Collateral Management
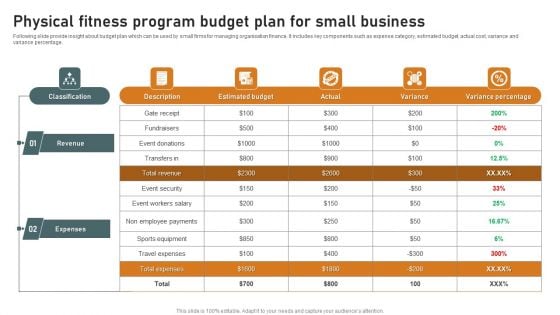
Physical Fitness Program Budget Plan For Small Business Guidelines PDF
Following slide provide insight about budget plan which can be used by small firms for managing organisation finance. It includes key components such as expense category, estimated budget, actual cost, variance and variance percentage. Showcasing this set of slides titled Physical Fitness Program Budget Plan For Small Business Guidelines PDF. The topics addressed in these templates are Revenue, Expenses, Event Security . All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
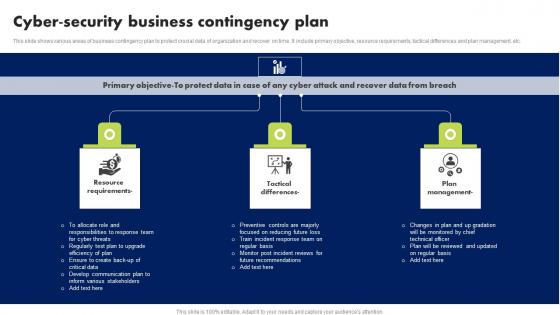
Cyber Security Business Contingency Plan Brochure Pdf
This slide shows various areas of business contingency plan to protect crucial data of organization and recover on time. It include primary objective, resource requirements, tactical differences and plan management, etc. Showcasing this set of slides titled Cyber Security Business Contingency Plan Brochure Pdf. The topics addressed in these templates are Resource Requirements, Tactical Differences, Plan Management. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide shows various areas of business contingency plan to protect crucial data of organization and recover on time. It include primary objective, resource requirements, tactical differences and plan management, etc.
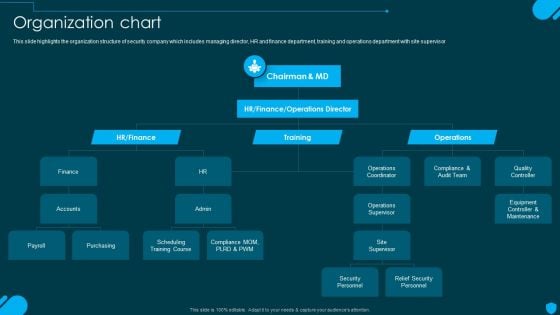
Security And Human Resource Services Business Profile Organization Chart Elements PDF
This slide highlights the organization structure of security company which includes managing director, HR and finance department, training and operations department with site supervisor. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Security And Human Resource Services Business Profile Organization Chart Elements PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Access Control Application Account Security Lock Ppt PowerPoint Presentation File Slide Portrait
This is a access control application account security lock ppt powerpoint presentation file slide portrait. This is a two stage process. The stages in this process are access rights, access management, business.

Access Control System Key Security Lock Ppt PowerPoint Presentation Pictures Summary
This is a access control system key security lock ppt powerpoint presentation pictures summary. This is a three stage process. The stages in this process are access rights, access management, business.

Impact Of Cyber Security Policies And Practices Ppt PowerPoint Presentation Diagram Graph Charts PDF
The following slide focuses on drafting cyber security policies to manage data control and breach. It mainly includes elements such as impact of existing cyber safety policies, mitigation actions, Presenting this PowerPoint presentation, titled Impact Of Cyber Security Policies And Practices Ppt PowerPoint Presentation Diagram Graph Charts PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Impact Of Cyber Security Policies And Practices Ppt PowerPoint Presentation Diagram Graph Charts PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Impact Of Cyber Security Policies And Practices Ppt PowerPoint Presentation Diagram Graph Charts PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.
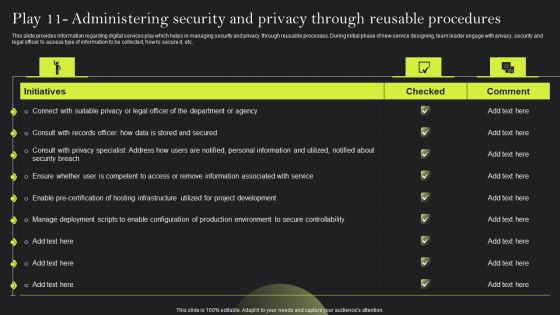
Playbook For Advancing Technology Play 11 Administering Security And Privacy Elements PDF
This slide provides information regarding digital services play which helps in managing security and privacy through reusable processes. During initial phase of new service designing, team leader engage with privacy, security and legal officer to assess type of information to be collected, how to secure it, etc. Retrieve professionally designed Playbook For Advancing Technology Play 11 Administering Security And Privacy Elements PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You dont have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
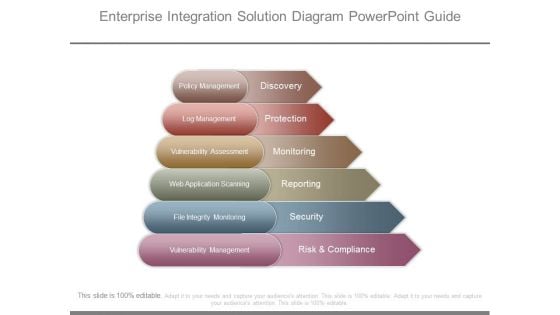
Enterprise Integration Solution Diagram Powerpoint Guide
This is a enterprise integration solution diagram powerpoint guide. This is a six stage process. The stages in this process are policy management, log management, vulnerability assessment, web application scanning, file integrity monitoring, vulnerability management, discovery, protection, monitoring, reporting, security, risk and compliance.
