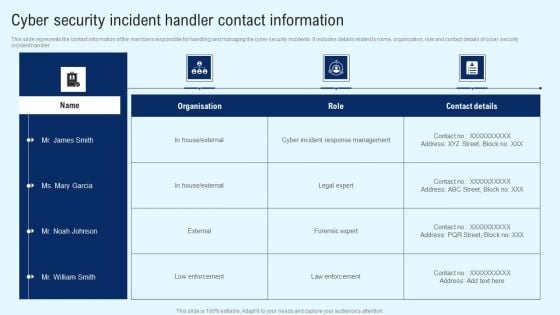
Implementing Cyber Security Incident Cyber Security Incident Handler Contact Information Diagrams PDF
This slide represents the contact information of the members responsible for handling and managing the cyber security incidents. It includes details related to name, organization, role and contact details of cyber security incident handler. Want to ace your presentation in front of a live audience Our Implementing Cyber Security Incident Cyber Security Incident Handler Contact Information Diagrams PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.
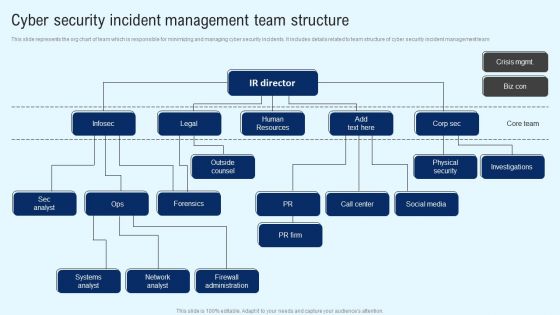
Implementing Cyber Security Incident Cyber Security Incident Team Structure Download PDF
This slide represents the org chart of team which is responsible for minimizing and managing cyber security incidents. It includes details related to team structure of cyber security incident management team The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Implementing Cyber Security Incident Cyber Security Incident Team Structure Download PDF from Slidegeeks and deliver a wonderful presentation.

Organizing Security Awareness Measuring The Impact Of Security Awareness Training Background PDF
The purpose of this slide is to highlight the positive impact of security awareness training. Information covered in this slide is related to malware attack, social engineering attack and business email compromise. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Organizing Security Awareness Measuring The Impact Of Security Awareness Training Background PDF from Slidegeeks and deliver a wonderful presentation.

Uniformed Security Project Summary For Security Guard Services Proposal Slides PDF
Deliver an awe inspiring pitch with this creative uniformed security project summary for security guard services proposal slides pdf bundle. Topics like relationship philosophy, organizational abilities, competitive advantages, customer service tools, innovative programs can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Uniformed Security Cover Letter For Security Guard Services Proposal Pictures PDF
Deliver an awe inspiring pitch with this creative uniformed security cover letter for security guard services proposal pictures pdf bundle. Topics like cover letter can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
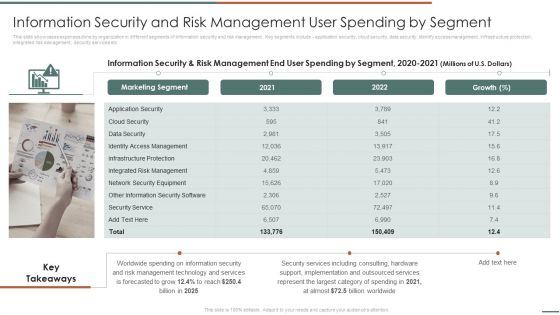
Information Security Risk Evaluation Information Security And Risk Management User Spending By Segment Demonstration PDF
This slide showcases expenses done by organization in different segments of information security and risk management. Key segments include application security, cloud security, data security, identify access management, infrastructure protection, integrated risk management, security services etc.This is a Information Security Risk Evaluation Information Security And Risk Management User Spending By Segment Demonstration PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Access Management, Infrastructure Protection, Security Equipment. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Elements Of Information Technology Security Information Technology Security Ppt Inspiration Icons PDF