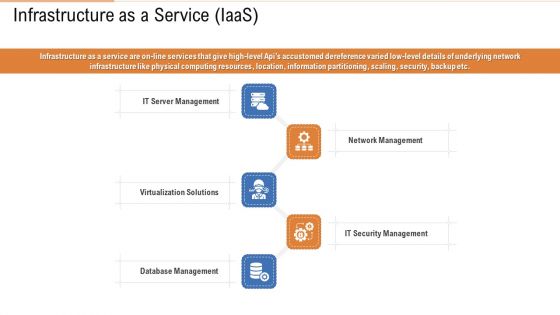
Public Vs Privatized Vs Hybrid Vs Alliance In Cloud Storage Infrastructure As A Service Iaas Formats PDF
This is a public vs privatized vs hybrid vs alliance in cloud storage infrastructure as a service iaas formats pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like network management, security management, database management, server management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
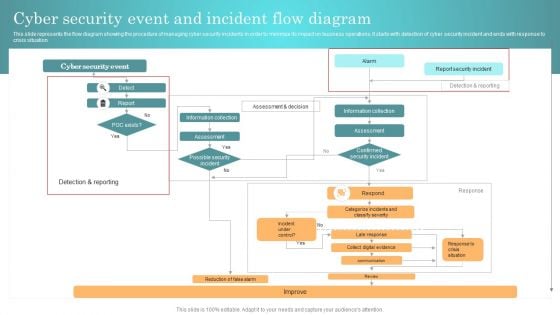
Incident Response Techniques Deployement Cyber Security Event And Incident Flow Diagram Structure PDF
This slide represents the flow diagram showing the procedure of managing cyber security incidents in order to minimize its impact on business operations. It starts with detection of cyber security incident and ends with response to crisis situation. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Incident Response Techniques Deployement Cyber Security Event And Incident Flow Diagram Structure PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Incident Response Techniques Deployement Cyber Security Event And Incident Flow Diagram Structure PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.
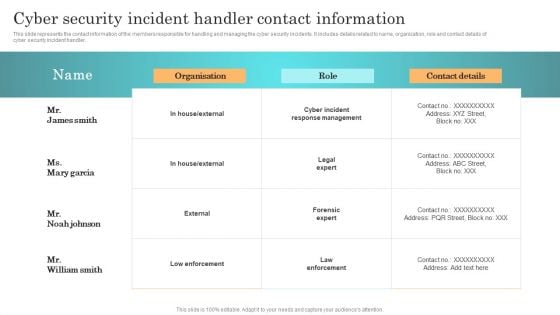
Incident Response Techniques Deployement Cyber Security Incident Handler Contact Information Guidelines PDF
This slide represents the contact information of the members responsible for handling and managing the cyber security incidents. It includes details related to name, organization, role and contact details of cyber security incident handler. Get a simple yet stunning designed Incident Response Techniques Deployement Cyber Security Incident Handler Contact Information Guidelines PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Incident Response Techniques Deployement Cyber Security Incident Handler Contact Information Guidelines PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
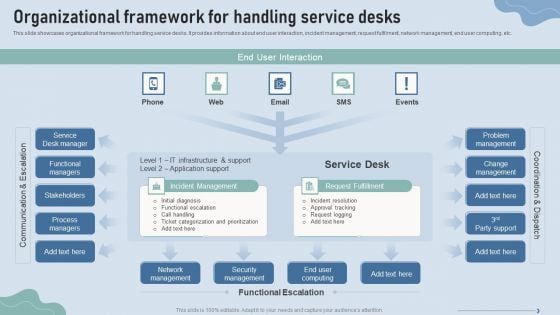
Improve IT Service Desk Organizational Framework For Handling Service Desks Background PDF
This slide showcases organizational framework for handling service desks. It provides information about end user interaction, incident management, request fulfilment, network management, end user computing, etc. Deliver and pitch your topic in the best possible manner with this Improve IT Service Desk Organizational Framework For Handling Service Desks Background PDF. Use them to share invaluable insights on Security Management, Network Management, Incident Resolution and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
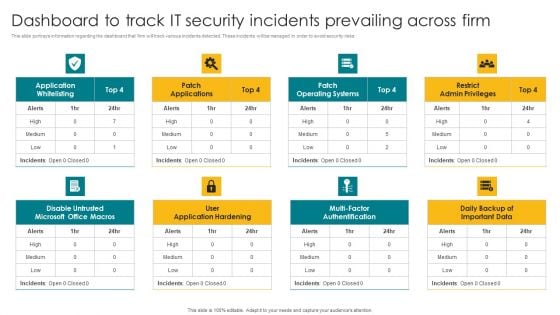
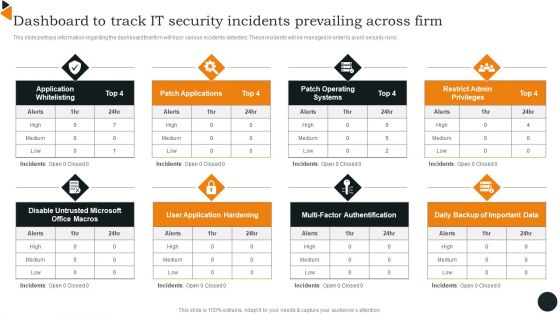
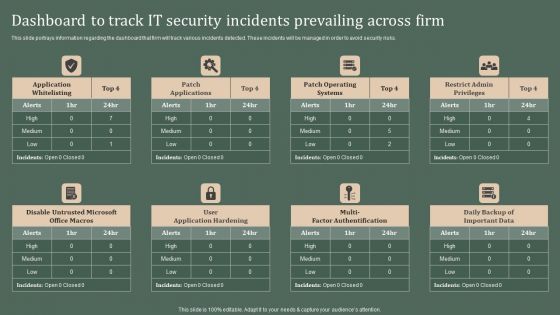
Dashboard To Track IT Security Incidents Prevailing Across Firm Elements PDF
This slide portrays information regarding the dashboard that firm will track various incidents detected. These incidents will be managed in order to avoid security risks. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Dashboard To Track IT Security Incidents Prevailing Across Firm Elements PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Dashboard To Track IT Security Incidents Prevailing Across Firm Elements PDF.
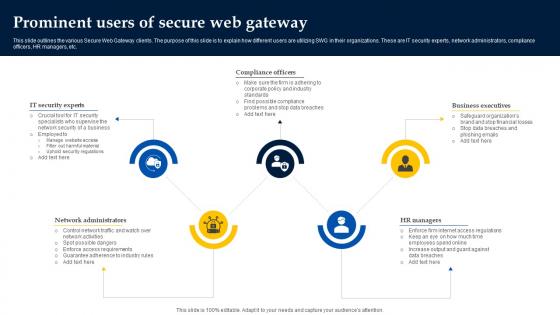
Web Access Control Solution Prominent Users Of Secure Web Gateway
Do you know about Slidesgeeks Web Access Control Solution Prominent Users Of Secure Web Gateway These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide outlines the various Secure Web Gateway clients. The purpose of this slide is to explain how different users are utilizing SWG in their organizations. These are IT security experts, network administrators, compliance officers, HR managers, etc.
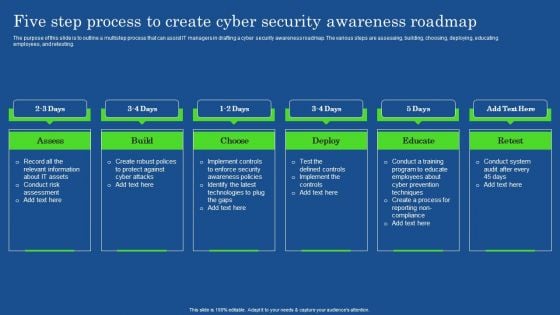
Five Step Process To Create Cyber Security Awareness Roadmap Microsoft PDF
The purpose of this slide is to outline a multistep process that can assist IT managers in drafting a cyber security awareness roadmap. The various steps are assessing, building, choosing, deploying, educating employees, and retesting. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Five Step Process To Create Cyber Security Awareness Roadmap Microsoft PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Five Step Process To Create Cyber Security Awareness Roadmap Microsoft PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers
Dashboard To Track IT Security Incidents Prevailing Across Firm Infographics PDF
This slide portrays information regarding the dashboard that firm will track various incidents detected. These incidents will be managed in order to avoid security risks. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Dashboard To Track IT Security Incidents Prevailing Across Firm Infographics PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Dashboard To Track IT Security Incidents Prevailing Across Firm Infographics PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.

Prevention Of Information How To Overcome The Security Awareness Training Introduction PDF
The purpose of this is to highlight various solutions which can be used to overcome the cyber security awareness challenges. The key solutions covered in the slide are introducing dynamic courses, fully managed training. If you are looking for a format to display your unique thoughts, then the professionally designed Prevention Of Information How To Overcome The Security Awareness Training Introduction PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Prevention Of Information How To Overcome The Security Awareness Training Introduction PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Implementing Cybersecurity Awareness Program To Prevent Attacks How To Overcome The Security Awareness Summary PDF
The purpose of this is to highlight various solutions which can be used to overcome the cyber security awareness challenges. The key solutions covered in the slide are introducing dynamic courses, fully managed training program, convenient program etc. If you are looking for a format to display your unique thoughts, then the professionally designed Implementing Cybersecurity Awareness Program To Prevent Attacks How To Overcome The Security Awareness Summary PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Implementing Cybersecurity Awareness Program To Prevent Attacks How To Overcome The Security Awareness Summary PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
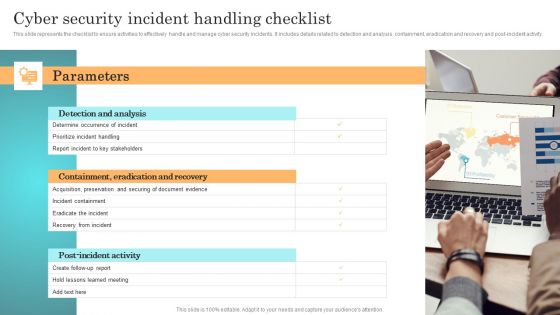
Incident Response Techniques Deployement Cyber Security Incident Handling Checklist Infographics PDF
This slide represents the checklist to ensure activities to effectively handle and manage cyber security incidents. It includes details related to detection and analysis, containment, eradication and recovery and post-incident activity. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Incident Response Techniques Deployement Cyber Security Incident Communication Strategy Brochure PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Incident Response Techniques Deployement Cyber Security Incident Communication Strategy Brochure PDF
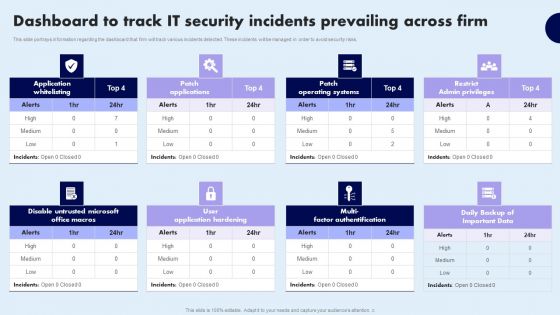
Dashboard To Track IT Security Incidents Prevailing Across Firm Demonstration PDF
This slide portrays information regarding the dashboard that firm will track various incidents detected. These incidents will be managed in order to avoid security risks. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Dashboard To Track IT Security Incidents Prevailing Across Firm Demonstration PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Dashboard To Track IT Security Incidents Prevailing Across Firm Demonstration PDF today and make your presentation stand out from the rest

How To Overcome The Security Awareness Training Program Challenges Infographics PDF
The purpose of this is to highlight various solutions which can be used to overcome the cyber security awareness challenges. The key solutions covered in the slide are introducing dynamic courses, fully managed training program, convenient program etc. Create an editable How To Overcome The Security Awareness Training Program Challenges Infographics PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. How To Overcome The Security Awareness Training Program Challenges Infographics PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Introduction PDF
This slide provides information about the fifth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Fine Tune Monitoring System. This is a modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring introduction pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity monitoring plan steps in detail fine tune monitoring system. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