This slide represents the network security element of network security and different network security methods such as firewalls, email security, web security, and antivirus software. Presenting elements of information technology security information technology security ppt inspiration icons pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like network security methods, tools, techniques, respond. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
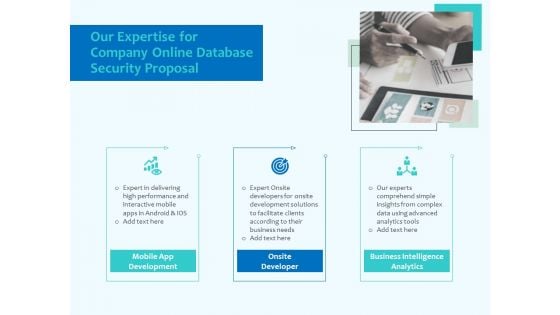
Best Data Security Software Our Expertise For Company Online Database Security Proposal Formats PDF
Presenting this set of slides with name best data security software our expertise for company online database security proposal formats pdf. This is a three stage process. The stages in this process are mobile app development, onsite developer, business intelligence analytics. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
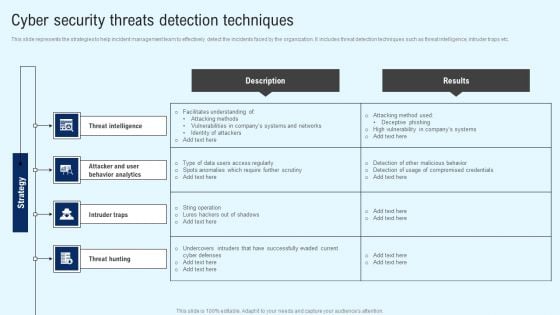
Implementing Cyber Security Incident Cyber Security Threats Detection Techniques Slides PDF
This slide represents the strategies to help incident management team to effectively detect the incidents faced by the organization. It includes threat detection techniques such as threat intelligence, intruder traps etc. Are you searching for a Implementing Cyber Security Incident Cyber Security Threats Detection Techniques Slides PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal. With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Implementing Cyber Security Incident Cyber Security Threats Detection Techniques Slides PDF from Slidegeeks today.
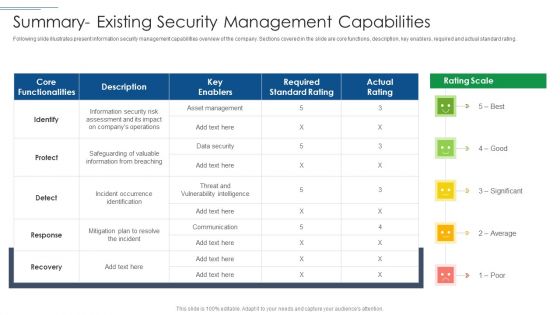
IT Security Risk Management Approach Introduction Summary Existing Security Management Capabilities Topics PDF
Deliver an awe inspiring pitch with this creative IT Security Risk Management Approach Introduction Summary Existing Security Management Capabilities Topics PDF bundle. Topics like Required Standard Rating, Asset Management, Protect can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Best Data Security Software Mode Of Communication For Company Online Database Security Proposal Inspiration PDF
Presenting this set of slides with name best data security software mode of communication for company online database security proposal inspiration pdf. The topics discussed in these slides are communicate medium, description. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
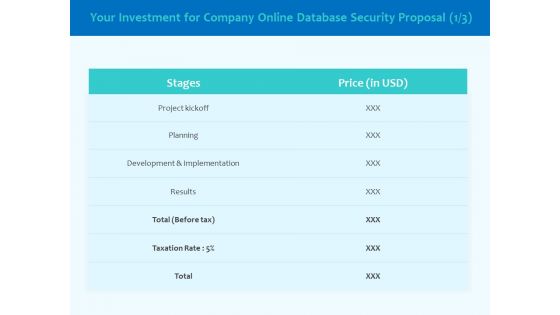
Best Data Security Software Your Investment For Company Online Database Security Proposal Slides PDF
Presenting this set of slides with name best data security software your investment for company online database security proposal slides pdf. The topics discussed in these slides are project kickoff, planning, development and implementation, result. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