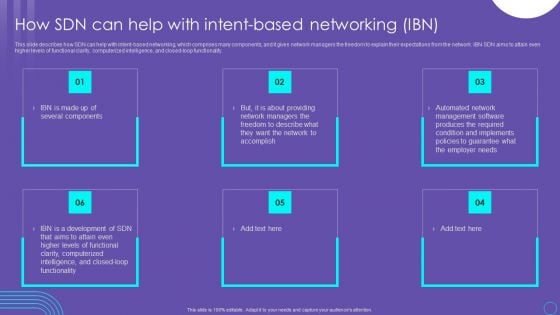
SDN Security Architecture How SDN Can Help With Intent Based Networking IBN Themes PDF
This slide describes how SDN can help with intent based networking, which comprises many components, and it gives network managers the freedom to explain their expectations from the network. IBN SDN aims to attain even higher levels of functional clarity, computerized intelligence, and closed loop functionality. Explore a selection of the finest SDN Security Architecture How SDN Can Help With Intent Based Networking IBN Themes PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our SDN Security Architecture How SDN Can Help With Intent Based Networking IBN Themes PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
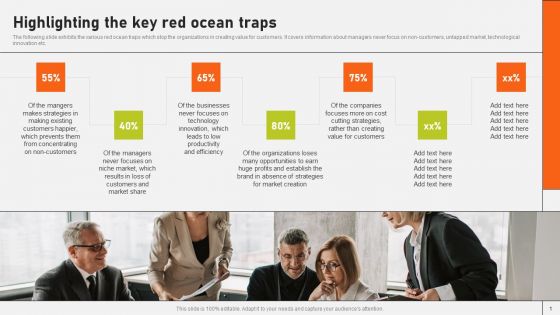
Securing Market Leadership Through Competitive Excellence Highlighting The Key Red Ocean Traps Guidelines PDF
The following slide exhibits the various red ocean traps which stop the organizations in creating value for customers. It covers information about managers never focus on non-customers, untapped market, technological innovation etc. Present like a pro with Securing Market Leadership Through Competitive Excellence Highlighting The Key Red Ocean Traps Guidelines PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
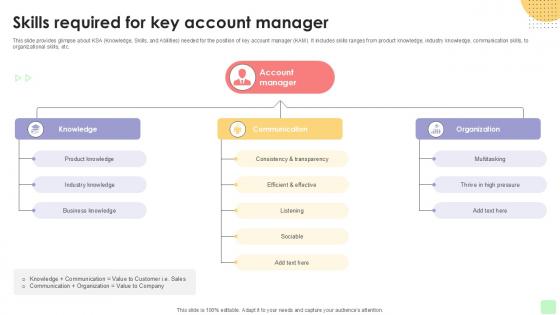
Skills Required For Key Account Detailed Business Account PPT Sample Strategy SS V
This slide provides glimpse about KSA Knowledge, Skills, and Abilities needed for the position of key account manager KAM. It includes skills ranges from product knowledge, industry knowledge, communication skills, to organizational skills, etc. Step up your game with our enchanting Skills Required For Key Account Detailed Business Account PPT Sample Strategy SS V deck, guaranteed to leave a lasting impression on your audience. Crafted with a perfect balance of simplicity, and innovation, our deck empowers you to alter it to your specific needs. You can also change the color theme of the slide to mold it to your companys specific needs. Save time with our ready-made design, compatible with Microsoft versions and Google Slides. Additionally, its available for download in various formats including JPG, JPEG, and PNG. Outshine your competitors with our fully editable and customized deck. This slide provides glimpse about KSA Knowledge, Skills, and Abilities needed for the position of key account manager KAM. It includes skills ranges from product knowledge, industry knowledge, communication skills, to organizational skills, etc.
Deploying Corporate Aligned IT Strategy Dashboard To Track IT Security Incidents Prevailing Across Firm Designs PDF
This slide portrays information regarding the dashboard that firm will track various incidents detected. These incidents will be managed in order to avoid security risks. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Deploying Corporate Aligned IT Strategy Dashboard To Track IT Security Incidents Prevailing Across Firm Designs PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Dashboard To Track IT Security Incidents Prevailing Across Firm Ppt PowerPoint Presentation File Outline PDF
This slide portrays information regarding the dashboard that firm will track various incidents detected. These incidents will be managed in order to avoid security risks. Slidegeeks is here to make your presentations a breeze with Dashboard To Track IT Security Incidents Prevailing Across Firm Ppt PowerPoint Presentation File Outline PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
Computer Enhanced Security System Ppt PowerPoint Presentation Show Structure
This is a computer enhanced security system ppt powerpoint presentation show structure. This is a three stage process. The stages in this process are access rights, access management, business.

Case Study 4 Improving Patient Security And Reducing Risk Of Violence Graphics PDF
Presenting case study 4 improving patient security and reducing risk of violence graphics pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like building management, security management, power management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
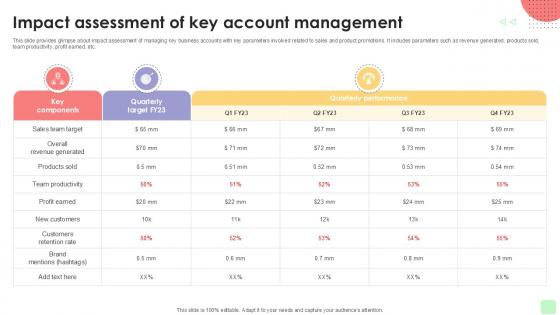
Impact Assessment Of Key Detailed Business Account PPT Example Strategy SS V
This slide provides glimpse about impact assessment of managing key business accounts with key parameters involved related to sales and product promotions. It includes parameters such as revenue generated, products sold, team productivity, profit earned, etc. Step up your game with our enchanting Impact Assessment Of Key Detailed Business Account PPT Example Strategy SS V deck, guaranteed to leave a lasting impression on your audience. Crafted with a perfect balance of simplicity, and innovation, our deck empowers you to alter it to your specific needs. You can also change the color theme of the slide to mold it to your companys specific needs. Save time with our ready-made design, compatible with Microsoft versions and Google Slides. Additionally, its available for download in various formats including JPG, JPEG, and PNG. Outshine your competitors with our fully editable and customized deck. This slide provides glimpse about impact assessment of managing key business accounts with key parameters involved related to sales and product promotions. It includes parameters such as revenue generated, products sold, team productivity, profit earned, etc.
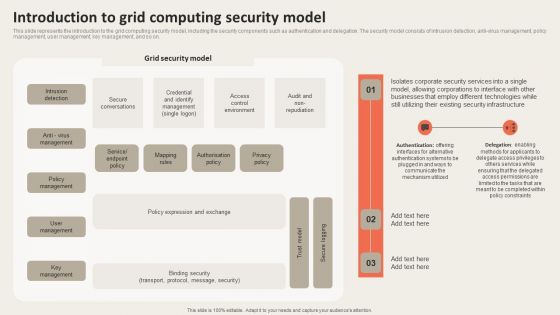
Grid Computing Applications Introduction To Grid Computing Security Model Rules PDF
This slide represents the introduction to the grid computing security model, including the security components such as authentication and delegation. The security model consists of intrusion detection, anti-virus management, policy management, user management, key management, and so on. Make sure to capture your audiences attention in your business displays with our gratis customizable Grid Computing Applications Introduction To Grid Computing Security Model Rules PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
Grid Computing For High Performance Solutions Introduction To Grid Computing Security Model Icons PDF
This slide represents the introduction to the grid computing security model, including the security components such as authentication and delegation. The security model consists of intrusion detection, anti-virus management, policy management, user management, key management, and so on. There are so many reasons you need a Grid Computing For High Performance Solutions Introduction To Grid Computing Security Model Icons PDF. The first reason is you cannot spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Setting Up Access Control System In Organization Application Security Testing
This slide represents the installation process of access control system for application security in an organization. Explore a selection of the finest Setting Up Access Control System In Organization Application Security Testing here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Setting Up Access Control System In Organization Application Security Testing to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide represents the installation process of access control system for application security in an organization.

Access Control Computer Screen With Lock Ppt PowerPoint Presentation Ideas Templates
This is aaccess control computer screen with lock ppt powerpoint presentation ideas templates. This is a two stage process. The stages in this process are access rights, access management, business.

Door Access Control Padlock On Door Ppt PowerPoint Presentation Infographic Template Graphics Example
This is a door access control padlock on door ppt powerpoint presentation infographic template graphics example. This is a four stage process. The stages in this process are access rights, access management, business.
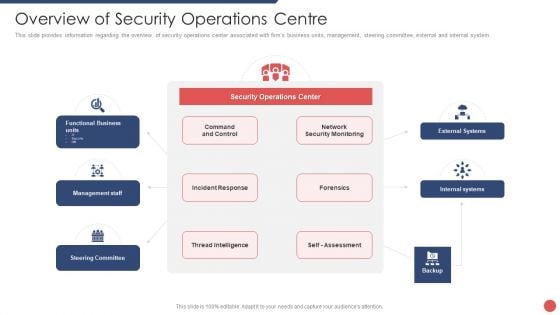
Security Functioning Centre Overview Of Security Operations Centre Summary PDF
This slide provides information regarding the overview of security operations center associated with firms business units, management, steering committee, external and internal system. Deliver and pitch your topic in the best possible manner with this security functioning centre overview of security operations centre summary pdf. Use them to share invaluable insights on management, thread intelligence, network security monitoring and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Adopt Security Auditing Checklist Comprehensive Guide To Blockchain Digital Security Template Pdf
The following slide depicts blockchain cybersecurity auditing checklist to minimize probability of frauds. It includes elements such as network, node, smart contract, security, consensus mechanism, data encryption, access management, etc. Are you searching for a Adopt Security Auditing Checklist Comprehensive Guide To Blockchain Digital Security Template Pdf that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Adopt Security Auditing Checklist Comprehensive Guide To Blockchain Digital Security Template Pdf from Slidegeeks today. The following slide depicts blockchain cybersecurity auditing checklist to minimize probability of frauds. It includes elements such as network, node, smart contract, security, consensus mechanism, data encryption, access management, etc.

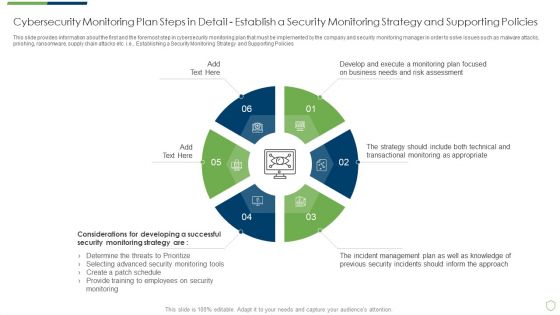
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Plan Steps In Professional PDF
This slide provides information about the first and the foremost step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Establishing a Security Monitoring Strategy and Supporting Policies. Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring plan steps in professional pdf bundle. Topics like cybersecurity monitoring plan steps in detail establish a security monitoring strategy and supporting policies can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
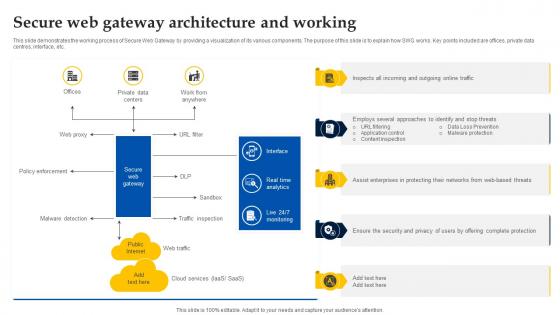
Web Access Control Solution Secure Web Gateway Architecture And Working
This slide demonstrates the working process of Secure Web Gateway by providing a visualization of its various components. The purpose of this slide is to explain how SWG works. Key points included are offices, private data centres, interface, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Web Access Control Solution Secure Web Gateway Architecture And Working for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide demonstrates the working process of Secure Web Gateway by providing a visualization of its various components. The purpose of this slide is to explain how SWG works. Key points included are offices, private data centres, interface, etc.