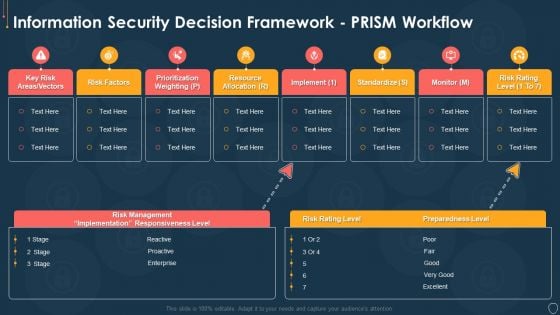
Cyber Security Risk Management Plan Information Security Decision Framework Prism Workflow Brochure PDF
Deliver and pitch your topic in the best possible manner with this cyber security risk management plan information security decision framework prism workflow brochure pdf. Use them to share invaluable insights on implement, standardize, monitor, risk rating level, resource allocation and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Information Security Dashboard For Threat Tracking In Data Security Summary PDF
Deliver an awe inspiring pitch with this creative information security dashboard for threat tracking in data security summary pdf bundle. Topics like monthly threat status, current risk status, threats based on role, threats by owners, risk by threats can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
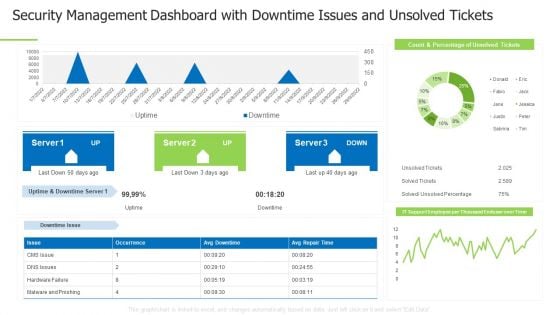
Techniques And Strategies To Reduce Security Management Risks Security Management Dashboard Information PDF
Deliver an awe inspiring pitch with this creative techniques and strategies to reduce security management risks security management dashboard information pdf bundle. Topics like logical access control, physical access control, access control categories can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
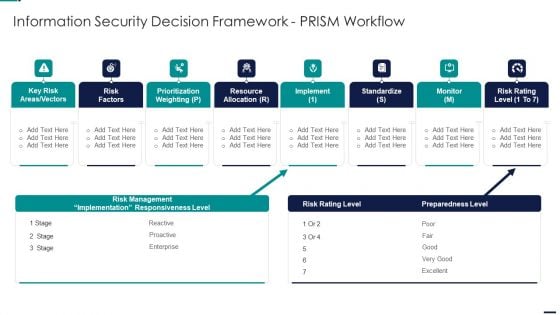
Risk Management Model For Data Security Information Security Decision Framework Prism Diagrams PDF
Deliver an awe inspiring pitch with this creative Risk Management Model For Data Security Information Security Decision Framework Prism Diagrams PDF bundle. Topics like Key Risk Areas, Vectors, Risk Factors, Prioritization Weighting, Resource Allocation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Organizing Security Awareness Comparison Of Various Security Awareness Training Themes PDF
The purpose of this slide is to drawn comparison of multiple software which can be used to provide cyber security training to the key stakeholders. Information covered in this slide is related to phishing simulations, security reporting, individualized security training plan etc. Want to ace your presentation in front of a live audience Our Organizing Security Awareness Comparison Of Various Security Awareness Training Themes PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.
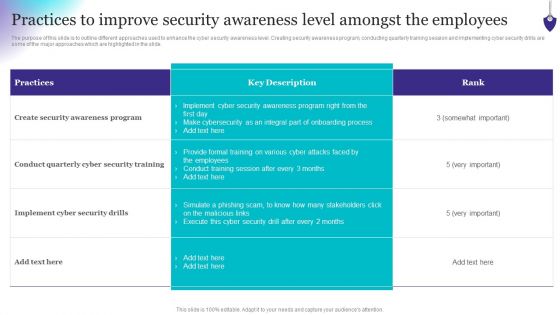
Organizing Security Awareness Practices To Improve Security Awareness Level Amongst Demonstration PDF
The purpose of this slide is to outline different approaches used to enhance the cyber security awareness level. Creating security awareness program, conducting quarterly training session and implementing cyber security drills are some of the major approaches which are highlighted in the slide. This Organizing Security Awareness Practices To Improve Security Awareness Level Amongst Demonstration PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.


 Continue with Email
Continue with Email

 Home
Home


