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Plan Steps In Detail Structure PDF
This slide provides information about the sixth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Setting up a Centralized Collection and Analysis Capability. This is a modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring plan steps in detail structure pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity monitoring plan steps in detail setting up a centralized collection and analysis capability. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
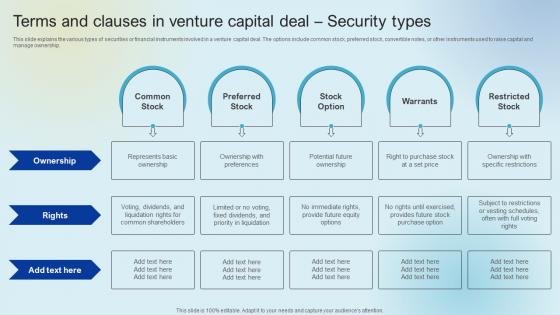
Terms And Clauses In Venture Raising Venture Capital A Holistic Approach Fin SS V
This slide explains the various types of securities or financial instruments involved in a venture capital deal. The options include common stock, preferred stock, convertible notes, or other instruments used to raise capital and manage ownership. This Terms And Clauses In Venture Raising Venture Capital A Holistic Approach Fin SS V is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Terms And Clauses In Venture Raising Venture Capital A Holistic Approach Fin SS V features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide explains the various types of securities or financial instruments involved in a venture capital deal. The options include common stock, preferred stock, convertible notes, or other instruments used to raise capital and manage ownership.

Various Types E Learning Courses HR Retention Techniques For Business Owners Download Pdf
The purpose of this slide is to showcase different types of online courses through which managers can enhance the existing skills of the workforce. Graphic designing cyber security, ethical hacking, digital marketing and web development are the major courses that are mentioned in the slide. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Various Types E Learning Courses HR Retention Techniques For Business Owners Download Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. The purpose of this slide is to showcase different types of online courses through which managers can enhance the existing skills of the workforce. Graphic designing cyber security, ethical hacking, digital marketing and web development are the major courses that are mentioned in the slide.
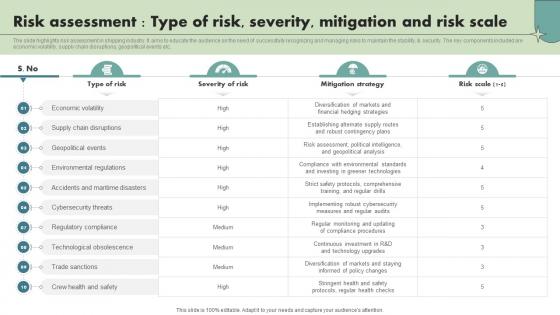
Risk Assessment Type Of Risk Severity Mitigation And Risk Scale Maritime Shipping Industry IR SS V
The slide highlights risk assessment in shipping industry. It aims to educate the audience on the need of successfully recognizing and managing risks to maintain the stability, and security. The key components included are economic volatility, supply chain disruptions, geopolitical events etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Risk Assessment Type Of Risk Severity Mitigation And Risk Scale Maritime Shipping Industry IR SS V to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Risk Assessment Type Of Risk Severity Mitigation And Risk Scale Maritime Shipping Industry IR SS V. The slide highlights risk assessment in shipping industry. It aims to educate the audience on the need of successfully recognizing and managing risks to maintain the stability, and security. The key components included are economic volatility, supply chain disruptions, geopolitical events etc.
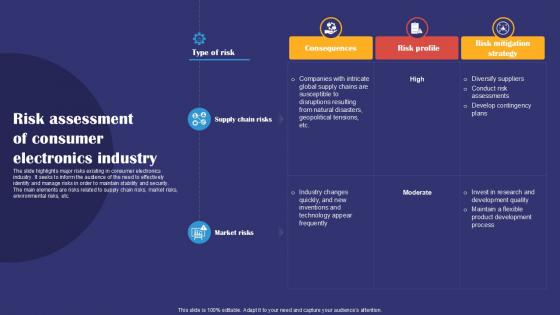
Risk Assessment Of Consumer Electronics Industry Smartphones Industry Report PPT Sample IR SS V
The slide highlights major risks existing in consumer electronics industry. It seeks to inform the audience of the need to effectively identify and manage risks in order to maintain stability and security. The main elements are risks related to supply chain risks, market risks, environmental risks, etc. Presenting this PowerPoint presentation, titled Risk Assessment Of Consumer Electronics Industry Smartphones Industry Report PPT Sample IR SS V, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Risk Assessment Of Consumer Electronics Industry Smartphones Industry Report PPT Sample IR SS V. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Risk Assessment Of Consumer Electronics Industry Smartphones Industry Report PPT Sample IR SS V that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. The slide highlights major risks existing in consumer electronics industry. It seeks to inform the audience of the need to effectively identify and manage risks in order to maintain stability and security. The main elements are risks related to supply chain risks, market risks, environmental risks, etc.
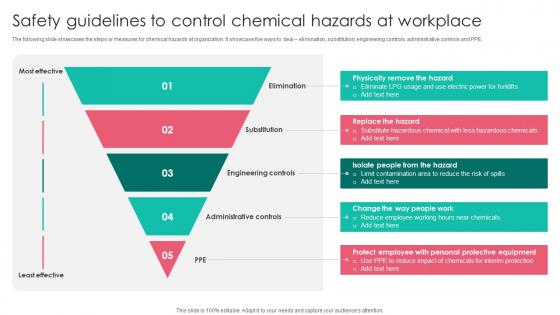
Safety Guidelines Control Chemical Workplace Safety Protocol And Security Practices Portrait Pdf
The following slide showcases the steps or measures for chemical hazards at organization. It showcase five ways to deal elimination, substitution, engineering controls, administrative controls and PPE.Find a pre designed and impeccable Safety Guidelines Control Chemical Workplace Safety Protocol And Security Practices Portrait Pdf. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. The following slide showcases the steps or measures for chemical hazards at organization. It showcase five ways to deal elimination, substitution, engineering controls, administrative controls and PPE.
Right Of Access To Private Land Ppt PowerPoint Presentation Pictures Ideas
This is a right of access to private land ppt powerpoint presentation pictures ideas. This is a three stage process. The stages in this process are access rights, access management, business.
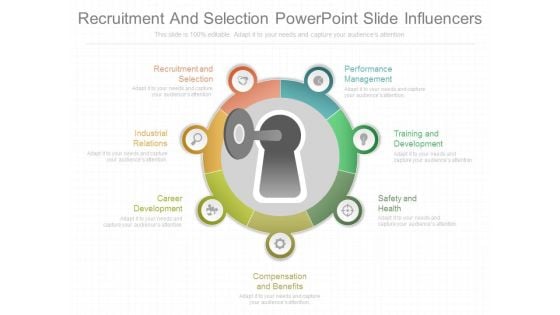
Recruitment And Selection Powerpoint Slide Influencers
This is a recruitment and selection powerpoint slide influencers. This is a seven stage process. The stages in this process are recruitment and selection, industrial relations, career development, compensation and benefits, safety and health, training and development, performance management.
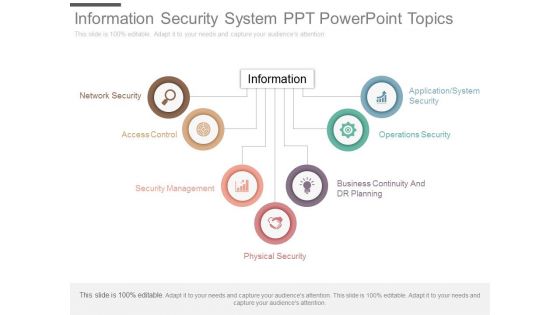
Information Security System Ppt Powerpoint Topics
This is a information security system ppt powerpoint topics. This is a seven stage process. The stages in this process are network security, access control, security management, physical security, business continuity and dr planning, operations security, application system security, information.
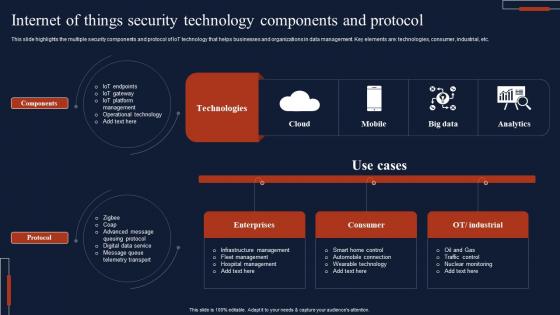
Internet Of Things Security Technology Components And Protocol Rules Pdf
This slide highlights the multiple security components and protocol of IoT technology that helps businesses and organizations in data management. Key elements are technologies, consumer, industrial, etc. Pitch your topic with ease and precision using this Internet Of Things Security Technology Components And Protocol Rules Pdf This layout presents information on Components, Protocol, Technologies, Consumer It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide highlights the multiple security components and protocol of IoT technology that helps businesses and organizations in data management. Key elements are technologies, consumer, industrial, etc.
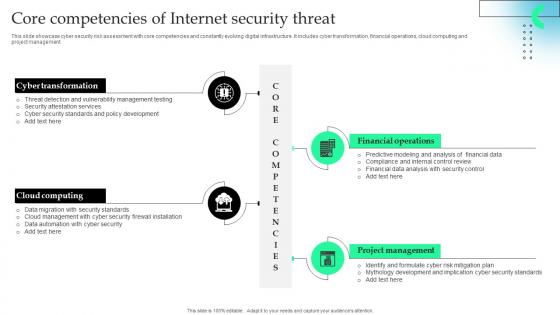
Core Competencies Of Internet Security Threat Portrait Pdf
This slide showcase cyber security risk assessment with core competencies and constantly evolving digital infrastructure. It includes cyber transformation, financial operations, cloud computing and project management.Showcasing this set of slides titled Core Competencies Of Internet Security Threat Portrait Pdf The topics addressed in these templates are Cyber Transformation, Cloud Computing, Financial Operations All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcase cyber security risk assessment with core competencies and constantly evolving digital infrastructure. It includes cyber transformation, financial operations, cloud computing and project management.

Impacts Of Cyber Security Data Compliance
Want to ace your presentation in front of a live audience Our Impacts Of Cyber Security Data Compliance can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide highlights benefits of cyber security compliance aiming to protect sensitive data and maintain integrity of information systems. It further includes benefits such as strengthening data protection etc.

Checklist For Inspecting Office Security To Ensure Employees Portrait Pdf
Following slide shows checklist for office safety inspection to assure staff which will assist in reducing employee turnover because of work environment. It includes major parameters such as housekeeping, ergonomics, electricals, etc. Showcasing this set of slides titled Checklist For Inspecting Office Security To Ensure Employees Portrait Pdf. The topics addressed in these templates are Satisfactory, Unsatisfactory, Checklist Parameters. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Following slide shows checklist for office safety inspection to assure staff which will assist in reducing employee turnover because of work environment. It includes major parameters such as housekeeping, ergonomics, electricals, etc.
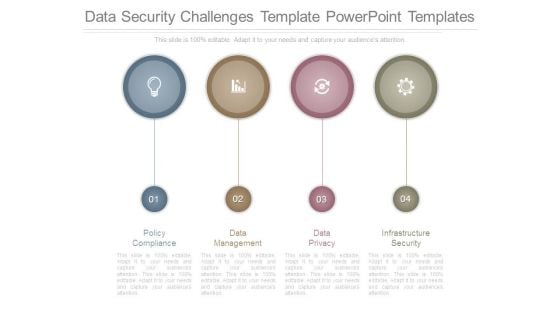
Data Security Challenges Template Powerpoint Templates
This is a data security challenges template powerpoint templates. This is a four stage process. The stages in this process are policy compliance, data management, data privacy, infrastructure security.
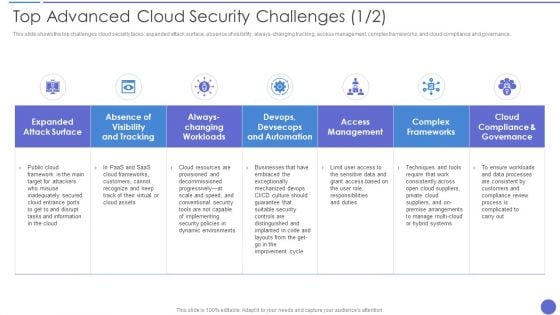
Top Advanced Cloud Security Challenges Brochure PDF
This slide shows the top challenges cloud security faces expanded attack surface, absence of visibility, always changing tracking, access management, complex frameworks, and cloud compliance and governance. Deliver an awe inspiring pitch with this creative Top Advanced Cloud Security Challenges Brochure PDF bundle. Topics like Complex Frameworks, Access Management, Dynamic Environments can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
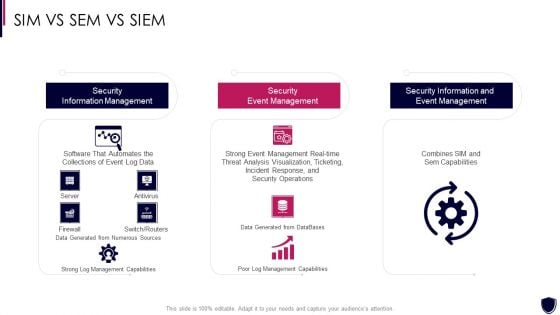
Enhancing Cyber Safety With Vulnerability Administration SIM Vs SEM Vs SIEM Brochure PDF
Presenting enhancing cyber safety with vulnerability administration sim vs sem vs siem brochure pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like security information management, security event management, security information and event management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
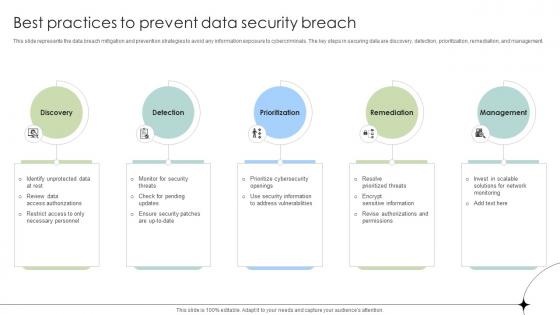
Best Practices To Prevent Data Security Breach Data Fortification Strengthening Defenses
This slide represents the data breach mitigation and prevention strategies to avoid any information exposure to cybercriminals. The key steps in securing data are discovery, detection, prioritization, remediation, and management. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Best Practices To Prevent Data Security Breach Data Fortification Strengthening Defenses a try. Our experts have put a lot of knowledge and effort into creating this impeccable Best Practices To Prevent Data Security Breach Data Fortification Strengthening Defenses. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide represents the data breach mitigation and prevention strategies to avoid any information exposure to cybercriminals. The key steps in securing data are discovery, detection, prioritization, remediation, and management.

Developing Firm Security Strategy Plan Addressing Performance Indicators To Determine Security Standards Structure PDF
This slide provides information about performance indicators in order to determine security standards at workplace in terms of incidents, offender management, risk assessments. Deliver an awe inspiring pitch with this creative developing firm security strategy plan addressing performance indicators to determine security standards structure pdf bundle. Topics like incidents, offender management, risk assessments can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
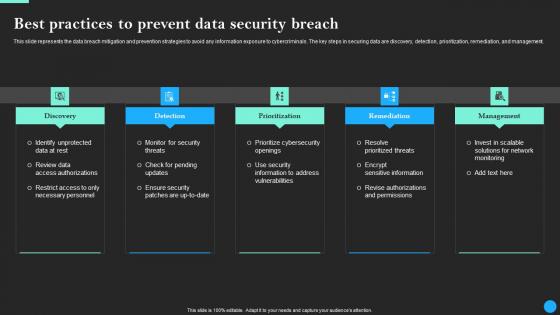
Best Practices To Prevent Data Security Breach Data Breach Prevention Information Pdf
This slide represents the data breach mitigation and prevention strategies to avoid any information exposure to cybercriminals. The key steps in securing data are discovery, detection, prioritization, remediation, and management. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Best Practices To Prevent Data Security Breach Data Breach Prevention Information Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Best Practices To Prevent Data Security Breach Data Breach Prevention Information Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide represents the data breach mitigation and prevention strategies to avoid any information exposure to cybercriminals. The key steps in securing data are discovery, detection, prioritization, remediation, and management.
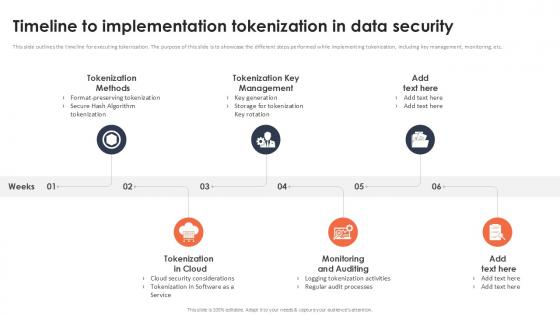
Timeline To Implementation Tokenization In Data Security Securing Your Data Ppt Sample
This slide outlines the timeline for executing tokenization. The purpose of this slide is to showcase the different steps performed while implementing tokenization, including key management, monitoring, etc. Get a simple yet stunning designed Timeline To Implementation Tokenization In Data Security Securing Your Data Ppt Sample It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Timeline To Implementation Tokenization In Data Security Securing Your Data Ppt Sample can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide outlines the timeline for executing tokenization. The purpose of this slide is to showcase the different steps performed while implementing tokenization, including key management, monitoring, etc.
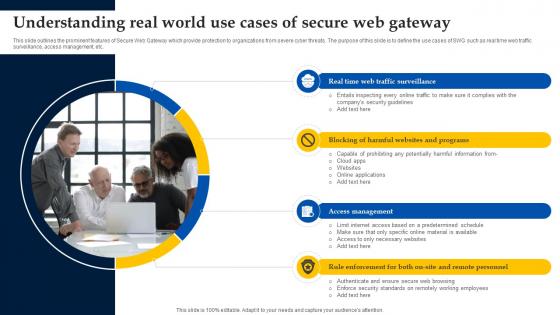
Web Access Control Solution Understanding Real World Use Cases Of Secure Web Gateway
This slide outlines the prominent features of Secure Web Gateway which provide protection to organizations from severe cyber threats. The purpose of this slide is to define the use cases of SWG such as real time web traffic surveillance, access management, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Web Access Control Solution Understanding Real World Use Cases Of Secure Web Gateway is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Web Access Control Solution Understanding Real World Use Cases Of Secure Web Gateway and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide outlines the prominent features of Secure Web Gateway which provide protection to organizations from severe cyber threats. The purpose of this slide is to define the use cases of SWG such as real time web traffic surveillance, access management, etc.


 Continue with Email
Continue with Email

 Home
Home


































